Network Layered Models, Addressing, and IPv6 Configuration Report
VerifiedAdded on 2023/01/09
|9
|2035
|33
Report
AI Summary
This report delves into the intricacies of computer networks, focusing on layered reference models like TCP/IP and OSI, essential for standardizing communication. It explores literature reviews on these models, highlighting their roles in data transmission and security. The report outlines an approach for documenting, executing, and testing network addressing, including the use of NAT. Furthermore, it provides practical examples of IPv6 subnet assignment and address configuration for routers and end devices, illustrating the application of MAC addresses for global unicast and link-local address assignments. The conclusion emphasizes the importance of these models for efficient and secure network operations, offering a comprehensive understanding of network architecture and addressing schemes. This report is a valuable resource for students studying network engineering, providing insights into the practical application of network principles and technologies.
Networks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................1
Part 1................................................................................................................................................1
1.1 Carry out literature search related with layered network reference model which is utilised
for execution of networking devices (routers, switches & end devices) will assist network
engineer and illustrate the output...........................................................................................1
1.2 Provide a review on required literature in context of reference models...........................1
1.3 Formulate approach for documenting, execution along with testing of network addressing
related with addressing computer network in figure along with its illustration.....................3
1.4 Justify the approach for implementing along with testing network addressing for computer
network...................................................................................................................................4
Part 2................................................................................................................................................4
Figure out and assign different 4 IPv6 subnets by appending subnet ID with global routing
prefix that is being given and then document IPv6 subnets in table......................................4
Illustrate global unicast IPv6 addresses for network interface related with router devices in
Interface Address table through the usage of MAC address..................................................5
Complete device address table, address along with prefix length and Link Local address with
end devices through usage of MAC address..........................................................................5
Conclusion.......................................................................................................................................5
References........................................................................................................................................6
Introduction......................................................................................................................................1
Part 1................................................................................................................................................1
1.1 Carry out literature search related with layered network reference model which is utilised
for execution of networking devices (routers, switches & end devices) will assist network
engineer and illustrate the output...........................................................................................1
1.2 Provide a review on required literature in context of reference models...........................1
1.3 Formulate approach for documenting, execution along with testing of network addressing
related with addressing computer network in figure along with its illustration.....................3
1.4 Justify the approach for implementing along with testing network addressing for computer
network...................................................................................................................................4
Part 2................................................................................................................................................4
Figure out and assign different 4 IPv6 subnets by appending subnet ID with global routing
prefix that is being given and then document IPv6 subnets in table......................................4
Illustrate global unicast IPv6 addresses for network interface related with router devices in
Interface Address table through the usage of MAC address..................................................5
Complete device address table, address along with prefix length and Link Local address with
end devices through usage of MAC address..........................................................................5
Conclusion.......................................................................................................................................5
References........................................................................................................................................6

Introduction
The set of connected systems in which data can be shared in between them is referred to
as computer networks. Connection between two systems is carried out by making use of different
cables they are, optical, twisted pair, Ethernet or fibre optical cable. This is responsible to
connect distinct parts related with distributed architecture (Saranya and Thangadurai, 2019).
While transmitting data, the network makes use of distinct frameworks, methods along with
protocols for ensuring safe transmission of data. Computer network denotes set of computer that
makes use of digital interconnections for sharing resources that are provided by networking
nodes. This report will illustrate the reference layered architecture, literature review along with
network addressing. In addition to this, example of IPv6 addressing will also be furnished.
Part 1
1.1 Carry out literature search related with layered network reference model which is utilised for
execution of networking devices (routers, switches & end devices) will assist network
engineer and illustrate the output.
The conceptual that is responsible for standardising communication among various or
different networks is defined as reference layered model. The layered model comprises of
different layers that are liable for carrying out predefined functions. By carrying out literature
survey, it has been acknowledged that TCP/IP and OSI are layered networks that are used for
transmitting data among different devices and reach the final destination. While doing so
different protocols and standards are being utilised by them for carrying out secured interaction
among them.
