Network Configuration Report: Design, Implementation, and Testing
VerifiedAdded on 2022/10/04
|19
|3655
|427
Report
AI Summary
This report details the design and implementation of a network solution for a UK-based company with four departments requiring individual connections and restricted functionality. The solution involves VLANs for each floor and remote systems to isolate traffic and enhance security and cost-effectiveness. The report includes an IP table outlining network addresses and subnet masks for each department, along with logical network designs and configuration details for PCs, routers, VLANs, DNS, mail, and wireless settings. It covers ping tests and descriptions of network components like NICs, switches, and protocols such as routing, DNS, and spanning tree. The report discusses network design principles, including the use of a star topology and LAN characteristics, and concludes with references to relevant literature. The solution utilizes Cisco Packet Tracer for network design and analysis, ensuring scalability, redundancy, performance, security, and practicality. The report also covers subnetting, wireless configurations, and various network protocols.

Running head: NETWORK CONFIGURATION
Network configuration
Name of the Student
Name of the university
Author note
Network configuration
Name of the Student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
IP Table........................................................................................................................................................3
Network design...........................................................................................................................................4
Configuration...............................................................................................................................................6
PCS Configuration....................................................................................................................................6
Router configuration...............................................................................................................................7
VLAN Configuration.................................................................................................................................7
DNS Configuration.................................................................................................................................10
Mail configuration.................................................................................................................................11
Wireless configuration...........................................................................................................................11
Ping Test....................................................................................................................................................12
Description................................................................................................................................................13
Network Interface Card (NIC)....................................................................................................................14
Switch........................................................................................................................................................14
Layer 1...................................................................................................................................................14
Layer 2...................................................................................................................................................15
Layer 3...................................................................................................................................................15
Subnetting.................................................................................................................................................15
Wireless.....................................................................................................................................................16
Network protocols used............................................................................................................................16
Routing..................................................................................................................................................16
Domain name system............................................................................................................................16
Spanning Tree protocol.........................................................................................................................17
Hot standby router protocol..................................................................................................................17
File transfer protocol.............................................................................................................................17
Simple mail transfer protocol................................................................................................................17
Conclusion.................................................................................................................................................17
References.................................................................................................................................................18
Introduction.................................................................................................................................................3
IP Table........................................................................................................................................................3
Network design...........................................................................................................................................4
Configuration...............................................................................................................................................6
PCS Configuration....................................................................................................................................6
Router configuration...............................................................................................................................7
VLAN Configuration.................................................................................................................................7
DNS Configuration.................................................................................................................................10
Mail configuration.................................................................................................................................11
Wireless configuration...........................................................................................................................11
Ping Test....................................................................................................................................................12
Description................................................................................................................................................13
Network Interface Card (NIC)....................................................................................................................14
Switch........................................................................................................................................................14
Layer 1...................................................................................................................................................14
Layer 2...................................................................................................................................................15
Layer 3...................................................................................................................................................15
Subnetting.................................................................................................................................................15
Wireless.....................................................................................................................................................16
Network protocols used............................................................................................................................16
Routing..................................................................................................................................................16
Domain name system............................................................................................................................16
Spanning Tree protocol.........................................................................................................................17
Hot standby router protocol..................................................................................................................17
File transfer protocol.............................................................................................................................17
Simple mail transfer protocol................................................................................................................17
Conclusion.................................................................................................................................................17
References.................................................................................................................................................18

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Introduction
This paper is associated with the developing a network solution for a Uk based company. They had four
departments which needs individual connection and restricted functionality in order to avoid interaction
with other departments.
VLANs are made over each floor and for remote systems. This is to expel the uncontrolled
communicated traffic arriving at another system. VLAN likewise gives a layer of system security and cost
decrease alternative by sensibly isolating hosts which is associated with a similar switch (no requirement
for extra switches).
