M2M Solutions: Network Design Report, Addressing and Analysis
VerifiedAdded on 2020/03/01
|12
|2260
|328
Report
AI Summary
This report addresses the network design requirements for M2M Solutions, a medium-sized organization with six sites across Sydney. The report begins with an executive summary outlining the need for a robust network to facilitate communication and data security. Task 1 focuses on addressing the company's network needs, considering the number of workstations at each site and the potential for future expansion. A Class A private IP addressing scheme (10.0.0.0) is proposed, with detailed subnetting configurations for each building, including finance, transport, research, sales, IT, and head offices. The addressing scheme considers future growth, providing for up to 2046 hosts per subnet. A network diagram visually represents the proposed network architecture. Task 2 introduces the concept of network analyzers as essential tools for monitoring, analyzing, and troubleshooting network issues. The report explains the functionality of network analyzers, including packet sniffing, and their role in identifying and resolving network problems. The report also discusses router-based and non-router-based monitoring techniques, and provides examples of popular network analyzer tools, such as Wireshark and Microsoft Network Monitor, emphasizing the benefits of using Wireshark due to its free availability and user-friendly interface. The report concludes with references to the sources used.

Running Head: NETWORKING 1
NETWORKING
NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING 2
Table of Contents
Executive summary.........................................................................................................................3
Task 1...............................................................................................................................................3
Addressing solution for the company..........................................................................................3
Network diagram.........................................................................................................................8
Number of hosts increases above 1024.......................................................................................9
Task 2...............................................................................................................................................9
Network analyzers.......................................................................................................................9
References......................................................................................................................................13
Table of Contents
Executive summary.........................................................................................................................3
Task 1...............................................................................................................................................3
Addressing solution for the company..........................................................................................3
Network diagram.........................................................................................................................8
Number of hosts increases above 1024.......................................................................................9
Task 2...............................................................................................................................................9
Network analyzers.......................................................................................................................9
References......................................................................................................................................13

NETWORKING 3
Executive summary
Having a good network for an organization enables proper communication and smooth function
of the activities of the organization. M2M Solutions is a medium sized organization. The
company has six sites across Sydney such that it has various departments running in these six
buildings. The company is planning to have a good network design so that the communication
among the various departments is smooth and the information stored is safe from outside access.
Each building is to be enabled with a router to form a network. The company is looking for a
new network design such that each building has its own single subnet. The network is designed
with class A address and network analyzer for analyzing, monitoring and for troubleshooting is
recommended for the network of the organization.
Task 1
The six buildings and the number of workstations in each building are given below:
Finance Office - 260 workstations
Transport Office - 130 workstations
Research Office - 120 workstations
Sales Office - 40 workstations
Information technology - 520 workstations
Head Office - 60 workstations
Thus, in total there are 1200 workstations.
Addressing solution for the company
The company is making use of a private IP address with IP as 10.0.0.0 for the entire network.
Each building shall have a router to connect to the network such that each building shall have its
Executive summary
Having a good network for an organization enables proper communication and smooth function
of the activities of the organization. M2M Solutions is a medium sized organization. The
company has six sites across Sydney such that it has various departments running in these six
buildings. The company is planning to have a good network design so that the communication
among the various departments is smooth and the information stored is safe from outside access.
Each building is to be enabled with a router to form a network. The company is looking for a
new network design such that each building has its own single subnet. The network is designed
with class A address and network analyzer for analyzing, monitoring and for troubleshooting is
recommended for the network of the organization.
Task 1
The six buildings and the number of workstations in each building are given below:
Finance Office - 260 workstations
Transport Office - 130 workstations
Research Office - 120 workstations
Sales Office - 40 workstations
Information technology - 520 workstations
Head Office - 60 workstations
Thus, in total there are 1200 workstations.
Addressing solution for the company
The company is making use of a private IP address with IP as 10.0.0.0 for the entire network.
Each building shall have a router to connect to the network such that each building shall have its
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORKING 4
own single subnet. Currently, the company has 1200 workstations and it is expected that in near
future the number of workstations may increase. Keeping expansion in the network in mind the
following addressing scheme using the 10.0.0.0 IP address for the six sites is given below:
The Building is making use of Class A private addressing scheme. For Class A the mask address
must begin with 255.0.0.0 at the minimum as the first octet of the IP address which defines the
location on the network must be used to define the network portion of the device. These network
portions are used by the routers to send packets to the network (Sunshine, 2013). Routers don’t
need any host address all they need is the network portion or the host’s address which defines
where the host is located and the MAC address which is used to find the host on the network.
The last three octets of this IP address mask are then used to represent the address of the hosts on
a network LAN. Keeping all these points in the mind following addressing scheme is proposed
for the network.
