University Network Design and Implementation Report, QAC020N253
VerifiedAdded on 2022/08/08
|17
|3681
|29
Report
AI Summary
This report presents a comprehensive network design and implementation plan for Speedfix.co.uk, a small business with four departments. The design incorporates four servers (email, DNS, web, and file server), departmental sub-routers connected to a main router, workstations, and printers. The report delves into network components such as routers, switches, connecting cables, VLANs, trunking, access control, and DHCP. It evaluates different network models (TCP and OSI), analyzes the requirements for scalability, security, and availability. The analysis includes detailed explanations of the various network components and their functions, along with diagrams. The aim is to provide Speedfix.co.uk with a robust and efficient network infrastructure that aligns with its business objectives. The report also covers testing, documentation, and reflection on the design process.

Running head: - NETWORK DESIGN AND IMPLEMENTATION
NETWORK DESIGN AND IMPLEMENTATION
Name of the Student
Name of the University
Author Note
NETWORK DESIGN AND IMPLEMENTATION
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK DESIGN AND IMPLEMENTATION
Table of Contents
1. Introduction............................................................................................................................2
2. Knowledge and Understanding..............................................................................................2
3. Analysis..................................................................................................................................3
4. Evaluation of different components.......................................................................................5
4.1 Router...............................................................................................................................5
4.2 Switch...............................................................................................................................6
4.3 Connecting Cables...........................................................................................................7
4.4 VLANs.............................................................................................................................8
4.5 Trunking...........................................................................................................................8
4.6 Access Control.................................................................................................................9
4.7 DHCP...............................................................................................................................9
5. Network Design...................................................................................................................10
6. Testing and Documentation.................................................................................................11
7. Reflection.............................................................................................................................12
8. References............................................................................................................................14
Table of Contents
1. Introduction............................................................................................................................2
2. Knowledge and Understanding..............................................................................................2
3. Analysis..................................................................................................................................3
4. Evaluation of different components.......................................................................................5
4.1 Router...............................................................................................................................5
4.2 Switch...............................................................................................................................6
4.3 Connecting Cables...........................................................................................................7
4.4 VLANs.............................................................................................................................8
4.5 Trunking...........................................................................................................................8
4.6 Access Control.................................................................................................................9
4.7 DHCP...............................................................................................................................9
5. Network Design...................................................................................................................10
6. Testing and Documentation.................................................................................................11
7. Reflection.............................................................................................................................12
8. References............................................................................................................................14

2NETWORK DESIGN AND IMPLEMENTATION
1. Introduction
Speedfix.co.uk is a small company that operates within the field of business that has
been in possession of a network for a long time but wants to design as well as implement a
new design to change the entire network architecture of the same (Govindan, Fattahi and
Keyvanshokooh 2017). Mainly, the company has four primary departments, which are
Finance, or the HR department, sales department, engineers as well as Administration
department. The newly proposed network will have the inclusion of four servers namely,
email, DNS, web as well as the common server for the files. Every individual user of the
organization will utilize all of the servers that will be implemented within the network. As a
part of the network, each of the four departments of the network will have a specific router
that will act as a sub-router receiving the connection from the main router of the organization.
Along with this, each of the department will be supplied with respective number of
workstations along with single printers for the work that is carried out within the
organizations (Tofighi, Torabi and Mansouri 2016). This report will also aim towards the
scalability, security as well as availability of the entire network infrastructure that will
provision the speedfix.co.uk company to have a better understanding of the business
objectives and to carry out the same set of actions with better efficiency. Various network
models have been studied to design the network.
2. Knowledge and Understanding
The network that belongs to speedfix.co.uk shall be designed having a complete
dependency upon the departments with their individual components that will provision with a
helping hand towards building the entire infrastructure of the network. In general, network
design commonly refers to the fact of carrying out the mechanisms that specifically deals
with the transport of data from one end to the other (Ceselli, Premoli and Secci 2017). In
1. Introduction
Speedfix.co.uk is a small company that operates within the field of business that has
been in possession of a network for a long time but wants to design as well as implement a
new design to change the entire network architecture of the same (Govindan, Fattahi and
Keyvanshokooh 2017). Mainly, the company has four primary departments, which are
Finance, or the HR department, sales department, engineers as well as Administration
department. The newly proposed network will have the inclusion of four servers namely,
email, DNS, web as well as the common server for the files. Every individual user of the
organization will utilize all of the servers that will be implemented within the network. As a
part of the network, each of the four departments of the network will have a specific router
that will act as a sub-router receiving the connection from the main router of the organization.
