Organization Network Design: Implementation and Protocols
VerifiedAdded on 2023/05/23
|10
|2270
|284
Report
AI Summary
This report provides a comprehensive overview of network design and implementation for an organization, focusing on a campus staff block as a case study. It covers key aspects such as network design approaches (top-down), the OSI model, TCP/IP protocols, IP addressing and subnetting, network devices (routers, firewalls, hubs, switches), network topologies (star topology), and routing design. The report details the practical implementation of the network design, emphasizing the importance of cost considerations, future extensibility, and the selection of appropriate hardware (UTP cables, Ethernet connectors, switches). Furthermore, it addresses troubleshooting strategies, including traffic management, network security measures (firewalls), and vulnerability prevention. The document concludes by highlighting the significance of a structured approach to network design, aligning with the organization's goals and technological requirements. Desklib offers a wide range of study resources, including past papers and solved assignments, to support students in mastering networking concepts and practical implementation.

NETWORK DESIGN AND IMPLEMENTATION
OF
THE NETWORK IN AN ORGANIZATION
OF
THE NETWORK IN AN ORGANIZATION
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Table of Contents...................................................................................................................................2
1.0 INTRODUCTION............................................................................................................................3
2.0 NETWORK DESIGN....................................................................................................................3
2.0.1 SCOPE OF THE DESIGN......................................................................................................3
2.0.2 INTERNATIONAL STANDARD FOR OPEN SYSTEMS INTERCONNECTION................4
2.0.3 INTERNET PROTOCOLS....................................................................................................4
2.0.3.1 IP ADDRESSING.............................................................................................................4
2.0.4 NETWORK DEVICES, TOPOLOGY AND CONNECTIVITY..............................................5
2.0.5 ROUTING DESIGN................................................................................................................6
2.1 IMPLEMENTATION OF NETWORK DESIGN.......................................................................7
2.3 TROUBLESHOOTING.................................................................................................................8
2.4 SUMMARY....................................................................................................................................9
References............................................................................................................................................10
Table of Contents...................................................................................................................................2
1.0 INTRODUCTION............................................................................................................................3
2.0 NETWORK DESIGN....................................................................................................................3
2.0.1 SCOPE OF THE DESIGN......................................................................................................3
2.0.2 INTERNATIONAL STANDARD FOR OPEN SYSTEMS INTERCONNECTION................4
2.0.3 INTERNET PROTOCOLS....................................................................................................4
2.0.3.1 IP ADDRESSING.............................................................................................................4
2.0.4 NETWORK DEVICES, TOPOLOGY AND CONNECTIVITY..............................................5
2.0.5 ROUTING DESIGN................................................................................................................6
2.1 IMPLEMENTATION OF NETWORK DESIGN.......................................................................7
2.3 TROUBLESHOOTING.................................................................................................................8
2.4 SUMMARY....................................................................................................................................9
References............................................................................................................................................10

1.0 INTRODUCTION
It is always advisable before any purchase of network equipment’s or even knowing the
platforms to be applied one may need to know the idea behind the problems of
communications. In the case here the network design to be put in to implementation should fit
the problems in existence in the organisation in need of the network (CPLEX:, 2007). When we
talk about the design of the network we refer to how the computers, routers, switches and
many other network gadgets are interconnected and far much the installation whether remote
or centralized and how they communicate with each other. In my discussion in explaining the
network design and the implementation of the network will major on network design,
topology and connectivity, address design and allocation, routing design, configuration
design, implementation network design and troubleshoot. A certain company that is within the
city requires a network design and all the concepts for networking needed to help in
implementing the network in the organization.
2.0 NETWORK DESIGN
There exist two major approaches used in analysing and designing networks namely the top-
down approach and the bottom-up approach. Considering the campus staff block we design
using the top-down approach making it simple when implementing. This is done by dividing
the major task in to small different design tasks making it to focus on the scope of the design
more and hence performed in a professional manner what may be termed to as what the
organization want before it submits it estimated budget. Campus staff block case after
analysing the goals, plans and the organization requirements the following design may apply
and fit better for the organization
2.0.1 SCOPE OF THE DESIGN
It is always advisable before one start gathering information and network plan it will be wise
to clearly understand the scope of the design and the analyses done thoroughly. This is
understanding the scope in that if there is any network in existence or also to know if there are
any network located in the area. what kind of network will suit the locality, the expected
hazards if the network is implemented and much more?