The first building is the finance office and it has 260 work stations.
Since the number of workstations is more than 254 then following addressing is used for the
finance office then 10.0.0.0/23 shall have [2^ (9) - 2] = 510 hosts (Hui et al, 2014). But the
information office has 520 hosts thus 10.0.0.0/22 should be used for addressing as this shall
accommodate 1022 hosts. But the company is expecting approximately 1200 workstation across
all the sites thus; subnetting should be done as 10.0.0.0/21 giving the ability to have 2046 hosts.
Currently, the company has 1010 hosts and in such scenario 10.0.0.22 is the best option. Thus,
the chosen addressing scheme is as follows:
Finance office: 260 Workstations
own single subnet. Currently, the company has 1200 workstations and it is expected that in near
future the number of workstations may increase. Keeping expansion in the network in mind the
following addressing scheme using the 10.0.0.0 IP address for the six sites is given below:
The Building is making use of Class A private addressing scheme. For Class A the mask address
must begin with 255.0.0.0 at the minimum as the first octet of the IP address which defines the
location on the network must be used to define the network portion of the device. These network
portions are used by the routers to send packets to the network (Sunshine, 2013). Routers don’t
need any host address all they need is the network portion or the host’s address which defines
where the host is located and the MAC address which is used to find the host on the network.
The last three octets of this IP address mask are then used to represent the address of the hosts on
a network LAN. Keeping all these points in the mind following addressing scheme is proposed
for the network.
The first building is the finance office and it has 260 work stations.
