Analysis of Motherboards and More Pty Ltd: Revenue and Security
VerifiedAdded on 2020/04/07
|7
|1373
|487
Report
AI Summary
The report provides an overview of Motherboards and More Pty Ltd's revenue cycle, detailing the order process from customer placement to payment collection. It identifies internal control weaknesses, such as down payment failures and incorrect packaging, and proposes solutions like commitment fees and proper documentation. The report also examines the threat of ransomware attacks, explaining their spread and impact on organizations, including hospitals. It then outlines cyber security controls that Motherboards and More Pty Ltd can implement, including online activity policies, firewalls, data encryption, and employee awareness programs. The conclusion emphasizes the importance of addressing revenue cycle weaknesses and implementing robust security measures to protect against cyber threats.

Motherboards and More Pty Ltd. Report
Name
Institution
Professor
Course
Date
Name
Institution
Professor
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Executive summary...................................................................................................................................3
Overview of the Revenue Cycle................................................................................................................3
Motherboards and More Pty Ltd Internal controls................................................................................4
Overview of Ransomware attack..............................................................................................................4
Cyber security controls.............................................................................................................................5
Conclusion..................................................................................................................................................6
References..................................................................................................................................................7
Executive summary...................................................................................................................................3
Overview of the Revenue Cycle................................................................................................................3
Motherboards and More Pty Ltd Internal controls................................................................................4
Overview of Ransomware attack..............................................................................................................4
Cyber security controls.............................................................................................................................5
Conclusion..................................................................................................................................................6
References..................................................................................................................................................7

Executive summary
Motherboards and More Pty Ltd is an organization that deals with manufacture of
computer and related accessories. Its revenue cycle gives a clear indication of an entire business
processes. With revenue cycle, it would be possible to monitor how business processes are done
and where errors are prone while improving operational procedures. In case of Ransomware
attack, organization should have proper mechanisms to resolve the problem. Measures such as
creating employees awareness, data encryption and implementing secure operational rules should
be put in place.
Overview of the Revenue Cycle
Customers have various ways of making an order from Motherboards and More Pty Ltd
Company. It can be either through a call, email or through an online ERP. This is provided by
the Company to help in making all customers able to access organizational items. When a
customer places an order, through whatever means, the order is processed from warehouse
department, packing is done and order is made available for delivery or picking by the customer
if no shipping is required. Upon customer receiving the goods, an inspection is done to ascertain
if it meets all the required standards. If it is the right item and are in good conditions, customers
are given an opportunity to pay in either 3 days or 14 days. Customer prepares the invoice, sends
to the bank for payment, Motherboards and More Pty Ltd collects the payments made by the
customer in support of cash receipt as document of poof.
Motherboards and More Pty Ltd is an organization that deals with manufacture of
computer and related accessories. Its revenue cycle gives a clear indication of an entire business
processes. With revenue cycle, it would be possible to monitor how business processes are done
and where errors are prone while improving operational procedures. In case of Ransomware
attack, organization should have proper mechanisms to resolve the problem. Measures such as
creating employees awareness, data encryption and implementing secure operational rules should
be put in place.
