NIT3122 Enterprise Network Management: Network Design & Implementation
VerifiedAdded on 2023/03/31
|29
|1240
|429
Project
AI Summary
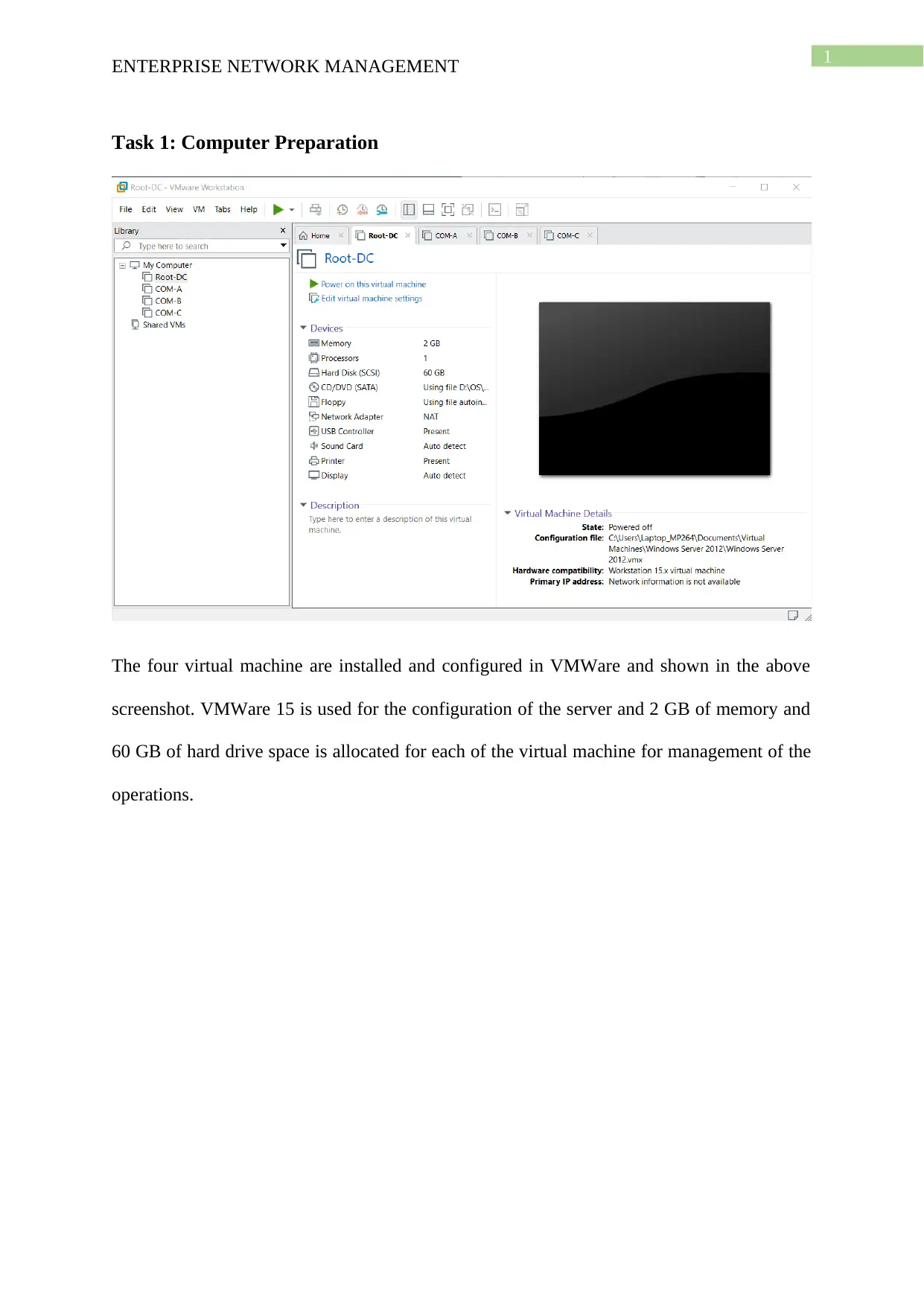
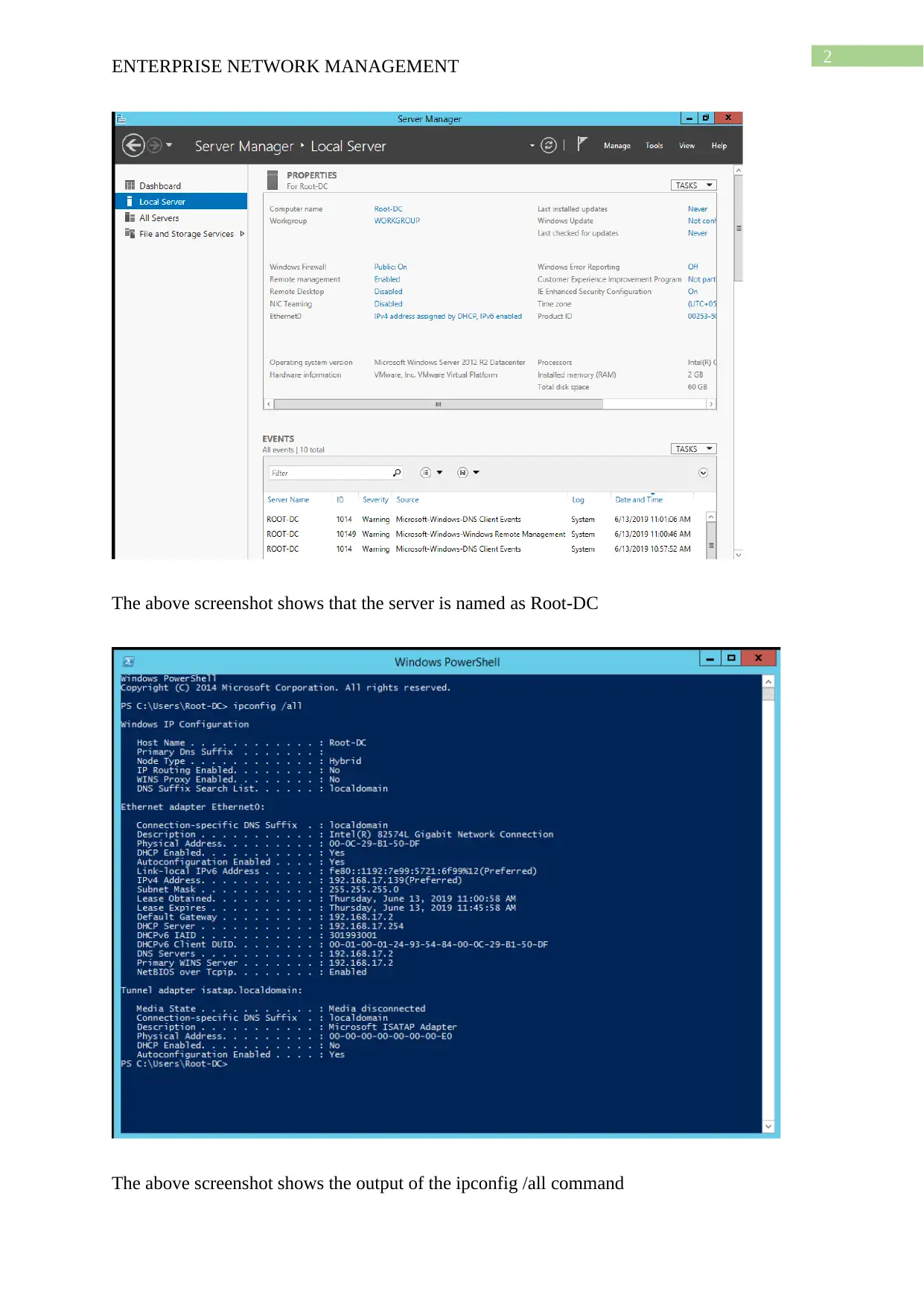