It is always advisable before any purchase of network equipment’s or even knowing the
platforms to be applied one may need to know the idea behind the problems of
communications. In the case here the network design to be put in to implementation should fit
the problems in existence in the organisation in need of the network (CPLEX:, 2007). When we
talk about the design of the network we refer to how the computers, routers, switches and
many other network gadgets are interconnected and far much the installation whether remote
or centralized and how they communicate with each other. In my discussion in explaining the
network design and the implementation of the network will major on network design,
topology and connectivity, address design and allocation, routing design, configuration
design, implementation network design and troubleshoot. A certain company that is within the
city requires a network design and all the concepts for networking needed to help in
implementing the network in the organization.
2.0 NETWORK DESIGN
There exist two major approaches used in analysing and designing networks namely the top-
down approach and the bottom-up approach. Considering the campus staff block we design
using the top-down approach making it simple when implementing. This is done by dividing
the major task in to small different design tasks making it to focus on the scope of the design
more and hence performed in a professional manner what may be termed to as what the
organization want before it submits it estimated budget. Campus staff block case after
analysing the goals, plans and the organization requirements the following design may apply
and fit better for the organization
2.0.1 SCOPE OF THE DESIGN
It is always advisable before one start gathering information and network plan it will be wise
to clearly understand the scope of the design and the analyses done thoroughly. This is
understanding the scope in that if there is any network in existence or also to know if there are
any network located in the area. what kind of network will suit the locality, the expected
hazards if the network is implemented and much more?
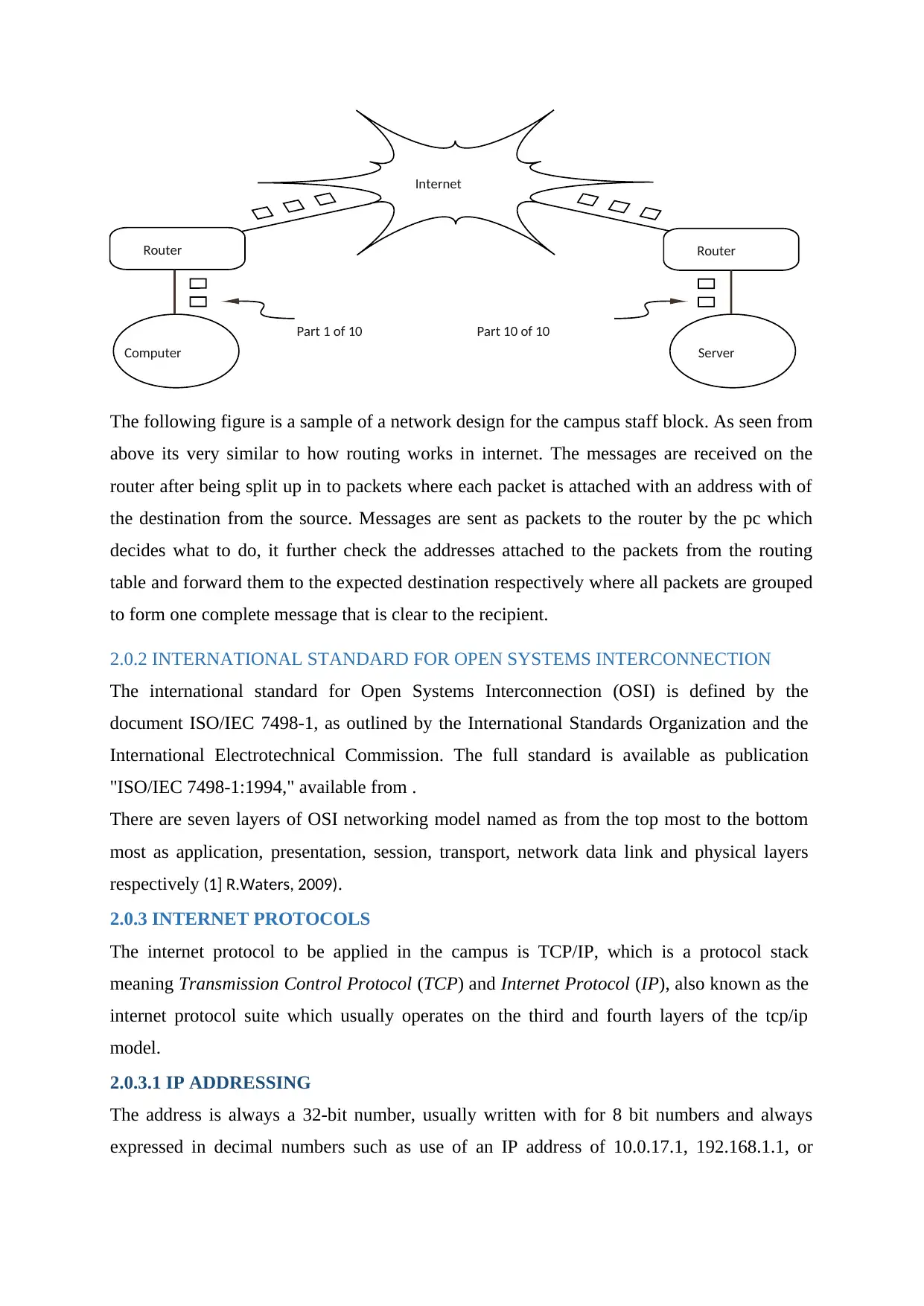
The following figure is a sample of a network design for the campus staff block. As seen from
above its very similar to how routing works in internet. The messages are received on the
router after being split up in to packets where each packet is attached with an address with of
the destination from the source. Messages are sent as packets to the router by the pc which
decides what to do, it further check the addresses attached to the packets from the routing
table and forward them to the expected destination respectively where all packets are grouped
to form one complete message that is clear to the recipient.
