MN503 Overview of Internetworking: Network Requirement Analysis
VerifiedAdded on 2023/04/04
|10
|1317
|337
Report
AI Summary
This report provides a network requirement analysis and plan for a financial and insurance company, focusing on organizational growth integration, network efficiency, IP address management, high uptime, and redundant link management. It details functional and non-functional requirements, including network performance enhancement, effective communication, scalable configuration, site surveys, feasibility studies, floor plans, and topology identification. The report includes an IP addressing subnet plan, network topology diagram, switch and router configurations, access point and server configuration guidelines, and security configurations with VLAN implementation for data protection. The conclusion emphasizes the importance of resource identification and security measures, such as access control and separate VLANs for print servers and guest users, to ensure network efficiency and security. References to various research papers are also included to support the analysis and design.

Network requirement analysis and plan
Name of the Student
Name of the University
Author’s Note
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Scope
The network is designed for financial and insurance company and foe this project, the following project
scope is identified:
To identify need for organizational growth and integrates it with the network design while
following the organizational structure
Increase network efficiency through division of IP address into smaller subnet for increasing
capacity of the network to deal with network traffic
To minimize waste of IP address though division of IP address and allow for migrating IP address
To provide high uptime for the network and maintain that even when traffic in the network is
high
To ensure appropriate management of redundant links in the network so that data is properly
sent to the destination host of the network and thus improving overall network structure of the
organization
Project Requirement
Functional Requirement
● Increasing network performance while minimizing the chances of jitters and loss of data packets
and improving traffic congestion of the network as well
● Ensuring effective communication through the network and for doing this data packets are
divided in various communication path to ensure that it reaches to the destination host of the
network
● Ensuring effective configuration for the network while providing space for allocating new IP
address for increasing scalability of the network
● Configure network according to the IP address plan
Non Functional Requirement
● To conduct survey at site to identify to conduct survey at site to identify design requirement and
needs
● Conduct feasibility study for hardware and budget estimation
The network is designed for financial and insurance company and foe this project, the following project
scope is identified:
