Proposal Document: PII Privacy Strategy for MyLicense Portal
VerifiedAdded on 2023/06/06
|4
|1102
|65
Report
AI Summary
This document presents a comprehensive PII (Personally Identifiable Information) privacy strategy for the MyLicense portal. The strategy focuses on controlling the collection, use, and dissemination of client agencies' PII data, particularly virtual licenses and associated contact information. It emphasizes informed consent for data collection and outlines various privacy and data protection controls to mitigate risks such as data theft, exposure, and cyber security threats. The document details measures for automatic information collection, third-party vendor data handling, cookie management, and security protocols for emails and third-party applications. References to relevant literature further support the proposed strategy, ensuring a robust approach to data privacy within the MyLicense portal.

PII PRIVACY STRATEGY FOR MYLICENSE
PORTAL (PROPOSAL DOCUMENT)
This plan serves as the basis for controlling the PII (Personally Identifiable Information) data
of the client agencies related to DAS. This plan will help to control the PII data regarding the
nature, use and purpose along with dissemination that will be gathered through the DAS
portal. The most important information that will be stored or used will be virtual licences
along with their integration. This strategy will be used for implementing policies for
providing clients of the company with the transparency about their PII data. This strategy will
relate to the various PII data whether online or offline and it will be collected through the
MyLicence portal. The PII includes the following:
Complete Virtual licenses (that can be intercepted for retrieval)
Email ID and Name
Home or Mailing Address
Phone numbers or other contact details
The PII data of the clients will be collected and stored only with their informed consent so
that those can be retrieved whenever required. The submission of the PII data will be carried
out voluntarily and the clients providing the permission to access will provide authority to
DAS for accessing and retrieving their PII data for mentioned purpose. In case, the user does
not provides the required information then access to certain specific services could be
restricted. The PII data will be collected after required information is being filled by the users
through the registration forms so that required services can be provided to the clients. The
services being offered will differ based on the query raised by the users or clients of the
company. The privacy notice that is generated while any user performs some action using the
portal will provide information on the intended used of their PII data, reason of collecting the
information and providing informed consent.
PORTAL (PROPOSAL DOCUMENT)
This plan serves as the basis for controlling the PII (Personally Identifiable Information) data
of the client agencies related to DAS. This plan will help to control the PII data regarding the
nature, use and purpose along with dissemination that will be gathered through the DAS
portal. The most important information that will be stored or used will be virtual licences
along with their integration. This strategy will be used for implementing policies for
providing clients of the company with the transparency about their PII data. This strategy will
relate to the various PII data whether online or offline and it will be collected through the
MyLicence portal. The PII includes the following:
