BSC Computing Technologies Network Design and Troubleshooting Report
VerifiedAdded on 2022/08/09
|17
|3617
|17
Report
AI Summary
This report presents a case study of speedfix.co.uk, detailing the design and implementation of a network infrastructure. The student evaluates the company's current business scenario and proposes a network design that incorporates VLANs to separate departments. The report covers the selection of network models, technologies, and protocols, including Cisco packet tracer 7.2 for simulation. It addresses IP addressing, subnetting, and the configuration of Layer 3 switches and DHCP servers. The design includes considerations for network security, IoT device integration, and wireless network access. The report provides a comprehensive analysis of the network requirements, design choices, and implementation steps, including subnet allocation, VLAN configuration, and access control lists. The document showcases the student's understanding of network technologies and their ability to apply them in a practical scenario. The report also includes an evaluation of the network design, addressing the needs of each department and proposing solutions for network scalability and security.

Running head: BSC COMPUTING TECHNOLOGIES
NETWORK DESIGNING AND TROUBLESHOOTING
Name of the Student
Name of the University
Author Note
NETWORK DESIGNING AND TROUBLESHOOTING
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BSC COMPUTING TECHNOLOGIES
Table of Contents
Introduction....................................................................................................................2
Knowledge and Understanding......................................................................................2
Application and Analysis...............................................................................................3
Evaluation and Judgement.............................................................................................4
Design and Implementation...........................................................................................5
Testing and Documentation.........................................................................................12
Conclusion....................................................................................................................14
References....................................................................................................................15
Table of Contents
Introduction....................................................................................................................2
Knowledge and Understanding......................................................................................2
Application and Analysis...............................................................................................3
Evaluation and Judgement.............................................................................................4
Design and Implementation...........................................................................................5
Testing and Documentation.........................................................................................12
Conclusion....................................................................................................................14
References....................................................................................................................15

2BSC COMPUTING TECHNOLOGIES
Introduction
The report deals with the case study of speedfix.co.uk, as they require implementing a
network after the evaluation of their present scenario of business and then separating every
departments of the company by implementing more than one Virtual LANs. An evaluation
about the various models of networks can be implemented and the various technologies that
can be used in order to configure the network for the Company. The company consists of the
four departments namely Finance/HR, sales, Admins and engineers. The network of the
company includes mainly four servers, dns, web, email and a file server those are common to
all. All the servers are shared between all the users of the network. The admin of the
company has decided to permit the staffs of the company to utilise the wireless networks by
using their own devices those are wireless such their mobile phones in order to access the
internet. The report deals with the knowledge and understanding of the network technologies
and the protocols those are required for the company, the design, and the implementation of
those technologies
Knowledge and Understanding
The business operation of the company need to be evaluated in order to identify the
requirements of the network. In order to simulate the network Cisco packet tracer 7.2 is
utilised and a model of the network is developed following the configuration of the VLAN
(Hameed and Mian 2016). For every division, separate switches are to be implemented and at
the center a device of layer 3 is utilised that is the switch of Cisco 3560 and the switch is
configured as the server of VTP and it is implemented in this way so that the information of
VLAN can be easily shared with the switch of the client. In order to improve the network, a
model of three layers hierarchical is chosen and the tools of the networks are implemented in
the network. The devices those are at the layer 2 are installed in the network of access
Introduction
The report deals with the case study of speedfix.co.uk, as they require implementing a
network after the evaluation of their present scenario of business and then separating every
departments of the company by implementing more than one Virtual LANs. An evaluation
about the various models of networks can be implemented and the various technologies that
can be used in order to configure the network for the Company. The company consists of the
four departments namely Finance/HR, sales, Admins and engineers. The network of the
company includes mainly four servers, dns, web, email and a file server those are common to
all. All the servers are shared between all the users of the network. The admin of the
company has decided to permit the staffs of the company to utilise the wireless networks by
using their own devices those are wireless such their mobile phones in order to access the
internet. The report deals with the knowledge and understanding of the network technologies
and the protocols those are required for the company, the design, and the implementation of
those technologies
Knowledge and Understanding
The business operation of the company need to be evaluated in order to identify the
requirements of the network. In order to simulate the network Cisco packet tracer 7.2 is
utilised and a model of the network is developed following the configuration of the VLAN
(Hameed and Mian 2016). For every division, separate switches are to be implemented and at
the center a device of layer 3 is utilised that is the switch of Cisco 3560 and the switch is
configured as the server of VTP and it is implemented in this way so that the information of
VLAN can be easily shared with the switch of the client. In order to improve the network, a
model of three layers hierarchical is chosen and the tools of the networks are implemented in
the network. The devices those are at the layer 2 are installed in the network of access
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BSC COMPUTING TECHNOLOGIES
(Hameed and Wasim 2019). The WAN and LAN is designed by following the principles of
design. The LAN is bounded to only 10 km and if it is extended it can cause loss of packets.
