Acme Corporation Network Security: Design and Implementation
VerifiedAdded on 2023/06/13
|8
|1203
|486
Report
AI Summary
This report details a network solution for Acme Corporation, focusing on connecting two branch offices with a constant 50 Mbps connection while ensuring robust security. The proposed network design incorporates firewalls at entry points, access control lists to restrict user access to core resources like data centers and web servers, and the implementation of 'breadcrumbs' as traps for attackers. The report recommends Cat 6 cables for local wiring due to their higher bandwidth support, wiring closets on each floor for easy management, and labeled cables for quick identification of broken links. Wireless access points are secured with encryption, and VLANs are created to separate data and voice traffic. Data center availability is enhanced through virtualization and load balancers to distribute traffic evenly, mitigating single points of failure. The report concludes by emphasizing the importance of analyzing gathered attack data to further improve network security.

Running head: TELECOMMUNICATION NETWORK SECURITY
Telecommunication and Network Security
Name of the Student
Name of the University
Author’s Note
Telecommunication and Network Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
TELECOMMUNICATION NETWORK SECURITY
Table of Contents
Introduction......................................................................................................................................2
Network Design...............................................................................................................................2
List of Recommended Cable...........................................................................................................3
List of recommended wiring closets................................................................................................3
Recommendation for securing the network.....................................................................................3
Building of traps for stopping attackers...........................................................................................4
Recommendation of WAN or wireless technology.........................................................................4
Technology used in data center for increasing the data availability................................................5
Justification of the recommendation................................................................................................5
Conclusion.......................................................................................................................................6
References........................................................................................................................................7
TELECOMMUNICATION NETWORK SECURITY
Table of Contents
Introduction......................................................................................................................................2
Network Design...............................................................................................................................2
List of Recommended Cable...........................................................................................................3
List of recommended wiring closets................................................................................................3
Recommendation for securing the network.....................................................................................3
Building of traps for stopping attackers...........................................................................................4
