CSU Project: NFC Sensors for Secured Data Transmission Review
VerifiedAdded on 2024/06/28
|87
|10938
|232
Literature Review
AI Summary
This literature review examines near-field communication (NFC) sensors and their modulation techniques for secured data transmission in personal security systems. It analyzes five journal papers, focusing on techniques like probabilistic model checking to address relay attacks and enhance security in NFC communications. The review covers the use of NFC tag sensors with smartphones for biochemical sensing in environmental monitoring, food safety, and healthcare, highlighting their wireless and passive nature. It further explores the impact of NFC adoption on visitor satisfaction and loyalty at Expos, utilizing the Motivation-Opportunity-Ability (MOA) framework. Finally, it addresses the challenge of eavesdropping on NFC communications, presenting analytical models to defend against such attacks. The studies collectively demonstrate the versatility and potential of NFC technology in various applications, while also acknowledging its limitations and ongoing security concerns. Desklib provides access to this and other solved assignments.

Literature Review
Student Name & CSU ID
Project Topic Title Near-field communication sensors modulation for secured data transmission in personal security system
1
Student Name & CSU ID
Project Topic Title Near-field communication sensors modulation for secured data transmission in personal security system
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Version 1.0 _ Week 1 (5 Journal Papers from CSU Library)
1
Reference in APA format that will be in 'Reference List' Alexiou, N., Basagiannis, S., & Petridou, S. (2016). Formal security analysis of near field
communication using model checking. Computers and Security, 60, 1-14.
Citation that will be in the content (Alexiou, et. al., 2015)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-com.ezproxy.csu.edu.au/science/
article/pii/S0167404816300244
Journal Ranking: Q1 Wireless communication, Near field
communication, Relay attack, Probabilistic model
checking, Security analysis
The Name of the Current Solution (Technique/ Method/
Scheme/ Algorithm/ Model/ Tool/ Framework/ ... etc. )
The Goal (Objective) of this
Solution & What is the Problem
that need to be solved
What are the components of it?
Technique/Algorithm name:
Probabilistic model checking
Radiofrequency identification
Tools:
PRISM model checker
Applied Area:
Security analysis
Problem:
The major problem is of security. It
faces the problem of relay attacks.
Also, there is a problem of delay in
packets.
Goal:
In this work, we analyze and verify
the NFC model and create a model to
recover quickly from relay attacks.
Also to solve the security issues and
establish secure ad-hoc connections.
Antenna
Smartphones
RFI
Reliable hardware implementations
Software card emulation
The Process (Mechanism) of this Work; The process steps of the Technique/system
2
1
Reference in APA format that will be in 'Reference List' Alexiou, N., Basagiannis, S., & Petridou, S. (2016). Formal security analysis of near field
communication using model checking. Computers and Security, 60, 1-14.
Citation that will be in the content (Alexiou, et. al., 2015)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-com.ezproxy.csu.edu.au/science/
article/pii/S0167404816300244
Journal Ranking: Q1 Wireless communication, Near field
communication, Relay attack, Probabilistic model
checking, Security analysis
The Name of the Current Solution (Technique/ Method/
Scheme/ Algorithm/ Model/ Tool/ Framework/ ... etc. )
The Goal (Objective) of this
Solution & What is the Problem
that need to be solved
What are the components of it?
Technique/Algorithm name:
Probabilistic model checking
Radiofrequency identification
Tools:
PRISM model checker
Applied Area:
Security analysis
Problem:
The major problem is of security. It
faces the problem of relay attacks.
Also, there is a problem of delay in
packets.
Goal:
In this work, we analyze and verify
the NFC model and create a model to
recover quickly from relay attacks.
Also to solve the security issues and
establish secure ad-hoc connections.
Antenna
Smartphones
RFI
Reliable hardware implementations
Software card emulation
The Process (Mechanism) of this Work; The process steps of the Technique/system
2
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 RF collision avoidance: To prevent collisions
between the surrounding readers.