2.0.2 INTERNATIONAL STANDARD FOR OPEN SYSTEMS INTERCONNECTION
The international standard for Open Systems Interconnection (OSI) is defined by the
document ISO/IEC 7498-1, as outlined by the International Standards Organization and the
International Electrotechnical Commission. The full standard is available as publication
"ISO/IEC 7498-1:1994," available from .
There are seven layers of OSI networking model named as from the top most to the bottom
most as application, presentation, session, transport, network data link and physical layers
respectively (1] R.Waters, 2009).
2.0.3 INTERNET PROTOCOLS
The internet protocol to be applied in the campus is TCP/IP, which is a protocol stack
meaning Transmission Control Protocol (TCP) and Internet Protocol (IP), also known as the
internet protocol suite which usually operates on the third and fourth layers of the tcp/ip
model.
2.0.3.1 IP ADDRESSING
The address is always a 32-bit number, usually written with for 8 bit numbers and always
expressed in decimal numbers such as use of an IP address of 10.0.17.1, 192.168.1.1, or
Internet
RouterRouter
Computer Server
Part 10 of 10Part 1 of 10
above its very similar to how routing works in internet. The messages are received on the
router after being split up in to packets where each packet is attached with an address with of
the destination from the source. Messages are sent as packets to the router by the pc which
decides what to do, it further check the addresses attached to the packets from the routing
table and forward them to the expected destination respectively where all packets are grouped
to form one complete message that is clear to the recipient.
2.0.2 INTERNATIONAL STANDARD FOR OPEN SYSTEMS INTERCONNECTION
The international standard for Open Systems Interconnection (OSI) is defined by the
document ISO/IEC 7498-1, as outlined by the International Standards Organization and the
International Electrotechnical Commission. The full standard is available as publication
"ISO/IEC 7498-1:1994," available from .
There are seven layers of OSI networking model named as from the top most to the bottom
most as application, presentation, session, transport, network data link and physical layers
respectively (1] R.Waters, 2009).
2.0.3 INTERNET PROTOCOLS
The internet protocol to be applied in the campus is TCP/IP, which is a protocol stack
meaning Transmission Control Protocol (TCP) and Internet Protocol (IP), also known as the
internet protocol suite which usually operates on the third and fourth layers of the tcp/ip
model.
2.0.3.1 IP ADDRESSING
The address is always a 32-bit number, usually written with for 8 bit numbers and always
expressed in decimal numbers such as use of an IP address of 10.0.17.1, 192.168.1.1, or
Internet
RouterRouter
Computer Server
Part 10 of 10Part 1 of 10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

172.16.5.23 The addresses for IP come from a central authority that gives standard number in
a coherent way. Each and every network has its own unique IP addresses.
2.0.3.1.4 SUBNETS.
Subnets are applied by use of a subnet mask to an IP address that logically defines both the
host and in the network where it belongs. The subnet masks are usually denoted in decimal
form just like an ip address eg. 255.255.255.0 which is one of the common most known as
netmask. Subnet is used to determine the size of any given network. See the calculation
below, where in a total of 32bits we subtract 24 bits for the netmask we get 8 bits which are
reserved for the hosts.
32bits-24bits(netmask)= 8 bits for the host. This may yield up to 256 possible addresses.
Consider below 28=256 using convention theory the 1st value is considered to as network
address noted as 00000000 where the last digit is referred to as the broadcast address
11111111 and hence leaving 245 as the addresses meant for the hosts and the process
continues like that as per the need of the organization.
2.0.4 NETWORK DEVICES, TOPOLOGY AND CONNECTIVITY
In networks for the devices to communicate with each other internet protocols must be used
over the internet. The devices that interconnects with each other can be described as follows.