Along with this, each of the department will be supplied with respective number of
workstations along with single printers for the work that is carried out within the
organizations (Tofighi, Torabi and Mansouri 2016). This report will also aim towards the
scalability, security as well as availability of the entire network infrastructure that will
provision the speedfix.co.uk company to have a better understanding of the business
objectives and to carry out the same set of actions with better efficiency. Various network
models have been studied to design the network.
2. Knowledge and Understanding
The network that belongs to speedfix.co.uk shall be designed having a complete
dependency upon the departments with their individual components that will provision with a
helping hand towards building the entire infrastructure of the network. In general, network
design commonly refers to the fact of carrying out the mechanisms that specifically deals
with the transport of data from one end to the other (Ceselli, Premoli and Secci 2017). In
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK DESIGN AND IMPLEMENTATION
accordance to principles of network, the organization network will be developed as well as
designed with the help of the primary analysis method requiring the necessary components
that will be working within the entire network of the organization. After this, the entire
network will be built on the basis of the requirements that is stated by the client during the
phase of implementation.
The network will have the primary inclusion of four servers namely the likes of
common file, web, DNS as well as the email server. The server within the field of network
particularly refers to the system that provisions all the other components of the network with
the internet connection that is required on a daily basis (Park et al. 2017). Hence, the
individual servers that have been mentioned to be included within the network will either
create a LAN (Local Area Network) or a WAN (Wide Area Network) including all the
components of the network. Hence, all the four servers individually will carry out the
activities of fulfilling the primary objectives associated with the network of speedfix.co.uk.
As a reason, the network that has been undertaken for designing as well as
implementation will be developed using the star topology for the fact that each of the
department will be having a specific router that will be connected to a main router
provisioning all the components such as the workstations and the printers with internet
connection.
3. Analysis
The network that has been designed for the organization named speedfix.co.uk had
been developed following such methods that no other existing department will be able to
gather information or communicate with the other workstations of the existing departments
(Rhu et al. 2016). All the computers from individual departments will be functioning as well
as performing all the activities with the help of getting connected to the DHCP server. On the
accordance to principles of network, the organization network will be developed as well as
designed with the help of the primary analysis method requiring the necessary components
that will be working within the entire network of the organization. After this, the entire
network will be built on the basis of the requirements that is stated by the client during the
phase of implementation.
The network will have the primary inclusion of four servers namely the likes of
common file, web, DNS as well as the email server. The server within the field of network
particularly refers to the system that provisions all the other components of the network with
the internet connection that is required on a daily basis (Park et al. 2017). Hence, the
individual servers that have been mentioned to be included within the network will either
create a LAN (Local Area Network) or a WAN (Wide Area Network) including all the
components of the network. Hence, all the four servers individually will carry out the
activities of fulfilling the primary objectives associated with the network of speedfix.co.uk.
As a reason, the network that has been undertaken for designing as well as
implementation will be developed using the star topology for the fact that each of the
department will be having a specific router that will be connected to a main router
provisioning all the components such as the workstations and the printers with internet
connection.
3. Analysis
The network that has been designed for the organization named speedfix.co.uk had
been developed following such methods that no other existing department will be able to
gather information or communicate with the other workstations of the existing departments
(Rhu et al. 2016). All the computers from individual departments will be functioning as well
as performing all the activities with the help of getting connected to the DHCP server. On the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK DESIGN AND IMPLEMENTATION
other hand, VLAN technology shall be used for the purpose of connection the routers with
that of the switch.
There shall also be the existence of access control with the help of which access will
be prevented from other departments into a respective department to prevent gathering or
might as well as prevent the department from accessing other information that is no relatable
to respective activities (Sachs et al. 2018). However, all the workstations belonging to
individual department of the company will have the provision to access all the four servers
that will be a part of the network infrastructure belonging to speedfix.co.uk organization. This
particular connection will be built using dedicated switches.
