Administering an Effective Network Environment Report - IT
VerifiedAdded on 2020/01/23
|12
|2984
|29
Report
AI Summary
This report examines the essential aspects of administering an effective network environment within an organization. It begins by outlining the creation and implementation of network services, focusing on Active Directory configuration and architecture to reflect the administrative scope of company employees. The report then delves into the critical evaluation of mail service administration within a Windows Server environment, proposing implementation methods and reflecting on the techniques used. Finally, it addresses the design and implementation of Distributed File System (DFS) administration, suggesting configurations for each department and appropriate folder permissions for robust data security. The report emphasizes the importance of security measures such as Group Policy Objects (GPOs), password policies, and proper naming conventions to ensure efficient network operations and data protection. The design is supported by evidence and literature to offer alternative solutions, ensuring a comprehensive understanding of network administration best practices.

Running HEAD: ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 1
ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT
Institution affiliation
Course
Student Name
Date
ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT
Institution affiliation
Course
Student Name
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 2
ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT
Introduction
LO1. Create network services administration and roll out, within a network
Network administration operations are associated with a computer network in an
organization for business purposes. Computer networks in an organization are monitored by a
network administrator who is a professional in the field of networking. The officers’ takes
control of different network operations required in the company to make sure all the staff and the
devices within the company are working effectively. Some operations done by network
administrator include network monitoring, expansion of the network, maintaining the network
and also configuring important updates required for the effective network operation. In order to
effect this activity, network tools and application soft wares are mostly utilized to make sure that
all the activities are running as required. Mail service system is one of the soft wares utilized in
most of the organizations to enable good mail delivery and communication.
Detail an Active Directory configuration and the architecture that reflects the
administrative scope of the company employees.
In order to deliver quality services in an organization, proper service administration needs
to be implemented. An organization with fifty employees is a big institution which requires
proper network setup and configuration. Active Directory is a Microsoft service for setting up
the network. The service was developed for Microsoft Windows servers operating systems. In
our scenario, the network administrator should set up a central domain management unit which
manages the network of the organization. It operates under a server called domain controller
which helps in the authentication and authorization of the company staff connected to the
ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT
Introduction
LO1. Create network services administration and roll out, within a network
Network administration operations are associated with a computer network in an
organization for business purposes. Computer networks in an organization are monitored by a
network administrator who is a professional in the field of networking. The officers’ takes
control of different network operations required in the company to make sure all the staff and the
devices within the company are working effectively. Some operations done by network
administrator include network monitoring, expansion of the network, maintaining the network
and also configuring important updates required for the effective network operation. In order to
effect this activity, network tools and application soft wares are mostly utilized to make sure that
all the activities are running as required. Mail service system is one of the soft wares utilized in
most of the organizations to enable good mail delivery and communication.
Detail an Active Directory configuration and the architecture that reflects the
administrative scope of the company employees.
In order to deliver quality services in an organization, proper service administration needs
to be implemented. An organization with fifty employees is a big institution which requires
proper network setup and configuration. Active Directory is a Microsoft service for setting up
the network. The service was developed for Microsoft Windows servers operating systems. In
our scenario, the network administrator should set up a central domain management unit which
manages the network of the organization. It operates under a server called domain controller
which helps in the authentication and authorization of the company staff connected to the

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 3
network. The active directory also manages the security of information passing through the
network in the company through a proper way of network monitoring.
The twelve staffs in the customer care desk should have different access permissions to
the information within the company from the sales department. Moreover, the active directory
service in the organization should be set up and configured in a way that IT support service team
have many privileges as compared to the management and marketing officials. Such
configurations ensure efficiency and security within the company. The active directory should be
set up in a way that it can store information concerning the number of members in the
organization, the connected devices, and the user’s credentials. Such configuration techniques
help in providing proper access rights for the information and data within the company. During
the configuration, the structure should be organized in a hierarchical manner such that there are
the parent and the child connection.
In its architecture, the network administrator should set up a network which is able to
achieve several objectives in the company. For instance, the active directory architecture should
be able to accommodate the available resources in the company, the connection between one
department and the other should be easy for flexibility during the administration and
maintenance periods. The company staff should also be able to access information such as
network. The active directory also manages the security of information passing through the
network in the company through a proper way of network monitoring.
