CMP73001 Cybersecurity Risk Assessment Report for MyHealth Company
VerifiedAdded on 2023/01/11
|22
|3679
|84
Report
AI Summary
This report presents a cybersecurity risk assessment for MyHealth, a healthcare company involved in clinical practice, education, and cancer-related research. The assessment begins with identifying and classifying MyHealth's information assets, including email servers, web servers, database servers, DHCP and DNS servers, ADSL routers, workstations, operating systems, firewalls, wireless access points, and Telnet connections. The report then discusses information security governance and suggests cybersecurity policies for MyHealth. It proceeds to explain enterprise risk management and vulnerability management, identifying vulnerabilities within each asset. The report culminates in the creation of a risk assessment table, outlining assets, threats, vulnerabilities, and risks, and concludes with observations from the assessment. The report aims to help MyHealth secure its practices by evaluating the security risk assessment of their company.

Running head: RISK ASSESSMENT FOR MYHEALTH
Risk Assessment for MyHealth
Name of the Student
Name of the University
Author Note
Risk Assessment for MyHealth
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK ASSESSMENT FOR MYHEALTH
Summary
The objective of the report is to conduct a security risk assessment for the company
MyHealth. The study discusses about each of the assets, explaining their role in the network
and then lists them in a tabular format. Thereafter the Information Security governance for
the company is talked about which suggests why and how it can be beneficial for MyHealth.
Next the cybersecurity policies are explained suggestions provided for MyHealth. The report
then proceeds to talk about Enterprise risk management and explains the steps after which the
vulnerability assessment table is given. After explaining assets, threats, vulnerabilities and
risks, the risk assessment table is created. The report then ends with concluding notes by
providing observations from the assessment.
Summary
The objective of the report is to conduct a security risk assessment for the company
MyHealth. The study discusses about each of the assets, explaining their role in the network
and then lists them in a tabular format. Thereafter the Information Security governance for
the company is talked about which suggests why and how it can be beneficial for MyHealth.
Next the cybersecurity policies are explained suggestions provided for MyHealth. The report
then proceeds to talk about Enterprise risk management and explains the steps after which the
vulnerability assessment table is given. After explaining assets, threats, vulnerabilities and
risks, the risk assessment table is created. The report then ends with concluding notes by
providing observations from the assessment.

2RISK ASSESSMENT FOR MYHEALTH
Table of Contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Task 1 Asset Identification.....................................................................................................3
The different information assets of MyHealth are:............................................................3
Information Security Governance and MyHealth............................................................10
Cybersecurity policies for MyHealth...............................................................................11
Task 2 Vulnerability Management and risk management....................................................12
Enterprise Risk Management...........................................................................................12
Vulnerabilities in assets of MyHealth..............................................................................13
Asset.................................................................................................................................17
Threat...............................................................................................................................17
Vulnerability....................................................................................................................17
Risk..................................................................................................................................17
Conclusion................................................................................................................................19
Bibliography.............................................................................................................................20
Table of Contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Task 1 Asset Identification.....................................................................................................3
The different information assets of MyHealth are:............................................................3
Information Security Governance and MyHealth............................................................10
Cybersecurity policies for MyHealth...............................................................................11
Task 2 Vulnerability Management and risk management....................................................12
Enterprise Risk Management...........................................................................................12
Vulnerabilities in assets of MyHealth..............................................................................13
Asset.................................................................................................................................17
Threat...............................................................................................................................17
Vulnerability....................................................................................................................17
Risk..................................................................................................................................17
Conclusion................................................................................................................................19
Bibliography.............................................................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISK ASSESSMENT FOR MYHEALTH
Introduction
The report concerns with carrying out the security risk assessment for the company
MyHealth which involves clinical practise in the field of cancer related research. It is clear
that the company deals with sensitive data and hence they are looking to secure their practises
by evaluating a security risk assessment of their company. As part of the risk assessment the
report is responsible for identifying and briefing on the assets of the network and classifying
them in a table (Kott and Arnold 2015). After that the report discusses on how and why
information security governance can be beneficial for the company and following which
cybersecurity policies are explained and suggestions are given for MyHealth. Then the report
enters vulnerability and risk management section by explaining enterprise risk management
and the steps. Next the vulnerabilities for each of the assets are identified and presented in the
vulnerability assessment table and thereafter assets, threats, vulnerabilities and risk are
explained. After that the risk assessment table is created and concluding notes are given.
