CMP73001: Cyber Security Report: Risk Assessment and Management
VerifiedAdded on 2023/01/17
|19
|3526
|79
Report
AI Summary
This cybersecurity report, prepared for MyHealth Company, addresses the need for improved security management in the healthcare sector. The report begins by identifying and assessing various information assets, including email servers, web servers, databases, network devices, and IT personnel, along with their locations and ownership. It then delves into information security governance, highlighting its benefits for strategic alignment, risk management, and resource optimization. Detailed password, acceptable use, access control, database security, firewall configuration, antivirus update, information security, incident response, and disaster recovery policies are outlined to enhance security posture. The report further examines vulnerability and risk management, providing a risk assessment plan based on the ISO framework and analyzing vulnerabilities in each asset. It also includes a threat analysis for each asset, proposing measures to mitigate potential risks and improve the overall security of MyHealth Company's operations.
Running Head: Cyber Security 0
Cyber Security
Report
Student name
Cyber Security
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 1
Task 1: Identify and manage asset
Health care sector is having many information assets to manage their operations in
present era. From last two decades, health care sector is highly used information systems and
medical software and hardware to enhance their performance and quality (ACSC, Australian
Cyber Security Centre 2017).
There are many assets in the health care sector, but few are so important from patients
and hospital point of view. These are information assets of MyHealth Company, servers,
networking devices, hardware and software, and many others (ACSC, Strategies to Mitigate
Cyber Security Incidents 2019).
An information system is an information asset of MyHealth Company and it provides
competitive advantage to the MyHealth Company. Computer systems and database are provides
many information of patients for their treatment. It is a way to manage reputation in the market.
it makes a good image in the mind of patients. All the assets have installed on the same floor and
all IT staff member are working on that floor. Server room is having all devices, such as switch,
server, router, and many others. All the staff members can access this area. It is not restricted
(Andrijcic and Horowitz 2016).
Number Asset
ID
Asset Asset Location Ownership Asset Description
1 S.01 Email
server
On a sever in the
server room
MyHealth
Company
Email Server: In health care sector,
communication requires between the
different departments and people to
share information about different
operations in their respective
departments. For non-verbal
communication, electronic mail is a
best way to communicate. Email
server manages all the internal
nonverbal communication between
Task 1: Identify and manage asset
Health care sector is having many information assets to manage their operations in
present era. From last two decades, health care sector is highly used information systems and
medical software and hardware to enhance their performance and quality (ACSC, Australian
Cyber Security Centre 2017).
There are many assets in the health care sector, but few are so important from patients
and hospital point of view. These are information assets of MyHealth Company, servers,
networking devices, hardware and software, and many others (ACSC, Strategies to Mitigate
Cyber Security Incidents 2019).
An information system is an information asset of MyHealth Company and it provides
competitive advantage to the MyHealth Company. Computer systems and database are provides
many information of patients for their treatment. It is a way to manage reputation in the market.
it makes a good image in the mind of patients. All the assets have installed on the same floor and
all IT staff member are working on that floor. Server room is having all devices, such as switch,
server, router, and many others. All the staff members can access this area. It is not restricted
(Andrijcic and Horowitz 2016).
Number Asset
ID
Asset Asset Location Ownership Asset Description
1 S.01 Email
server
On a sever in the
server room
MyHealth
Company
Email Server: In health care sector,
communication requires between the
different departments and people to
share information about different
operations in their respective
departments. For non-verbal
communication, electronic mail is a
best way to communicate. Email
server manages all the internal
nonverbal communication between
Cyber Security 2
different people. MyHealth
Company is having different
departments, such as education,
clinic practice and cancer research
department. They have different
people to manage their necessary
work in respective departments.
Email server is responsible for
communication between different
people of MyHealth Company
(Arlitsch and Edelman 2014). It
provides separate username and
password to each user for non-
verbal communication in the
MyHealth Company. In addition,
emails are having confidential
information of products and
services. Therefore, it requires a
high security from different types of
cyber-attacks.
2 S.02 Web
server
On a sever in the
server room
MyHealth
Company
Web Server: Web server is an
important information asset of
MyHealth Company. it provides
web services and payment gateways
to different people of MyHealth
Company as well as patients. It is a
way to access the information
system of MyHealth Company and
made respective payment for
acquired products and services.
different people. MyHealth
Company is having different
departments, such as education,
clinic practice and cancer research
department. They have different
people to manage their necessary
work in respective departments.
