Ransomware Threats on Revenue Cycle: Motherboard and More Pty Ltd
VerifiedAdded on 2020/03/28
|10
|1638
|81
Report
AI Summary
This report focuses on the threats of ransomware attacks on the revenue cycle of Motherboard and More Pty Ltd, a medium-sized Australian firm. It analyzes the organization's revenue cycle, identifying weaknesses such as credit sales and the use of a single dock, and their impact on operations. The report delves into the nature of ransomware attacks, emphasizing their encryption methods and the demand for ransom payments. It proposes control measures like reducing credit, implementing software for tracking goods, establishing a database, and creating alternative solutions for returns. Furthermore, the report underscores the importance of security measures such as antivirus software, data backups, and security patches to mitigate the risk of ransomware attacks, providing a comprehensive overview of the issue and suggesting actionable solutions for businesses.

Running Head: ACCOUNTING INFORMATION SYSTEM
ACCOUNTING INFORMATION SYSTEM
Name of the student
Name of the University
Author Note:
ACCOUNTING INFORMATION SYSTEM
Name of the student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ACCOUNTING INFORMATION SYSTEM
Executive Summary
The given report mainly emphasizes on the various threats of ransomware on the organizations
revenue cycle. For the given report the organization chosen is Motherboard and More Pty Ltd.
The report mainly relates to the various risk mitigation process related to this ransomware attack.
Proper analysis on attack ransomware is checked with its principle of working with its effect on
various system round the globe has been discussed properly in the coming pages the given
report. Various other factors like backup of Data, adoption of different security measure,
application of different security patches has been discussed properly
Executive Summary
The given report mainly emphasizes on the various threats of ransomware on the organizations
revenue cycle. For the given report the organization chosen is Motherboard and More Pty Ltd.
The report mainly relates to the various risk mitigation process related to this ransomware attack.
Proper analysis on attack ransomware is checked with its principle of working with its effect on
various system round the globe has been discussed properly in the coming pages the given
report. Various other factors like backup of Data, adoption of different security measure,
application of different security patches has been discussed properly

2ACCOUNTING INFORMATION SYSTEM
Table of Contents
Executive Summary.............................................................................................................1
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Overview of revenue cycle..................................................................................................3
Identification of Weakness..................................................................................................5
Weakness.........................................................................................................................5
Impact of Weakness.........................................................................................................5
Control.............................................................................................................................6
Overview of ransomware attack..........................................................................................6
Control of ransomware attack..............................................................................................7
Conclusion...........................................................................................................................7
References............................................................................................................................8
Table of Contents
Executive Summary.............................................................................................................1
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Overview of revenue cycle..................................................................................................3
Identification of Weakness..................................................................................................5
Weakness.........................................................................................................................5
Impact of Weakness.........................................................................................................5
Control.............................................................................................................................6
Overview of ransomware attack..........................................................................................6
Control of ransomware attack..............................................................................................7
Conclusion...........................................................................................................................7
References............................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ACCOUNTING INFORMATION SYSTEM
Introduction
The given report is all about various threats of ransomware attack on the organizations
revenue cycle. The firm chosen for the report is Motherboard and More Pty Ltd. The report also
focuses on the various dangerous effects and possible way that must be chosen to overcome the
problem (Andronio, Zanero & Maggi, 2015). It also emphasizes on the different possible ways
that must be used for checking the organizations revenue cycle and it also recommends the
various techniques that must be chosen to overcome the problem.
Discussion
The given organization that is Motherboard and More Pty Ltd is considered as a medium
size firm which is located in Australia. This firm mainly emphasizes on the manufacturing of
computer microchip, graphic card and motherboard. Apart from this the firm also manufacture
various computer system and also repair system which is based in Australia (Everett, 2016).
This organization has various business firm in Australia for more than eight years and has
integrated framework for ERP system. In the central building of this building the managerial
place of work is located which mainly manages the manufacturing and import and export
division which are situated on the verge of the town that is considered to very easily
approachable with in few minutes of time.