A plan in order to allocate the address of IP is developed where the number of hosts and the
other devices those are required to be installed in every department of the company. The
more than one LAN is combined in order to form the WAN and a pc of the admin is required
to be deployed with a monitoring tool of the network such that the network can be monitored
and the test of a network is required in order to execute the jobs of maintenance of the
network. The interface of the router is connected to the device of layer 3 and the
configuration of DHCP is done by following the plan of subnet so that the address of IP gets
auto allocated (Raza, Kulkarni and Sooriyabandara 2017). The configuration of the device of
network with the DHCP assists in maximizing the network scalability and it can be
constructed with the device that is at the central in order to implement the changes.
Application and Analysis
The network of the company is required to be constructed in order to connect the
devices of the IoT and monitor the environment of the rooms of the servers to maintain a best
environment (Wurm et al 2016). A private address of IP of 192.168.1680/24 is utilised for the
LAN and 10.10.10.0/24 is utilised for the network that is wireless. An illustration of the
network is developed with the description of evaluation and proper address of subnet is
developed for the construction of the network. A model of the network is proposed that will
assist in choosing the technology and the protocol and then create the network following the
requirements of the company (Park et al 2016). An evaluation is made on the requirement of
the security and applied to isolate the admittance of every department and the documentation
of testing is developed to configure and verify the configuration.
(Hameed and Wasim 2019). The WAN and LAN is designed by following the principles of
design. The LAN is bounded to only 10 km and if it is extended it can cause loss of packets.
A plan in order to allocate the address of IP is developed where the number of hosts and the
other devices those are required to be installed in every department of the company. The
more than one LAN is combined in order to form the WAN and a pc of the admin is required
to be deployed with a monitoring tool of the network such that the network can be monitored
and the test of a network is required in order to execute the jobs of maintenance of the
network. The interface of the router is connected to the device of layer 3 and the
configuration of DHCP is done by following the plan of subnet so that the address of IP gets
auto allocated (Raza, Kulkarni and Sooriyabandara 2017). The configuration of the device of
network with the DHCP assists in maximizing the network scalability and it can be
constructed with the device that is at the central in order to implement the changes.
Application and Analysis
The network of the company is required to be constructed in order to connect the
devices of the IoT and monitor the environment of the rooms of the servers to maintain a best
environment (Wurm et al 2016). A private address of IP of 192.168.1680/24 is utilised for the
LAN and 10.10.10.0/24 is utilised for the network that is wireless. An illustration of the
network is developed with the description of evaluation and proper address of subnet is
developed for the construction of the network. A model of the network is proposed that will
assist in choosing the technology and the protocol and then create the network following the
requirements of the company (Park et al 2016). An evaluation is made on the requirement of
the security and applied to isolate the admittance of every department and the documentation
of testing is developed to configure and verify the configuration.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BSC COMPUTING TECHNOLOGIES
The switch of layer three is utilised in order to permit configuration of the server of
VTP and permit the devices of layer 2 that is configured as the client in order to
automatically fetch the information of the Virtual LAN (Mellette et al 2016). The router
administers the admittance of the user of the various virtual LAN in order to reach the server
and can be constructed with the list of access control in order to enforce the centralized
management and then limit an address of IP to gain admittance to the server.