Complete Virtual licenses (that can be intercepted for retrieval)
Email ID and Name
Home or Mailing Address
Phone numbers or other contact details
The PII data of the clients will be collected and stored only with their informed consent so
that those can be retrieved whenever required. The submission of the PII data will be carried
out voluntarily and the clients providing the permission to access will provide authority to
DAS for accessing and retrieving their PII data for mentioned purpose. In case, the user does
not provides the required information then access to certain specific services could be
restricted. The PII data will be collected after required information is being filled by the users
through the registration forms so that required services can be provided to the clients. The
services being offered will differ based on the query raised by the users or clients of the
company. The privacy notice that is generated while any user performs some action using the
portal will provide information on the intended used of their PII data, reason of collecting the
information and providing informed consent.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
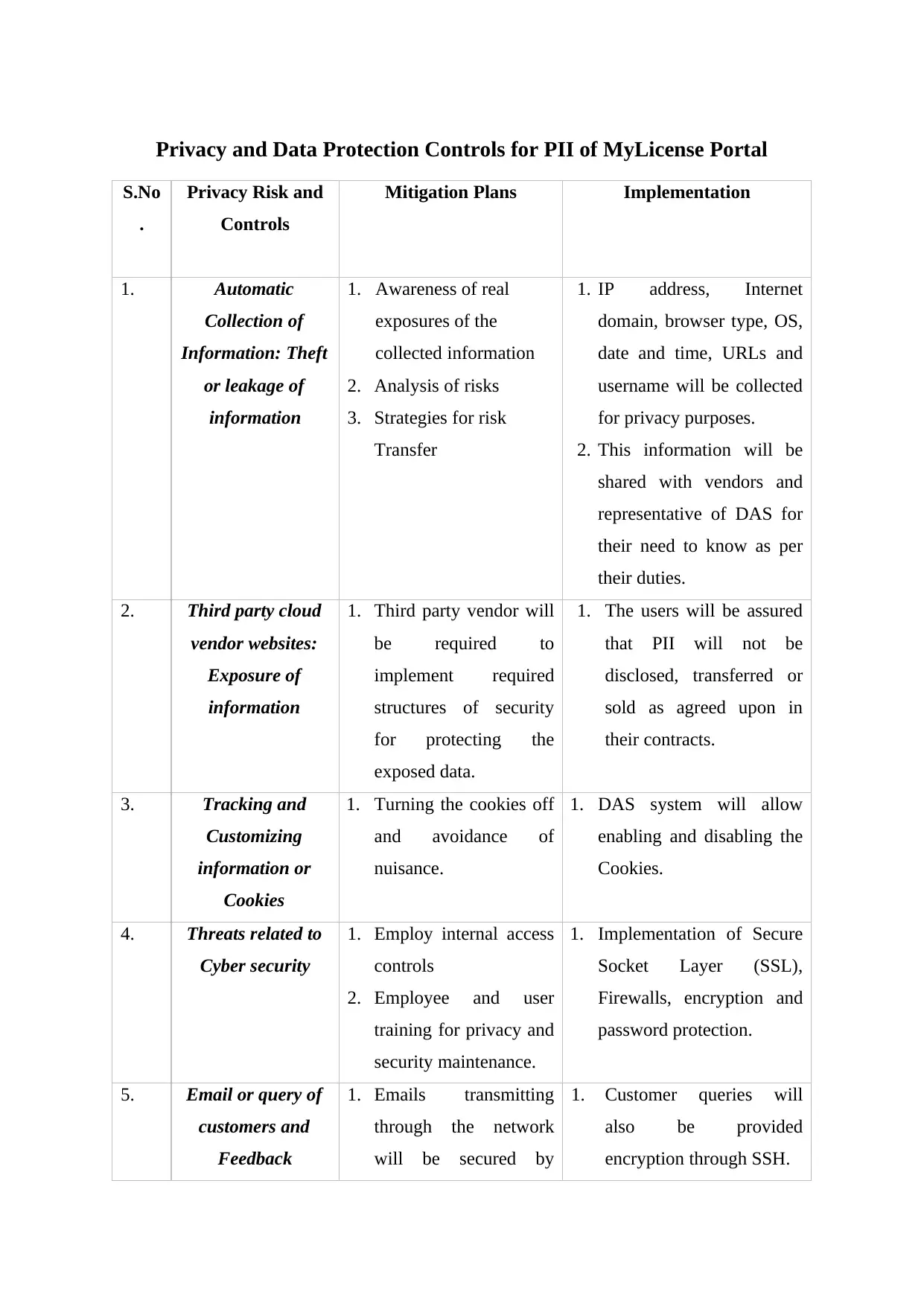
Privacy and Data Protection Controls for PII of MyLicense Portal
S.No
.
Privacy Risk and
Controls
Mitigation Plans Implementation
1. Automatic
Collection of
Information: Theft
or leakage of
information
1. Awareness of real
exposures of the
collected information
2. Analysis of risks
3. Strategies for risk
Transfer
1. IP address, Internet
domain, browser type, OS,
date and time, URLs and
username will be collected
for privacy purposes.
2. This information will be
shared with vendors and
representative of DAS for
their need to know as per
their duties.
2. Third party cloud
vendor websites:
Exposure of
information
1. Third party vendor will
be required to
implement required
structures of security
for protecting the
exposed data.
1. The users will be assured
that PII will not be
disclosed, transferred or
sold as agreed upon in
their contracts.
3. Tracking and
Customizing
information or
Cookies
1. Turning the cookies off
and avoidance of
nuisance.
1. DAS system will allow
enabling and disabling the
Cookies.
4. Threats related to
Cyber security
1. Employ internal access
controls
2. Employee and user
training for privacy and
security maintenance.
1. Implementation of Secure
Socket Layer (SSL),
Firewalls, encryption and
password protection.
5. Email or query of
customers and
Feedback
1. Emails transmitting
through the network
will be secured by
1. Customer queries will
also be provided
encryption through SSH.
S.No
.
Privacy Risk and
Controls
Mitigation Plans Implementation
1. Automatic
Collection of
Information: Theft
or leakage of
information
1. Awareness of real
exposures of the
collected information
2. Analysis of risks
3. Strategies for risk
Transfer
1. IP address, Internet
domain, browser type, OS,
date and time, URLs and
username will be collected
for privacy purposes.
2. This information will be
shared with vendors and
representative of DAS for
their need to know as per
their duties.
2. Third party cloud
vendor websites:
Exposure of
information
1. Third party vendor will
be required to
implement required
structures of security
for protecting the
exposed data.
1. The users will be assured
that PII will not be
disclosed, transferred or
sold as agreed upon in
their contracts.
3. Tracking and
Customizing
information or
Cookies
1. Turning the cookies off
and avoidance of
nuisance.