Overview of revenue cycle
This particular organization mainly takes order form different firms by using different
methods like Email, Telephone and the order can be easily put on the portal of this particular
company (Faruki et al., 2012). Various order received can be easily delivered to the dock which
is considered to be best for managing both the imported and exported goods via different order of
Introduction
The given report is all about various threats of ransomware attack on the organizations
revenue cycle. The firm chosen for the report is Motherboard and More Pty Ltd. The report also
focuses on the various dangerous effects and possible way that must be chosen to overcome the
problem (Andronio, Zanero & Maggi, 2015). It also emphasizes on the different possible ways
that must be used for checking the organizations revenue cycle and it also recommends the
various techniques that must be chosen to overcome the problem.
Discussion
The given organization that is Motherboard and More Pty Ltd is considered as a medium
size firm which is located in Australia. This firm mainly emphasizes on the manufacturing of
computer microchip, graphic card and motherboard. Apart from this the firm also manufacture
various computer system and also repair system which is based in Australia (Everett, 2016).
This organization has various business firm in Australia for more than eight years and has
integrated framework for ERP system. In the central building of this building the managerial
place of work is located which mainly manages the manufacturing and import and export
division which are situated on the verge of the town that is considered to very easily
approachable with in few minutes of time.
Overview of revenue cycle
This particular organization mainly takes order form different firms by using different
methods like Email, Telephone and the order can be easily put on the portal of this particular
company (Faruki et al., 2012). Various order received can be easily delivered to the dock which
is considered to be best for managing both the imported and exported goods via different order of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
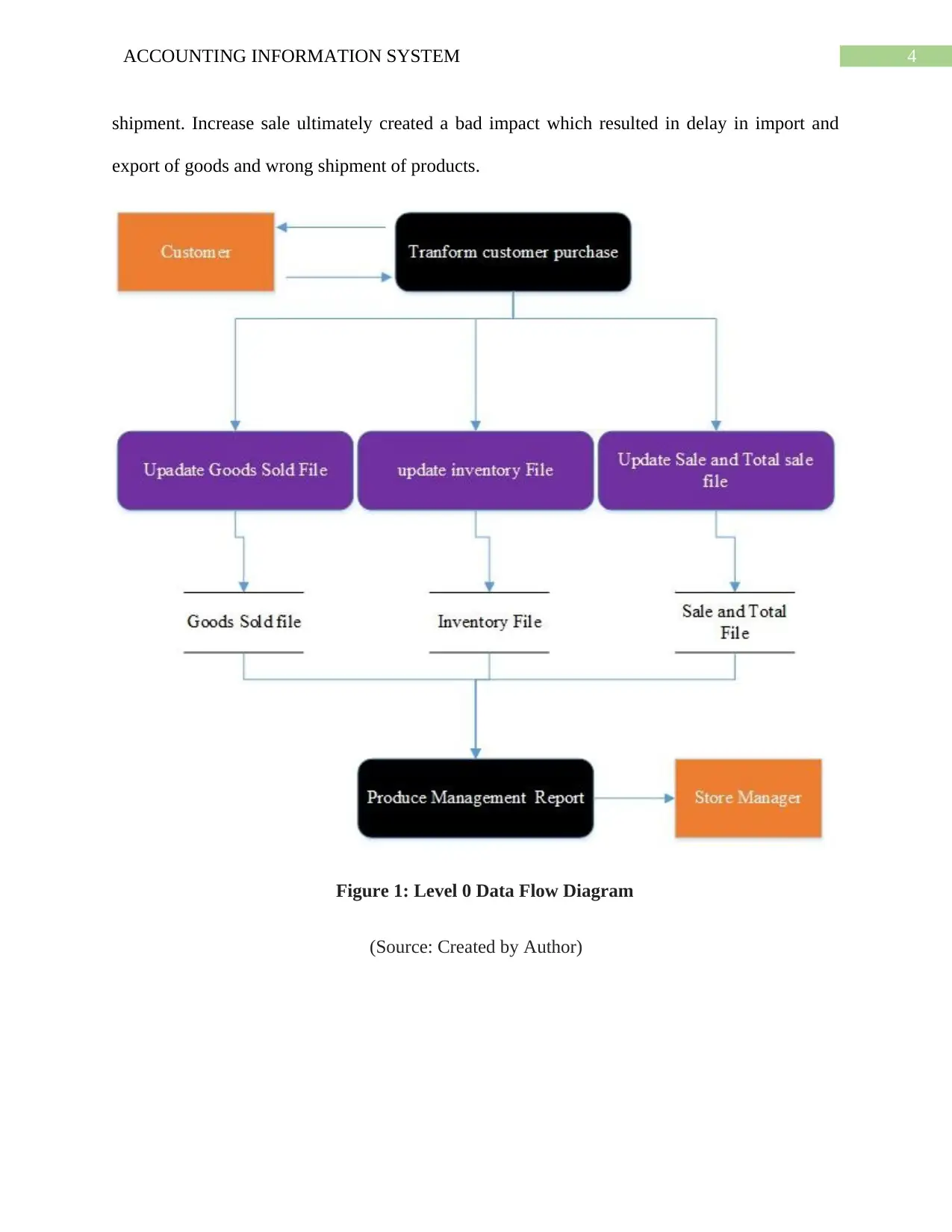
4ACCOUNTING INFORMATION SYSTEM
shipment. Increase sale ultimately created a bad impact which resulted in delay in import and
export of goods and wrong shipment of products.
Figure 1: Level 0 Data Flow Diagram
(Source: Created by Author)
shipment. Increase sale ultimately created a bad impact which resulted in delay in import and
export of goods and wrong shipment of products.
Figure 1: Level 0 Data Flow Diagram