Evaluation and Judgement
There are more than one department in the company such as the finance, engineers,
HR and sales. The virtual LANs are required to be developed for the various department of
the company and the various technologies such as the server, devices of IoT are required to
be deployed in order to configure the network. A virtual LAN is any domain of broadcast that
is isolated and partitioned in network of computer at the layer of data link (Achleitner et al
2017). The VLAN can be utilised in order to separate the various departments of the
company and the VLAN assists in providing the user of the system to manage and secure the
flow of the network and upgrade the scalability of the network. The LAN is utilised in order
to connect the systems of the company and the VLANs are utilised in order to connect with
the physical network without the requirement of more than one set of cable and devices those
are used in the network. The VLAN can assist the administrator of the network to group the
host when the devices of the network are not connected with the similar switch. The VLAN
can assist in developing a easy design of the network and then implement the network in
order to minimize the collision and congestion those are present in the network (Lai and Liou
2016). The network can be further split into virtual LANs and configuring the devices of the
network and then dividing the network as the port that is physical.
The switch of layer three is utilised in order to permit configuration of the server of
VTP and permit the devices of layer 2 that is configured as the client in order to
automatically fetch the information of the Virtual LAN (Mellette et al 2016). The router
administers the admittance of the user of the various virtual LAN in order to reach the server
and can be constructed with the list of access control in order to enforce the centralized
management and then limit an address of IP to gain admittance to the server.
Evaluation and Judgement
There are more than one department in the company such as the finance, engineers,
HR and sales. The virtual LANs are required to be developed for the various department of
the company and the various technologies such as the server, devices of IoT are required to
be deployed in order to configure the network. A virtual LAN is any domain of broadcast that
is isolated and partitioned in network of computer at the layer of data link (Achleitner et al
2017). The VLAN can be utilised in order to separate the various departments of the
company and the VLAN assists in providing the user of the system to manage and secure the
flow of the network and upgrade the scalability of the network. The LAN is utilised in order
to connect the systems of the company and the VLANs are utilised in order to connect with
the physical network without the requirement of more than one set of cable and devices those
are used in the network. The VLAN can assist the administrator of the network to group the
host when the devices of the network are not connected with the similar switch. The VLAN
can assist in developing a easy design of the network and then implement the network in
order to minimize the collision and congestion those are present in the network (Lai and Liou
2016). The network can be further split into virtual LANs and configuring the devices of the
network and then dividing the network as the port that is physical.

5BSC COMPUTING TECHNOLOGIES
A layer 3 switch is a device of hardware that is utilised in the routing of the network.
Both can maintain the same protocols of routing, examine the packets those are incoming and
make decisions of routing those are dynamic and it is usually based on the destination and the
source address (Van et al 2018). A layer 3 switch amalgamates the features of a router and a
switch. It acts as a switch in order to connect to the devices that are on the similar subnet or
the VLAN at very fast speed and has the intelligence of IP routing that is constructed into the
switch in order to double it up as a router.
In order to configure the switch of layer 3, the configuration of the server of VTP is
examined and then a configuration is made for the switch that will be implemented in the
network. The main switch of layer 3 is connected with the interface of the router and then it is
configured as the server of VTP (Sharma, Verma and Nahar 2019). The switch that is
deployed in order to offer services to the various departments is then configured as the VTP
client. The switch port are then configured with the network trunk in order to share the
information of the VLAN and permit the host to be allocated with the particular address of IP
that is developed for the pool of DHCP.
Design and Implementation
A layer 3 switch is a device of hardware that is utilised in the routing of the network.
Both can maintain the same protocols of routing, examine the packets those are incoming and
make decisions of routing those are dynamic and it is usually based on the destination and the
source address (Van et al 2018). A layer 3 switch amalgamates the features of a router and a
switch. It acts as a switch in order to connect to the devices that are on the similar subnet or
the VLAN at very fast speed and has the intelligence of IP routing that is constructed into the
switch in order to double it up as a router.