The twelve staffs in the customer care desk should have different access permissions to
the information within the company from the sales department. Moreover, the active directory
service in the organization should be set up and configured in a way that IT support service team
have many privileges as compared to the management and marketing officials. Such
configurations ensure efficiency and security within the company. The active directory should be
set up in a way that it can store information concerning the number of members in the
organization, the connected devices, and the user’s credentials. Such configuration techniques
help in providing proper access rights for the information and data within the company. During
the configuration, the structure should be organized in a hierarchical manner such that there are
the parent and the child connection.
In its architecture, the network administrator should set up a network which is able to
achieve several objectives in the company. For instance, the active directory architecture should
be able to accommodate the available resources in the company, the connection between one
department and the other should be easy for flexibility during the administration and
maintenance periods. The company staff should also be able to access information such as
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 4
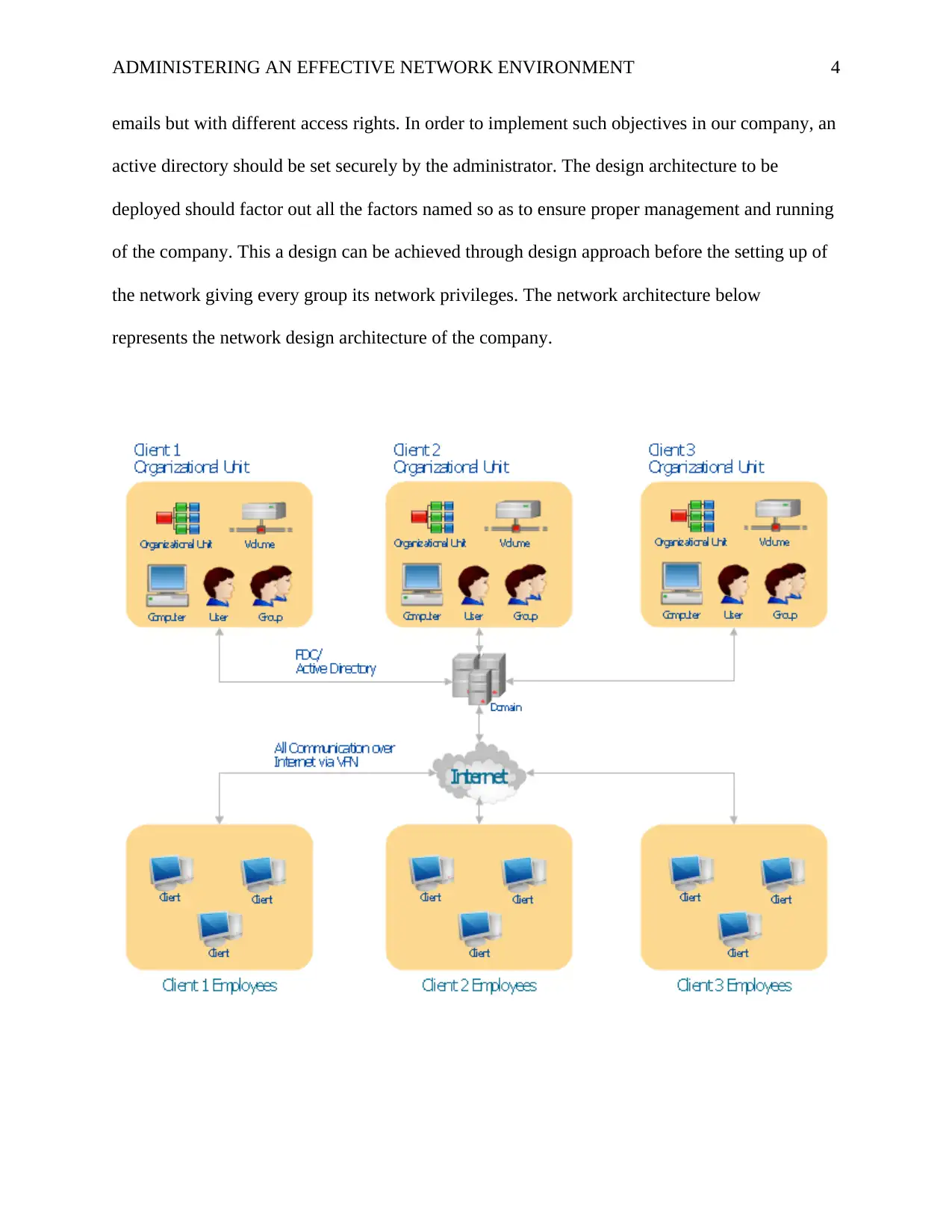
emails but with different access rights. In order to implement such objectives in our company, an
active directory should be set securely by the administrator. The design architecture to be
deployed should factor out all the factors named so as to ensure proper management and running
of the company. This a design can be achieved through design approach before the setting up of
the network giving every group its network privileges. The network architecture below
represents the network design architecture of the company.
