Networking Theory and Simulation Exercises: IP Addressing and Routing
VerifiedAdded on 2021/04/21
|21
|2613
|32
Homework Assignment
AI Summary
This assignment delves into the core concepts of networking, encompassing IP addressing, subnetting, and routing protocols. It explores the functionalities of broadcast IP addresses, default gateways, and subnet masks, along with the operation of the Address Resolution Protocol (ARP). The assignment covers the structure of IPv4 and IPv6 routing tables, demonstrating how to recover passwords on a Cisco 2960 switch and reset it to factory settings. Part B focuses on network design and configuration, including subnetting a major network, configuring router interfaces with specific IP addresses, and setting up routing tables for communication between different branches. The document provides detailed router configurations, including hostname setup, enabling secrets, interface configurations, and the implementation of IP routes. The assignment concludes with verification of network connectivity using ping commands, demonstrating the functionality of ICMP protocol for network troubleshooting. The provided document covers the concepts using the Cisco Packet Tracer simulation tool.

Running head: THEORY AND SIMULATION EXERCISES
Assessment Item 2
Theory and Simulation Exercises
Name of the Student
Name of the University
Author’s Note
Assessment Item 2
Theory and Simulation Exercises
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
THEORY AND SIMULATION EXERCISES
Table of Contents
PART A...............................................................................................................................2
Answer to Question 1:.....................................................................................................2
Answer to Question 2:.....................................................................................................2
Answer to Question 3:.....................................................................................................4
Answer to Question 4:.....................................................................................................6
PART B...............................................................................................................................8
Answer to Question 5:.....................................................................................................8
Answer to Question 6:.....................................................................................................9
Answer to Question 7:...................................................................................................13
Answer to Question 8:...................................................................................................15
Bibliography......................................................................................................................18
THEORY AND SIMULATION EXERCISES
Table of Contents
PART A...............................................................................................................................2
Answer to Question 1:.....................................................................................................2
Answer to Question 2:.....................................................................................................2
Answer to Question 3:.....................................................................................................4
Answer to Question 4:.....................................................................................................6
PART B...............................................................................................................................8
Answer to Question 5:.....................................................................................................8
Answer to Question 6:.....................................................................................................9
Answer to Question 7:...................................................................................................13
Answer to Question 8:...................................................................................................15
Bibliography......................................................................................................................18

2
THEORY AND SIMULATION EXERCISES
PART A
Answer to Question 1:
A. Broadcast IP address – It is the IP address using which all the hosts are connected in
the network and it helps the network administrator to verify the successful transmission of the
data packets in the network (Shah et al. 2015). The DHCP and the bootstrap protocol are uses the
broadcast address for locating and transmitting the request from different servers.
B. Default Gateway – It is utilized as an access point and that is used by the computers
connected in the network to send data packets to the computer connected in another network.
We need the default gateway because without a default gateway the device in the network
cannot communicate with the device outside the network and it remains isolated.
C. A subnet mask is a number that is used for defining a range of IP address that can be
applied in a network. The subnet mask is used for breaking an address block into smaller subnet
and restricting the connection between the two subnets (Walker et al. 2016). The traffic in a
network can be limited suing the subnet because the network is partitioned.
D. As an example of the broadcasting uses on the TCP/IP is ARP on IP. It is used for
updating the routing tables with the IP address and its corresponding Mac address.
Answer to Question 2:
Defaults gateway
10.10.30.1
THEORY AND SIMULATION EXERCISES
PART A
Answer to Question 1:
A. Broadcast IP address – It is the IP address using which all the hosts are connected in
the network and it helps the network administrator to verify the successful transmission of the
data packets in the network (Shah et al. 2015). The DHCP and the bootstrap protocol are uses the
broadcast address for locating and transmitting the request from different servers.
B. Default Gateway – It is utilized as an access point and that is used by the computers
connected in the network to send data packets to the computer connected in another network.
We need the default gateway because without a default gateway the device in the network
cannot communicate with the device outside the network and it remains isolated.