In order to configure the switch of layer 3, the configuration of the server of VTP is
examined and then a configuration is made for the switch that will be implemented in the
network. The main switch of layer 3 is connected with the interface of the router and then it is
configured as the server of VTP (Sharma, Verma and Nahar 2019). The switch that is
deployed in order to offer services to the various departments is then configured as the VTP
client. The switch port are then configured with the network trunk in order to share the
information of the VLAN and permit the host to be allocated with the particular address of IP
that is developed for the pool of DHCP.
Design and Implementation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6BSC COMPUTING TECHNOLOGIES
The network is created by following the workstation and distribution table of the
server and the model of three-layer network is related in order to create the design of the
LAN for the company speedfix.co.uk. The configuration of IP is done in the router and then it
is configured with ACL. This is done because the devices of the network those are connected
with the devices of the layer of access are limited to communicate with the devices those are
connected to the other Virtual LANs. The admittance to the server is required to be
maintained for every department and separate network is required to be utilised for the
network that is wireless with the various addresses of IP so that it can assist in maximizing
the network security. A server is required to be configured in order to connect the devices of
IoT and administering the temperature and the doors. A system of cooling and a system of
fire detection is added in order to secure the workplace if any case breakout of fire occurs.
The main IP address of the network: 192.168.168.0/24
Number of IPs those are available in the main network: 254
Number of available IPs those are required: 83
Number of available IPs in the assigned subnet: 124
About 53% of the IPs that is available is utilised
About 67% of the IPs those are subnetted are utilised.
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Finance /
HR
11 14 192.168.16
8.96
/28 255.255.25
5.240
192.168.16
8.97 -
192.168.16
192.168.16
8.111
The network is created by following the workstation and distribution table of the
server and the model of three-layer network is related in order to create the design of the
LAN for the company speedfix.co.uk. The configuration of IP is done in the router and then it
is configured with ACL. This is done because the devices of the network those are connected
with the devices of the layer of access are limited to communicate with the devices those are
connected to the other Virtual LANs. The admittance to the server is required to be
maintained for every department and separate network is required to be utilised for the
network that is wireless with the various addresses of IP so that it can assist in maximizing
the network security. A server is required to be configured in order to connect the devices of
IoT and administering the temperature and the doors. A system of cooling and a system of
fire detection is added in order to secure the workplace if any case breakout of fire occurs.
The main IP address of the network: 192.168.168.0/24
Number of IPs those are available in the main network: 254
Number of available IPs those are required: 83
Number of available IPs in the assigned subnet: 124
About 53% of the IPs that is available is utilised
About 67% of the IPs those are subnetted are utilised.
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Finance /
HR
11 14 192.168.16
8.96
/28 255.255.25
5.240
192.168.16
8.97 -
192.168.16
192.168.16
8.111
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BSC COMPUTING TECHNOLOGIES
8.110
Sales 38 62 192.168.16
8.0
/26 255.255.25
5.192
192.168.16
8.1 -
192.168.16
8.62
192.168.16
8.63
Engineers 20 30 192.168.16
8.64
/27 255.255.25
5.224
192.168.16
8.65 -
192.168.16
8.94
192.168.16
8.95
Admins 5 6 192.168.16
8.112
/29 255.255.25
5.248
192.168.16
8.113 -
192.168.16
8.118
192.168.16
8.119
Wireless
Devices
254 254 10.10.10.0 /24
255.255.25
5.0
10.10.10.1 -
10.10.10.25
4
10.10.10.25
5
dns/web/
email &
File
server
4 6 192.168.16
8.128
/29 255.255.25
5.248
192.168.16
8.129 -
192.168.16
8.134
192.168.16
8.135
IoT
devices
5 6 192.168.16
8.120
/29 255.255.25
5.248
192.168.16
8.121 -
192.168.16
192.168.16
8.127
8.110
Sales 38 62 192.168.16
8.0
/26 255.255.25
5.192
192.168.16
8.1 -
192.168.16
8.62
192.168.16
8.63
Engineers 20 30 192.168.16
8.64
/27 255.255.25
5.224
192.168.16
8.65 -
192.168.16
8.94