Routers and firewalls which usually provides connection on segments for local network,
where the work of the router is to forward the sent messages in form of packets between the
desired local network segments. Physically a router may have two or more physical network
interfaces. Routers are always installed with firewalls for filtering and redirecting packets that
may be insecure. Another part of the connectivity is that each and every machine has a mac
address assigned by the manufacturer that uniquely defines the machine or device over the
network especially when picked by another machine hence help in connectivity process and
hence easy communication. Hubs are devices used for connecting for more than one Ethernet
machines together and works at the lowest layer referred to as physical layer. Switch is much
like a hub but its dedication is based on ports and works by referencing which ports are
communicating by picking their address and providing easy connectivity between devices.
The following devices are applied in networking. Topology is the logical or physical
arrangement or layout of the above devices over the network. There are different types of
topologies namely bus, star, ring, mesh, hierarchical and hybrid topologies respectively. In
campus staff block the chosen topology is the star topology where all devices will be
a coherent way. Each and every network has its own unique IP addresses.
2.0.3.1.4 SUBNETS.
Subnets are applied by use of a subnet mask to an IP address that logically defines both the
host and in the network where it belongs. The subnet masks are usually denoted in decimal
form just like an ip address eg. 255.255.255.0 which is one of the common most known as
netmask. Subnet is used to determine the size of any given network. See the calculation
below, where in a total of 32bits we subtract 24 bits for the netmask we get 8 bits which are
reserved for the hosts.
32bits-24bits(netmask)= 8 bits for the host. This may yield up to 256 possible addresses.
Consider below 28=256 using convention theory the 1st value is considered to as network
address noted as 00000000 where the last digit is referred to as the broadcast address
11111111 and hence leaving 245 as the addresses meant for the hosts and the process
continues like that as per the need of the organization.
2.0.4 NETWORK DEVICES, TOPOLOGY AND CONNECTIVITY
In networks for the devices to communicate with each other internet protocols must be used
over the internet. The devices that interconnects with each other can be described as follows.
