Comprehensive Network Design and Setup Report for UMUC University
VerifiedAdded on 2022/11/26
|16
|3097
|289
Project
AI Summary
This report details a network design and setup for a university environment, encompassing various aspects of network infrastructure. It begins by outlining the requirements, including the need for a robust wired and wireless network to serve classrooms, offices, and campuses. The report proposes a ring topology for the wired network, utilizing Cat 6 cables, and details the use of switches, routers, and wireless routers to facilitate connectivity. Subnet calculations are provided, along with the implementation of a firewall and a DMZ (Demilitarized Zone) to enhance security. The report covers WAN design, computer systems hardware, and network addressing, including the assignment of IP addresses. The report also addresses the technical requirements for cabling, networking devices, and computer systems, providing justification for the proposed solutions and concludes with observations.

Running head: NETWORK DESIGN AND SETUP
Network Design and Setup
Name of the Student
Name of the University
Author Note
Network Design and Setup
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK DESIGN AND SETUP
Summary
Network design is an important part of setting up a network as it defines how efficient and
secure the implemented network turns out to be. First the report presents the requirements
summary and then provides the network design before discussing it and identifying the cost
of components involved. Then the report lays down the subnet calculation of the wired
network and later provides details of the wireless network. After that the report talks about
the installation of firewalls and setup of the perimeter network or DMZ and then ends with
observations in concluding notes.
Summary
Network design is an important part of setting up a network as it defines how efficient and
secure the implemented network turns out to be. First the report presents the requirements
summary and then provides the network design before discussing it and identifying the cost
of components involved. Then the report lays down the subnet calculation of the wired
network and later provides details of the wireless network. After that the report talks about
the installation of firewalls and setup of the perimeter network or DMZ and then ends with
observations in concluding notes.

2NETWORK DESIGN AND SETUP
Table of Contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Summary of Requirements.....................................................................................................3
Network Design.....................................................................................................................4
Subnet calculation..................................................................................................................6
Firewall and DMZ..................................................................................................................8
Conclusion..................................................................................................................................8
References................................................................................................................................10
Table of Contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Summary of Requirements.....................................................................................................3
Network Design.....................................................................................................................4
Subnet calculation..................................................................................................................6
Firewall and DMZ..................................................................................................................8
Conclusion..................................................................................................................................8
References................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK DESIGN AND SETUP
Introduction
The report highlights the importance of network design in setting up of networks as
they help define how efficient and secure the implemented network can end up being. The
report begins by presenting the requirements summary and then provides the network design
before discussing it and identifying the cost of components involved [7]. Then the report lays
down the subnet calculation of the wired network and later provides details of the wireless
network. After that the report talks about the installation of firewalls and setup of the
perimeter network or DMZ and then ends with observations in concluding notes.
I. Network Design
A. Network Topology
Technical Requirements
The various classrooms, offices, libraries and labs of the university must be served by the
proposed network.
The physical networking topologies used need to be explained with detail.
This network needs to serve university members over a wide area in both the building as well
as the campuses.
The addressing method for the network needs to be detailed.
The internal network of the university needs to be secured using a DMZ or perimeter network
Proposed Topology
Secure Network Contractors is of the opinion that by comparing the various types of
topologies available it is noted that a ring topology is best suited for connecting the individual
devices as per the requirements defined by University of Maryland University College
Introduction
The report highlights the importance of network design in setting up of networks as
they help define how efficient and secure the implemented network can end up being. The
report begins by presenting the requirements summary and then provides the network design
before discussing it and identifying the cost of components involved [7]. Then the report lays
down the subnet calculation of the wired network and later provides details of the wireless
network. After that the report talks about the installation of firewalls and setup of the
perimeter network or DMZ and then ends with observations in concluding notes.
I. Network Design
A. Network Topology
Technical Requirements
The various classrooms, offices, libraries and labs of the university must be served by the
proposed network.
The physical networking topologies used need to be explained with detail.
This network needs to serve university members over a wide area in both the building as well
as the campuses.
The addressing method for the network needs to be detailed.