emails but with different access rights. In order to implement such objectives in our company, an
active directory should be set securely by the administrator. The design architecture to be
deployed should factor out all the factors named so as to ensure proper management and running
of the company. This a design can be achieved through design approach before the setting up of
the network giving every group its network privileges. The network architecture below
represents the network design architecture of the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 5
Implementation of GPOs with password policies which reflect the hierarchical structure of
the company.
Organizations need to have a good security of information within the operation. When
using active directory service, a network administrator should utilize the active directory group
policy objects which help in managing active directory users within the company. In addition,
the available computers and departments are manned easily and more effectively with the use of
directory group policy objects. The administrator can opt for utilization of ADManager Plus tool
which assists in the creation of creation passwords for different users in the business.
The service is connected to the domain and manages the reporting of information
concerning the users connected to the network. The service assigns passwords in a hierarchical
manner depending on the security and the department an officer is working in. The advanced
software may contain pre-built Group Policy Reports which will facilitate the fetching of Group
Policy associated information swiftly.
The company should poses and hierarchical structure which starts with the Management,
followed by the marketing team, sales department, IT Support Services Customer Services and
the R and D unit. Such an order of group policy will ensure that all the information and
passwords set are effective for easy monitoring. Group policing can be enabled or disabled in
relation to the status of the staff. Administrators will be able to enable the required group policy
objects when the need arises. There are containers in the group policy service which hold the
information of the users and the devices in the network. A network administrator can add or
block a user from accessing some sensitive information within the company using group policy
approach. The advantage with the group policy services is that they are easy to set up and
Implementation of GPOs with password policies which reflect the hierarchical structure of
the company.
Organizations need to have a good security of information within the operation. When
using active directory service, a network administrator should utilize the active directory group
policy objects which help in managing active directory users within the company. In addition,
the available computers and departments are manned easily and more effectively with the use of
directory group policy objects. The administrator can opt for utilization of ADManager Plus tool
which assists in the creation of creation passwords for different users in the business.
The service is connected to the domain and manages the reporting of information
concerning the users connected to the network. The service assigns passwords in a hierarchical
manner depending on the security and the department an officer is working in. The advanced
software may contain pre-built Group Policy Reports which will facilitate the fetching of Group
Policy associated information swiftly.
The company should poses and hierarchical structure which starts with the Management,
followed by the marketing team, sales department, IT Support Services Customer Services and
the R and D unit. Such an order of group policy will ensure that all the information and
passwords set are effective for easy monitoring. Group policing can be enabled or disabled in
relation to the status of the staff. Administrators will be able to enable the required group policy
objects when the need arises. There are containers in the group policy service which hold the
information of the users and the devices in the network. A network administrator can add or
block a user from accessing some sensitive information within the company using group policy
approach. The advantage with the group policy services is that they are easy to set up and

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 6
flexible to accommodate many users and also to remove some officials. It should work
effectively with the active directory which is first installed for the purpose of monitoring the
communication.
Reflect upon the design, source evidence and literature to support your design and to offer
alternative solutions.
The design of an active directory within the group policy should implement security
factors in the company. When designing, the administrator should consider the domain service
passwords if they are strong enough to prevent malicious officials from changing the connection
and privileges. Smart tips required for security should include the administrators’ password,
account password, and domain controller security consideration. These three factors influence
the security in group policy implementation.
