ICT120 - Introduction to Computer Networks: Network Design Report
VerifiedAdded on 2022/08/22
|10
|2235
|13
Report
AI Summary
This report outlines the design of a network for a safety supplier company, which is a wholesaler supplying safety equipment across New Zealand and Australia. The company's head office is located in Melbourne, and the report focuses on designing a network plan that caters to the needs of the company, including the logistics and sales departments, as well as the office administration. The design covers the network topology, which describes the arrangement of network components and the flow of data, and network planning, which involves iterative procedures including topological design, network realization, and network synthesis. Essential network services such as structured cabling, application layers, TCP/IP services, UDP and TCP comparisons, firewalls, user accounts, and network safety are discussed in detail. The report emphasizes the importance of security measures, including firewalls and up-to-date operating systems and antivirus software to protect sensitive data and ensure smooth business operations. The design caters to 25 employees in the major business departments, and 5 office admin staff, with considerations for bandwidth, server allocation, and user access. The report recommends the implementation of a secure and efficient network infrastructure to support the company's operations.

Running head: ICT120
ICT120
Name of the Student
Name of the University
Author Note
ICT120
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICT120 1
Executive summary:
The main aim of this paper is to design a network for safety suppliers. The safety suppliers is
actually a wholesaler who supplies safety supplies to the organisations in New Zealand and
Australia. The head office of the company is in Melbourne that occupies in a 1 building in
one of the rows of the warehouses.
Executive summary:
The main aim of this paper is to design a network for safety suppliers. The safety suppliers is
actually a wholesaler who supplies safety supplies to the organisations in New Zealand and
Australia. The head office of the company is in Melbourne that occupies in a 1 building in
one of the rows of the warehouses.

2ICT120
Table of Contents
Introduction:...............................................................................................................................2
Network topology design:..........................................................................................................2
Network planning:......................................................................................................................2
References:.................................................................................................................................4
Table of Contents
Introduction:...............................................................................................................................2
Network topology design:..........................................................................................................2
Network planning:......................................................................................................................2
References:.................................................................................................................................4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ICT120
Introduction:
The purpose of this paper is to design a network for safety suppliers. The safety
suppliers is actually a wholesaler who supplies safety supplies to the organisations in New
Zealand and Australia. The head office of the company is in Melbourne that occupies in a 1
building in one of the rows of the warehouses (Gilchrist, 2019). There are four servers in the
head office, two of the servers run services for supporting different types of internal functions
of business that include file sharing, job tracking, Payroll, etc. The main task is to design a
network plan for the company. The report will also discuss why the recommended network
solution is the appropriate most as well as how the business will be benefitted from this.
Network topology design:
The network topology is basically the schematic description of the arrangement of
network which can connect various nodes by lines of connection. The topology can define the
structure of a network that how all of the components are connected with each other. The
physical topology is basically the placement of several components that are existed in a
network such as cable installation and device location. On the other side, the logical topology
can illustrate how the data can flow within a network (Mestres et al., 2017). The application
layer is one of the abstraction layer that is reserved for the methodologies that are designed
process to process communication between the IP computer networks and abstraction layers
that are reserved for the communication protocols. The distances between physical
interconnections, nodes however the topologies can be identical. The physical topology of a
network is a particular concern of the OSI model’s physical layer (Perlman, Kaufman and
Speciner, 2016). The company is having 2 major departments which are the logistics or
warehousing department and sales. The headquarter of the company is situated in Melbourne
that occupies 1 building in the row of the warehouses. There are about 25 employees from the
Introduction:
The purpose of this paper is to design a network for safety suppliers. The safety
suppliers is actually a wholesaler who supplies safety supplies to the organisations in New
Zealand and Australia. The head office of the company is in Melbourne that occupies in a 1
building in one of the rows of the warehouses (Gilchrist, 2019). There are four servers in the
head office, two of the servers run services for supporting different types of internal functions
of business that include file sharing, job tracking, Payroll, etc. The main task is to design a
network plan for the company. The report will also discuss why the recommended network
solution is the appropriate most as well as how the business will be benefitted from this.
