Comprehensive Network Design and Inter VLAN Routing Report for ALM
VerifiedAdded on 2022/09/16
|23
|4256
|22
Report
AI Summary
This report presents a comprehensive network design for the company alm.co.uk, focusing on network segmentation and security to mitigate cyber threats. It outlines the requirements, solution, and detailed network design using Cisco Packet Tracer 6.2. The report covers IP addressing, subnetting, VLAN implementation, and access control lists to restrict inter-departmental access. It also discusses the DMZ server setup and the use of DHCP for automated IP addressing. The report includes validation and testing procedures to ensure the network meets the specified requirements. The network is designed based on a hierarchical model consisting of core, distribution, and access layers. The report also includes detailed subnetting information and diagrams to illustrate the network's architecture and functionality. The implementation of VLANs and access restrictions using ACL commands is clearly explained, along with the rationale for the design choices. The report concludes with a discussion of the automated IP addressing protocol utilizing the DHCP protocol, emphasizing the importance of network security and performance.

Running head: NETWORK DESIGN AND INTER VLAN ROUTING
Network Design and Inter Vlan Routing
Name of the Student:
Name of the University:
Author Note:
Network Design and Inter Vlan Routing
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK DESIGN AND INTER VLAN ROUTING
Executive Summary
According to the recent findings, the segmentation of the specific networks as well as the
internal security related to that of the network segments have been playing a major role
within the prevention of networks from facing compromise by the related threat from that of
the hackers as well as the other attacks prevailing within the cyber security. This report
specifically puts forward for the company al.co.uk the methods of such segmentation that
have been created as well as considered to be the exact specific measures to ensure the
security of threats prevalently existing within the networks. . The report provides the design
of the network that has been illustrated as well as configured within the Cisco Packet Tracer
6.2 after which the network design along with that of the architecture gets explained in detail.
The IP addressing, the classifications of the subnet as well as the addressing related to that of
the IP has been briefly explained. After which, the report specifically explains the usage of
the access control list. In addition to this, the restrictions related to that of the ACL
commands has been shown as to how the specific departments have been restricted from
access within this network. Lastly, the report provisions with the related test as well as of the
validations to keep a check running upon the proposed network to match footsteps with the
specific requirements of the AML. The reports ends with the discussion of the automated IP
addressing protocol utilizing the DHCP protocol.
NETWORK DESIGN AND INTER VLAN ROUTING
Executive Summary
According to the recent findings, the segmentation of the specific networks as well as the
internal security related to that of the network segments have been playing a major role
within the prevention of networks from facing compromise by the related threat from that of
the hackers as well as the other attacks prevailing within the cyber security. This report
specifically puts forward for the company al.co.uk the methods of such segmentation that
have been created as well as considered to be the exact specific measures to ensure the
security of threats prevalently existing within the networks. . The report provides the design
of the network that has been illustrated as well as configured within the Cisco Packet Tracer
6.2 after which the network design along with that of the architecture gets explained in detail.
The IP addressing, the classifications of the subnet as well as the addressing related to that of
the IP has been briefly explained. After which, the report specifically explains the usage of
the access control list. In addition to this, the restrictions related to that of the ACL
commands has been shown as to how the specific departments have been restricted from
access within this network. Lastly, the report provisions with the related test as well as of the
validations to keep a check running upon the proposed network to match footsteps with the
specific requirements of the AML. The reports ends with the discussion of the automated IP
addressing protocol utilizing the DHCP protocol.

2
NETWORK DESIGN AND INTER VLAN ROUTING
Table of Contents
Introduction................................................................................................................................3
Requirements..............................................................................................................................3
Solution......................................................................................................................................5
Network Design.....................................................................................................................5
Department servers.................................................................................................................6
DMZ server............................................................................................................................7
Subnetting of this network.........................................................................................................7
Implementation of VLAN....................................................................................................10
Access restrictions of VLAN utilizing Access Control list.................................................12
Validation and testing..........................................................................................................17
Protocols related connecting devices...................................................................................18
Conclusion................................................................................................................................19
References................................................................................................................................20
NETWORK DESIGN AND INTER VLAN ROUTING
Table of Contents
Introduction................................................................................................................................3
Requirements..............................................................................................................................3
Solution......................................................................................................................................5
Network Design.....................................................................................................................5
Department servers.................................................................................................................6
DMZ server............................................................................................................................7
Subnetting of this network.........................................................................................................7
Implementation of VLAN....................................................................................................10
Access restrictions of VLAN utilizing Access Control list.................................................12
Validation and testing..........................................................................................................17
Protocols related connecting devices...................................................................................18
Conclusion................................................................................................................................19
References................................................................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK DESIGN AND INTER VLAN ROUTING
Introduction
This report specifically puts forward the various important aspects related to that of the
segmentation along with the internal security existing within the networks having played a
major role within the acts of preventing the various networks from getting wholly
compromised towards the threat placed by the hackers and the other existing security attacks
related to that of cyber security (Batalla et al., 2016). This particular report initiates itself
with the summary of all the necessary requirements related to that of the ALM network
within which the specific number of devices for each of the segment, the access related to all
of the restrictions as well as the kinds of the servers that have been installed along with the
specific subnets as classified. In addition to this, this particular report provides with the
network diagram that has been diagrammatically drawn as well as been configured with the
Cisco Packet Tracker 6.2 followed by the explanation in brief detail (Kafle, Fukushima and
Harai, 2016). After which, the implementation of the various types of VLAN has been placed
forward, keeping into consideration the various methods related to the implementation of the
VLAN as well as the how the related routing works. Then after, the report specifically places
a discussion about the access control list and the related commands for the prohibition of the
departments from accessing each other. Along with this, the report also puts forward the tests
along with that of the validations to keep a check upon the network, which has been proposed
to meet the specific requirements of the AML. Followed by the discussion of the IP
addressing related to that of the protocol attached with the notes providing with the
conclusion.