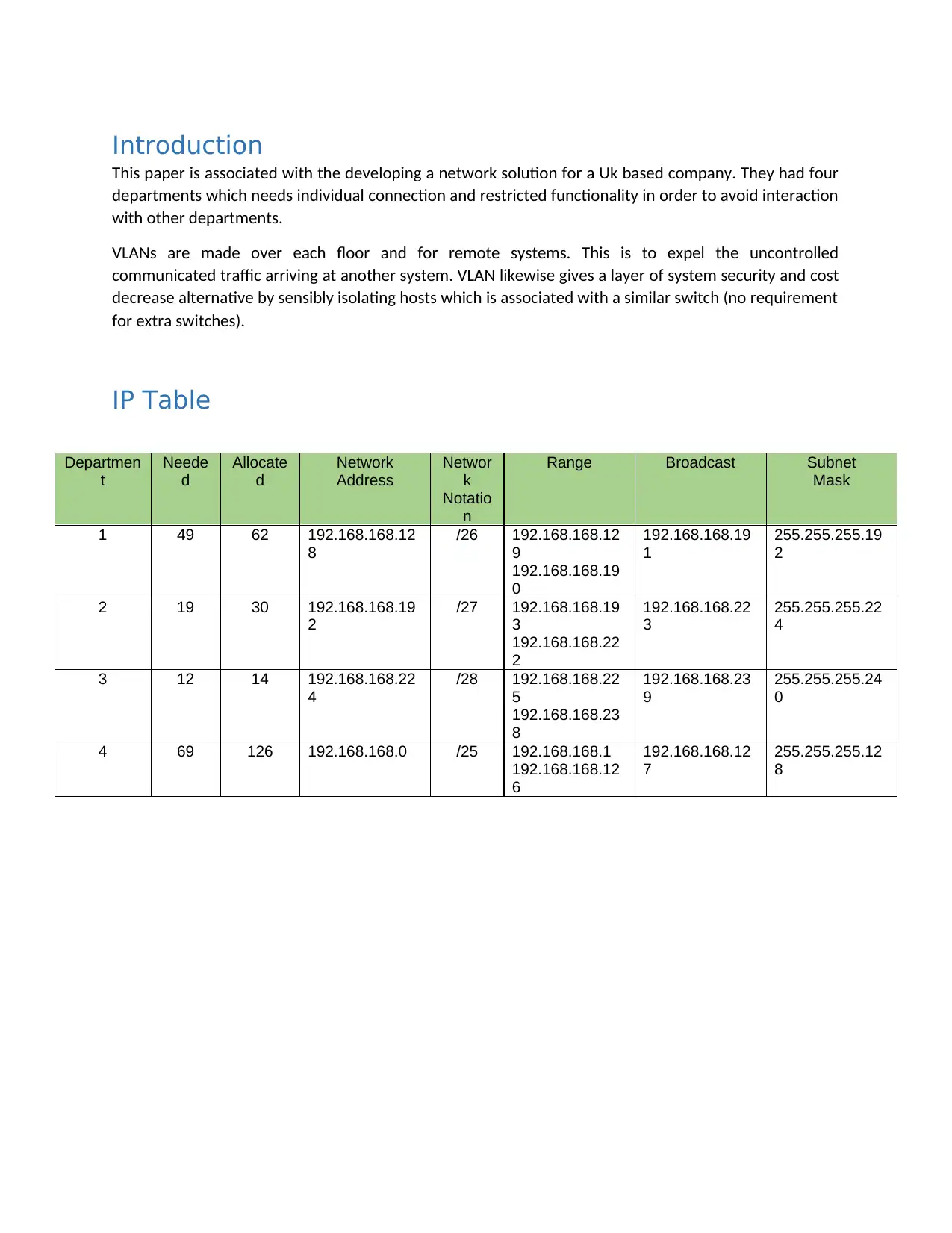
IP Table
Departmen
t
Neede
d
Allocate
d
Network
Address
Networ
k
Notatio
n
Range Broadcast Subnet
Mask
1 49 62 192.168.168.12
8
/26 192.168.168.12
9
192.168.168.19
0
192.168.168.19
1
255.255.255.19
2
2 19 30 192.168.168.19
2
/27 192.168.168.19
3
192.168.168.22
2
192.168.168.22
3
255.255.255.22
4
3 12 14 192.168.168.22
4
/28 192.168.168.22
5
192.168.168.23
8
192.168.168.23
9
255.255.255.24
0
4 69 126 192.168.168.0 /25 192.168.168.1
192.168.168.12
6
192.168.168.12
7
255.255.255.12
8
This paper is associated with the developing a network solution for a Uk based company. They had four
departments which needs individual connection and restricted functionality in order to avoid interaction
with other departments.
VLANs are made over each floor and for remote systems. This is to expel the uncontrolled
communicated traffic arriving at another system. VLAN likewise gives a layer of system security and cost
decrease alternative by sensibly isolating hosts which is associated with a similar switch (no requirement
for extra switches).