To identify need for organizational growth and integrates it with the network design while
following the organizational structure
Increase network efficiency through division of IP address into smaller subnet for increasing
capacity of the network to deal with network traffic
To minimize waste of IP address though division of IP address and allow for migrating IP address
To provide high uptime for the network and maintain that even when traffic in the network is
high
To ensure appropriate management of redundant links in the network so that data is properly
sent to the destination host of the network and thus improving overall network structure of the
organization
Project Requirement
Functional Requirement
● Increasing network performance while minimizing the chances of jitters and loss of data packets
and improving traffic congestion of the network as well
● Ensuring effective communication through the network and for doing this data packets are
divided in various communication path to ensure that it reaches to the destination host of the
network
● Ensuring effective configuration for the network while providing space for allocating new IP
address for increasing scalability of the network
● Configure network according to the IP address plan
Non Functional Requirement
● To conduct survey at site to identify to conduct survey at site to identify design requirement and
needs
● Conduct feasibility study for hardware and budget estimation
● Prepare floor plans for installation of network devices and various equipment required for
network design
● Identify network topology according to the organizational structure and requirements for
designing network properly
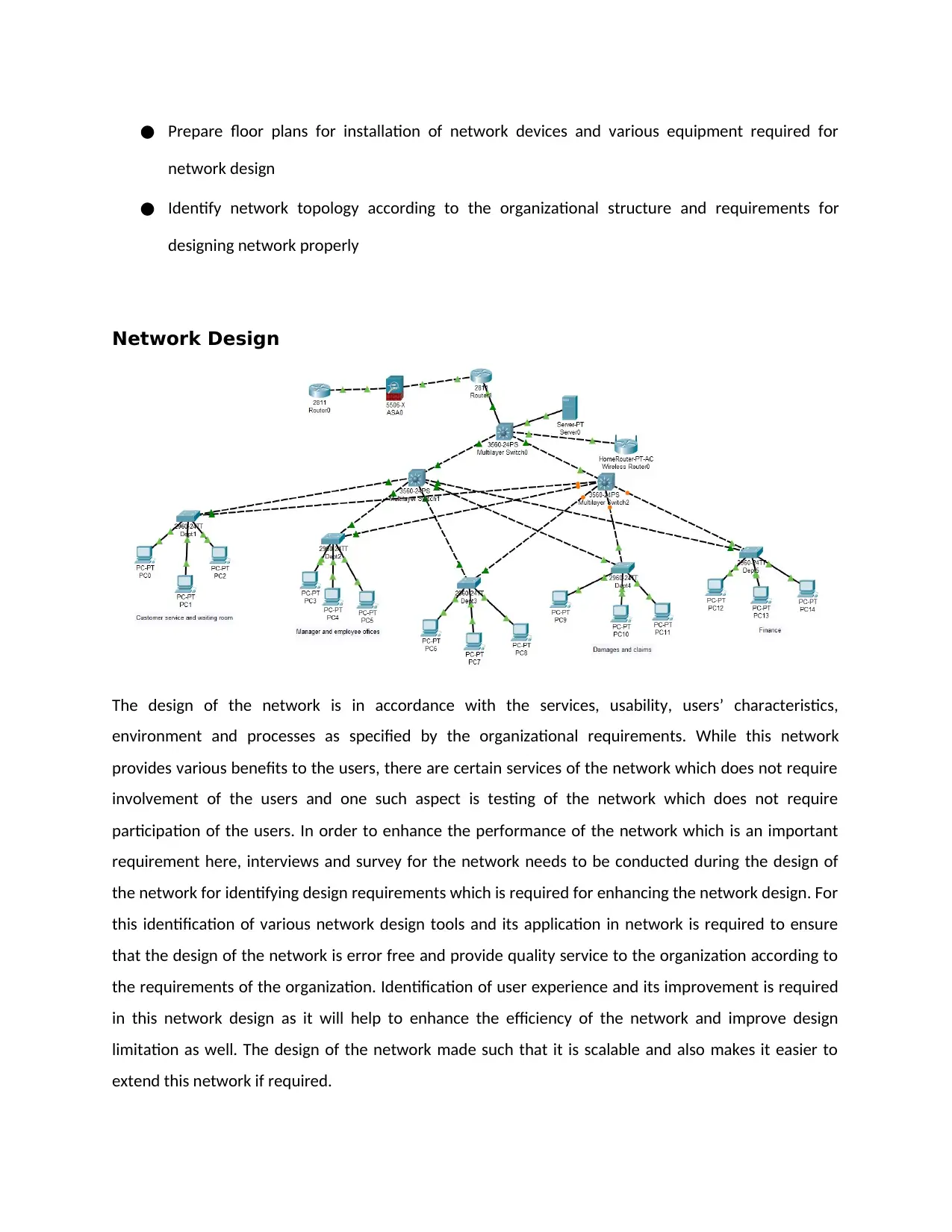
Network Design
The design of the network is in accordance with the services, usability, users’ characteristics,
environment and processes as specified by the organizational requirements. While this network
provides various benefits to the users, there are certain services of the network which does not require
involvement of the users and one such aspect is testing of the network which does not require
participation of the users. In order to enhance the performance of the network which is an important
requirement here, interviews and survey for the network needs to be conducted during the design of
the network for identifying design requirements which is required for enhancing the network design. For
this identification of various network design tools and its application in network is required to ensure
that the design of the network is error free and provide quality service to the organization according to
the requirements of the organization. Identification of user experience and its improvement is required
in this network design as it will help to enhance the efficiency of the network and improve design
limitation as well. The design of the network made such that it is scalable and also makes it easier to
extend this network if required.
