.NET Encryption: Advanced Runtime Techniques and Security Analysis
VerifiedAdded on 2023/06/13
|4
|657
|176
Report
AI Summary
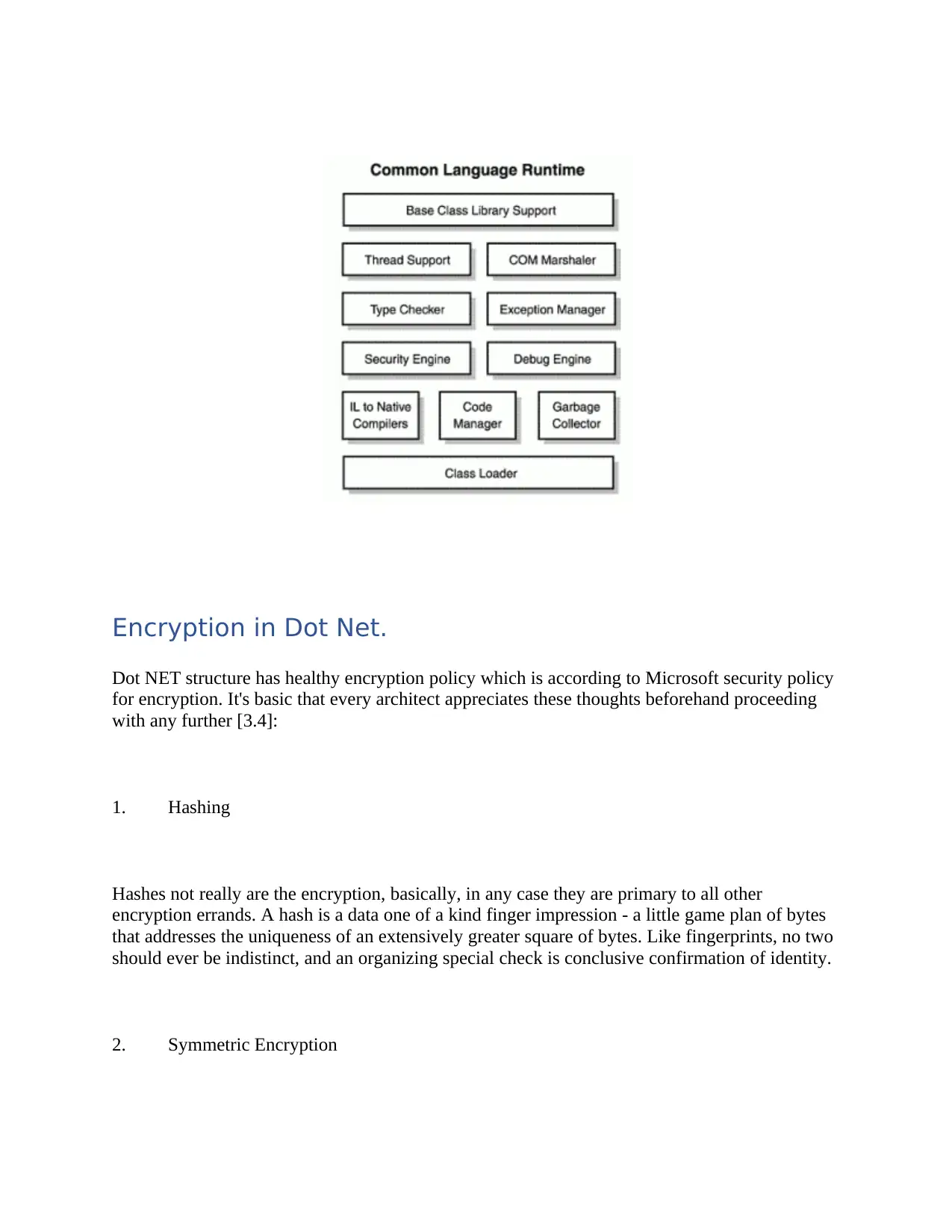
This report provides an overview of .NET encryption techniques, focusing on the runtime environment and security protocols. It discusses the Common Language Runtime (CLR) and the distinction between managed and unmanaged code. The report elaborates on encryption methods within the .NET framework, including hashing, symmetric encryption, and asymmetric encryption, highlighting their respective strengths and weaknesses. It emphasizes the importance of understanding these concepts for architects and developers to implement robust security measures. The document references various sources to support its explanations and provide a comprehensive understanding of .NET encryption strategies.
1 out of 4





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)