IP Table
Departmen
t
Neede
d
Allocate
d
Network
Address
Networ
k
Notatio
n
Range Broadcast Subnet
Mask
1 49 62 192.168.168.12
8
/26 192.168.168.12
9
192.168.168.19
0
192.168.168.19
1
255.255.255.19
2
2 19 30 192.168.168.19
2
/27 192.168.168.19
3
192.168.168.22
2
192.168.168.22
3
255.255.255.22
4
3 12 14 192.168.168.22
4
/28 192.168.168.22
5
192.168.168.23
8
192.168.168.23
9
255.255.255.24
0
4 69 126 192.168.168.0 /25 192.168.168.1
192.168.168.12
6
192.168.168.12
7
255.255.255.12
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
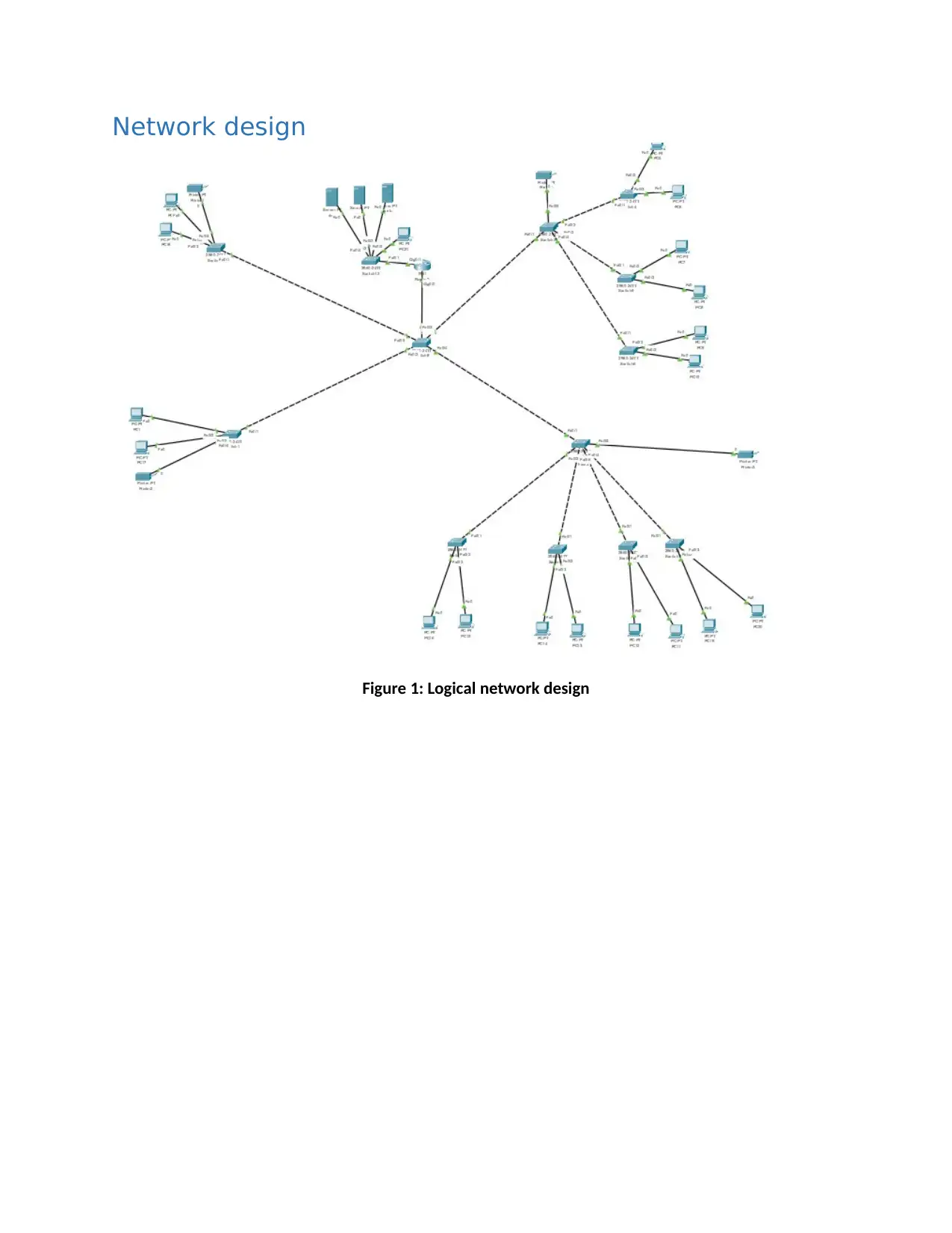
Network design