Overview of the Revenue Cycle
Customers have various ways of making an order from Motherboards and More Pty Ltd
Company. It can be either through a call, email or through an online ERP. This is provided by
the Company to help in making all customers able to access organizational items. When a
customer places an order, through whatever means, the order is processed from warehouse
department, packing is done and order is made available for delivery or picking by the customer
if no shipping is required. Upon customer receiving the goods, an inspection is done to ascertain
if it meets all the required standards. If it is the right item and are in good conditions, customers
are given an opportunity to pay in either 3 days or 14 days. Customer prepares the invoice, sends
to the bank for payment, Motherboards and More Pty Ltd collects the payments made by the
customer in support of cash receipt as document of poof.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
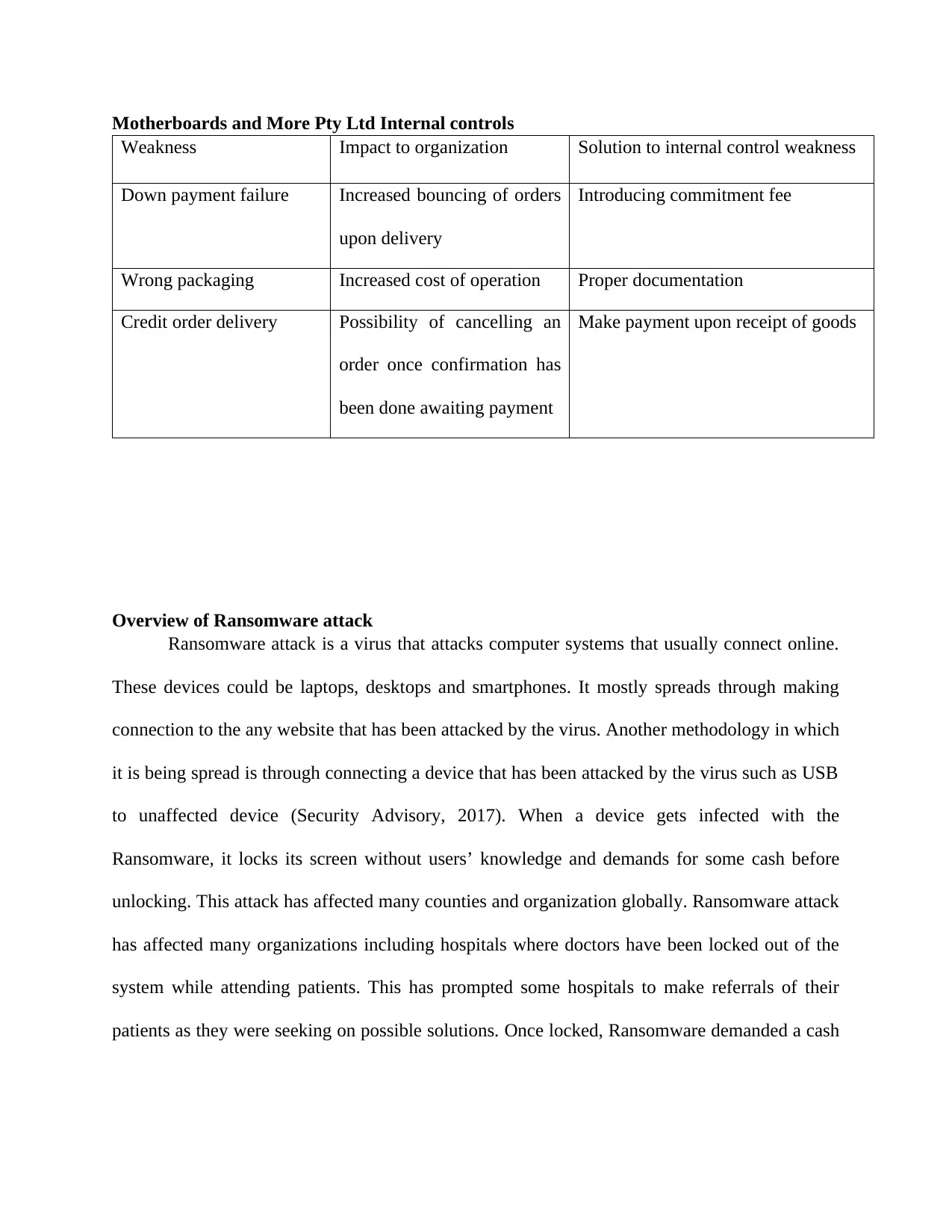
Motherboards and More Pty Ltd Internal controls
Weakness Impact to organization Solution to internal control weakness
Down payment failure Increased bouncing of orders
upon delivery
Introducing commitment fee
Wrong packaging Increased cost of operation Proper documentation
Credit order delivery Possibility of cancelling an
order once confirmation has
been done awaiting payment
Make payment upon receipt of goods
Overview of Ransomware attack
Ransomware attack is a virus that attacks computer systems that usually connect online.
These devices could be laptops, desktops and smartphones. It mostly spreads through making
connection to the any website that has been attacked by the virus. Another methodology in which
it is being spread is through connecting a device that has been attacked by the virus such as USB
to unaffected device (Security Advisory, 2017). When a device gets infected with the
Ransomware, it locks its screen without users’ knowledge and demands for some cash before
unlocking. This attack has affected many counties and organization globally. Ransomware attack
has affected many organizations including hospitals where doctors have been locked out of the
system while attending patients. This has prompted some hospitals to make referrals of their
patients as they were seeking on possible solutions. Once locked, Ransomware demanded a cash
Weakness Impact to organization Solution to internal control weakness
Down payment failure Increased bouncing of orders
upon delivery
Introducing commitment fee
Wrong packaging Increased cost of operation Proper documentation
Credit order delivery Possibility of cancelling an
order once confirmation has
been done awaiting payment
Make payment upon receipt of goods
Overview of Ransomware attack
Ransomware attack is a virus that attacks computer systems that usually connect online.
