Network Infrastructure Design and Services Report for Cookie Co.
VerifiedAdded on 2020/05/08
|13
|2517
|37
Report
AI Summary
This report details the design and implementation of a new network infrastructure for Cookie Co., addressing the company's need for efficient communication between its office locations. It covers key aspects like network convergence, LAN and WAN connections, transmission media, and IP/DNS management. The report also explores essential network services such as file sharing (WWW, P2P), email, print servers, and VoIP. Furthermore, it examines data processing facilities, including data storage solutions (data centers, SAN, cloud, distributed databases) and data processing models (client-server, peer-to-peer). The report concludes by emphasizing the significance of the proposed network architecture for Cookie Co.'s resource sharing and overall business efficiency, recommending the use of peer-to-peer technology in business operations.

Network management
Name of the student
Name of the University
Author Note
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive summary
The following report discusses about the installation of a new network infrastructure for a
proposed business solution. The company to be chosen here is Cookie CO. The main
requirements for the business are to make a new network infrastructure among the office
locations which can be used to connect with other branches related to the business. In addition,
this report also includes a proposed network service that will be integrated with the business
solutions to match their requirements Moreover, this report also discusses about a data storage
facility which can be used to store the data pertaining to the business which can be accessed
through all the locations associated with the business.
NETWORK MANAGEMENT Page ii
The following report discusses about the installation of a new network infrastructure for a
proposed business solution. The company to be chosen here is Cookie CO. The main
requirements for the business are to make a new network infrastructure among the office
locations which can be used to connect with other branches related to the business. In addition,
this report also includes a proposed network service that will be integrated with the business
solutions to match their requirements Moreover, this report also discusses about a data storage
facility which can be used to store the data pertaining to the business which can be accessed
through all the locations associated with the business.
NETWORK MANAGEMENT Page ii

Table of Contents
Introduction:.................................................................................................................................. 3
Discussion:..................................................................................................................................... 3
1. Network infrastructure:.........................................................................................................3
2. Network services:.................................................................................................................. 6
3. Data processing facilities:...................................................................................................... 8
Conclusion:.................................................................................................................................... 9
References:.................................................................................................................................. 10
NETWORK MANAGEMENT Page iii
Introduction:.................................................................................................................................. 3
Discussion:..................................................................................................................................... 3
1. Network infrastructure:.........................................................................................................3
2. Network services:.................................................................................................................. 6
3. Data processing facilities:...................................................................................................... 8
Conclusion:.................................................................................................................................... 9
References:.................................................................................................................................. 10
NETWORK MANAGEMENT Page iii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction:
Businesses now-a-days need more efficiency in normal processing of their activities. This
is usually done by maintaining a central location for addressing such requirements. However, for
a growing business, it is not possible to manage all such activities by maintaining a single
location. This creates an added requirement for maintaining multiple locations to meet the
demands in business. This report includes the section of the infrastructural requirements of the
network of a company. In addition, this report also includes the presence of all the network
services that are to be included in the working of the newly made infrastructure. Additionally,
this report also includes the presence of the data processing activities that will also be
integrated in the architecture.
Discussion:
This section of the report discusses about the main content of the network
infrastructure.
1. Network infrastructure:
This section of the report discusses about the installation of a new network
infrastructure for a proposed business solution in the company Cookie Co. The main
requirements for the business are to make a new network infrastructure among the office
locations which can be used to connect with other branches related to the business.
Network convergence:
NETWORK MANAGEMENT Page iv
Businesses now-a-days need more efficiency in normal processing of their activities. This
is usually done by maintaining a central location for addressing such requirements. However, for
a growing business, it is not possible to manage all such activities by maintaining a single
location. This creates an added requirement for maintaining multiple locations to meet the
demands in business. This report includes the section of the infrastructural requirements of the
network of a company. In addition, this report also includes the presence of all the network
services that are to be included in the working of the newly made infrastructure. Additionally,
this report also includes the presence of the data processing activities that will also be
integrated in the architecture.
Discussion:
This section of the report discusses about the main content of the network
infrastructure.
1. Network infrastructure:
This section of the report discusses about the installation of a new network
infrastructure for a proposed business solution in the company Cookie Co. The main
requirements for the business are to make a new network infrastructure among the office
locations which can be used to connect with other branches related to the business.