Figure 1: Logical network design
Figure 1: Logical network design
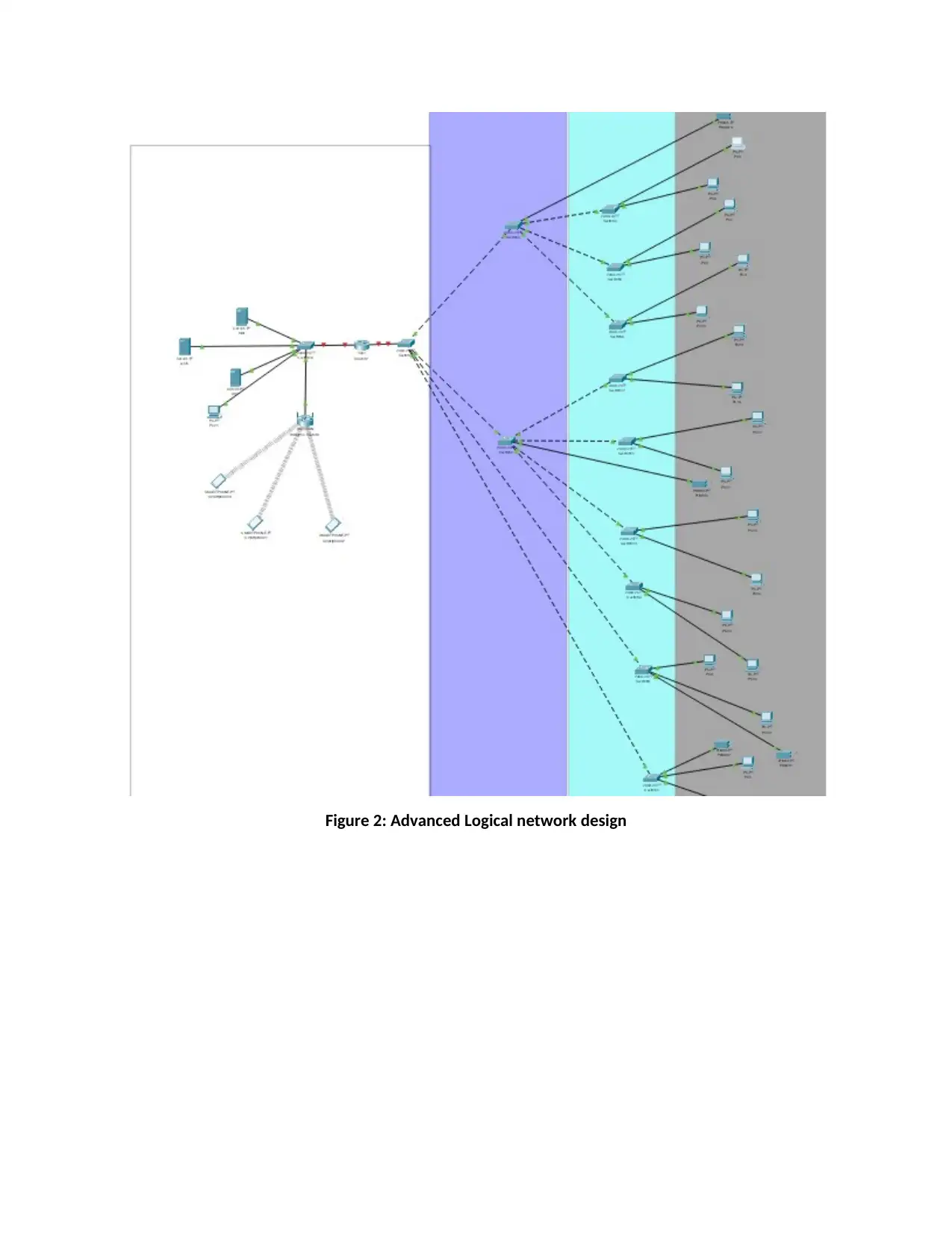
Figure 2: Advanced Logical network design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
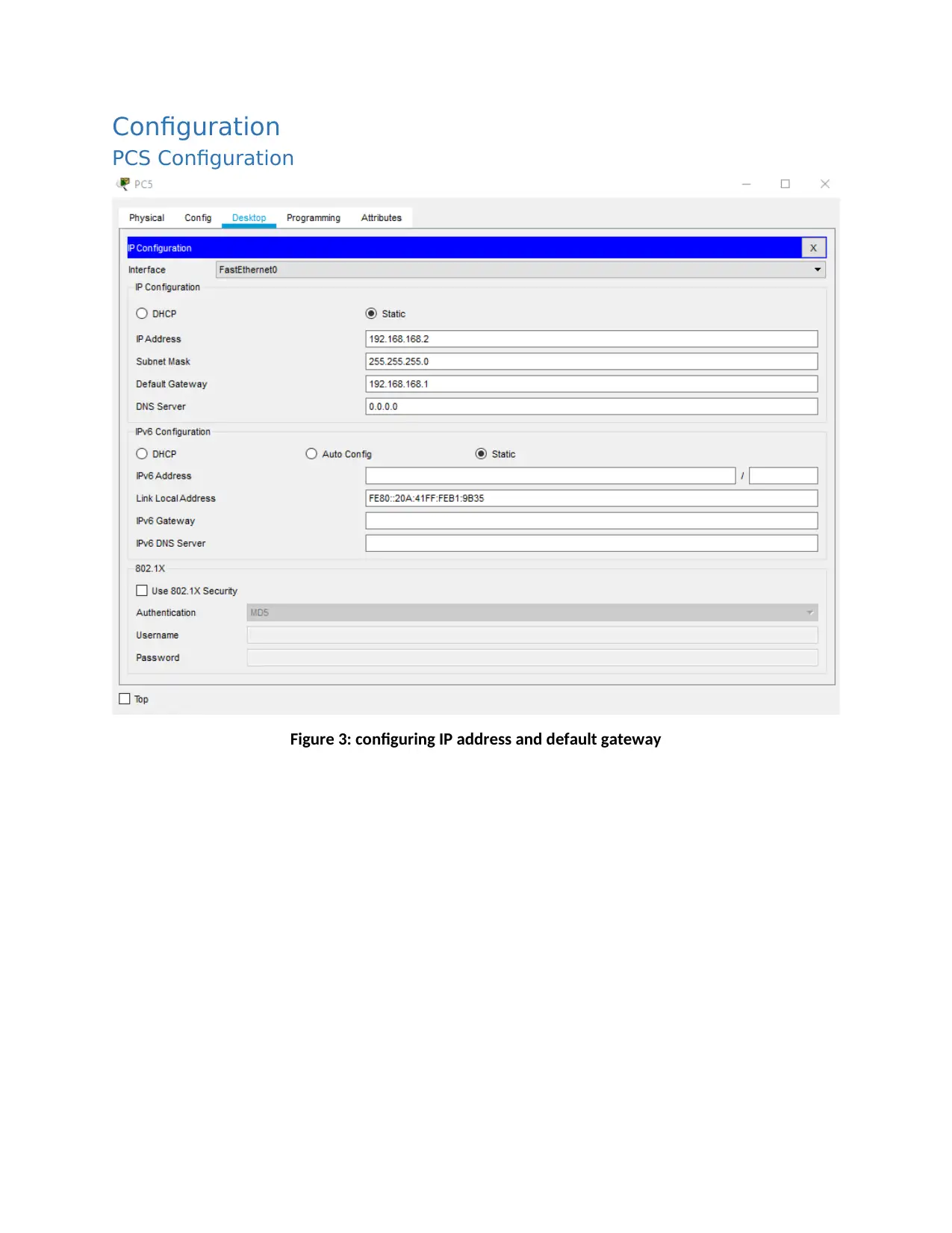
Configuration
PCS Configuration