If no RF field is detected than reader enables
its own field.
N/A
2 Initialization single device detection: Allows
the reader to detect NFC- enabled device
It targets nearby by broadcasting polling
request. The further one is selected and then it
is replied back.
Only one card is supported.
3 Transport protocol: Reader select a nearby
target, it starts data transmission with Transport
protocol.
It gives an acknowledgment for receiving a
successful packet.
N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Model transitions between states Protocols
End user application Secure ad-hoc connections
Input and Output Critical Thinking: Feature of
this work, and Why (Justify)
Critical Thinking: Limitations
of the research current solution,
and Why (Justify)
Input (Data) Output (View)
Data Packets
For encoding and
decoding thedata
which requires
several processing
It can be in any form either
picture, document etc. We
can transmit this data to
another device.
NFC is used for wireless
communications in a short range
for secure connections. It is
integrated with devices for the
purpose of authentic and
authorized exchange of data via
The major limitation is the relay
attack. It is similar to a man-in-
the-middle attack. In this when
data is exchanged between two
than malicious user either
intercepts the data and make
3
1 RF collision avoidance: To prevent collisions
between the surrounding readers.
If no RF field is detected than reader enables
its own field.
N/A
2 Initialization single device detection: Allows
the reader to detect NFC- enabled device
It targets nearby by broadcasting polling
request. The further one is selected and then it
is replied back.
Only one card is supported.
3 Transport protocol: Reader select a nearby
target, it starts data transmission with Transport
protocol.
It gives an acknowledgment for receiving a
successful packet.
N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Model transitions between states Protocols
End user application Secure ad-hoc connections
Input and Output Critical Thinking: Feature of
this work, and Why (Justify)
Critical Thinking: Limitations
of the research current solution,
and Why (Justify)
Input (Data) Output (View)
Data Packets
For encoding and
decoding thedata
which requires
several processing
It can be in any form either
picture, document etc. We
can transmit this data to
another device.
NFC is used for wireless
communications in a short range
for secure connections. It is
integrated with devices for the
purpose of authentic and
authorized exchange of data via
The major limitation is the relay
attack. It is similar to a man-in-
the-middle attack. In this when
data is exchanged between two
than malicious user either
intercepts the data and make
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
for the analog data
to be used in
packet reception.
short-range NFC channels. And
also helps in improving personal
security with the help of the near
field sensors.
changes in it. After that, it re-
transmits it back.
(Describe the research/current solution) Evaluation Criteria How this research/current
solution is valuable for your
project
Near field communication help in allowing wireless communications for
supporting smart device application. In this two devices that are kept at 10 cm are
paired with each other. It is highly secure, but there are chances of relay attacks
between them so we describe the solutions to prevent the relay attacks by using
Probabilistic model checking. This model checking is a formal verification
technique and helps to find out the errors and unusual behavior in the system
(Alexiou, et. al., 2015).
In this the end users are the
humans who uses NFC sensors
with wireless communication
technology using for payments,
tickets.
Model checking is helpful to
analyze the security system. It
offers the advantage of automated
analysis, which helps in
communication technologies and
registered systems. With this, we
can increase personal security by
NFC.
Diagram/Flowchart
Figure: Security analysis proposal
4
to be used in
packet reception.
short-range NFC channels. And
also helps in improving personal
security with the help of the near
field sensors.
changes in it. After that, it re-
transmits it back.
(Describe the research/current solution) Evaluation Criteria How this research/current
solution is valuable for your
project
Near field communication help in allowing wireless communications for
supporting smart device application. In this two devices that are kept at 10 cm are
paired with each other. It is highly secure, but there are chances of relay attacks
between them so we describe the solutions to prevent the relay attacks by using
Probabilistic model checking. This model checking is a formal verification
technique and helps to find out the errors and unusual behavior in the system
(Alexiou, et. al., 2015).
In this the end users are the
humans who uses NFC sensors
with wireless communication
technology using for payments,
tickets.
