IT NE 2005 - Network Security Analysis: Attacks and Audit Tools
VerifiedAdded on 2022/10/13
|13
|2701
|31
Report
AI Summary
This report provides a comprehensive analysis of network security, focusing on two key areas: network attacks and network security audit tools. The first part of the report details the Code Red (CRv2) worm attack, including its type, dates of occurrence, affected systems, operational mechanisms, and mitigation strategies. The analysis covers the worm's exploitation of vulnerabilities in Microsoft's IIS web servers, its propagation methods, and the denial-of-service attacks it initiated. The report also discusses the vulnerabilities and the available solutions to prevent such attacks. The second part of the report explores network security audit tools, specifically the Cisco Security Device Manager (SDM). It examines the tool's developer, type, and application on network devices, cost, key features, and capabilities. The report highlights SDM's GUI-based interface, ease of use, audit wizard, and its role in simplifying network security configurations, providing proactive network performance monitoring, and offering advanced security features. References include sources that support the analysis.

Running Head: Network Security Analysis 1
Network Security
Name of the Student
Name of the Institution
Network Security
Name of the Student
Name of the Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Security Analysis 2
Network Security Analysis
Part 1: Researching Network Attacks
Step 1: Research various network attacks
With sophisticated technology development, hackers have continued to advance their
tools to match present-day technology and have been able to launch several attacks targeted at
stealing information and gaining access and control to information systems. Throughout the IT
world history, some of the devastating attacks that have dealt the world tough blows include
Code Red, Nimba, Back Orifine, SQL Slammer and Tribe flood network attack among others.
Step 2: Fill in the following form for the network attack selected
Name of the Attack
The Code Red (CRv2) Worm Attack
Type of the Attack
Worm attack
Dates of the Attack
31st July, 2001.
Computers and Organizations affected
In less than 14 hours, more than 359,000 computers that were connected to the internet were
infected with the worm in an attack that was estimated to hav costed global organizations over
$2.6 billion.
Affected IIS versions 4.0 and 5.0 as well as Cisco products.
Systems running on XP beta, Windows 95, 98 and ME were also affected by the warm.
Network Security Analysis
Part 1: Researching Network Attacks
Step 1: Research various network attacks
With sophisticated technology development, hackers have continued to advance their
tools to match present-day technology and have been able to launch several attacks targeted at
stealing information and gaining access and control to information systems. Throughout the IT
world history, some of the devastating attacks that have dealt the world tough blows include
Code Red, Nimba, Back Orifine, SQL Slammer and Tribe flood network attack among others.
Step 2: Fill in the following form for the network attack selected
Name of the Attack
The Code Red (CRv2) Worm Attack
Type of the Attack
Worm attack
Dates of the Attack
31st July, 2001.
Computers and Organizations affected
In less than 14 hours, more than 359,000 computers that were connected to the internet were
infected with the worm in an attack that was estimated to hav costed global organizations over
$2.6 billion.
Affected IIS versions 4.0 and 5.0 as well as Cisco products.
Systems running on XP beta, Windows 95, 98 and ME were also affected by the warm.

Network Security Analysis 3
The worm attack was a global attack that targeted large corporations and preyed on both home-
based and small computers (Moore & Colleen, 2002).
How it works and what it did
Prior to the attack, eEye had released buffer overflow vulnerabilities in Microsoft’s Internet
Information Server (IIS) web servers on June 18 the same year. Microsoft responded by
releasing a software security patch update nine days later. Unfortunately, the patch did not work
as Code Red v2 stroke a few days later, by way of exploiting the reported vulnerabilities
(Berghel, 2001).
As an active worm, Code Red exploited security weaknesses in networking operating systems in
a highly aggressive manner to gain entry into computer and computing systems. Additionally,
the worm had a few more features that are never found in other worms. These included the
ability to propagate through transmission control protocol/internet protocol (TCP/IP) hypertext
transfer protocol port 80, identifying itself by defacing websites with the www.worm.com –
hacked by Chinese welcome messages. Other features included self-propagation that was fueled
by means of random generation of IP addressed that had bugs in them. Soon after gaining access
to a computer system, the worm was designed in such a way that it automatically initiated denial
of service (DoS) attacks on both machines and computer systems. The randomly generated IPs
were then probed on each machine while the worm tries to while the worm tried to infect more
machines between 1st and 19th of each month (incubation and infection stages). Between 20th and
28th of every month, the worm is programmed to cause DoS attacks and remains dormant for the
rest days of the month.
