Network Design and Directory Structure of Talon Textile Fasteners
VerifiedAdded on 2023/04/19
|16
|2928
|115
Project
AI Summary
This report details the network design for Talon Textile Fasteners (TTF), aiming to upgrade its infrastructure to meet expanding business demands. It begins with a requirements summary and proposes an upgraded network design, including IP address specifications. The report then explains the components of the Active Directory, such as Sites, Organizational Units, and Groups, with a focus on user roles. Server layout and roles are discussed, and project-specific documents like sign-off, task lists, and test plans are provided. The report includes a maintenance plan, router and server specifications, and a comprehensive security plan. The security plan covers defense-in-depth strategies, perimeter design, remote access, threat identification, and disaster recovery. The project also provides details on the existing network topology, stakeholder interviews, and a business plan to give context to the design. The report concludes with observations drawn from the study, offering a complete solution for TTF's network upgrade.

Running head: NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Network Design and Directory Structure of TTF
Name of the Student
Name of the University
Author Note
Network Design and Directory Structure of TTF
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Summary
The purpose of this report is to analyse the network requirements of Talon Textile Fasteners
(TTF) and suggest an upgraded network design that meets the demands of the expanding
business. The report starts by summarizing the requirements in a requirements specification
table and proceeds to suggest the upgraded network design while also mentioning the IP
address related specifications. Then the components of the active directory are explained by
talking about the Sites, Organizational Units and Groups where added focus is given on role
of users with respect to the organizational units and domains. Thereafter the server layout and
role are discussed and various project specific documents like sign-off, task list and test plan
are given. Then the report lists the maintenance plan and discusses about router and server
specifications afterwards. The report then ends with conclusions drawn from the study.
Summary
The purpose of this report is to analyse the network requirements of Talon Textile Fasteners
(TTF) and suggest an upgraded network design that meets the demands of the expanding
business. The report starts by summarizing the requirements in a requirements specification
table and proceeds to suggest the upgraded network design while also mentioning the IP
address related specifications. Then the components of the active directory are explained by
talking about the Sites, Organizational Units and Groups where added focus is given on role
of users with respect to the organizational units and domains. Thereafter the server layout and
role are discussed and various project specific documents like sign-off, task list and test plan
are given. Then the report lists the maintenance plan and discusses about router and server
specifications afterwards. The report then ends with conclusions drawn from the study.

2NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Table of Contents
Introduction................................................................................................................................4
Discussion..................................................................................................................................4
Requirements Summary.........................................................................................................4
Upgraded Network Design.....................................................................................................5
Active Directory.....................................................................................................................6
Sites....................................................................................................................................6
Organizational Units..........................................................................................................6
Groups................................................................................................................................6
Server specifications..............................................................................................................7
Number and location..........................................................................................................7
Server Role.........................................................................................................................7
Approval sign-off document..............................................................................................8
Server maintenance plan............................................................................................................9
Router Specifications...........................................................................................................10
Security plan and policy.......................................................................................................11
Defence in depth..............................................................................................................11
Perimeter Design..............................................................................................................11
Remote Access.................................................................................................................12
Threat Identification.........................................................................................................12
Policies.............................................................................................................................12
Disaster Recovery................................................................................................................12
Table of Contents
Introduction................................................................................................................................4
Discussion..................................................................................................................................4
Requirements Summary.........................................................................................................4
Upgraded Network Design.....................................................................................................5
Active Directory.....................................................................................................................6
Sites....................................................................................................................................6
Organizational Units..........................................................................................................6
Groups................................................................................................................................6
Server specifications..............................................................................................................7
Number and location..........................................................................................................7
Server Role.........................................................................................................................7
Approval sign-off document..............................................................................................8
Server maintenance plan............................................................................................................9
Router Specifications...........................................................................................................10
Security plan and policy.......................................................................................................11
Defence in depth..............................................................................................................11
Perimeter Design..............................................................................................................11
Remote Access.................................................................................................................12
Threat Identification.........................................................................................................12
Policies.............................................................................................................................12
Disaster Recovery................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Conclusion................................................................................................................................13
Bibliography.............................................................................................................................14
Conclusion................................................................................................................................13
Bibliography.............................................................................................................................14
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Introduction
The report aims to analyse the requirements of Talon Textile Fasteners (TTF) so that
it can suggest the upgraded network design for the company. The study begins by listing the
requirements summary in a tabular format, following which the upgraded network design is
provided and also mentions the IP address related specifications. Thereafter the components
of the active directory are discussed namely – Sites, Organizational Units and Groups by
emphasizing role of the users. Thereafter the layout and role of the servers present in the
network are talked about in the server specifications sections. Then the various documents
regarding sign-off, server task list and the test plan are provided. After mentioning the router
specifications, the security plan of the network is given. Then the report ends with concluding
notes where observations are given based upon the report.