The differently existing models of network that can be approached while designing
the entire network of the company have been briefly discussed below for proper
implementation. These are,
TCP Model- this commonly refers to a respective model within the field of network
that has been developed much before the OSI model of networking had come into
play. Hence, this states forward the fact that there is the shared existence of difference
from the OSI model of networking (Zhang et al. 2018). This particular model has the
primary inclusion of five layers namely the likes of application, transport, network,
data link along with the physical layer. In addition to this, the TCP model has no
inclusion of any limitations in regards to the procedure of implementation.
OSI Model- this refers to the major sized model for communication within the field of
networking that is directly associated with the workstations and have the primary
responsibility of building up the connection and making the network work in a proper
manner with successful communication. OSI particularly stands for Open System
Interconnection (Boland et al. 2017). The name specifically states the fact that this
other hand, VLAN technology shall be used for the purpose of connection the routers with
that of the switch.
There shall also be the existence of access control with the help of which access will
be prevented from other departments into a respective department to prevent gathering or
might as well as prevent the department from accessing other information that is no relatable
to respective activities (Sachs et al. 2018). However, all the workstations belonging to
individual department of the company will have the provision to access all the four servers
that will be a part of the network infrastructure belonging to speedfix.co.uk organization. This
particular connection will be built using dedicated switches.
The differently existing models of network that can be approached while designing
the entire network of the company have been briefly discussed below for proper
implementation. These are,
TCP Model- this commonly refers to a respective model within the field of network
that has been developed much before the OSI model of networking had come into
play. Hence, this states forward the fact that there is the shared existence of difference
from the OSI model of networking (Zhang et al. 2018). This particular model has the
primary inclusion of five layers namely the likes of application, transport, network,
data link along with the physical layer. In addition to this, the TCP model has no
inclusion of any limitations in regards to the procedure of implementation.
OSI Model- this refers to the major sized model for communication within the field of
networking that is directly associated with the workstations and have the primary
responsibility of building up the connection and making the network work in a proper
manner with successful communication. OSI particularly stands for Open System
Interconnection (Boland et al. 2017). The name specifically states the fact that this

5NETWORK DESIGN AND IMPLEMENTATION
model of network can only be included into the network models that already have an
existence making the OSI model highly adaptable. The OSI model of network can be
properly utilized for the purpose of making all the devices work together that already
share an existence within a respective network and to carry out the communication in
an efficient manner. This particular model of network has the inclusion of seven
primary layers that are the likes of Physical, network, presentation, data link,
transport, application as well as session.
4. Evaluation of different components
All of the components that have a primary existence within the network of
speedfix.co.uk has been briefly discussed below with all the necessary details that is required
for the basic knowledge with the help of implementing the same (González et al. 2016).
Various components have been utilized to make the network properly working with
provisioning highly efficient results to improve the business activities of speedfix.co.uk.
4.1 Router
Every single department of the organization working within speedfix.co.uk has been
provisioned with an individual router that will be acting as a sub-router that will again be
connected to the main router of the organization. This connection is the primary reason that
each of the workstations of the company shall be getting the internet connectivity along with
the printers that will need the same (Babazadeh et al. 2017). Router is a network device that
commonly refers to the activity of forwarding the data packets from the source to that of the
destination. In this scenario, the data packets shall be supplied to the workstations along with
the printers of each individual department from that of the four servers present within the
organization itself.
model of network can only be included into the network models that already have an
existence making the OSI model highly adaptable. The OSI model of network can be
properly utilized for the purpose of making all the devices work together that already
share an existence within a respective network and to carry out the communication in
an efficient manner. This particular model of network has the inclusion of seven
primary layers that are the likes of Physical, network, presentation, data link,
transport, application as well as session.
4. Evaluation of different components
All of the components that have a primary existence within the network of
speedfix.co.uk has been briefly discussed below with all the necessary details that is required
for the basic knowledge with the help of implementing the same (González et al. 2016).
Various components have been utilized to make the network properly working with
provisioning highly efficient results to improve the business activities of speedfix.co.uk.