After first infecting a machine, the probing was done to check if th machine was already Code
Red v2 infected. If not, the worm then proceeded to initiate propagation mechanism by setting up
The worm attack was a global attack that targeted large corporations and preyed on both home-
based and small computers (Moore & Colleen, 2002).
How it works and what it did
Prior to the attack, eEye had released buffer overflow vulnerabilities in Microsoft’s Internet
Information Server (IIS) web servers on June 18 the same year. Microsoft responded by
releasing a software security patch update nine days later. Unfortunately, the patch did not work
as Code Red v2 stroke a few days later, by way of exploiting the reported vulnerabilities
(Berghel, 2001).
As an active worm, Code Red exploited security weaknesses in networking operating systems in
a highly aggressive manner to gain entry into computer and computing systems. Additionally,
the worm had a few more features that are never found in other worms. These included the
ability to propagate through transmission control protocol/internet protocol (TCP/IP) hypertext
transfer protocol port 80, identifying itself by defacing websites with the www.worm.com –
hacked by Chinese welcome messages. Other features included self-propagation that was fueled
by means of random generation of IP addressed that had bugs in them. Soon after gaining access
to a computer system, the worm was designed in such a way that it automatically initiated denial
of service (DoS) attacks on both machines and computer systems. The randomly generated IPs
were then probed on each machine while the worm tries to while the worm tried to infect more
machines between 1st and 19th of each month (incubation and infection stages). Between 20th and
28th of every month, the worm is programmed to cause DoS attacks and remains dormant for the
rest days of the month.
After first infecting a machine, the probing was done to check if th machine was already Code
Red v2 infected. If not, the worm then proceeded to initiate propagation mechanism by setting up
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Security Analysis 4
a backdoor and causing an auto-reboot in a machine. Unlike other versions of Code Red, code
Red v2 does not reside in system memory and cannot be eliminated by restarting an already
infected machine did not eliminate the warm.
In IIS server machines, the worm exists in .dll indexing file, a fact that made it possible for the
worm to run on the highest system privileges. It was easily possible fo the worm to do whatever
it wanted with a system from this level.
The worm has two parts- exploit and payload. The exploit represents sequence of actions that
enabled the worm to take advantage of security vulnerabilities by performing HTTP Get requests
through port 80 on the IIS and looking for the default.ida file. The file search is then followed by
a code to cause buffer overflow and execute attacks. Where the default.ida file was not available,
the worm made calls idd.dll file running system privileges, enabling it to jump to bypass the
unfound ida.dll file.
During the payload phase, system services crash and restart. During this restart, the worm
propagate itself through the internet by performing IP range scans, deface web pages and
launches DoS attacks.
Mitigating Against Code Red
Computer security analysts recommend that any computer systems should be patched regardless
of whether they are Code Red infected or not. An ideal solution would be to patch the system
before the infection takes place. Security experts also indicate that this attack could have been
easily mitigated should have Windows IIS server machines users installed the patch updates and
hot-fixes in time. Other techniques include utilizing websites and newsletters that provide
comprehensive information that could be helpful in fixing security flaws in computer systems.
Microsoft also recommends a series of steps as follows:
a backdoor and causing an auto-reboot in a machine. Unlike other versions of Code Red, code
Red v2 does not reside in system memory and cannot be eliminated by restarting an already
infected machine did not eliminate the warm.
In IIS server machines, the worm exists in .dll indexing file, a fact that made it possible for the
worm to run on the highest system privileges. It was easily possible fo the worm to do whatever
it wanted with a system from this level.
The worm has two parts- exploit and payload. The exploit represents sequence of actions that
enabled the worm to take advantage of security vulnerabilities by performing HTTP Get requests
through port 80 on the IIS and looking for the default.ida file. The file search is then followed by
a code to cause buffer overflow and execute attacks. Where the default.ida file was not available,
the worm made calls idd.dll file running system privileges, enabling it to jump to bypass the
unfound ida.dll file.