Since the number of workstations is more than 254 then following addressing is used for the
finance office then 10.0.0.0/23 shall have [2^ (9) - 2] = 510 hosts (Hui et al, 2014). But the
information office has 520 hosts thus 10.0.0.0/22 should be used for addressing as this shall
accommodate 1022 hosts. But the company is expecting approximately 1200 workstation across
all the sites thus; subnetting should be done as 10.0.0.0/21 giving the ability to have 2046 hosts.
Currently, the company has 1010 hosts and in such scenario 10.0.0.22 is the best option. Thus,
the chosen addressing scheme is as follows:
Finance office: 260 Workstations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
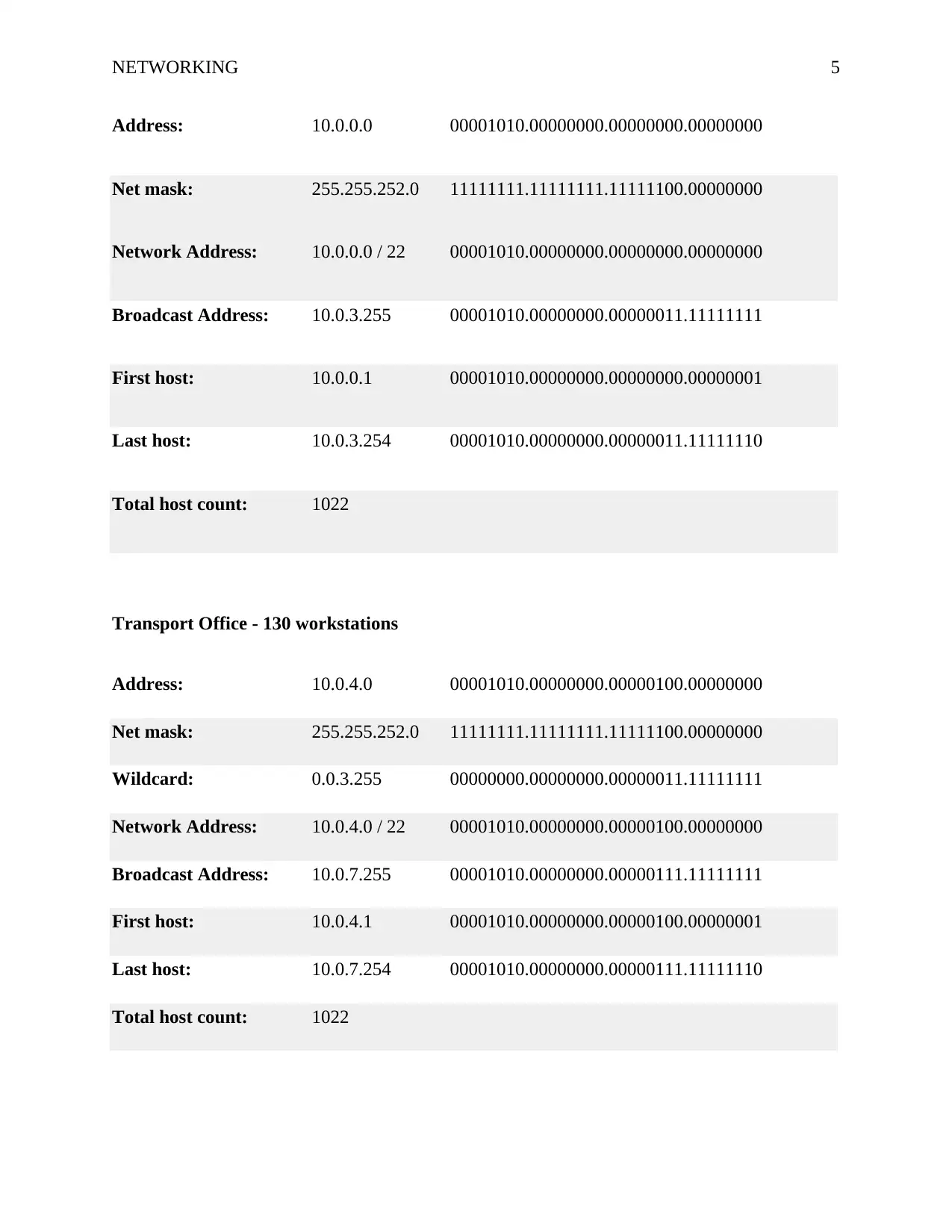
NETWORKING 5
Address: 10.0.0.0 00001010.00000000.00000000.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Network Address: 10.0.0.0 / 22 00001010.00000000.00000000.00000000
Broadcast Address: 10.0.3.255 00001010.00000000.00000011.11111111
First host: 10.0.0.1 00001010.00000000.00000000.00000001
Last host: 10.0.3.254 00001010.00000000.00000011.11111110
Total host count: 1022
Transport Office - 130 workstations
Address: 10.0.4.0 00001010.00000000.00000100.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.4.0 / 22 00001010.00000000.00000100.00000000
Broadcast Address: 10.0.7.255 00001010.00000000.00000111.11111111
First host: 10.0.4.1 00001010.00000000.00000100.00000001
Last host: 10.0.7.254 00001010.00000000.00000111.11111110
Total host count: 1022
Address: 10.0.0.0 00001010.00000000.00000000.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Network Address: 10.0.0.0 / 22 00001010.00000000.00000000.00000000
Broadcast Address: 10.0.3.255 00001010.00000000.00000011.11111111
First host: 10.0.0.1 00001010.00000000.00000000.00000001
Last host: 10.0.3.254 00001010.00000000.00000011.11111110