Discussion
Requirements Summary
Branch Servers Workstations Connections Floors
HQ 3 37 40 3
Mt Burr 2 23 25 2
Pt Pirie 0 1 1 1
Pt Adelaide 1 5 6 1
H-Burr 2
HQ-Pirie 2
HQ-Adelaide 2
Introduction
The report aims to analyse the requirements of Talon Textile Fasteners (TTF) so that
it can suggest the upgraded network design for the company. The study begins by listing the
requirements summary in a tabular format, following which the upgraded network design is
provided and also mentions the IP address related specifications. Thereafter the components
of the active directory are discussed namely – Sites, Organizational Units and Groups by
emphasizing role of the users. Thereafter the layout and role of the servers present in the
network are talked about in the server specifications sections. Then the various documents
regarding sign-off, server task list and the test plan are provided. After mentioning the router
specifications, the security plan of the network is given. Then the report ends with concluding
notes where observations are given based upon the report.
Discussion
Requirements Summary
Branch Servers Workstations Connections Floors
HQ 3 37 40 3
Mt Burr 2 23 25 2
Pt Pirie 0 1 1 1
Pt Adelaide 1 5 6 1
H-Burr 2
HQ-Pirie 2
HQ-Adelaide 2
5NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
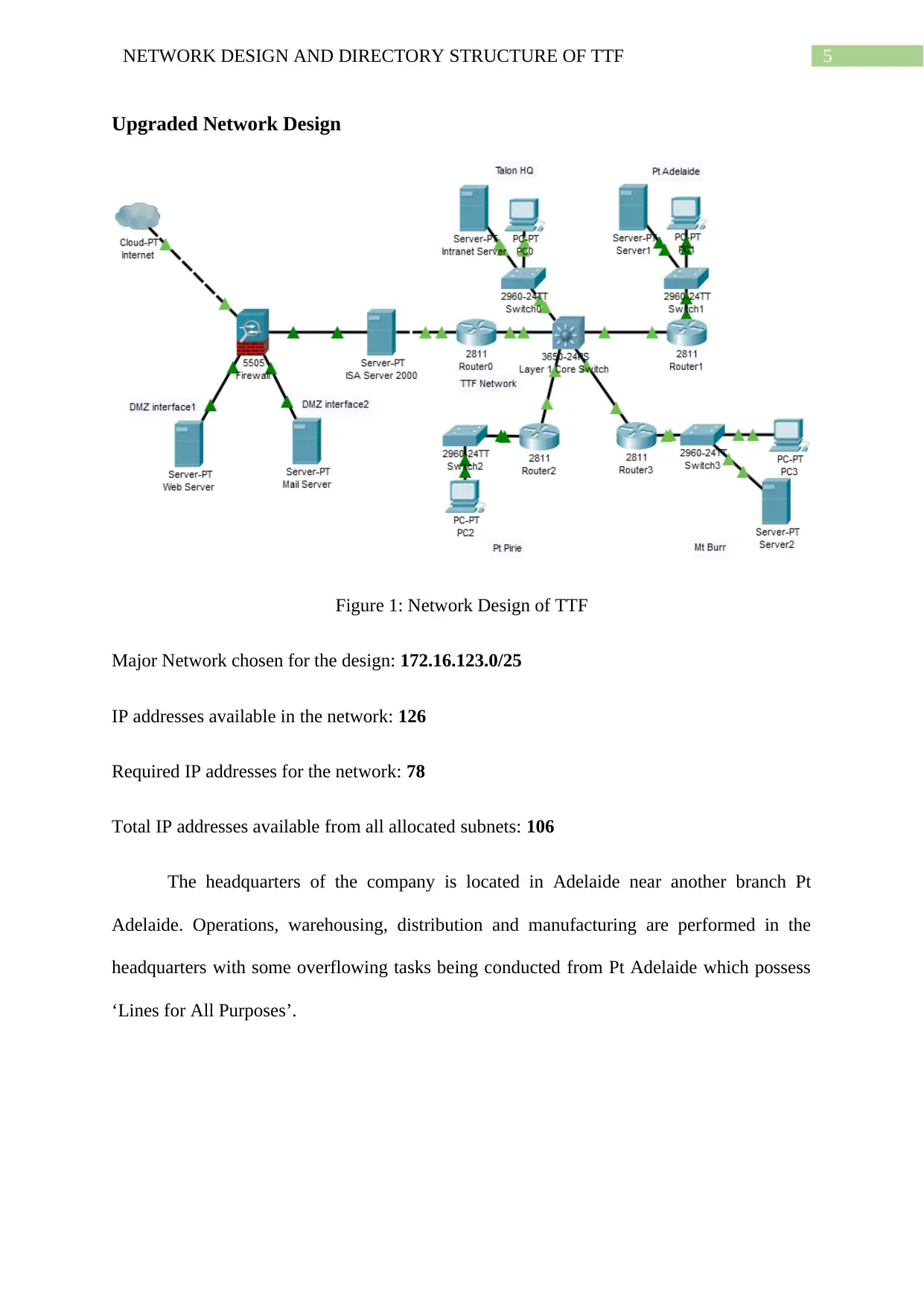
Upgraded Network Design
Figure 1: Network Design of TTF
Major Network chosen for the design: 172.16.123.0/25
IP addresses available in the network: 126
Required IP addresses for the network: 78
Total IP addresses available from all allocated subnets: 106
The headquarters of the company is located in Adelaide near another branch Pt
Adelaide. Operations, warehousing, distribution and manufacturing are performed in the
headquarters with some overflowing tasks being conducted from Pt Adelaide which possess
‘Lines for All Purposes’.
Upgraded Network Design
Figure 1: Network Design of TTF
Major Network chosen for the design: 172.16.123.0/25
IP addresses available in the network: 126
Required IP addresses for the network: 78
Total IP addresses available from all allocated subnets: 106
The headquarters of the company is located in Adelaide near another branch Pt
Adelaide. Operations, warehousing, distribution and manufacturing are performed in the
headquarters with some overflowing tasks being conducted from Pt Adelaide which possess
‘Lines for All Purposes’.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Active Directory
Sites
The headquarters of the company is located in Adelaide along with the branch of Pt
Adelaide. Other sites include branches of Mt Burr and Pt Pirie. This means, in the active
directory of TTF there exists four different domains – one for each site.
Organizational Units
The different organizational units of Talon Textile Fasteners are:
Operations
Sales
Finance
Information Technology
Out of the above organizational units, operations exist in all the branches/sites with the