C. A subnet mask is a number that is used for defining a range of IP address that can be
applied in a network. The subnet mask is used for breaking an address block into smaller subnet
and restricting the connection between the two subnets (Walker et al. 2016). The traffic in a
network can be limited suing the subnet because the network is partitioned.
D. As an example of the broadcasting uses on the TCP/IP is ARP on IP. It is used for
updating the routing tables with the IP address and its corresponding Mac address.
Answer to Question 2:
Defaults gateway
10.10.30.1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
THEORY AND SIMULATION EXERCISES
THEORY AND SIMULATION EXERCISES
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
THEORY AND SIMULATION EXERCISES
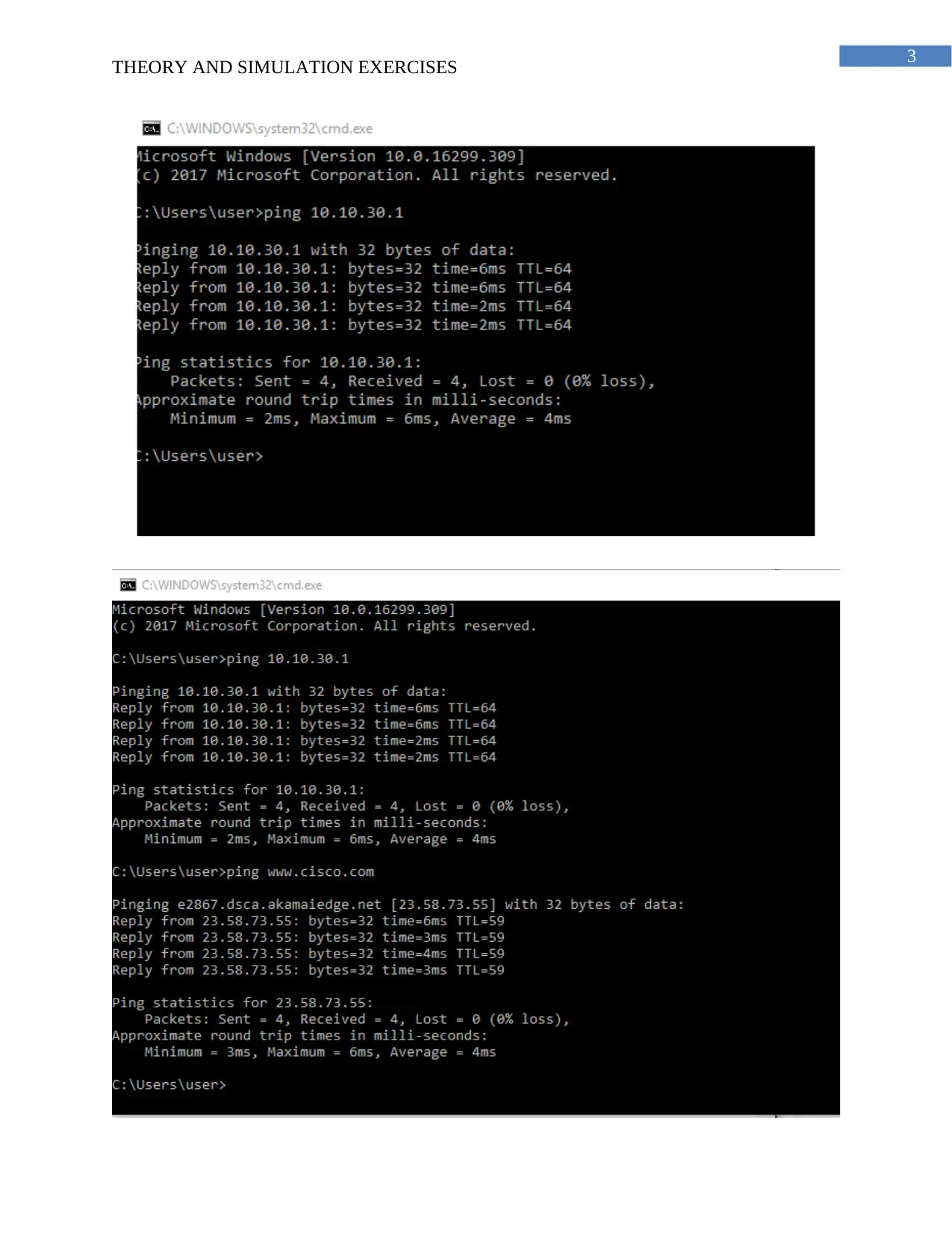
The arp command is used for the displaying and modification of the ARP cache. The
ARP cache is used for maintaining a mapping of the IP address and the MAC address for
reducing the lookup time in the network. The arp –a command is used for fetching the details of
the arp cache without the IP address.