Discussion
Task 1 Asset Identification
The different information assets of MyHealth are:
Email Server: Email servers also called mail servers, are applications or computers
placed in a network the purpose of which is acting as virtual post offices. The servers store
incoming mails as also distribute them to the local users and are responsible for sending
outgoing messages. They use client-server applications for sending and receiving messages
via the Simple Mail Transfer Protocol (SMTP) protocol. Email servers can also be called
mail and message transfer agents.
Web server: Web servers are programs make use of Hypertext Transfer Protocol (HTTP)
so they can serve files that form the web page, as response against user requests. These web
Introduction
The report concerns with carrying out the security risk assessment for the company
MyHealth which involves clinical practise in the field of cancer related research. It is clear
that the company deals with sensitive data and hence they are looking to secure their practises
by evaluating a security risk assessment of their company. As part of the risk assessment the
report is responsible for identifying and briefing on the assets of the network and classifying
them in a table (Kott and Arnold 2015). After that the report discusses on how and why
information security governance can be beneficial for the company and following which
cybersecurity policies are explained and suggestions are given for MyHealth. Then the report
enters vulnerability and risk management section by explaining enterprise risk management
and the steps. Next the vulnerabilities for each of the assets are identified and presented in the
vulnerability assessment table and thereafter assets, threats, vulnerabilities and risk are
explained. After that the risk assessment table is created and concluding notes are given.
Discussion
Task 1 Asset Identification
The different information assets of MyHealth are:
Email Server: Email servers also called mail servers, are applications or computers
placed in a network the purpose of which is acting as virtual post offices. The servers store
incoming mails as also distribute them to the local users and are responsible for sending
outgoing messages. They use client-server applications for sending and receiving messages
via the Simple Mail Transfer Protocol (SMTP) protocol. Email servers can also be called
mail and message transfer agents.
Web server: Web servers are programs make use of Hypertext Transfer Protocol (HTTP)
so they can serve files that form the web page, as response against user requests. These web
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RISK ASSESSMENT FOR MYHEALTH
pages get forwarded through the HTTP clients of the computers. Computers and applications
dedicated for such tasks are also called web servers.
Database Server: Database server refers to hardware as well as software solutions used
for running databases as per requirements. The software side database servers act as back
ends of databases following client-server model. These back end portions are at times called
instances. These can also be physical computers used for hosting databases. These are
generally high-end computers that are dedicated for database purposes only.
DHCP and DNS server: Although both DNS and DHCP work using the client-server
architecture they are completely different. DNS is used for mapping domain names to IP
addresses while the DHCP protocol assigns IPs to hosts present in the network through static
or dynamic methods. Even for configuring the DNS server with hosts the DHCP used.
ADSL router: Configuring WiFi ADSL Routers can be done in a matter of minutes so
that the Internet connection can be shared. Sharing of hard drives, files and printers can be
performed from any place within the WiFi range or through wired Ethernet connections via
any of the Ethernet ports found at the back of WiFi ADSL routers. Because of having built-in
ADSL modem, the ADSL routers can plug directly with the telephone line through micro-
filters.
Workstations: Workstations are computers dedicated to users or a user group of
businesses for performing professional tasks. These systems include displays with high
display resolutions and much faster processors than regular personal computers (PC).
Workstations also have higher multitasking capabilities owing to the additional amount of
random-access memory (RAM), hard drives and hard drive capacities. Workstations can also
possess graphics adapters relatively faster than regular PCs as also have more peripheral
connections.
pages get forwarded through the HTTP clients of the computers. Computers and applications
dedicated for such tasks are also called web servers.
Database Server: Database server refers to hardware as well as software solutions used
for running databases as per requirements. The software side database servers act as back
ends of databases following client-server model. These back end portions are at times called
instances. These can also be physical computers used for hosting databases. These are
generally high-end computers that are dedicated for database purposes only.
DHCP and DNS server: Although both DNS and DHCP work using the client-server
architecture they are completely different. DNS is used for mapping domain names to IP
addresses while the DHCP protocol assigns IPs to hosts present in the network through static
or dynamic methods. Even for configuring the DNS server with hosts the DHCP used.
