Network Design and Troubleshoot Report for Speedfix.co.uk - QAC020N253
VerifiedAdded on 2022/08/14
|24
|3869
|12
Report
AI Summary
This report details the design and implementation of a network for Speedfix.co.uk, addressing the company's needs for separate departments (Finance/HR, Sales, Engineers, Admins, and Wireless) and servers. The report covers the evaluation of network models, technologies, and protocols, including the use of VLANs for network segmentation and security. It includes the use of Cisco Packet Tracer for network simulation, the selection of a three-layer hierarchical network model, and the creation of an IP addressing scheme with subnetting. The report further describes the configuration of a Layer 3 switch as a VTP server and Layer 2 switches as clients, along with the configuration of a router with DHCP and ACLs. The design also incorporates IoT devices for monitoring and security. The report concludes with testing and documentation, providing a comprehensive overview of the network design and troubleshooting process.

Running head: NETWORK DESIGNING AND TROUBLESHOOT
Network Designing and Troubleshoot
Name of the Student
Name of the University
Author’s Note
Network Designing and Troubleshoot
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK DESIGNING AND TROUBLESHOOT
Table of Contents
Introduction......................................................................................................................................2
Knowledge and understanding........................................................................................................3
Application and Analysis.................................................................................................................4
Evaluation and Judgement...............................................................................................................4
Design and Implementation.............................................................................................................5
Testing and documentation............................................................................................................12
Conclusion.....................................................................................................................................15
Reference List................................................................................................................................16
Appendix A....................................................................................................................................19
NETWORK DESIGNING AND TROUBLESHOOT
Table of Contents
Introduction......................................................................................................................................2
Knowledge and understanding........................................................................................................3
Application and Analysis.................................................................................................................4
Evaluation and Judgement...............................................................................................................4
Design and Implementation.............................................................................................................5
Testing and documentation............................................................................................................12
Conclusion.....................................................................................................................................15
Reference List................................................................................................................................16
Appendix A....................................................................................................................................19

2
NETWORK DESIGNING AND TROUBLESHOOT
Introduction
The report is created for speedfix.co.uk that have the need to deploy a network after
analysis of the current business scenario and separating each of the department by assigning
multiple VLANs. An analysis is made on the different network model that can be deployed and
the technologies and protocols that can be used for configuring the network. The functional and
nonfunctional needs of the network are evaluated for finding the relation between them with the
network equipment’s. The company have three department i.e. finance /HR, sales and engineers
and they are needed to be assigned with LAN. The network is needed to be designed such that
servers are installed in separate area and assigned to separate VLAN. A wireless network is also
required to be configured for connecting the wireless network and its access is needed to be
restricted for the other departments.
Department Devices Requirements
Finance / HR 10 Computer & Printer Other department cannot be accessed
Sales 37 Computers & Printer Other department cannot be accessed
Engineers 19 Computers & printer Other department cannot be accessed
Admins 4 Computers & printer Other department cannot be accessed
Wireless Devices
Should be sufficient for
staff access
Other department cannot be accessed,
need to be in a separate logical network
but can access servers
NETWORK DESIGNING AND TROUBLESHOOT
Introduction
The report is created for speedfix.co.uk that have the need to deploy a network after
analysis of the current business scenario and separating each of the department by assigning
multiple VLANs. An analysis is made on the different network model that can be deployed and
the technologies and protocols that can be used for configuring the network. The functional and
nonfunctional needs of the network are evaluated for finding the relation between them with the
network equipment’s. The company have three department i.e. finance /HR, sales and engineers
and they are needed to be assigned with LAN. The network is needed to be designed such that
servers are installed in separate area and assigned to separate VLAN. A wireless network is also
required to be configured for connecting the wireless network and its access is needed to be
restricted for the other departments.
Department Devices Requirements
Finance / HR 10 Computer & Printer Other department cannot be accessed
Sales 37 Computers & Printer Other department cannot be accessed
Engineers 19 Computers & printer Other department cannot be accessed
Admins 4 Computers & printer Other department cannot be accessed
Wireless Devices
Should be sufficient for
staff access
Other department cannot be accessed,
need to be in a separate logical network
but can access servers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK DESIGNING AND TROUBLESHOOT
dns/web/email &
File server
4 Servers Accessible by all computers
IoT devices
Requirements to add some IoT devices to monitor temperature and
server room door etc..