When designing the group policy and implementing the active directory, documentation
of the users and devices in the network is kept safe. A clear document will help in providing
evidence for the connection of a certain user in case criminal activity occurs in the company. In
addition, the design should have few administrators to avoid conflict. The administration activity
should start at the top management but the information technology staff should also have some
administrator privileges.
LO2. Critically evaluate Mail Service Administration within a Windows Server
environment
Propose how a mail server could be implemented within the network environment.
flexible to accommodate many users and also to remove some officials. It should work
effectively with the active directory which is first installed for the purpose of monitoring the
communication.
Reflect upon the design, source evidence and literature to support your design and to offer
alternative solutions.
The design of an active directory within the group policy should implement security
factors in the company. When designing, the administrator should consider the domain service
passwords if they are strong enough to prevent malicious officials from changing the connection
and privileges. Smart tips required for security should include the administrators’ password,
account password, and domain controller security consideration. These three factors influence
the security in group policy implementation.
When designing the group policy and implementing the active directory, documentation
of the users and devices in the network is kept safe. A clear document will help in providing
evidence for the connection of a certain user in case criminal activity occurs in the company. In
addition, the design should have few administrators to avoid conflict. The administration activity
should start at the top management but the information technology staff should also have some
administrator privileges.
LO2. Critically evaluate Mail Service Administration within a Windows Server
environment
Propose how a mail server could be implemented within the network environment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 7
In any organization, communication is relevant and most of the individuals use the email
within a connected network in the company. In order to implement proper communication of the
staff, the company administrator implements a service called mail server which supports
communication. It process emails using a certain protocol for the transfer of mails. Mail server
coordinates the exchange of emails among the clients and routes the mails to the intended
receivers. In order to implement a secure and appropriate mail communication, the administrator
needs to utilize the protocols such as POP and IMAP. These are mail transfer protocols which
facilitate efficient delivery of mails. The email sent or received has no clear interaction with the
server. However, an administrator has to utilize the Mail User Urgent protocol in the
implementation process so that mails can be delivered effectively and with no fail.
Evaluate and reflect upon the implementation method/s used.
Mail server implementation uses a protocol called simple mail transfer protocol which
facilitates the exchange of mails. User level client email applications utilize simple mail transfer
protocol for sending mail messages to the mail server. The server facilitates the relaying
operations to the receiver. On the other hand, the client POP3 or IMAP applications to retrieve
the mail message. For proper implementation, the network administrator should set up the
connection to the server to use port 25. Mail client submits the relayed mails to the server
through port 587. Security of the network should be considered for effective communication. As
a result, SMTP should be set to authenticate the users and the information they receive and send
through the email.
During the setup process, the administrator should ensure that communication and relay
of information flow as it is required. SMTP server flows through the server locating the recipient
In any organization, communication is relevant and most of the individuals use the email
within a connected network in the company. In order to implement proper communication of the
staff, the company administrator implements a service called mail server which supports
communication. It process emails using a certain protocol for the transfer of mails. Mail server
coordinates the exchange of emails among the clients and routes the mails to the intended
receivers. In order to implement a secure and appropriate mail communication, the administrator
needs to utilize the protocols such as POP and IMAP. These are mail transfer protocols which
facilitate efficient delivery of mails. The email sent or received has no clear interaction with the
server. However, an administrator has to utilize the Mail User Urgent protocol in the
implementation process so that mails can be delivered effectively and with no fail.
Evaluate and reflect upon the implementation method/s used.
Mail server implementation uses a protocol called simple mail transfer protocol which
facilitates the exchange of mails. User level client email applications utilize simple mail transfer
protocol for sending mail messages to the mail server. The server facilitates the relaying
operations to the receiver. On the other hand, the client POP3 or IMAP applications to retrieve
the mail message. For proper implementation, the network administrator should set up the
connection to the server to use port 25. Mail client submits the relayed mails to the server
through port 587. Security of the network should be considered for effective communication. As
a result, SMTP should be set to authenticate the users and the information they receive and send
through the email.