Recommendation of WAN or wireless technology.........................................................................4
Technology used in data center for increasing the data availability................................................5
Justification of the recommendation................................................................................................5
Conclusion.......................................................................................................................................6
References........................................................................................................................................7
2
TELECOMMUNICATION NETWORK SECURITY
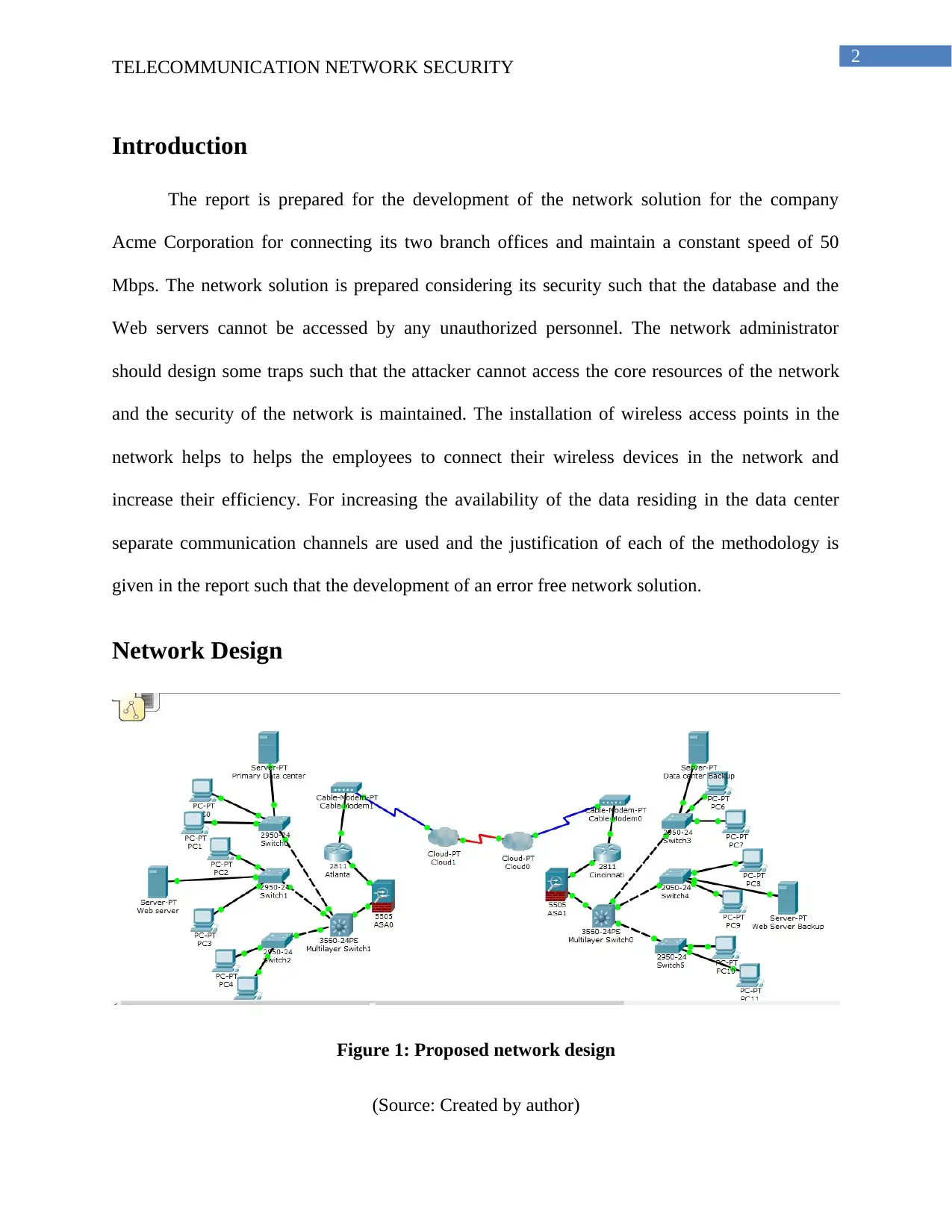
Introduction
The report is prepared for the development of the network solution for the company
Acme Corporation for connecting its two branch offices and maintain a constant speed of 50
Mbps. The network solution is prepared considering its security such that the database and the
Web servers cannot be accessed by any unauthorized personnel. The network administrator
should design some traps such that the attacker cannot access the core resources of the network
and the security of the network is maintained. The installation of wireless access points in the
network helps to helps the employees to connect their wireless devices in the network and
increase their efficiency. For increasing the availability of the data residing in the data center
separate communication channels are used and the justification of each of the methodology is
given in the report such that the development of an error free network solution.
Network Design
Figure 1: Proposed network design
(Source: Created by author)
TELECOMMUNICATION NETWORK SECURITY
Introduction
The report is prepared for the development of the network solution for the company
Acme Corporation for connecting its two branch offices and maintain a constant speed of 50
Mbps. The network solution is prepared considering its security such that the database and the
Web servers cannot be accessed by any unauthorized personnel. The network administrator
should design some traps such that the attacker cannot access the core resources of the network
and the security of the network is maintained. The installation of wireless access points in the
network helps to helps the employees to connect their wireless devices in the network and
increase their efficiency. For increasing the availability of the data residing in the data center
separate communication channels are used and the justification of each of the methodology is
given in the report such that the development of an error free network solution.
Network Design
Figure 1: Proposed network design
(Source: Created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
TELECOMMUNICATION NETWORK SECURITY
List of Recommended Cable
Frequency Bandwidth Technology Supported Category
100 MHz 100 Mbps Ethernet (100 Base
TX)
5
100 MHz 100 Mbps Ethernet (100 Base
TX) & 1000 Mbps Ethernet
(1000 Base T)
5e
250 MHz 1000 Mbps Ethernet (1000
Base T)
6
500 MHz 1000 Mbps Ethernet (1000
Base T) & 10 Gbps Ethernet
(10G base T)
6a
List of recommended wiring closets
For the backbone of the network Fiber optics cable are used and the internal wiring is
done using the cat 5e or 6 cables. For each of the floor a wiring closet is required to be installed
for connecting the PCs, servers and the data centers with the category 5e/6 patch cord and the
network equipment. A 19” rack or cabinet would be sufficient for installation of the switch and
the connecting the cords with it.