4.1 Router
Every single department of the organization working within speedfix.co.uk has been
provisioned with an individual router that will be acting as a sub-router that will again be
connected to the main router of the organization. This connection is the primary reason that
each of the workstations of the company shall be getting the internet connectivity along with
the printers that will need the same (Babazadeh et al. 2017). Router is a network device that
commonly refers to the activity of forwarding the data packets from the source to that of the
destination. In this scenario, the data packets shall be supplied to the workstations along with
the printers of each individual department from that of the four servers present within the
organization itself.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK DESIGN AND IMPLEMENTATION
Figure-1: Router
(Source- Babazadeh et al. 2017)
4.2 Switch
Individual sub-routers of the department shall have a specific connection to the
computer systems present within the respective departments with the help of a separate
switch. Each of the switch will have the total control over switching on or off the entire
connection that will be coming in from the main router of the organization that will again
have a connection to the server of the organization (Radosavovic et al. 2019). A switch is that
network device that has the primary responsibility of making connections between the source
of a connection and that of the end device that has the requirement of network connection for
working properly. The switches make use of the data packet switching technology. Hence,
switches are primarily utilized for receiving, along with that of sending data to the respective
workstations as well as the devices present on the receiving end.
Figure-2: Switch
(Source- Radosavovic et al. 2019)
Figure-1: Router
(Source- Babazadeh et al. 2017)
4.2 Switch
Individual sub-routers of the department shall have a specific connection to the
computer systems present within the respective departments with the help of a separate
switch. Each of the switch will have the total control over switching on or off the entire
connection that will be coming in from the main router of the organization that will again
have a connection to the server of the organization (Radosavovic et al. 2019). A switch is that
network device that has the primary responsibility of making connections between the source
of a connection and that of the end device that has the requirement of network connection for
working properly. The switches make use of the data packet switching technology. Hence,
switches are primarily utilized for receiving, along with that of sending data to the respective
workstations as well as the devices present on the receiving end.
Figure-2: Switch
(Source- Radosavovic et al. 2019)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK DESIGN AND IMPLEMENTATION
4.3 Connecting Cables
Connecting cables commonly refer to the primary components that are specifically
needed within the designing of a network for establishing the connections within all the other
existing components of the network as well as to carry out the transfer of data packets and
that of the internet connectivity. Within the network design of the speedfix.co.uk
organization, the main router of company has been connected to all the sub-routers belonging
to the different departments with the help of serial DTE cables (Crainic et al. 2016). This
specific cable puts forward the allowance for an efficient connection of carrying the data
packets across the whole network of the company increasing the efficiency of the same.
On the other hand, the switch that completely belongs to every department of the
company has been connected to the workstations with the help of Connecting Copper wires to
establish a secure as well as a faster communication of internet connectivity. These wires also
safeguard the information that is been communicated from the source to the destination or
vice versa against data leakage to external sources.
Hence, each of the primary building components of the entire network has been
provisioned with the best quality products keeping in the fact that speedfix.co.uk is an
organization that carries out certain activities within the field of business that is in urgent
need of higher efficiency with proper end outcomes (Baker et al. 2016). In addition to this,
various technologies along with that of protocols have been utilized to make the network
advanced in regards to the digitalize technological advancement within the field of business.
4.3 Connecting Cables
Connecting cables commonly refer to the primary components that are specifically
needed within the designing of a network for establishing the connections within all the other
existing components of the network as well as to carry out the transfer of data packets and
that of the internet connectivity. Within the network design of the speedfix.co.uk
organization, the main router of company has been connected to all the sub-routers belonging
to the different departments with the help of serial DTE cables (Crainic et al. 2016). This
specific cable puts forward the allowance for an efficient connection of carrying the data
packets across the whole network of the company increasing the efficiency of the same.
On the other hand, the switch that completely belongs to every department of the
company has been connected to the workstations with the help of Connecting Copper wires to
establish a secure as well as a faster communication of internet connectivity. These wires also
safeguard the information that is been communicated from the source to the destination or
vice versa against data leakage to external sources.