Total host count: 1022
Transport Office - 130 workstations
Address: 10.0.4.0 00001010.00000000.00000100.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.4.0 / 22 00001010.00000000.00000100.00000000
Broadcast Address: 10.0.7.255 00001010.00000000.00000111.11111111
First host: 10.0.4.1 00001010.00000000.00000100.00000001
Last host: 10.0.7.254 00001010.00000000.00000111.11111110
Total host count: 1022
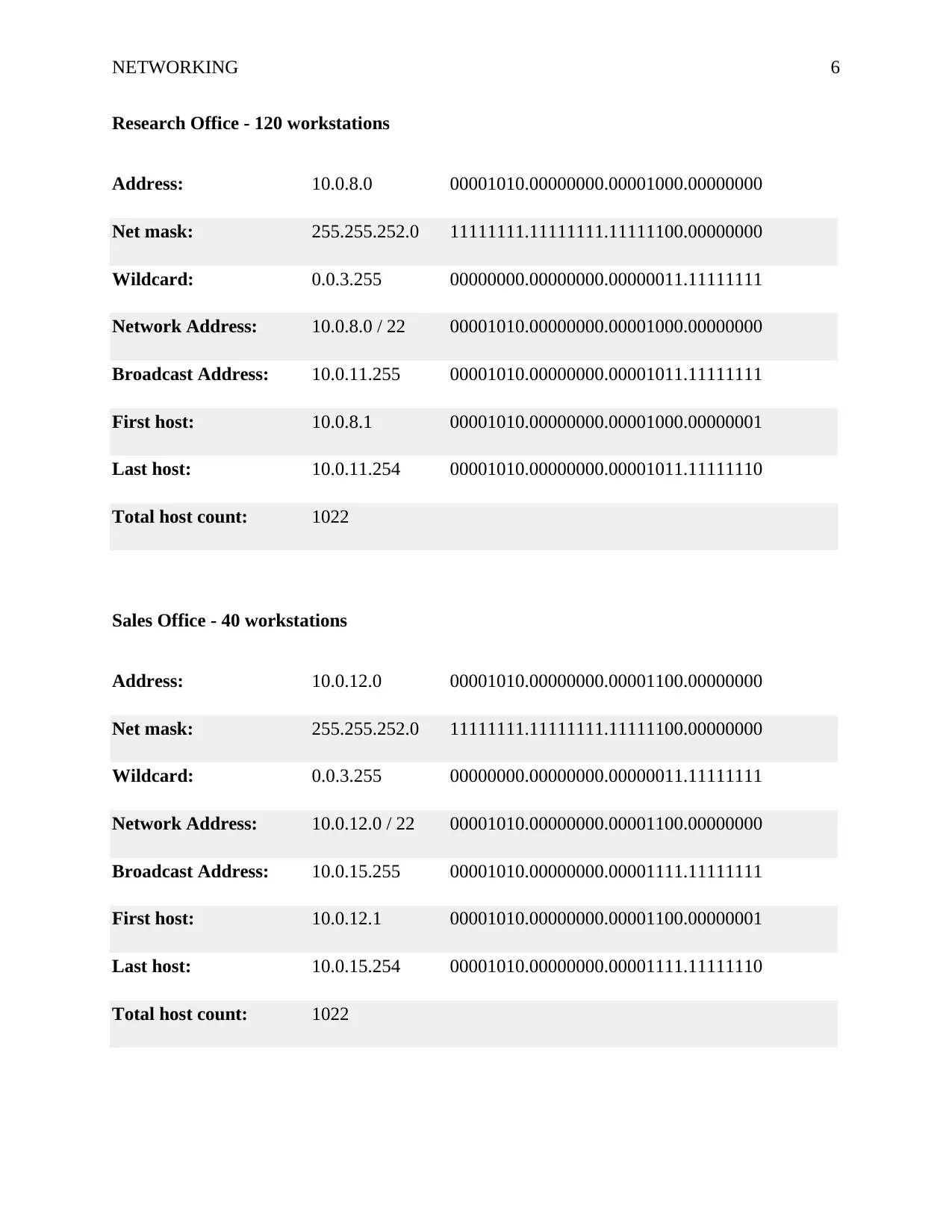
NETWORKING 6
Research Office - 120 workstations
Address: 10.0.8.0 00001010.00000000.00001000.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.8.0 / 22 00001010.00000000.00001000.00000000
Broadcast Address: 10.0.11.255 00001010.00000000.00001011.11111111
First host: 10.0.8.1 00001010.00000000.00001000.00000001
Last host: 10.0.11.254 00001010.00000000.00001011.11111110
Total host count: 1022
Sales Office - 40 workstations
Address: 10.0.12.0 00001010.00000000.00001100.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.12.0 / 22 00001010.00000000.00001100.00000000
Broadcast Address: 10.0.15.255 00001010.00000000.00001111.11111111
First host: 10.0.12.1 00001010.00000000.00001100.00000001
Last host: 10.0.15.254 00001010.00000000.00001111.11111110
Total host count: 1022
Research Office - 120 workstations
Address: 10.0.8.0 00001010.00000000.00001000.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.8.0 / 22 00001010.00000000.00001000.00000000
Broadcast Address: 10.0.11.255 00001010.00000000.00001011.11111111
First host: 10.0.8.1 00001010.00000000.00001000.00000001
Last host: 10.0.11.254 00001010.00000000.00001011.11111110
Total host count: 1022
Sales Office - 40 workstations
Address: 10.0.12.0 00001010.00000000.00001100.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.12.0 / 22 00001010.00000000.00001100.00000000
Broadcast Address: 10.0.15.255 00001010.00000000.00001111.11111111