ADSL router: Configuring WiFi ADSL Routers can be done in a matter of minutes so
that the Internet connection can be shared. Sharing of hard drives, files and printers can be
performed from any place within the WiFi range or through wired Ethernet connections via
any of the Ethernet ports found at the back of WiFi ADSL routers. Because of having built-in
ADSL modem, the ADSL routers can plug directly with the telephone line through micro-
filters.
Workstations: Workstations are computers dedicated to users or a user group of
businesses for performing professional tasks. These systems include displays with high
display resolutions and much faster processors than regular personal computers (PC).
Workstations also have higher multitasking capabilities owing to the additional amount of
random-access memory (RAM), hard drives and hard drive capacities. Workstations can also
possess graphics adapters relatively faster than regular PCs as also have more peripheral
connections.

5RISK ASSESSMENT FOR MYHEALTH
Operating system: Operating systems in computers are among the most important
components of computers. Almost all computers including cellular telephones need operating
systems for operating as intended. Operating systems allow users to work with the computer
without the need of understanding how computers work.
Firewall: firewalls are security systems that use predetermined set of rules for analysing
and controlling traffic going in and out of the network. In other words, firewalls serve as
gatekeepers which keep malicious programs and viruses away from the network for
preventing breach of data.
Telnet connection: The Telnet protocol is used for providing communication through the
Internet or a LAN by using virtual terminal connections. This is by default installed on Linux
and old Mac operating systems but has to be separately installed on windows based operating
systems and macOS High Sierra 10.13 or later.
Wireless Access Points: In wireless local area networks (WLAN), every access point is
the station that transmits and receives data (transceivers). Wireless access points connect one
user with another in the network, also serving like interconnects between WLAN and the
wired network. Wireless access points are used for serving multiple users in specified
network areas. When people exit the range of an access point, they automatically get
connected to the next. Small WLANs might only be requiring a single wireless access point
but the number increases proportionally with the number of network users and the network
size.
Number
Asset ID Asset Asset
Location
Ownership Asset
Description
Operating system: Operating systems in computers are among the most important
components of computers. Almost all computers including cellular telephones need operating
systems for operating as intended. Operating systems allow users to work with the computer
without the need of understanding how computers work.
Firewall: firewalls are security systems that use predetermined set of rules for analysing
and controlling traffic going in and out of the network. In other words, firewalls serve as
gatekeepers which keep malicious programs and viruses away from the network for
preventing breach of data.
Telnet connection: The Telnet protocol is used for providing communication through the
Internet or a LAN by using virtual terminal connections. This is by default installed on Linux
and old Mac operating systems but has to be separately installed on windows based operating
systems and macOS High Sierra 10.13 or later.
Wireless Access Points: In wireless local area networks (WLAN), every access point is
the station that transmits and receives data (transceivers). Wireless access points connect one
user with another in the network, also serving like interconnects between WLAN and the
wired network. Wireless access points are used for serving multiple users in specified
network areas. When people exit the range of an access point, they automatically get
connected to the next. Small WLANs might only be requiring a single wireless access point
but the number increases proportionally with the number of network users and the network
size.