Network topology design:
The network topology is basically the schematic description of the arrangement of
network which can connect various nodes by lines of connection. The topology can define the
structure of a network that how all of the components are connected with each other. The
physical topology is basically the placement of several components that are existed in a
network such as cable installation and device location. On the other side, the logical topology
can illustrate how the data can flow within a network (Mestres et al., 2017). The application
layer is one of the abstraction layer that is reserved for the methodologies that are designed
process to process communication between the IP computer networks and abstraction layers
that are reserved for the communication protocols. The distances between physical
interconnections, nodes however the topologies can be identical. The physical topology of a
network is a particular concern of the OSI model’s physical layer (Perlman, Kaufman and
Speciner, 2016). The company is having 2 major departments which are the logistics or
warehousing department and sales. The headquarter of the company is situated in Melbourne
that occupies 1 building in the row of the warehouses. There are about 25 employees from the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
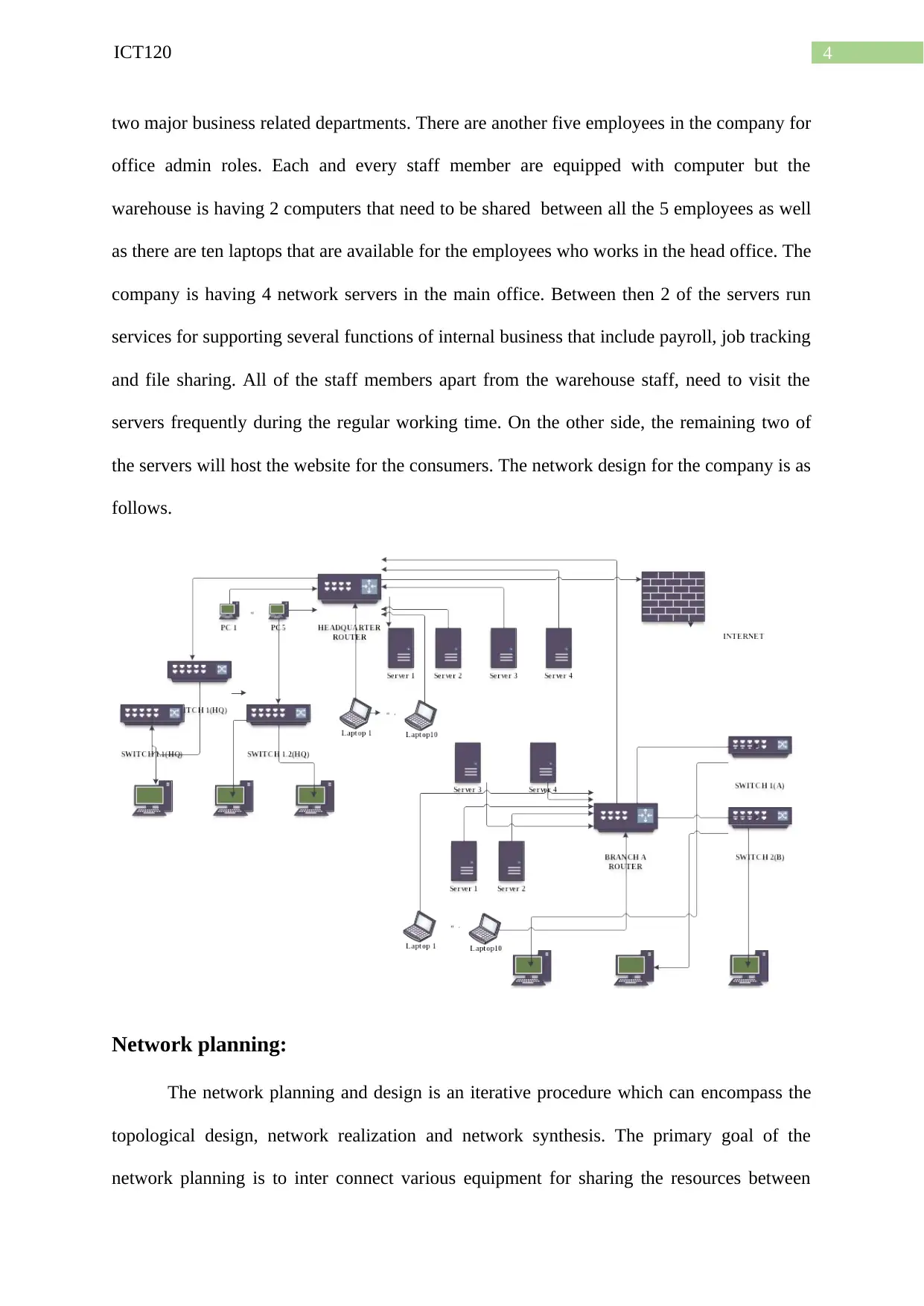
4ICT120
two major business related departments. There are another five employees in the company for
office admin roles. Each and every staff member are equipped with computer but the
warehouse is having 2 computers that need to be shared between all the 5 employees as well
as there are ten laptops that are available for the employees who works in the head office. The
company is having 4 network servers in the main office. Between then 2 of the servers run
services for supporting several functions of internal business that include payroll, job tracking
and file sharing. All of the staff members apart from the warehouse staff, need to visit the
servers frequently during the regular working time. On the other side, the remaining two of
the servers will host the website for the consumers. The network design for the company is as
follows.