1. DAS system will allow
enabling and disabling the
Cookies.
4. Threats related to
Cyber security
1. Employ internal access
controls
2. Employee and user
training for privacy and
security maintenance.
1. Implementation of Secure
Socket Layer (SSL),
Firewalls, encryption and
password protection.
5. Email or query of
customers and
Feedback
1. Emails transmitting
through the network
will be secured by
1. Customer queries will
also be provided
encryption through SSH.

appropriate means.
6. Third Party
Applications:
Exposure of PII
data
1. The application setting
will be changed to
minimise the security
risks.
1. These applications will
come with predefined
settings for changing the
security settings.
Description
1. Automatic Collection of Information: The system will facilitate automatic
collection of information of the users visiting the portal. It will comprise of domain
name, browser type, OS type, IP address, time and date of access along with their
username.
2. Websites of Third party cloud vendor: The website will collect basic information of
the users who will be registering into the system. The details will include Email ID,
name, contact details which will be entered at the time of registration through the
portal.
3. Tracking and Customizing Information or Cookies: The information included will
involve session as well as persistent cookies which will highlighted to users so that
specific information of users can be remembered for their own convenience.
4. Threats related to Cyber security: The information of customers within the
repositories of DAS will be prone to threats related to security so specific measures
will be implemented for access controls, firewall along with password protection
using strong encryption methods.
5. Email or query of customers and Feedback: The information of the users is
distributed when the users send an email or raise a query or provides feedback
highlighting some specific issue.
6. Third Party Applications: The users will access these type of applications for their
own convenience to access certain services as per the information provided by them
in the system.
6. Third Party
Applications:
Exposure of PII
data
1. The application setting
will be changed to
minimise the security
risks.
1. These applications will
come with predefined
settings for changing the
security settings.
Description
1. Automatic Collection of Information: The system will facilitate automatic
collection of information of the users visiting the portal. It will comprise of domain
name, browser type, OS type, IP address, time and date of access along with their
username.
2. Websites of Third party cloud vendor: The website will collect basic information of
the users who will be registering into the system. The details will include Email ID,
name, contact details which will be entered at the time of registration through the
portal.
3. Tracking and Customizing Information or Cookies: The information included will
involve session as well as persistent cookies which will highlighted to users so that
specific information of users can be remembered for their own convenience.
4. Threats related to Cyber security: The information of customers within the
repositories of DAS will be prone to threats related to security so specific measures
will be implemented for access controls, firewall along with password protection
using strong encryption methods.
5. Email or query of customers and Feedback: The information of the users is
distributed when the users send an email or raise a query or provides feedback
highlighting some specific issue.
6. Third Party Applications: The users will access these type of applications for their
own convenience to access certain services as per the information provided by them
in the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Barrett, C. (2017). Managing privacy and access with digital forensics tools and techniques.
Casanovas, P., De Koker, L., Mendelson, D., & Watts, D. (2017). Regulation of Big Data:
Perspectives on strategy, policy, law and privacy. Health and Technology, 7(4), 335-
349.
Courtney, M. (2017). Careless talk costs privacy [digital assistants]. Engineering &
Technology, 12(10), 50-53.
Martin, K. D., & Murphy, P. E. (2017). The role of data privacy in marketing. Journal of the
Academy of Marketing Science, 45(2), 135-155.
Rice, J. C., & Sussan, F. (2016). Digital privacy: A conceptual framework for
business. Journal of Payments Strategy & Systems, 10(3), 260-266.
Yin, C., Xi, J., Sun, R., & Wang, J. (2018). Location privacy protection based on differential
privacy strategy for big data in industrial internet of things. IEEE Transactions on
Industrial Informatics, 14(8), 3628-3636.
Barrett, C. (2017). Managing privacy and access with digital forensics tools and techniques.
Casanovas, P., De Koker, L., Mendelson, D., & Watts, D. (2017). Regulation of Big Data:
Perspectives on strategy, policy, law and privacy. Health and Technology, 7(4), 335-
349.
Courtney, M. (2017). Careless talk costs privacy [digital assistants]. Engineering &
Technology, 12(10), 50-53.
Martin, K. D., & Murphy, P. E. (2017). The role of data privacy in marketing. Journal of the
Academy of Marketing Science, 45(2), 135-155.
Rice, J. C., & Sussan, F. (2016). Digital privacy: A conceptual framework for
business. Journal of Payments Strategy & Systems, 10(3), 260-266.
Yin, C., Xi, J., Sun, R., & Wang, J. (2018). Location privacy protection based on differential
privacy strategy for big data in industrial internet of things. IEEE Transactions on
Industrial Informatics, 14(8), 3628-3636.
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