Number
Asset ID Asset Asset
Location
Ownership Asset
Description
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
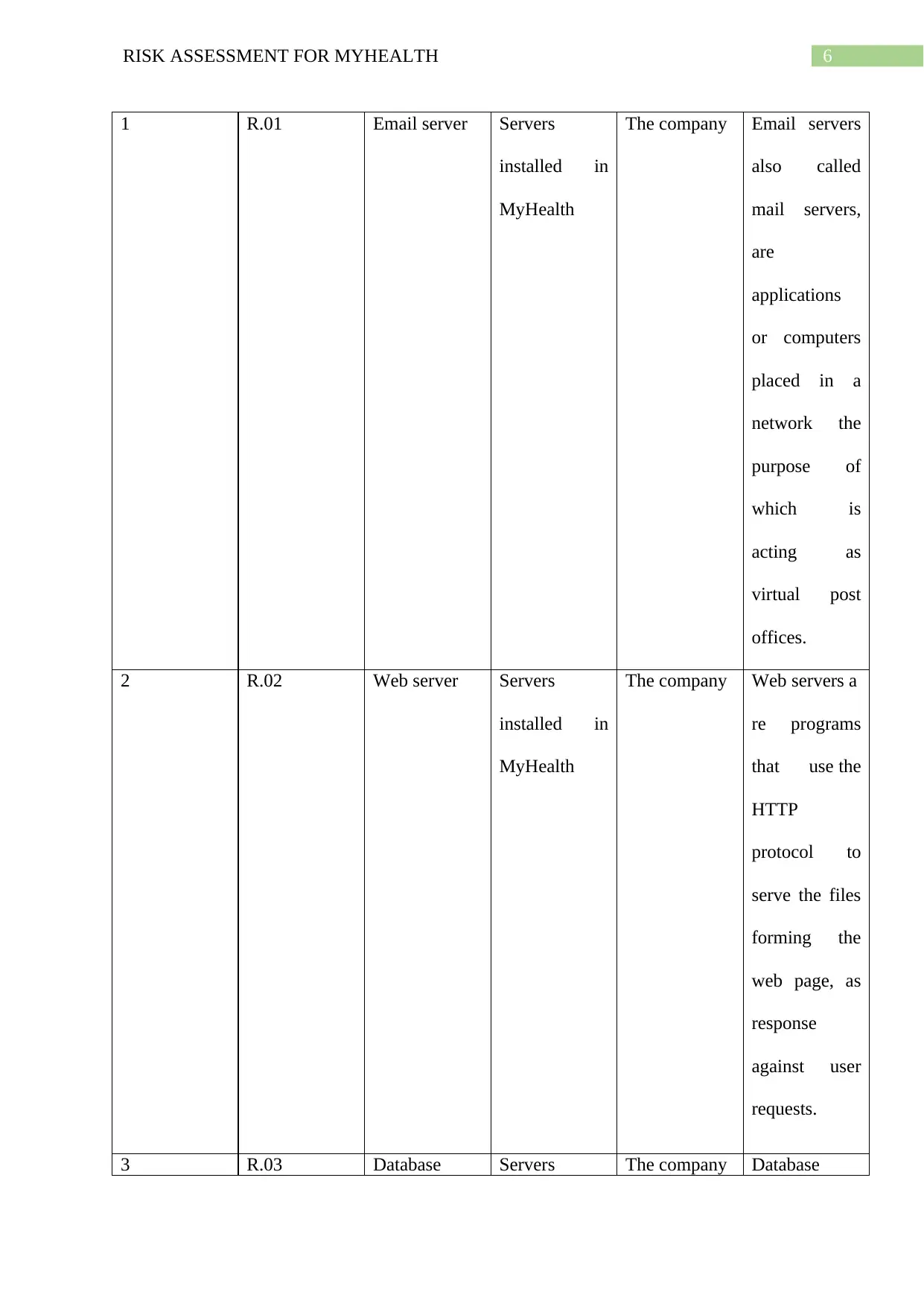
6RISK ASSESSMENT FOR MYHEALTH
1 R.01 Email server Servers
installed in
MyHealth
The company Email servers
also called
mail servers,
are
applications
or computers
placed in a
network the
purpose of
which is
acting as
virtual post
offices.
2 R.02 Web server Servers
installed in
MyHealth
The company Web servers a
re programs
that use the
HTTP
protocol to
serve the files
forming the
web page, as
response
against user
requests.
3 R.03 Database Servers The company Database
1 R.01 Email server Servers
installed in
MyHealth
The company Email servers
also called
mail servers,
are
applications
or computers
placed in a
network the
purpose of
which is
acting as
virtual post
offices.
2 R.02 Web server Servers
installed in
MyHealth
The company Web servers a
re programs
that use the
HTTP
protocol to
serve the files
forming the
web page, as
response
against user
requests.