Network planning:
The network planning and design is an iterative procedure which can encompass the
topological design, network realization and network synthesis. The primary goal of the
network planning is to inter connect various equipment for sharing the resources between
two major business related departments. There are another five employees in the company for
office admin roles. Each and every staff member are equipped with computer but the
warehouse is having 2 computers that need to be shared between all the 5 employees as well
as there are ten laptops that are available for the employees who works in the head office. The
company is having 4 network servers in the main office. Between then 2 of the servers run
services for supporting several functions of internal business that include payroll, job tracking
and file sharing. All of the staff members apart from the warehouse staff, need to visit the
servers frequently during the regular working time. On the other side, the remaining two of
the servers will host the website for the consumers. The network design for the company is as
follows.
Network planning:
The network planning and design is an iterative procedure which can encompass the
topological design, network realization and network synthesis. The primary goal of the
network planning is to inter connect various equipment for sharing the resources between

5ICT120
several users. Capacity planning and traffic forecasting is included in the network planning
for balancing the investment in a network, network performance and end user experience.
The services related to network planning can help the operator too for developing the network
strategies as well as action plans which may achieve the goals of the business and provide
input for the subsequent design as well as integration of the network (Fisch, White and
Pooch, 2017). The company is having 2 major departments which are the logistics or
warehousing department and sales. The headquarter of the company is situated in Melbourne
that occupies 1 building in the row of the warehouses. There are about 25 employees from the
two major business related departments. There are another five employees in the company for
office admin roles. The requirement for the bandwidth that is increased for the high
performance network that are available for present situation, need transmission media
hardware that are having the capability to transmit, the optical and electrical signals from the
point to point accurately as well as consistently. For better security firewall is also needed to
be installed to the network as it can monitor the outgoing and incoming traffics of network as
well as give permission or having the ability to block the data packets on the basis of a set of
rules related to the security. The main purpose of the firewall is to make establishment of a
barrier that is between the incoming traffic and internal network that comes from the external
sources for blocking the traffic that are malicious such as hackers attack or viruses
(Acemoglu, Malekian and Ozdaglar, 2016). The application layer is one of the abstraction
layer that is reserved for the methodologies that are designed process to process
communication between the IP computer networks and abstraction layers that are reserved for
the communication protocols. As seen in the network design, each and every staff member
are equipped with computer but the warehouse is having 2 computers that need to be shared
between all the 5 employees as well as there are ten laptops that are available for the
employees who works in the head office. For running the internet services smoothly, there are
several users. Capacity planning and traffic forecasting is included in the network planning
for balancing the investment in a network, network performance and end user experience.
The services related to network planning can help the operator too for developing the network
strategies as well as action plans which may achieve the goals of the business and provide
input for the subsequent design as well as integration of the network (Fisch, White and
Pooch, 2017). The company is having 2 major departments which are the logistics or
warehousing department and sales. The headquarter of the company is situated in Melbourne
that occupies 1 building in the row of the warehouses. There are about 25 employees from the
two major business related departments. There are another five employees in the company for
office admin roles. The requirement for the bandwidth that is increased for the high
performance network that are available for present situation, need transmission media
hardware that are having the capability to transmit, the optical and electrical signals from the
point to point accurately as well as consistently. For better security firewall is also needed to
be installed to the network as it can monitor the outgoing and incoming traffics of network as
well as give permission or having the ability to block the data packets on the basis of a set of
rules related to the security. The main purpose of the firewall is to make establishment of a
barrier that is between the incoming traffic and internal network that comes from the external
sources for blocking the traffic that are malicious such as hackers attack or viruses
(Acemoglu, Malekian and Ozdaglar, 2016). The application layer is one of the abstraction
layer that is reserved for the methodologies that are designed process to process
communication between the IP computer networks and abstraction layers that are reserved for
the communication protocols. As seen in the network design, each and every staff member
are equipped with computer but the warehouse is having 2 computers that need to be shared
between all the 5 employees as well as there are ten laptops that are available for the
employees who works in the head office. For running the internet services smoothly, there are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ICT120
having 4 network servers in the main office of the company. The company needs two servers
for running services for supporting several functions of internal business that include payroll,
job tracking and file sharing, for that 2 servers are allocated. The file transfer needs full
accuracy with zero fault as well as it can be done by utilizing the TCP (Kang, and Kang,
2016). On the other side, the audio conferencing can be done by utilizing the UDP.All of the
staff members apart from the warehouse staff, need to visit the servers frequently during the
regular working time as they need to check the servers are running frequently. On the other
side, the remaining two of the servers will host the website for the consumers. According to
the network design, there will be switches for each of the branches.