Network convergence:
NETWORK MANAGEMENT Page iv
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The main considerations of the proposed solution will have expanding facilities for
business expansions. In addition, the company can also have branch offices which will facilitate
connection with the main office in a secured and efficient way.
The main office will have the core network requirements to support the business. This
includes the presence of a server with six 2U rack storage (Hsiao 2012). This will facilitate
connectivity of a large business. The servers will be directly connected to a switch which will
form the bridge between the various other devices. The switch normally has 1x8 ports or 1x24
connections.
One of the ports of the switch will be passed through a firewall and connected to a
router for internet access. Another port will be to comply with the IEEE 802.11n standard for
wireless access. This port will also be routed through a firewall setting.
The next port will be connected to the LAN connection of the offices. These LAN ports
will then be used by the computer devices to get secured access to the internet. In addition, a
print server will also be enabled to facilitate wireless print and fax operations. In addition, the
use of Ethernet cables will be facilitated for connectivity features.
NETWORK MANAGEMENT Page v
business expansions. In addition, the company can also have branch offices which will facilitate
connection with the main office in a secured and efficient way.
The main office will have the core network requirements to support the business. This
includes the presence of a server with six 2U rack storage (Hsiao 2012). This will facilitate
connectivity of a large business. The servers will be directly connected to a switch which will
form the bridge between the various other devices. The switch normally has 1x8 ports or 1x24
connections.
One of the ports of the switch will be passed through a firewall and connected to a
router for internet access. Another port will be to comply with the IEEE 802.11n standard for
wireless access. This port will also be routed through a firewall setting.
The next port will be connected to the LAN connection of the offices. These LAN ports
will then be used by the computer devices to get secured access to the internet. In addition, a
print server will also be enabled to facilitate wireless print and fax operations. In addition, the
use of Ethernet cables will be facilitated for connectivity features.
NETWORK MANAGEMENT Page v
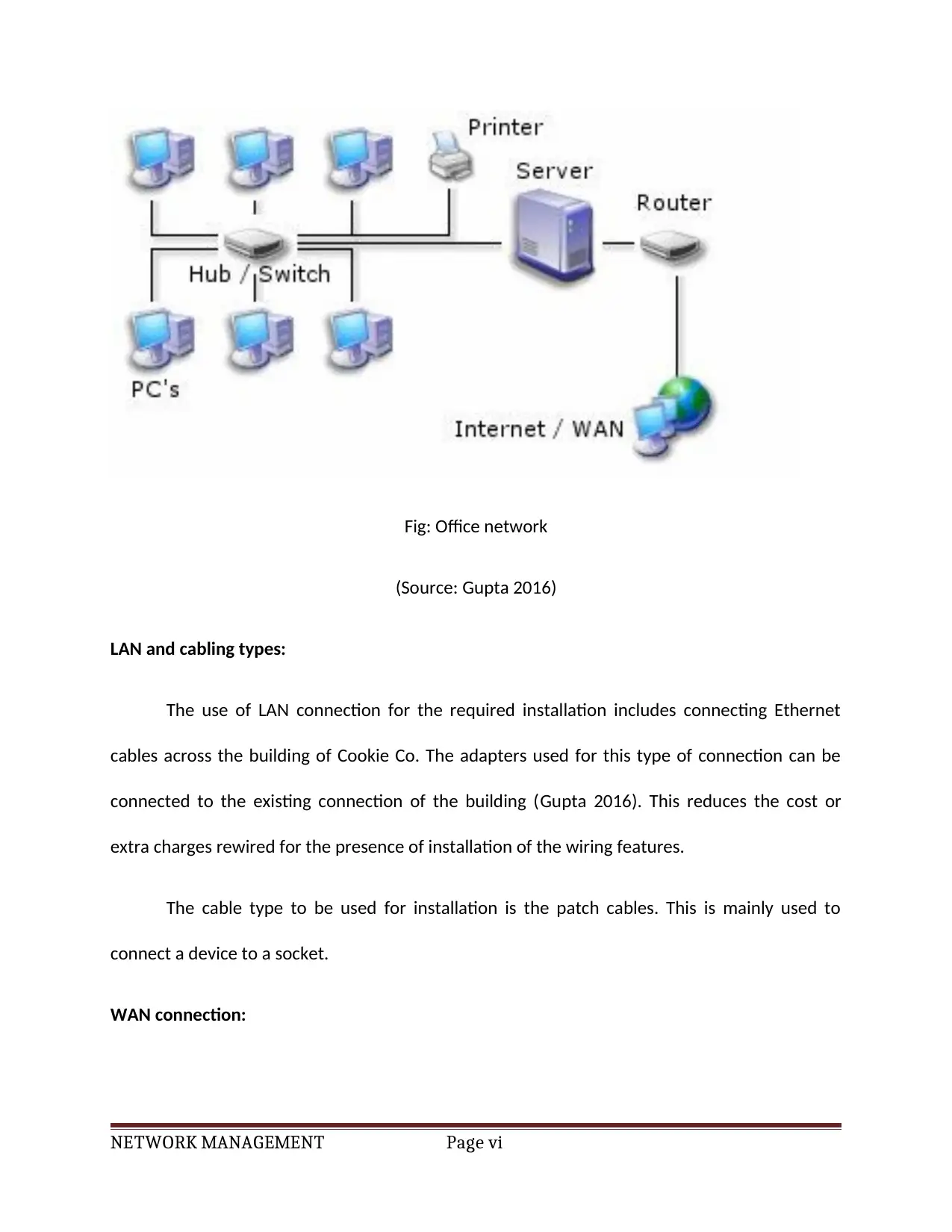
Fig: Office network
(Source: Gupta 2016)
LAN and cabling types:
The use of LAN connection for the required installation includes connecting Ethernet
cables across the building of Cookie Co. The adapters used for this type of connection can be
connected to the existing connection of the building (Gupta 2016). This reduces the cost or
extra charges rewired for the presence of installation of the wiring features.
The cable type to be used for installation is the patch cables. This is mainly used to