b. The ARP stands for Address Resolution Protocol.
c. We need the ARP for translating the host address (IP address) to the MAC address and
storing the details of the host and the IP address in a tabular form (Coleman et al. 2015). It maps
the IP address to the physical address of the device.
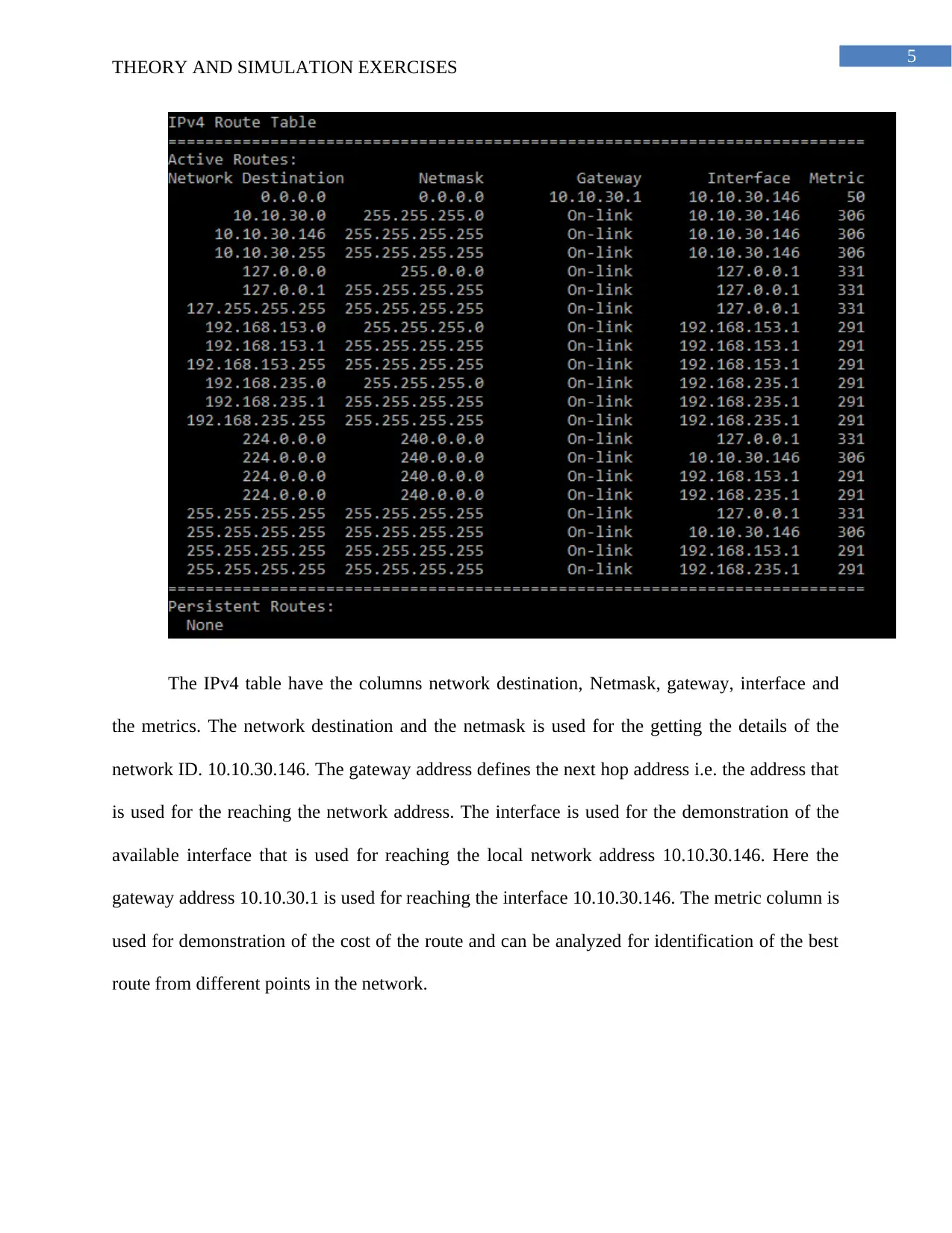
Answer to Question 3:
IPv4 Routing Table
THEORY AND SIMULATION EXERCISES
The arp command is used for the displaying and modification of the ARP cache. The
ARP cache is used for maintaining a mapping of the IP address and the MAC address for
reducing the lookup time in the network. The arp –a command is used for fetching the details of
the arp cache without the IP address.
