Network Design and Troubleshooting Project: alm.co.uk Network Design
VerifiedAdded on 2022/10/01
|28
|2662
|88
Project
AI Summary
This project report details the design and implementation of a network for alm.co.uk, addressing the need for a scalable, reliable, and secure infrastructure. The project utilizes a collapsed hierarchical network topology, incorporating Layer 2 switches, a router, and various network types (LAN, MAN, WAN) to connect four departments and a wireless network. The report includes detailed configurations for DMZ, routers, and switches, along with subnetting, VLAN setup, DHCP configuration, and access control lists. The project uses Packet Tracer for network design and testing, focusing on optimizing performance and security. The document provides a comprehensive overview of network design principles, configuration, and troubleshooting techniques, demonstrating the practical application of networking concepts.

Running head: NETWORK DESIGN AND TROUBLESHOOTING
Network design and troubleshooting
Name of the Student
Name of the University
Author Note
Network design and troubleshooting
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK DESIGN AND TROUBLESHOOTING
Table of Contents
Introduction......................................................................................................................................2
Table 1: Department details and the access rules............................................................................2
DMZ configuration..........................................................................................................................4
CLI for multilayer switches...........................................................................................................10
CLI for router.................................................................................................................................11
CLI for switch................................................................................................................................14
Configuration Table for subnet......................................................................................................14
Network configuration...................................................................................................................15
Configuration for switch................................................................................................................18
Conclusion.....................................................................................................................................25
Bibliography..................................................................................................................................26
NETWORK DESIGN AND TROUBLESHOOTING
Table of Contents
Introduction......................................................................................................................................2
Table 1: Department details and the access rules............................................................................2
DMZ configuration..........................................................................................................................4
CLI for multilayer switches...........................................................................................................10
CLI for router.................................................................................................................................11
CLI for switch................................................................................................................................14
Configuration Table for subnet......................................................................................................14
Network configuration...................................................................................................................15
Configuration for switch................................................................................................................18
Conclusion.....................................................................................................................................25
Bibliography..................................................................................................................................26

2
NETWORK DESIGN AND TROUBLESHOOTING
Introduction
Network engineer is a person that focuses entirely on determining the network
performance. As a network engineer it is the responsibility to implement the requested design so
that it can ensure better performance. The main focus of ITT directors is on determining that
proper scalability, availability is being provided towards the customers. The network
infrastructure is being implemented and designed within the organization with the help of private
IP address 192.168.168.0/24 within LAN. The main concern is too ensuring proper security
within the system so that it can provide better support. On the other hand the wireless network
IP address is 10.11.12.0/24. The network of alm.co.uk is being designed with the use of four
servers, web, email, common file server, dns and all the servers that is being shared between all
the common users. In order to understand the distribution of workstation table 1 is being
described in the later part of the report.
Table 1: Department details and the access rules
Dept. Devices Access Rules
1 48 Computers one printer Users cannot access any other department
2 18 Computers one printer Users cannot access any other department
3 11 Computers one printer Users cannot access any other department
4 68 Computers one printer Users cannot access any other department
NETWORK DESIGN AND TROUBLESHOOTING
Introduction
Network engineer is a person that focuses entirely on determining the network
performance. As a network engineer it is the responsibility to implement the requested design so
that it can ensure better performance. The main focus of ITT directors is on determining that
proper scalability, availability is being provided towards the customers. The network
infrastructure is being implemented and designed within the organization with the help of private
IP address 192.168.168.0/24 within LAN. The main concern is too ensuring proper security
within the system so that it can provide better support. On the other hand the wireless network
IP address is 10.11.12.0/24. The network of alm.co.uk is being designed with the use of four
servers, web, email, common file server, dns and all the servers that is being shared between all
the common users. In order to understand the distribution of workstation table 1 is being
described in the later part of the report.