The internal network of the university needs to be secured using a DMZ or perimeter network
Proposed Topology
Secure Network Contractors is of the opinion that by comparing the various types of
topologies available it is noted that a ring topology is best suited for connecting the individual
devices as per the requirements defined by University of Maryland University College
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
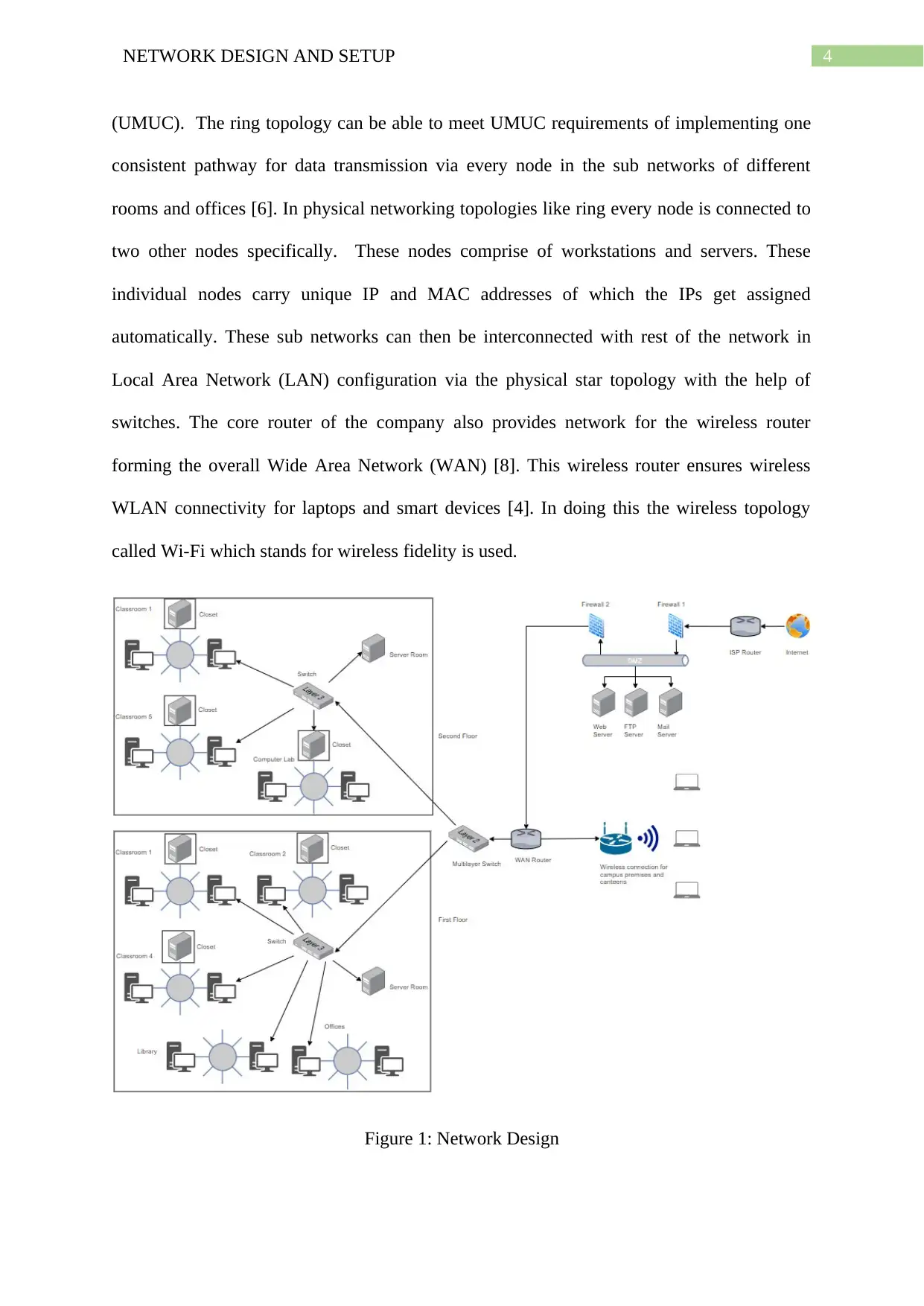
4NETWORK DESIGN AND SETUP
(UMUC). The ring topology can be able to meet UMUC requirements of implementing one
consistent pathway for data transmission via every node in the sub networks of different
rooms and offices [6]. In physical networking topologies like ring every node is connected to
two other nodes specifically. These nodes comprise of workstations and servers. These
individual nodes carry unique IP and MAC addresses of which the IPs get assigned
automatically. These sub networks can then be interconnected with rest of the network in
Local Area Network (LAN) configuration via the physical star topology with the help of
switches. The core router of the company also provides network for the wireless router
forming the overall Wide Area Network (WAN) [8]. This wireless router ensures wireless
WLAN connectivity for laptops and smart devices [4]. In doing this the wireless topology
called Wi-Fi which stands for wireless fidelity is used.