network design
● Identify network topology according to the organizational structure and requirements for
designing network properly
Network Design
The design of the network is in accordance with the services, usability, users’ characteristics,
environment and processes as specified by the organizational requirements. While this network
provides various benefits to the users, there are certain services of the network which does not require
involvement of the users and one such aspect is testing of the network which does not require
participation of the users. In order to enhance the performance of the network which is an important
requirement here, interviews and survey for the network needs to be conducted during the design of
the network for identifying design requirements which is required for enhancing the network design. For
this identification of various network design tools and its application in network is required to ensure
that the design of the network is error free and provide quality service to the organization according to
the requirements of the organization. Identification of user experience and its improvement is required
in this network design as it will help to enhance the efficiency of the network and improve design
limitation as well. The design of the network made such that it is scalable and also makes it easier to
extend this network if required.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
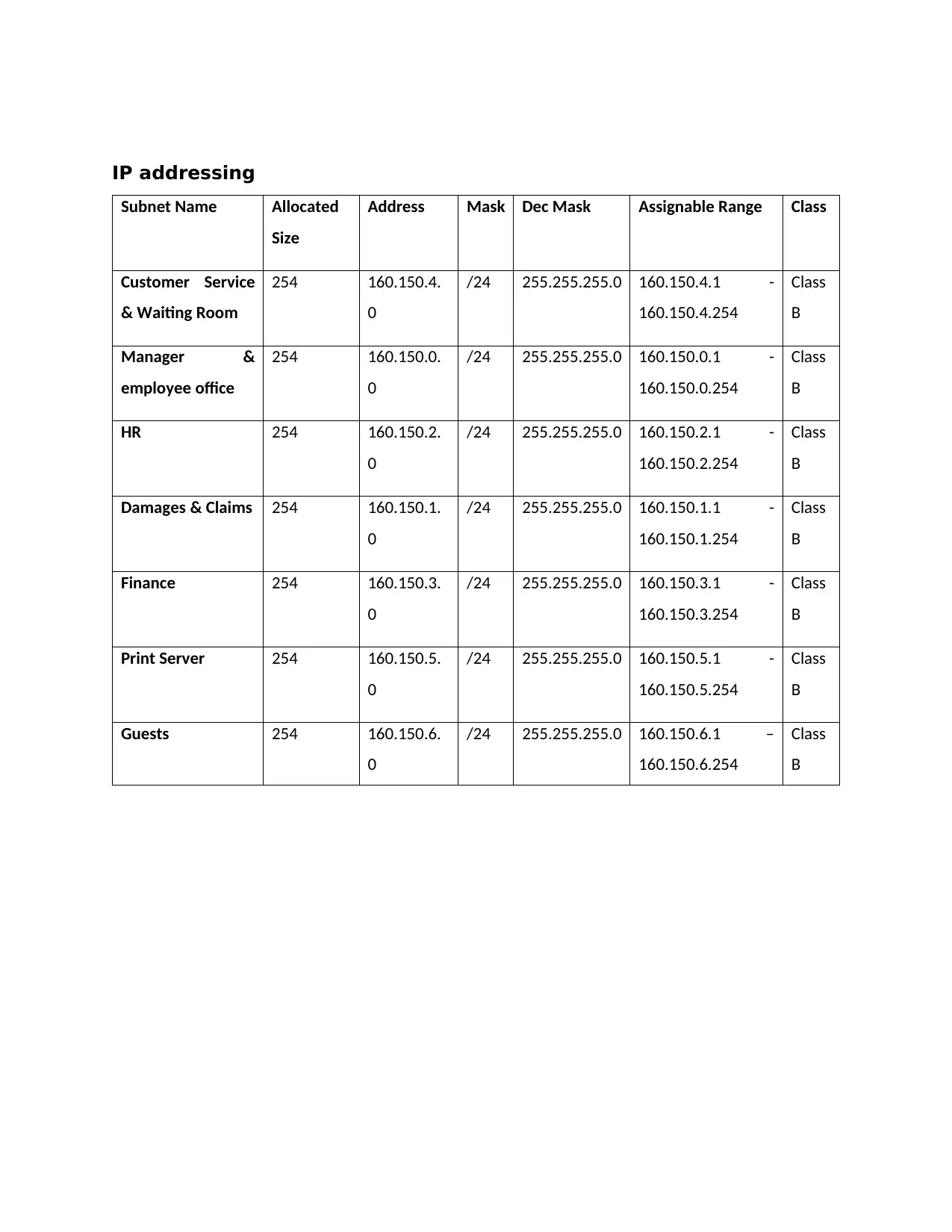
IP addressing
Subnet Name Allocated
Size
Address Mask Dec Mask Assignable Range Class
Customer Service
& Waiting Room
254 160.150.4.
0
/24 255.255.255.0 160.150.4.1 -
160.150.4.254
Class
B
Manager &
employee office
254 160.150.0.
0
/24 255.255.255.0 160.150.0.1 -
160.150.0.254
Class
B
HR 254 160.150.2.