Table 1: Department details and the access rules
Dept. Devices Access Rules
1 48 Computers one printer Users cannot access any other department
2 18 Computers one printer Users cannot access any other department
3 11 Computers one printer Users cannot access any other department
4 68 Computers one printer Users cannot access any other department
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK DESIGN AND TROUBLESHOOTING
After analyzing the above case study it can be stated that there is a need to perform
preliminary investigation so that it becomes easy to understand the performance of the current
network design. The network design is being carried out for the purpose of designing and testing
the functionality of the network. For analysis purpose packet tracer is being used. In order to
create a small network for the alm.co.uk the hierarchical network topology was being developed
that is known as the collapsed model. The main reason behind using this model is that it helps in
maintaining proper scalability, reliability, security, maintainability, redundancy and also ensures
that high performance is being obtained with the use of this topology. The main components of
using network design is to determine whether the developed network offers enhanced
performance, better reliability and ensures that the cost has been reduced. In order to identify the
ill defined problem network illustration design is being used.
For the purpose of creating the network design of the above mentioned scenario 7
switches of layer two models was inserted into local area network. The network contains 2960
switch 2p layer 2 switches and 3560 multilayer switch 24 p, 2811 series router.
NETWORK DESIGN AND TROUBLESHOOTING
After analyzing the above case study it can be stated that there is a need to perform
preliminary investigation so that it becomes easy to understand the performance of the current
network design. The network design is being carried out for the purpose of designing and testing
the functionality of the network. For analysis purpose packet tracer is being used. In order to
create a small network for the alm.co.uk the hierarchical network topology was being developed
that is known as the collapsed model. The main reason behind using this model is that it helps in
maintaining proper scalability, reliability, security, maintainability, redundancy and also ensures
that high performance is being obtained with the use of this topology. The main components of
using network design is to determine whether the developed network offers enhanced
performance, better reliability and ensures that the cost has been reduced. In order to identify the
ill defined problem network illustration design is being used.
For the purpose of creating the network design of the above mentioned scenario 7
switches of layer two models was inserted into local area network. The network contains 2960
switch 2p layer 2 switches and 3560 multilayer switch 24 p, 2811 series router.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK DESIGN AND TROUBLESHOOTING
Apart from all these the network design is being implemented with three different types
of networks. This includes LAN, MAN and WAN. Local area network is being used for the
purpose of controlling the transmission that takes place within the single organization. This
ensures that proper communication is being performed between the digital devices and similar
devices. Moreover the transmission range of a LAN can get from 1 bit to 1 million bits per
second. LAN transmission is being developed in such a way within the network so that it can
provide better reliability with high speed access over the data. According to different researches
and IEE it has been observed that the local area network is differentiated from different types of
data network and used mainly for the purpose of providing better and enhanced communication
within small area. Small area can be warehouse or a building that relies entirely on physical
communication channel. The main reason behind relying on physical communication channel is
that it offers reliably low error rate. Beside this several authors stated that LAN has been
emerged as a result of two different technologies that are combined together.
DMZ configuration
!===DMZ Config
!=== Router config // this is used for configuring the router
!===
!===
!Vlan 10 = 192.168.168.0 255.255.255.128 0.0.0.127 // this is used for explaining that the
subnets that comes under this ip address.
!Vlan 20 = 192.168.168.128 255.255.255.192 0.0.0.63
NETWORK DESIGN AND TROUBLESHOOTING
Apart from all these the network design is being implemented with three different types
of networks. This includes LAN, MAN and WAN. Local area network is being used for the
purpose of controlling the transmission that takes place within the single organization. This
ensures that proper communication is being performed between the digital devices and similar
devices. Moreover the transmission range of a LAN can get from 1 bit to 1 million bits per
second. LAN transmission is being developed in such a way within the network so that it can
provide better reliability with high speed access over the data. According to different researches
and IEE it has been observed that the local area network is differentiated from different types of
data network and used mainly for the purpose of providing better and enhanced communication
within small area. Small area can be warehouse or a building that relies entirely on physical
communication channel. The main reason behind relying on physical communication channel is
that it offers reliably low error rate. Beside this several authors stated that LAN has been
emerged as a result of two different technologies that are combined together.