Figure 3: configuring IP address and default gateway
PCS Configuration
Figure 3: configuring IP address and default gateway
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
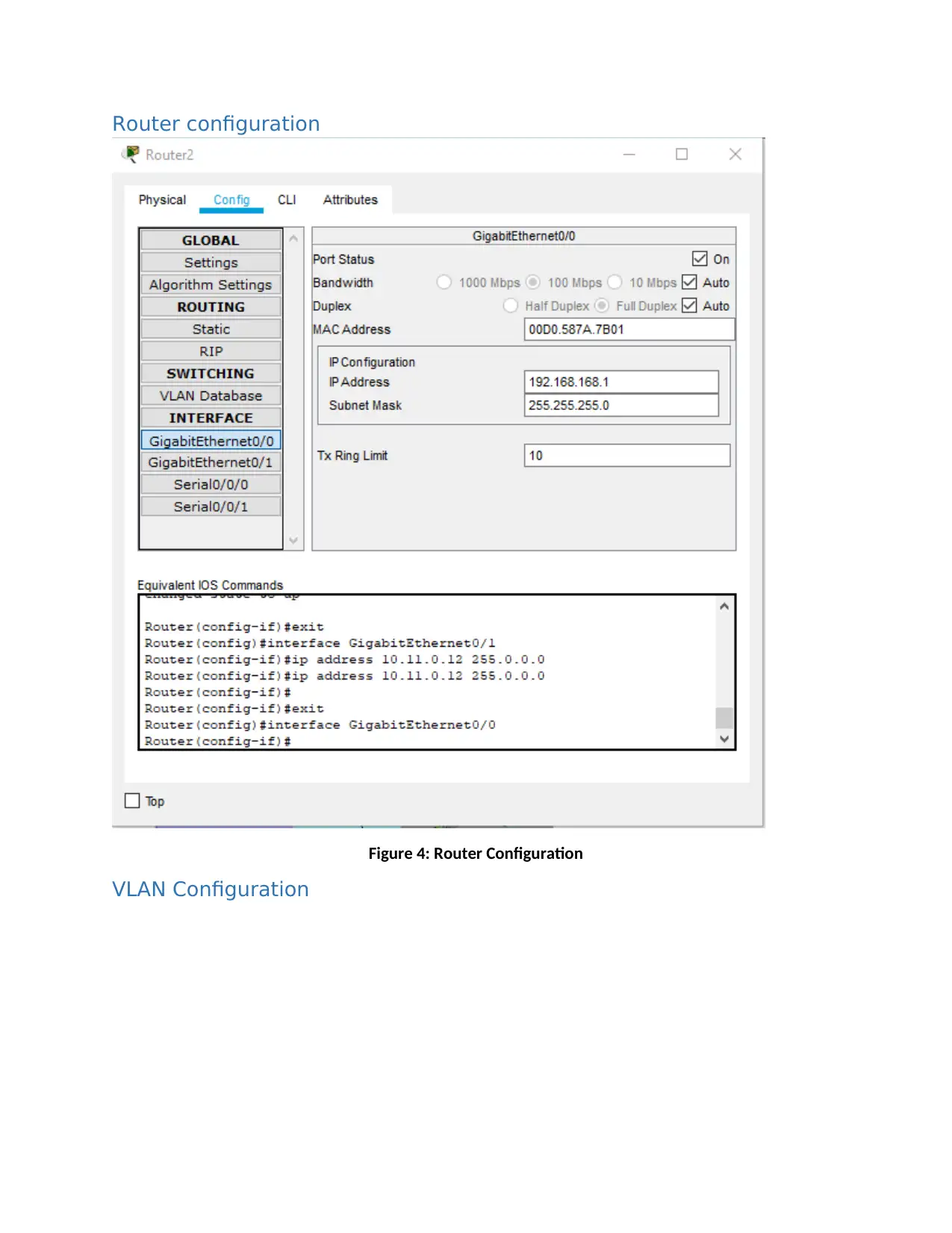
Router configuration
Figure 4: Router Configuration
VLAN Configuration
Figure 4: Router Configuration