Essential network services:
The essential network services for the company are as follows:
Structured cabling:
The need for the bandwidth that is increased for the high performance network that
are available for present situation, need transmission media hardware that are having the
capability to transmit, the optical and electrical signals from the point to point accurately as
well as consistently (Zou et al., 2016). The professional installation of the structured cabling
of high standards is very much important for getting success. Tech technologies like RS232,
RS422, RS485, thicknet, thinnet, twinax are having standardization of the cabling framework
that is structured.
Application layer:
In the network programming of the computer, the application layer is one of the
abstraction layer that is reserved for the methodologies that are designed process to process
communication between the IP computer networks and abstraction layers that are reserved for
the communication protocols. The protocols of the application layers utilize the transportation
having 4 network servers in the main office of the company. The company needs two servers
for running services for supporting several functions of internal business that include payroll,
job tracking and file sharing, for that 2 servers are allocated. The file transfer needs full
accuracy with zero fault as well as it can be done by utilizing the TCP (Kang, and Kang,
2016). On the other side, the audio conferencing can be done by utilizing the UDP.All of the
staff members apart from the warehouse staff, need to visit the servers frequently during the
regular working time as they need to check the servers are running frequently. On the other
side, the remaining two of the servers will host the website for the consumers. According to
the network design, there will be switches for each of the branches.
Essential network services:
The essential network services for the company are as follows:
Structured cabling:
The need for the bandwidth that is increased for the high performance network that
are available for present situation, need transmission media hardware that are having the
capability to transmit, the optical and electrical signals from the point to point accurately as
well as consistently (Zou et al., 2016). The professional installation of the structured cabling
of high standards is very much important for getting success. Tech technologies like RS232,
RS422, RS485, thicknet, thinnet, twinax are having standardization of the cabling framework
that is structured.
Application layer:
In the network programming of the computer, the application layer is one of the
abstraction layer that is reserved for the methodologies that are designed process to process
communication between the IP computer networks and abstraction layers that are reserved for
the communication protocols. The protocols of the application layers utilize the transportation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ICT120
layer that is underlying the protocols of transport layers for establishing the host to host
connections for the services of network.
TCP-IP network services:
Most of the services that are internet protocol based are having association with one
of the particular port number that is well known that is standardized by the technical
governance of Internet. As example, it can be said that the world wide web servers can
operate on port-80.
TCP versus UDP:
Various services utilize different types of pack transmission techniques. The packets
which have to get through in an order that is correct. As example, it can be said that the file
transfer needs full accuracy with zero fault as well as it can be done by utilizing the TCP. On
the other side, the audio conferencing can be done by utilizing the UDP. The UDP is lacked
in the built in network congestion avoidance as well as the protocols which utilize the UDP,
need to be designed extremely carefully for preventing the collapse of the network.
Firewall:
The firewall is one of the much needed for the company as the company needs two
servers for running services for supporting several functions of internal business that include
payroll, job tracking and file sharing, for that 2 servers are allocated. The firewall is basically
a network security related device which can monitor the outgoing and incoming traffics of
network as well as give permission or having the ability to block the data packets on the basis
of a set of rules related to the security. The main purpose of the firewall is to make
establishment of a barrier that is between the incoming traffic and internal network that
comes from the external sources for blocking the traffic that are malicious such as hackers
attack or viruses.
layer that is underlying the protocols of transport layers for establishing the host to host
connections for the services of network.
TCP-IP network services:
Most of the services that are internet protocol based are having association with one
of the particular port number that is well known that is standardized by the technical
governance of Internet. As example, it can be said that the world wide web servers can
operate on port-80.
TCP versus UDP:
Various services utilize different types of pack transmission techniques. The packets
which have to get through in an order that is correct. As example, it can be said that the file
transfer needs full accuracy with zero fault as well as it can be done by utilizing the TCP. On
the other side, the audio conferencing can be done by utilizing the UDP. The UDP is lacked
in the built in network congestion avoidance as well as the protocols which utilize the UDP,
need to be designed extremely carefully for preventing the collapse of the network.
Firewall:
The firewall is one of the much needed for the company as the company needs two
servers for running services for supporting several functions of internal business that include
payroll, job tracking and file sharing, for that 2 servers are allocated. The firewall is basically
a network security related device which can monitor the outgoing and incoming traffics of
network as well as give permission or having the ability to block the data packets on the basis
of a set of rules related to the security. The main purpose of the firewall is to make
establishment of a barrier that is between the incoming traffic and internal network that
comes from the external sources for blocking the traffic that are malicious such as hackers
attack or viruses.