connect a device to a socket.
WAN connection:
NETWORK MANAGEMENT Page vi
(Source: Gupta 2016)
LAN and cabling types:
The use of LAN connection for the required installation includes connecting Ethernet
cables across the building of Cookie Co. The adapters used for this type of connection can be
connected to the existing connection of the building (Gupta 2016). This reduces the cost or
extra charges rewired for the presence of installation of the wiring features.
The cable type to be used for installation is the patch cables. This is mainly used to
connect a device to a socket.
WAN connection:
NETWORK MANAGEMENT Page vi
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The WAN connection is to be facilitated across the office locations so that the main
office and the branch office can be connected of the Cookie Co. This can be done either by
installing a data service unit at the ends of the main office and the branch office or by using a
VPN connection. This is further connected to the equipments of the telecomm provider (Zhang
et al. 2012). The internet access is facilitated by these telecomm providers by using a router at
both ends and setting up a firewall so that the total local network can be connected.
VPN can also be connected to serve as a WAN, which requires the presence of VPN
hardware and software. This is then connected to the public network for getting internet access.
However, this cost effective solution is not recommended as the presence of certain security
hacks are still eminent and this can raise security concerns in the business.
Transmission media and connecting device:
The basic transmission media to be used are the use of optical fibers. The use of such
transmission guides tends to promote the signal strength and the presence of interference is
mostly zero (Okoshi 2012). In addition, the waveguides inside the cables travels using the
property of total internal reflection which reduces the presence of any attenuation in the signal
and thus connection is very smooth in this case.
The connecting devices to be used are the presence of repeaters. Although the use of
these devices is very minimal in case of the optical fibers, repeaters are needed for better
connections.
IP and DNS management:
NETWORK MANAGEMENT Page vii
office and the branch office can be connected of the Cookie Co. This can be done either by
installing a data service unit at the ends of the main office and the branch office or by using a
VPN connection. This is further connected to the equipments of the telecomm provider (Zhang
et al. 2012). The internet access is facilitated by these telecomm providers by using a router at
both ends and setting up a firewall so that the total local network can be connected.
VPN can also be connected to serve as a WAN, which requires the presence of VPN
hardware and software. This is then connected to the public network for getting internet access.
However, this cost effective solution is not recommended as the presence of certain security
hacks are still eminent and this can raise security concerns in the business.