VLAN Configuration
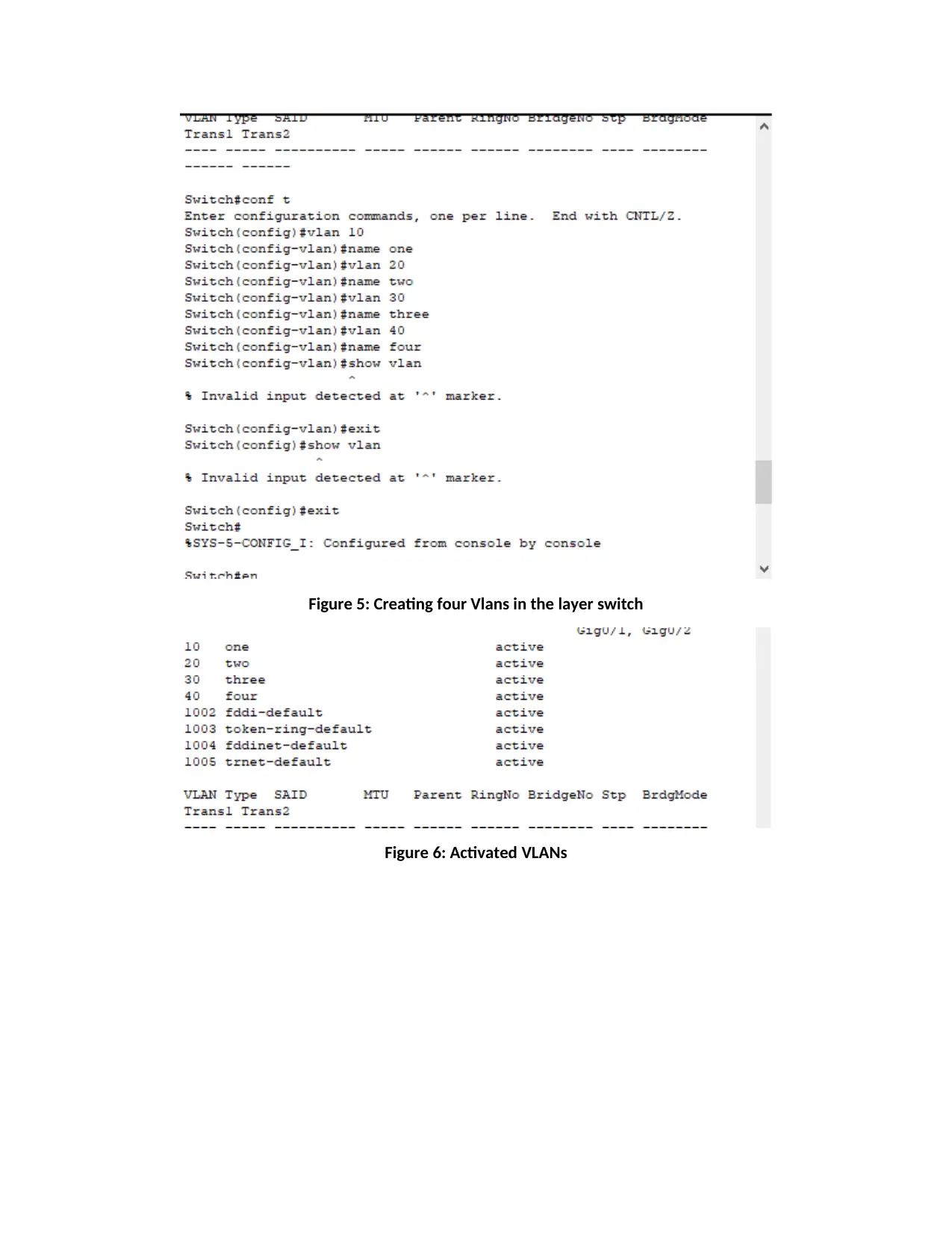
Figure 5: Creating four Vlans in the layer switch
Figure 6: Activated VLANs
Figure 6: Activated VLANs
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
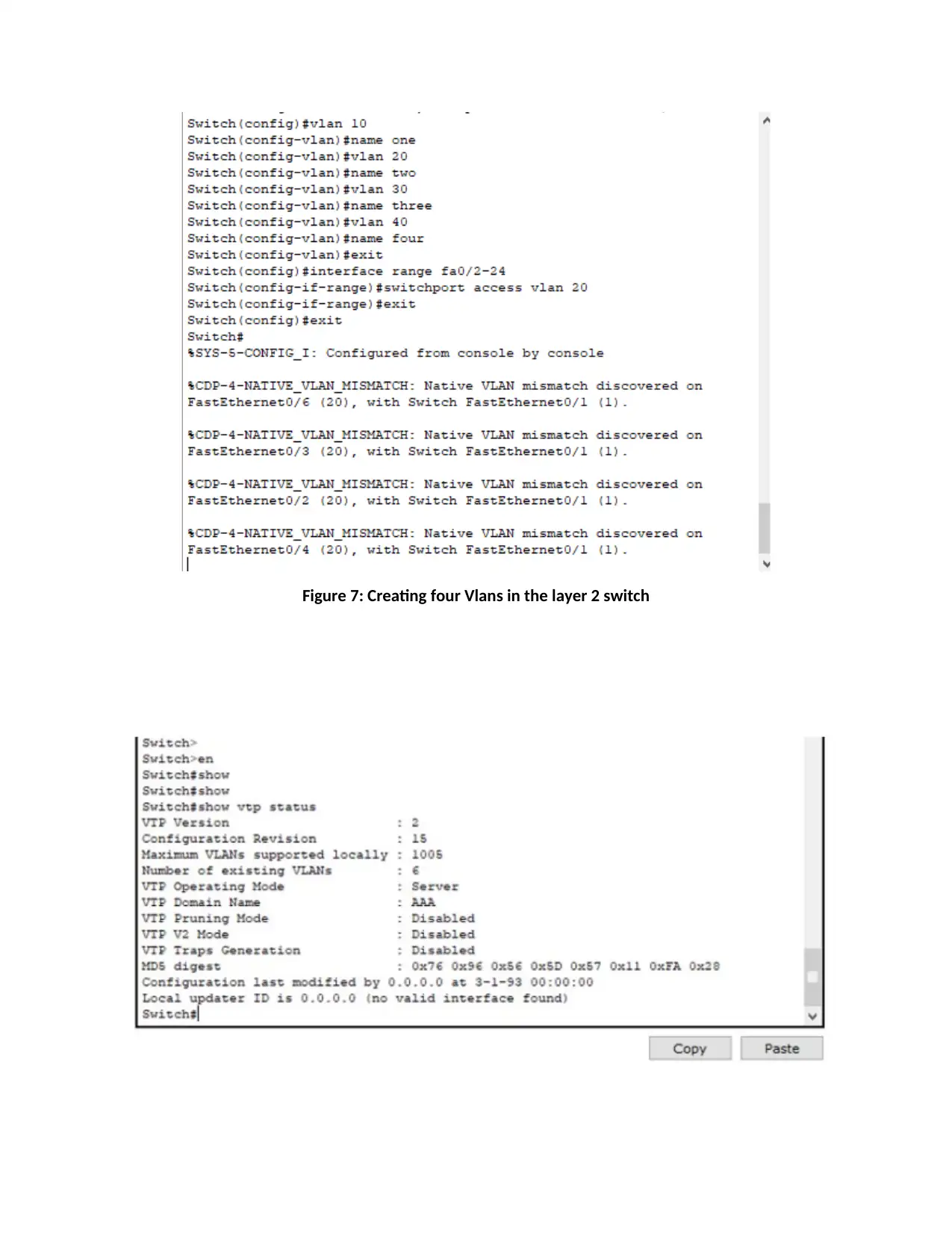