First host: 10.0.12.1 00001010.00000000.00001100.00000001
Last host: 10.0.15.254 00001010.00000000.00001111.11111110
Total host count: 1022
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
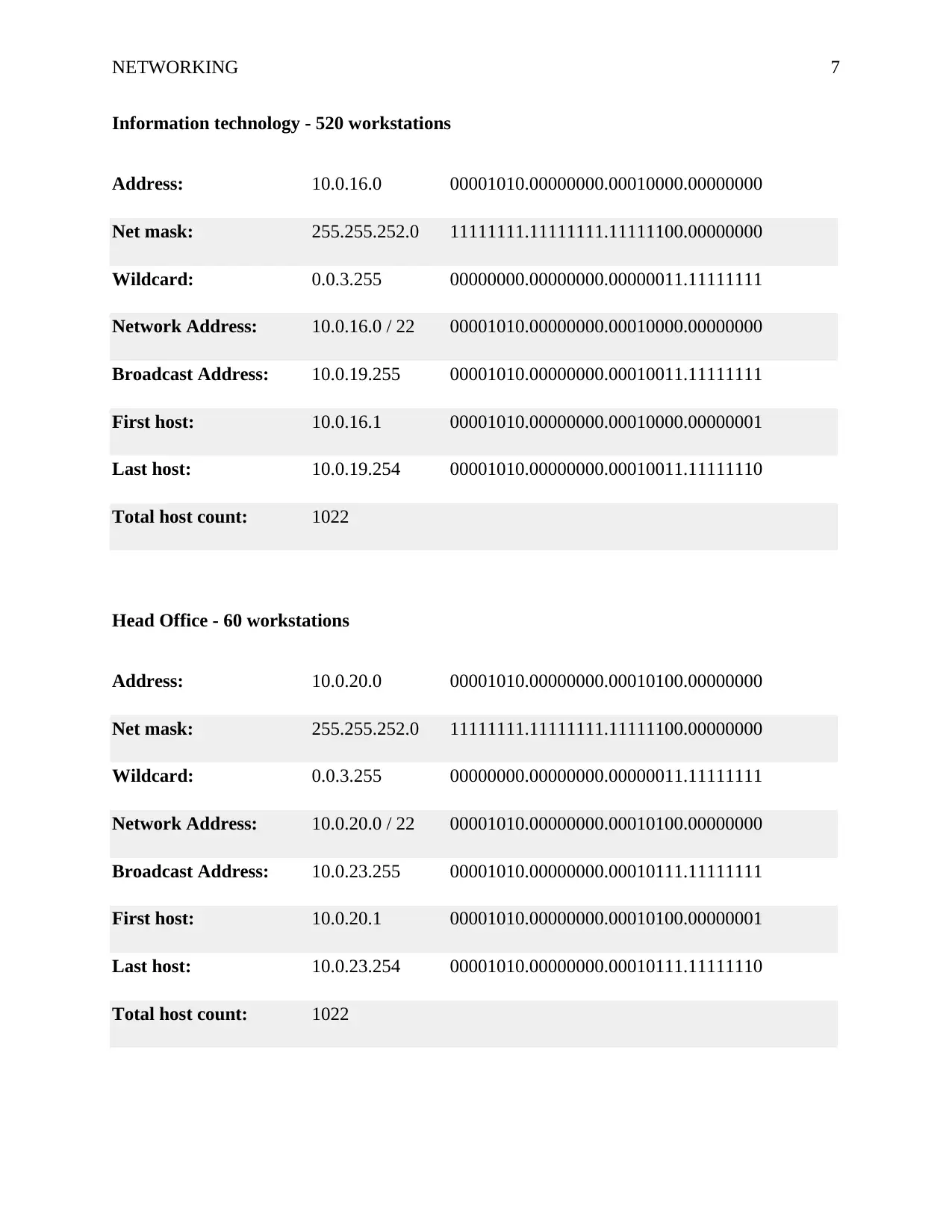
NETWORKING 7
Information technology - 520 workstations
Address: 10.0.16.0 00001010.00000000.00010000.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.16.0 / 22 00001010.00000000.00010000.00000000
Broadcast Address: 10.0.19.255 00001010.00000000.00010011.11111111
First host: 10.0.16.1 00001010.00000000.00010000.00000001
Last host: 10.0.19.254 00001010.00000000.00010011.11111110
Total host count: 1022
Head Office - 60 workstations
Address: 10.0.20.0 00001010.00000000.00010100.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.20.0 / 22 00001010.00000000.00010100.00000000
Broadcast Address: 10.0.23.255 00001010.00000000.00010111.11111111
First host: 10.0.20.1 00001010.00000000.00010100.00000001
Last host: 10.0.23.254 00001010.00000000.00010111.11111110
Total host count: 1022
Information technology - 520 workstations
Address: 10.0.16.0 00001010.00000000.00010000.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.16.0 / 22 00001010.00000000.00010000.00000000
Broadcast Address: 10.0.19.255 00001010.00000000.00010011.11111111
First host: 10.0.16.1 00001010.00000000.00010000.00000001
Last host: 10.0.19.254 00001010.00000000.00010011.11111110
Total host count: 1022
Head Office - 60 workstations
Address: 10.0.20.0 00001010.00000000.00010100.00000000
Net mask: 255.255.252.0 11111111.11111111.11111100.00000000
Wildcard: 0.0.3.255 00000000.00000000.00000011.11111111
Network Address: 10.0.20.0 / 22 00001010.00000000.00010100.00000000
Broadcast Address: 10.0.23.255 00001010.00000000.00010111.11111111
First host: 10.0.20.1 00001010.00000000.00010100.00000001