3 R.03 Database Servers The company Database
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
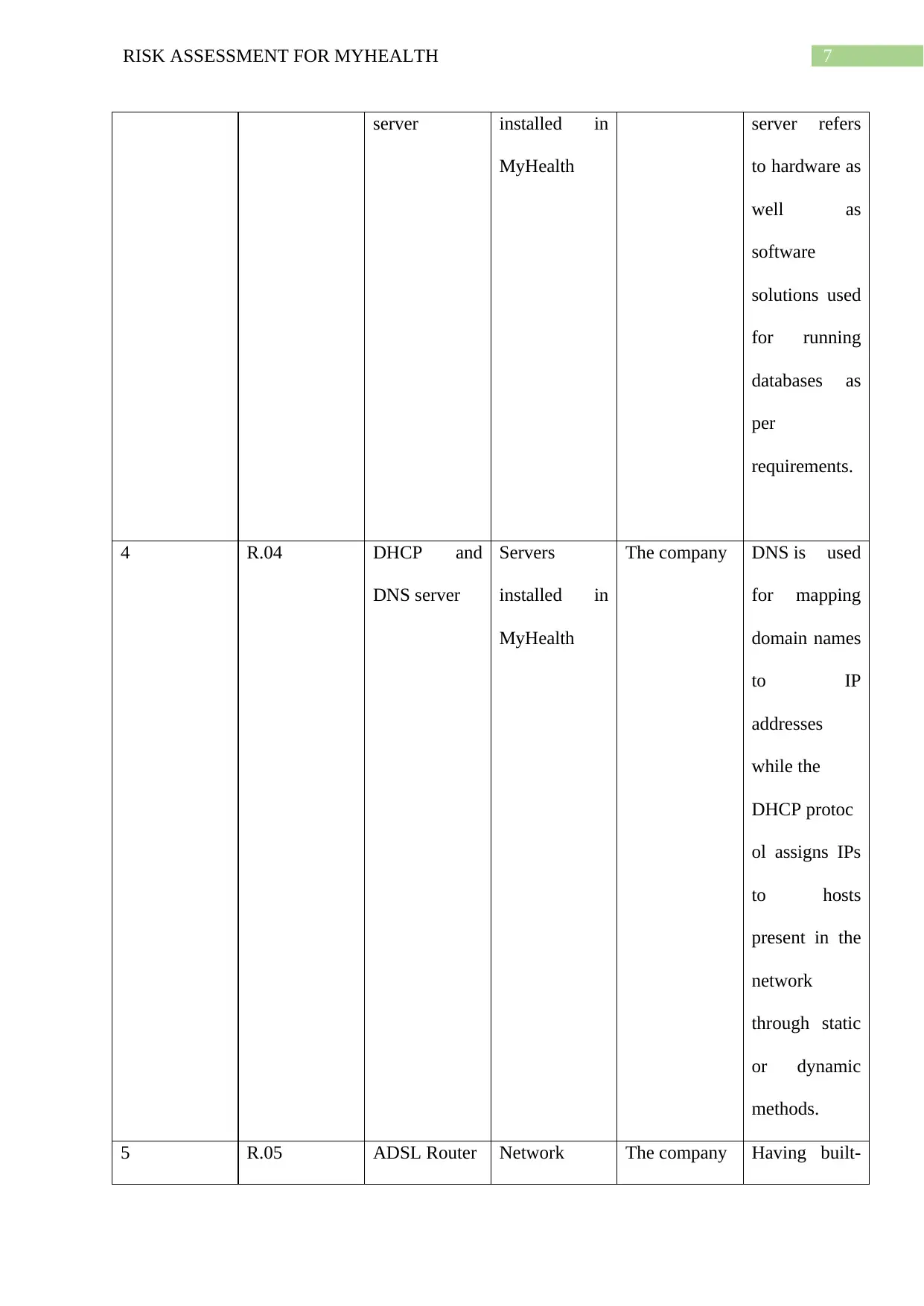
7RISK ASSESSMENT FOR MYHEALTH
server installed in
MyHealth
server refers
to hardware as
well as
software
solutions used
for running
databases as
per
requirements.
4 R.04 DHCP and
DNS server
Servers
installed in
MyHealth
The company DNS is used
for mapping
domain names
to IP
addresses
while the
DHCP protoc
ol assigns IPs
to hosts
present in the
network
through static
or dynamic
methods.
5 R.05 ADSL Router Network The company Having built-
server installed in
MyHealth
server refers
to hardware as
well as
software
solutions used
for running
databases as
per
requirements.
4 R.04 DHCP and
DNS server
Servers
installed in
MyHealth
The company DNS is used
for mapping
domain names
to IP
addresses
while the
DHCP protoc
ol assigns IPs
to hosts
present in the
network
through static
or dynamic
methods.