0
/24 255.255.255.0 160.150.2.1 -
160.150.2.254
Class
B
Damages & Claims 254 160.150.1.
0
/24 255.255.255.0 160.150.1.1 -
160.150.1.254
Class
B
Finance 254 160.150.3.
0
/24 255.255.255.0 160.150.3.1 -
160.150.3.254
Class
B
Print Server 254 160.150.5.
0
/24 255.255.255.0 160.150.5.1 -
160.150.5.254
Class
B
Guests 254 160.150.6.
0
/24 255.255.255.0 160.150.6.1 –
160.150.6.254
Class
B
Subnet Name Allocated
Size
Address Mask Dec Mask Assignable Range Class
Customer Service
& Waiting Room
254 160.150.4.
0
/24 255.255.255.0 160.150.4.1 -
160.150.4.254
Class
B
Manager &
employee office
254 160.150.0.
0
/24 255.255.255.0 160.150.0.1 -
160.150.0.254
Class
B
HR 254 160.150.2.
0
/24 255.255.255.0 160.150.2.1 -
160.150.2.254
Class
B
Damages & Claims 254 160.150.1.
0
/24 255.255.255.0 160.150.1.1 -
160.150.1.254
Class
B
Finance 254 160.150.3.
0
/24 255.255.255.0 160.150.3.1 -
160.150.3.254
Class
B
Print Server 254 160.150.5.
0
/24 255.255.255.0 160.150.5.1 -
160.150.5.254
Class
B
Guests 254 160.150.6.
0
/24 255.255.255.0 160.150.6.1 –
160.150.6.254
Class
B
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
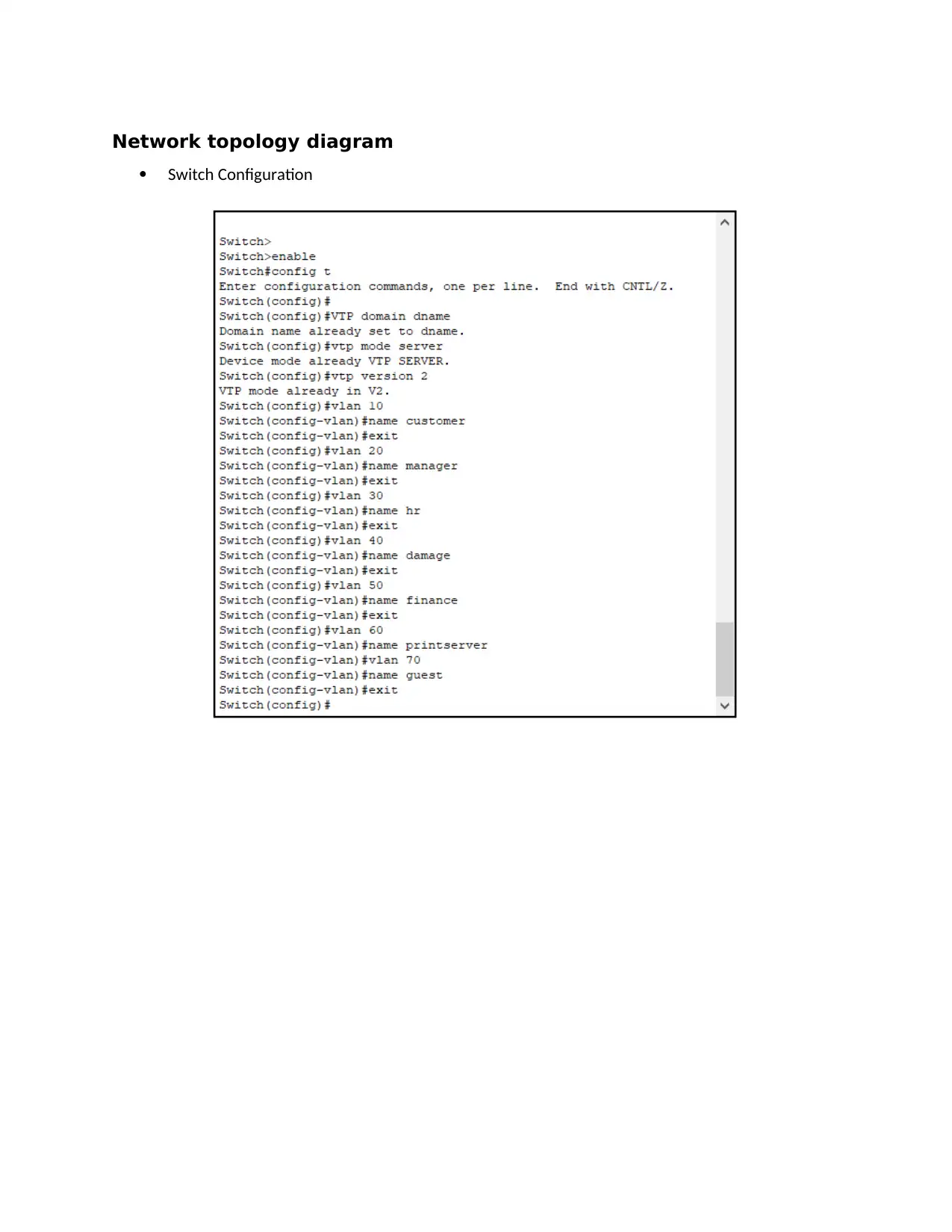
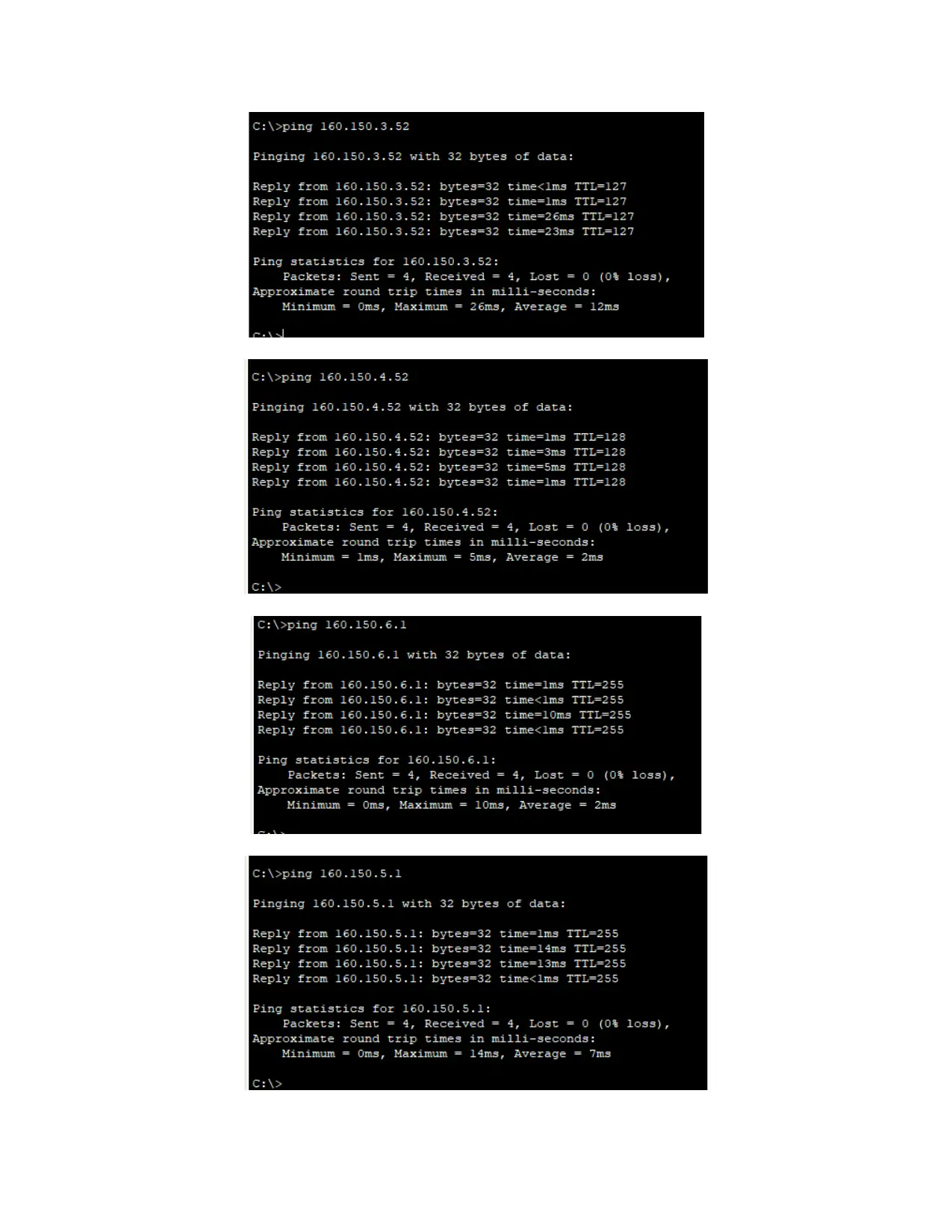
Network topology diagram
Switch Configuration
Switch Configuration

Router Configuration
Access Point and Server Configuration Guidelines – In order to ensure security of the network, it is
required to develop a proper network policy and for developing a network policy it is important to
consult with appropriate authority in the organization. This policy is required to provide detailed
guidelines and rules for accessing network and network related services. It will provide guidelines for
various department of the organization. This guideline will also provide rules to transfer data and
Access Point and Server Configuration Guidelines – In order to ensure security of the network, it is
required to develop a proper network policy and for developing a network policy it is important to
consult with appropriate authority in the organization. This policy is required to provide detailed
guidelines and rules for accessing network and network related services. It will provide guidelines for
various department of the organization. This guideline will also provide rules to transfer data and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

manage access to those data. This guidelines also provide context for deploying various applications that