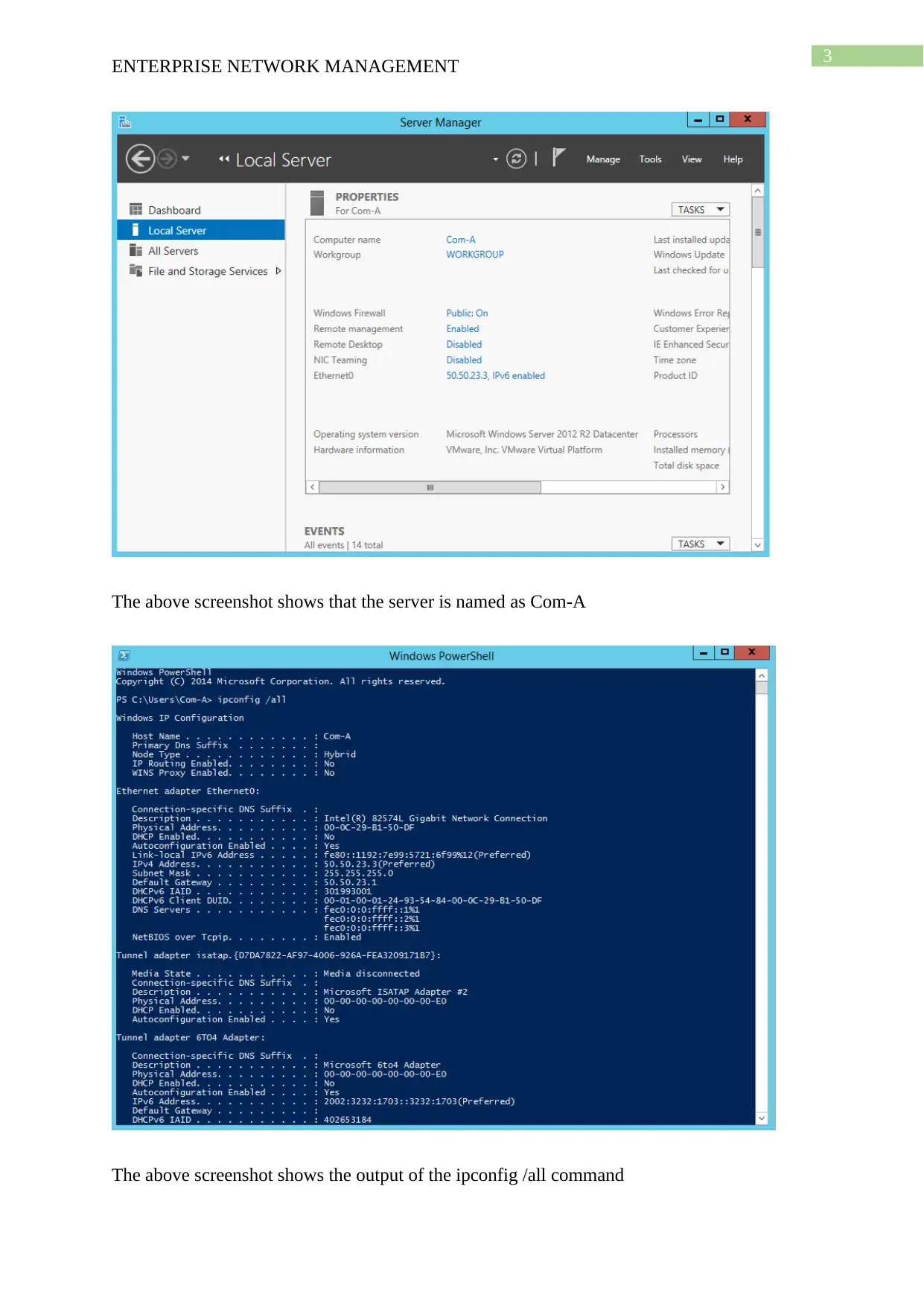
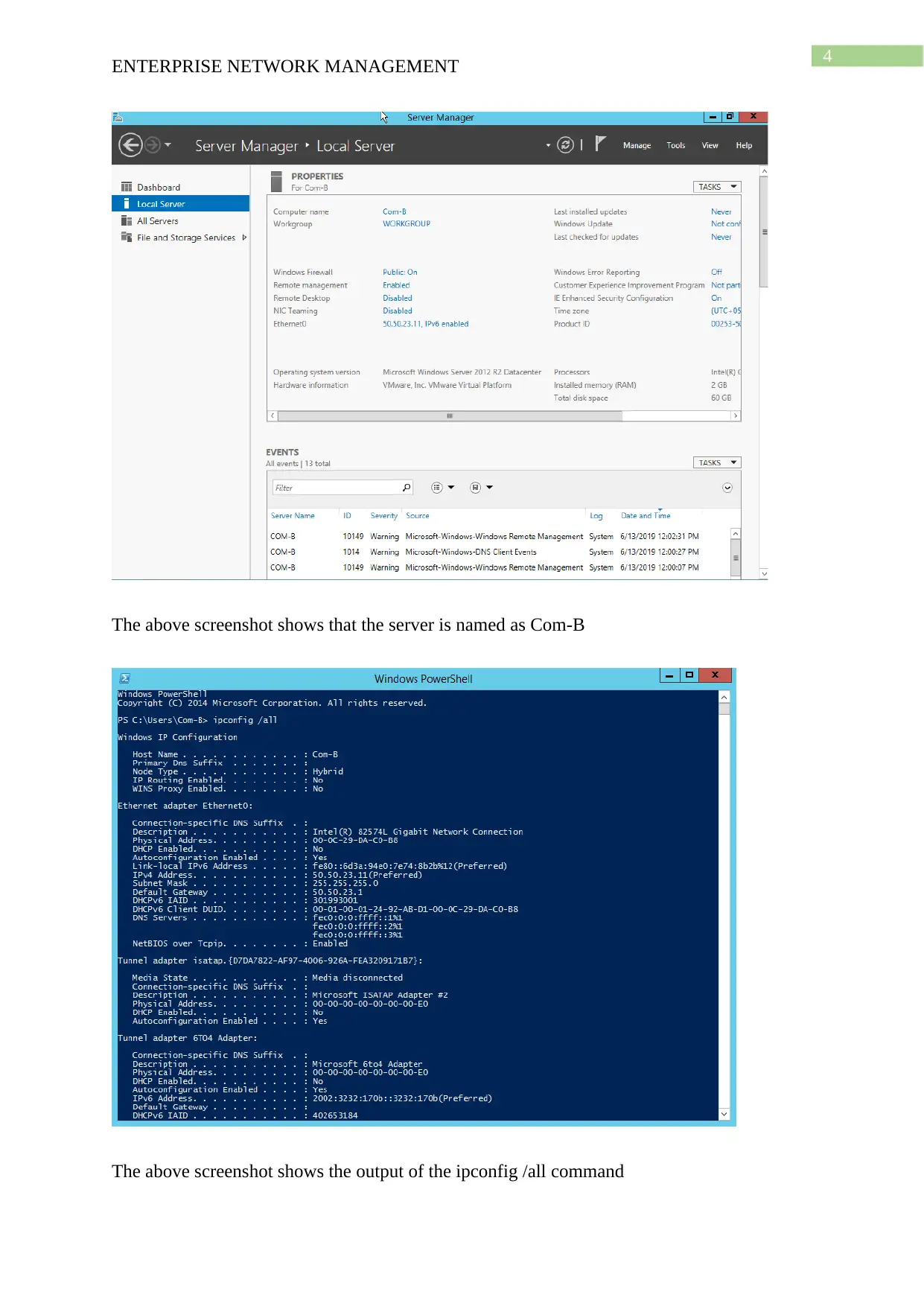
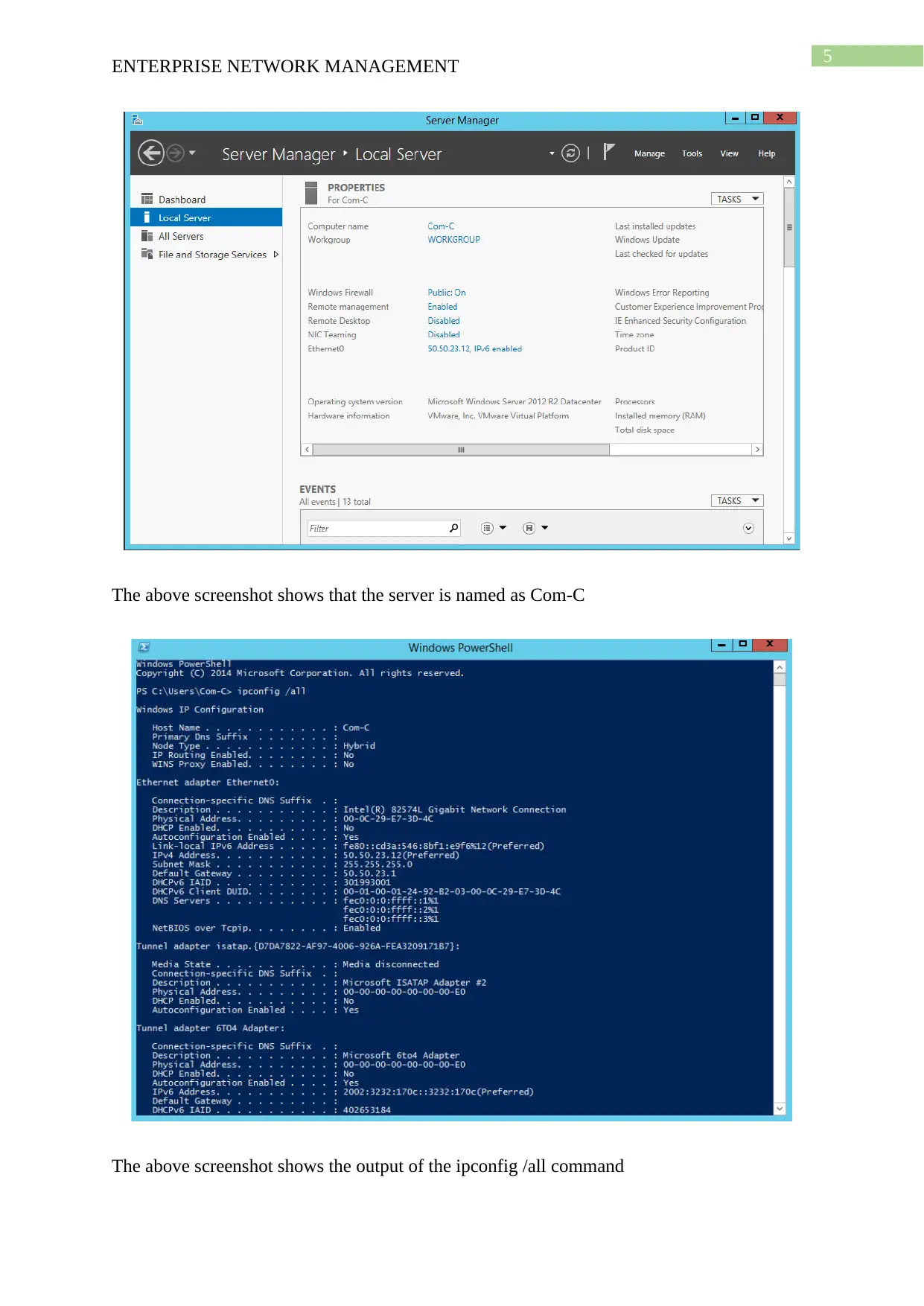
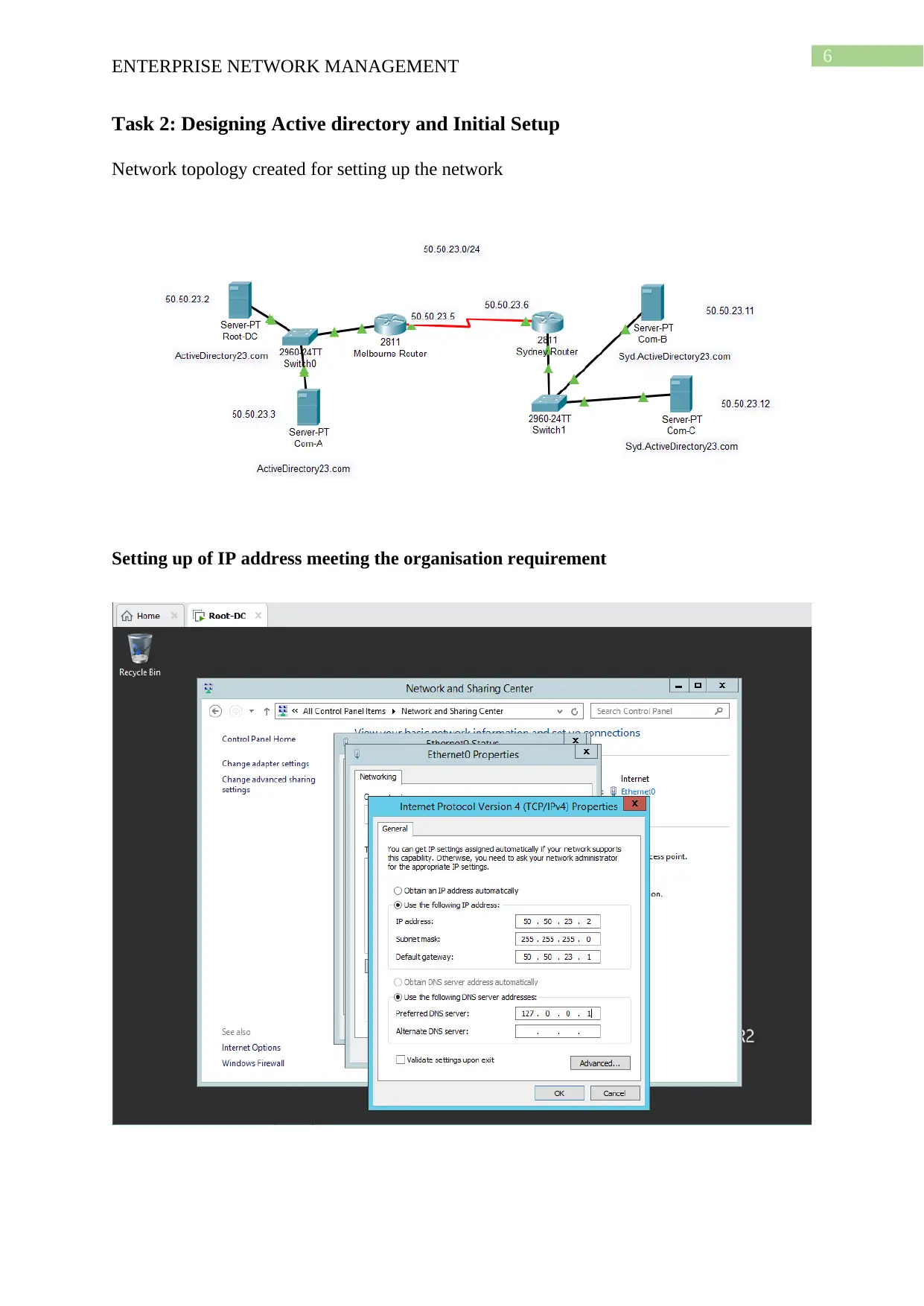
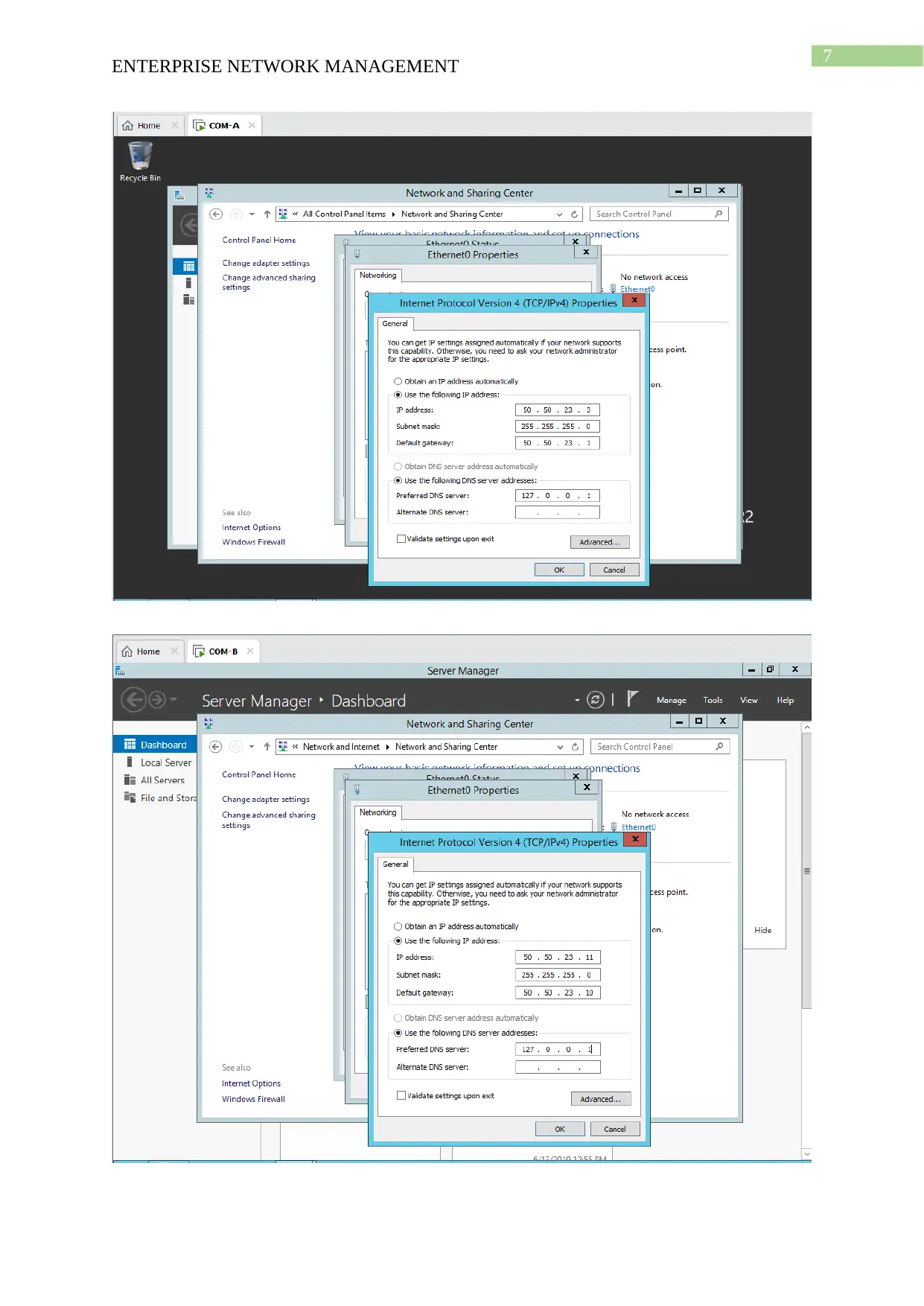