headquarters and Pt Adelaide executing most of the operational tasks. This suggests that other
sites have more than one organizational unit in their domain.
Groups
The different groups in which the stakeholders should be placed are:
Data Entry Officer – Domain user
This is because, for data entry tasks one domain is enough and they do not have the
requirement to be present in multiple sites.
Manufacturing supervisor – Global administrator
Manufacturing like operations is also performed in multiple branches and hence
manufacturing supervisors will be required to visit these sites and work with the installed
systems and hence requires access for multiple domains.
Active Directory
Sites
The headquarters of the company is located in Adelaide along with the branch of Pt
Adelaide. Other sites include branches of Mt Burr and Pt Pirie. This means, in the active
directory of TTF there exists four different domains – one for each site.
Organizational Units
The different organizational units of Talon Textile Fasteners are:
Operations
Sales
Finance
Information Technology
Out of the above organizational units, operations exist in all the branches/sites with the
headquarters and Pt Adelaide executing most of the operational tasks. This suggests that other
sites have more than one organizational unit in their domain.
Groups
The different groups in which the stakeholders should be placed are:
Data Entry Officer – Domain user
This is because, for data entry tasks one domain is enough and they do not have the
requirement to be present in multiple sites.
Manufacturing supervisor – Global administrator
Manufacturing like operations is also performed in multiple branches and hence
manufacturing supervisors will be required to visit these sites and work with the installed
systems and hence requires access for multiple domains.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Sales manager – Domain user
Sales is another set of activities that do not require multiple branches, but even then,
sales managers are assigned to oversee activities in their own site and therefore only require
accesses to single domain only
Manager of operations – Domain user
Although operations are conducted in all branches, operations managers like sales
managers are asked to oversee activities of their site and so single domain access is enough.
CEO – Global user, CFO – Global user, CIO – Global user
These people belong to the CXO level and often travel across multiple sites within
and beyond the company and hence require global access.
IT Administrator – Global administrator
Since the IT administrators are responsible for maintaining the network uptime and
require access to every part of the network, they get global access.
Server specifications
Number and location
The company network has a total of 6 physical servers out of which 3 are located in
the headquarters, 2 at Mt Burr and the other one is in Pt Adelaide. The 3 servers in different
branches all perform network specific workloads.