DMZ configuration
!===DMZ Config
!=== Router config // this is used for configuring the router
!===
!===
!Vlan 10 = 192.168.168.0 255.255.255.128 0.0.0.127 // this is used for explaining that the
subnets that comes under this ip address.
!Vlan 20 = 192.168.168.128 255.255.255.192 0.0.0.63

5
NETWORK DESIGN AND TROUBLESHOOTING
!Vlan 30 = 192.168.168.192 255.255.255.224 0.0.0.31
!Vlan 40 = 192.168.168.224 255.255.255.240 0.0.0.15
!Vlan 50 = 10.11.12.0 255.255.255.0 0.0.0.255
en
conf t
!
no access-list 110 // this is used for removing the firewall configuration that was blocked by this
component
no access-list 120
no access-list 130
no access-list 140
no access-list 150
no access-list 160
!
!
!vlan10
NETWORK DESIGN AND TROUBLESHOOTING
!Vlan 30 = 192.168.168.192 255.255.255.224 0.0.0.31
!Vlan 40 = 192.168.168.224 255.255.255.240 0.0.0.15
!Vlan 50 = 10.11.12.0 255.255.255.0 0.0.0.255
en
conf t
!
no access-list 110 // this is used for removing the firewall configuration that was blocked by this
component
no access-list 120
no access-list 130
no access-list 140
no access-list 150
no access-list 160
!
!
!vlan10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK DESIGN AND TROUBLESHOOTING
access-list 110 deny ip 192.168.168.0 0.0.0.127 192.168.168.128 0.0.0.63 // this is the access
list for the given ip address. These ensures that proper permit or deny is provided towards the
protocol suit.
access-list 110 deny ip 192.168.168.0 0.0.0.127 192.168.168.192 0.0.0.31
access-list 110 deny ip 192.168.168.0 0.0.0.127 192.168.168.224 0.0.0.15
access-list 110 deny ip 192.168.168.0 0.0.0.127 10.11.12.0 0.0.0.255
access-list 110 permit ip any any
!
!vlan 20
access-list 120 deny ip 192.168.168.128 0.0.0.63 192.168.168.0 0.0.0.127
access-list 120 deny ip 192.168.168.128 0.0.0.63 192.168.168.192 0.0.0.31
access-list 120 deny ip 192.168.168.128 0.0.0.63 192.168.168.224 0.0.0.15
access-list 120 deny ip 192.168.168.128 0.0.0.63 10.11.12.0 0.0.0.255
access-list 120 permit ip any any
!
!vlan 30
access-list 130 deny ip 192.168.168.192 0.0.0.31 192.168.168.0 0.0.0.127
access-list 130 deny ip 192.168.168.192 0.0.0.31 192.168.168.128 0.0.0.63
NETWORK DESIGN AND TROUBLESHOOTING
access-list 110 deny ip 192.168.168.0 0.0.0.127 192.168.168.128 0.0.0.63 // this is the access
list for the given ip address. These ensures that proper permit or deny is provided towards the
protocol suit.
access-list 110 deny ip 192.168.168.0 0.0.0.127 192.168.168.192 0.0.0.31
access-list 110 deny ip 192.168.168.0 0.0.0.127 192.168.168.224 0.0.0.15
access-list 110 deny ip 192.168.168.0 0.0.0.127 10.11.12.0 0.0.0.255
access-list 110 permit ip any any
!
!vlan 20
access-list 120 deny ip 192.168.168.128 0.0.0.63 192.168.168.0 0.0.0.127
access-list 120 deny ip 192.168.168.128 0.0.0.63 192.168.168.192 0.0.0.31
access-list 120 deny ip 192.168.168.128 0.0.0.63 192.168.168.224 0.0.0.15
access-list 120 deny ip 192.168.168.128 0.0.0.63 10.11.12.0 0.0.0.255
access-list 120 permit ip any any
!
!vlan 30
access-list 130 deny ip 192.168.168.192 0.0.0.31 192.168.168.0 0.0.0.127
access-list 130 deny ip 192.168.168.192 0.0.0.31 192.168.168.128 0.0.0.63
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK DESIGN AND TROUBLESHOOTING
access-list 130 deny ip 192.168.168.192 0.0.0.31 192.168.168.224 0.0.0.15
access-list 130 deny ip 192.168.168.192 0.0.0.31 10.11.12.0 0.0.0.255
access-list 130 permit ip any any
!