During the payload phase, system services crash and restart. During this restart, the worm
propagate itself through the internet by performing IP range scans, deface web pages and
launches DoS attacks.
Mitigating Against Code Red
Computer security analysts recommend that any computer systems should be patched regardless
of whether they are Code Red infected or not. An ideal solution would be to patch the system
before the infection takes place. Security experts also indicate that this attack could have been
easily mitigated should have Windows IIS server machines users installed the patch updates and
hot-fixes in time. Other techniques include utilizing websites and newsletters that provide
comprehensive information that could be helpful in fixing security flaws in computer systems.
Microsoft also recommends a series of steps as follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Security Analysis 5
Access processes running in a system by clicking Ctrl+Alt+Del and selecting task manager
Determine whether a system is infected by checking if a website’s home page is defaced. It
should be noted that defacing last only ten hours upon which the system reverts back to the
original state.
Where the system is already infected but no compromise has taken place yet, Code Red Clean
Up tool can be installed and run to eliminate the worm. The Clean Up tool is a small utility that
is developed and programmed to eliminate effects of the Code Red v2 worm in webservers. This
tool can also be used to remove any mappings made and generated by the worm in network
system. According to Microsoft, the best way to recover from the attack is to reformat the drive,
reinstall it, the software and any other security patch.
Network configurations and management should also be critically considered. Network host
devices and machines should be protected by use of a Demilitarized Zone (DMZ), access
controls and firewall applications. Web servers can be protected against the attack by setting up a
remote proxy server to control access to TCP port 80. This way, all web content generated within
a network system is then cached on the proxy server making it hard for hackers and attackers to
gain access to network system.
References
Berghel, H. (2001). The code red worm. Communications of the ACM, 44(12), 15-19.
Moore, D., & Colleen, S. (2002). Code-Red: a case study on the spread and victims of an
Internet worm. Proceedings of the 2nd ACM SIGCOMM Workshop on Internet
measurment (pp. 273-284). ACM.
Access processes running in a system by clicking Ctrl+Alt+Del and selecting task manager
Determine whether a system is infected by checking if a website’s home page is defaced. It
should be noted that defacing last only ten hours upon which the system reverts back to the
original state.
Where the system is already infected but no compromise has taken place yet, Code Red Clean
Up tool can be installed and run to eliminate the worm. The Clean Up tool is a small utility that
is developed and programmed to eliminate effects of the Code Red v2 worm in webservers. This
tool can also be used to remove any mappings made and generated by the worm in network
system. According to Microsoft, the best way to recover from the attack is to reformat the drive,
reinstall it, the software and any other security patch.
Network configurations and management should also be critically considered. Network host
devices and machines should be protected by use of a Demilitarized Zone (DMZ), access
controls and firewall applications. Web servers can be protected against the attack by setting up a
remote proxy server to control access to TCP port 80. This way, all web content generated within
a network system is then cached on the proxy server making it hard for hackers and attackers to
gain access to network system.
References
Berghel, H. (2001). The code red worm. Communications of the ACM, 44(12), 15-19.
Moore, D., & Colleen, S. (2002). Code-Red: a case study on the spread and victims of an
Internet worm. Proceedings of the 2nd ACM SIGCOMM Workshop on Internet
measurment (pp. 273-284). ACM.