Email server is responsible for
communication between different
people of MyHealth Company
(Arlitsch and Edelman 2014). It
provides separate username and
password to each user for non-
verbal communication in the
MyHealth Company. In addition,
emails are having confidential
information of products and
services. Therefore, it requires a
high security from different types of
cyber-attacks.
2 S.02 Web
server
On a sever in the
server room
MyHealth
Company
Web Server: Web server is an
important information asset of
MyHealth Company. it provides
web services and payment gateways
to different people of MyHealth
Company as well as patients. It is a
way to access the information
system of MyHealth Company and
made respective payment for
acquired products and services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cyber Security 3
MyHealth Company uses web
server to provide online interface to
all the staff members and patients. It
is included in the MyHealth
Company to manage all online
works of their different services,
such as clinical practice, education
and cancer-related services (BWISE
2018).
3 S.03 Database
server
On a sever in the
server room
MyHealth
Company
Database server: it is used to store
lots of data of patients and research
data, which can be used in future for
patient’s treatments. Research has
huge data for literature survey and
analysis. Therefore, researchers are
required previous data to innovate
new things in the field of medical
science. MyHealth Company is
having cancer-related research and
development centre. In addition,
medical services are based on the
history of patients for treatment of
many diseases. Therefore, it is
necessary to include in MyHealth
Company. it require a high security
from cyber-attacks (Barkly 2018).
4 NW.01 Access
layer
switches
In Network rack
on same floor
MyHealth
Company
Access Layer Switches: switches are
used to forward packets to desired
destination in a network. MyHealth
Company is having two 24-port
CISCO switches to connect different
MyHealth Company uses web
server to provide online interface to
all the staff members and patients. It
is included in the MyHealth
Company to manage all online
works of their different services,
such as clinical practice, education
and cancer-related services (BWISE
2018).
3 S.03 Database
server
On a sever in the
server room
MyHealth
Company
Database server: it is used to store
lots of data of patients and research
data, which can be used in future for
patient’s treatments. Research has
huge data for literature survey and
analysis. Therefore, researchers are
required previous data to innovate
new things in the field of medical
science. MyHealth Company is
having cancer-related research and
development centre. In addition,
medical services are based on the
history of patients for treatment of
many diseases. Therefore, it is
necessary to include in MyHealth
Company. it require a high security
from cyber-attacks (Barkly 2018).
4 NW.01 Access
layer
switches
In Network rack
on same floor
MyHealth
Company
Access Layer Switches: switches are
used to forward packets to desired
destination in a network. MyHealth
Company is having two 24-port
CISCO switches to connect different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 4
computer system for data transfer
and processing. Access layer switch
are lowest quality switches in a
network. It includes in the
MyHealth Company to connect
different departments systems, such
as sales, payroll, payment, and many
others ( Bradford 2018).
5 HW.01 Computer
systems
In MyHealth
Company
MyHealth
Company
Personal computer systems:
MyHealth Company is having 40
PCs, which have outdates antivirus.
Personal computers are having lots
of information about the patients
and their treatments. Therefore, it is
necessary to secure them. PCs are
included in the health care to store
information of patients ( Cobb
2010).
6 SW.01 Firewalls On 40 personal
computer systems
MyHealth
Company
Firewalls: MyHealth Company is
having default windows firewall of
all computer system. Firewall is
used to filter suspicious packet from
network. it secures systems from
different types of attacks from
malwares in a network (Dutton
2017).
7 NW.02 Routers Server room MyHealth
Company
Routers: Asymmetric Digital
Subscriber Line (ADSL) router is
used for routing. It provides a route
to a packet. It uses different routing
algorithms for routing, such as link-
computer system for data transfer
and processing. Access layer switch
are lowest quality switches in a
network. It includes in the
MyHealth Company to connect
different departments systems, such
as sales, payroll, payment, and many
others ( Bradford 2018).
5 HW.01 Computer
systems
In MyHealth
Company
MyHealth
Company
Personal computer systems:
MyHealth Company is having 40
PCs, which have outdates antivirus.
Personal computers are having lots
of information about the patients
and their treatments. Therefore, it is
necessary to secure them. PCs are
included in the health care to store
information of patients ( Cobb
2010).