Model checking is helpful to
analyze the security system. It
offers the advantage of automated
analysis, which helps in
communication technologies and
registered systems. With this, we
can increase personal security by
NFC.
Diagram/Flowchart
Figure: Security analysis proposal
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
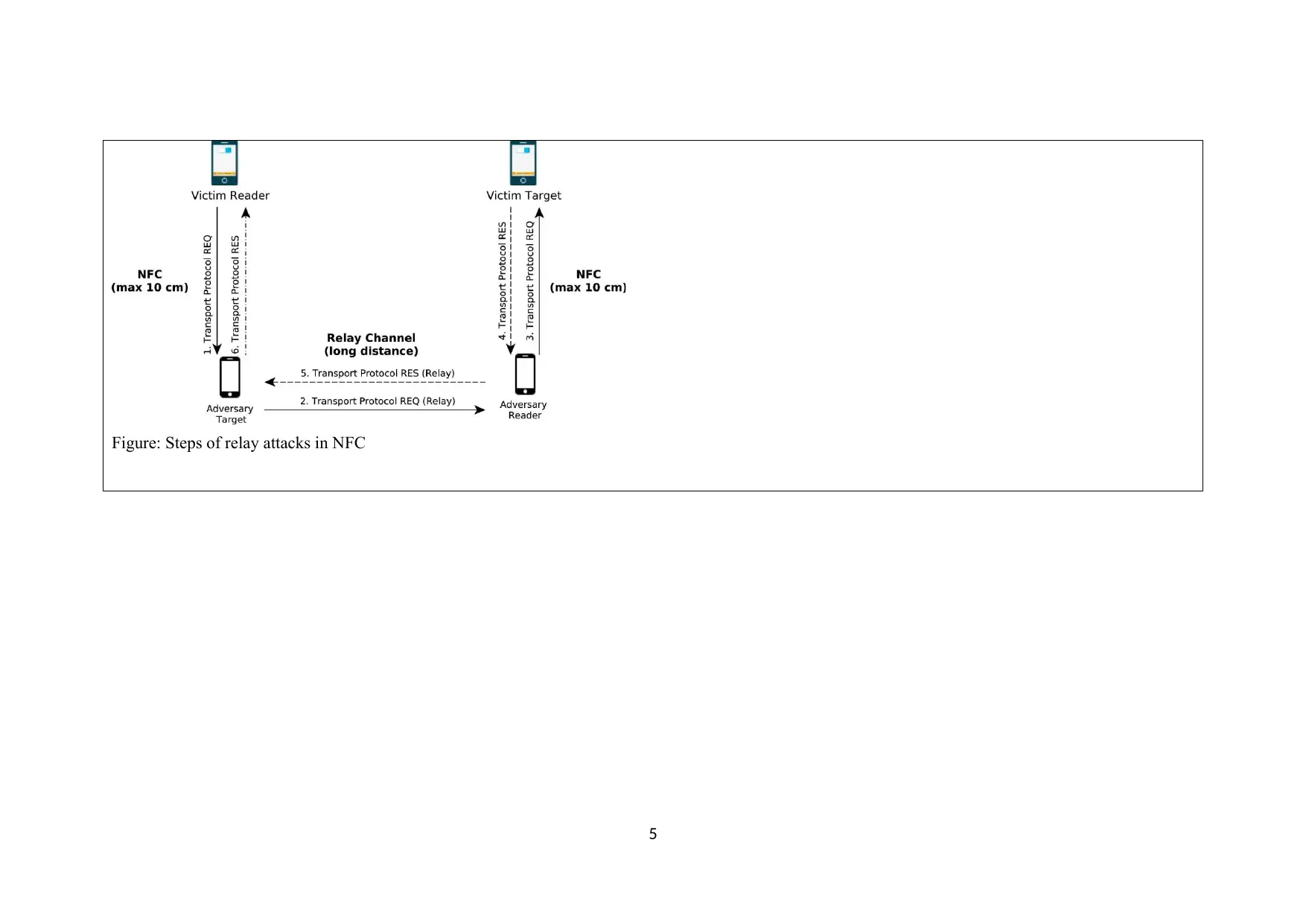
Figure: Steps of relay attacks in NFC
5
5
2
Reference in APA format that will be in
'Reference List'
Xu, G., Zhang, Q., Lu, Y., Liu, L., Ji, D., Li, S., & Liu, Q. (2017). Passive and wireless near field
communication tag sensors for biochemical sensing with smartphone. Sensors and Actuators, B: Chemical, 246,
748-755.