b. The ARP stands for Address Resolution Protocol.
c. We need the ARP for translating the host address (IP address) to the MAC address and
storing the details of the host and the IP address in a tabular form (Coleman et al. 2015). It maps
the IP address to the physical address of the device.
Answer to Question 3:
IPv4 Routing Table
5
THEORY AND SIMULATION EXERCISES
The IPv4 table have the columns network destination, Netmask, gateway, interface and
the metrics. The network destination and the netmask is used for the getting the details of the
network ID. 10.10.30.146. The gateway address defines the next hop address i.e. the address that
is used for the reaching the network address. The interface is used for the demonstration of the
available interface that is used for reaching the local network address 10.10.30.146. Here the
gateway address 10.10.30.1 is used for reaching the interface 10.10.30.146. The metric column is
used for demonstration of the cost of the route and can be analyzed for identification of the best
route from different points in the network.
THEORY AND SIMULATION EXERCISES
The IPv4 table have the columns network destination, Netmask, gateway, interface and
the metrics. The network destination and the netmask is used for the getting the details of the
network ID. 10.10.30.146. The gateway address defines the next hop address i.e. the address that
is used for the reaching the network address. The interface is used for the demonstration of the
available interface that is used for reaching the local network address 10.10.30.146. Here the
gateway address 10.10.30.1 is used for reaching the interface 10.10.30.146. The metric column is