1.2 Provide a review on required literature in context of reference models.
According to Md M. Alani (2014), relevant introduction is provided of TCP/IP reference
layered model as well as protocols that are utilised with the layer. In addition to this,
internetwork is also specified in operating layers such as ICMP, ARP, RARP, InARP and IP.
Furthermore, protocols that are used for transmitting message among source and destination have
been specified (Alani, 2014).
As per P.Suresh (2016), focus is on open system interconnection reference model which
comprises of distinct seven layers where each have their own specified liabilities. Networking is
1
The set of connected systems in which data can be shared in between them is referred to
as computer networks. Connection between two systems is carried out by making use of different
cables they are, optical, twisted pair, Ethernet or fibre optical cable. This is responsible to
connect distinct parts related with distributed architecture (Saranya and Thangadurai, 2019).
While transmitting data, the network makes use of distinct frameworks, methods along with
protocols for ensuring safe transmission of data. Computer network denotes set of computer that
makes use of digital interconnections for sharing resources that are provided by networking
nodes. This report will illustrate the reference layered architecture, literature review along with
network addressing. In addition to this, example of IPv6 addressing will also be furnished.
Part 1
1.1 Carry out literature search related with layered network reference model which is utilised for
execution of networking devices (routers, switches & end devices) will assist network
engineer and illustrate the output.
The conceptual that is responsible for standardising communication among various or
different networks is defined as reference layered model. The layered model comprises of
different layers that are liable for carrying out predefined functions. By carrying out literature
survey, it has been acknowledged that TCP/IP and OSI are layered networks that are used for
transmitting data among different devices and reach the final destination. While doing so
different protocols and standards are being utilised by them for carrying out secured interaction
among them.
1.2 Provide a review on required literature in context of reference models.
According to Md M. Alani (2014), relevant introduction is provided of TCP/IP reference
layered model as well as protocols that are utilised with the layer. In addition to this,
internetwork is also specified in operating layers such as ICMP, ARP, RARP, InARP and IP.
Furthermore, protocols that are used for transmitting message among source and destination have
been specified (Alani, 2014).
As per P.Suresh (2016), focus is on open system interconnection reference model which
comprises of distinct seven layers where each have their own specified liabilities. Networking is
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

evolving from general principle that involves transmission of information from one system to
other.
According to Hamound M. Aldosari (2017), on the basis of IoT reference model
substantial changes are needed that can be attained by adding security layer. This will assist
within ensuring that sender or receiver will have blocking servers through which they can ensure
that their messages are not intercepted via a third person (Aldosari, 2015).
According to Pranaab Bandhu Nath (2015), functionalities have been organised into four
different abstraction layers which are then used to sort associated protocols with respect to scope
of network which is involved in this (Nath and Uddin, 2015). The paper illustrates operations
conducted by TCP/IP suite in data communication network.
As per Sergio Duque Castilho (2017), the IoT based survey is conducted in context of
security where technologies ae used. The risks related with such kind of devices will be exposed.
The TCP/IP reference model is utilised in this transmission or connection. The purpose of
initiation of models is dependent on ISO 7498-2 (Castilho and et. al, 2017).
According to Jean-Yuves Colin (2016), emphasis is laid on new open logistic
interconnection reference model that is being utilised for having physical internet which is
enhanced open systems interconnection model for dealing with different data networks and
ensure that transmission takes place among them (Colin, Mathieu and Nakechbandi, 2016). This
signifies critical variation with other models, like in reference models definitions are associated
with physical objects within different layers and just the lowest ones. On the other hand, NOLI
opts for containerisation along with de-containerisation in top layer and in last two. This is liable
for uniting session and transport layers into one.
According to Pakawat Pupawibul (2015), SDN with OpenFlow is enabled for direct
manipulation with respect to forwarding plan associated with hubs, router or any other
networking devices. These methods depend on flow from protocols like OpenFlow which
operates in contrast with different networking devices such as MAC table, TCP/IP, etc. routing.