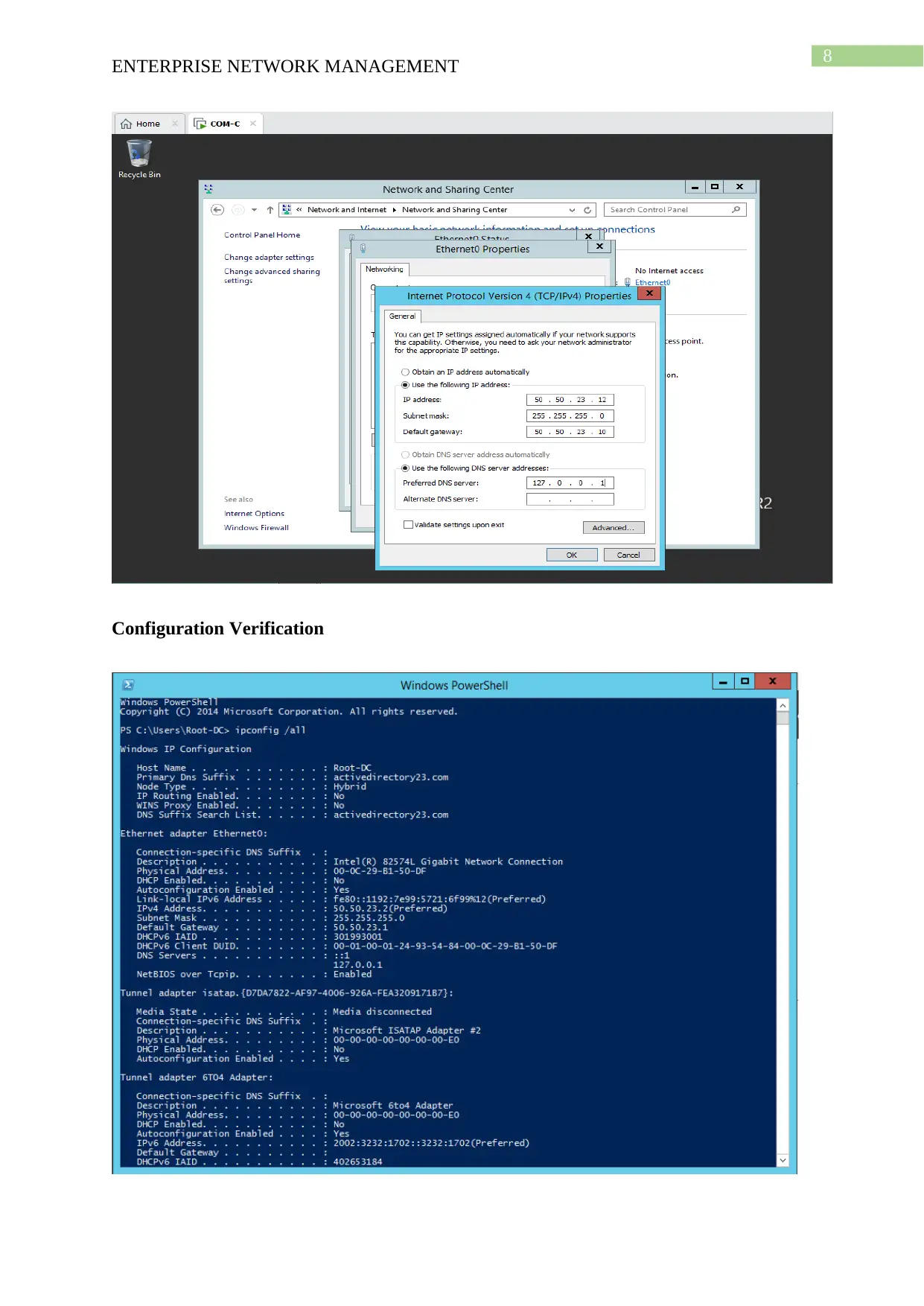
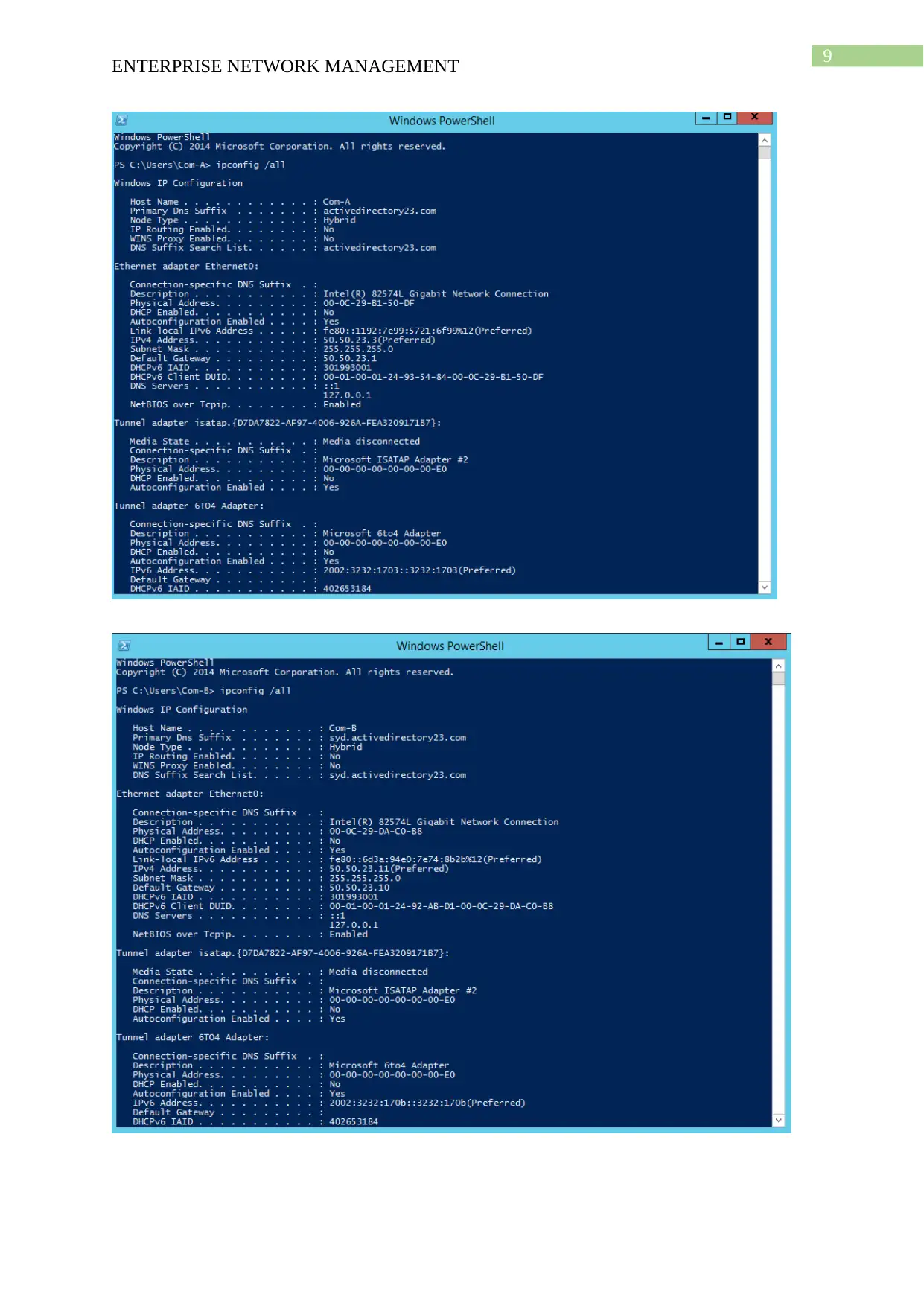
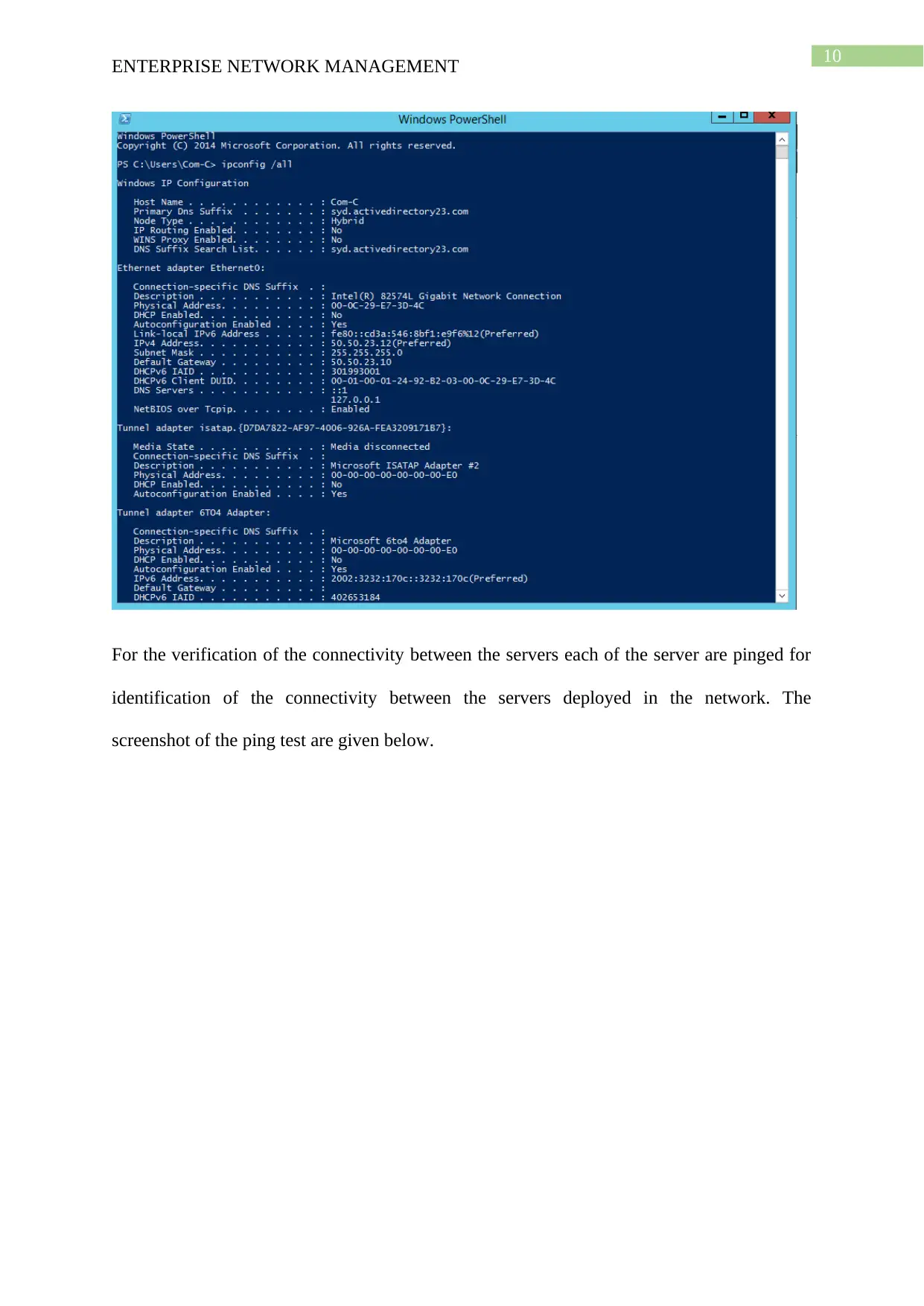
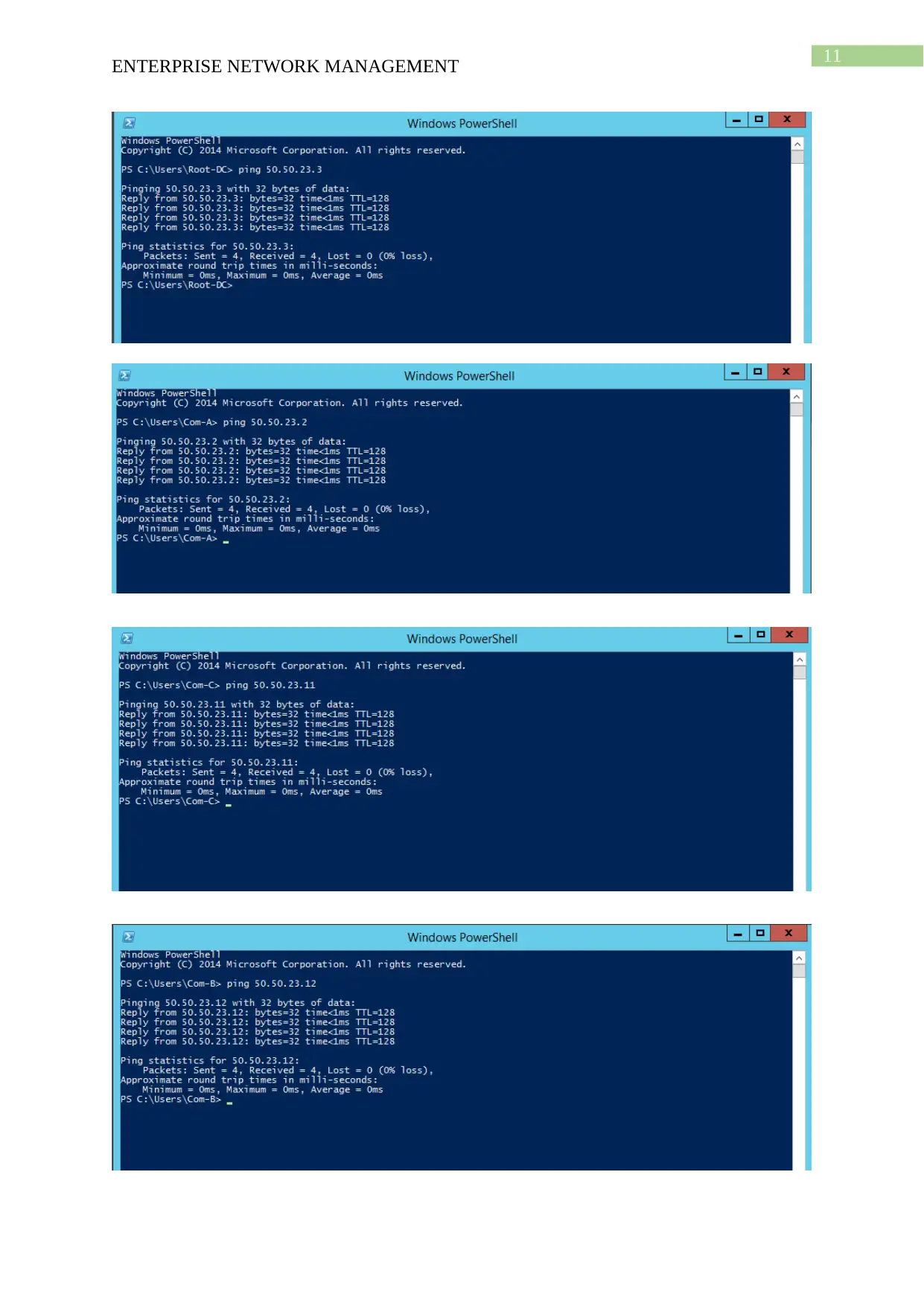
This project solution outlines the design and implementation of an enterprise network using Windows Server 2012, based on a provided scenario involving ActiveDirectoryxx.com. The project covers computer preparation with VMware, including the configuration of four virtual machines (Root-DC, Com-A, Com-B, and Com-C). It details the design of an Active Directory infrastructure, including IP address setup, domain controller configuration (including a Read-Only Domain Controller), and a child domain (Syd.ActiveDirectoryxx.com). The solution further explains Active Directory management, covering group management, user account management (creation and policy enforcement), and policies applications such as automatic deletion of temp folder contents and software restriction policies using group policies to manage user access to applications like Internet Explorer. Connectivity verification between servers using ping tests is also demonstrated.
1 out of 29







![[object Object]](/_next/static/media/star-bottom.7253800d.svg)