!vlan 40
access-list 140 deny ip 192.168.168.224 0.0.0.15 192.168.168.0 0.0.0.127
access-list 140 deny ip 192.168.168.224 0.0.0.15 192.168.168.128 0.0.0.63
access-list 140 deny ip 192.168.168.224 0.0.0.15 192.168.168.192 0.0.0.31
access-list 140 deny ip 192.168.168.224 0.0.0.15 10.11.12.0 0.0.0.255
access-list 140 permit ip any any
!
!vlan 50
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.0 0.0.0.127
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.128 0.0.0.63
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.192 0.0.0.31
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.224 0.0.0.15
access-list 150 permit ip any any
NETWORK DESIGN AND TROUBLESHOOTING
access-list 130 deny ip 192.168.168.192 0.0.0.31 192.168.168.224 0.0.0.15
access-list 130 deny ip 192.168.168.192 0.0.0.31 10.11.12.0 0.0.0.255
access-list 130 permit ip any any
!
!vlan 40
access-list 140 deny ip 192.168.168.224 0.0.0.15 192.168.168.0 0.0.0.127
access-list 140 deny ip 192.168.168.224 0.0.0.15 192.168.168.128 0.0.0.63
access-list 140 deny ip 192.168.168.224 0.0.0.15 192.168.168.192 0.0.0.31
access-list 140 deny ip 192.168.168.224 0.0.0.15 10.11.12.0 0.0.0.255
access-list 140 permit ip any any
!
!vlan 50
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.0 0.0.0.127
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.128 0.0.0.63
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.192 0.0.0.31
access-list 150 deny ip 10.11.12.0 0.0.0.255 192.168.168.224 0.0.0.15
access-list 150 permit ip any any

8
NETWORK DESIGN AND TROUBLESHOOTING
!
!servers
!incoming
access-list 160 permit udp any any eq domain
!outcoming // address the outcome for the network and ip address
access-list 160 permit udp any eq domain any
!
access-list 160 permit udp any any eq bootps
access-list 160 permit udp any any eq bootpc
access-list 160 permit tcp any any eq smtp
access-list 160 permit tcp any any eq pop3
access-list 160 permit tcp any any eq ftp
access-list 160 permit tcp any any eq 20
access-list 160 permit tcp any any established
!
interface F0/0.10
ip access-group 110 in
NETWORK DESIGN AND TROUBLESHOOTING
!
!servers
!incoming
access-list 160 permit udp any any eq domain
!outcoming // address the outcome for the network and ip address
access-list 160 permit udp any eq domain any
!
access-list 160 permit udp any any eq bootps
access-list 160 permit udp any any eq bootpc
access-list 160 permit tcp any any eq smtp
access-list 160 permit tcp any any eq pop3
access-list 160 permit tcp any any eq ftp
access-list 160 permit tcp any any eq 20
access-list 160 permit tcp any any established
!
interface F0/0.10
ip access-group 110 in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK DESIGN AND TROUBLESHOOTING
no shut
!
interface F0/0.20
ip access-group 120 in
no shut // no shutdown command does not have any impact if the port is having static access port
!
interface F0/0.30
ip access-group 130 in
no shut
!
interface F0/0.40
ip access-group 140 in
no shut
!
interface F0/0.50
ip access-group 150 in
no shut
NETWORK DESIGN AND TROUBLESHOOTING
no shut
!
interface F0/0.20
ip access-group 120 in
no shut // no shutdown command does not have any impact if the port is having static access port
!
interface F0/0.30
ip access-group 130 in
no shut
!
interface F0/0.40
ip access-group 140 in
no shut
!
interface F0/0.50
ip access-group 150 in
no shut
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK DESIGN AND TROUBLESHOOTING
!
interface FastEthernet 0/1
ip access-group 160 in
!
