NIT3122 Enterprise Network Management: Active Directory Design Project
VerifiedAdded on 2023/04/26
|32
|1363
|383
Project
AI Summary
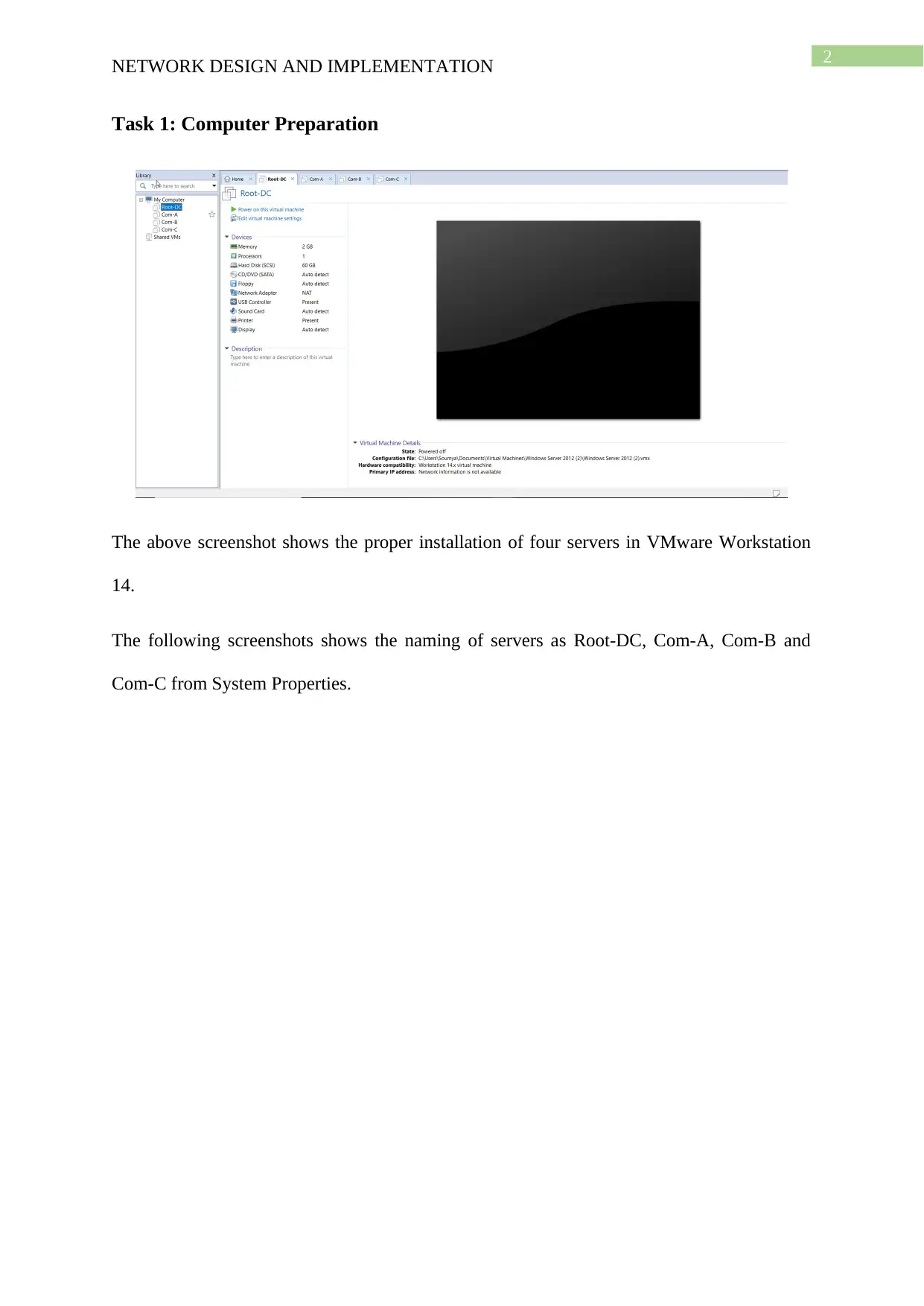
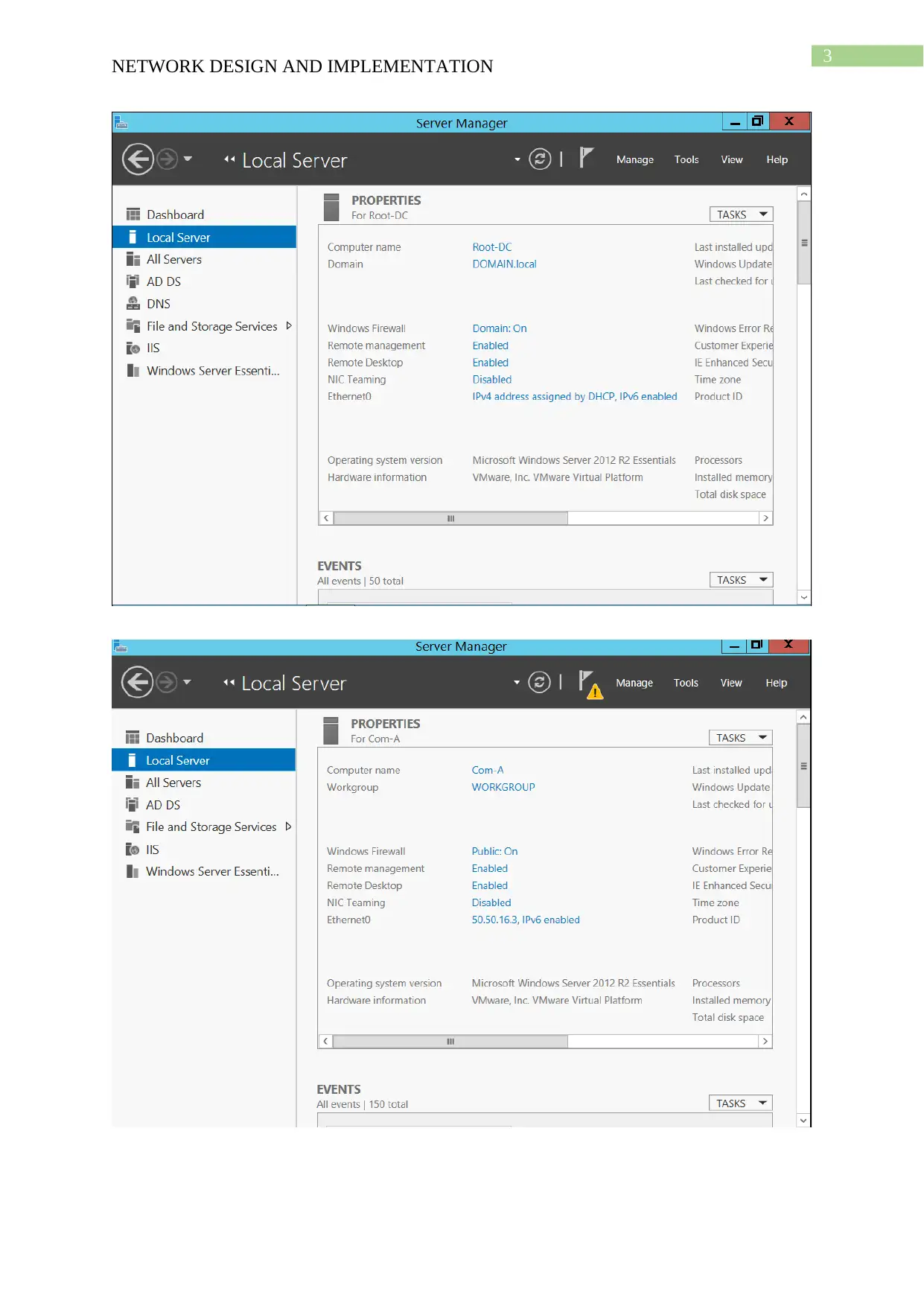