Hence, each of the primary building components of the entire network has been
provisioned with the best quality products keeping in the fact that speedfix.co.uk is an
organization that carries out certain activities within the field of business that is in urgent
need of higher efficiency with proper end outcomes (Baker et al. 2016). In addition to this,
various technologies along with that of protocols have been utilized to make the network
advanced in regards to the digitalize technological advancement within the field of business.

8NETWORK DESIGN AND IMPLEMENTATION
Figure-3: Connecting Cables
(Source- Baker et al. 2016)
4.4 VLANs
The Virtual Area Network is the part of networking that deals with the broadcasting
domain in regards to the partition of the isolated computer network having the primary aim of
connecting to the data link layer (Zhong, Yan and Liu 2017). Installation of the Virtual Area
Network into the network of speedfix.co.uk will have the relative provision to allow the
administrators to have the existence of all the hosts to be connected to the same network with
the help of switches and gathering the internet connectivity from the common server that
exists.
4.5 Trunking
Trunking refers to a network term that has a specific existence within the field of
telecommunication that deals with the procedure of providing the access to all the clients that
exists within a network having a share of common lines along with that of frequencies
keeping aside the fact of providing them with the access of a specific individual note (Liptak
and Eren 2018). This particular structure resembles the structure of a tree having a single
trunk by with the inclusion of multiple branches within a network.
Figure-3: Connecting Cables
(Source- Baker et al. 2016)
4.4 VLANs
The Virtual Area Network is the part of networking that deals with the broadcasting
domain in regards to the partition of the isolated computer network having the primary aim of
connecting to the data link layer (Zhong, Yan and Liu 2017). Installation of the Virtual Area
Network into the network of speedfix.co.uk will have the relative provision to allow the
administrators to have the existence of all the hosts to be connected to the same network with
the help of switches and gathering the internet connectivity from the common server that
exists.
4.5 Trunking
Trunking refers to a network term that has a specific existence within the field of
telecommunication that deals with the procedure of providing the access to all the clients that
exists within a network having a share of common lines along with that of frequencies
keeping aside the fact of providing them with the access of a specific individual note (Liptak
and Eren 2018). This particular structure resembles the structure of a tree having a single
trunk by with the inclusion of multiple branches within a network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK DESIGN AND IMPLEMENTATION
4.6 Access Control
Access Control is the name of the procedure that deals with the fact of placing a
certain kind of limitation upon a node belonging to a respective network to make it secure
against any individual kind of unauthorized access from any external sources. Such nodes
need to be safeguarded against any existing clients who do not have a permission to access
that particular node and might result in intrusion activities. In regards to the network
infrastructure that has been designed for the business organization named speedfix.co.uk
consists of separate nodes belonging individual department of the company (Almoghathawi
et al. 2017). Every single node of the department that exists within the network of the
company, no other department will have the permission to access the node that belongs to
another department. As a result, each department will have a secured network that will
prevent other departments to access into the work and interfere with the same. This is the
primary activity that is carried out by the policies of access control within the field of
network.
Figure-4: Access Control
(Source- Zhong, Yan and Liu 2017)
4.7 DHCP
DHCP commonly stands for Dynamic Host Control Protocol that particularly refers to
management of protocols as well as the networks having a direct relation to internet
protocols. Within this protocol, the server that belongs to DHCP carries out the dynamic
assigning of IP addresses along with the other parameters of configuration network belonging
4.6 Access Control
Access Control is the name of the procedure that deals with the fact of placing a
certain kind of limitation upon a node belonging to a respective network to make it secure
against any individual kind of unauthorized access from any external sources. Such nodes
need to be safeguarded against any existing clients who do not have a permission to access
that particular node and might result in intrusion activities. In regards to the network
infrastructure that has been designed for the business organization named speedfix.co.uk
consists of separate nodes belonging individual department of the company (Almoghathawi
et al. 2017). Every single node of the department that exists within the network of the
company, no other department will have the permission to access the node that belongs to
another department. As a result, each department will have a secured network that will
prevent other departments to access into the work and interfere with the same. This is the
primary activity that is carried out by the policies of access control within the field of
network.