Citation that will be in the content (Xu, et. al., 2017)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/
S0925400517303751
Level of Journal: Q1 Near field communication (NFC) tag, Wireless and passive,
Biochemical sensing, Accurate semi-quantitative detection,
Smartphone
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Accurate semi-quantitative detection
Inductive coupling
Tools:
Resonant Circuits
Applied Area:
Environment monitoring, food safety, and
healthcare diagnosis.
Problem:
The major problem is that different sensing
device is used to detect ions, bacteria, and
gases. For each, we need different instruments.
Goal: To develop a wireless NFC tag sensor
that can be used with smartphones and receive
the results.
Smartphones
Integrated circuit
Chip capacitor
Resonant circuit
Electrodes
Sensors
Rheostat
The Process (Mechanism) of this Work; The process steps of the Technique/system
6
Reference in APA format that will be in
'Reference List'
Xu, G., Zhang, Q., Lu, Y., Liu, L., Ji, D., Li, S., & Liu, Q. (2017). Passive and wireless near field
communication tag sensors for biochemical sensing with smartphone. Sensors and Actuators, B: Chemical, 246,
748-755.
Citation that will be in the content (Xu, et. al., 2017)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/pii/
S0925400517303751
Level of Journal: Q1 Near field communication (NFC) tag, Wireless and passive,
Biochemical sensing, Accurate semi-quantitative detection,
Smartphone
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Accurate semi-quantitative detection
Inductive coupling
Tools:
Resonant Circuits
Applied Area:
Environment monitoring, food safety, and
healthcare diagnosis.
Problem:
The major problem is that different sensing
device is used to detect ions, bacteria, and
gases. For each, we need different instruments.
Goal: To develop a wireless NFC tag sensor
that can be used with smartphones and receive
the results.
Smartphones
Integrated circuit
Chip capacitor
Resonant circuit
Electrodes
Sensors
Rheostat
The Process (Mechanism) of this Work; The process steps of the Technique/system
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1
NFC tag sensors construction: It has a simple
resonant circuit with IC, capacitor, inductance,
chip and a polyethylene terephthalate (PET)
substrate.
Its state is detected by On or Off state. The applications read the NFC tags when
kept at a distance less than 2 cm.
2
NFC tag sensor modification for semi-
quantitative detections: With adding rheostat
in threshold value it changes.
It can also be calculated by using a sensor
array.
N/A
3
With NFC tag sensors and smartphone,
detection is performed: In this an
electrochemical workstation is connected
through an electrode for recording time-
impedance.
It is used to calculate the accuracy rate of
detections.
N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Accuracy Sensor array
Gas detection NFC tag sensors
7
1
NFC tag sensors construction: It has a simple
resonant circuit with IC, capacitor, inductance,
chip and a polyethylene terephthalate (PET)
substrate.
Its state is detected by On or Off state. The applications read the NFC tags when
kept at a distance less than 2 cm.
2
NFC tag sensor modification for semi-
quantitative detections: With adding rheostat
in threshold value it changes.
It can also be calculated by using a sensor
array.
N/A
3
With NFC tag sensors and smartphone,
detection is performed: In this an
electrochemical workstation is connected
through an electrode for recording time-
impedance.
It is used to calculate the accuracy rate of
detections.