6 SW.01 Firewalls On 40 personal
computer systems
MyHealth
Company
Firewalls: MyHealth Company is
having default windows firewall of
all computer system. Firewall is
used to filter suspicious packet from
network. it secures systems from
different types of attacks from
malwares in a network (Dutton
2017).
7 NW.02 Routers Server room MyHealth
Company
Routers: Asymmetric Digital
Subscriber Line (ADSL) router is
used for routing. It provides a route
to a packet. It uses different routing
algorithms for routing, such as link-
Cyber Security 5
state algorithms, and many others. It
include in MyHealth Company to
connect all the devices from
internet. MyHealth Company is not
having configuration on routers and
switches (Fruhlinger 2018).
8 NW.03 Wireless
access
points
Server Room MyHealth
Company
Wireless access points: wireless
access points are used to distribute
network in different devices, such as
personal computer systems, mobile
phones, laptops. MyHealth
Company is having two wireless
access points to share network in
different devices. It is include for
distribution of network without
physical media in an open area, such
as reception, seminar hall, and many
others (Gordon and Loeb 2006).
9 SM.01 IT people Three IT staff in
same floor of
MyHealth
Company
MyHealth
Company
IT people: MyHealth Company is
having IT staff to manage different
works, which is related to the
network and computer system, such
as internet connection, video
conference facilities, network
devices, server, computers, LAN,
Wi-Fi, software, Voice over IP
service, and hardware. All staff
members are working on a same
floor because all the devices and
systems are installed in a same floor
(www.stanfieldit.com 2019).
state algorithms, and many others. It
include in MyHealth Company to
connect all the devices from
internet. MyHealth Company is not
having configuration on routers and
switches (Fruhlinger 2018).
8 NW.03 Wireless
access
points
Server Room MyHealth
Company
Wireless access points: wireless
access points are used to distribute
network in different devices, such as
personal computer systems, mobile
phones, laptops. MyHealth
Company is having two wireless
access points to share network in
different devices. It is include for
distribution of network without
physical media in an open area, such
as reception, seminar hall, and many
others (Gordon and Loeb 2006).
9 SM.01 IT people Three IT staff in
same floor of
MyHealth
Company
MyHealth
Company
IT people: MyHealth Company is
having IT staff to manage different
works, which is related to the
network and computer system, such
as internet connection, video
conference facilities, network
devices, server, computers, LAN,
Wi-Fi, software, Voice over IP
service, and hardware. All staff
members are working on a same
floor because all the devices and
systems are installed in a same floor
(www.stanfieldit.com 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cyber Security 6
10 CS.01 Wireless
security
On wireless
access point in
server room
MyHealth
Company
Wireless security: MyHealth
Company is used wireless access
point to share network in different
devices. Therefore, it is securing the
network from outsiders. Anyone can
use the wireless network and theft
data and information from personal
computers. It includes in the
MyHealth Company to provide
network in open areas
(iso27001security.com 2019).
11 S.03 DHCP
and DNS
server
On a sever in the
server room
MyHealth
Company
DHCP and DNS server: Dynamic
Host Configuration Protocol
(DHCP) is used to provide IP
addresses to the personal computers.
It provides dynamic IP addresses to
the live devices in a network. It
includes for dynamic conflagration
of IP addresses in the MyHealth
Company’s network (export.gov
2019).
12 SW.02 Operating
System
40 personal
computer systems
to different staff
members as per
their requirement
MyHealth
Company
Operation system should have
proper updates with antivirus
updates.
d.
Number Asset Class
10 CS.01 Wireless
security
On wireless
access point in
server room
MyHealth
Company
Wireless security: MyHealth
Company is used wireless access
point to share network in different
devices. Therefore, it is securing the
network from outsiders. Anyone can
use the wireless network and theft
data and information from personal
computers. It includes in the
MyHealth Company to provide
network in open areas
(iso27001security.com 2019).
11 S.03 DHCP
and DNS
server
On a sever in the
server room
MyHealth
Company
DHCP and DNS server: Dynamic
Host Configuration Protocol
(DHCP) is used to provide IP
addresses to the personal computers.
It provides dynamic IP addresses to
the live devices in a network. It
includes for dynamic conflagration
of IP addresses in the MyHealth
Company’s network (export.gov
2019).
12 SW.02 Operating
System
40 personal
computer systems
to different staff
members as per
their requirement
MyHealth
Company
Operation system should have
proper updates with antivirus
updates.
d.