Transmission media and connecting device:
The basic transmission media to be used are the use of optical fibers. The use of such
transmission guides tends to promote the signal strength and the presence of interference is
mostly zero (Okoshi 2012). In addition, the waveguides inside the cables travels using the
property of total internal reflection which reduces the presence of any attenuation in the signal
and thus connection is very smooth in this case.
The connecting devices to be used are the presence of repeaters. Although the use of
these devices is very minimal in case of the optical fibers, repeaters are needed for better
connections.
IP and DNS management:
NETWORK MANAGEMENT Page vii
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The IP and DNS management is done by the use of network management tools. This
address management tools are used to manage the IP addresses, DNS and the MAC address of
the network (Khiyaita et al. 2012). The OptUtils is one such commercial software used for
network monitoring. This tool can be used by network managers to look for static IP addresses
and utilize them for establishing a secured connection. Basically these tools search for a subnet
which can provide a pool of IP addresses.
The DNS management can also be done by using this tool. The host name, default
subnet mask, network status and lookups can be reviewed for a specific IP address.
2. Network services:
The network service is defined as an application which involves the use of the network
layer of the architecture. They are basically used to provide applications of storage,
manipulations and communications. The various network services that will be used in Cookie
CO. include file sharing by the use of WWW or peer-to-peer technologies, Email, Print server
and VoIP.
File sharing:
This process involves the transmission and reception of electronic media which basically
includes multimedia programs, electronic books and documents. The most common methods of
file sharing include utilizing removable media, central servers, WWW (World Wide Web) and
P2P networks (peer-to-peer).
The P2P protocol utilizes the method of file sharing where the file is stored in the
directory servers. The setup of the Peer-to-Peer network needs the use of routers and Ethernet
NETWORK MANAGEMENT Page viii
address management tools are used to manage the IP addresses, DNS and the MAC address of
the network (Khiyaita et al. 2012). The OptUtils is one such commercial software used for
network monitoring. This tool can be used by network managers to look for static IP addresses
and utilize them for establishing a secured connection. Basically these tools search for a subnet
which can provide a pool of IP addresses.
The DNS management can also be done by using this tool. The host name, default
subnet mask, network status and lookups can be reviewed for a specific IP address.
2. Network services:
The network service is defined as an application which involves the use of the network
layer of the architecture. They are basically used to provide applications of storage,
manipulations and communications. The various network services that will be used in Cookie
CO. include file sharing by the use of WWW or peer-to-peer technologies, Email, Print server
and VoIP.
File sharing:
This process involves the transmission and reception of electronic media which basically
includes multimedia programs, electronic books and documents. The most common methods of
file sharing include utilizing removable media, central servers, WWW (World Wide Web) and
P2P networks (peer-to-peer).
The P2P protocol utilizes the method of file sharing where the file is stored in the
directory servers. The setup of the Peer-to-Peer network needs the use of routers and Ethernet
NETWORK MANAGEMENT Page viii

cables (Ricci and Carlini 2012). In addition, depending on the use of the operating system, the
devices can be put in the office in the same Home group (for windows 7) or Workgroup (for
windows XP) of the Cookie Co. The most common method of this technology is the BitTorrent.
The World Wide Web is an informative resource space where the presence of all
resources is identified by the use of the URLs. This is mainly used to get a digital presence of the
company (Aghaei, Nematbakhsh and Farsani 2012). Thus, the company needs to make a domain
name to use the WWW protocol. This can be done by purchasing a domain from commercial
domain providers. GoDaddy is one such commercial provider of domain names
Email:
The E-mail, also known as the electronic mail is used to send messages in the digital
world. It can be used to send mails, receive mails, or send textual documents embedded in the
mail. Cookie Co. needs to make a very own email id for business purposes. Gmail is the most
commercially used mail client.
Print server:
A print server is used to connect a printer to the network. This reduces the need to
connect a printer to one device and can be used without wired connectivity. This is done so that
the printer can be used by all the devices connected to the network (Cheshire and Krochmal
2013). This is mainly done by connecting the Ethernet cable to the printer and setting up a new
IP address and a port number for the connection across the Cookie Co.