Last host: 10.0.23.254 00001010.00000000.00010111.11111110
Total host count: 1022
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
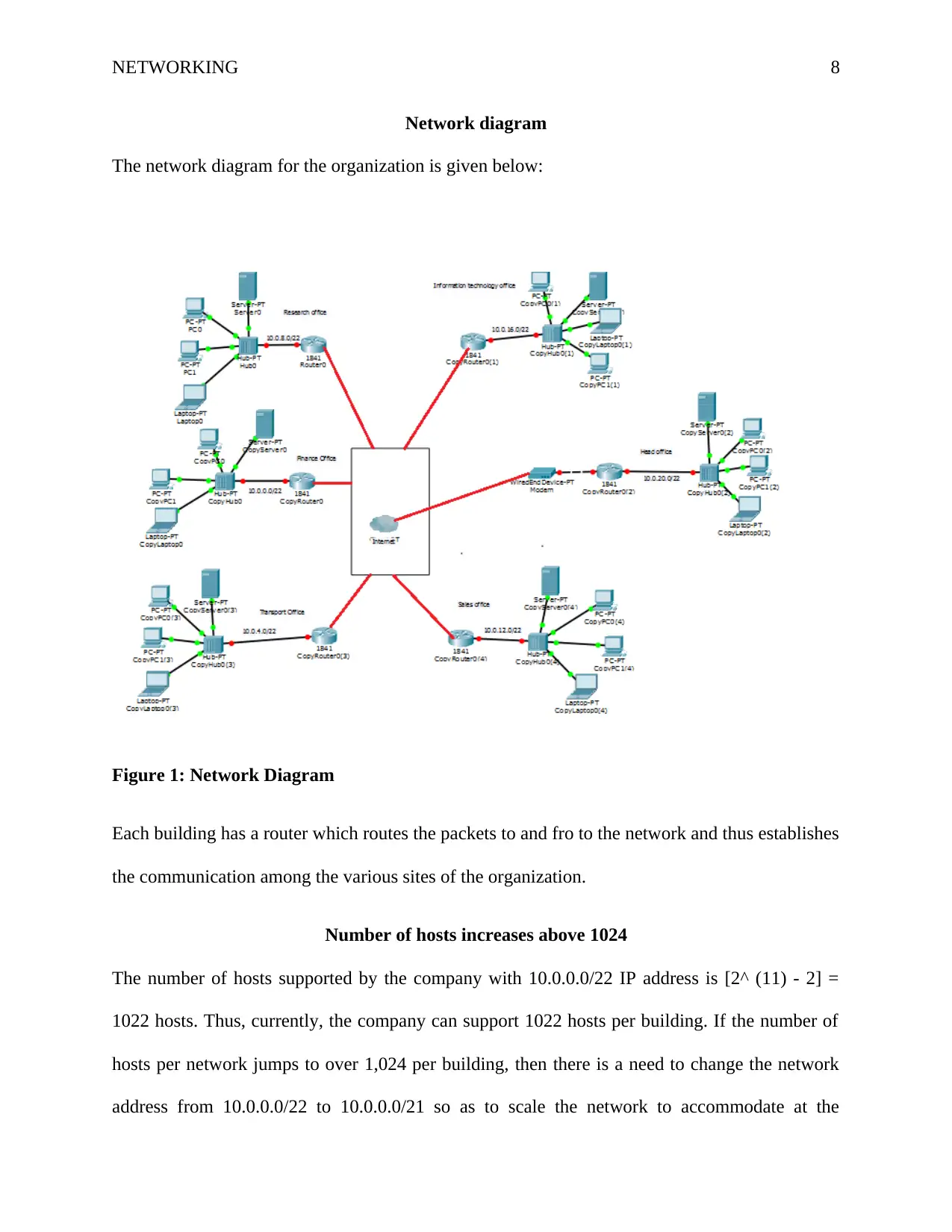
NETWORKING 8
Network diagram
The network diagram for the organization is given below:
Figure 1: Network Diagram
Each building has a router which routes the packets to and fro to the network and thus establishes
the communication among the various sites of the organization.
Number of hosts increases above 1024
The number of hosts supported by the company with 10.0.0.0/22 IP address is [2^ (11) - 2] =
1022 hosts. Thus, currently, the company can support 1022 hosts per building. If the number of
hosts per network jumps to over 1,024 per building, then there is a need to change the network
address from 10.0.0.0/22 to 10.0.0.0/21 so as to scale the network to accommodate at the
Network diagram
The network diagram for the organization is given below:
Figure 1: Network Diagram
Each building has a router which routes the packets to and fro to the network and thus establishes
the communication among the various sites of the organization.
Number of hosts increases above 1024
The number of hosts supported by the company with 10.0.0.0/22 IP address is [2^ (11) - 2] =
1022 hosts. Thus, currently, the company can support 1022 hosts per building. If the number of
hosts per network jumps to over 1,024 per building, then there is a need to change the network
address from 10.0.0.0/22 to 10.0.0.0/21 so as to scale the network to accommodate at the

NETWORKING 9
maximum 2046 hosts as then the number of hosts is [2^ (11) - 2] = 2046 hosts. Thus the new
subnetting for the buildings can be Finance Office - 10.0.0.0/21, Transport Office – 10.0.4.0/21,
Research Office - 10.0.8.0/21, Sales Office - 10.0.12.0/21,Information technology – 10.0.16.0/21
and Head Office - 10.0.20.0/21.