Server Role
The main roles played by these servers is facilitating communication channels with
among the network including two-way connections between the headquarters and Pt Adelaide
so that operations, manufacturing, distribution and warehousing specific tasks can be
performed without a hitch. Out of the 3 servers in the headquarters, one is used for processing
Sales manager – Domain user
Sales is another set of activities that do not require multiple branches, but even then,
sales managers are assigned to oversee activities in their own site and therefore only require
accesses to single domain only
Manager of operations – Domain user
Although operations are conducted in all branches, operations managers like sales
managers are asked to oversee activities of their site and so single domain access is enough.
CEO – Global user, CFO – Global user, CIO – Global user
These people belong to the CXO level and often travel across multiple sites within
and beyond the company and hence require global access.
IT Administrator – Global administrator
Since the IT administrators are responsible for maintaining the network uptime and
require access to every part of the network, they get global access.
Server specifications
Number and location
The company network has a total of 6 physical servers out of which 3 are located in
the headquarters, 2 at Mt Burr and the other one is in Pt Adelaide. The 3 servers in different
branches all perform network specific workloads.
Server Role
The main roles played by these servers is facilitating communication channels with
among the network including two-way connections between the headquarters and Pt Adelaide
so that operations, manufacturing, distribution and warehousing specific tasks can be
performed without a hitch. Out of the 3 servers in the headquarters, one is used for processing
8NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
transfer of mails and messages. Another server is used for storing information while the other
one is being used to ensure security.
Approval sign-off document
Name and Title of Approver Decision Reason for Rejection Date
Project Manager Approved
Rejected
02.04.20
19
Business Analyst Approved
Rejected
02.04.20
19
Lead Architect Approved
Rejected
02.04.20
19
Sponsor Approved
Rejected
02.04.20
19
Approved
Rejected
Figure 2: Approval sign-off document
# Date Activities/Tasks/Items Priority Status
1 01.04.2019 Operations High In Progress
2 01.04.2019 Manufacturing Medium Delayed
3 01.04.2019 Sales High Not yet begun
4 01.04.2019 Operations Medium Delayed
5 01.04.2019 Finance Medium In Progress
transfer of mails and messages. Another server is used for storing information while the other
one is being used to ensure security.
Approval sign-off document
Name and Title of Approver Decision Reason for Rejection Date
Project Manager Approved
Rejected
02.04.20
19
Business Analyst Approved
Rejected
02.04.20
19
Lead Architect Approved
Rejected
02.04.20
19
Sponsor Approved
Rejected
02.04.20
19
Approved
Rejected
Figure 2: Approval sign-off document
# Date Activities/Tasks/Items Priority Status
1 01.04.2019 Operations High In Progress
2 01.04.2019 Manufacturing Medium Delayed
3 01.04.2019 Sales High Not yet begun
4 01.04.2019 Operations Medium Delayed
5 01.04.2019 Finance Medium In Progress
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
6 01.04.2019 Manufacturing Medium Not yet begun
Figure 3: Server Task list
ID TC_R1
Description Ensure all data is consistent among all
servers
Precondition Target server is configured, turned on and
an existing server added the server
Action Server which added the new server ensures
data between the servers are similar
Expected Result Target server has similar data which is
consistent with all other servers
Failure Condition 1. Target server does not have all data
2. Data in Target server is not the same
Figure 4: Server Test Plan
Server maintenance plan
The server maintenance plan generally requires several steps, including:
checking of log files of servers
assessing of hard disks
examination of folder permissions
monitoring applications for reading network temperature
ensuring acceptable redundancy in systems
6 01.04.2019 Manufacturing Medium Not yet begun
Figure 3: Server Task list
ID TC_R1
Description Ensure all data is consistent among all
servers
Precondition Target server is configured, turned on and
an existing server added the server
Action Server which added the new server ensures
data between the servers are similar
Expected Result Target server has similar data which is
consistent with all other servers
Failure Condition 1. Target server does not have all data
2. Data in Target server is not the same
Figure 4: Server Test Plan
Server maintenance plan
The server maintenance plan generally requires several steps, including:
checking of log files of servers
assessing of hard disks
examination of folder permissions
monitoring applications for reading network temperature
ensuring acceptable redundancy in systems
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
examination of security features
installing patches for security software
reading of server logs for checking security specific alerts or even evidence of
attempts for hacking
updating security applications of all computers in the network
installing critical updates like service packs, bug fixes and other software updates
Router Specifications
Router chosen: Cisco 2800 series
Specifications:
2 Integrated 10/100 Fast Ethernet ports. > 4 High-Speed WAN Interface Card Slots
AC-IP max in-line power distribution: 160W
DC Input Voltage: 24 to 60 VDC
Optional integrated inline power (PoE): Yes
A total of 4 of these routers are chosen, one for each site. The network routed among
each other and switches are used to distribute the network from router to individual devices
like servers and clients.