192.168.16
8.95
Admins 5 6 192.168.16
8.112
/29 255.255.25
5.248
192.168.16
8.113 -
192.168.16
8.118
192.168.16
8.119
Wireless
Devices
254 254 10.10.10.0 /24
255.255.25
5.0
10.10.10.1 -
10.10.10.25
4
10.10.10.25
5
dns/web/
email &
File
server
4 6 192.168.16
8.128
/29 255.255.25
5.248
192.168.16
8.129 -
192.168.16
8.134
192.168.16
8.135
IoT
devices
5 6 192.168.16
8.120
/29 255.255.25
5.248
192.168.16
8.121 -
192.168.16
192.168.16
8.127

8BSC COMPUTING TECHNOLOGIES
8.126
The addresses of IP are utilised in order to configure the devices of network with an
address and then it is categorized into various classes to connect to the devices and then link
it to the particular device of network. The address of IP is utilised in order to share
information between the hosts and the server those are connected to the network and
recognise the host to which the packers of data is destined. The address of IP are divided into
various classes and the IP address has the size of 32 bits that evaluates the subnet mask and
uses the address in order to assign and minimize the misuse of address of IP. The address of
IP address has two different components, first is the address of the network and the second is
the address of the host. A mask is utilised in order to split the IP address as the address off
host and address of network. The address of IP is subnetting in order to split a large network
into much smaller networks so that the network can organized and the security of the network
can be upgraded. The routing of classless inter domain is utilised in order to represent the
classful address and maximize the efficiency of assigning the address of IP.
The department of finance have the requirement of 10 computers and a printer and it
is allocated with a private address of IP to assign 11 address of IP to the printers and the
computers. The IP address 192.168.168/26 is allocated as a subnet of department of finance
and in order to do this the allocable range of the TP is 192.168.168.97- 192.168.168.110 and
the address of subnet mask that is utilised here is 255.255.255.192. A table of subnet is
created in order to list the allocable address of IP, address of broadcast and the subnet mask
for every department.
The department of sales has a need of 38 addresses of IP in order to connect to the
printers and the computers. The address of IP 192.168.168.96/28 is allocated as the subnet of
8.126
The addresses of IP are utilised in order to configure the devices of network with an
address and then it is categorized into various classes to connect to the devices and then link
it to the particular device of network. The address of IP is utilised in order to share
information between the hosts and the server those are connected to the network and
recognise the host to which the packers of data is destined. The address of IP are divided into
various classes and the IP address has the size of 32 bits that evaluates the subnet mask and
uses the address in order to assign and minimize the misuse of address of IP. The address of
IP address has two different components, first is the address of the network and the second is
the address of the host. A mask is utilised in order to split the IP address as the address off
host and address of network. The address of IP is subnetting in order to split a large network
into much smaller networks so that the network can organized and the security of the network
can be upgraded. The routing of classless inter domain is utilised in order to represent the
classful address and maximize the efficiency of assigning the address of IP.
The department of finance have the requirement of 10 computers and a printer and it
is allocated with a private address of IP to assign 11 address of IP to the printers and the
computers. The IP address 192.168.168/26 is allocated as a subnet of department of finance
and in order to do this the allocable range of the TP is 192.168.168.97- 192.168.168.110 and
the address of subnet mask that is utilised here is 255.255.255.192. A table of subnet is
created in order to list the allocable address of IP, address of broadcast and the subnet mask
for every department.
The department of sales has a need of 38 addresses of IP in order to connect to the
printers and the computers. The address of IP 192.168.168.96/28 is allocated as the subnet of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BSC COMPUTING TECHNOLOGIES
the department of sales and for the department the allocable address of IP is 192.168.168.1 –
192.168.168.62 and the address of subnet mask that is utilised in this department is
255.255.255.240.