Task 2
Network analyzers
When the network size grows it becomes difficult for the network administrator to monitor and
trouble shoots the problems associated with the network. Manually going and finding the fault
within the network, diagnosing the fault and then trouble shooting it takes a lot of time and till
then the network may not be available for the usage. Thus, there are some tools like network
analyzers which assist the network administrator to perform such networking monitoring,
analyzing and troubleshooting tasks easily and efficiently. Network analyzers are also known as
a packet sniffer and these are tools which help the network administrator to monitor the network
of the organization, to perform the diagnostic tests of the entire network and troubleshoot the
problems of the network (Ndatinya et al 2015).
Network analysis is a process performed by the network administrator where the network traffic
is captured and inspected closely so as to determine what is happening in the network. There are
two techniques of network monitoring namely router based monitoring and non-router based
monitoring techniques. The monitoring facilities built-into the routers and require no additional
hardware or software installation is known as the router based techniques. In non-router based
techniques need additional hardware and software (Ndatinya et al 2015).
maximum 2046 hosts as then the number of hosts is [2^ (11) - 2] = 2046 hosts. Thus the new
subnetting for the buildings can be Finance Office - 10.0.0.0/21, Transport Office – 10.0.4.0/21,
Research Office - 10.0.8.0/21, Sales Office - 10.0.12.0/21,Information technology – 10.0.16.0/21
and Head Office - 10.0.20.0/21.
Task 2
Network analyzers
When the network size grows it becomes difficult for the network administrator to monitor and
trouble shoots the problems associated with the network. Manually going and finding the fault
within the network, diagnosing the fault and then trouble shooting it takes a lot of time and till
then the network may not be available for the usage. Thus, there are some tools like network
analyzers which assist the network administrator to perform such networking monitoring,
analyzing and troubleshooting tasks easily and efficiently. Network analyzers are also known as
a packet sniffer and these are tools which help the network administrator to monitor the network
of the organization, to perform the diagnostic tests of the entire network and troubleshoot the
problems of the network (Ndatinya et al 2015).
Network analysis is a process performed by the network administrator where the network traffic
is captured and inspected closely so as to determine what is happening in the network. There are
two techniques of network monitoring namely router based monitoring and non-router based
monitoring techniques. The monitoring facilities built-into the routers and require no additional
hardware or software installation is known as the router based techniques. In non-router based
techniques need additional hardware and software (Ndatinya et al 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORKING 10
Generally, in a network, the communication takes place through the networking protocols like
OSI model and the TCP/IP model. The internet based network generally makes use of TCP/IP
model and in this model, the data is broken down in the forms of packets and sent to the
destination address. Each host on the network has an IP address. The packet's header comprise of
the destination address and the source address. The packet is forwarded to the destination address
via packet-switched networks. These packets then are reassembled at the destination end and the
message is delivered to the end user. In general computer network without the packet sniffer, the
host computer looks only at the packet addressed to it and ignores the rest of the packets on the
network. But when the packets sniffer or the network analyzer is used the network analyzer sets
itself to the promiscuous mode and looks for everything coming on to the network. It even
captures the raw data packets and analyzes the packet (Gandhi et al, 2014).
While dealing with any network issue the network administrator executes the steps employed as
standard steps of trouble shooting like identifying the sources of the problem and take necessary
corrections. Some of the methods employed are performing Ping, checking client devices, IP
addresses, etc. but these methods fail to deal with complex network problems and here the
network analyzer come to play. It captures the packets and displays the details related to the
packet along with the protocol options and the data payload. This information gives the details of
what is going on in the entire network and gives quick details to the network administrator for
fast trouble shooting (Gandhi et al, 2014).
Some example of the network analyzer capabilities are as follows:
Generally, in a network, the communication takes place through the networking protocols like
OSI model and the TCP/IP model. The internet based network generally makes use of TCP/IP
model and in this model, the data is broken down in the forms of packets and sent to the
destination address. Each host on the network has an IP address. The packet's header comprise of
the destination address and the source address. The packet is forwarded to the destination address
via packet-switched networks. These packets then are reassembled at the destination end and the
message is delivered to the end user. In general computer network without the packet sniffer, the
host computer looks only at the packet addressed to it and ignores the rest of the packets on the
network. But when the packets sniffer or the network analyzer is used the network analyzer sets
itself to the promiscuous mode and looks for everything coming on to the network. It even
captures the raw data packets and analyzes the packet (Gandhi et al, 2014).