Knowledge and understanding
For the scenario of the company speedfix.co.uk an evaluation is made that helps in
identification of the needs of network and the requirement of each of the staffs are identified. For
the simulation of the network cisco packet tracer 7.2 is used and a prototype of the network is
created following the VLAN configuration. For each of the subdivision separate switches are
needed to be assigned and at the center a layer 3 device is used i.e. cisco 3560 switch and it is
configured as VTP server such that the vlan information can be shared with the client switch. For
the improvement of network outline three layer hierarchical model is selected and the network
equipment’s are installed in the core network and the layer 2 devices are installed in the access
network (Dou et al. 2018). The LAN and the WAN is designed following the design principles.
The local area network is limited to 10 km and its further extension can cause packet loss. A plan
for assigning IP address is created following the number of hosts and other devices needed to be
installed in each of the department. The multiple local area network is combined to form the
wide area network and an admin pc is needed to be installed with a network monitoring tool such
that it can monitored and a network test is needed to be made such that network maintenance
jobs can be performed. The router interface is connected with the layer 3 device and DHCP
configuration is made following the subnet plan such that the IP address gets automatically
NETWORK DESIGNING AND TROUBLESHOOT
dns/web/email &
File server
4 Servers Accessible by all computers
IoT devices
Requirements to add some IoT devices to monitor temperature and
server room door etc..
Knowledge and understanding
For the scenario of the company speedfix.co.uk an evaluation is made that helps in
identification of the needs of network and the requirement of each of the staffs are identified. For
the simulation of the network cisco packet tracer 7.2 is used and a prototype of the network is
created following the VLAN configuration. For each of the subdivision separate switches are
needed to be assigned and at the center a layer 3 device is used i.e. cisco 3560 switch and it is
configured as VTP server such that the vlan information can be shared with the client switch. For
the improvement of network outline three layer hierarchical model is selected and the network
equipment’s are installed in the core network and the layer 2 devices are installed in the access
network (Dou et al. 2018). The LAN and the WAN is designed following the design principles.
The local area network is limited to 10 km and its further extension can cause packet loss. A plan
for assigning IP address is created following the number of hosts and other devices needed to be
installed in each of the department. The multiple local area network is combined to form the
wide area network and an admin pc is needed to be installed with a network monitoring tool such
that it can monitored and a network test is needed to be made such that network maintenance
jobs can be performed. The router interface is connected with the layer 3 device and DHCP
configuration is made following the subnet plan such that the IP address gets automatically
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK DESIGNING AND TROUBLESHOOT
assigned (Hasan and Mahmood 2019). The configuration of the network device with DHCP
helps in increasing the scalability of the network and it can be configured at the central device
for implementation of the changes.
Application and Analysis
The network is needed to be configured for connecting IoT devices and monitoring the
environment of the server rooms for maintaining an optimal environment. A private IP address
of 192.168.168.0/24 is used for the wired LAN and 10.10.10.0/24 is used for the wireless
network. A network diagram is created with the description of analysis and appropriate subnet
address is created for the configuration of the network. A network model is proposed that would
help in selection of protocol and technology and develop the network following the company
needs (Ortiz 2016). An analysis is also made on the security needs and applied for isolating the
access of each of the department and testing documentation is created for the configuration and
network device and verification of the configuration.
The layer three switch is used for allowing VTP server configuration and allowing the
layer 2 devices configured as client to automatically fetch the VLAN information (Talavera and
Santisteban 2015). The router manages the access of the users of different VLAN to reach the
server and can be configured with access control list for enforcing centralized management and
restrict an IP to access the server.
Evaluation and Judgement
There are multiple departments in the speedfix.co.uk company that is Finance/HR, Sales,
Engineers, Admins. Vlans are needed to be created for the department and the server, wireless
and iot devices network and it is needed to be assigned with a name and number for configuring
NETWORK DESIGNING AND TROUBLESHOOT
assigned (Hasan and Mahmood 2019). The configuration of the network device with DHCP
helps in increasing the scalability of the network and it can be configured at the central device
for implementation of the changes.