The emphasis within paper is laid on relationship that prevails in between distinct processes that
are associated with forward packets in case of IP address routing table with respect to OpenFlow
table (Banjar, Pupatwibul and Braun, 2015).
2
other.
According to Hamound M. Aldosari (2017), on the basis of IoT reference model
substantial changes are needed that can be attained by adding security layer. This will assist
within ensuring that sender or receiver will have blocking servers through which they can ensure
that their messages are not intercepted via a third person (Aldosari, 2015).
According to Pranaab Bandhu Nath (2015), functionalities have been organised into four
different abstraction layers which are then used to sort associated protocols with respect to scope
of network which is involved in this (Nath and Uddin, 2015). The paper illustrates operations
conducted by TCP/IP suite in data communication network.
As per Sergio Duque Castilho (2017), the IoT based survey is conducted in context of
security where technologies ae used. The risks related with such kind of devices will be exposed.
The TCP/IP reference model is utilised in this transmission or connection. The purpose of
initiation of models is dependent on ISO 7498-2 (Castilho and et. al, 2017).
According to Jean-Yuves Colin (2016), emphasis is laid on new open logistic
interconnection reference model that is being utilised for having physical internet which is
enhanced open systems interconnection model for dealing with different data networks and
ensure that transmission takes place among them (Colin, Mathieu and Nakechbandi, 2016). This
signifies critical variation with other models, like in reference models definitions are associated
with physical objects within different layers and just the lowest ones. On the other hand, NOLI
opts for containerisation along with de-containerisation in top layer and in last two. This is liable
for uniting session and transport layers into one.
According to Pakawat Pupawibul (2015), SDN with OpenFlow is enabled for direct
manipulation with respect to forwarding plan associated with hubs, router or any other
networking devices. These methods depend on flow from protocols like OpenFlow which
operates in contrast with different networking devices such as MAC table, TCP/IP, etc. routing.
The emphasis within paper is laid on relationship that prevails in between distinct processes that
are associated with forward packets in case of IP address routing table with respect to OpenFlow
table (Banjar, Pupatwibul and Braun, 2015).
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As per Ammar Rayes (2016), paper specifies that it is critical to have large scale
networks due to various complexities related with this (Rayes, and Salam, 2017). OSI standards
are utilised to conduct networking tasks through which composite problems can be addressed.
As per Preeti Sinha (2017), the emphasis is made on security vulnerabilities in distinct
WSNs according different layers of OSI reference model (Sinha and et. al, 2017). There exist
few technical challenges that must be addressed carefully so that secured transmission can be
carried out.
According to Nitish Aggarwal (2014), the comparative analysis is being provided with
reference to TCP/IP as well as OSI reference model. The reference model illustrates way to
define the ways for communication (Aggarwal, Gupta and Saxena, 2019).
The literature review of different papers has been carried out in context of layered
reference models. they will assist within having adequate knowledge related with ways in which
transmission takes place by making use of different networking devices. It has been identified
that by making use of layered models within setting up networking devices to communicate with
one other will be easy as well as security concerns will also be taken into regards.
1.3 Formulate approach for documenting, execution along with testing of network addressing
related with addressing computer network in figure along with its illustration.
When networking project is done, it is important to ensure that documentation is carried
out in proper manner through which all the aspects are covered as well as in case of any kind of
problem there will be a reference. In this context, the essential entities related with this
comprises of determination of assets, analysing related security risks, security needs as well as
associated tradeoff, development of security plans, clear specification of procedures that will be
applied within security policies, development of technical implementation strategies, have buy-in
capacity from technical, managers and users, give training to users as well as employees. execute
technical strategies & security procedures, test the security aspects and update them if any case
of issue is identified and maintain security. In addition to this, network address translation will
be used that is liable for reassigning IP address space for carrying out any change within the
network address data in IP header related with peculiar data frame when they are sent over a
network.
3
networks due to various complexities related with this (Rayes, and Salam, 2017). OSI standards
are utilised to conduct networking tasks through which composite problems can be addressed.