(Source: Created by Author)

5ACCOUNTING INFORMATION SYSTEM
Identification of Weakness
This particular part of the report mainly focuses on the different methods that may be
adopted easily for monitoring weakness and the effect of it on the revenue cycle of Motherboard
and More Pty Ltd. Apart from this it also checks the possible solution for the weakness of this
organization.
Weakness
Department of organization of this organization is addressing some issue due to many
weaknesses that are present in the internal part of the organization (Kharraz et al., 2015). The
first issue that is firm is addressing is that it allows the various consumers to buy products on
credit which has ultimately reduced the growth of profit of this organization. The second
problem that is issued is that usage of dock for both incoming and outgoing products using dock.
Impact of Weakness
First weakness that this firm is addressing is that is allow the consumer to buy and sell
goods on credit, this ultimately brings us to the point that firm is giving the product to consumers
for 30 days’ free trial. Due to this the sales operation of this organization was hampered in the
operation of product which is given or provided to customer at the time of delivery (Mercaldo et
al.,2016). The next weakness that is addressed is using dock for delivery of various products and
operation which are mainly related for addressing of goods in a right way to promote easy
delivery of products. Various organization all around globe mainly requires a proper data for
maintaining of various goods that are imported and exported.
Control
This part of the given report mainly focuses on the different ways of control that can be
easily applied to various business for tracking the various risk that is involved (O'Gorman &
Identification of Weakness
This particular part of the report mainly focuses on the different methods that may be
adopted easily for monitoring weakness and the effect of it on the revenue cycle of Motherboard
and More Pty Ltd. Apart from this it also checks the possible solution for the weakness of this
organization.
Weakness
Department of organization of this organization is addressing some issue due to many
weaknesses that are present in the internal part of the organization (Kharraz et al., 2015). The
first issue that is firm is addressing is that it allows the various consumers to buy products on
credit which has ultimately reduced the growth of profit of this organization. The second
problem that is issued is that usage of dock for both incoming and outgoing products using dock.