During the setup process, the administrator should ensure that communication and relay
of information flow as it is required. SMTP server flows through the server locating the recipient
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 8
using the domain name. The administrator matches the domain names for easy remembering and
also for easy delivery of mails. With simpler names for the users and the server, the SMTP server
locates the recipient easily and transfer the mail to the indented recipient. However, the naming
of the domain names should be unique to ensure that they represent a unique address.
Post Office Protocol servers should be set during the implementation process to ensure
the mails are received. It is relevant for the company to purchase the new POP technology which
is represented by digit ‘3’. The protocol has all mails accounts for the users and devices
connected to the network. With such consideration, it will easy the process of monitoring and
maintenance of the network in the organization. The organization may grow big and increase the
number of employees. As a result, the network administrator should map the mail account to a
specific username and password combined. Proper naming facilitates easy remembering even for
the staff working in the marketing department. Moreover, proper naming of devices and users in
the mail server allows easy addition of new users to the system. Thus the mail server should be
made scalable.
LO3. Design and implement Distributed File System Administration to a given scenario.
Propose a DFS configuration for each department using a naming convention.
During the implementation of the network system, a network administrator should
consider employing the Distributed file system server to allow the organization organize several
distributed SMB file sharing within the distributed system. Distributed file server offers location
transparency besides redundancy to increase information availability in case of network failure
or even heavy load. It allows sharing in multiple various localities to be rationally grouped in a
single folder of distributed file system. Microsoft distributed file system is convenient to use and
using the domain name. The administrator matches the domain names for easy remembering and
also for easy delivery of mails. With simpler names for the users and the server, the SMTP server
locates the recipient easily and transfer the mail to the indented recipient. However, the naming
of the domain names should be unique to ensure that they represent a unique address.
Post Office Protocol servers should be set during the implementation process to ensure
the mails are received. It is relevant for the company to purchase the new POP technology which
is represented by digit ‘3’. The protocol has all mails accounts for the users and devices
connected to the network. With such consideration, it will easy the process of monitoring and
maintenance of the network in the organization. The organization may grow big and increase the
number of employees. As a result, the network administrator should map the mail account to a
specific username and password combined. Proper naming facilitates easy remembering even for
the staff working in the marketing department. Moreover, proper naming of devices and users in
the mail server allows easy addition of new users to the system. Thus the mail server should be
made scalable.
LO3. Design and implement Distributed File System Administration to a given scenario.
Propose a DFS configuration for each department using a naming convention.
During the implementation of the network system, a network administrator should
consider employing the Distributed file system server to allow the organization organize several
distributed SMB file sharing within the distributed system. Distributed file server offers location
transparency besides redundancy to increase information availability in case of network failure
or even heavy load. It allows sharing in multiple various localities to be rationally grouped in a
single folder of distributed file system. Microsoft distributed file system is convenient to use and

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT 9
implement in an organization with different departments. For proper remembering, good naming
conventions should be utilized for each department.
In the marketing department, the administrator will utilize the distributed file server to
store the information required in the department. This server can use a simple namespace
components even without the use of the distributed file services file replication technique.
However, the administrator may decide to utilize file replication between the servers. A
networker professional should utilize two different mechanisms of implementing distributed file
services. Standalone distributed file services enable the user to utilize namespace and allow the
distributed file services root the only works in a local computer.
For the sales and customer services units, it is relevant that they use standalone
distributed system because it can only be accessed from the computer of installation. Only a
single computer poses the data and the information related to the department operations. For
such a case, all the information stored in the marketing department computer or server will only
be accessible by the persons in the unit and those with access rights to the data.
Information and Technology department in addition to R&D and management office
should implement the use of Domain-based distributed file services namespace. Such system
store information in an active directory. A proper namespace root is accessible through a domain
id. The Information and technology office does not require a lot of data though it is very
sensitive, for such cases, the. Network professional will need to use domain based distributed file
services namespace.
Suggest appropriate permissions to folder structures for data security.
implement in an organization with different departments. For proper remembering, good naming
conventions should be utilized for each department.
In the marketing department, the administrator will utilize the distributed file server to
store the information required in the department. This server can use a simple namespace
components even without the use of the distributed file services file replication technique.
However, the administrator may decide to utilize file replication between the servers. A
networker professional should utilize two different mechanisms of implementing distributed file
services. Standalone distributed file services enable the user to utilize namespace and allow the
distributed file services root the only works in a local computer.