Number Asset Class
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 7
1. Email server Restricted
2. Web server Restricted
3. Database server Restricted
4. Access layer switches Internal
5. Computer systems Internal
6. Firewalls Internal
7. Routers Restricted
8. Wireless access points Internal
9. IT people Public
10. Wireless security Internal
11. DHCP and DNS server Restricted
12. Operating System Internal
2-
Information security governance can manage different assets of MyHealth Company. It will
provide many benefits to the company to secure their resources and asset management.
Information Security Governance (ISG) identifies different critical risks of the MyHealth
Company and provide them a rank based on their risk level (Von Solms and Van Niekerk 2013).
It is having few objective to secure the assets of company, which are as:
1. Objectives are achieved
2. Risks is mitigates
3. MyHealth Company’s resources are used responsibly, and
4. Monitor security program of MyHealth Company
It will provide many benefits, such as strategic alignment, risk management, resource
management, performance management, and value delivery.
1. Email server Restricted
2. Web server Restricted
3. Database server Restricted
4. Access layer switches Internal
5. Computer systems Internal
6. Firewalls Internal
7. Routers Restricted
8. Wireless access points Internal
9. IT people Public
10. Wireless security Internal
11. DHCP and DNS server Restricted
12. Operating System Internal
2-
Information security governance can manage different assets of MyHealth Company. It will
provide many benefits to the company to secure their resources and asset management.
Information Security Governance (ISG) identifies different critical risks of the MyHealth
Company and provide them a rank based on their risk level (Von Solms and Van Niekerk 2013).
It is having few objective to secure the assets of company, which are as:
1. Objectives are achieved
2. Risks is mitigates
3. MyHealth Company’s resources are used responsibly, and
4. Monitor security program of MyHealth Company
It will provide many benefits, such as strategic alignment, risk management, resource
management, performance management, and value delivery.

Cyber Security 8
3-
Password Policy:
Password should have at least eight characters
It contains different combination, such as lowercase, uppercase, number, and special
characters (NCSC 2019).
Password should change in every week because of security reasons
Do not use personal information in password
Acceptable Use Policy:
Respective person is responsible for their credential, such as password, network ID, and
many others
All assets are under the responsibility of respective person
Access control policy:
No one can have access in restricted areas except authenticated persons
Server room should have locks
Wireless devices should have physical security
Database security:
Database should have limited access
Only authorized person can access the database server
Payment methods can be secure using biometric devices
Firewall configuration policy:
Network administrator should secure firewall configuration
Configuration should have all the risk controls
Antivirus update policy:
Administrator or IT people should responsible for updates of antivirus in all the systems
All staff members are responsible for their allocated system
Information Security Policy:
All the staff members are responsible for their personal computer and their credentials
IT people are responsible for their roles and duties
Incident Response Policy:
3-
Password Policy:
Password should have at least eight characters
It contains different combination, such as lowercase, uppercase, number, and special
characters (NCSC 2019).
Password should change in every week because of security reasons
Do not use personal information in password
Acceptable Use Policy:
Respective person is responsible for their credential, such as password, network ID, and
many others
All assets are under the responsibility of respective person
Access control policy:
No one can have access in restricted areas except authenticated persons
Server room should have locks
Wireless devices should have physical security
Database security:
Database should have limited access
Only authorized person can access the database server
Payment methods can be secure using biometric devices
Firewall configuration policy:
Network administrator should secure firewall configuration
Configuration should have all the risk controls
Antivirus update policy:
Administrator or IT people should responsible for updates of antivirus in all the systems
All staff members are responsible for their allocated system
Information Security Policy:
All the staff members are responsible for their personal computer and their credentials
IT people are responsible for their roles and duties
Incident Response Policy:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 9
Everyone is responsible for response for any incident with their allocated assets
It requires intent response on the incident to responsible person, such as CISOs.