Routers and firewalls which usually provides connection on segments for local network,
where the work of the router is to forward the sent messages in form of packets between the
desired local network segments. Physically a router may have two or more physical network
interfaces. Routers are always installed with firewalls for filtering and redirecting packets that
may be insecure. Another part of the connectivity is that each and every machine has a mac
address assigned by the manufacturer that uniquely defines the machine or device over the
network especially when picked by another machine hence help in connectivity process and
hence easy communication. Hubs are devices used for connecting for more than one Ethernet
machines together and works at the lowest layer referred to as physical layer. Switch is much
like a hub but its dedication is based on ports and works by referencing which ports are
communicating by picking their address and providing easy connectivity between devices.
The following devices are applied in networking. Topology is the logical or physical
arrangement or layout of the above devices over the network. There are different types of
topologies namely bus, star, ring, mesh, hierarchical and hybrid topologies respectively. In
campus staff block the chosen topology is the star topology where all devices will be
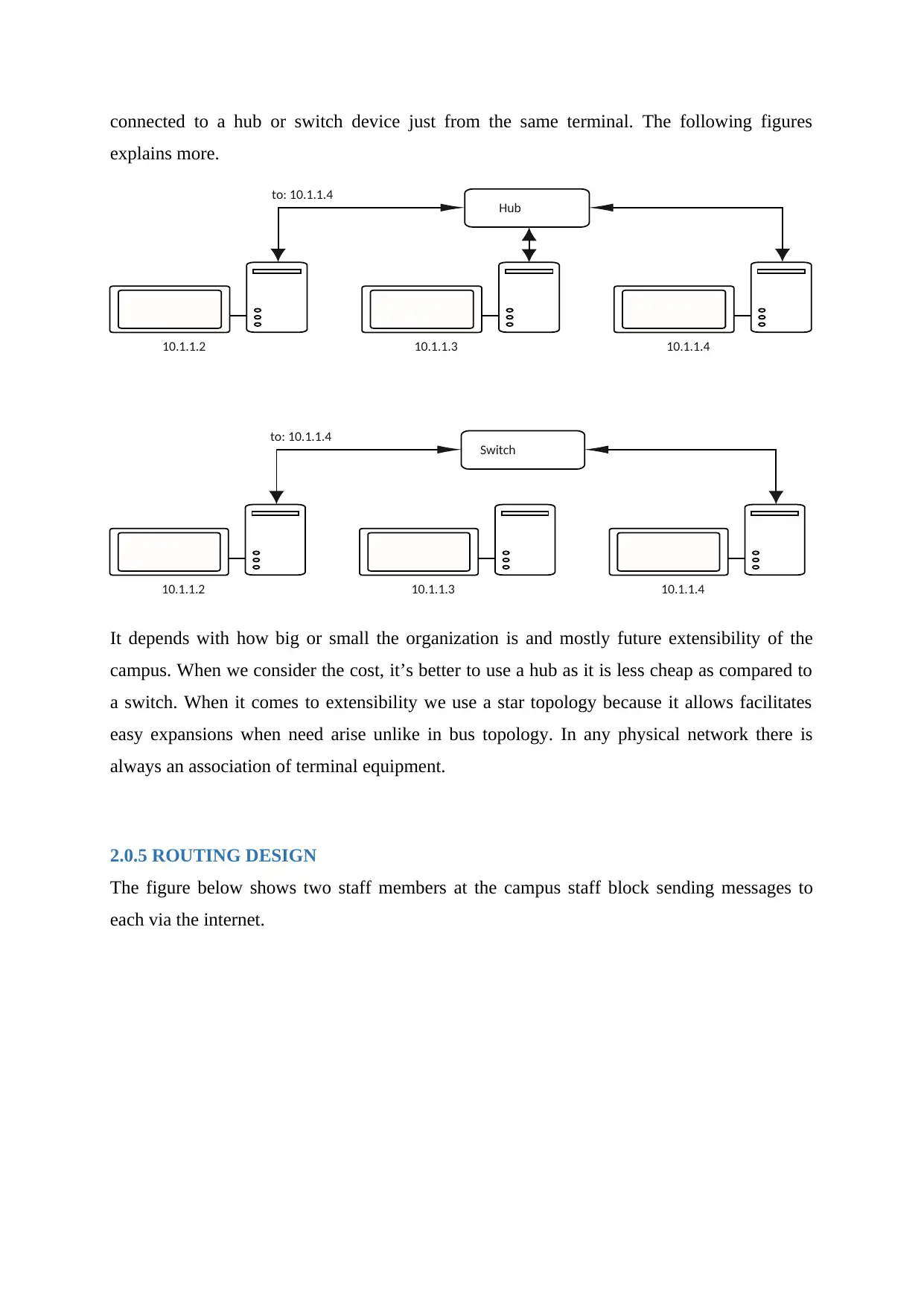
connected to a hub or switch device just from the same terminal. The following figures
explains more.
It depends with how big or small the organization is and mostly future extensibility of the
campus. When we consider the cost, it’s better to use a hub as it is less cheap as compared to
a switch. When it comes to extensibility we use a star topology because it allows facilitates
easy expansions when need arise unlike in bus topology. In any physical network there is
always an association of terminal equipment.
2.0.5 ROUTING DESIGN
The figure below shows two staff members at the campus staff block sending messages to
each via the internet.
10.1.1.2 10.1.1.3 10.1.1.4
Hub
to: 10.1.1.4
10.1.1.2 10.1.1.3 10.1.1.4
Switch
to: 10.1.1.4
explains more.
It depends with how big or small the organization is and mostly future extensibility of the
campus. When we consider the cost, it’s better to use a hub as it is less cheap as compared to
a switch. When it comes to extensibility we use a star topology because it allows facilitates
easy expansions when need arise unlike in bus topology. In any physical network there is
always an association of terminal equipment.