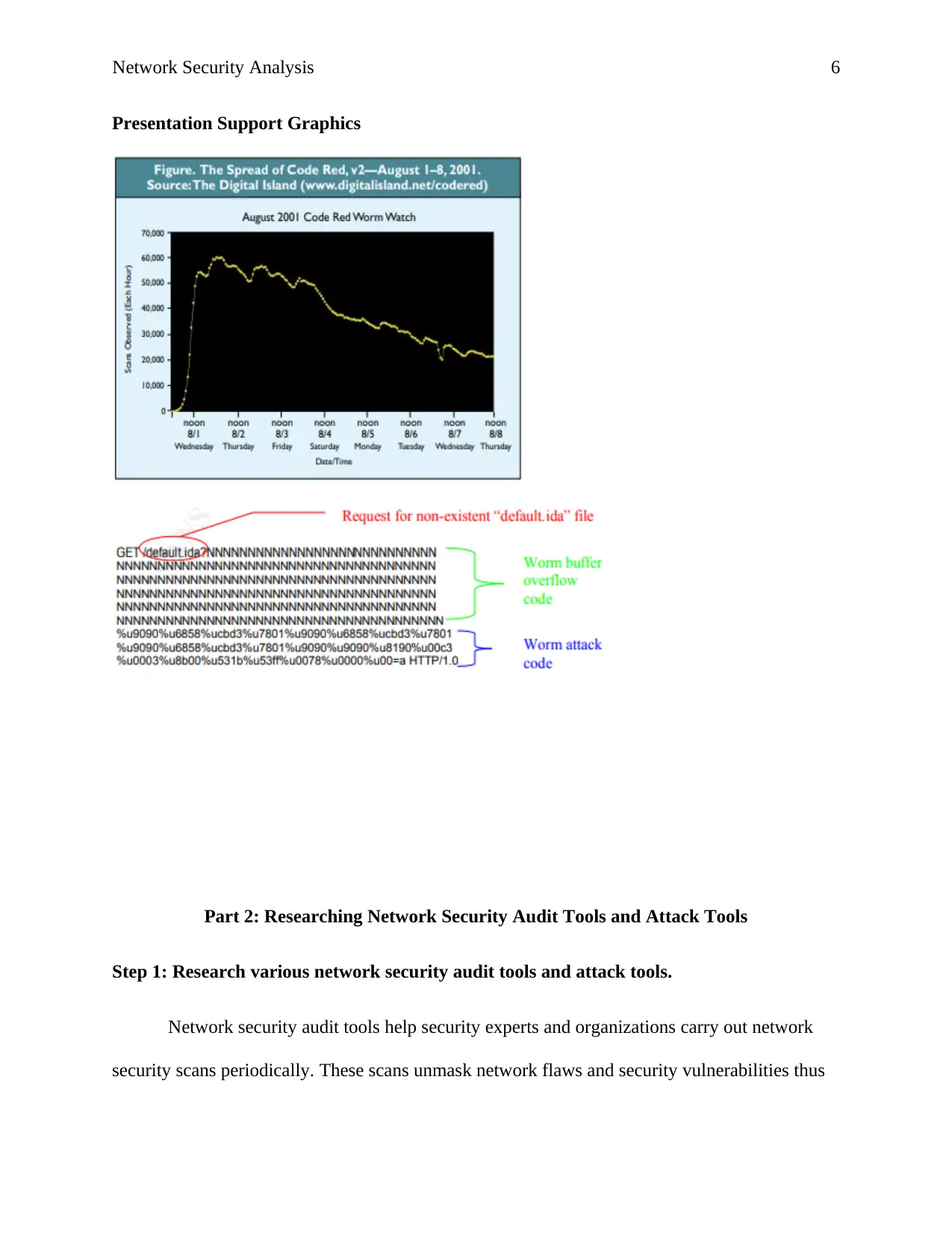
Network Security Analysis 6
Presentation Support Graphics
Part 2: Researching Network Security Audit Tools and Attack Tools
Step 1: Research various network security audit tools and attack tools.
Network security audit tools help security experts and organizations carry out network
security scans periodically. These scans unmask network flaws and security vulnerabilities thus
Presentation Support Graphics
Part 2: Researching Network Security Audit Tools and Attack Tools
Step 1: Research various network security audit tools and attack tools.
Network security audit tools help security experts and organizations carry out network
security scans periodically. These scans unmask network flaws and security vulnerabilities thus
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Security Analysis 7
simplifying network administration operations by offering monitoring services, checking for
security compliance and detecting and thwarting attacks on network. Peripheral security tools-
antivirus, IDS, IPS and firewalls are used to maintain safe networking system environment while
such utilities as mappers, packet analyzers and port scanners among others are useful in texting
network for vulnerabilities and weaknesses that hackers can exploit to launch attacks on
computer network systems.