Figure 1: Network Design
(UMUC). The ring topology can be able to meet UMUC requirements of implementing one
consistent pathway for data transmission via every node in the sub networks of different
rooms and offices [6]. In physical networking topologies like ring every node is connected to
two other nodes specifically. These nodes comprise of workstations and servers. These
individual nodes carry unique IP and MAC addresses of which the IPs get assigned
automatically. These sub networks can then be interconnected with rest of the network in
Local Area Network (LAN) configuration via the physical star topology with the help of
switches. The core router of the company also provides network for the wireless router
forming the overall Wide Area Network (WAN) [8]. This wireless router ensures wireless
WLAN connectivity for laptops and smart devices [4]. In doing this the wireless topology
called Wi-Fi which stands for wireless fidelity is used.
Figure 1: Network Design

5NETWORK DESIGN AND SETUP
Justification
The university requires to provide connectivity for students and staff in offices. Hence
to ensure a very cost efficient network implementation the ring topology is used to connect
the systems of individual rooms to ensure separate interfaces and additional switches are not
needed to be acquired. Routers are only used where different sub networks are required to be
created. Switches are only used to interconnect the sub networks of different rooms and
offices with the rest of the network. The wireless network enables network access for laptops
and smart devices. The DMZ network help isolate the internal network of the university from
the public to prevent intrusion by hackers.
B. Cables and Connectors
Technical Requirements
Separate cables needs to be acquired for different DMZ interfaces in the perimeter network.
After that a single long Ethernet cable is needed for connecting the core router of UMUC
from the firewall.
There is need of another Ethernet cable for connecting the distribution layer switch.
From the distribution layer switch multiple Ethernet cables are required for connecting the
two access layer switches in first and second floors [2]. From these a workstation or server of
a respective room is again connected with these cables. The cables are also used for
interconnecting the different devices interconnected in ring topology.
Proposed Cables and Connectors
Justification
The university requires to provide connectivity for students and staff in offices. Hence
to ensure a very cost efficient network implementation the ring topology is used to connect
the systems of individual rooms to ensure separate interfaces and additional switches are not
needed to be acquired. Routers are only used where different sub networks are required to be
created. Switches are only used to interconnect the sub networks of different rooms and
offices with the rest of the network. The wireless network enables network access for laptops
and smart devices. The DMZ network help isolate the internal network of the university from
the public to prevent intrusion by hackers.
B. Cables and Connectors
Technical Requirements
Separate cables needs to be acquired for different DMZ interfaces in the perimeter network.
After that a single long Ethernet cable is needed for connecting the core router of UMUC
from the firewall.
There is need of another Ethernet cable for connecting the distribution layer switch.
From the distribution layer switch multiple Ethernet cables are required for connecting the
two access layer switches in first and second floors [2]. From these a workstation or server of
a respective room is again connected with these cables. The cables are also used for
interconnecting the different devices interconnected in ring topology.
Proposed Cables and Connectors
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK DESIGN AND SETUP
The required cables for the proposed network are Cat 6 version of Ethernet cables.
This type of cables are to be used in the various parts of the network among the different sub
networks as well as connecting them with rest of the network. Since there exists a perimeter
network along with the need to connect devices in two separate floors as well as in
connecting individual devices, it is estimated that 100ft of cabling will be needed.
Justification
Cat 6 Ethernet cables are chosen because they support reasonably fast networks across
a decent range of effectiveness. These cables support 10-BASE-T, 100BASE-TX (Fast
Ethernet), 1000BASE-T/1000BASE-TX (Gigabit Ethernet) as also 10BASE-T (10-Gigabit
Ethernet) thereby offering the university plenty of options with the network setup and
bandwidth requirements.