Application and Analysis
The network is needed to be configured for connecting IoT devices and monitoring the
environment of the server rooms for maintaining an optimal environment. A private IP address
of 192.168.168.0/24 is used for the wired LAN and 10.10.10.0/24 is used for the wireless
network. A network diagram is created with the description of analysis and appropriate subnet
address is created for the configuration of the network. A network model is proposed that would
help in selection of protocol and technology and develop the network following the company
needs (Ortiz 2016). An analysis is also made on the security needs and applied for isolating the
access of each of the department and testing documentation is created for the configuration and
network device and verification of the configuration.
The layer three switch is used for allowing VTP server configuration and allowing the
layer 2 devices configured as client to automatically fetch the VLAN information (Talavera and
Santisteban 2015). The router manages the access of the users of different VLAN to reach the
server and can be configured with access control list for enforcing centralized management and
restrict an IP to access the server.
Evaluation and Judgement
There are multiple departments in the speedfix.co.uk company that is Finance/HR, Sales,
Engineers, Admins. Vlans are needed to be created for the department and the server, wireless
and iot devices network and it is needed to be assigned with a name and number for configuring

5
NETWORK DESIGNING AND TROUBLESHOOT
the network. The VLAN can be used as a separation for the different departments and it helps in
offering the user to secure and management of network flow and improve the network scalability
(Ahamed 2018). Local area network is used for connecting the computers and the virtual LANs
can be used for connecting with the physical network without the need of multiple cabling set
and network device. The VLAN can help the network administrator grouping the host even if the
network devices are not connected with the same switch directly. VLAN can help in creating a
simple network design and deploy the network for reducing congestion and collision in the
network (Gao et al. 2017). The network can be subdivided into VLANs and configuring the
network equipment’s and partition the network as the physical port.
For the configuration of the layer 3 switch VTP server configuration is analyzed and a
configuration is made for the switch and configuring the VTP domain and named as AAA. The
main layer 3 switch connected with the router interface is configured as VTP server and the
switch installed for providing service to the different departments are configured as VTP client
(Xu et al. 2015). The switchport are configured with trunk for sharing the VLAN information
and allow the host to be assigned with specific IP address created for that dhcp pool.
NETWORK DESIGNING AND TROUBLESHOOT
the network. The VLAN can be used as a separation for the different departments and it helps in
offering the user to secure and management of network flow and improve the network scalability
(Ahamed 2018). Local area network is used for connecting the computers and the virtual LANs
can be used for connecting with the physical network without the need of multiple cabling set
and network device. The VLAN can help the network administrator grouping the host even if the
network devices are not connected with the same switch directly. VLAN can help in creating a
simple network design and deploy the network for reducing congestion and collision in the
network (Gao et al. 2017). The network can be subdivided into VLANs and configuring the
network equipment’s and partition the network as the physical port.
For the configuration of the layer 3 switch VTP server configuration is analyzed and a
configuration is made for the switch and configuring the VTP domain and named as AAA. The
main layer 3 switch connected with the router interface is configured as VTP server and the
switch installed for providing service to the different departments are configured as VTP client
(Xu et al. 2015). The switchport are configured with trunk for sharing the VLAN information
and allow the host to be assigned with specific IP address created for that dhcp pool.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK DESIGNING AND TROUBLESHOOT
Design and Implementation
The network is developed following the workstation and server distribution table and
three layer network model is applied for developing the LAN design for speedfix.co.uk. The IP
configuration are done in the router and it is also configured with ACL such that the network
device connected with the access layer device are restricted to communicate with the device
connected with other VLAN. The access of the server is needed to be maintained for each of the
department and separate network is needed to be used for the wireless network with different IP
address such that it can help in increasing the security of the network (Naji et al. 2016). A server
is needed to be configured for connecting the IoT devices and monitoring the doors and
temperature. A cooling system and fire detection system is also added for securing the
workspace from fire breakout.
Major IP Address: 192.168.168.0/24
Number of available IPs in the major network: 254
Number of available IPs needed: 83
NETWORK DESIGNING AND TROUBLESHOOT
Design and Implementation
The network is developed following the workstation and server distribution table and
three layer network model is applied for developing the LAN design for speedfix.co.uk. The IP
configuration are done in the router and it is also configured with ACL such that the network
device connected with the access layer device are restricted to communicate with the device
connected with other VLAN. The access of the server is needed to be maintained for each of the
department and separate network is needed to be used for the wireless network with different IP
address such that it can help in increasing the security of the network (Naji et al. 2016). A server
is needed to be configured for connecting the IoT devices and monitoring the doors and
temperature. A cooling system and fire detection system is also added for securing the
workspace from fire breakout.