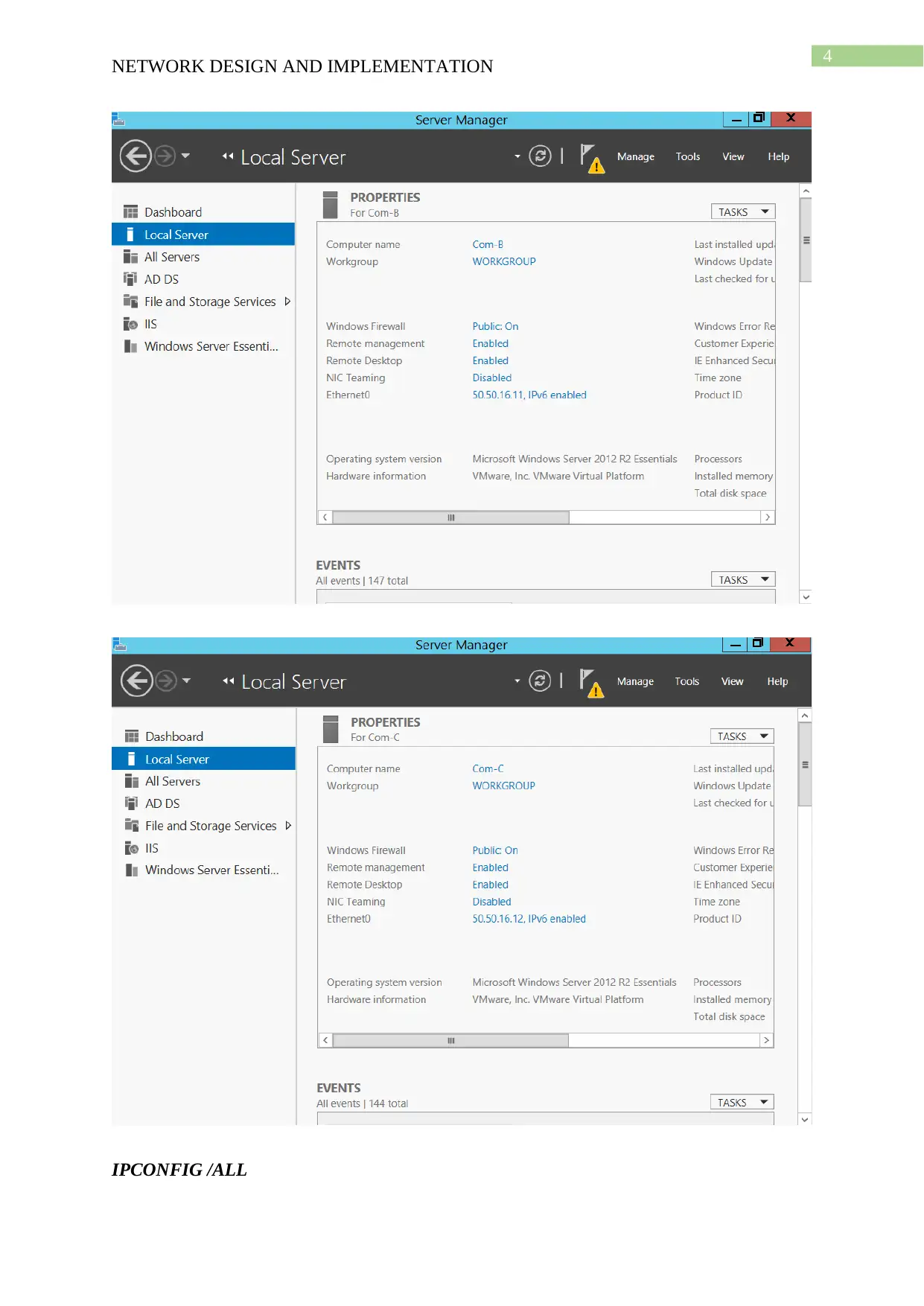
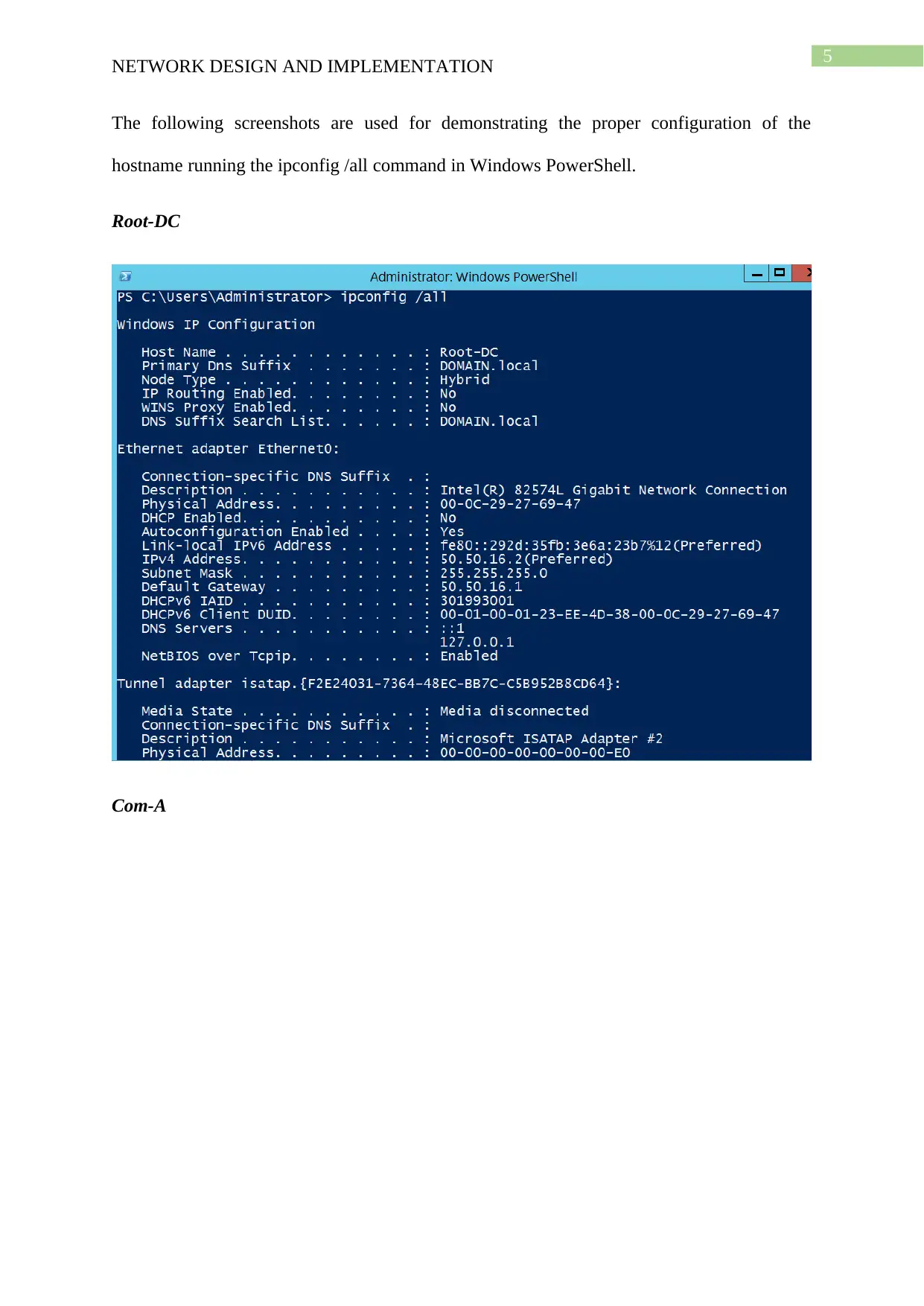
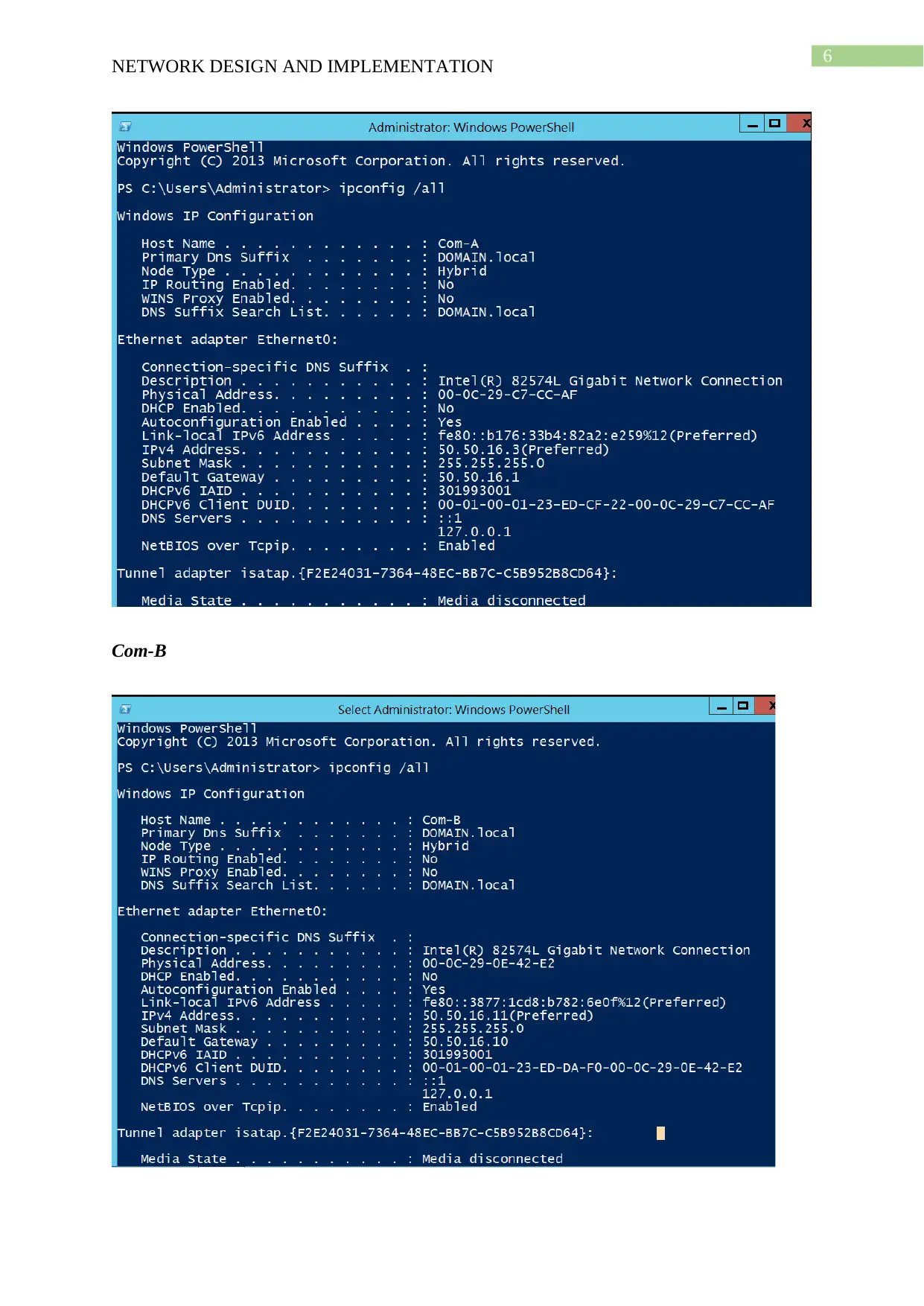
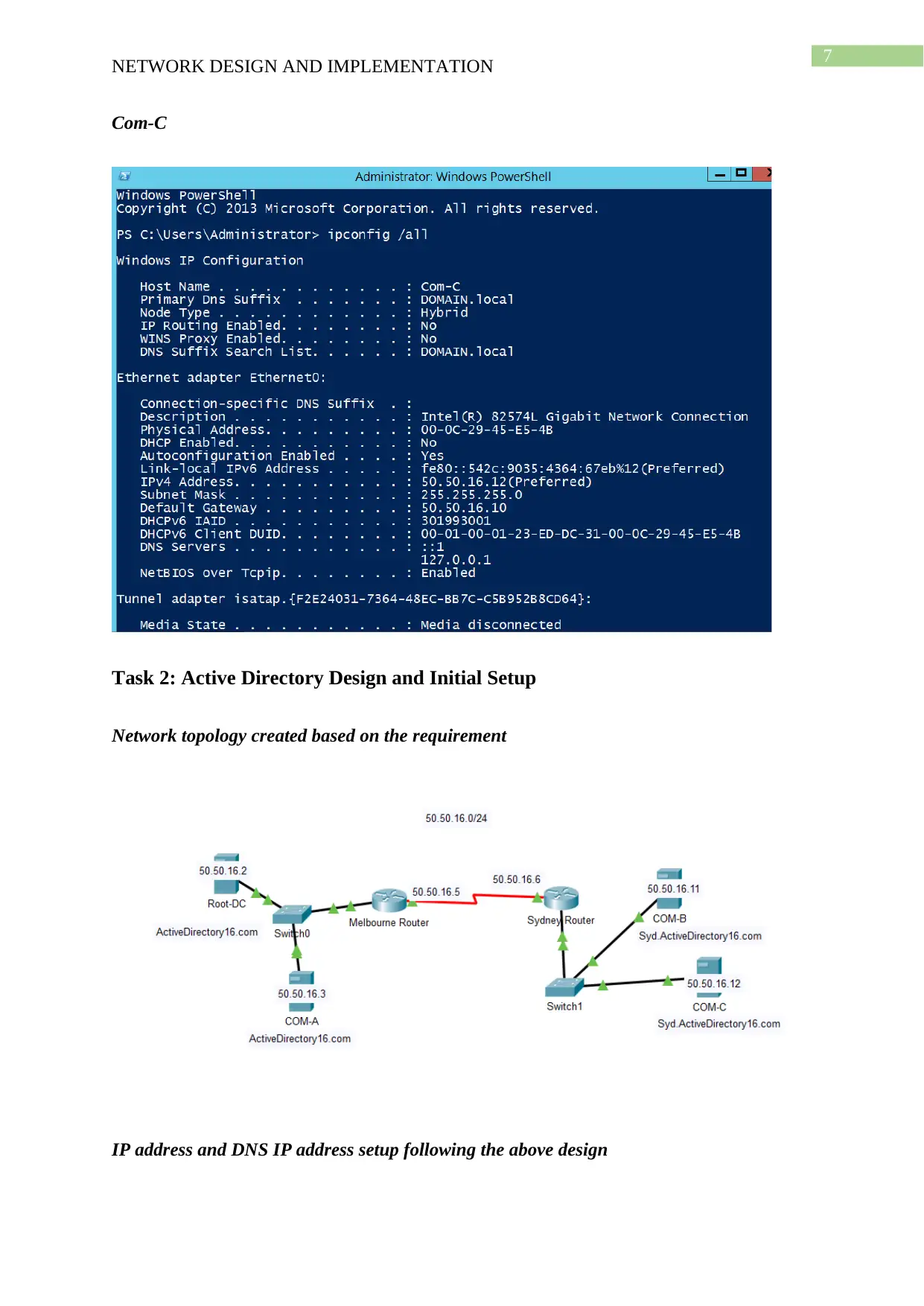
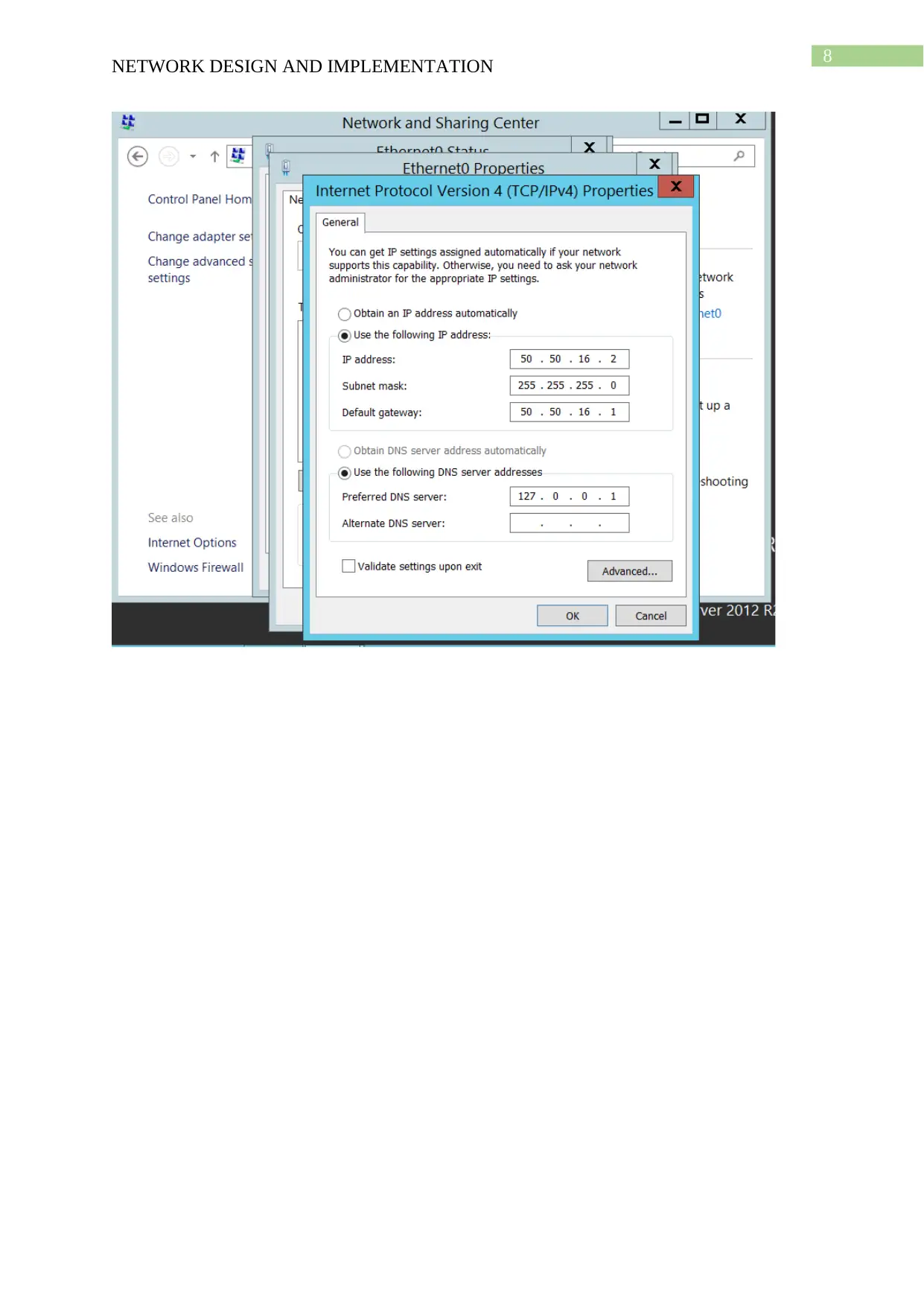