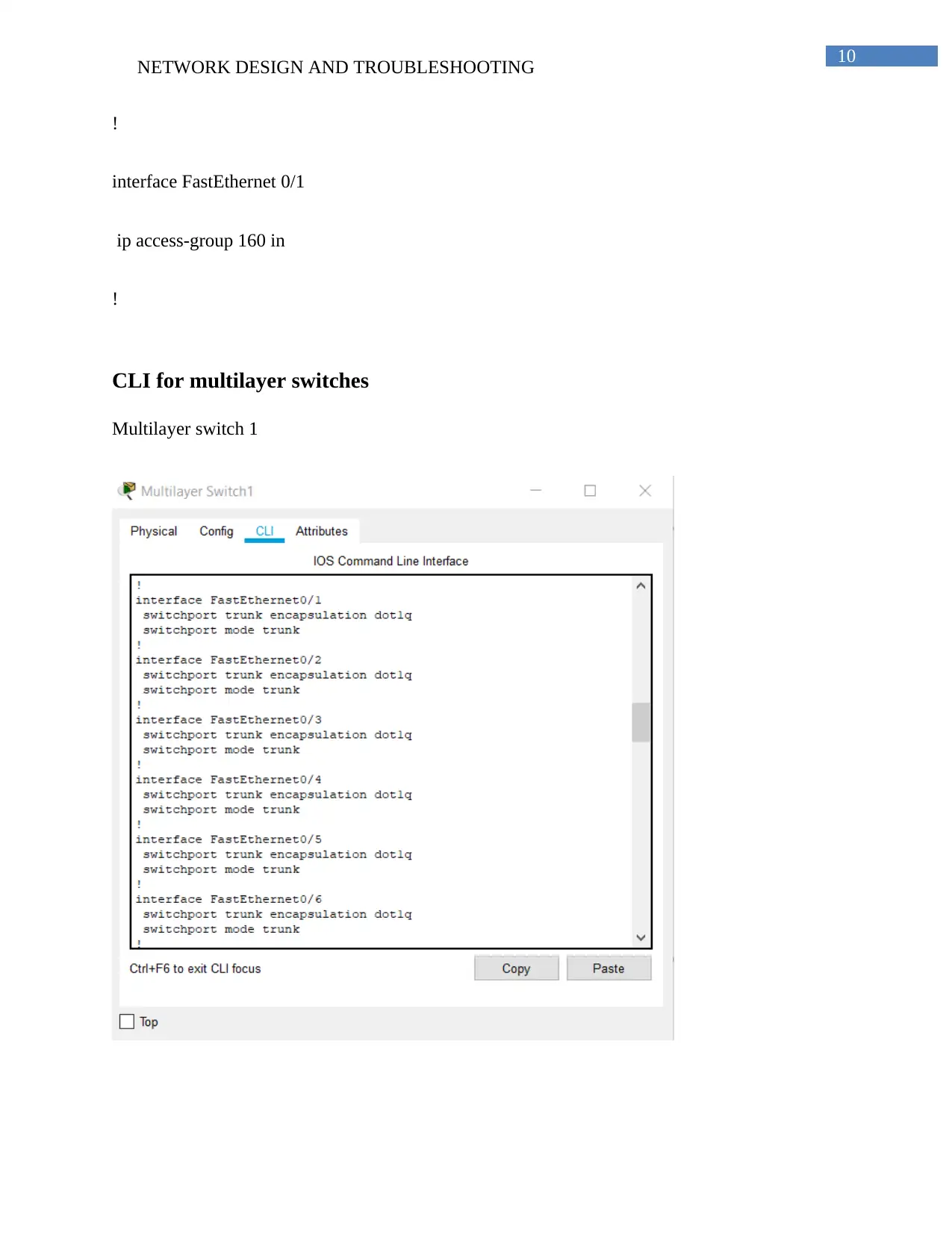
CLI for multilayer switches
Multilayer switch 1
NETWORK DESIGN AND TROUBLESHOOTING
!
interface FastEthernet 0/1
ip access-group 160 in
!