Cables chosen to connect the routers is Fast Ethernet while Gigabit Ethernet cables
are used for connecting the individual devices to the switches.
For creating the different subnets for each of the four routers, Classless Inter Domain
Routing (CIDR) based subnet calculation is performed.
Third party applications like Wireshark can be used to detect and monitor the traffic
of the network in real time as also keep the sessions recorded.
examination of security features
installing patches for security software
reading of server logs for checking security specific alerts or even evidence of
attempts for hacking
updating security applications of all computers in the network
installing critical updates like service packs, bug fixes and other software updates
Router Specifications
Router chosen: Cisco 2800 series
Specifications:
2 Integrated 10/100 Fast Ethernet ports. > 4 High-Speed WAN Interface Card Slots
AC-IP max in-line power distribution: 160W
DC Input Voltage: 24 to 60 VDC
Optional integrated inline power (PoE): Yes
A total of 4 of these routers are chosen, one for each site. The network routed among
each other and switches are used to distribute the network from router to individual devices
like servers and clients.
Cables chosen to connect the routers is Fast Ethernet while Gigabit Ethernet cables
are used for connecting the individual devices to the switches.
For creating the different subnets for each of the four routers, Classless Inter Domain
Routing (CIDR) based subnet calculation is performed.
Third party applications like Wireshark can be used to detect and monitor the traffic
of the network in real time as also keep the sessions recorded.

11NETWORK DESIGN AND DIRECTORY STRUCTURE OF TTF
Security plan and policy
Defence in depth
The security of the network is ensured by hardware and software level security
solutions installed in the servers that form the perimeter network of the company. The server
performs the role of a firewall and ensures authentication, proactive threat detection and real-
time monitoring services. To do this the industry leading SOPHOS security solution is being
used. SOPHOS is mostly known for their security solutions for businesses and enterprises.
Next the SBS server comes equipped with ISA server 2000 which isolates the intranet from
the servers which require public network access and provides additional security features. On
top of this, every client computer and server present in the network have antivirus and
antimalware security applications installed which provide similar security features like the
firewalls in addition to detection and removal mechanisms to prevent security risks from
human errors. They act as a second layer of security if by any means, the firewall gets
compromised. While the firewall device secures the network at the physical and data link
layers the software based firewalls and other security applications secure the network in other
five layers of OSI reference model. The individual security applications also help when
removable drives are being connected to the client computers. It is here that most of the
attacks to client computers in workplaces occur.
Perimeter Design
The perimeter network of the company involves securing the web and mail servers
from threats over the internet. However these devices require public access from outside the
company network for business purposes. Therefore further security is needed to secure the
internal network of the company. This is ensured by the SBS server which is equipped with
ISA Server 2000 – a solution designed for windows 2000 platform for management,
networking and authentication purposes. The web server and the mail server is connected to
Security plan and policy
Defence in depth
The security of the network is ensured by hardware and software level security
solutions installed in the servers that form the perimeter network of the company. The server
performs the role of a firewall and ensures authentication, proactive threat detection and real-
time monitoring services. To do this the industry leading SOPHOS security solution is being
used. SOPHOS is mostly known for their security solutions for businesses and enterprises.
Next the SBS server comes equipped with ISA server 2000 which isolates the intranet from
the servers which require public network access and provides additional security features. On
top of this, every client computer and server present in the network have antivirus and
antimalware security applications installed which provide similar security features like the
firewalls in addition to detection and removal mechanisms to prevent security risks from
human errors. They act as a second layer of security if by any means, the firewall gets
compromised. While the firewall device secures the network at the physical and data link
layers the software based firewalls and other security applications secure the network in other
five layers of OSI reference model. The individual security applications also help when
removable drives are being connected to the client computers. It is here that most of the
attacks to client computers in workplaces occur.
Perimeter Design
The perimeter network of the company involves securing the web and mail servers
from threats over the internet. However these devices require public access from outside the
company network for business purposes. Therefore further security is needed to secure the
internal network of the company. This is ensured by the SBS server which is equipped with
ISA Server 2000 – a solution designed for windows 2000 platform for management,
networking and authentication purposes. The web server and the mail server is connected to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