Major IP Address: 192.168.168.0/24
Number of available IPs in the major network: 254
Number of available IPs needed: 83
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK DESIGNING AND TROUBLESHOOT
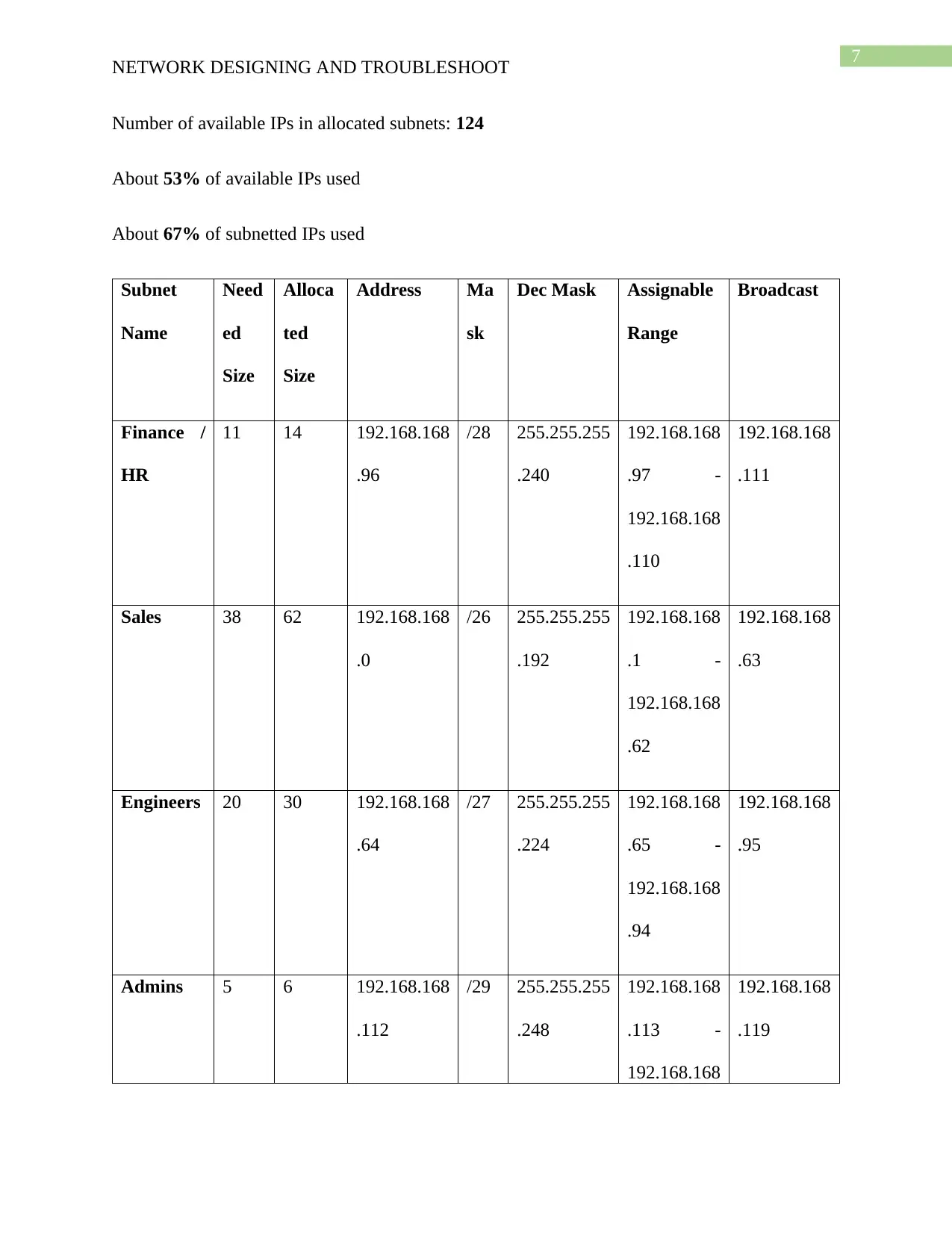
Number of available IPs in allocated subnets: 124
About 53% of available IPs used
About 67% of subnetted IPs used
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Finance /
HR
11 14 192.168.168
.96
/28 255.255.255
.240
192.168.168
.97 -
192.168.168
.110
192.168.168
.111
Sales 38 62 192.168.168
.0
/26 255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Engineers 20 30 192.168.168
.64
/27 255.255.255
.224
192.168.168
.65 -
192.168.168
.94
192.168.168
.95
Admins 5 6 192.168.168
.112
/29 255.255.255
.248
192.168.168
.113 -
192.168.168
192.168.168
.119
NETWORK DESIGNING AND TROUBLESHOOT
Number of available IPs in allocated subnets: 124
About 53% of available IPs used
About 67% of subnetted IPs used
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Finance /
HR
11 14 192.168.168
.96
/28 255.255.255
.240
192.168.168
.97 -
192.168.168
.110
192.168.168
.111
Sales 38 62 192.168.168
.0
/26 255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Engineers 20 30 192.168.168
.64
/27 255.255.255
.224
192.168.168
.65 -
192.168.168
.94
192.168.168
.95
Admins 5 6 192.168.168
.112
/29 255.255.255
.248
192.168.168
.113 -
192.168.168
192.168.168
.119
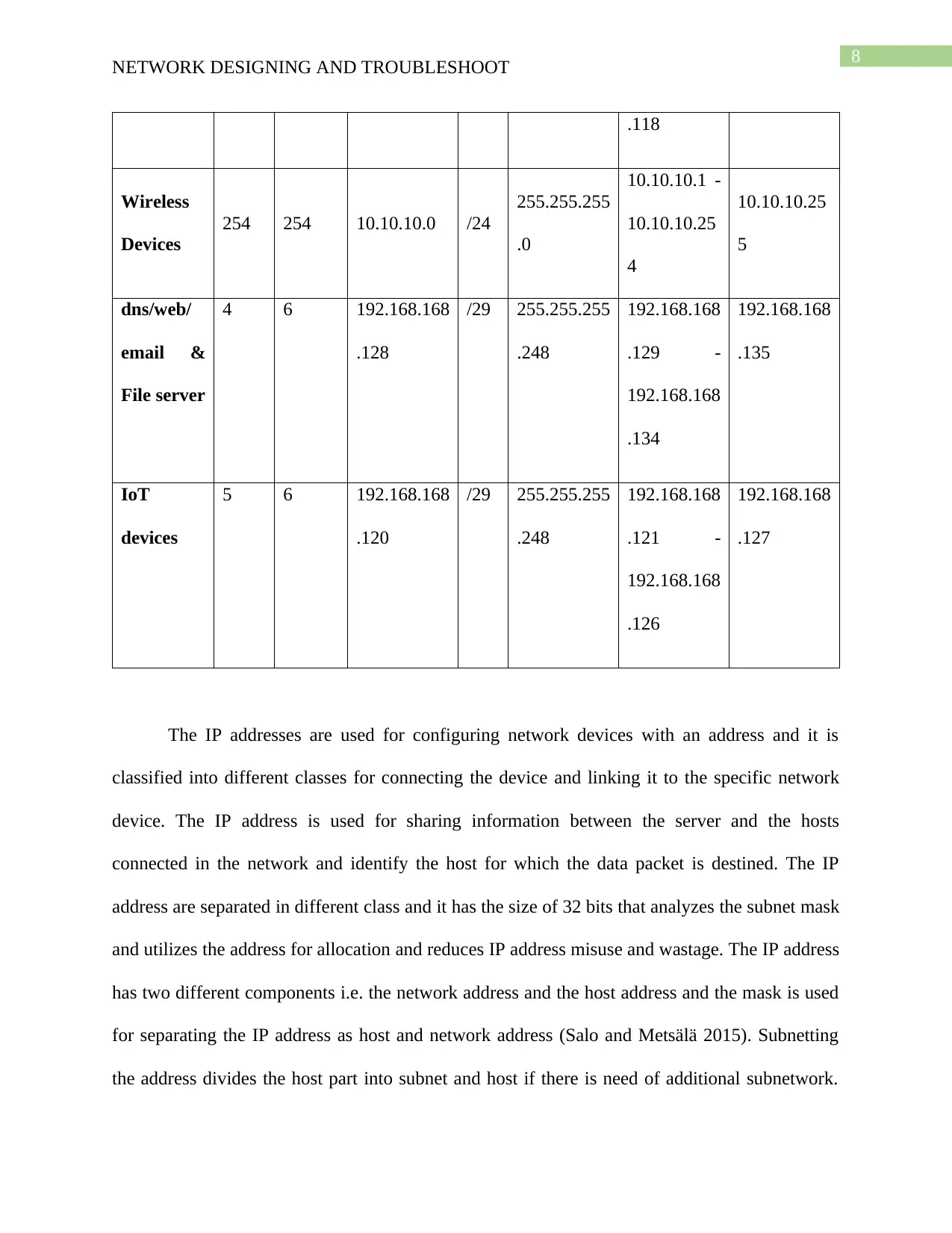
8
NETWORK DESIGNING AND TROUBLESHOOT
.118
Wireless
Devices
254 254 10.10.10.0 /24
255.255.255
.0
10.10.10.1 -
10.10.10.25
4
10.10.10.25
5
dns/web/
email &
File server
4 6 192.168.168
.128
/29 255.255.255
.248
192.168.168
.129 -
192.168.168
.134
192.168.168
.135