requires access to this network. It will make sure that access to the network for various related services
and applications is consistent and effective.
Security Configuration - The routers that have been integrated with the network also requires security
control as it has significant impact on the overall security of the network. Proper security control of the
router ensure that access to the network and the data stored in the network server is authorized and
authenticated and no department of the organization is able to exploit the network through illegal
access. In this regard VLAN of all the five departments are configured through network switches and this
is done for protection of internal data from illegal access. However, one important requirement for data
security is to monitor network activities properly and for this IDS and IPS system are installed. In this
context separate VLANs are created for both print server and guest users and this ensures that no gust
users are able to access internal network infrastructure of the organization.
Demonstration
requires access to this network. It will make sure that access to the network for various related services
and applications is consistent and effective.
Security Configuration - The routers that have been integrated with the network also requires security
control as it has significant impact on the overall security of the network. Proper security control of the
router ensure that access to the network and the data stored in the network server is authorized and
authenticated and no department of the organization is able to exploit the network through illegal
access. In this regard VLAN of all the five departments are configured through network switches and this
is done for protection of internal data from illegal access. However, one important requirement for data
security is to monitor network activities properly and for this IDS and IPS system are installed. In this
context separate VLANs are created for both print server and guest users and this ensures that no gust
users are able to access internal network infrastructure of the organization.
Demonstration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
While designing network infrastructure for the organization, it is important to identify organizational
resources. Identification of resources are required for designing network that is consistent with