2.0.5 ROUTING DESIGN
The figure below shows two staff members at the campus staff block sending messages to
each via the internet.
10.1.1.2 10.1.1.3 10.1.1.4
Hub
to: 10.1.1.4
10.1.1.2 10.1.1.3 10.1.1.4
Switch
to: 10.1.1.4
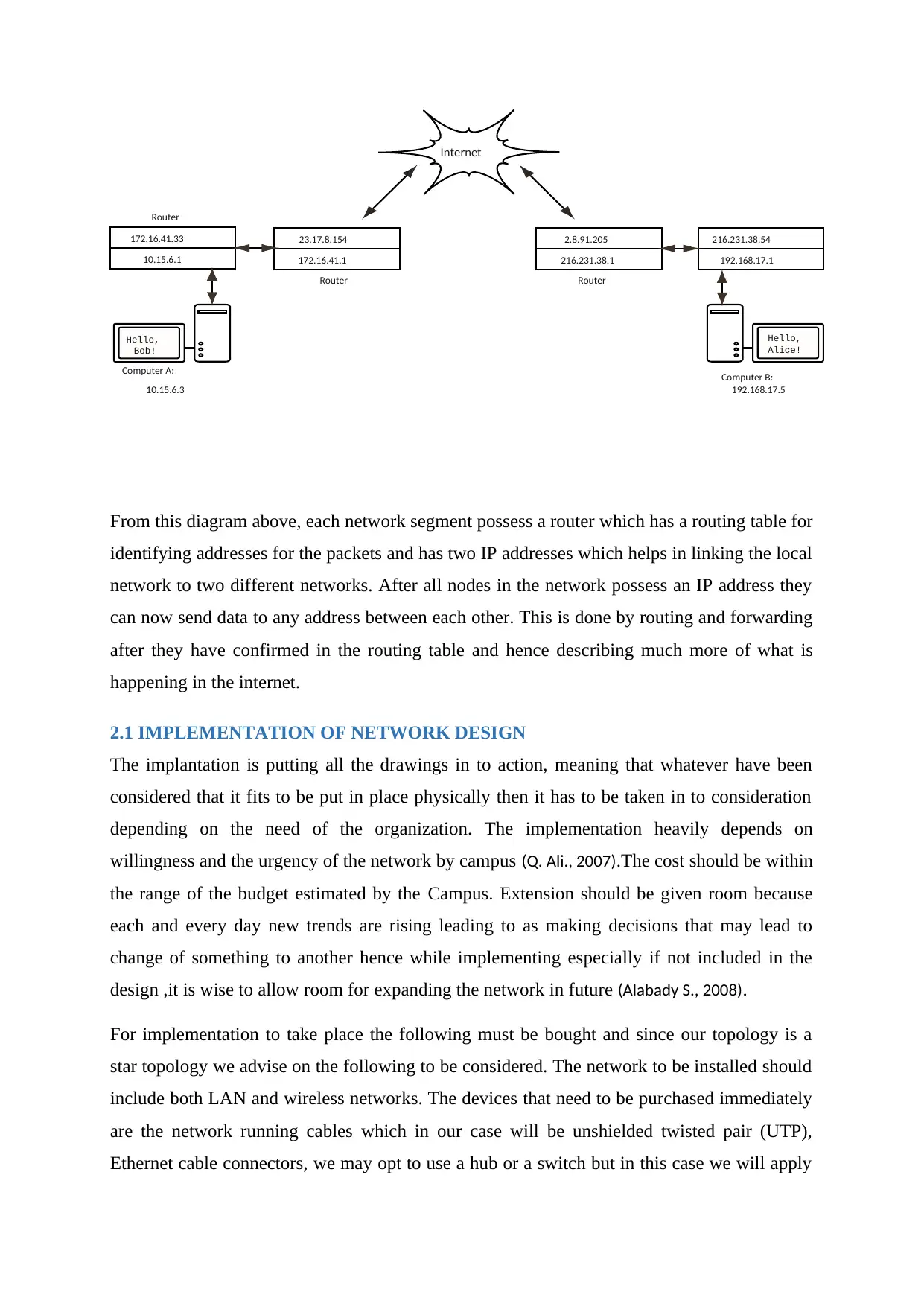
From this diagram above, each network segment possess a router which has a routing table for
identifying addresses for the packets and has two IP addresses which helps in linking the local
network to two different networks. After all nodes in the network possess an IP address they
can now send data to any address between each other. This is done by routing and forwarding
after they have confirmed in the routing table and hence describing much more of what is
happening in the internet.
2.1 IMPLEMENTATION OF NETWORK DESIGN
The implantation is putting all the drawings in to action, meaning that whatever have been
considered that it fits to be put in place physically then it has to be taken in to consideration
depending on the need of the organization. The implementation heavily depends on
willingness and the urgency of the network by campus (Q. Ali., 2007).The cost should be within
the range of the budget estimated by the Campus. Extension should be given room because
each and every day new trends are rising leading to as making decisions that may lead to
change of something to another hence while implementing especially if not included in the
design ,it is wise to allow room for expanding the network in future (Alabady S., 2008).
For implementation to take place the following must be bought and since our topology is a
star topology we advise on the following to be considered. The network to be installed should
include both LAN and wireless networks. The devices that need to be purchased immediately
are the network running cables which in our case will be unshielded twisted pair (UTP),
Ethernet cable connectors, we may opt to use a hub or a switch but in this case we will apply
Internet
2.8.91.205
216.231.38.1
23.17.8.154
172.16.41.1
Router
172.16.41.33
10.15.6.1
Computer A:
10.15.6.3
Hello,
Bob!
Router
Router
216.231.38.54
192.168.17.1
Hello,
Alice!
Computer B:
192.168.17.5
identifying addresses for the packets and has two IP addresses which helps in linking the local
network to two different networks. After all nodes in the network possess an IP address they
can now send data to any address between each other. This is done by routing and forwarding
after they have confirmed in the routing table and hence describing much more of what is
happening in the internet.