Impact of Weakness
First weakness that this firm is addressing is that is allow the consumer to buy and sell
goods on credit, this ultimately brings us to the point that firm is giving the product to consumers
for 30 days’ free trial. Due to this the sales operation of this organization was hampered in the
operation of product which is given or provided to customer at the time of delivery (Mercaldo et
al.,2016). The next weakness that is addressed is using dock for delivery of various products and
operation which are mainly related for addressing of goods in a right way to promote easy
delivery of products. Various organization all around globe mainly requires a proper data for
maintaining of various goods that are imported and exported.
Control
This part of the given report mainly focuses on the different ways of control that can be
easily applied to various business for tracking the various risk that is involved (O'Gorman &
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6ACCOUNTING INFORMATION SYSTEM
McDonald, 2012). The organization should reduce the value of credit as it directly affects the
organization. Different consumer with good credit score are not given credit for balancing its
rank in market.
Control of internal
weakness
Effect Possible Solution to
tackle the problem
Buying different
goods on credit
Sales operation was
disturbed badly
Checking of credit
scores of customers
Using the same dock
different products are
shipped.
Unable to maintain
the count of different
products.
Delivery of goods can
be easily tracked by using a
proper software.
Non-presence of a
database
Different goods
cannot be tracked easily
Proper database needs
to be implemented.
High discount is given
while returning of products.
Customers always
choose this method which has
led to reduce the amount of
profit.
Alternative solution is
needed.
Overview of ransomware attack
Ransomware attack is the biggest cyber-attack which impacted almost every system of
globe. This attack mainly involves the encryption of different important files containing data and
information which ultimately prevents its access (Pathak & Nanded, 2016). The impacted
computers mainly displayed a message containing information which contains a note displaying
the demand of money of 300 dollars to the hackers.
McDonald, 2012). The organization should reduce the value of credit as it directly affects the
organization. Different consumer with good credit score are not given credit for balancing its
rank in market.
Control of internal
weakness
Effect Possible Solution to
tackle the problem
Buying different
goods on credit
Sales operation was
disturbed badly
Checking of credit
scores of customers
Using the same dock
different products are
shipped.
Unable to maintain
the count of different
products.
Delivery of goods can
be easily tracked by using a
proper software.
Non-presence of a
database
Different goods
cannot be tracked easily
Proper database needs
to be implemented.
High discount is given
while returning of products.
Customers always
choose this method which has
led to reduce the amount of
profit.
Alternative solution is
needed.
Overview of ransomware attack
Ransomware attack is the biggest cyber-attack which impacted almost every system of
globe. This attack mainly involves the encryption of different important files containing data and
information which ultimately prevents its access (Pathak & Nanded, 2016). The impacted
computers mainly displayed a message containing information which contains a note displaying
the demand of money of 300 dollars to the hackers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ACCOUNTING INFORMATION SYSTEM
Control of ransomware attack
Ransomware can be considered to be the biggest attack which impacted more than 99
countries round the globe. This particular firm needs to maintain a track on the security by
making use of various software of antivirus in various system. Software of antivirus are mainly
considered to be helpful in detecting the existence of any virus in the different system. Backup of
data is considered to be very useful for given system as it promotes in building a secure system
to tackle any disaster (Song, Kim & Lee, 2016). As the many systems have faults in it, it become
the key point for the hackers to implement attacks like ransomware. Patches are considered to be
very useful for eliminating various attacks.
Conclusion
From the given that is done in the report it can be concluded that various organization
must maintain a track on the advice that is provided in the instruction part of this report. The
following advice will help various organization round the globe in taking some proper ways that
is proved to be beneficial to this organization. Proper checking on ransomware attack is done
with its principle of working, measure to control has been discussed. Certain measure must be
taken to control the attack of ransomware are like back of vital data containing information,
choosing certain security methods, application of various patches of security has been stated in
briefly in the report.