Disaster recovery policy:
CISO and team will manage incident based on the incident response policy
Business continuity plan will be activated
Cyber security check will start after disaster to prevent system
Business Continuity Policy:
CISO and team will start the backup process to continue business processes
Security check will be start by the administrator
Network testing will start by network administrator
Task 2: Vulnerability management and risk management
1-
There are some basic steps to secure enterprise from different risks by ISO framework (Hayslip
2018). ISO framework provides risk management plan to prevent risk and mitigates them when
they occur in the system (Kosutic 2016). These are the steps to secure enterprise:
1. Identify the Objectives of your Business
2. Obtain Management Support
3. Define the Scope
4. Write a brief ISMS Policy
5. Define Risk Assessment Methodology & Strategy
6. Create a Risk Treatment Plan & Manage those Risks
7. Set Up Policies and Procedures to Control Risks
8. Allocate Required Resources and Implement Training plus Awareness Programs
9. Carefully Monitor the ISMS
10. Prepare for an Internal Audit
11. Periodic Management Review
Everyone is responsible for response for any incident with their allocated assets
It requires intent response on the incident to responsible person, such as CISOs.
Disaster recovery policy:
CISO and team will manage incident based on the incident response policy
Business continuity plan will be activated
Cyber security check will start after disaster to prevent system
Business Continuity Policy:
CISO and team will start the backup process to continue business processes
Security check will be start by the administrator
Network testing will start by network administrator
Task 2: Vulnerability management and risk management
1-
There are some basic steps to secure enterprise from different risks by ISO framework (Hayslip
2018). ISO framework provides risk management plan to prevent risk and mitigates them when
they occur in the system (Kosutic 2016). These are the steps to secure enterprise:
1. Identify the Objectives of your Business
2. Obtain Management Support
3. Define the Scope
4. Write a brief ISMS Policy
5. Define Risk Assessment Methodology & Strategy
6. Create a Risk Treatment Plan & Manage those Risks
7. Set Up Policies and Procedures to Control Risks