C. Networking and Internetworking Hardware
Technical Requirements
Computers and servers in the rooms and offices should be interconnected with two of the
neighbouring nodes. One such device needs to be connected to the internal network of the
university to obtain connectivity.
The internal network of the university needs to be distributed to the two different floors
The wireless network needs to be connected to the network as well to negate the necessity to
invest in a separate line from the perimeter network lessen the need for extra routers.
Proposed Networking and Internetworking Devices
The individual devices connected with neighbouring nodes in ring topology are
connected via the eight wired RJ45 connectors of the Ethernet cables. Switches of the access
layer are used for connecting these devices to the network for providing network access. The
The required cables for the proposed network are Cat 6 version of Ethernet cables.
This type of cables are to be used in the various parts of the network among the different sub
networks as well as connecting them with rest of the network. Since there exists a perimeter
network along with the need to connect devices in two separate floors as well as in
connecting individual devices, it is estimated that 100ft of cabling will be needed.
Justification
Cat 6 Ethernet cables are chosen because they support reasonably fast networks across
a decent range of effectiveness. These cables support 10-BASE-T, 100BASE-TX (Fast
Ethernet), 1000BASE-T/1000BASE-TX (Gigabit Ethernet) as also 10BASE-T (10-Gigabit
Ethernet) thereby offering the university plenty of options with the network setup and
bandwidth requirements.
C. Networking and Internetworking Hardware
Technical Requirements
Computers and servers in the rooms and offices should be interconnected with two of the
neighbouring nodes. One such device needs to be connected to the internal network of the
university to obtain connectivity.
The internal network of the university needs to be distributed to the two different floors
The wireless network needs to be connected to the network as well to negate the necessity to
invest in a separate line from the perimeter network lessen the need for extra routers.
Proposed Networking and Internetworking Devices
The individual devices connected with neighbouring nodes in ring topology are
connected via the eight wired RJ45 connectors of the Ethernet cables. Switches of the access
layer are used for connecting these devices to the network for providing network access. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK DESIGN AND SETUP
distribution layer switches provide network access to these two switches. The core level
router obtains network from the firewall and routes it to the distributed switch and the
wireless router. The laptops and mobile devices use the Wi-Fi interface for network access.
Justification
The three layer hierarchical network model introduced by distribution and access
layer switches bring efficiency to network and alleviates the requirement of extra switching
and routing hardware for interconnections within the network. For the use case of the
university network, it is understood that Wi-Fi is the most suited wireless interface for
connecting the mobile devices as they are not located too far apart from where the wireless
router is installed.
D. Wide Area Network (WAN) Design
Technical Requirements
UMUC needs to provide network connectivity for laptops and smart devices in canteens and
campuses outside the university building.
Thus a wireless network needs to be setup to effectively serve mobile devices with decent
network bandwidth and response rates.
Proposed Wide Area Network (WAN) Design
UMUC has installed wireless router in the canteen located in the campus of the
university. The wireless router can transmit effective network signals up to a 150ft radius.
This helps the wireless network cover Wi-Fi services for all parts of the university campus.
Justification
distribution layer switches provide network access to these two switches. The core level
router obtains network from the firewall and routes it to the distributed switch and the
wireless router. The laptops and mobile devices use the Wi-Fi interface for network access.
Justification
The three layer hierarchical network model introduced by distribution and access
layer switches bring efficiency to network and alleviates the requirement of extra switching
and routing hardware for interconnections within the network. For the use case of the
university network, it is understood that Wi-Fi is the most suited wireless interface for
connecting the mobile devices as they are not located too far apart from where the wireless
router is installed.
D. Wide Area Network (WAN) Design
Technical Requirements
UMUC needs to provide network connectivity for laptops and smart devices in canteens and
campuses outside the university building.
Thus a wireless network needs to be setup to effectively serve mobile devices with decent
network bandwidth and response rates.
Proposed Wide Area Network (WAN) Design
UMUC has installed wireless router in the canteen located in the campus of the
university. The wireless router can transmit effective network signals up to a 150ft radius.
This helps the wireless network cover Wi-Fi services for all parts of the university campus.