While dealing with any network issue the network administrator executes the steps employed as
standard steps of trouble shooting like identifying the sources of the problem and take necessary
corrections. Some of the methods employed are performing Ping, checking client devices, IP
addresses, etc. but these methods fail to deal with complex network problems and here the
network analyzer come to play. It captures the packets and displays the details related to the
packet along with the protocol options and the data payload. This information gives the details of
what is going on in the entire network and gives quick details to the network administrator for
fast trouble shooting (Gandhi et al, 2014).
Some example of the network analyzer capabilities are as follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING 11
a. Real time network card utilization: through this tool the network administrator gets
information on the bandwidth utilization of the entire network. This enables spot packet
burst and other traffic patterns (Gandhi et al, 2014).
b. The traffic captured using the network analyzer is generally stored in a buffer space. This
buffer can be stored in the hard disk and can be analyzed later for the network monitoring
tools.
c. There are some configuration problems which are difficult to identify by the network
administrator. The network analyzer helps on automatically identifying the network
problem and thus allows uncovering any suspicious activities on the network or any
hacking attempts on the network by any unauthorized user.
d. When connected to ISP the network analyzer can give details on the type of website
visited, what was searched, whom the email was sent to, what is downloaded etc (Gandhi
et al, 2014).
Some of the famous networking analyzer tools are as follows:
1. Wire shark: This is a freely available network analyzer tool which is capable of
inspecting traffic, identifying denial-of–services attacks, analyze the packets, and
troubleshoot the devices and firewalls. It also analyzes the protocol analyzer (Ndatinya et
al 2015).
2. Microsoft Network monitor: this is a deprecated packet analyzer which captures, view
and analyzes the network data and deciphers the network protocols. This is used for
troubleshooting network problems and thus can be used for rectifying the network based
issues (Gandhi et al, 2014).
a. Real time network card utilization: through this tool the network administrator gets
information on the bandwidth utilization of the entire network. This enables spot packet
burst and other traffic patterns (Gandhi et al, 2014).
b. The traffic captured using the network analyzer is generally stored in a buffer space. This
buffer can be stored in the hard disk and can be analyzed later for the network monitoring
tools.
c. There are some configuration problems which are difficult to identify by the network
administrator. The network analyzer helps on automatically identifying the network
problem and thus allows uncovering any suspicious activities on the network or any
hacking attempts on the network by any unauthorized user.
d. When connected to ISP the network analyzer can give details on the type of website
visited, what was searched, whom the email was sent to, what is downloaded etc (Gandhi
et al, 2014).
Some of the famous networking analyzer tools are as follows:
1. Wire shark: This is a freely available network analyzer tool which is capable of
inspecting traffic, identifying denial-of–services attacks, analyze the packets, and
troubleshoot the devices and firewalls. It also analyzes the protocol analyzer (Ndatinya et
al 2015).
2. Microsoft Network monitor: this is a deprecated packet analyzer which captures, view
and analyzes the network data and deciphers the network protocols. This is used for
troubleshooting network problems and thus can be used for rectifying the network based
issues (Gandhi et al, 2014).

NETWORKING 12
3. Cpasa: This is a network analyzer that is capable of capturing the packets from multiple
and single adapters, analyze the contents of each packet, provides statistics related to the
IP addresses and the MAC address, analyses the protocols from data link and application
layer, give logs of web browsing, email, computer anomalies to the user. IT alerts the
network administrator regarding any type of anomalies coming to the network. This is a
paid network analyzing tool and the cost is $0-$995, depending on version (Varanasi et
al, 2016).
It is better to go for Wire shark as the network analyzing tool as it is freely available and
gives proper network analysis and monitoring capabilities. It also provides details regarding
the packets, their IP address, and MAC address and can thus be used easily for
troubleshooting. The GUI of the Wire shark is user-friendly and easy to use (Ndatinya et al
2015).
3. Cpasa: This is a network analyzer that is capable of capturing the packets from multiple
and single adapters, analyze the contents of each packet, provides statistics related to the
IP addresses and the MAC address, analyses the protocols from data link and application
layer, give logs of web browsing, email, computer anomalies to the user. IT alerts the
network administrator regarding any type of anomalies coming to the network. This is a
paid network analyzing tool and the cost is $0-$995, depending on version (Varanasi et
al, 2016).
It is better to go for Wire shark as the network analyzing tool as it is freely available and
gives proper network analysis and monitoring capabilities. It also provides details regarding
the packets, their IP address, and MAC address and can thus be used easily for
troubleshooting. The GUI of the Wire shark is user-friendly and easy to use (Ndatinya et al
2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