8. Allocate Required Resources and Implement Training plus Awareness Programs
9. Carefully Monitor the ISMS
10. Prepare for an Internal Audit
11. Periodic Management Review
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 10
All these steps are used to implement security plan in the organisation (Verma 2019). MyHealth
Company can choose ISO/IEC 27001 framework for enterprise risk management ( Licato 2014).
2-
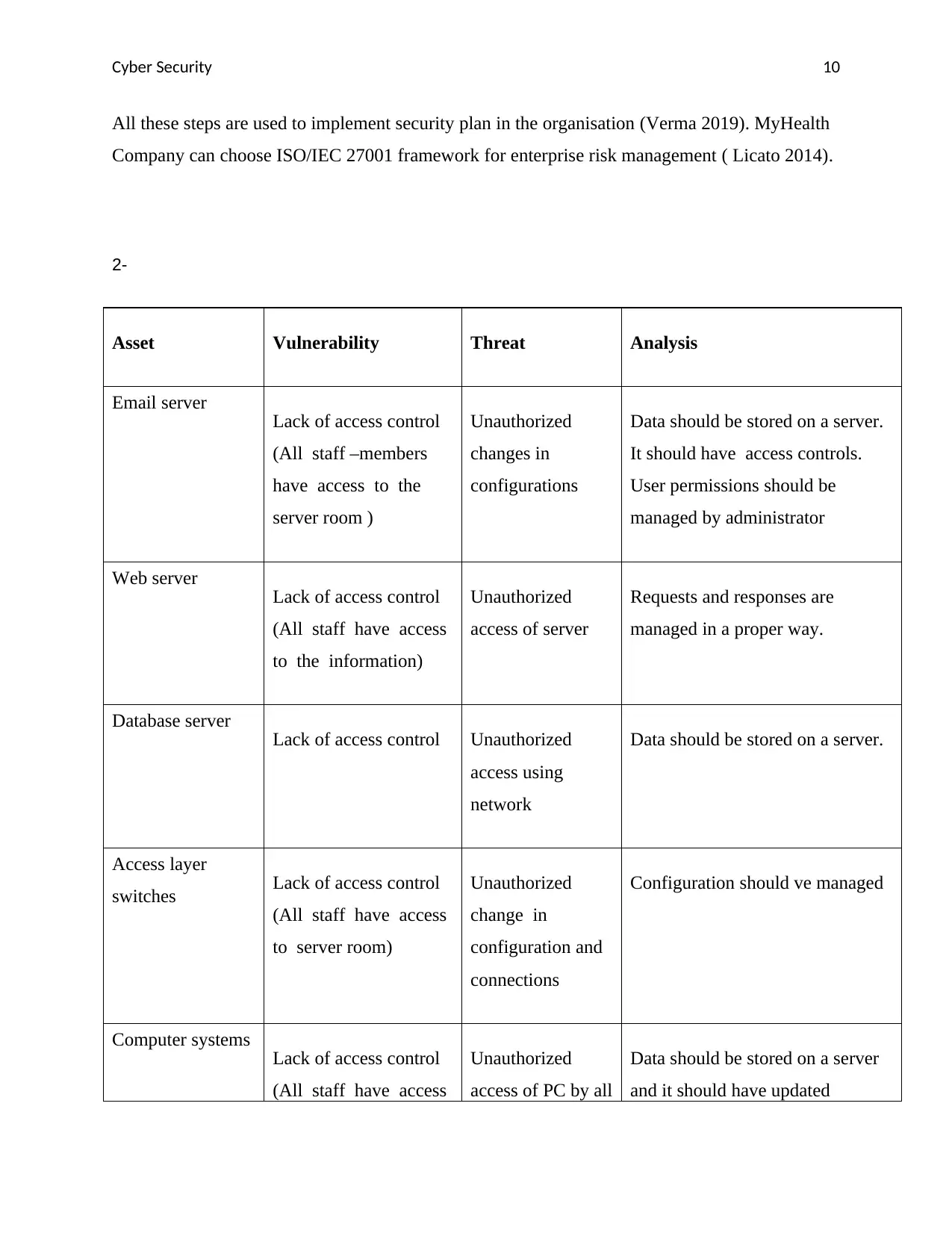
Asset Vulnerability Threat Analysis
Email server
Lack of access control
(All staff –members
have access to the
server room )
Unauthorized
changes in
configurations
Data should be stored on a server.
It should have access controls.
User permissions should be
managed by administrator
Web server
Lack of access control
(All staff have access
to the information)
Unauthorized
access of server
Requests and responses are
managed in a proper way.
Database server
Lack of access control Unauthorized
access using
network
Data should be stored on a server.
Access layer
switches Lack of access control
(All staff have access
to server room)
Unauthorized
change in
configuration and
connections
Configuration should ve managed
Computer systems
Lack of access control
(All staff have access
Unauthorized
access of PC by all
Data should be stored on a server
and it should have updated
All these steps are used to implement security plan in the organisation (Verma 2019). MyHealth
Company can choose ISO/IEC 27001 framework for enterprise risk management ( Licato 2014).
2-
Asset Vulnerability Threat Analysis
Email server
Lack of access control
(All staff –members
have access to the
server room )
Unauthorized
changes in
configurations
Data should be stored on a server.
It should have access controls.
User permissions should be
managed by administrator
Web server
Lack of access control
(All staff have access
to the information)
Unauthorized
access of server
Requests and responses are
managed in a proper way.
Database server
Lack of access control Unauthorized
access using
network
Data should be stored on a server.
Access layer
switches Lack of access control
(All staff have access
to server room)
Unauthorized
change in
configuration and
connections
Configuration should ve managed
Computer systems
Lack of access control
(All staff have access
Unauthorized
access of PC by all
Data should be stored on a server