These devices could be laptops, desktops and smartphones. It mostly spreads through making
connection to the any website that has been attacked by the virus. Another methodology in which
it is being spread is through connecting a device that has been attacked by the virus such as USB
to unaffected device (Security Advisory, 2017). When a device gets infected with the
Ransomware, it locks its screen without users’ knowledge and demands for some cash before
unlocking. This attack has affected many counties and organization globally. Ransomware attack
has affected many organizations including hospitals where doctors have been locked out of the
system while attending patients. This has prompted some hospitals to make referrals of their
patients as they were seeking on possible solutions. Once locked, Ransomware demanded a cash
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

of $300 in order to unlock the device. The only possible solution that deemed appropriate in
short term was to put down all systems to avoid more attacks (Cert-MU, 2017).
Cyber security controls
With rising incidents in cyber security, there is need for organizations to implement
security measures which could be used to protect organization from various attacks such as
Ransomware virus. Some of appropriate application and control measures which could be used
by Motherboards and More Pty Ltd are; putting in place policies which would govern online
activities (Kaplan et al, 2015). Since some of organizational activities are purely done offline, it
is recommended to restrict organizational employees from making any recommended online
connection using organizational computers. Rules governing online connection should be made
clear to all users of the system. To avoid attacks, policies regarding online connection should
govern all devices including personal devices such as smartphones. Some of the employees
makes connection with their devices which later are connected to organizational computers for
data transfer. Secondly, since Motherboards and More Pty Ltd make use of website for clients to
order their goods, firewalls should be implemented with strong security features to screen all
incoming signals which could harm organizational system (Beissel, 2016). In this case, since not
all departments operate online, there should be separate terminals for department that operate
online with those do not. Department that is concerned with order reception through email and
website should be separated from others for security purposes. Separation of operational
procedures makes sure not all departments are affected in case there is an attacker.
Similarly, organization should implement data encryption to prevent data copying to untrusted
parties. Since it is not clear if Ransomware reads data, it is essential to encrypt the entire
organizational data such that if an attacker is reported, no data loss would be experienced. When
short term was to put down all systems to avoid more attacks (Cert-MU, 2017).
Cyber security controls
With rising incidents in cyber security, there is need for organizations to implement
security measures which could be used to protect organization from various attacks such as
Ransomware virus. Some of appropriate application and control measures which could be used
by Motherboards and More Pty Ltd are; putting in place policies which would govern online
activities (Kaplan et al, 2015). Since some of organizational activities are purely done offline, it
is recommended to restrict organizational employees from making any recommended online
connection using organizational computers. Rules governing online connection should be made
clear to all users of the system. To avoid attacks, policies regarding online connection should
govern all devices including personal devices such as smartphones. Some of the employees
makes connection with their devices which later are connected to organizational computers for
data transfer. Secondly, since Motherboards and More Pty Ltd make use of website for clients to
order their goods, firewalls should be implemented with strong security features to screen all
incoming signals which could harm organizational system (Beissel, 2016). In this case, since not
all departments operate online, there should be separate terminals for department that operate
online with those do not. Department that is concerned with order reception through email and
website should be separated from others for security purposes. Separation of operational
procedures makes sure not all departments are affected in case there is an attacker.
Similarly, organization should implement data encryption to prevent data copying to untrusted
parties. Since it is not clear if Ransomware reads data, it is essential to encrypt the entire
organizational data such that if an attacker is reported, no data loss would be experienced. When

data is encrypted, data is deciphered to make it of no use to a third party who may access it.