Justification

8NETWORK DESIGN AND SETUP
Thee wireless router is chosen it is more cost efficient option compared to other
wireless options like setting up antennas and dishes and setting up point to point networks.
The wireless routers are also better manageable and easy to troubleshoot for the network
administrators.
E. Computer Systems Hardware
Technical Requirements
Servers and workstations needs to be operated by the university in the various rooms and
offices.
They also require to operate all the different network equipment and ensure that sustained
uptime of the network can be provided to university members.
Proposed Computer Systems Hardware
The hardware systems used by the university are PowerEdge 2900 III servers from
Dell as well as OptiPlex 3060 for the workstations. These servers are used by the instructors
in the classrooms as also in other departments and offices of the university by other staff.
Justification
These workstations can effectively serve the resource needs for the research and
analytical tasks performed by the students as well as help the university staff with other
activities. The PowerEdge servers provide additional resources for helping the instructors
with managing and teaching the learning modules.
II. Network Addressing and Security
A. Subnetting
Overview
Thee wireless router is chosen it is more cost efficient option compared to other
wireless options like setting up antennas and dishes and setting up point to point networks.
The wireless routers are also better manageable and easy to troubleshoot for the network
administrators.
E. Computer Systems Hardware
Technical Requirements
Servers and workstations needs to be operated by the university in the various rooms and
offices.
They also require to operate all the different network equipment and ensure that sustained
uptime of the network can be provided to university members.
Proposed Computer Systems Hardware
The hardware systems used by the university are PowerEdge 2900 III servers from
Dell as well as OptiPlex 3060 for the workstations. These servers are used by the instructors
in the classrooms as also in other departments and offices of the university by other staff.
Justification
These workstations can effectively serve the resource needs for the research and
analytical tasks performed by the students as well as help the university staff with other
activities. The PowerEdge servers provide additional resources for helping the instructors
with managing and teaching the learning modules.
II. Network Addressing and Security
A. Subnetting
Overview
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK DESIGN AND SETUP
Major network used in creating the 8 subnets for the network is 192.168.3.0. Here
each of the subnets are to serve 25 devices except the Library subnet which only servers 15
devices. The IP network is a class C IP and the CIDR (Classless Interdomain Routing) used
here is /24 [5]. All the address space offered by this CIDR value get allocated to the
respective subnets.
Additionally there needs to be a wireless network established with a different
network. This network is chosen to be 192.168.4.0. The wireless network is supposed to
server all the laptops and mobile devices of students, faculty and other stuff and hence
requires more than 126 IP addresses. There an entire octet of 254 IP addresses is being
allocated. Therefore the network details are:
Network Address: 192.168.4.0
IP Address range: 192.168.4.1 – 192.168.4.254
Broadcast Address: 192.168.4.255
Class Octet Decimal Range
A 1 - 126
B 128 - 191
C 192 - 223
Network addresses 192.168.3.0 and 192.168.4.0 are assigned to the wired and wireless
networks respectively. Based on the above table, these are Class C IP addresses.
Class Subnet Mask Format
Major network used in creating the 8 subnets for the network is 192.168.3.0. Here
each of the subnets are to serve 25 devices except the Library subnet which only servers 15
devices. The IP network is a class C IP and the CIDR (Classless Interdomain Routing) used
here is /24 [5]. All the address space offered by this CIDR value get allocated to the
respective subnets.
Additionally there needs to be a wireless network established with a different
network. This network is chosen to be 192.168.4.0. The wireless network is supposed to
server all the laptops and mobile devices of students, faculty and other stuff and hence
requires more than 126 IP addresses. There an entire octet of 254 IP addresses is being
allocated. Therefore the network details are:
Network Address: 192.168.4.0
IP Address range: 192.168.4.1 – 192.168.4.254
Broadcast Address: 192.168.4.255
Class Octet Decimal Range
A 1 - 126
B 128 - 191
C 192 - 223
Network addresses 192.168.3.0 and 192.168.4.0 are assigned to the wired and wireless
networks respectively. Based on the above table, these are Class C IP addresses.