used for demonstration of the cost of the route and can be analyzed for identification of the best
route from different points in the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
THEORY AND SIMULATION EXERCISES
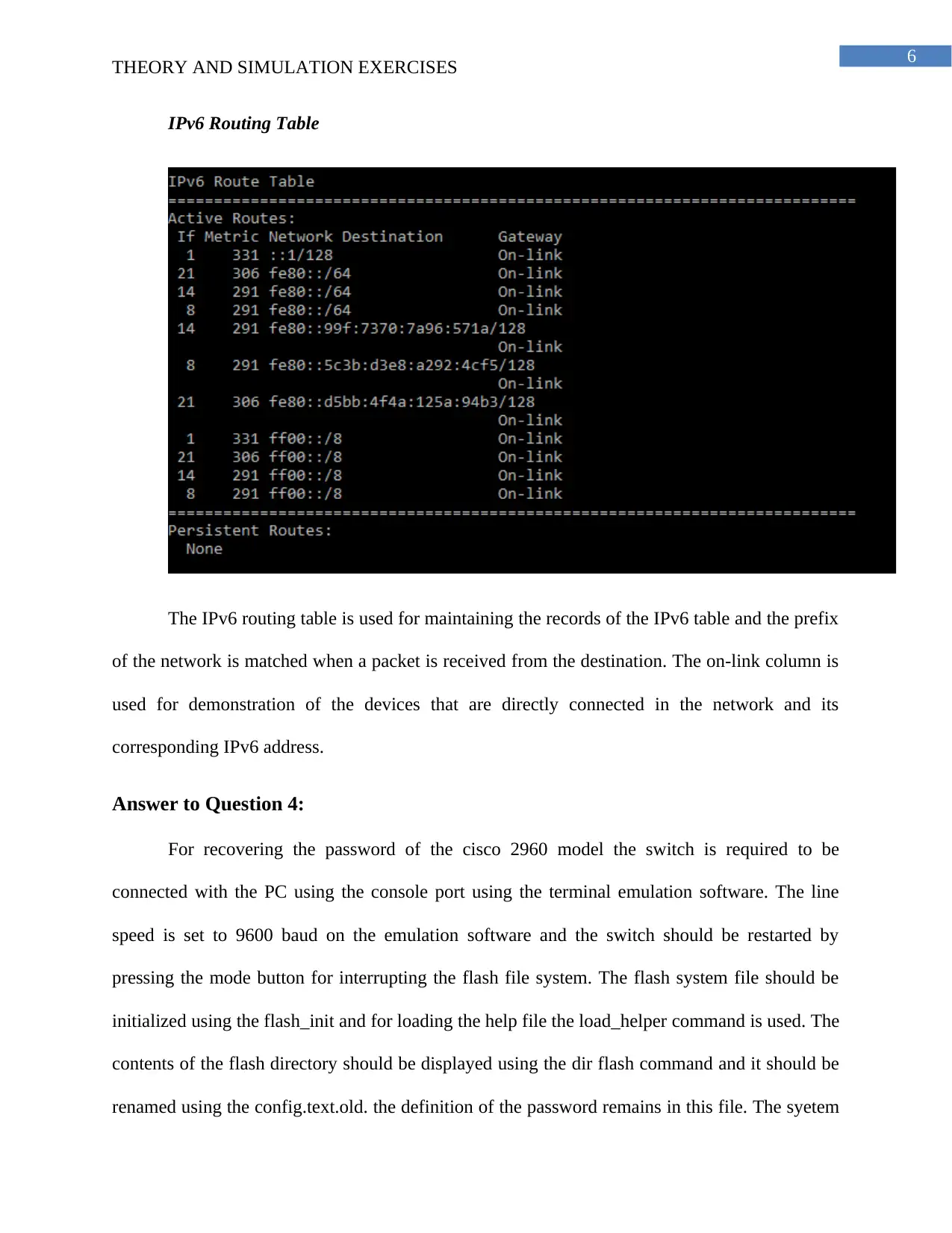
IPv6 Routing Table
The IPv6 routing table is used for maintaining the records of the IPv6 table and the prefix
of the network is matched when a packet is received from the destination. The on-link column is
used for demonstration of the devices that are directly connected in the network and its
corresponding IPv6 address.
Answer to Question 4:
For recovering the password of the cisco 2960 model the switch is required to be
connected with the PC using the console port using the terminal emulation software. The line
speed is set to 9600 baud on the emulation software and the switch should be restarted by
pressing the mode button for interrupting the flash file system. The flash system file should be
initialized using the flash_init and for loading the help file the load_helper command is used. The
contents of the flash directory should be displayed using the dir flash command and it should be
renamed using the config.text.old. the definition of the password remains in this file. The syetem
THEORY AND SIMULATION EXERCISES
IPv6 Routing Table
The IPv6 routing table is used for maintaining the records of the IPv6 table and the prefix
of the network is matched when a packet is received from the destination. The on-link column is
used for demonstration of the devices that are directly connected in the network and its
corresponding IPv6 address.