Lastly, creating awareness to all organizational employees is very important because it makes
sure they are alert. According to Cyber Security and Privacy EU Forum, Cleary & Felici (2015),
awareness helps organizations to safe resources from increased sabotage in case an attacker
occurs. When employees are aware about Ransomware virus and such an incident occurs, it
would be possible for organizational employees to take recommended measures when there are
suspicious activities in the system. This helps organization safe a lot of resources which could be
used in recovering the system. In this case, if only one computer is infected and an employee
notices the incident immediately, it would be possible to disconnect infected computer from
organizational communication channels in order to prevent virus from spreading (Alsmadi,
Karabatis & Aleroud, 2016). In turn, this safes organizational resources which could have been
used to make payment required to unlock Ransomware attacked devices.
Conclusion
The revenue cycle gives a clear simulation of how Motherboards and More Pty Ltd
operates and what is required to make business a success. Identified weakness such as delay in
delivery makes it difficult for business to make maximum profits since some of clients may
withdrawal their orders due to delay. Similarly, there should be ordering commitment fee which
guarantees supplier seriousness of placed order. This eliminates client who may place an order
and end up turning it down once it has been delivered. In case of data security, Motherboards and
More Pty Ltd should come up with security controls such as; data encryption, online connection
policies for all employees in the organization and creating awareness to all employees and
necessary security measures to take in case of attacker. Some of measures should be easy and
simple to be performed by employees without assistance of Technical department.
Lastly, creating awareness to all organizational employees is very important because it makes
sure they are alert. According to Cyber Security and Privacy EU Forum, Cleary & Felici (2015),
awareness helps organizations to safe resources from increased sabotage in case an attacker
occurs. When employees are aware about Ransomware virus and such an incident occurs, it
would be possible for organizational employees to take recommended measures when there are
suspicious activities in the system. This helps organization safe a lot of resources which could be
used in recovering the system. In this case, if only one computer is infected and an employee
notices the incident immediately, it would be possible to disconnect infected computer from
organizational communication channels in order to prevent virus from spreading (Alsmadi,
Karabatis & Aleroud, 2016). In turn, this safes organizational resources which could have been
used to make payment required to unlock Ransomware attacked devices.
Conclusion
The revenue cycle gives a clear simulation of how Motherboards and More Pty Ltd
operates and what is required to make business a success. Identified weakness such as delay in
delivery makes it difficult for business to make maximum profits since some of clients may
withdrawal their orders due to delay. Similarly, there should be ordering commitment fee which
guarantees supplier seriousness of placed order. This eliminates client who may place an order
and end up turning it down once it has been delivered. In case of data security, Motherboards and
More Pty Ltd should come up with security controls such as; data encryption, online connection
policies for all employees in the organization and creating awareness to all employees and
necessary security measures to take in case of attacker. Some of measures should be easy and
simple to be performed by employees without assistance of Technical department.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Alsmadi, I., Karabatis, G., & Aleroud, A. (2016). Information fusion for cyber-security
analytics.
Beissel, S. (2016). Cybersecurity investments: Decision support under economic aspects.
Cert-MU. (2017). The massive Wannacry global Ransomware attack
Cyber Security and Privacy EU Forum, In Cleary, F., & In Felici, M. (2015). Cyber security and
privacy: 4th Cyber Security and Privacy Innovation Forum, CSP Innovation Forum 2015,
Brussels, Belgium April 28-29, 2015, revised selected papers.
Kaplan, J. M., Bailey, T., Rezek, C., O'Halloran, D., & Marcus, A. (2015). Beyond
cybersecurity: Protecting your digital business.
Security Advisory. (2017). WannaCry Ransomware Campaign Exploiting SMB Vulnerability.
Alsmadi, I., Karabatis, G., & Aleroud, A. (2016). Information fusion for cyber-security
analytics.
Beissel, S. (2016). Cybersecurity investments: Decision support under economic aspects.
Cert-MU. (2017). The massive Wannacry global Ransomware attack
Cyber Security and Privacy EU Forum, In Cleary, F., & In Felici, M. (2015). Cyber security and
privacy: 4th Cyber Security and Privacy Innovation Forum, CSP Innovation Forum 2015,
Brussels, Belgium April 28-29, 2015, revised selected papers.
Kaplan, J. M., Bailey, T., Rezek, C., O'Halloran, D., & Marcus, A. (2015). Beyond
cybersecurity: Protecting your digital business.
Security Advisory. (2017). WannaCry Ransomware Campaign Exploiting SMB Vulnerability.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