IoT
devices
5 6 192.168.168
.120
/29 255.255.255
.248
192.168.168
.121 -
192.168.168
.126
192.168.168
.127
The IP addresses are used for configuring network devices with an address and it is
classified into different classes for connecting the device and linking it to the specific network
device. The IP address is used for sharing information between the server and the hosts
connected in the network and identify the host for which the data packet is destined. The IP
address are separated in different class and it has the size of 32 bits that analyzes the subnet mask
and utilizes the address for allocation and reduces IP address misuse and wastage. The IP address
has two different components i.e. the network address and the host address and the mask is used
for separating the IP address as host and network address (Salo and Metsälä 2015). Subnetting
the address divides the host part into subnet and host if there is need of additional subnetwork.
NETWORK DESIGNING AND TROUBLESHOOT
.118
Wireless
Devices
254 254 10.10.10.0 /24
255.255.255
.0
10.10.10.1 -
10.10.10.25
4
10.10.10.25
5
dns/web/
email &
File server
4 6 192.168.168
.128
/29 255.255.255
.248
192.168.168
.129 -
192.168.168
.134
192.168.168
.135
IoT
devices
5 6 192.168.168
.120
/29 255.255.255
.248
192.168.168
.121 -
192.168.168
.126
192.168.168
.127
The IP addresses are used for configuring network devices with an address and it is
classified into different classes for connecting the device and linking it to the specific network
device. The IP address is used for sharing information between the server and the hosts
connected in the network and identify the host for which the data packet is destined. The IP