A Virtual LAN is developed for the department of admin and it has the need of five
address of IP in order to connect the printers and the computers. The address of IP
192.168.168.112/29 is allocated as a subnet of the department of admin and for this
department the allocable range of address of IP 192.168.168.113- 192.168.168.118 and the
address of subnet mask utilised here is 255.255.255.248.
A Virtual LAN is developed for the 4 various servers such as the DNS, email, web
and the file server and it has the need of 4 address of IP in order to connect to more than one
server. The address of IP 192.168.168.128/29 is allocated as a subnet of the server and for
this the allocable range of the IP address is 192.168.168.129 – 192.168.168.134 and the
address of subnet mask that is utilised here 255.255.255.248.
A VLAN is developed in order to connect the devices of IoT in order to enable the
devices to be allocated with the address of IP automatically from the pool of DHCP.
A subnet is developed for the networks that have the need to connect the devices
those are mobile with network of the organization. For the network that is wireless various
addresses of IP is utilised and configured so that admittance of the servers are limited for the
devices those are connected with the point of access those are wireless. The address of IP
10.10.10.0/24 is allocated as a subnet of the server and for it the allocable range of the
address of IP is 10.10.10.1 – 10.10.10.254 and the address of subnet mask that is utilised here
is 255.255.255.0.
Router Configuration
the department of sales and for the department the allocable address of IP is 192.168.168.1 –
192.168.168.62 and the address of subnet mask that is utilised in this department is
255.255.255.240.
A Virtual LAN is developed for the department of admin and it has the need of five
address of IP in order to connect the printers and the computers. The address of IP
192.168.168.112/29 is allocated as a subnet of the department of admin and for this
department the allocable range of address of IP 192.168.168.113- 192.168.168.118 and the
address of subnet mask utilised here is 255.255.255.248.
A Virtual LAN is developed for the 4 various servers such as the DNS, email, web
and the file server and it has the need of 4 address of IP in order to connect to more than one
server. The address of IP 192.168.168.128/29 is allocated as a subnet of the server and for
this the allocable range of the IP address is 192.168.168.129 – 192.168.168.134 and the
address of subnet mask that is utilised here 255.255.255.248.
A VLAN is developed in order to connect the devices of IoT in order to enable the