Class Subnet Mask Format
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK DESIGN AND SETUP
A 255.0.0.0 Network.Host.Host.Host
B 255.255.0.0 Network.Network.Host.Host
C 255.255.255.0 Network.Network.Network.Host
These classes have subnet masks by defined for them by default. This forms the part of the
network and how much is still available for allocation.
CIDR (Classless Inter Domain Routing)
Method used in creating the different subnets is CIDR or Classless Inter Domain Routing
which offers meaningful advantages as opposed to the classful IP addressing scheme.
This addressing scheme helps with incremental variance in available address space
with the change of every CIDR value.
These are denoted by the slash notation for example /27.
The subnet mask for the networks used are 255.255.255.0 and the corresponding
CIDR value is 24.
Technical Requirements
The network involves offices including the admission office. The admission office has
5 computers, other offices contain 1 computer each.
There are five computers, three from the floor 1 and two from the floor 2. Each of
these classrooms comprise of 23 computers to serve the students, 1 to serve the
instructor along with a server.
A 255.0.0.0 Network.Host.Host.Host
B 255.255.0.0 Network.Network.Host.Host
C 255.255.255.0 Network.Network.Network.Host
These classes have subnet masks by defined for them by default. This forms the part of the
network and how much is still available for allocation.
CIDR (Classless Inter Domain Routing)
Method used in creating the different subnets is CIDR or Classless Inter Domain Routing
which offers meaningful advantages as opposed to the classful IP addressing scheme.
This addressing scheme helps with incremental variance in available address space
with the change of every CIDR value.
These are denoted by the slash notation for example /27.
The subnet mask for the networks used are 255.255.255.0 and the corresponding
CIDR value is 24.
Technical Requirements
The network involves offices including the admission office. The admission office has
5 computers, other offices contain 1 computer each.
There are five computers, three from the floor 1 and two from the floor 2. Each of
these classrooms comprise of 23 computers to serve the students, 1 to serve the
instructor along with a server.
11NETWORK DESIGN AND SETUP
UMUC computer lab contains 24 computers to help students do their work and 1
server.
The library offers 10 computers for university students and 5 for use by the university
staff.
Subnet Description Required Hosts
Classroom 1 (First Floor) 25 Computers
Classroom 2 (First Floor) 25 Computers
Classroom 4 (First Floor) 25 Computers
Classroom 1 (Second Floor) 25 Computers
Classroom 5 (Second Floor) 25 Computers
Office 5 – Admissions (Second Floor) 25 Computers
Student Computer Lab 25 Computers
Library 15 Computers
Subnet Network Address Host Address Range Broadcast
Address
Subnet Mask: 255.255.255. 0___
Classroom 1
(First Floor)
192.168.3.0 192.168.3.1 - 192.168.3.30 192.168.3.31
Classroom 2
(First Floor)
192.168.3. 32_ 192.168.3. 33_ - 192.168.3.62 _ 192.168.3.63 _
Classroom 4
(First Floor)
192.168.3. 64_ 192.168.3. 65_ - 192.168.3. 94_ 192.168.3. 95_
Classroom 1 192.168.3.96 192.168.3.97 - 192.168.3.126 192.168.3.127
UMUC computer lab contains 24 computers to help students do their work and 1
server.
The library offers 10 computers for university students and 5 for use by the university
staff.
Subnet Description Required Hosts
Classroom 1 (First Floor) 25 Computers
Classroom 2 (First Floor) 25 Computers
Classroom 4 (First Floor) 25 Computers
Classroom 1 (Second Floor) 25 Computers
Classroom 5 (Second Floor) 25 Computers
Office 5 – Admissions (Second Floor) 25 Computers
Student Computer Lab 25 Computers
Library 15 Computers
Subnet Network Address Host Address Range Broadcast
Address
Subnet Mask: 255.255.255. 0___
Classroom 1
(First Floor)
192.168.3.0 192.168.3.1 - 192.168.3.30 192.168.3.31
Classroom 2
(First Floor)
192.168.3. 32_ 192.168.3. 33_ - 192.168.3.62 _ 192.168.3.63 _
Classroom 4
(First Floor)
192.168.3. 64_ 192.168.3. 65_ - 192.168.3. 94_ 192.168.3. 95_
Classroom 1 192.168.3.96 192.168.3.97 - 192.168.3.126 192.168.3.127
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