Answer to Question 4:
For recovering the password of the cisco 2960 model the switch is required to be
connected with the PC using the console port using the terminal emulation software. The line
speed is set to 9600 baud on the emulation software and the switch should be restarted by
pressing the mode button for interrupting the flash file system. The flash system file should be
initialized using the flash_init and for loading the help file the load_helper command is used. The
contents of the flash directory should be displayed using the dir flash command and it should be
renamed using the config.text.old. the definition of the password remains in this file. The syetem
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
THEORY AND SIMULATION EXERCISES
required to be booted up and when the prompt screen appears N should be selected and the
privilege EXE mode should be entered using the enable command. The configuration file should
be renamed to its original name using the command “rename flash: config.text.old and flash:
config.text”. the configuration file should be copied into the memory and using the command
“Switch# copy flash:config.text system:running-config”
Source filename [config.text]?
Destination filename [running-config]?”
The password now can be changed by entering into the global config mode.
The commands used for cleaning the old configuration of the switch and resetting it to
the factory default settings is as follows:
Step 1:
The switch should be connected with a Pc using a console cable and the boot process
should be interrupted by pressing the mode button
Step 2:
The flash system file should be initialized using the flash_init command
Step 3:
The config.text file should be deleted from the flash directory
Step 4:
If there are VLAN configuration it should be deleted by deleting the vlan.dat file present
in the flash directory.
THEORY AND SIMULATION EXERCISES
required to be booted up and when the prompt screen appears N should be selected and the
privilege EXE mode should be entered using the enable command. The configuration file should
be renamed to its original name using the command “rename flash: config.text.old and flash:
config.text”. the configuration file should be copied into the memory and using the command
“Switch# copy flash:config.text system:running-config”
Source filename [config.text]?
Destination filename [running-config]?”
The password now can be changed by entering into the global config mode.
The commands used for cleaning the old configuration of the switch and resetting it to
the factory default settings is as follows:
Step 1:
The switch should be connected with a Pc using a console cable and the boot process
should be interrupted by pressing the mode button
Step 2:
The flash system file should be initialized using the flash_init command
Step 3:
The config.text file should be deleted from the flash directory
Step 4:
If there are VLAN configuration it should be deleted by deleting the vlan.dat file present
in the flash directory.
8
THEORY AND SIMULATION EXERCISES
Step 5:
On rebooting the switch the switch is set to its factory default condition and the old
configurations gets deleted.
PART B
Answer to Question 5:
Major Network: 12.97.0.0/16
Available IP addresses in major network: 65534
Number of IP addresses needed: 6126
Available IP addresses in allocated subnets: 6138
About 9% of available major network address space is used
About 100% of subnetted network address space is used
Route
r Interfaces
IP
Address
(Highest)
IP
Address (Lowest)
Subnet
Mask
Default
Gateway
HQ 12.97.8.
1
12.97.15.2
54
255.255.248
.0
12.97.8.
1
Branc
h 1
12.97.0.
1
12.97.7.25
4
255.255.248
.0
12.97.0.
1
THEORY AND SIMULATION EXERCISES
Step 5:
On rebooting the switch the switch is set to its factory default condition and the old
configurations gets deleted.
PART B
Answer to Question 5:
Major Network: 12.97.0.0/16
Available IP addresses in major network: 65534
Number of IP addresses needed: 6126
Available IP addresses in allocated subnets: 6138
About 9% of available major network address space is used
About 100% of subnetted network address space is used
Route
r Interfaces
IP
Address
(Highest)
IP
Address (Lowest)
Subnet
Mask
Default
Gateway
HQ 12.97.8.
1
12.97.15.2
54
255.255.248
.0
12.97.8.
1
Branc
h 1
12.97.0.
1
12.97.7.25
4
255.255.248
.0
12.97.0.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
THEORY AND SIMULATION EXERCISES
Branc
h 2
12.97.16
.1
12.97.23.2
54
255.255.248
.0
12.97.16
.1
S
ubnet
Name
N
eeded
Size
A
llocated
Size
A
ddress
M
ask
Dec
Mask
As
signable
Range
Bro
adcast
H
Q
2
042
2
046
12
.97.8.0
/
21
255.
255.248.0
12.
97.8.1 -
12.97.15.2
54
12.
97.15.255
B
ranch 1
2
042
2
046
12
.97.0.0
/
21
255.
255.248.0
12.
97.0.1 -
12.97.7.25
4
12.