For the sales and customer services units, it is relevant that they use standalone
distributed system because it can only be accessed from the computer of installation. Only a
single computer poses the data and the information related to the department operations. For
such a case, all the information stored in the marketing department computer or server will only
be accessible by the persons in the unit and those with access rights to the data.
Information and Technology department in addition to R&D and management office
should implement the use of Domain-based distributed file services namespace. Such system
store information in an active directory. A proper namespace root is accessible through a domain
id. The Information and technology office does not require a lot of data though it is very
sensitive, for such cases, the. Network professional will need to use domain based distributed file
services namespace.
Suggest appropriate permissions to folder structures for data security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT
10
The process of file system development requires strong security techniques to facilitate
proper identifications of information in the server. Distributed file server enables folder
management technique for the files stored on the server for different departments. Folders of the
NTFS structure can be protected safely in the distributed file system and ensure access only by
the authorized users. Also, it allows the protection of the NTFS file structure and prevents data
destruction. The folders can be managed through the use of PowerShell scripts. Such techniques
provide appropriate permission for the files stored on the server.
The network administrator should utilize the distributed files system and make some
department files non-inheritable. Such an operation prevents breach to the folders. The NTFS
folder structure can work effectively by monitoring the Windows NTFS authorizations on the
folder. Microsoft developed a new ADManger Plus tool for giving permissions to folders stored
in a server. It is relevant for the administrator to incorporate the ADManger Plus tool to monitor
and maintain different folder structures stored in the computer server.
A company can suggest the use of ADManager Plus for providing reports to the active
directory groups folders. Those folders of the structure of NTFS, use the NTFS permissions
technique for folders to report lists of all users in a certain group. The associated right to use
control accesses clearly indicate the level of access a user/group has a folder and also specifies
the inheritable permissions if they are set. Such directory permission report can be utilized as
NTFS permissions analyzer. It helps the administrator to ensure freedom access delivery to
specific folders. As a result, administrators can secure different file types for various departments
by monitoring NTFS security authorizations on folders.
10
The process of file system development requires strong security techniques to facilitate
proper identifications of information in the server. Distributed file server enables folder
management technique for the files stored on the server for different departments. Folders of the
NTFS structure can be protected safely in the distributed file system and ensure access only by
the authorized users. Also, it allows the protection of the NTFS file structure and prevents data
destruction. The folders can be managed through the use of PowerShell scripts. Such techniques
provide appropriate permission for the files stored on the server.
The network administrator should utilize the distributed files system and make some
department files non-inheritable. Such an operation prevents breach to the folders. The NTFS
folder structure can work effectively by monitoring the Windows NTFS authorizations on the
folder. Microsoft developed a new ADManger Plus tool for giving permissions to folders stored
in a server. It is relevant for the administrator to incorporate the ADManger Plus tool to monitor
and maintain different folder structures stored in the computer server.
A company can suggest the use of ADManager Plus for providing reports to the active
directory groups folders. Those folders of the structure of NTFS, use the NTFS permissions
technique for folders to report lists of all users in a certain group. The associated right to use
control accesses clearly indicate the level of access a user/group has a folder and also specifies
the inheritable permissions if they are set. Such directory permission report can be utilized as
NTFS permissions analyzer. It helps the administrator to ensure freedom access delivery to
specific folders. As a result, administrators can secure different file types for various departments
by monitoring NTFS security authorizations on folders.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT
11
Additionally, the NTFS folder structure can be maintained through the use of active
directory password management system. The security codes set for different files can effectively
maintain the files securely and ensure all the files are stored safely. A network professional can
set and reset passwords from a unique web-based console. In such situations, the administrator
does not compromise the security of AD.
Evaluate the effectiveness of your security suggestion and provide alternative methods.
The use of ADManager Plus for the provision of reports help the administrator to keep a
correct record of the users in the network. The system ensures proper report is generated on all
the connected devices and users in the network. Moreover, an administrator can decide to utilize
active directory clean up technique to remove the inactive, unwanted objects in the active
directory. Such an operation make sure that the folders are secure and cannot be altered by any
malicious user.