8ICT120
User accounts:
As seen in the network design, each and every staff member are equipped with
computer but the warehouse is having 2 computers that need to be shared between all the 5
employees as well as there are ten laptops that are available for the employees who works in
the head office. So the user accounts are very much important for the company (Rathore et
al., 2017). As there should be different user accounts for all of the employees such that they
can manage their responsibilities. All the users need to be alert as they should keep safe their
passcodes and user login credential that no one can misuse the accounts.
Network safety:
The network safety is the most important thing for any company as there are
confidential data that are stored in the systems. There will be also payment related services
that will be done by using the network. For better security, firewall needs to be installed with
the latest update. The operating system should be up to date with an antivirus.
Conclusion:
Thus, it can be concluded from the report that in the paper a network design has been
made for safety suppliers which is a wholesaler who supplies safety supplies to the
organisations in New Zealand and Australia. Recommendation has been given for better
security as the network security is the important most thing for the company.
User accounts:
As seen in the network design, each and every staff member are equipped with
computer but the warehouse is having 2 computers that need to be shared between all the 5
employees as well as there are ten laptops that are available for the employees who works in
the head office. So the user accounts are very much important for the company (Rathore et
al., 2017). As there should be different user accounts for all of the employees such that they
can manage their responsibilities. All the users need to be alert as they should keep safe their
passcodes and user login credential that no one can misuse the accounts.
Network safety:
The network safety is the most important thing for any company as there are
confidential data that are stored in the systems. There will be also payment related services
that will be done by using the network. For better security, firewall needs to be installed with
the latest update. The operating system should be up to date with an antivirus.
Conclusion:
Thus, it can be concluded from the report that in the paper a network design has been
made for safety suppliers which is a wholesaler who supplies safety supplies to the
organisations in New Zealand and Australia. Recommendation has been given for better
security as the network security is the important most thing for the company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ICT120
References:
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and
contagion. Journal of Economic Theory, 166, pp.536-585.
Fisch, E.A., White, G.B. and Pooch, U.W., 2017. Computer system and network security.
CRC press.
Gilchrist, A., 2019. The Well-Connected Community 3E: A Networking Approach to
Community Development. Policy Press.
Kang, M.J. and Kang, J.W., 2016. Intrusion detection system using deep neural network for
in-vehicle network security. PloS one, 11(6).
Mestres, A., Rodriguez-Natal, A., Carner, J., Barlet-Ros, P., Alarcón, E., Solé, M., Muntés-
Mulero, V., Meyer, D., Barkai, S., Hibbett, M.J. and Estrada, G., 2017. Knowledge-defined
networking. ACM SIGCOMM Computer Communication Review, 47(3), pp.2-10.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication
in a public world. Pearson Education India.
Rathore, S., Sharma, P.K., Loia, V., Jeong, Y.S. and Park, J.H., 2017. Social network
security: Issues, challenges, threats, and solutions. Information sciences, 421, pp.43-69.
Zou, Y., Zhu, J., Wang, X. and Hanzo, L., 2016. A survey on wireless security: Technical
challenges, recent advances, and future trends. Proceedings of the IEEE, 104(9), pp.1727-
1765.
References:
Acemoglu, D., Malekian, A. and Ozdaglar, A., 2016. Network security and
contagion. Journal of Economic Theory, 166, pp.536-585.
Fisch, E.A., White, G.B. and Pooch, U.W., 2017. Computer system and network security.
CRC press.
Gilchrist, A., 2019. The Well-Connected Community 3E: A Networking Approach to
Community Development. Policy Press.
Kang, M.J. and Kang, J.W., 2016. Intrusion detection system using deep neural network for
in-vehicle network security. PloS one, 11(6).
Mestres, A., Rodriguez-Natal, A., Carner, J., Barlet-Ros, P., Alarcón, E., Solé, M., Muntés-
Mulero, V., Meyer, D., Barkai, S., Hibbett, M.J. and Estrada, G., 2017. Knowledge-defined
networking. ACM SIGCOMM Computer Communication Review, 47(3), pp.2-10.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication
in a public world. Pearson Education India.
Rathore, S., Sharma, P.K., Loia, V., Jeong, Y.S. and Park, J.H., 2017. Social network
security: Issues, challenges, threats, and solutions. Information sciences, 421, pp.43-69.
Zou, Y., Zhu, J., Wang, X. and Hanzo, L., 2016. A survey on wireless security: Technical
challenges, recent advances, and future trends. Proceedings of the IEEE, 104(9), pp.1727-
1765.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