N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Accuracy Sensor array
Gas detection NFC tag sensors
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Different types of
Gas solutions used
with NFC tags
sensors. Doping,
functionalizing and
hybridization can be
done using diverse
gases.
The gas detector
detects the gases and
their leakage in a
particular area as a
safety.
In this gas is with the help of smartphones and
NFC sensors for the purpose of safety. When a
leakage is found then an alarm rings so that
precautions can be taken and some safety measures
can help humans, animals, and organic life.
It has only one sensing module in it and also these
tag sensors cannot be used for purpose of
conversions. Also, these sensors have very less
capacity.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In this gas is detected with the NFC sensors and
smartphones. It is used for a safety purpose
because leakage of gas is identified. After
detection, we apply NFC tag sensors for detection
of Staphylococcus aureus and KCL in the
solution (Xu, et. al., 2017).
In this end users are individual and it is used for the
purpose of safety for humans, animals, and organic
life. It is wireless and has a low cost plus it is very
flexible.
It is a wireless solution that is used for food safety,
health care purpose and monitoring of the
environment. It has biochemical sensing and tells
how NFC tag sensors can be used.
Diagram/Flowchart
8
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
Different types of
Gas solutions used
with NFC tags
sensors. Doping,
functionalizing and
hybridization can be
done using diverse
gases.
The gas detector
detects the gases and
their leakage in a
particular area as a
safety.
In this gas is with the help of smartphones and
NFC sensors for the purpose of safety. When a
leakage is found then an alarm rings so that
precautions can be taken and some safety measures
can help humans, animals, and organic life.
It has only one sensing module in it and also these
tag sensors cannot be used for purpose of
conversions. Also, these sensors have very less
capacity.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In this gas is detected with the NFC sensors and
smartphones. It is used for a safety purpose
because leakage of gas is identified. After
detection, we apply NFC tag sensors for detection
of Staphylococcus aureus and KCL in the
solution (Xu, et. al., 2017).