Some network audit and attack tools identified in this research include Cisco Security
Device Manager, Microsoft Baseline Security Analyzer (MBSA), and Security Audit Wizard,
Sourceforge network security analysis tool (NSA) and Solarwinds Engineering Toolset among
others. Network attacker tools identified are Cain and Abel, Netcat, John and Ripper, Nessus,
DSniff as well as WebCrack attacker tool.
Step 2: Fill in the following form for the network security audit tool/attack tool selected
Nam of the tool The Cisco Security Device Manager
Developer Cisco Inc.
type of tool- GUI or character based Works on Cisco routers, Graphical user
interface based.
One does not require the command line
interface knowledge to deploy, configure and
monitor.
Where used- network device or host The tools is used on routers series 830, 3700,
3600, and 2600xm- network devices.
Cost The application is free to download.
It is an ideal security management tool for
simplifying network administration operations by offering monitoring services, checking for
security compliance and detecting and thwarting attacks on network. Peripheral security tools-
antivirus, IDS, IPS and firewalls are used to maintain safe networking system environment while
such utilities as mappers, packet analyzers and port scanners among others are useful in texting
network for vulnerabilities and weaknesses that hackers can exploit to launch attacks on
computer network systems.
Some network audit and attack tools identified in this research include Cisco Security
Device Manager, Microsoft Baseline Security Analyzer (MBSA), and Security Audit Wizard,
Sourceforge network security analysis tool (NSA) and Solarwinds Engineering Toolset among
others. Network attacker tools identified are Cain and Abel, Netcat, John and Ripper, Nessus,
DSniff as well as WebCrack attacker tool.
Step 2: Fill in the following form for the network security audit tool/attack tool selected
Nam of the tool The Cisco Security Device Manager
Developer Cisco Inc.
type of tool- GUI or character based Works on Cisco routers, Graphical user
interface based.
One does not require the command line
interface knowledge to deploy, configure and
monitor.
Where used- network device or host The tools is used on routers series 830, 3700,
3600, and 2600xm- network devices.
Cost The application is free to download.
It is an ideal security management tool for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Security Analysis 8
both small and medium-sized organizations
since SDM allows device-by-device security
implementations while eliminating the need
of purchasing the software.
Can easily be deployed even by non-expert
net admins and centrally managed. These
features/capabilities saves on costs in terms of
human resource and time.
Description of key features and capabilities of product or tool
Cisco’s SDM Audit wizard tool refers to a web-based network management tool that is
embedded within network routers. The tool simplifies network security configurations by use
of wizards that allow clients to quickly deploy, configure and monitor their networks without
necessarily requiring CLI knowledge (Cisco, 2007). This audit tool is:
Highly flexible and easy to use- seurity features can easily be configured on a device-by-
device basis. Such a configuration creates a proactive network performance monitoring
environment. Its ease of use is further complemented by the fact that the tool is GUI-based
rather than CLI.
The intelligent wizards used in the tool provide step-by-step guidance to users during initial
configurations for configuring Wan interfaces, virtual private networks (VPN) as well as local
area network. The wizards too have the capability of detecting incorrect network
configurations and propose remedial actions.
CISCO SDM product provides advanced security features than those of Cisco’s IOS software.
Professionals and network experts are therefore in a position to review all commands
both small and medium-sized organizations
since SDM allows device-by-device security
implementations while eliminating the need
of purchasing the software.
Can easily be deployed even by non-expert
net admins and centrally managed. These
features/capabilities saves on costs in terms of
human resource and time.
Description of key features and capabilities of product or tool
Cisco’s SDM Audit wizard tool refers to a web-based network management tool that is
embedded within network routers. The tool simplifies network security configurations by use
of wizards that allow clients to quickly deploy, configure and monitor their networks without
necessarily requiring CLI knowledge (Cisco, 2007). This audit tool is:
Highly flexible and easy to use- seurity features can easily be configured on a device-by-
device basis. Such a configuration creates a proactive network performance monitoring
environment. Its ease of use is further complemented by the fact that the tool is GUI-based
rather than CLI.