Figure-4: Access Control
(Source- Zhong, Yan and Liu 2017)
4.7 DHCP
DHCP commonly stands for Dynamic Host Control Protocol that particularly refers to
management of protocols as well as the networks having a direct relation to internet
protocols. Within this protocol, the server that belongs to DHCP carries out the dynamic
assigning of IP addresses along with the other parameters of configuration network belonging
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10NETWORK DESIGN AND IMPLEMENTATION
to individual devices present within the network to carry out communication with the other
existing IP networks in particular (Kyle-Davidson and Clark 2018). A server belonging to
DHCP provisions the computers with the allowance to request for IP addresses along with
other parameters of the network in an automated manner from the Internet Service Provider
(ISP). This particularly reduces the specific need of a network administrator and the work of
the administrator to manually assign IP addresses to all the devices that belongs to a
particular network (Andújar et al. 2017). However, absence of the DHCP server, the devices
or might as well be the computers that has the primary requirement of manual assignment of
IP addressed itself assigns an APIPA address to enable the procedure of communication
outside the existing local subnet.
On the other hand, DHCP servers can also be specifically implemented upon
networks that range from large size to that of home networks as well as campus networks. In
regards to this, a normal router or that of a residential gateway can also carry out the work of
a DHCP server in particular.
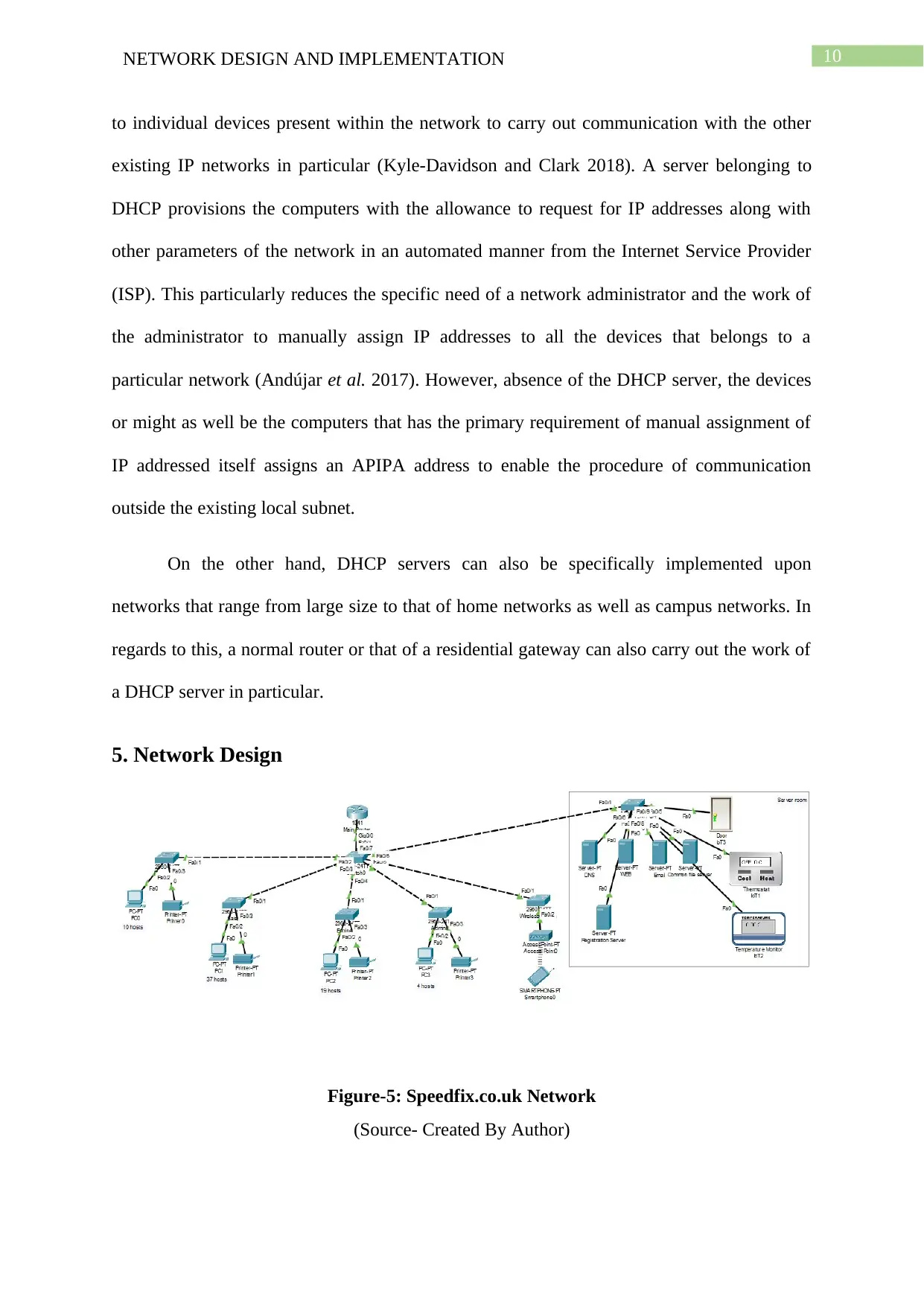
5. Network Design
Figure-5: Speedfix.co.uk Network
(Source- Created By Author)
to individual devices present within the network to carry out communication with the other
existing IP networks in particular (Kyle-Davidson and Clark 2018). A server belonging to
DHCP provisions the computers with the allowance to request for IP addresses along with
other parameters of the network in an automated manner from the Internet Service Provider
(ISP). This particularly reduces the specific need of a network administrator and the work of
the administrator to manually assign IP addresses to all the devices that belongs to a
particular network (Andújar et al. 2017). However, absence of the DHCP server, the devices
or might as well be the computers that has the primary requirement of manual assignment of
IP addressed itself assigns an APIPA address to enable the procedure of communication
outside the existing local subnet.
On the other hand, DHCP servers can also be specifically implemented upon
networks that range from large size to that of home networks as well as campus networks. In
regards to this, a normal router or that of a residential gateway can also carry out the work of
a DHCP server in particular.
5. Network Design
Figure-5: Speedfix.co.uk Network
(Source- Created By Author)
11NETWORK DESIGN AND IMPLEMENTATION
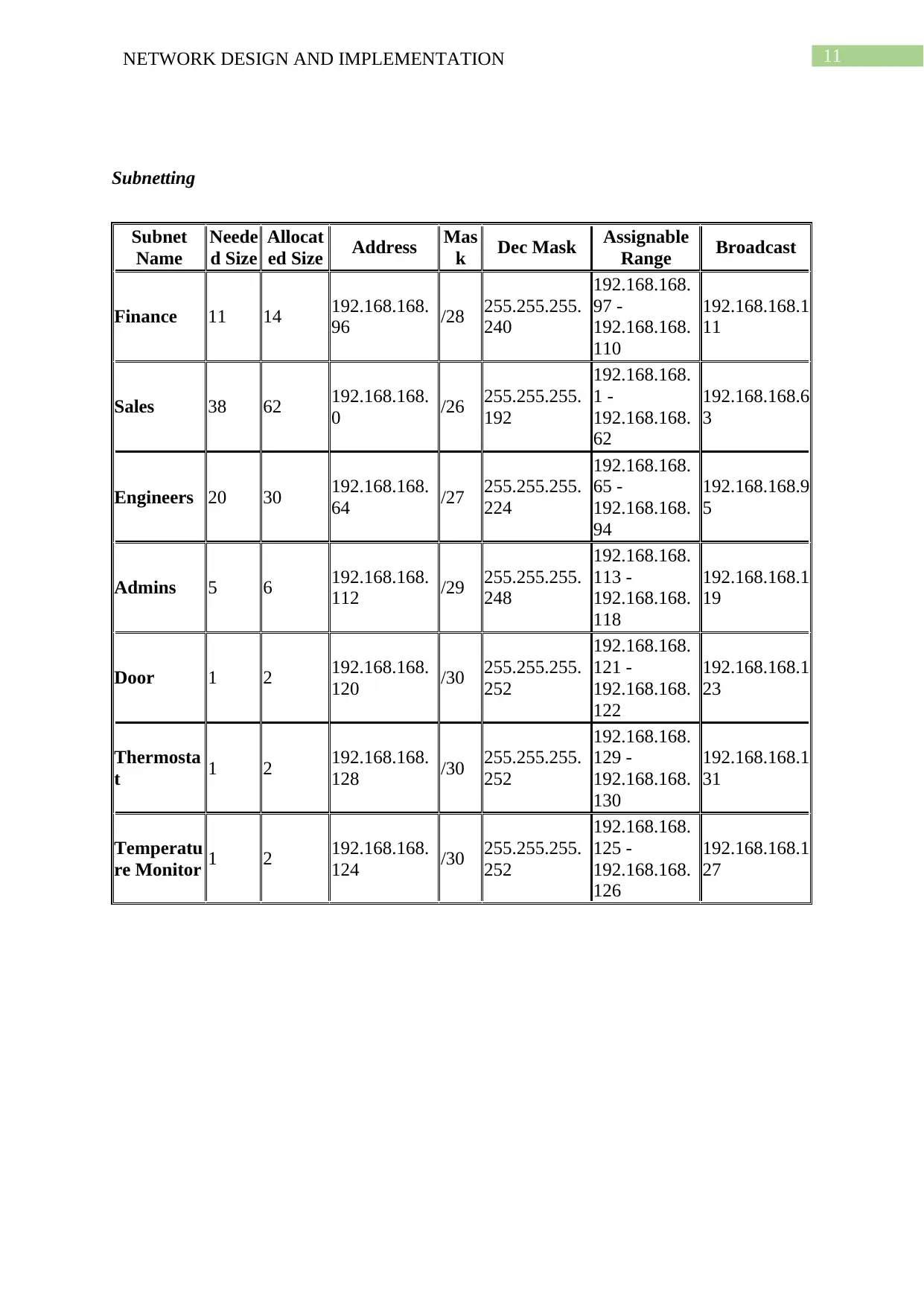
Subnetting
Subnet
Name
Neede
d Size
Allocat
ed Size Address Mas
k Dec Mask Assignable
Range Broadcast
Finance 11 14 192.168.168.