In this end users are individual and it is used for the
purpose of safety for humans, animals, and organic
life. It is wireless and has a low cost plus it is very
flexible.
It is a wireless solution that is used for food safety,
health care purpose and monitoring of the
environment. It has biochemical sensing and tells
how NFC tag sensors can be used.
Diagram/Flowchart
8
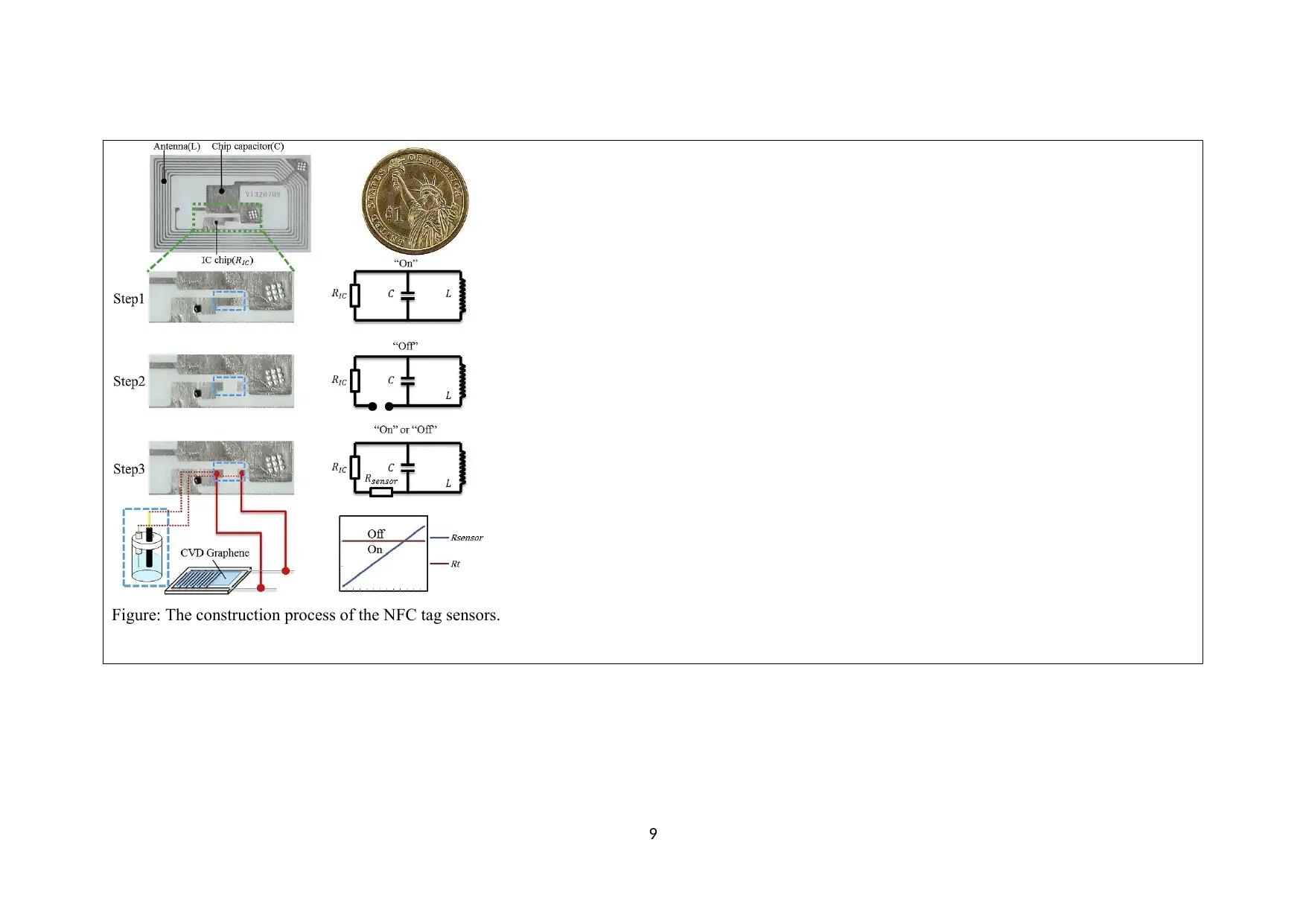
Figure: The construction process of the NFC tag sensors.
9
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
Reference in APA format that will be in
'Reference List'
Han, H., Park, A., Chung, N., & Lee, K. J. (2016). A near field communication adoption and its impact on Expo
visitors’ behavior. International Journal of Information Management, 36(6), 1328-1339.
Citation that will be in the content
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S026840121630192X#sec0070
Level of Journal: Q1 Satisfaction transfer, Near field communication, Smart
tourism, Expo, the Motivation-opportunity-ability framework
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Measurement model
Structural model
Tools:
Satisfaction transfer
Motivation-opportunity-ability (MOA)
Applied Area:
Tourism sector
Problem:
The major problem is of customer satisfaction
and loyalty at Expo. Also, it is limited to only
those visitors who participated in one Expo.
Goal:
The goal is to enhance and rejuvenate the
experience of visitors at Expo using
Motivation-opportunity-ability (MOA).
Tags
Stickers
Key Fobs
Cards
Initiator
A target
The Process (Mechanism) of this Work; The process steps of the Technique/system
10
Reference in APA format that will be in
'Reference List'
Han, H., Park, A., Chung, N., & Lee, K. J. (2016). A near field communication adoption and its impact on Expo
visitors’ behavior. International Journal of Information Management, 36(6), 1328-1339.
Citation that will be in the content
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S026840121630192X#sec0070
Level of Journal: Q1 Satisfaction transfer, Near field communication, Smart
tourism, Expo, the Motivation-opportunity-ability framework
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Measurement model
Structural model
Tools:
Satisfaction transfer
Motivation-opportunity-ability (MOA)
Applied Area:
Tourism sector
Problem:
The major problem is of customer satisfaction
and loyalty at Expo. Also, it is limited to only
those visitors who participated in one Expo.