Recommendation for securing the network
For securing the network from being attacked firewalls must be installed in the entry
point of the network for each of the branch offices. The internal network should be managed by
TELECOMMUNICATION NETWORK SECURITY
List of Recommended Cable
Frequency Bandwidth Technology Supported Category
100 MHz 100 Mbps Ethernet (100 Base
TX)
5
100 MHz 100 Mbps Ethernet (100 Base
TX) & 1000 Mbps Ethernet
(1000 Base T)
5e
250 MHz 1000 Mbps Ethernet (1000
Base T)
6
500 MHz 1000 Mbps Ethernet (1000
Base T) & 10 Gbps Ethernet
(10G base T)
6a
List of recommended wiring closets
For the backbone of the network Fiber optics cable are used and the internal wiring is
done using the cat 5e or 6 cables. For each of the floor a wiring closet is required to be installed
for connecting the PCs, servers and the data centers with the category 5e/6 patch cord and the
network equipment. A 19” rack or cabinet would be sufficient for installation of the switch and
the connecting the cords with it.
Recommendation for securing the network
For securing the network from being attacked firewalls must be installed in the entry
point of the network for each of the branch offices. The internal network should be managed by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
TELECOMMUNICATION NETWORK SECURITY
adding access control list and restricting the users to access the core resources such as the data
centers and the web servers.
Building of traps for stopping attackers
Bread Crumbs can be used throughout the network to fool the attacker and lead the
attacker in a particular direction such that original servers and the resources are kept safe.
Figure 2: Breadcrumb network
(Source: Mierzejewski & rarr, 2016)
Recommendation of WAN or wireless technology
For connecting the two offices the cost and the functionality of the network should be
considered. The integration of the voice, video and the data traffic would help the organization to
get the maximum output from then network solution. The monitoring and maintenance of the
network is important for managing all the remote location. Retransmission of the packets should
be implemented for reducing the delay and increasing the reliability of the network. The
TELECOMMUNICATION NETWORK SECURITY
adding access control list and restricting the users to access the core resources such as the data
centers and the web servers.
Building of traps for stopping attackers
Bread Crumbs can be used throughout the network to fool the attacker and lead the
attacker in a particular direction such that original servers and the resources are kept safe.
Figure 2: Breadcrumb network
(Source: Mierzejewski & rarr, 2016)
Recommendation of WAN or wireless technology
For connecting the two offices the cost and the functionality of the network should be
considered. The integration of the voice, video and the data traffic would help the organization to
get the maximum output from then network solution. The monitoring and maintenance of the
network is important for managing all the remote location. Retransmission of the packets should
be implemented for reducing the delay and increasing the reliability of the network. The

5
TELECOMMUNICATION NETWORK SECURITY
installation of the wireless access point in the network helps in connecting the handheld devices
in the network and increases the efficiency of the network (Khan, 2014).
Technology used in data center for increasing the data availability
The virtualization of the data center and the migrating the data in the cloud servers
increases the redundancy and the data becomes available to the users all the time (Rodríguez et
al., 2015). Load balancers should be used for the management of the loads on the server and
increasing the scalability and availability of the resources.
Justification of the recommendation
The cat 6 cable is recommended for the local wiring because it can support a larger
bandwidth than the normal cat 5 cable. A wiring closet is recommend to be installed in each of
the floor such that it can be easily managed. The cables should be labelled such that a broken
link can be easily identified. The bread crumb are used throughout the network such that it does
not cause suspicion on the attacker and the attacker feels that they are really attacking the
network and found the real resource. The data regarding the attack process should be gathered by
the network development team for securing the network in future from illegal access. The
wireless access point must be secured with proper encryption algorithm and the different
VLANS must be created for the data and the voice for reducing the congestion and increasing the
availability of the network. The virtualization and implementation of load balancer for
distribution of the data traffic evenly increases the availability of the data and reduces the risk of
single point failure.