2.1 IMPLEMENTATION OF NETWORK DESIGN
The implantation is putting all the drawings in to action, meaning that whatever have been
considered that it fits to be put in place physically then it has to be taken in to consideration
depending on the need of the organization. The implementation heavily depends on
willingness and the urgency of the network by campus (Q. Ali., 2007).The cost should be within
the range of the budget estimated by the Campus. Extension should be given room because
each and every day new trends are rising leading to as making decisions that may lead to
change of something to another hence while implementing especially if not included in the
design ,it is wise to allow room for expanding the network in future (Alabady S., 2008).
For implementation to take place the following must be bought and since our topology is a
star topology we advise on the following to be considered. The network to be installed should
include both LAN and wireless networks. The devices that need to be purchased immediately
are the network running cables which in our case will be unshielded twisted pair (UTP),
Ethernet cable connectors, we may opt to use a hub or a switch but in this case we will apply
Internet
2.8.91.205
216.231.38.1
23.17.8.154
172.16.41.1
Router
172.16.41.33
10.15.6.1
Computer A:
10.15.6.3
Hello,
Bob!
Router
Router
216.231.38.54
192.168.17.1
Hello,
Alice!
Computer B:
192.168.17.5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
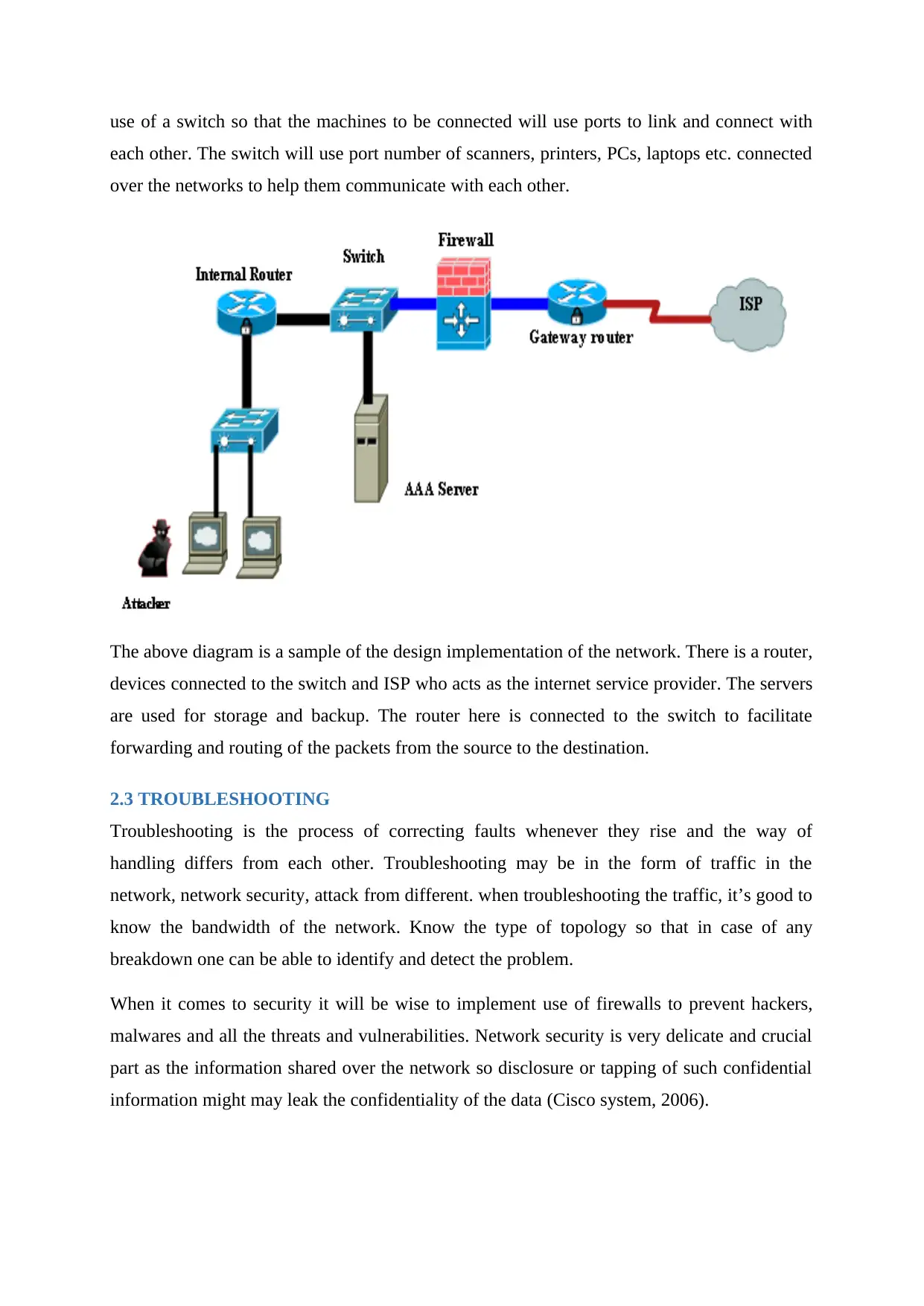
use of a switch so that the machines to be connected will use ports to link and connect with
each other. The switch will use port number of scanners, printers, PCs, laptops etc. connected
over the networks to help them communicate with each other.