Goal:
The goal is to enhance and rejuvenate the
experience of visitors at Expo using
Motivation-opportunity-ability (MOA).
Tags
Stickers
Key Fobs
Cards
Initiator
A target
The Process (Mechanism) of this Work; The process steps of the Technique/system
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1
Instrument development:
In this those items are considered whose
parameters are reliable and validated. And these
are used by NFC in Expo.
It re-examines the items and confirms the final
questions.
N/A
2
Data collection:
It collects data from NFC capable smartphones
for obtaining info about products in the
exhibition, discounts, location,
recommendations, popular sites etc.
NFC tag is used for counting the total times
when NFC was used at Expo.
It is difficult to conduct probability
sampling.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Reuse of technology Satisfaction
Recognition and data transmission Network area
Input and Output Critical Thinking: Feature of this work, and Critical Thinking: Limitations of the research
11
1
Instrument development:
In this those items are considered whose
parameters are reliable and validated. And these
are used by NFC in Expo.
It re-examines the items and confirms the final
questions.
N/A
2
Data collection:
It collects data from NFC capable smartphones
for obtaining info about products in the
exhibition, discounts, location,
recommendations, popular sites etc.
NFC tag is used for counting the total times
when NFC was used at Expo.
It is difficult to conduct probability
sampling.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Reuse of technology Satisfaction
Recognition and data transmission Network area
Input and Output Critical Thinking: Feature of this work, and Critical Thinking: Limitations of the research
11
Why (Justify) current solution, and Why (Justify)
Input (Data) Output (View)
Information is feed to
the NFC in order to
improve the quality of
the input information
It is transferred in
short distance by
wireless technology
without a physical
device.
If visitors are satisfied with the NFC use at the
Expo, their satisfaction with the overall Expo will
also increase. In studies related to satisfaction,
satisfaction is transferred from one component of an
object to the object overall
The major limitation is that only limited visitors
who have one Expo can participate. Hence
verification of the NFC role is done to verify the
findings. There are females and young age people
in the samples.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In this Measurement model and Structural model
is used. These models enhance the Expo
experience with the use of NFC. It mainly focuses
satisfaction of visitors, motivation-opportunity-
ability framework, intention to reuse NFC and
loyalty of Expo. They strengthen the expo
experience and helps in delivering the
information. MOA framework is used for
explaining how Expo visitors process the given
information with the help of NFC.
These are used by the visitors. These results
demonstrate why the use and application of new
smart technologies are important to the tourism
industry.
This research is helpful in increasing the
satisfaction level with the use of NFC and with
Expo. This satisfaction creates energy and brings
loyalty. NFC is used for the purpose of delivery of
correct information and improving the experience.
Diagram/Flowchart
12
Input (Data) Output (View)
Information is feed to
the NFC in order to
improve the quality of
the input information
It is transferred in
short distance by
wireless technology
without a physical
device.
If visitors are satisfied with the NFC use at the
Expo, their satisfaction with the overall Expo will
also increase. In studies related to satisfaction,
satisfaction is transferred from one component of an
object to the object overall
The major limitation is that only limited visitors
who have one Expo can participate. Hence
verification of the NFC role is done to verify the
findings. There are females and young age people
in the samples.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In this Measurement model and Structural model
is used. These models enhance the Expo
experience with the use of NFC. It mainly focuses
satisfaction of visitors, motivation-opportunity-
ability framework, intention to reuse NFC and
loyalty of Expo. They strengthen the expo
experience and helps in delivering the
information. MOA framework is used for
explaining how Expo visitors process the given
information with the help of NFC.
These are used by the visitors. These results
demonstrate why the use and application of new
smart technologies are important to the tourism
industry.
This research is helpful in increasing the
satisfaction level with the use of NFC and with
Expo. This satisfaction creates energy and brings
loyalty. NFC is used for the purpose of delivery of
correct information and improving the experience.
Diagram/Flowchart
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 87
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.