Active directory automation can also be effected to secure the folders in the active
directory. The AD can be critically be automated and the file structure of NTFS remain safe
unaltered. Network administrators should maintain the security of information stored in the
company databases by use of relevant technologies. When information is secure the department
officials will only be able to access what is relevant to them. Access to information by
unauthorized personnel will be eliminated
11
Additionally, the NTFS folder structure can be maintained through the use of active
directory password management system. The security codes set for different files can effectively
maintain the files securely and ensure all the files are stored safely. A network professional can
set and reset passwords from a unique web-based console. In such situations, the administrator
does not compromise the security of AD.
Evaluate the effectiveness of your security suggestion and provide alternative methods.
The use of ADManager Plus for the provision of reports help the administrator to keep a
correct record of the users in the network. The system ensures proper report is generated on all
the connected devices and users in the network. Moreover, an administrator can decide to utilize
active directory clean up technique to remove the inactive, unwanted objects in the active
directory. Such an operation make sure that the folders are secure and cannot be altered by any
malicious user.
Active directory automation can also be effected to secure the folders in the active
directory. The AD can be critically be automated and the file structure of NTFS remain safe
unaltered. Network administrators should maintain the security of information stored in the
company databases by use of relevant technologies. When information is secure the department
officials will only be able to access what is relevant to them. Access to information by
unauthorized personnel will be eliminated

ADMINISTERING AN EFFECTIVE NETWORK ENVIRONMENT
12
References
Yemini, Y., Konstantinou, A. V., & Florissi, D. (2000). NESTOR: an architecture for network
self-management and organization. IEEE Journal on Selected Areas in Communications, 18(5),
758-766.
Border, C. (2007, March). The development and deployment of a multi-user, remote access
virtualization system for networking, security, and system administration classes. In ACM
SIGCSE Bulletin (Vol. 39, No. 1, pp. 576-580). ACM.
Brady Jr, K. A., Yi, J. K. M., Weimholt, A. W., Tsaur, J. F., & Norton, L. K. (2005). U.S. Patent
No. 6,973,479. Washington, DC: U.S. Patent and Trademark Office.
Zhang, D. G., & Zhang, X. D. (2012). Design and implementation of embedded un-interruptible
power supply system (EUPSS) for web-based mobile application. Enterprise Information
Systems, 6(4), 473-489.
Hamlen, K. W., & Thuraisingham, B. (2013). Data security services, solutions and standards for
outsourcing. Computer Standards & Interfaces, 35(1), 1-5.
Edge, C., & O’Donnell, D. (2016). File System Permissions. In Enterprise Mac Security (pp. 83-
114). Apress.
Sherman, J., Sherman, C. H., Cordover, J., & Singh, V. (2015). U.S. Patent No. 20,150,319,157.
Washington, DC: U.S. Patent and Trademark Office.
12
References
Yemini, Y., Konstantinou, A. V., & Florissi, D. (2000). NESTOR: an architecture for network
self-management and organization. IEEE Journal on Selected Areas in Communications, 18(5),
758-766.
Border, C. (2007, March). The development and deployment of a multi-user, remote access
virtualization system for networking, security, and system administration classes. In ACM
SIGCSE Bulletin (Vol. 39, No. 1, pp. 576-580). ACM.
Brady Jr, K. A., Yi, J. K. M., Weimholt, A. W., Tsaur, J. F., & Norton, L. K. (2005). U.S. Patent
No. 6,973,479. Washington, DC: U.S. Patent and Trademark Office.
Zhang, D. G., & Zhang, X. D. (2012). Design and implementation of embedded un-interruptible
power supply system (EUPSS) for web-based mobile application. Enterprise Information
Systems, 6(4), 473-489.
Hamlen, K. W., & Thuraisingham, B. (2013). Data security services, solutions and standards for
outsourcing. Computer Standards & Interfaces, 35(1), 1-5.
Edge, C., & O’Donnell, D. (2016). File System Permissions. In Enterprise Mac Security (pp. 83-
114). Apress.
Sherman, J., Sherman, C. H., Cordover, J., & Singh, V. (2015). U.S. Patent No. 20,150,319,157.
Washington, DC: U.S. Patent and Trademark Office.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





