COIT20262 - Internet Protocols and Wireshark Analysis Assignment
VerifiedAdded on 2020/03/04
|3
|978
|100
Homework Assignment
AI Summary
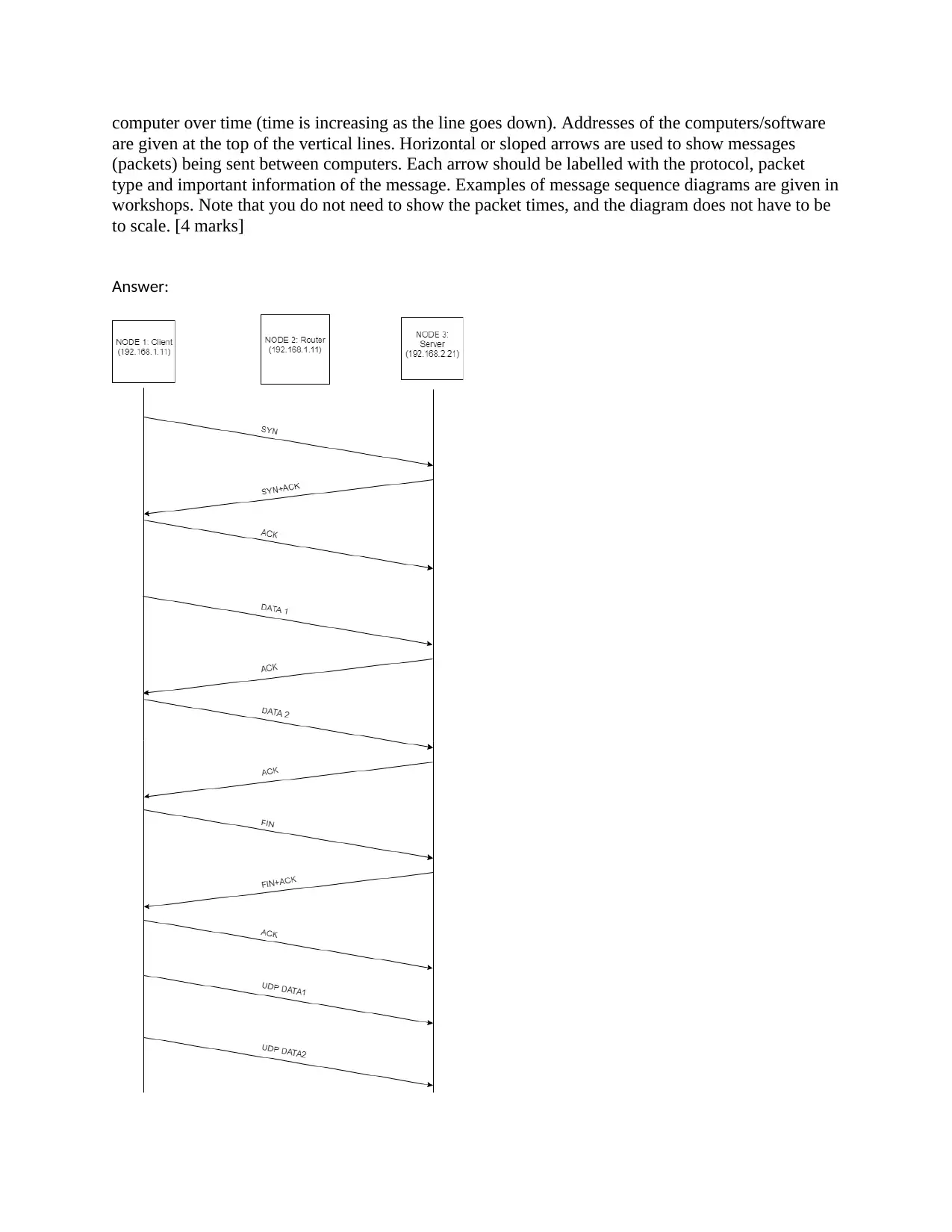
This assignment involves analyzing network protocols using Wireshark and virtnet. The student is tasked with capturing TCP and UDP packets using netcat, creating a message sequence diagram, and answering questions about the captured data. The assignment requires setting up a network topology in virtnet, running netcat servers and clients, and capturing the network traffic using tcpdump. The student needs to submit the capture file and answer questions regarding the duration of TCP connections, the timing of UDP interactions, client port numbers, the limitations of using port numbers to identify applications, and what can be learned from client port numbers. This practical exercise aims to provide a solid understanding of common Internet protocols and the use of packet capture software. This solution is provided to the student for educational purposes, and Desklib offers various study resources like past papers and solved assignments.
1 out of 3









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)