5 R.05 ADSL Router Network The company Having built-
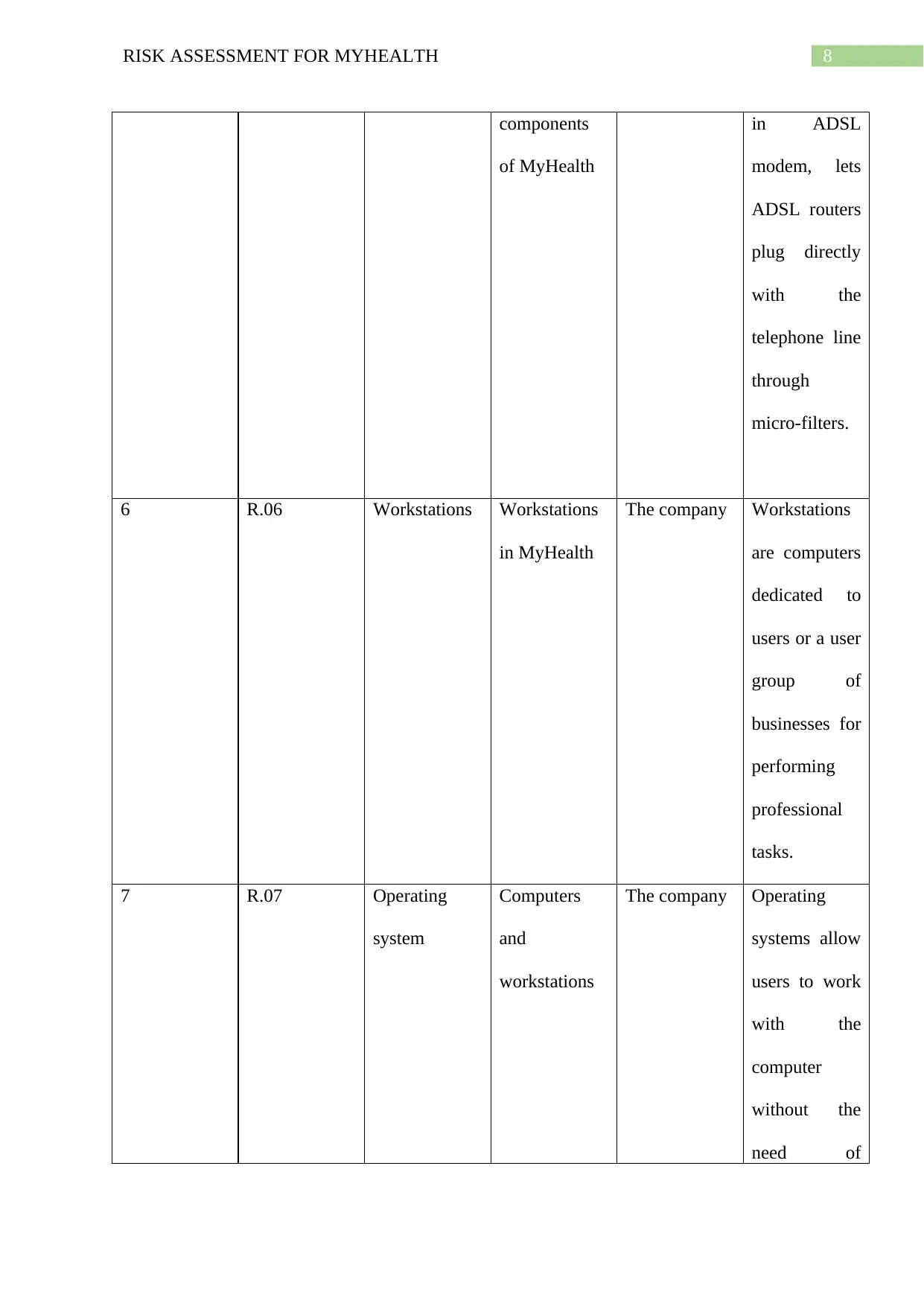
8RISK ASSESSMENT FOR MYHEALTH
components
of MyHealth
in ADSL
modem, lets
ADSL routers
plug directly
with the
telephone line
through
micro-filters.
6 R.06 Workstations Workstations
in MyHealth
The company Workstations
are computers
dedicated to
users or a user
group of
businesses for
performing
professional
tasks.