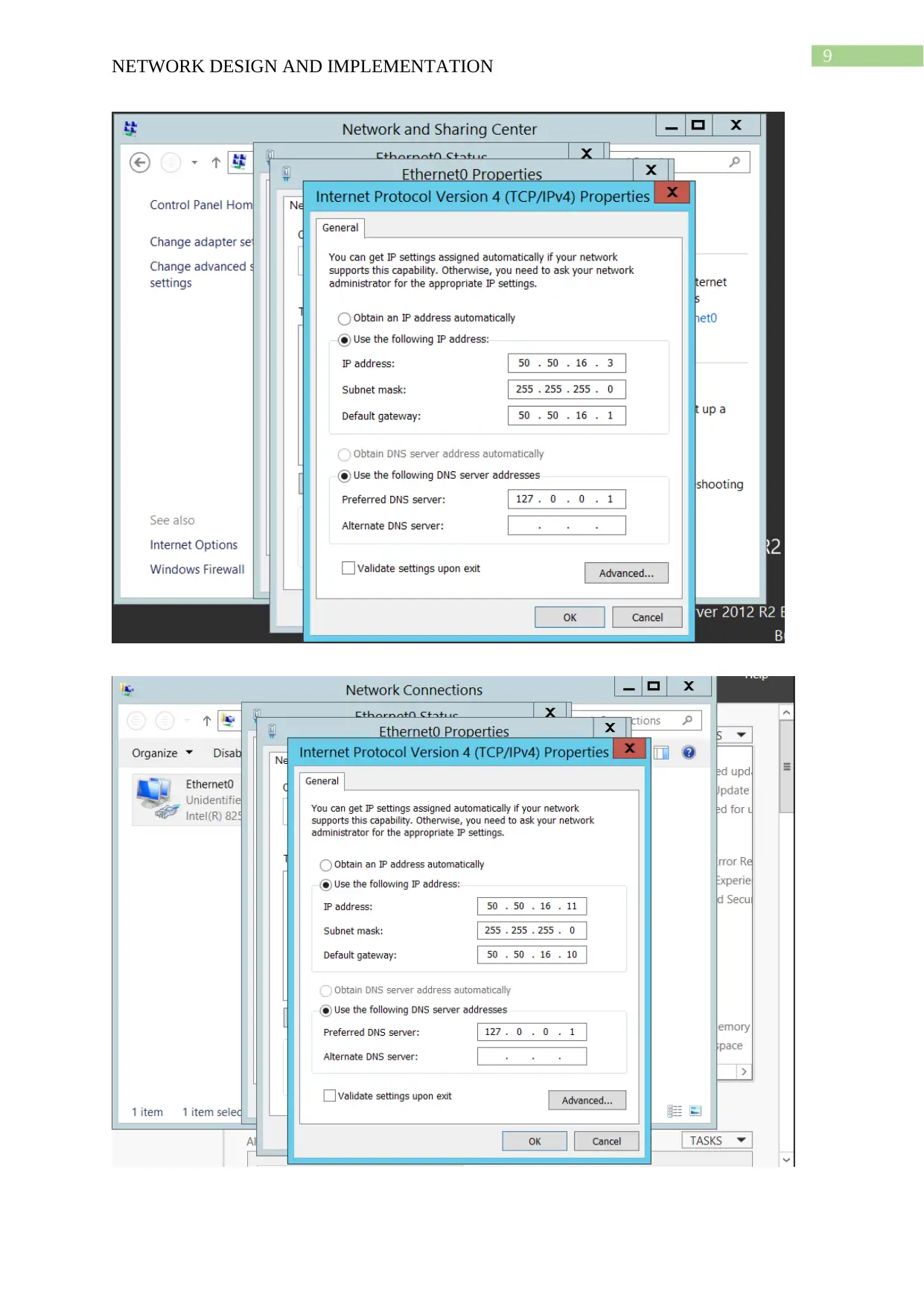
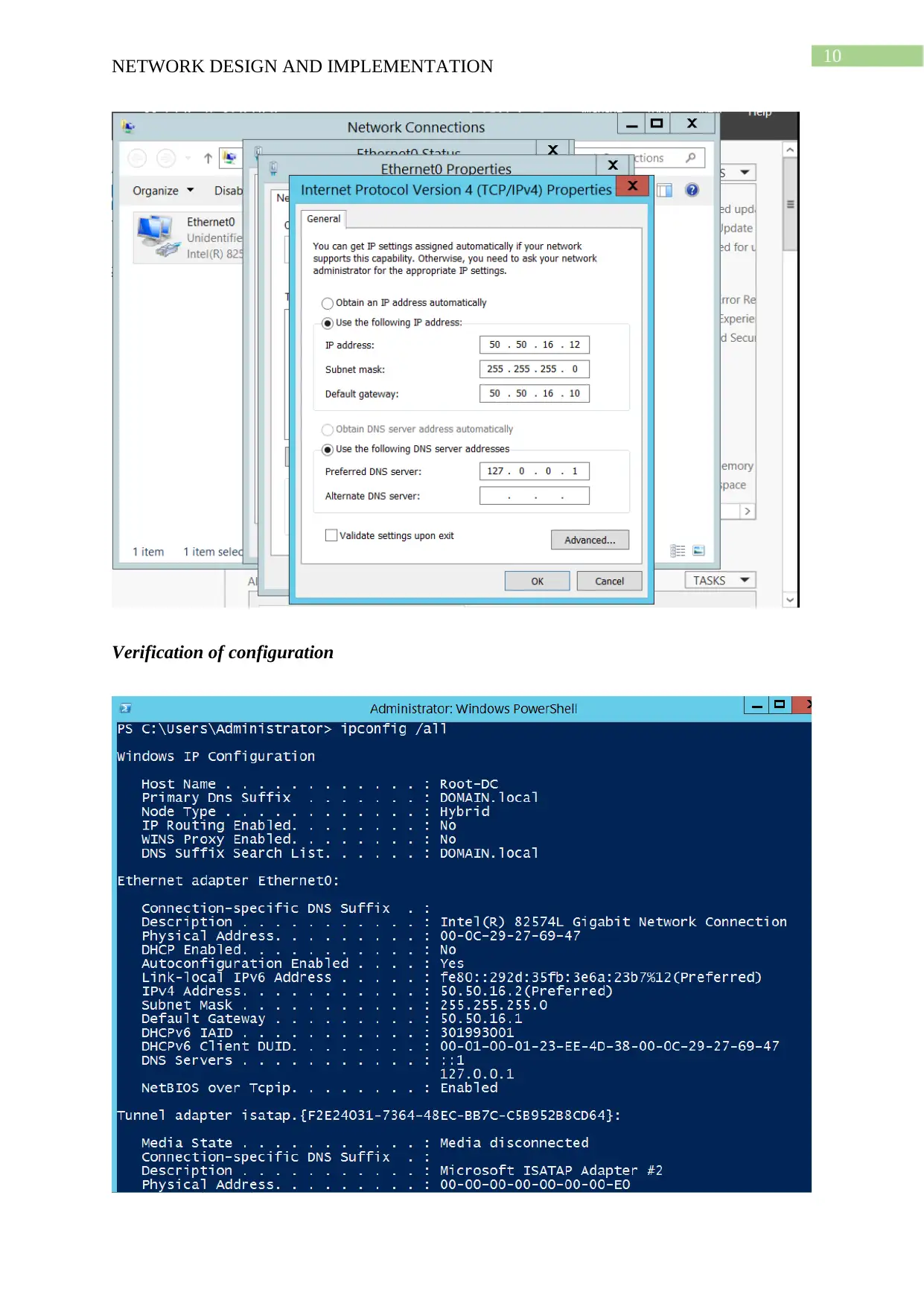
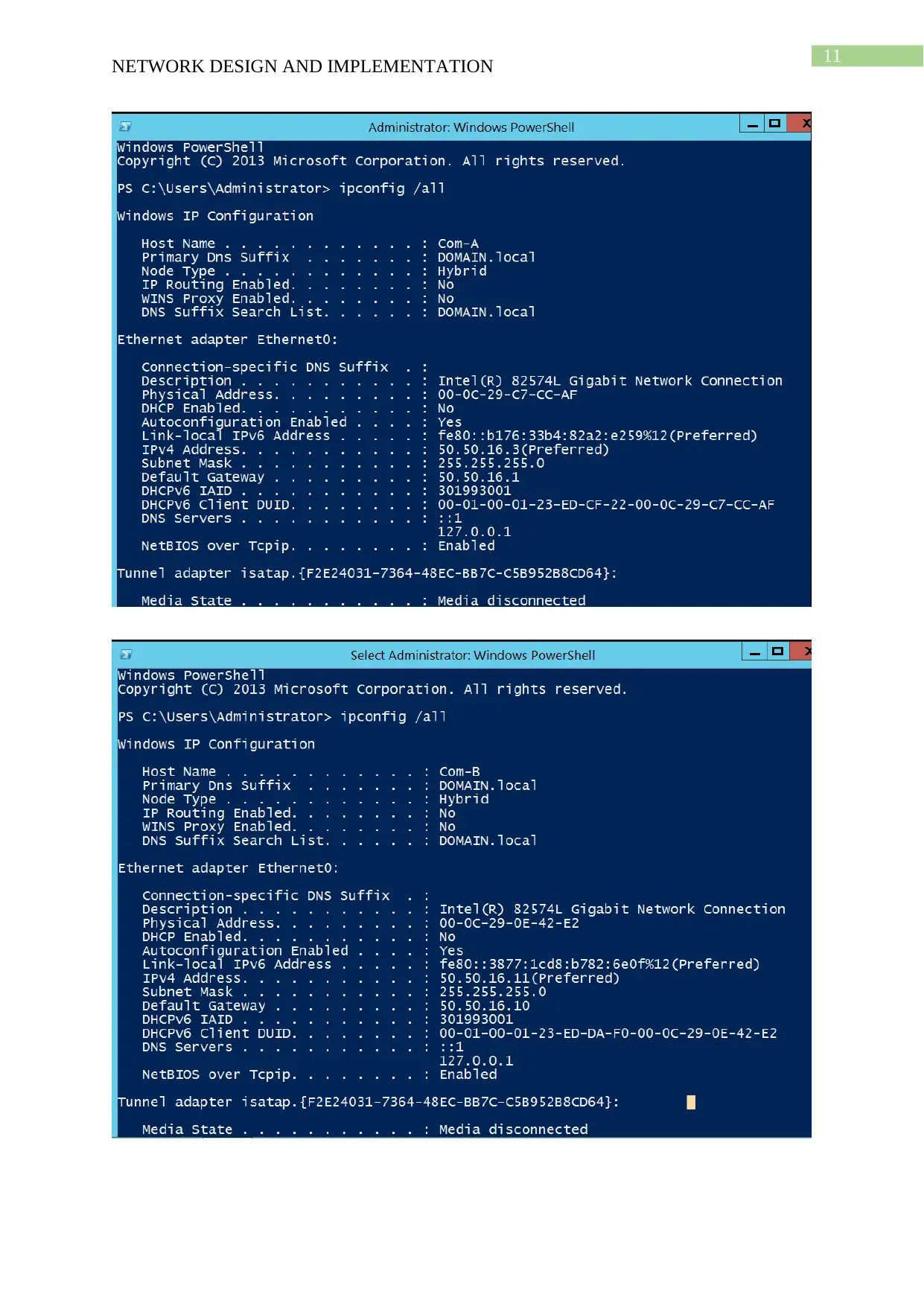
This project details the design and implementation of a network using Windows Server 2012 R2 and Active Directory, based on the NIT3122 Enterprise Network Management assignment. The project covers computer preparation, Active Directory design and initial setup, Active Directory installation, and Active Directory management. The network consists of four servers (Root-DC, Com-A, Com-B, and Com-C) configured in VMware Workstation 14. The Active Directory setup includes a root domain (activedirectory16.com) and a child domain (Syd.ActiveDirectoryxx.com), with one server configured as a Read-Only Domain Controller. The management tasks include group management, user account management (creation of ADTest_User), application of policies (automatic deletion of temp folder content), and software restriction (blocking ADTest_User from accessing Internet Explorer). The project demonstrates the configuration steps, verification processes, and troubleshooting involved in setting up and managing an Active Directory network.
1 out of 32









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)