The intelligent wizards used in the tool provide step-by-step guidance to users during initial
configurations for configuring Wan interfaces, virtual private networks (VPN) as well as local
area network. The wizards too have the capability of detecting incorrect network
configurations and propose remedial actions.
CISCO SDM product provides advanced security features than those of Cisco’s IOS software.
Professionals and network experts are therefore in a position to review all commands

Network Security Analysis 9
generated by the tool before parsing on the changes to the router.
The tool also allows many users to configure and remotely access and monitor their devices
using the Secure Sockets Layer (SSL).
SDM works by running a series running some predefined checklists as a way of assessing a
host devices’ security configurations. It then generate recommendations that can be selectively
applied by security admins based on its findings. The tool also allows one-step route lockdown
option by configuring the device with a set of special security features as recommended.
The audit feature examines current security configurations and give best recommendations
thus ensuring network security. The audit examines running and current configurations against
organizational predefined security settings, lists all problems as identified as their appropriate
solutions, allows network security experts to select which problems to first fix based on their
priority indexes, and delivers command necessary and appropriate to configure the selected
security problem. The SDM wizard acts as an intelligent ‘agent’ that detect these
misconfigurations and propose solutions based on the predefined security settings.
The online help interface provides complete background information, step-by-step procedures
that are used to enter data in the SDM application windows. An online glossary included in the
web interface of the utility program provides all networking security terms and definitions that
users might need in their interactions with the security tool.
The product also includes an advanced mode that is used to quickly configure network security
settings. This gives experienced network professionals review all generated by the SDM
before writing such changes to the device. Features such as access control lists editors provide
a means to quickly fine-tune security configurations.
The host devices can also be configured and monitored remotely. This is made possible
generated by the tool before parsing on the changes to the router.
The tool also allows many users to configure and remotely access and monitor their devices
using the Secure Sockets Layer (SSL).
SDM works by running a series running some predefined checklists as a way of assessing a
host devices’ security configurations. It then generate recommendations that can be selectively
applied by security admins based on its findings. The tool also allows one-step route lockdown
option by configuring the device with a set of special security features as recommended.
The audit feature examines current security configurations and give best recommendations
thus ensuring network security. The audit examines running and current configurations against
organizational predefined security settings, lists all problems as identified as their appropriate
solutions, allows network security experts to select which problems to first fix based on their
priority indexes, and delivers command necessary and appropriate to configure the selected
security problem. The SDM wizard acts as an intelligent ‘agent’ that detect these
misconfigurations and propose solutions based on the predefined security settings.
The online help interface provides complete background information, step-by-step procedures
that are used to enter data in the SDM application windows. An online glossary included in the
web interface of the utility program provides all networking security terms and definitions that
users might need in their interactions with the security tool.
The product also includes an advanced mode that is used to quickly configure network security
settings. This gives experienced network professionals review all generated by the SDM
before writing such changes to the device. Features such as access control lists editors provide
a means to quickly fine-tune security configurations.
The host devices can also be configured and monitored remotely. This is made possible
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Security Analysis 10
through Secure Socket layer (SSL) powered connections. SSL provides secure remote
connection between a user’s web browser’s interface and that of the host network device.in a
branch office set up, Cisco SDM-enabled devices are configured and monitored from
corporate headquarters thus reducing the need for the provision of IT support services at the
branch offices.
Basic router configurations such as configuring LAN and WAN interfaces can easily be
performed using the LAN configuration wizard, from which IP address and subnet masks can
easily be assigned. Additionally, dynamic host configuration protocol (DHCP) can be enabled
or disabled from WAN/LAN interfaces.
The T1/E1, xDSL and Ethernet interfaces can easily be assigned IP addresses either statically
or dynamically. Frame relay connections, HDLC encapsulation, PPP and any other serial
connections are easily be implemented. PPP, local link management, and frame relay
connections configured via Cisco’s SDM allow user authentication via DLCI configured
parameters. Common routing protocols such as open shortest path first, enhanced interior
gateway routing protocol and rooting information protocol can also be configured via SDM
interface.