7 R.07 Operating
system
Computers
and
workstations
The company Operating
systems allow
users to work
with the
computer
without the
need of
components
of MyHealth
in ADSL
modem, lets
ADSL routers
plug directly
with the
telephone line
through
micro-filters.
6 R.06 Workstations Workstations
in MyHealth
The company Workstations
are computers
dedicated to
users or a user
group of
businesses for
performing
professional
tasks.
7 R.07 Operating
system
Computers
and
workstations
The company Operating
systems allow
users to work
with the
computer
without the
need of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
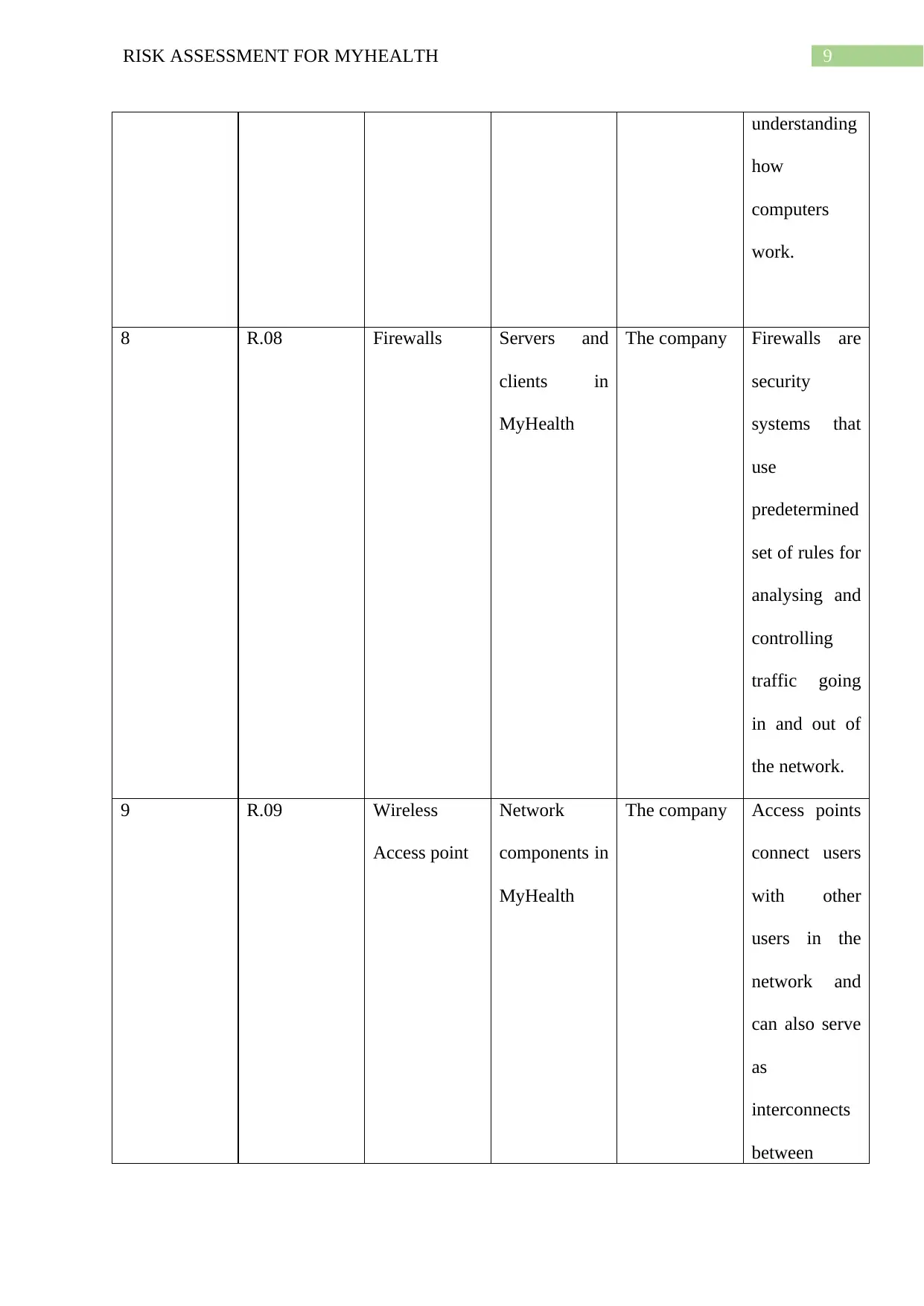
9RISK ASSESSMENT FOR MYHEALTH
understanding
how
computers
work.