VoIP (Voice over IP):
NETWORK MANAGEMENT Page ix
devices can be put in the office in the same Home group (for windows 7) or Workgroup (for
windows XP) of the Cookie Co. The most common method of this technology is the BitTorrent.
The World Wide Web is an informative resource space where the presence of all
resources is identified by the use of the URLs. This is mainly used to get a digital presence of the
company (Aghaei, Nematbakhsh and Farsani 2012). Thus, the company needs to make a domain
name to use the WWW protocol. This can be done by purchasing a domain from commercial
domain providers. GoDaddy is one such commercial provider of domain names
Email:
The E-mail, also known as the electronic mail is used to send messages in the digital
world. It can be used to send mails, receive mails, or send textual documents embedded in the
mail. Cookie Co. needs to make a very own email id for business purposes. Gmail is the most
commercially used mail client.
Print server:
A print server is used to connect a printer to the network. This reduces the need to
connect a printer to one device and can be used without wired connectivity. This is done so that
the printer can be used by all the devices connected to the network (Cheshire and Krochmal
2013). This is mainly done by connecting the Ethernet cable to the printer and setting up a new
IP address and a port number for the connection across the Cookie Co.
VoIP (Voice over IP):
NETWORK MANAGEMENT Page ix
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The VoIP is a method of delivering network calls which is mainly done by utilizing a
network connection. The benefits of this application include better voice quality so that a strong
business process is ensured (Jelassi et al. 2012). The main processes involved in the setup of a
VoIP process consist of signaling, channel setup, A2D conversion (analog to digital) and encoding
or decoding to achieve them.
3. Data processing facilities:
This section of the report is concerned with the storage solutions and the processing
model of the company.
Data Storage:
Data storage is done for the Cookie Co. to store their data. This data can be utilized
remotely or can be accessed physically. The most common data storage options are the use of
data center, SAN, Cloud and distributed database.
The data center is utilized to store the data of the company. The company needs to hire
infrastructures so that the data pertaining to the business can be stored in the data center.
This concept is used to provide storage facilities which can be used when connected to
an existing network. However, this network is not accessible by using the local area network.
The device that stores the data usually consists of disk arrays for information storing.
The cloud solutions are used to provide virtual infrastructure for dedicated application
uses (Arora, Parashar and Transforming 2013). The presence of a physical structure is reduced
and virtual structures are used for application addressing.
NETWORK MANAGEMENT Page x
network connection. The benefits of this application include better voice quality so that a strong
business process is ensured (Jelassi et al. 2012). The main processes involved in the setup of a
VoIP process consist of signaling, channel setup, A2D conversion (analog to digital) and encoding
or decoding to achieve them.
3. Data processing facilities:
This section of the report is concerned with the storage solutions and the processing
model of the company.
Data Storage:
Data storage is done for the Cookie Co. to store their data. This data can be utilized
remotely or can be accessed physically. The most common data storage options are the use of
data center, SAN, Cloud and distributed database.
The data center is utilized to store the data of the company. The company needs to hire
infrastructures so that the data pertaining to the business can be stored in the data center.
This concept is used to provide storage facilities which can be used when connected to
an existing network. However, this network is not accessible by using the local area network.
The device that stores the data usually consists of disk arrays for information storing.
The cloud solutions are used to provide virtual infrastructure for dedicated application
uses (Arora, Parashar and Transforming 2013). The presence of a physical structure is reduced
and virtual structures are used for application addressing.
NETWORK MANAGEMENT Page x
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The distributed database involves sharing of the database resource by storing the
database nodes at different networks.
Data Processing:
This section is used to define the processing of the data that is to be integrated in the
business solutions of the company. This includes the client-server model and the peer-to-peer
model. The client server model is used to divide the network resource between the client
(network requester) and the server (service providers). The P2P protocol utilizes the method of
file sharing where the file is stored in the directory servers (Ricci and Carlini 2012). The setup of
the Peer-to-Peer network needs the use of routers and Ethernet cables.
Conclusion:
Thus, the conclusion that can be drawn from this report is that for the development of a
successful infrastructure in the network layer of the company needs to apply the analysis made.
This is done by utilizing the network architecture in the main as well as the branch offices to
meet their intended requirements. This will facilitate better connectivity and efficiency which
will be utilized in the sharing of resources among each other. Moreover, the company is also
recommended to use the peer-to-peer technology in business operations.