As per Preeti Sinha (2017), the emphasis is made on security vulnerabilities in distinct
WSNs according different layers of OSI reference model (Sinha and et. al, 2017). There exist
few technical challenges that must be addressed carefully so that secured transmission can be
carried out.
According to Nitish Aggarwal (2014), the comparative analysis is being provided with
reference to TCP/IP as well as OSI reference model. The reference model illustrates way to
define the ways for communication (Aggarwal, Gupta and Saxena, 2019).
The literature review of different papers has been carried out in context of layered
reference models. they will assist within having adequate knowledge related with ways in which
transmission takes place by making use of different networking devices. It has been identified
that by making use of layered models within setting up networking devices to communicate with
one other will be easy as well as security concerns will also be taken into regards.
1.3 Formulate approach for documenting, execution along with testing of network addressing
related with addressing computer network in figure along with its illustration.
When networking project is done, it is important to ensure that documentation is carried
out in proper manner through which all the aspects are covered as well as in case of any kind of
problem there will be a reference. In this context, the essential entities related with this
comprises of determination of assets, analysing related security risks, security needs as well as
associated tradeoff, development of security plans, clear specification of procedures that will be
applied within security policies, development of technical implementation strategies, have buy-in
capacity from technical, managers and users, give training to users as well as employees. execute
technical strategies & security procedures, test the security aspects and update them if any case
of issue is identified and maintain security. In addition to this, network address translation will
be used that is liable for reassigning IP address space for carrying out any change within the
network address data in IP header related with peculiar data frame when they are sent over a
network.
3
1.4 Justify the approach for implementing along with testing network addressing for computer
network.
An example can be taken to understand this concept like in case inside host of
192.168.0.4/30 have to interact with 172.16.0.0/18 the data frames or packets will be sent via
NAT-enabled gateway router for having message transmission or interaction. The gateway router