The above diagram is a sample of the design implementation of the network. There is a router,
devices connected to the switch and ISP who acts as the internet service provider. The servers
are used for storage and backup. The router here is connected to the switch to facilitate
forwarding and routing of the packets from the source to the destination.
2.3 TROUBLESHOOTING
Troubleshooting is the process of correcting faults whenever they rise and the way of
handling differs from each other. Troubleshooting may be in the form of traffic in the
network, network security, attack from different. when troubleshooting the traffic, it’s good to
know the bandwidth of the network. Know the type of topology so that in case of any
breakdown one can be able to identify and detect the problem.
When it comes to security it will be wise to implement use of firewalls to prevent hackers,
malwares and all the threats and vulnerabilities. Network security is very delicate and crucial
part as the information shared over the network so disclosure or tapping of such confidential
information might may leak the confidentiality of the data (Cisco system, 2006).
each other. The switch will use port number of scanners, printers, PCs, laptops etc. connected
over the networks to help them communicate with each other.
The above diagram is a sample of the design implementation of the network. There is a router,
devices connected to the switch and ISP who acts as the internet service provider. The servers
are used for storage and backup. The router here is connected to the switch to facilitate
forwarding and routing of the packets from the source to the destination.
2.3 TROUBLESHOOTING
Troubleshooting is the process of correcting faults whenever they rise and the way of
handling differs from each other. Troubleshooting may be in the form of traffic in the
network, network security, attack from different. when troubleshooting the traffic, it’s good to
know the bandwidth of the network. Know the type of topology so that in case of any
breakdown one can be able to identify and detect the problem.
When it comes to security it will be wise to implement use of firewalls to prevent hackers,
malwares and all the threats and vulnerabilities. Network security is very delicate and crucial
part as the information shared over the network so disclosure or tapping of such confidential
information might may leak the confidentiality of the data (Cisco system, 2006).

2.4 SUMMARY
In achieving a good design that will deliver the campus values that aligns with the campus
goals and the directions. As a designer of networking an approach that is structured must be
put in to implementation. The structured approach as describes starts from the top going down
focusing on the needs of the business and hence an architecture of the network design will be
good as it will help in deploying the hardware and the technology requirements.
Network design plays a major role in network plan and setting. How one route and connects
with each other. How the IP address are unique for each and every machine? How the ports
switch among the different machines with connection with switch.
.
In achieving a good design that will deliver the campus values that aligns with the campus
goals and the directions. As a designer of networking an approach that is structured must be
put in to implementation. The structured approach as describes starts from the top going down
focusing on the needs of the business and hence an architecture of the network design will be
good as it will help in deploying the hardware and the technology requirements.
Network design plays a major role in network plan and setting. How one route and connects
with each other. How the IP address are unique for each and every machine? How the ports
switch among the different machines with connection with switch.
.

References
1] R.Waters. (2009). “Microsoft’s Ozzie Declares End to PC Era,” Financial Times,.
Alabady S., ". (2008). Design and Implementation of a Network Security Model using Static
VLAN and AAA Server. In Proceedings International Conference on Information &
Communication Technologies: from Theory to Applications.
Cisco system, I. (2006). Network Security 1 ",Cisco System. Network Security 1 ",.
CPLEX:, I. (2007). High-performance software for mathematical programming and
optimization. Retrieved from http://www.ilog.com/products/cplex/, 2007.
Q. Ali., a. A. (2007). "Design and Implementation of A Secured Remotely Administrated
Network,". In Proceedings International Arab Conference on Information
Technology, .
1] R.Waters. (2009). “Microsoft’s Ozzie Declares End to PC Era,” Financial Times,.
Alabady S., ". (2008). Design and Implementation of a Network Security Model using Static
VLAN and AAA Server. In Proceedings International Conference on Information &
Communication Technologies: from Theory to Applications.
Cisco system, I. (2006). Network Security 1 ",Cisco System. Network Security 1 ",.
CPLEX:, I. (2007). High-performance software for mathematical programming and
optimization. Retrieved from http://www.ilog.com/products/cplex/, 2007.
Q. Ali., a. A. (2007). "Design and Implementation of A Secured Remotely Administrated
Network,". In Proceedings International Arab Conference on Information
Technology, .
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