organizational requirements, otherwise network design will not be proper in organizational context.
Identification of resources will also help in defining budget and thus providing assistance in defining
budget for the network design. Security of the network is another important aspect that requires proper
assessment and it is one of the prime importance in any network design. In order to ensure security of
the network, access control has been integrated with the network and VLANs have been created as well
and this allows to connect all of the five departments to the network and communicate through the
network. To avoid illegal access to the network, separate VLANs are considered for print server and
guest users and this will ensure that guest users are not allowed to access internal network of the
organization. Hence this network design has managed efficiency and security of the network properly.
While designing network infrastructure for the organization, it is important to identify organizational
resources. Identification of resources are required for designing network that is consistent with
organizational requirements, otherwise network design will not be proper in organizational context.
Identification of resources will also help in defining budget and thus providing assistance in defining
budget for the network design. Security of the network is another important aspect that requires proper
assessment and it is one of the prime importance in any network design. In order to ensure security of
the network, access control has been integrated with the network and VLANs have been created as well
and this allows to connect all of the five departments to the network and communicate through the
network. To avoid illegal access to the network, separate VLANs are considered for print server and
guest users and this will ensure that guest users are not allowed to access internal network of the
organization. Hence this network design has managed efficiency and security of the network properly.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Bibliography
[1]. Fogel, A., Fung, S., Pedrosa, L., Walraed-Sullivan, M., Govindan, R., Mahajan, R. and Millstein, T. A
general approach to network configuration analysis. In 12th {USENIX} Symposium on Networked Systems
Design and Implementation ({NSDI} 15) (pp. 469-483). , 2015.