NETWORK MANAGEMENT Page xi
database nodes at different networks.
Data Processing:
This section is used to define the processing of the data that is to be integrated in the
business solutions of the company. This includes the client-server model and the peer-to-peer
model. The client server model is used to divide the network resource between the client
(network requester) and the server (service providers). The P2P protocol utilizes the method of
file sharing where the file is stored in the directory servers (Ricci and Carlini 2012). The setup of
the Peer-to-Peer network needs the use of routers and Ethernet cables.
Conclusion:
Thus, the conclusion that can be drawn from this report is that for the development of a
successful infrastructure in the network layer of the company needs to apply the analysis made.
This is done by utilizing the network architecture in the main as well as the branch offices to
meet their intended requirements. This will facilitate better connectivity and efficiency which
will be utilized in the sharing of resources among each other. Moreover, the company is also
recommended to use the peer-to-peer technology in business operations.
NETWORK MANAGEMENT Page xi

References:
Aghaei, S., Nematbakhsh, M.A. and Farsani, H.K., 2012. Evolution of the world wide web: From
WEB 1.0 TO WEB 4.0. International Journal of Web & Semantic Technology, 3(1), p.1.
Arora, R., Parashar, A. and Transforming, C.C.I., 2013. Secure user data in cloud computing using
encryption algorithms. International journal of engineering research and applications, 3(4),
pp.1922-1926.
Cheshire, S. and Krochmal, M., 2013. DNS-based service discovery (No. RFC 6763).
Gupta, S., 2016. A Comparative Analysis of Wired and Wireless Network
Architecture. International Journal of Emerging Trends in Research, 1(1), pp.05-11.
Hsiao, E.L., 2012. Synchronous and asynchronous communication in an online environment:
Faculty experiences and perceptions. Quarterly Review of Distance Education, 13(1), p.15.
Jelassi, S., Rubino, G., Melvin, H., Youssef, H. and Pujolle, G., 2012. Quality of experience of VoIP
service: A survey of assessment approaches and open issues. IEEE Communications surveys &
tutorials, 14(2), pp.491-513.
Khiyaita, A., El Bakkali, H., Zbakh, M. and El Kettani, D., 2012, April. Load balancing cloud
computing: State of art. In Network Security and Systems (JNS2), 2012 National Days of (pp. 106-
109). IEEE.
Lin, M., Chen, Q. and Yan, S., 2013. Network in network. arXiv preprint arXiv:1312.4400.
Okoshi, T., 2012. Optical fibers. Elsevier.
NETWORK MANAGEMENT Page xii
Aghaei, S., Nematbakhsh, M.A. and Farsani, H.K., 2012. Evolution of the world wide web: From
WEB 1.0 TO WEB 4.0. International Journal of Web & Semantic Technology, 3(1), p.1.
Arora, R., Parashar, A. and Transforming, C.C.I., 2013. Secure user data in cloud computing using
encryption algorithms. International journal of engineering research and applications, 3(4),
pp.1922-1926.
Cheshire, S. and Krochmal, M., 2013. DNS-based service discovery (No. RFC 6763).
Gupta, S., 2016. A Comparative Analysis of Wired and Wireless Network
Architecture. International Journal of Emerging Trends in Research, 1(1), pp.05-11.
Hsiao, E.L., 2012. Synchronous and asynchronous communication in an online environment:
Faculty experiences and perceptions. Quarterly Review of Distance Education, 13(1), p.15.
Jelassi, S., Rubino, G., Melvin, H., Youssef, H. and Pujolle, G., 2012. Quality of experience of VoIP
service: A survey of assessment approaches and open issues. IEEE Communications surveys &
tutorials, 14(2), pp.491-513.
Khiyaita, A., El Bakkali, H., Zbakh, M. and El Kettani, D., 2012, April. Load balancing cloud
computing: State of art. In Network Security and Systems (JNS2), 2012 National Days of (pp. 106-
109). IEEE.
Lin, M., Chen, Q. and Yan, S., 2013. Network in network. arXiv preprint arXiv:1312.4400.
Okoshi, T., 2012. Optical fibers. Elsevier.
NETWORK MANAGEMENT Page xii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