will have details related with source IP address and within the table will look whether conditions
related with translation have been addressed or not. Gateway router is responsible to maintain
access control list through which host will be located that will lead to internal network
translation. Thus, inside IP address will further be converted within global IP address. It will be
stored in NAT table and gateway router through which message can be transmitted to
destination. In this manner, NAT will be executed as well testing of message will be carried out
by transmitting it to destination and ensure that any kind of alterations have not been done. Tis
being carried out by making use of referenced layer models for ensuring high levels of security.
Part 2
Figure out and assign different 4 IPv6 subnets by appending subnet ID with global routing prefix
that is being given and then document IPv6 subnets in table
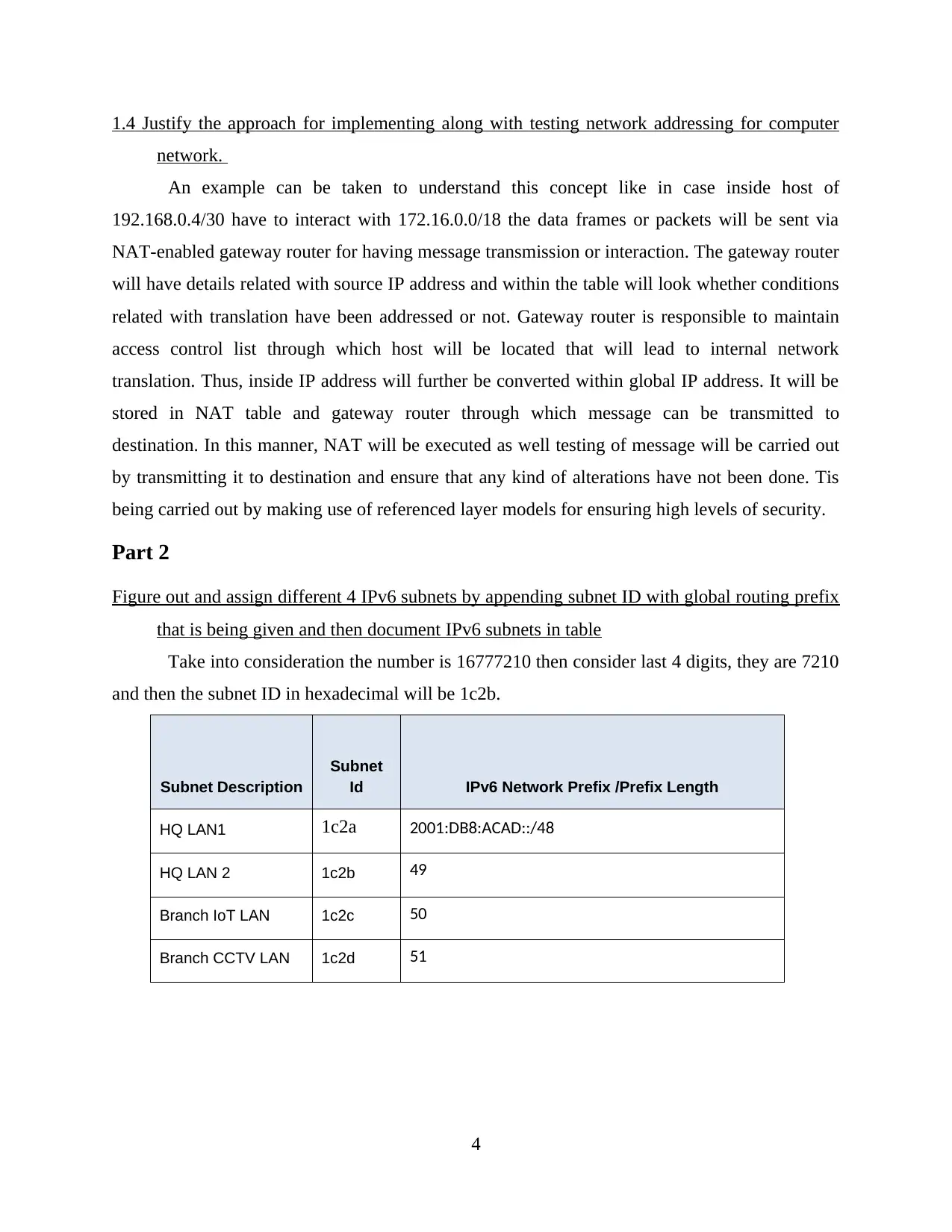
Take into consideration the number is 16777210 then consider last 4 digits, they are 7210
and then the subnet ID in hexadecimal will be 1c2b.
Subnet Description
Subnet
Id IPv6 Network Prefix /Prefix Length
HQ LAN1 1c2a 2001:DB8:ACAD::/48
HQ LAN 2 1c2b 49
Branch IoT LAN 1c2c 50
Branch CCTV LAN 1c2d 51
4
network.
An example can be taken to understand this concept like in case inside host of
192.168.0.4/30 have to interact with 172.16.0.0/18 the data frames or packets will be sent via
NAT-enabled gateway router for having message transmission or interaction. The gateway router
will have details related with source IP address and within the table will look whether conditions
related with translation have been addressed or not. Gateway router is responsible to maintain
access control list through which host will be located that will lead to internal network
translation. Thus, inside IP address will further be converted within global IP address. It will be
stored in NAT table and gateway router through which message can be transmitted to
destination. In this manner, NAT will be executed as well testing of message will be carried out
by transmitting it to destination and ensure that any kind of alterations have not been done. Tis
being carried out by making use of referenced layer models for ensuring high levels of security.
Part 2
Figure out and assign different 4 IPv6 subnets by appending subnet ID with global routing prefix
that is being given and then document IPv6 subnets in table
Take into consideration the number is 16777210 then consider last 4 digits, they are 7210
and then the subnet ID in hexadecimal will be 1c2b.