devices to be allocated with the address of IP automatically from the pool of DHCP.
A subnet is developed for the networks that have the need to connect the devices
those are mobile with network of the organization. For the network that is wireless various
addresses of IP is utilised and configured so that admittance of the servers are limited for the
devices those are connected with the point of access those are wireless. The address of IP
10.10.10.0/24 is allocated as a subnet of the server and for it the allocable range of the
address of IP is 10.10.10.1 – 10.10.10.254 and the address of subnet mask that is utilised here
is 255.255.255.0.
Router Configuration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
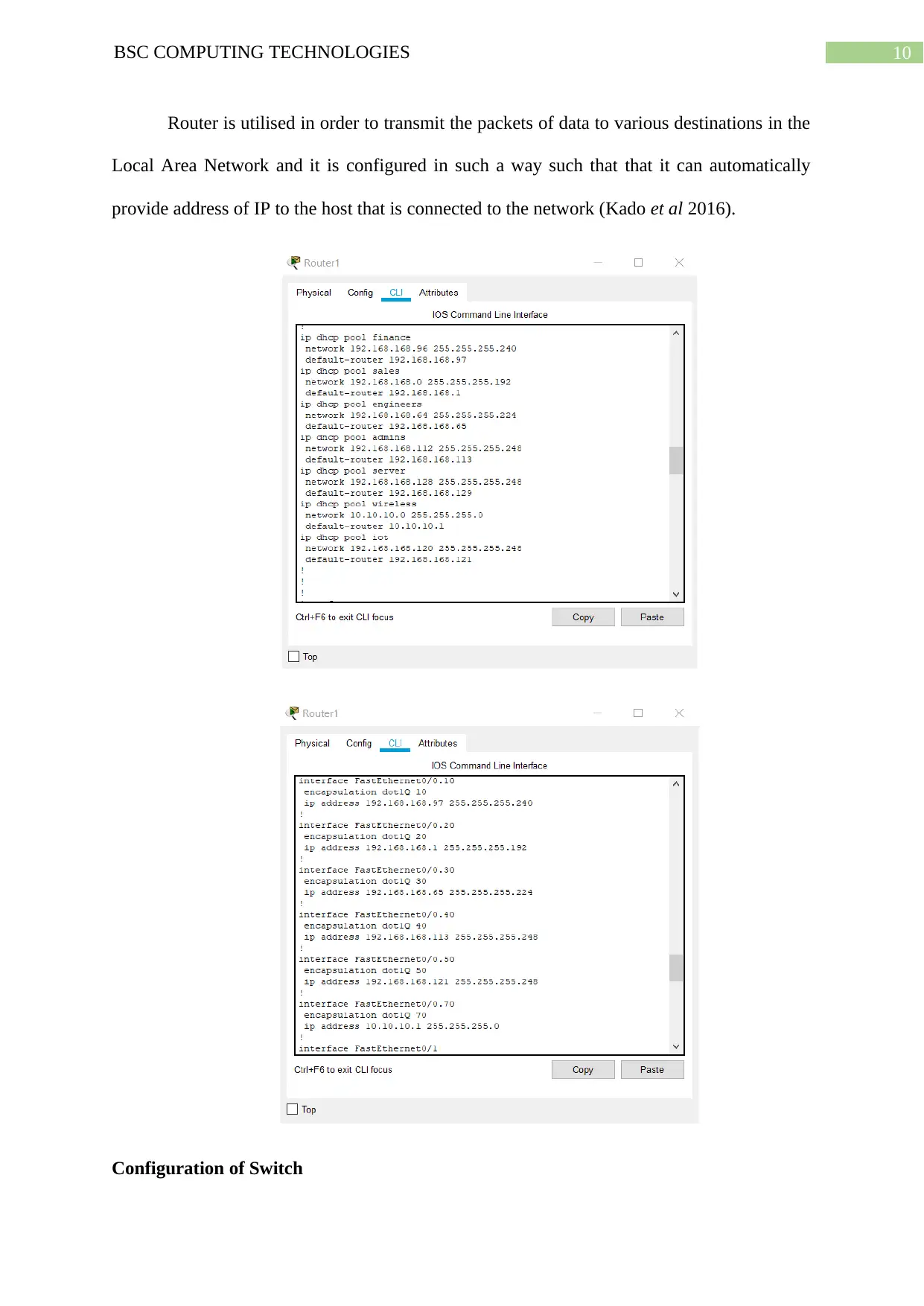
10BSC COMPUTING TECHNOLOGIES
Router is utilised in order to transmit the packets of data to various destinations in the
Local Area Network and it is configured in such a way such that that it can automatically
provide address of IP to the host that is connected to the network (Kado et al 2016).
Configuration of Switch
Router is utilised in order to transmit the packets of data to various destinations in the
Local Area Network and it is configured in such a way such that that it can automatically
provide address of IP to the host that is connected to the network (Kado et al 2016).
Configuration of Switch

11BSC COMPUTING TECHNOLOGIES
The network of the company is designed in order to install the multilayer switch as a
device of layer 3 and execute the features as the device of the root such that it can offer
admittance to the devices those are at the level of access. The router is connected to the port
of fast Ethernet and it is configured as the mode trunk of the switch port such that the
information of the VLAN can be easily shared between the various devices (Ueda et al 2016).
Every department of the company are allowed admittance for the allocated VLAN such that it
gets allocated with the address of IP for the department.
The network of the company is designed in order to install the multilayer switch as a
device of layer 3 and execute the features as the device of the root such that it can offer
admittance to the devices those are at the level of access. The router is connected to the port
of fast Ethernet and it is configured as the mode trunk of the switch port such that the
information of the VLAN can be easily shared between the various devices (Ueda et al 2016).
Every department of the company are allowed admittance for the allocated VLAN such that it
gets allocated with the address of IP for the department.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