The tools monitor mode creates an overview through which status and performance metrics
such a new software release, CPU and memory usages, and interface status of a given host
device. One can easily tell the number of attempts made by an unauthorized user to access the
network- remotely or locally in the firewall devices’ log files. The tool also allows monitoring
of any Virtual Private Network (VPN) – IP Security tunnels and respective status.
References
Router, C. Security Device Manager 2.4 User's Guide, Ch. 34, 2007, 32 pgs., Cisco
through Secure Socket layer (SSL) powered connections. SSL provides secure remote
connection between a user’s web browser’s interface and that of the host network device.in a
branch office set up, Cisco SDM-enabled devices are configured and monitored from
corporate headquarters thus reducing the need for the provision of IT support services at the
branch offices.
Basic router configurations such as configuring LAN and WAN interfaces can easily be
performed using the LAN configuration wizard, from which IP address and subnet masks can
easily be assigned. Additionally, dynamic host configuration protocol (DHCP) can be enabled
or disabled from WAN/LAN interfaces.
The T1/E1, xDSL and Ethernet interfaces can easily be assigned IP addresses either statically
or dynamically. Frame relay connections, HDLC encapsulation, PPP and any other serial
connections are easily be implemented. PPP, local link management, and frame relay
connections configured via Cisco’s SDM allow user authentication via DLCI configured
parameters. Common routing protocols such as open shortest path first, enhanced interior
gateway routing protocol and rooting information protocol can also be configured via SDM
interface.
The tools monitor mode creates an overview through which status and performance metrics
such a new software release, CPU and memory usages, and interface status of a given host
device. One can easily tell the number of attempts made by an unauthorized user to access the
network- remotely or locally in the firewall devices’ log files. The tool also allows monitoring
of any Virtual Private Network (VPN) – IP Security tunnels and respective status.
References
Router, C. Security Device Manager 2.4 User's Guide, Ch. 34, 2007, 32 pgs., Cisco
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Security Analysis 11
Systems. Inc., San Jose, CA.
Reflection
1. What is the impact of network attacks on the operation of an organization? What are
some key steps organizations can take to help protect their networks and resources?
Code Red and all its variants (versions) are massive attacks that affect large network
portions are rare due to continued mitigation strategies put in place by large organizations.
Smaller attacks targeted at smaller organizations and aimed at stealing data are more common.
Networking devices- both host and end user devices are vulnerable to attacks, which exploit
security vulnerabilities and are easily propagated through the internet.
Security vulnerability tools help security experts identify system vulnerabilities and take
corrective measures before threats escalates to risks. Intrusion detection and prevention systems,
firewalls, network device hardening, encryption and end-point protection can additionally be
used to complement network security settings.
2. What steps can you take to protect your own PC or laptop computer?
To ensure that my personal computer is protected, I would always seek to update my
operating system and any other installed applications updated by using respective software
patches, personal firewall applications, having strong passwords configured to secure my
computer system, set my screensaver to auto-timeout and require passwords when ‘waking up,’
encrypting all important files and password-protecting them besides making them read-only files,
and keeping a backup system for my PC.
Systems. Inc., San Jose, CA.
Reflection
1. What is the impact of network attacks on the operation of an organization? What are
some key steps organizations can take to help protect their networks and resources?
Code Red and all its variants (versions) are massive attacks that affect large network
portions are rare due to continued mitigation strategies put in place by large organizations.
Smaller attacks targeted at smaller organizations and aimed at stealing data are more common.
Networking devices- both host and end user devices are vulnerable to attacks, which exploit
security vulnerabilities and are easily propagated through the internet.
Security vulnerability tools help security experts identify system vulnerabilities and take
corrective measures before threats escalates to risks. Intrusion detection and prevention systems,
firewalls, network device hardening, encryption and end-point protection can additionally be
used to complement network security settings.
2. What steps can you take to protect your own PC or laptop computer?
To ensure that my personal computer is protected, I would always seek to update my
operating system and any other installed applications updated by using respective software
patches, personal firewall applications, having strong passwords configured to secure my
computer system, set my screensaver to auto-timeout and require passwords when ‘waking up,’
encrypting all important files and password-protecting them besides making them read-only files,
and keeping a backup system for my PC.

Network Security Analysis 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