Subnet Description
Subnet
Id IPv6 Network Prefix /Prefix Length
HQ LAN1 1c2a 2001:DB8:ACAD::/48
HQ LAN 2 1c2b 49
Branch IoT LAN 1c2c 50
Branch CCTV LAN 1c2d 51
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
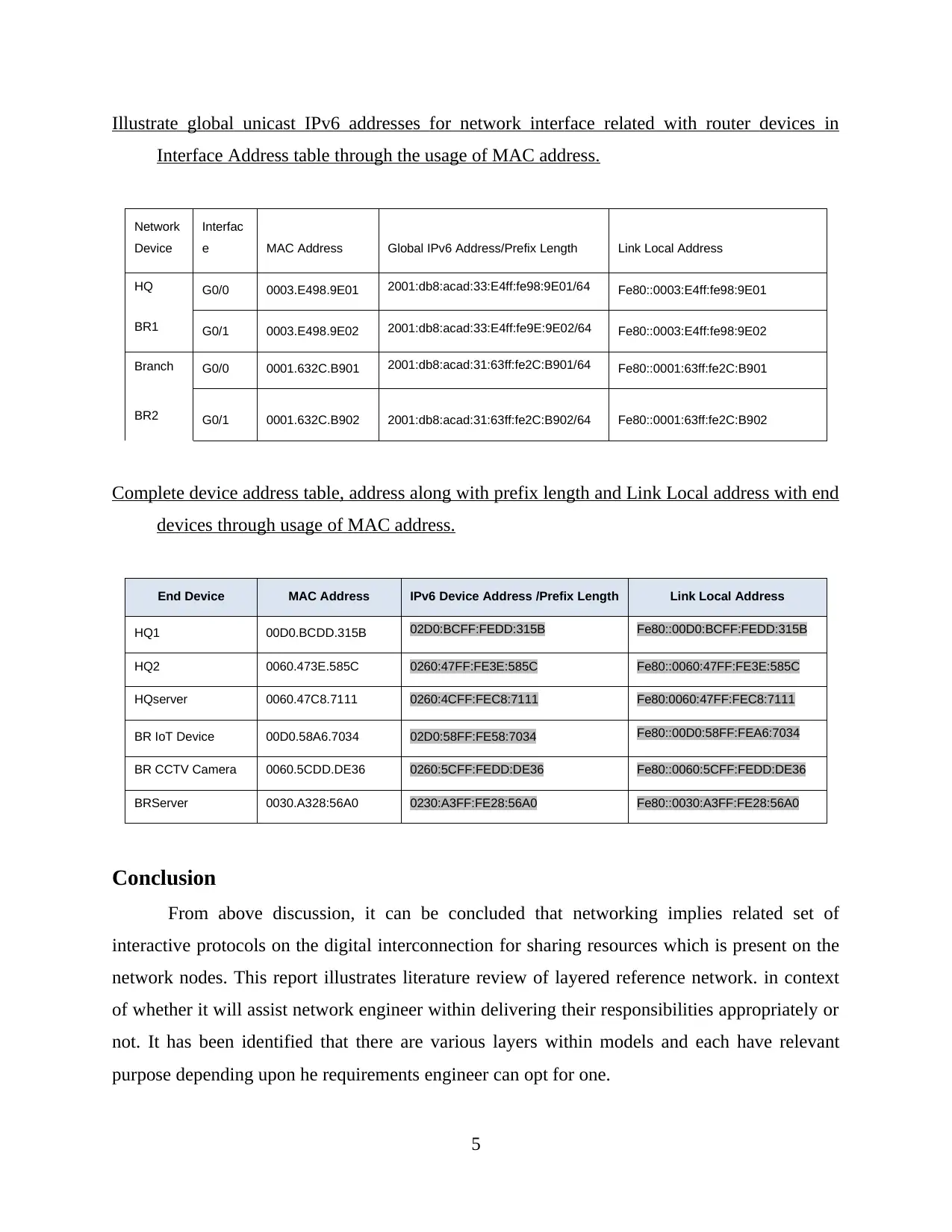
Illustrate global unicast IPv6 addresses for network interface related with router devices in
Interface Address table through the usage of MAC address.