TELECOMMUNICATION NETWORK SECURITY
installation of the wireless access point in the network helps in connecting the handheld devices
in the network and increases the efficiency of the network (Khan, 2014).
Technology used in data center for increasing the data availability
The virtualization of the data center and the migrating the data in the cloud servers
increases the redundancy and the data becomes available to the users all the time (Rodríguez et
al., 2015). Load balancers should be used for the management of the loads on the server and
increasing the scalability and availability of the resources.
Justification of the recommendation
The cat 6 cable is recommended for the local wiring because it can support a larger
bandwidth than the normal cat 5 cable. A wiring closet is recommend to be installed in each of
the floor such that it can be easily managed. The cables should be labelled such that a broken
link can be easily identified. The bread crumb are used throughout the network such that it does
not cause suspicion on the attacker and the attacker feels that they are really attacking the
network and found the real resource. The data regarding the attack process should be gathered by
the network development team for securing the network in future from illegal access. The
wireless access point must be secured with proper encryption algorithm and the different
VLANS must be created for the data and the voice for reducing the congestion and increasing the
availability of the network. The virtualization and implementation of load balancer for
distribution of the data traffic evenly increases the availability of the data and reduces the risk of
single point failure.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
TELECOMMUNICATION NETWORK SECURITY
Conclusion
From the above report it can be concluded that with the development of the network
solution for the company the requirement of the company was analyzed. The location of the
server and the cable used for connecting the servers are analyzed for recommending the best
cable and the layout of the cable for designing the network solution. A network design is created
and a list is prepared for the recommended cables that should be used for connecting the two
destinations. The wiring closet that should be used for the installation of the hardware devices
are also given in the report. A list of recommendation is given for the development of a secure
network solution and eliminate the threat in the network for securing the organizational
information.
TELECOMMUNICATION NETWORK SECURITY
Conclusion
From the above report it can be concluded that with the development of the network
solution for the company the requirement of the company was analyzed. The location of the
server and the cable used for connecting the servers are analyzed for recommending the best
cable and the layout of the cable for designing the network solution. A network design is created
and a list is prepared for the recommended cables that should be used for connecting the two
destinations. The wiring closet that should be used for the installation of the hardware devices
are also given in the report. A list of recommendation is given for the development of a secure
network solution and eliminate the threat in the network for securing the organizational
information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
TELECOMMUNICATION NETWORK SECURITY
References
Khan, F. (2014, October). Secure communication and routing architecture in wireless sensor
networks. In Consumer Electronics (GCCE), 2014 IEEE 3rd Global Conference on(pp.
647-650). IEEE.
Mierzejewski, S., & →, V. (2016). When the Attacker Becomes the Prey: Trapping Hackers
in Your Network. Secure Your Workplace Network. Retrieved 14 April 2018, from
https://workplacetablet.com/2016/06/27/when-the-attacker-becomes-the-prey-trapping-
hackers-in-your-network/
Rodríguez, L. J., Tran, N. H., Duong, T. Q., Le-Ngoc, T., Elkashlan, M., & Shetty, S. (2015).
Physical layer security in wireless cooperative relay networks: State of the art and
beyond. IEEE Communications Magazine, 53(12), 32-39.
TELECOMMUNICATION NETWORK SECURITY
References
Khan, F. (2014, October). Secure communication and routing architecture in wireless sensor
networks. In Consumer Electronics (GCCE), 2014 IEEE 3rd Global Conference on(pp.
647-650). IEEE.
Mierzejewski, S., & →, V. (2016). When the Attacker Becomes the Prey: Trapping Hackers
in Your Network. Secure Your Workplace Network. Retrieved 14 April 2018, from
https://workplacetablet.com/2016/06/27/when-the-attacker-becomes-the-prey-trapping-
hackers-in-your-network/
Rodríguez, L. J., Tran, N. H., Duong, T. Q., Le-Ngoc, T., Elkashlan, M., & Shetty, S. (2015).
Physical layer security in wireless cooperative relay networks: State of the art and
beyond. IEEE Communications Magazine, 53(12), 32-39.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