[2]. Beckett, R., Gupta, A., Mahajan, R. and Walker, D. A general approach to network configuration
verification. In Proceedings of the Conference of the ACM Special Interest Group on Data
Communication (pp. 155-168). ACM. , 2017, August.
[3]. Nakagawa, Y., Lee, C., Hyoudou, K., Kobayashi, S., Shiraki, O., Tanaka, J. and Ishihara, T. Dynamic
virtual network configuration between containers using physical switch functions for NFV infrastructure.
In 2015 IEEE Conference on Network Function Virtualization and Software Defined Network (NFV-
SDN) (pp. 156-162). IEEE. , 2015, November.
[4]. Yang, Q., Ren, H., Zhao, G. and Zhang, H. Automatic Configuration Method of Smart Substation
Process Layer Network. In 2017 2nd International Conference on Electrical, Control and Automation
Engineering (ECAE 2017). Atlantis Press. , 2017, December.
[5]. Chandramouli, R. and Chandramouli, R. Secure virtual network configuration for virtual machine
(vm) protection. NIST Special Publication, 800, p.125B. , 2016.
[6]. Addis, B., Belabed, D., Bouet, M. and Secci, S. Virtual network functions placement and routing
optimization. In 2015 IEEE 4th International Conference on Cloud Networking (CloudNet) (pp. 171-177).
IEEE. , 2015, October.
[7]. Balakumar, N. and Prabhu, B. Evaluation of Quality in Network and Interoperable Connectivity
between IP Networks. International Journal of Current Engineering and Scientific Research
(IJCESR), 3(9). , 2016.
[8]. Jevremovic, A., Shimic, G., Veinovic, M. and Ristic, N. IP Addressing: Problem-Based Learning
Approach on Computer Networks. IEEE Transactions on Learning Technologies, 10(3), pp.367-378. ,
2016.
[1]. Fogel, A., Fung, S., Pedrosa, L., Walraed-Sullivan, M., Govindan, R., Mahajan, R. and Millstein, T. A
general approach to network configuration analysis. In 12th {USENIX} Symposium on Networked Systems
Design and Implementation ({NSDI} 15) (pp. 469-483). , 2015.
[2]. Beckett, R., Gupta, A., Mahajan, R. and Walker, D. A general approach to network configuration
verification. In Proceedings of the Conference of the ACM Special Interest Group on Data
Communication (pp. 155-168). ACM. , 2017, August.
[3]. Nakagawa, Y., Lee, C., Hyoudou, K., Kobayashi, S., Shiraki, O., Tanaka, J. and Ishihara, T. Dynamic
virtual network configuration between containers using physical switch functions for NFV infrastructure.
In 2015 IEEE Conference on Network Function Virtualization and Software Defined Network (NFV-
SDN) (pp. 156-162). IEEE. , 2015, November.
[4]. Yang, Q., Ren, H., Zhao, G. and Zhang, H. Automatic Configuration Method of Smart Substation
Process Layer Network. In 2017 2nd International Conference on Electrical, Control and Automation
Engineering (ECAE 2017). Atlantis Press. , 2017, December.
[5]. Chandramouli, R. and Chandramouli, R. Secure virtual network configuration for virtual machine
(vm) protection. NIST Special Publication, 800, p.125B. , 2016.
[6]. Addis, B., Belabed, D., Bouet, M. and Secci, S. Virtual network functions placement and routing
optimization. In 2015 IEEE 4th International Conference on Cloud Networking (CloudNet) (pp. 171-177).
IEEE. , 2015, October.
[7]. Balakumar, N. and Prabhu, B. Evaluation of Quality in Network and Interoperable Connectivity
between IP Networks. International Journal of Current Engineering and Scientific Research
(IJCESR), 3(9). , 2016.
[8]. Jevremovic, A., Shimic, G., Veinovic, M. and Ristic, N. IP Addressing: Problem-Based Learning
Approach on Computer Networks. IEEE Transactions on Learning Technologies, 10(3), pp.367-378. ,
2016.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