Control of ransomware attack
Ransomware can be considered to be the biggest attack which impacted more than 99
countries round the globe. This particular firm needs to maintain a track on the security by
making use of various software of antivirus in various system. Software of antivirus are mainly
considered to be helpful in detecting the existence of any virus in the different system. Backup of
data is considered to be very useful for given system as it promotes in building a secure system
to tackle any disaster (Song, Kim & Lee, 2016). As the many systems have faults in it, it become
the key point for the hackers to implement attacks like ransomware. Patches are considered to be
very useful for eliminating various attacks.
Conclusion
From the given that is done in the report it can be concluded that various organization
must maintain a track on the advice that is provided in the instruction part of this report. The
following advice will help various organization round the globe in taking some proper ways that
is proved to be beneficial to this organization. Proper checking on ransomware attack is done
with its principle of working, measure to control has been discussed. Certain measure must be
taken to control the attack of ransomware are like back of vital data containing information,
choosing certain security methods, application of various patches of security has been stated in
briefly in the report.

8ACCOUNTING INFORMATION SYSTEM
References
Andronio, N., Zanero, S., & Maggi, F. (2015, November). Heldroid: Dissecting and detecting
mobile ransomware. In International Workshop on Recent Advances in Intrusion
Detection (pp. 382-404). Springer International Publishing.
Everett, C. (2016). Ransomware: to pay or not to pay? Computer Fraud & Security, 2016(4), 8-
12.
Faruki, P., Laxmi, V., Gaur, M. S., & Vinod, P. (2012, October). Mining control flow graph as
API call-grams to detect portable executable malware. In Proceedings of the Fifth
International Conference on Security of Information and Networks (pp. 130-137). ACM.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International Conference
on Detection of Intrusions and Malware, and Vulnerability Assessment (pp. 3-24).
Springer, Cham.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal Techniques
for Distributed Objects, Components, and Systems (pp. 212-221). Springer, Cham.
O'Gorman, G., & McDonald, G. (2012). Ransomware: A growing menace. Symantec
Corporation.
Pathak, D. P., & Nanded, Y. M. (2016). A dangerous trend of cybercrime: ransomware growing
challenge. International Journal of Advanced Research in Computer Engineering &
Technology (IJARCET) Volume, 5.
References
Andronio, N., Zanero, S., & Maggi, F. (2015, November). Heldroid: Dissecting and detecting
mobile ransomware. In International Workshop on Recent Advances in Intrusion
Detection (pp. 382-404). Springer International Publishing.
Everett, C. (2016). Ransomware: to pay or not to pay? Computer Fraud & Security, 2016(4), 8-
12.
Faruki, P., Laxmi, V., Gaur, M. S., & Vinod, P. (2012, October). Mining control flow graph as
API call-grams to detect portable executable malware. In Proceedings of the Fifth
International Conference on Security of Information and Networks (pp. 130-137). ACM.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International Conference
on Detection of Intrusions and Malware, and Vulnerability Assessment (pp. 3-24).
Springer, Cham.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal Techniques
for Distributed Objects, Components, and Systems (pp. 212-221). Springer, Cham.
O'Gorman, G., & McDonald, G. (2012). Ransomware: A growing menace. Symantec
Corporation.
Pathak, D. P., & Nanded, Y. M. (2016). A dangerous trend of cybercrime: ransomware growing
challenge. International Journal of Advanced Research in Computer Engineering &
Technology (IJARCET) Volume, 5.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ACCOUNTING INFORMATION SYSTEM
Song, S., Kim, B., & Lee, S. (2016). The effective ransomware prevention technique using
process monitoring on android platform. Mobile Information Systems, 2016.
Song, S., Kim, B., & Lee, S. (2016). The effective ransomware prevention technique using
process monitoring on android platform. Mobile Information Systems, 2016.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