CLI for multilayer switches
Multilayer switch 1
11
NETWORK DESIGN AND TROUBLESHOOTING
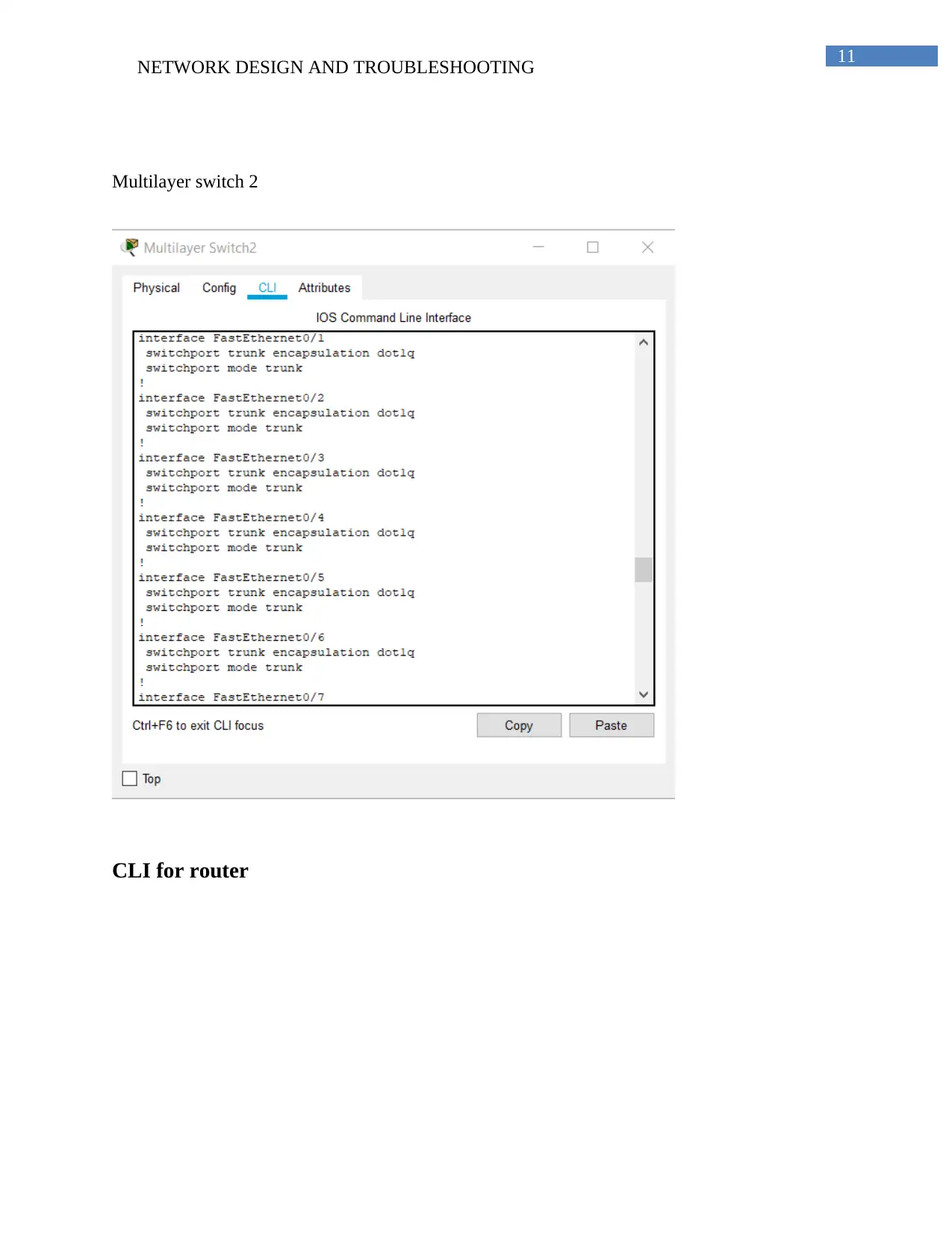
Multilayer switch 2
CLI for router
NETWORK DESIGN AND TROUBLESHOOTING
Multilayer switch 2
CLI for router
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



