Comprehensive Wireshark Report: Network Analysis and Performance
VerifiedAdded on 2023/06/03
|23
|1706
|301
Report
AI Summary
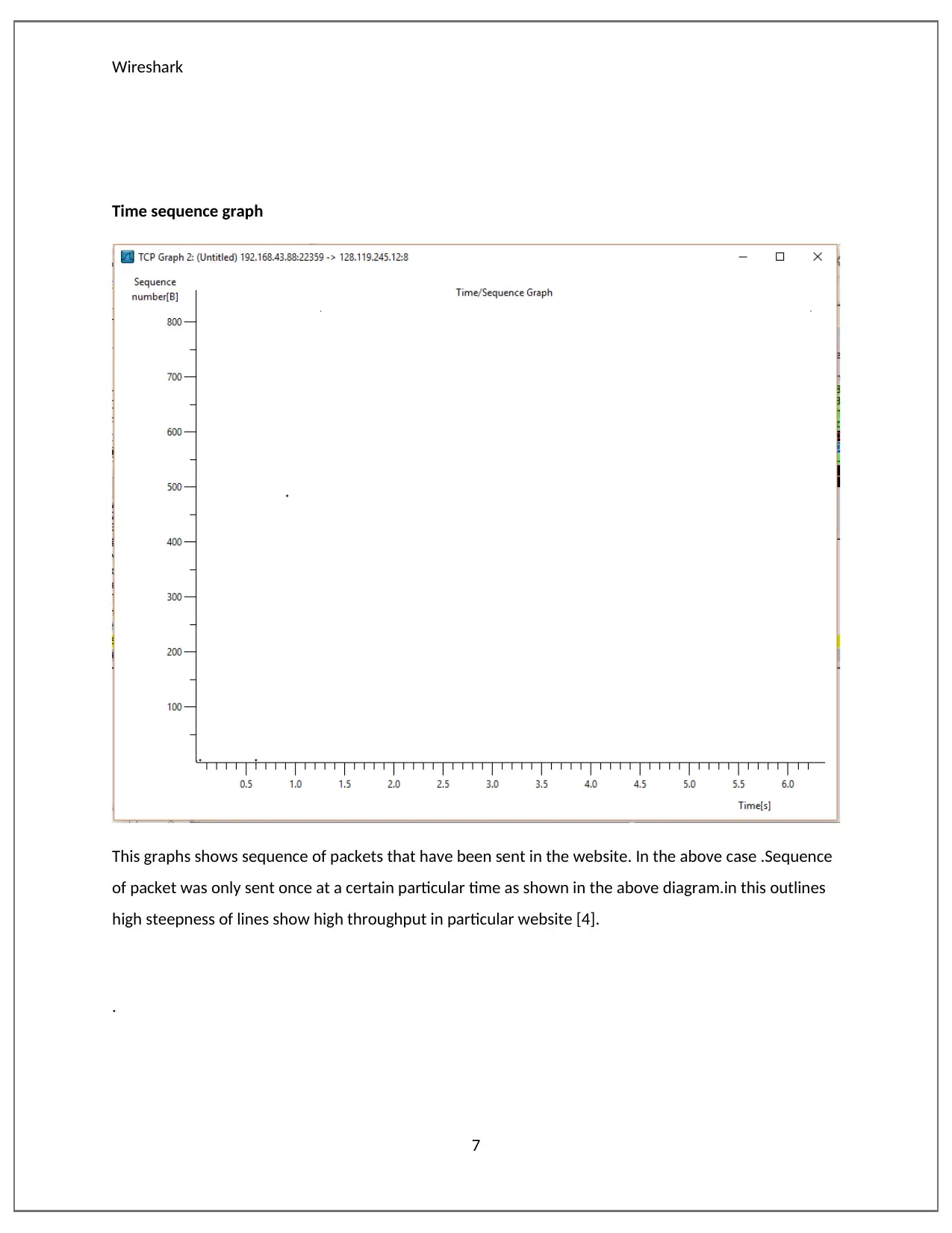
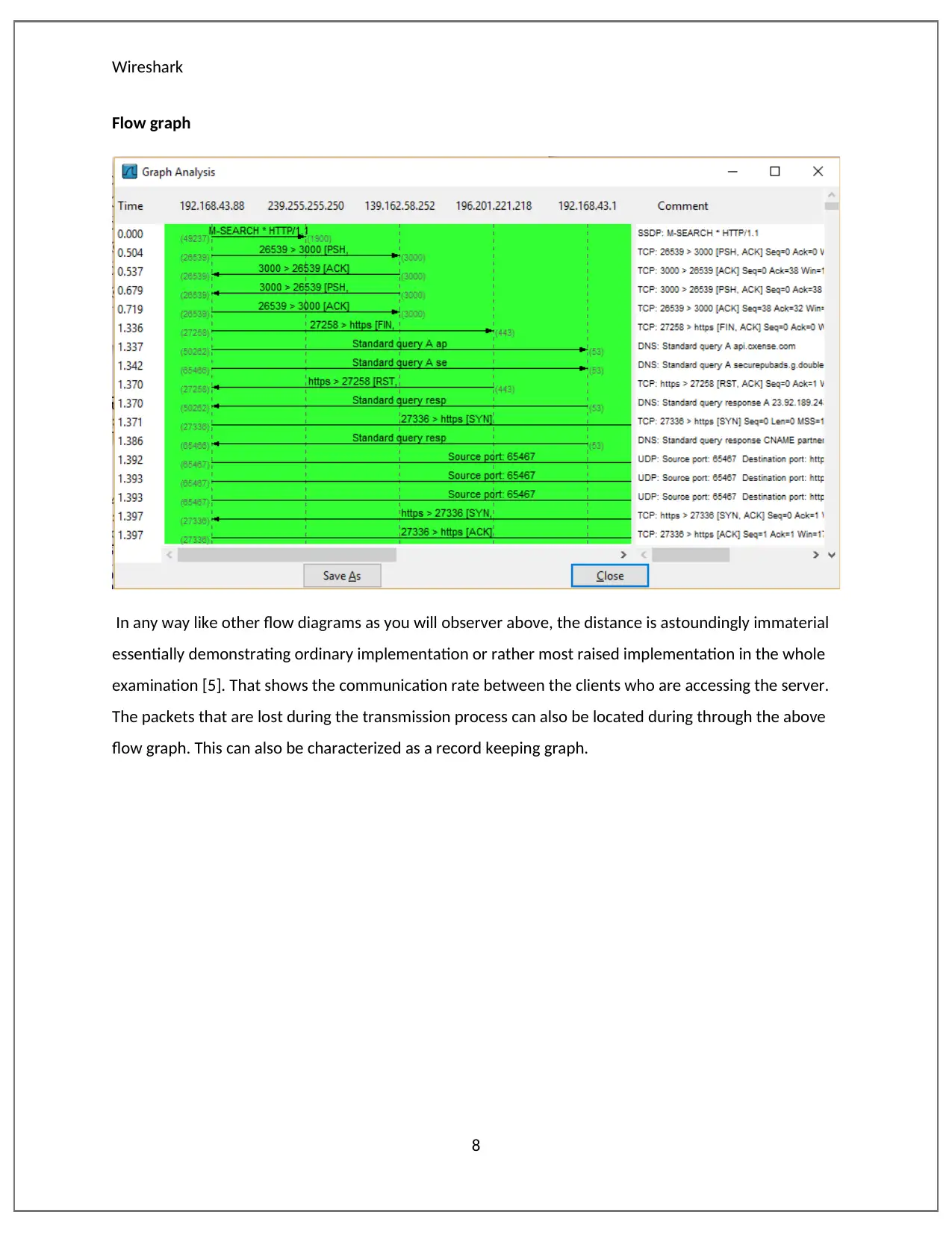
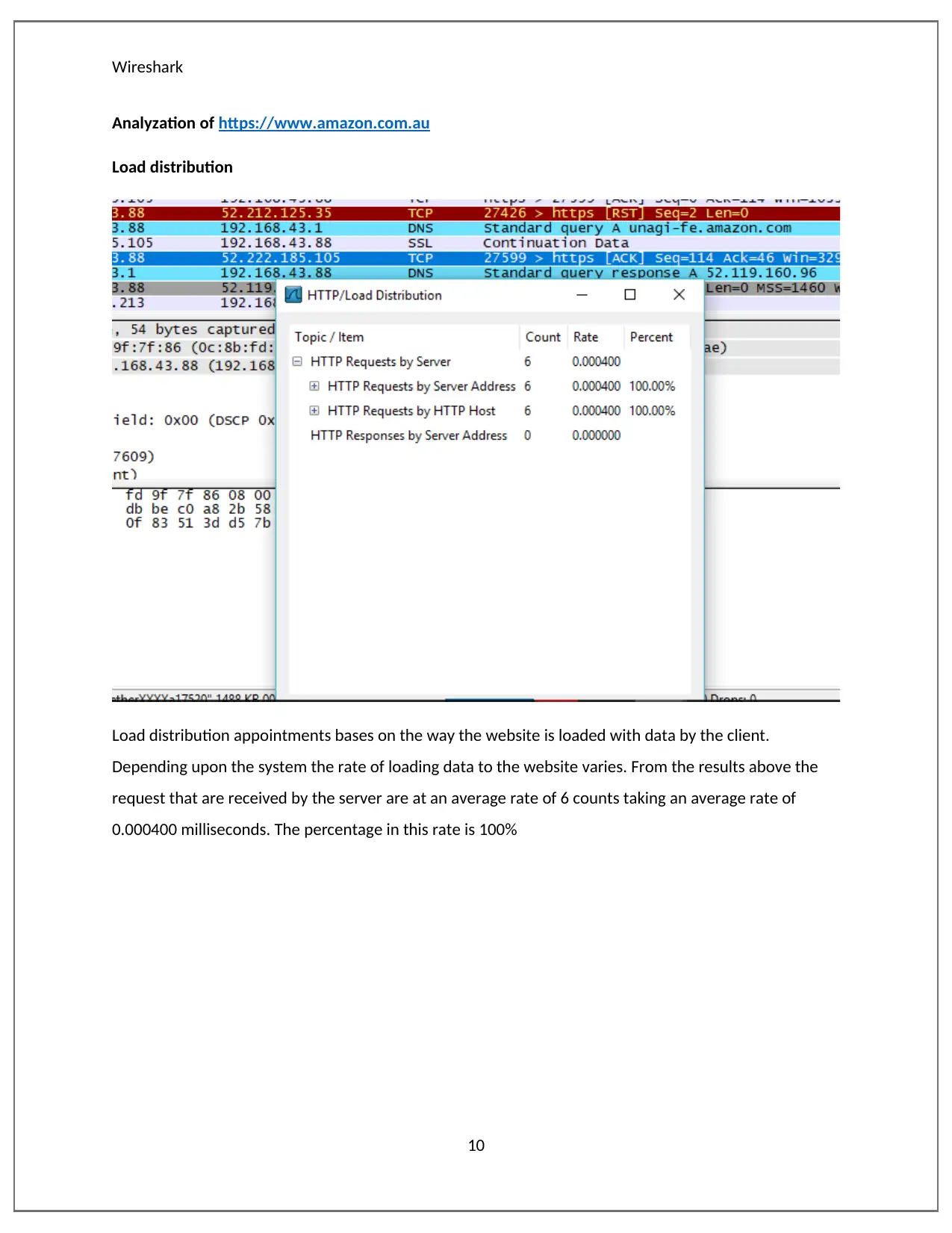
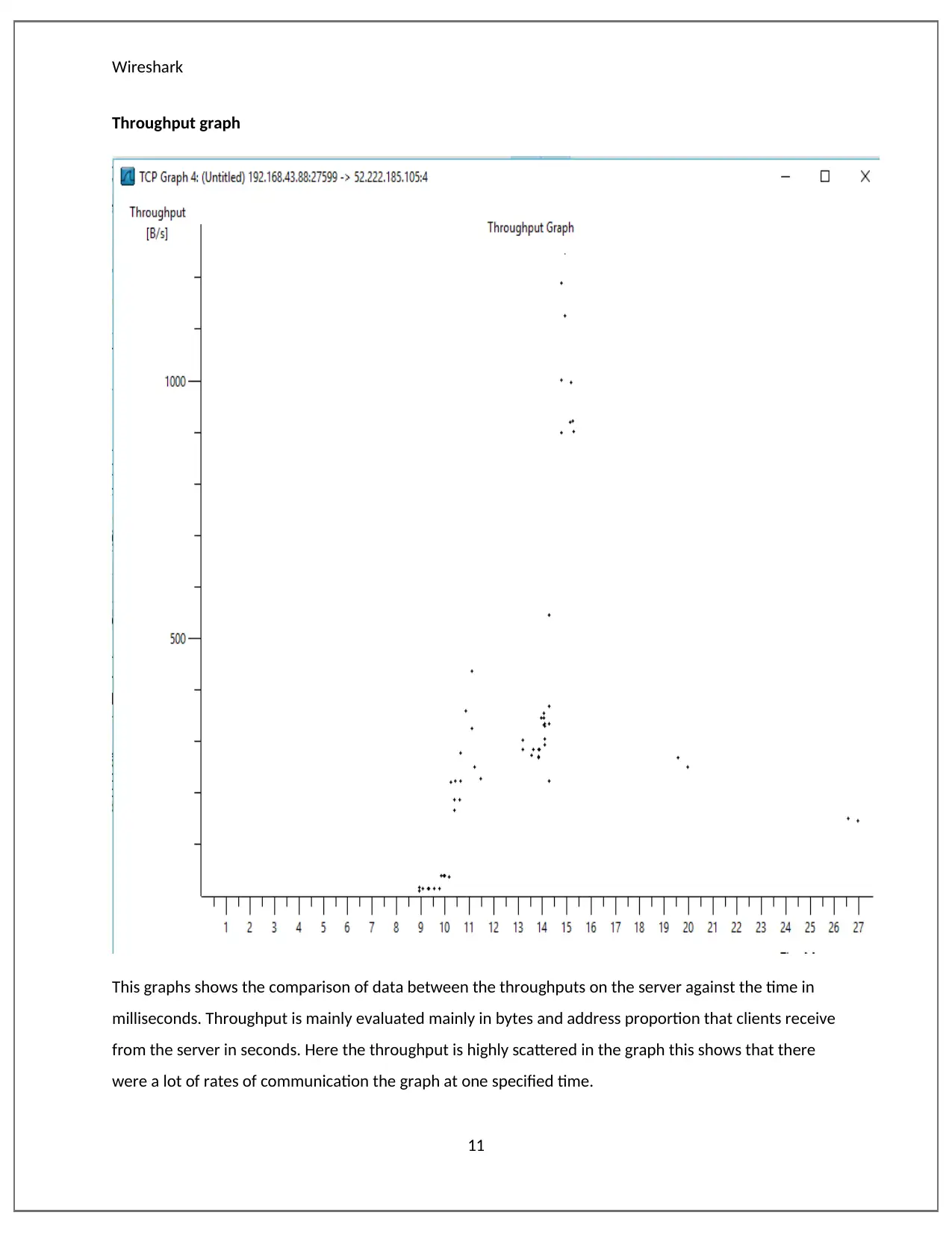
This report provides a detailed analysis of network packets using Wireshark, examining various websites to understand their load distribution, throughput, and time sequence. The analysis compares packet flows across different websites, highlighting variations in server responses to client requests. Wireshark, a packet sniffer, captures and analyzes network traffic by setting the network card in promiscuous mode. The report includes graphs illustrating throughput, time sequence, and flow, offering insights into network performance and communication rates. Specific websites such as sbs.com.au, amazon.com.au, and howeverythingworks.org are analyzed to demonstrate the software's capabilities in evaluating network behavior. This document explains how different website packets have been analyzed with Wireshark. The result that are produced by the software are totally different from each other. This is an indication that servers respond differently to request send by clients. Desklib provides a platform for students to access similar solved assignments and study tools.
1 out of 23









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)