96 /28 255.255.255.
240
192.168.168.
97 -
192.168.168.
110
192.168.168.1
11
Sales 38 62 192.168.168.
0 /26 255.255.255.
192
192.168.168.
1 -
192.168.168.
62
192.168.168.6
3
Engineers 20 30 192.168.168.
64 /27 255.255.255.
224
192.168.168.
65 -
192.168.168.
94
192.168.168.9
5
Admins 5 6 192.168.168.
112 /29 255.255.255.
248
192.168.168.
113 -
192.168.168.
118
192.168.168.1
19
Door 1 2 192.168.168.
120 /30 255.255.255.
252
192.168.168.
121 -
192.168.168.
122
192.168.168.1
23
Thermosta
t 1 2 192.168.168.
128 /30 255.255.255.
252
192.168.168.
129 -
192.168.168.
130
192.168.168.1
31
Temperatu
re Monitor 1 2 192.168.168.
124 /30 255.255.255.
252
192.168.168.
125 -
192.168.168.
126
192.168.168.1
27
Subnetting
Subnet
Name
Neede
d Size
Allocat
ed Size Address Mas
k Dec Mask Assignable
Range Broadcast
Finance 11 14 192.168.168.
96 /28 255.255.255.
240
192.168.168.
97 -
192.168.168.
110
192.168.168.1
11
Sales 38 62 192.168.168.
0 /26 255.255.255.
192
192.168.168.
1 -
192.168.168.
62
192.168.168.6
3
Engineers 20 30 192.168.168.
64 /27 255.255.255.
224
192.168.168.
65 -
192.168.168.
94
192.168.168.9
5
Admins 5 6 192.168.168.
112 /29 255.255.255.
248
192.168.168.
113 -
192.168.168.
118
192.168.168.1
19
Door 1 2 192.168.168.
120 /30 255.255.255.
252
192.168.168.
121 -
192.168.168.
122
192.168.168.1
23
Thermosta
t 1 2 192.168.168.
128 /30 255.255.255.
252
192.168.168.
129 -
192.168.168.
130
192.168.168.1
31
Temperatu
re Monitor 1 2 192.168.168.
124 /30 255.255.255.
252
192.168.168.
125 -
192.168.168.
126
192.168.168.1
27
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