address are separated in different class and it has the size of 32 bits that analyzes the subnet mask
and utilizes the address for allocation and reduces IP address misuse and wastage. The IP address
has two different components i.e. the network address and the host address and the mask is used
for separating the IP address as host and network address (Salo and Metsälä 2015). Subnetting
the address divides the host part into subnet and host if there is need of additional subnetwork.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK DESIGNING AND TROUBLESHOOT
The IP network is subnetted for dividing a big network into smaller network such that the
network can be reorganized and the network security can be improved. Classless inter domain
routing is used for the representation of classful address and increasing the efficiency of
allocation of IP address.
The Finance or HR department have the need of 10 computer and a printer and is
assigned with a private IP address for the allocation of 11 IP address to the computers and the
printers. The IP address 192.168.168.96 /26 is assigned as a subnet of Finance /HR
department and for it the assignable range of IP address 192.168.168.97 - 192.168.168.110 and
the subnet mask address used here is 255.255.255.192. A subnet table is created for listing the
assignable of Ip address, subnet mask, broadcast address, for each of the department.
The sales department has the requirement of 38 IP address for connecting the computers
and printers. The IP address 192.168.168.96/28 is assigned as a subnet of sales department and
for it the assignable range of IP address 192.168.168.1 - 192.168.168.62 and the subnet mask
address used here is 255.255.255.240.