97.7.255
B
ranch 2
2
042
2
046
12
.97.16.0
/
21
255.
255.248.0
12.
97.16.1 -
12.97.23.2
54
12.
97.23.255
Answer to Question 6:
Router Configuration
THEORY AND SIMULATION EXERCISES
Branc
h 2
12.97.16
.1
12.97.23.2
54
255.255.248
.0
12.97.16
.1
S
ubnet
Name
N
eeded
Size
A
llocated
Size
A
ddress
M
ask
Dec
Mask
As
signable
Range
Bro
adcast
H
Q
2
042
2
046
12
.97.8.0
/
21
255.
255.248.0
12.
97.8.1 -
12.97.15.2
54
12.
97.15.255
B
ranch 1
2
042
2
046
12
.97.0.0
/
21
255.
255.248.0
12.
97.0.1 -
12.97.7.25
4
12.
97.7.255
B
ranch 2
2
042
2
046
12
.97.16.0
/
21
255.
255.248.0
12.
97.16.1 -
12.97.23.2
54
12.
97.23.255
Answer to Question 6:
Router Configuration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
THEORY AND SIMULATION EXERCISES
Router 0
Router>
Router>en
Router#config t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname Branch1
Branch1(config)#
Branch1(config)#enable secret class
Branch1(config)#interface FastEthernet0/0
Branch1(config-if)#ip address 12.97.0.1 255.0.0.0
Branch1(config-if)#ip address 12.97.0.1 255.255.255.252
Branch1(config-if)#no shutdown
Branch1(config)#interface Serial0/3/0
Branch1(config-if)#ip address 12.97.0.10 255.255.255.252
Branch1(config-if)#no shutdown
Branch1(config)#ip route 12.97.8.0 255.255.255.0 12.97.17.2
Branch1(config)#ip route 12.97.16.0 255.255.255.0 12.97.18.2
Branch1(config)#ip route 12.97.18.0 255.255.255.0 12.97.17.2
THEORY AND SIMULATION EXERCISES
Router 0
Router>
Router>en
Router#config t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname Branch1
Branch1(config)#
Branch1(config)#enable secret class
Branch1(config)#interface FastEthernet0/0
Branch1(config-if)#ip address 12.97.0.1 255.0.0.0
Branch1(config-if)#ip address 12.97.0.1 255.255.255.252
Branch1(config-if)#no shutdown
Branch1(config)#interface Serial0/3/0
Branch1(config-if)#ip address 12.97.0.10 255.255.255.252
Branch1(config-if)#no shutdown
Branch1(config)#ip route 12.97.8.0 255.255.255.0 12.97.17.2
Branch1(config)#ip route 12.97.16.0 255.255.255.0 12.97.18.2
Branch1(config)#ip route 12.97.18.0 255.255.255.0 12.97.17.2
11
THEORY AND SIMULATION EXERCISES
Branch1(config)#
Router 1
Router>
Router>en
Router#config t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname HQ
HQ(config)#
HQ(config)#enable secret class
HQ(config)#interface FastEthernet0/0
HQ(config-if)#ip address 12.97.8.1 255.255.255.252
HQ(config-if)#
HQ(config-if)#exit
HQ(config)#interface Serial0/3/0
HQ(config-if)#ip address 12.97.8.10 255.255.255.252
HQ(config-if)#
HQ(config-if)#exit
HQ(config)#interface Serial0/3/1
THEORY AND SIMULATION EXERCISES
Branch1(config)#
Router 1
Router>
Router>en
Router#config t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname HQ
HQ(config)#
HQ(config)#enable secret class
HQ(config)#interface FastEthernet0/0
HQ(config-if)#ip address 12.97.8.1 255.255.255.252
HQ(config-if)#
HQ(config-if)#exit
HQ(config)#interface Serial0/3/0
HQ(config-if)#ip address 12.97.8.10 255.255.255.252
HQ(config-if)#
HQ(config-if)#exit
HQ(config)#interface Serial0/3/1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