Network
Device
Interfac
e MAC Address Global IPv6 Address/Prefix Length Link Local Address
HQ
BR1
G0/0 0003.E498.9E01 2001:db8:acad:33:E4ff:fe98:9E01/64 Fe80::0003:E4ff:fe98:9E01
G0/1 0003.E498.9E02 2001:db8:acad:33:E4ff:fe9E:9E02/64 Fe80::0003:E4ff:fe98:9E02
Branch G0/0 0001.632C.B901 2001:db8:acad:31:63ff:fe2C:B901/64 Fe80::0001:63ff:fe2C:B901
BR2 G0/1 0001.632C.B902 2001:db8:acad:31:63ff:fe2C:B902/64 Fe80::0001:63ff:fe2C:B902
Complete device address table, address along with prefix length and Link Local address with end
devices through usage of MAC address.
End Device MAC Address IPv6 Device Address /Prefix Length Link Local Address
HQ1 00D0.BCDD.315B 02D0:BCFF:FEDD:315B Fe80::00D0:BCFF:FEDD:315B
HQ2 0060.473E.585C 0260:47FF:FE3E:585C Fe80::0060:47FF:FE3E:585C
HQserver 0060.47C8.7111 0260:4CFF:FEC8:7111 Fe80:0060:47FF:FEC8:7111
BR IoT Device 00D0.58A6.7034 02D0:58FF:FE58:7034 Fe80::00D0:58FF:FEA6:7034
BR CCTV Camera 0060.5CDD.DE36 0260:5CFF:FEDD:DE36 Fe80::0060:5CFF:FEDD:DE36
BRServer 0030.A328:56A0 0230:A3FF:FE28:56A0 Fe80::0030:A3FF:FE28:56A0
Conclusion
From above discussion, it can be concluded that networking implies related set of
interactive protocols on the digital interconnection for sharing resources which is present on the
network nodes. This report illustrates literature review of layered reference network. in context
of whether it will assist network engineer within delivering their responsibilities appropriately or
not. It has been identified that there are various layers within models and each have relevant
purpose depending upon he requirements engineer can opt for one.
5
Interface Address table through the usage of MAC address.
Network
Device
Interfac
e MAC Address Global IPv6 Address/Prefix Length Link Local Address
HQ
BR1
G0/0 0003.E498.9E01 2001:db8:acad:33:E4ff:fe98:9E01/64 Fe80::0003:E4ff:fe98:9E01
G0/1 0003.E498.9E02 2001:db8:acad:33:E4ff:fe9E:9E02/64 Fe80::0003:E4ff:fe98:9E02
Branch G0/0 0001.632C.B901 2001:db8:acad:31:63ff:fe2C:B901/64 Fe80::0001:63ff:fe2C:B901
BR2 G0/1 0001.632C.B902 2001:db8:acad:31:63ff:fe2C:B902/64 Fe80::0001:63ff:fe2C:B902
Complete device address table, address along with prefix length and Link Local address with end
devices through usage of MAC address.
End Device MAC Address IPv6 Device Address /Prefix Length Link Local Address
HQ1 00D0.BCDD.315B 02D0:BCFF:FEDD:315B Fe80::00D0:BCFF:FEDD:315B
HQ2 0060.473E.585C 0260:47FF:FE3E:585C Fe80::0060:47FF:FE3E:585C
HQserver 0060.47C8.7111 0260:4CFF:FEC8:7111 Fe80:0060:47FF:FEC8:7111
BR IoT Device 00D0.58A6.7034 02D0:58FF:FE58:7034 Fe80::00D0:58FF:FEA6:7034
BR CCTV Camera 0060.5CDD.DE36 0260:5CFF:FEDD:DE36 Fe80::0060:5CFF:FEDD:DE36
BRServer 0030.A328:56A0 0230:A3FF:FE28:56A0 Fe80::0030:A3FF:FE28:56A0
Conclusion
From above discussion, it can be concluded that networking implies related set of
interactive protocols on the digital interconnection for sharing resources which is present on the
network nodes. This report illustrates literature review of layered reference network. in context
of whether it will assist network engineer within delivering their responsibilities appropriately or
not. It has been identified that there are various layers within models and each have relevant
purpose depending upon he requirements engineer can opt for one.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6

References
Books & Journals
7
Books & Journals
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