The Engineers department has the requirement of 20 IP address for connecting the
computers and printers. The IP address 192.168.168.64 /27 is assigned as a subnet of
engineers department and for it the assignable range of IP address 192.168.168.65 -
192.168.168.94 and the subnet mask address used here is 255.255.255.224.
A VLAN is created for the Admin department and it has the requirement of 5 IP address
for connecting the computers and printers (Teo and Cho 2016). The IP address 192.168.168.112
/29 is assigned as a subnet of admin department and for it the assignable range of IP
NETWORK DESIGNING AND TROUBLESHOOT
The IP network is subnetted for dividing a big network into smaller network such that the
network can be reorganized and the network security can be improved. Classless inter domain
routing is used for the representation of classful address and increasing the efficiency of
allocation of IP address.
The Finance or HR department have the need of 10 computer and a printer and is
assigned with a private IP address for the allocation of 11 IP address to the computers and the
printers. The IP address 192.168.168.96 /26 is assigned as a subnet of Finance /HR
department and for it the assignable range of IP address 192.168.168.97 - 192.168.168.110 and
the subnet mask address used here is 255.255.255.192. A subnet table is created for listing the
assignable of Ip address, subnet mask, broadcast address, for each of the department.
The sales department has the requirement of 38 IP address for connecting the computers
and printers. The IP address 192.168.168.96/28 is assigned as a subnet of sales department and
for it the assignable range of IP address 192.168.168.1 - 192.168.168.62 and the subnet mask
address used here is 255.255.255.240.
The Engineers department has the requirement of 20 IP address for connecting the
computers and printers. The IP address 192.168.168.64 /27 is assigned as a subnet of
engineers department and for it the assignable range of IP address 192.168.168.65 -
192.168.168.94 and the subnet mask address used here is 255.255.255.224.
A VLAN is created for the Admin department and it has the requirement of 5 IP address
for connecting the computers and printers (Teo and Cho 2016). The IP address 192.168.168.112
/29 is assigned as a subnet of admin department and for it the assignable range of IP
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK DESIGNING AND TROUBLESHOOT
address 192.168.168.113 - 192.168.168.118 and the subnet mask address used here is
255.255.255.248.
A VLAN is created for the 4 servers such as dns, web, email and file server and it has the
requirement of 4 IP address for connecting the multiple servers. The IP address 192.168.168.128
/29 is assigned as a subnet of server and for it the assignable range of IP address
192.168.168.129 - 192.168.168.134 and the subnet mask address used here is 255.255.255.248.
A VLAN is created for connecting the IoT devices for enabling the device to be assigned
with IP address automatically from the DHCP pool.
Lastly, a subnet is created for the Wireless Network that have the requirement to connect
mobile devices with the organizational network. For the wireless network different IP address is
used and it is configured such that the right to use of the servers are restricted for the devices
connected with the wireless access point (Toivakka 2018). The IP address 10.10.10.0 /24 is
assigned as a subnet of server and for it the assignable range of IP address 10.10.10.1 -
10.10.10.254 and the subnet mask address used here is 255.255.255.0.