Figure 7: Creating four Vlans in the layer 2 switch
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
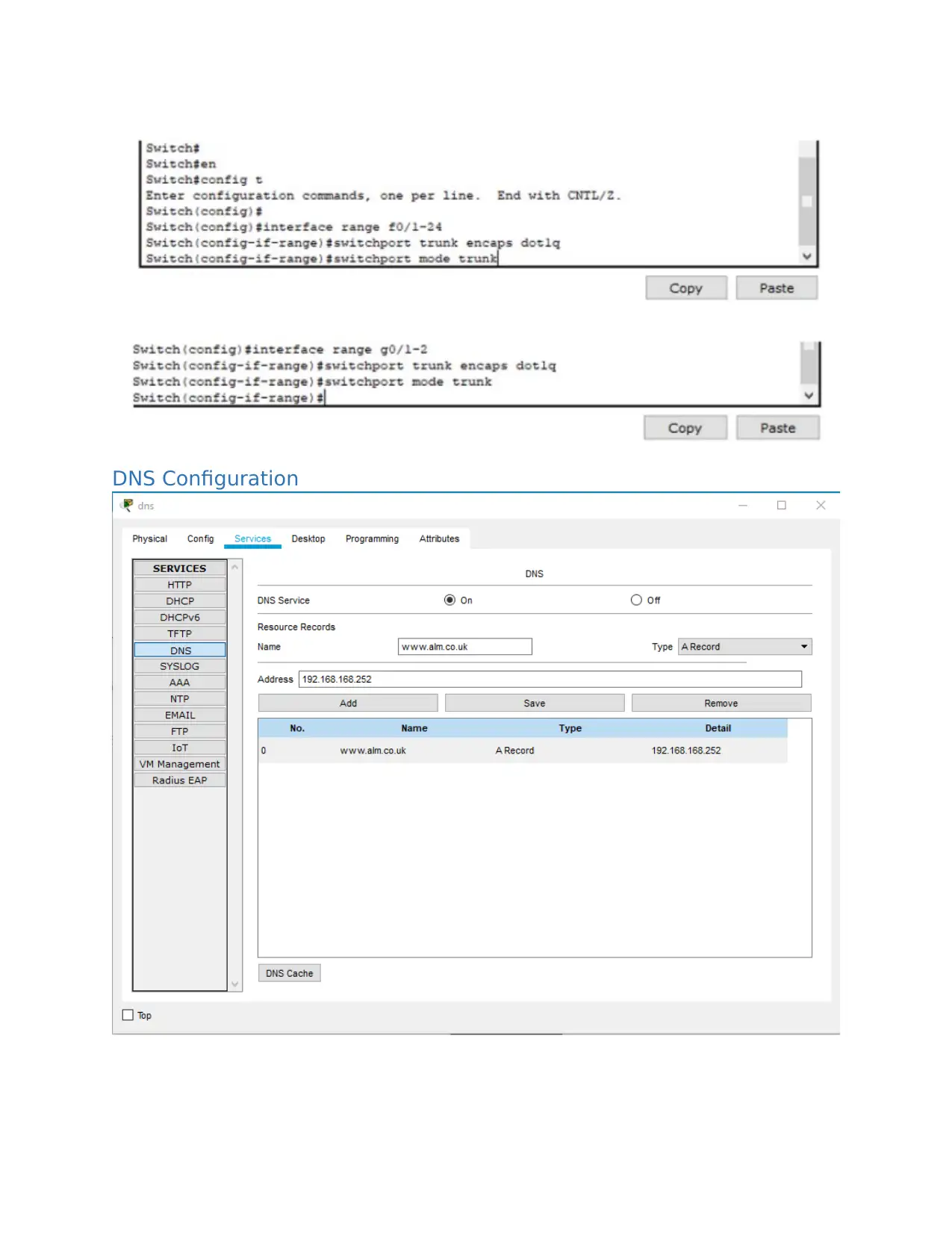
DNS Configuration
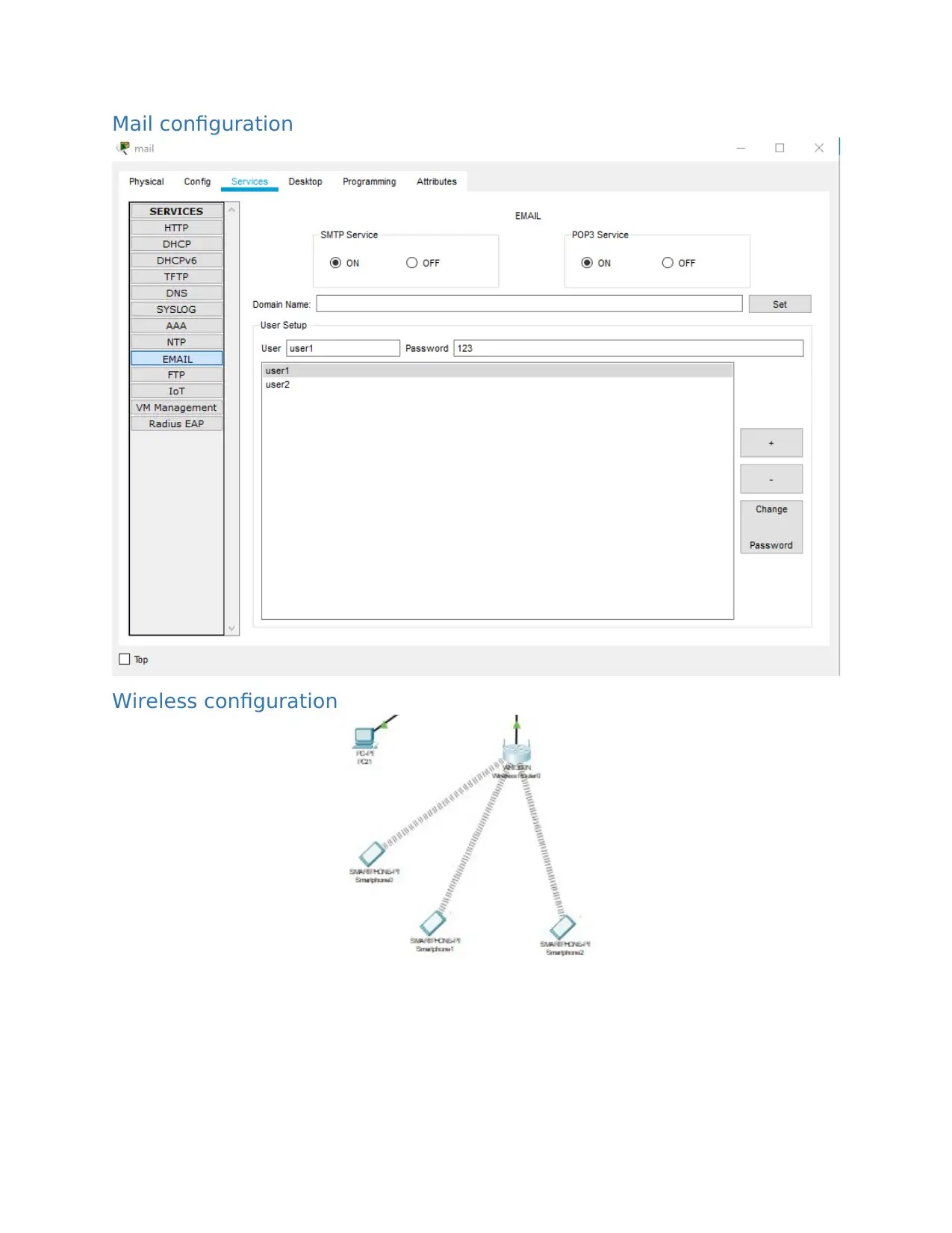
Mail configuration
Wireless configuration
Wireless configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