and it should have updated
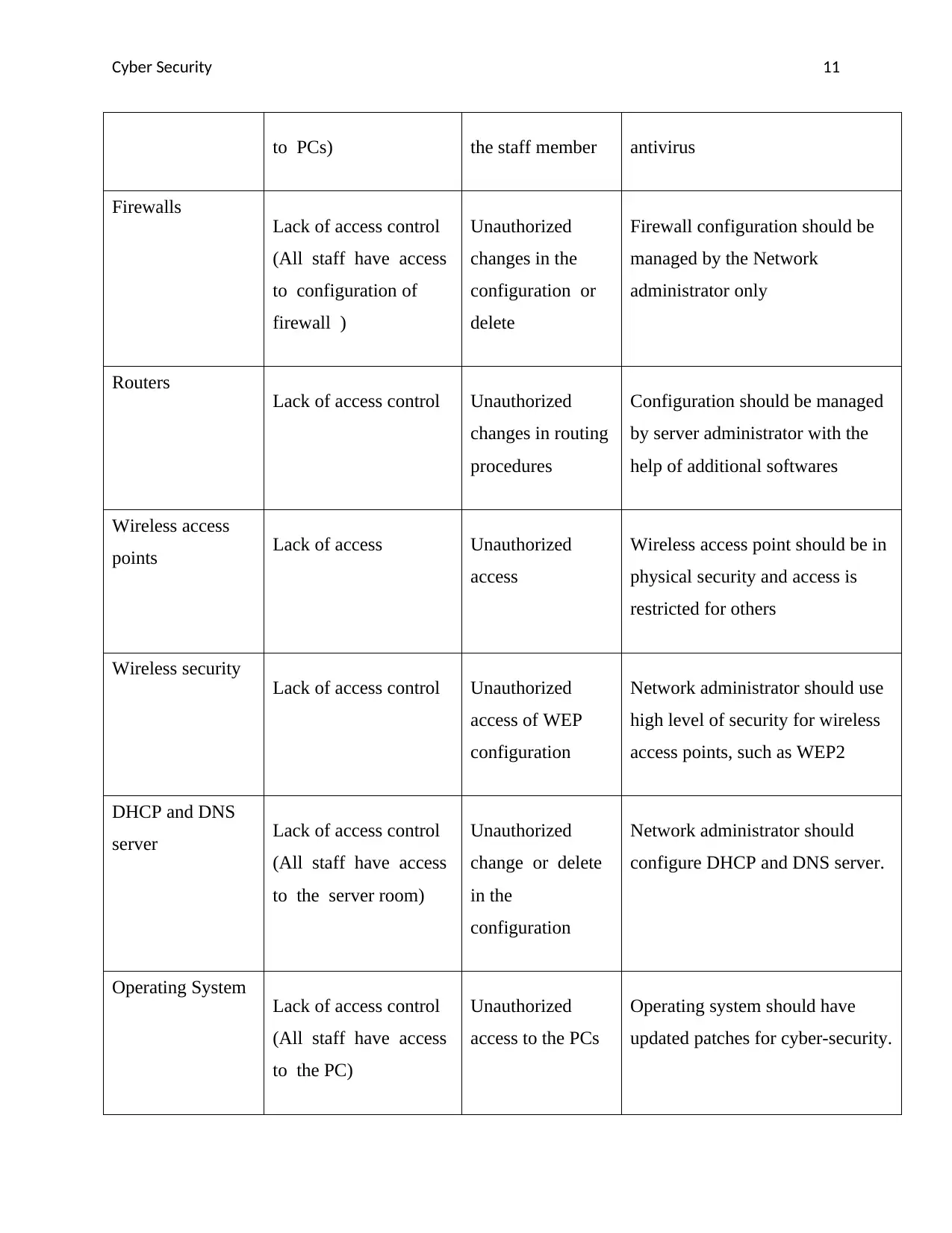
Cyber Security 11
to PCs) the staff member antivirus
Firewalls
Lack of access control
(All staff have access
to configuration of
firewall )
Unauthorized
changes in the
configuration or
delete
Firewall configuration should be
managed by the Network
administrator only
Routers
Lack of access control Unauthorized
changes in routing
procedures
Configuration should be managed
by server administrator with the
help of additional softwares
Wireless access
points Lack of access Unauthorized
access
Wireless access point should be in
physical security and access is
restricted for others
Wireless security
Lack of access control Unauthorized
access of WEP
configuration
Network administrator should use
high level of security for wireless
access points, such as WEP2
DHCP and DNS
server Lack of access control
(All staff have access
to the server room)
Unauthorized
change or delete
in the
configuration
Network administrator should
configure DHCP and DNS server.
Operating System
Lack of access control
(All staff have access
to the PC)
Unauthorized
access to the PCs
Operating system should have
updated patches for cyber-security.
to PCs) the staff member antivirus
Firewalls
Lack of access control
(All staff have access
to configuration of
firewall )
Unauthorized
changes in the
configuration or
delete
Firewall configuration should be
managed by the Network
administrator only
Routers
Lack of access control Unauthorized
changes in routing
procedures
Configuration should be managed
by server administrator with the
help of additional softwares
Wireless access
points Lack of access Unauthorized
access
Wireless access point should be in
physical security and access is
restricted for others
Wireless security
Lack of access control Unauthorized
access of WEP
configuration
Network administrator should use
high level of security for wireless
access points, such as WEP2
DHCP and DNS
server Lack of access control
(All staff have access
to the server room)
Unauthorized
change or delete
in the
configuration
Network administrator should
configure DHCP and DNS server.
Operating System
Lack of access control
(All staff have access
to the PC)
Unauthorized
access to the PCs
Operating system should have
updated patches for cyber-security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