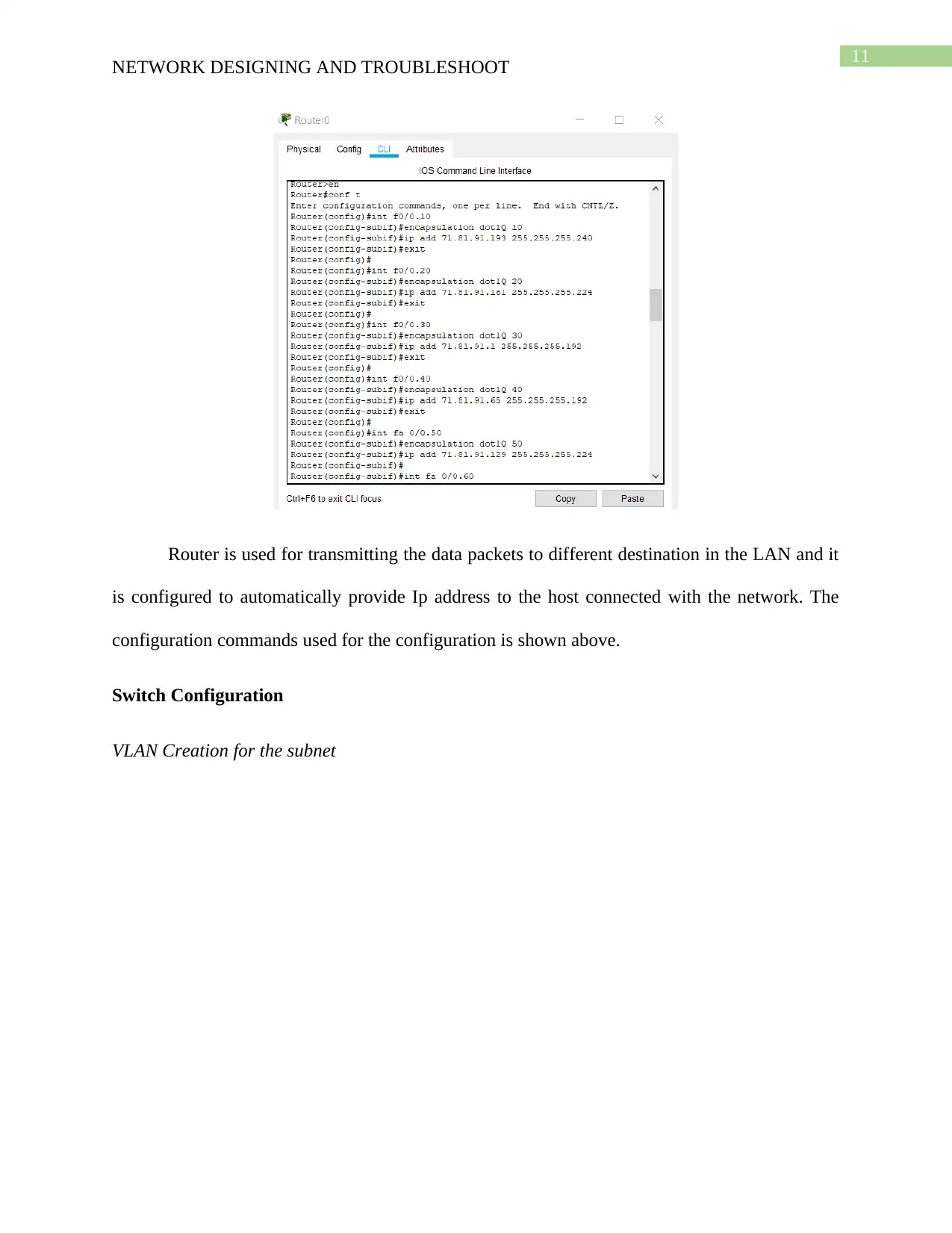
Router Configuration
NETWORK DESIGNING AND TROUBLESHOOT
address 192.168.168.113 - 192.168.168.118 and the subnet mask address used here is
255.255.255.248.
A VLAN is created for the 4 servers such as dns, web, email and file server and it has the
requirement of 4 IP address for connecting the multiple servers. The IP address 192.168.168.128
/29 is assigned as a subnet of server and for it the assignable range of IP address
192.168.168.129 - 192.168.168.134 and the subnet mask address used here is 255.255.255.248.
A VLAN is created for connecting the IoT devices for enabling the device to be assigned
with IP address automatically from the DHCP pool.
Lastly, a subnet is created for the Wireless Network that have the requirement to connect
mobile devices with the organizational network. For the wireless network different IP address is
used and it is configured such that the right to use of the servers are restricted for the devices
connected with the wireless access point (Toivakka 2018). The IP address 10.10.10.0 /24 is
assigned as a subnet of server and for it the assignable range of IP address 10.10.10.1 -
10.10.10.254 and the subnet mask address used here is 255.255.255.0.
Router Configuration
11
NETWORK DESIGNING AND TROUBLESHOOT
Router is used for transmitting the data packets to different destination in the LAN and it
is configured to automatically provide Ip address to the host connected with the network. The
configuration commands used for the configuration is shown above.
Switch Configuration
VLAN Creation for the subnet
NETWORK DESIGNING AND TROUBLESHOOT
Router is used for transmitting the data packets to different destination in the LAN and it
is configured to automatically provide Ip address to the host connected with the network. The
configuration commands used for the configuration is shown above.
Switch Configuration
VLAN Creation for the subnet
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