8 R.08 Firewalls Servers and
clients in
MyHealth
The company Firewalls are
security
systems that
use
predetermined
set of rules for
analysing and
controlling
traffic going
in and out of
the network.
9 R.09 Wireless
Access point
Network
components in
MyHealth
The company Access points
connect users
with other
users in the
network and
can also serve
as
interconnects
between
understanding
how
computers
work.
8 R.08 Firewalls Servers and
clients in
MyHealth
The company Firewalls are
security
systems that
use
predetermined
set of rules for
analysing and
controlling
traffic going
in and out of
the network.
9 R.09 Wireless
Access point
Network
components in
MyHealth
The company Access points
connect users
with other
users in the
network and
can also serve
as
interconnects
between
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10RISK ASSESSMENT FOR MYHEALTH
WLAN and
the wired
network.
10 R.10 Telnet
connection
Client
computers
The company The
Telnet protoco
l is used for
providing
communicatio
n through the
Internet or a
LAN by using
virtual
terminal
connections.
Information Security Governance and MyHealth
A multitude of compliance and legislative requirements on IT security mandate
overseeing of how information security issues ae addressed by institutions. They need to
adhere by the governance framework to meet these regulations. Information Security
Governance concerns with identifying and ranking of risks that are most critical to the
business and to provide means for monitoring information-related access controls and data
integrity violations.
WLAN and
the wired
network.
10 R.10 Telnet
connection
Client
computers
The company The
Telnet protoco
l is used for
providing
communicatio
n through the
Internet or a
LAN by using
virtual
terminal
connections.
Information Security Governance and MyHealth
A multitude of compliance and legislative requirements on IT security mandate
overseeing of how information security issues ae addressed by institutions. They need to
adhere by the governance framework to meet these regulations. Information Security
Governance concerns with identifying and ranking of risks that are most critical to the
business and to provide means for monitoring information-related access controls and data
integrity violations.

11RISK ASSESSMENT FOR MYHEALTH
This formal approach makes Information Security Governance extremely essential for
MyHealth where all the IT staff help manage information security in a generic way without
defined roles. The above-mentioned approach alleviates this problem.
Cybersecurity policies for MyHealth
Cyber security policies outline assets that are needed to be protected, threats to these
assets as also controls and rules for protecting the members and the business. The policy must
tell the users and employees of the respective responsibilities for protecting technologies and
information assets of the business. Among these issues are:
Type of business information to be shared
Agreed upon usage policy of materials and devices
Handling and storing sensitive material
Policies to secure operations of MyHEalth can be:
1. Authentication: Having segmented access levels for the different business
processes of MyHealth secured with passwords which should only be known to
the domain personnel and the IT staff and should be updated periodically.
2. Emailing standards: These should include opening of email attachments from
trusted businesses and contacts. Blocking of spam and junk emails and deleting
suspicious mail.
3. Locking of computers: The users must not forget to shut down the computers and
mobile after the day’s work and locking computer screen if not being used.
This formal approach makes Information Security Governance extremely essential for
MyHealth where all the IT staff help manage information security in a generic way without
defined roles. The above-mentioned approach alleviates this problem.
Cybersecurity policies for MyHealth
Cyber security policies outline assets that are needed to be protected, threats to these
assets as also controls and rules for protecting the members and the business. The policy must
tell the users and employees of the respective responsibilities for protecting technologies and
information assets of the business. Among these issues are:
Type of business information to be shared
Agreed upon usage policy of materials and devices
Handling and storing sensitive material
Policies to secure operations of MyHEalth can be:
1. Authentication: Having segmented access levels for the different business
processes of MyHealth secured with passwords which should only be known to
the domain personnel and the IT staff and should be updated periodically.
2. Emailing standards: These should include opening of email attachments from
trusted businesses and contacts. Blocking of spam and junk emails and deleting
suspicious mail.
3. Locking of computers: The users must not forget to shut down the computers and
mobile after the day’s work and locking computer screen if not being used.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