Requirements
Referring to the small network existing within the company alm.co.uk consists of the
inclusion related to that of different configurations supported by the LAN for the existing
NETWORK DESIGN AND INTER VLAN ROUTING
Introduction
This report specifically puts forward the various important aspects related to that of the
segmentation along with the internal security existing within the networks having played a
major role within the acts of preventing the various networks from getting wholly
compromised towards the threat placed by the hackers and the other existing security attacks
related to that of cyber security (Batalla et al., 2016). This particular report initiates itself
with the summary of all the necessary requirements related to that of the ALM network
within which the specific number of devices for each of the segment, the access related to all
of the restrictions as well as the kinds of the servers that have been installed along with the
specific subnets as classified. In addition to this, this particular report provides with the
network diagram that has been diagrammatically drawn as well as been configured with the
Cisco Packet Tracker 6.2 followed by the explanation in brief detail (Kafle, Fukushima and
Harai, 2016). After which, the implementation of the various types of VLAN has been placed
forward, keeping into consideration the various methods related to the implementation of the
VLAN as well as the how the related routing works. Then after, the report specifically places
a discussion about the access control list and the related commands for the prohibition of the
departments from accessing each other. Along with this, the report also puts forward the tests
along with that of the validations to keep a check upon the network, which has been proposed
to meet the specific requirements of the AML. Followed by the discussion of the IP
addressing related to that of the protocol attached with the notes providing with the
conclusion.
Requirements
Referring to the small network existing within the company alm.co.uk consists of the
inclusion related to that of different configurations supported by the LAN for the existing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK DESIGN AND INTER VLAN ROUTING
four different departments having the inclusion of the configurations related to the LAN
specified for the servers as well as the wirelessly working network (Sarkar, Basavaraju and
Puttamadappa, 2016).
The configuration of the servers consist of the inclusion of existing individual servers
related to that of the DNS, email, the web as well as the purposes related to that of the
sharing.
Each individual servers needs to have the specific access to the individual
workstations belonging to every user within all of the four departments (Wang, Wu and Ni,
2016). The classification of the subnet related to that of the ALM network needs to have a
count per workstations along with that of the printers as well as the servers belonging to each
user of every single department.
ALM’s respective network needs to have the inclusion of a wireless network to
provide with the support of the various necessary smartphones as well as the laptop having
the belonging to all of the users in each department.
Particularly, this network needs to be segmented so as to provide the network with
that of the access as well as from all the devices belonging to the four departments taking into
consideration all of the existing LAN configurations that can be very well controlled as well
as managed with the rule related to that of the specified access (Kobo, Abu-Mahfouz and
Hancke, 2017). However, each of the department shall be blocked from the majorly accessing
systems belonging to the other three existing departments utilizing the restrictions to that of
the security that have been implemented internally.
The specific number of workstations as well as the printers that share the existence
between four of the existing departments can be supplied with 48 personal computers along
with that of 1 printer for department 1, 18 of the workstations along with that of the 1 printer
NETWORK DESIGN AND INTER VLAN ROUTING
four different departments having the inclusion of the configurations related to the LAN
specified for the servers as well as the wirelessly working network (Sarkar, Basavaraju and
Puttamadappa, 2016).
The configuration of the servers consist of the inclusion of existing individual servers
related to that of the DNS, email, the web as well as the purposes related to that of the
sharing.
Each individual servers needs to have the specific access to the individual
workstations belonging to every user within all of the four departments (Wang, Wu and Ni,
2016). The classification of the subnet related to that of the ALM network needs to have a
count per workstations along with that of the printers as well as the servers belonging to each
user of every single department.
ALM’s respective network needs to have the inclusion of a wireless network to
provide with the support of the various necessary smartphones as well as the laptop having
the belonging to all of the users in each department.
Particularly, this network needs to be segmented so as to provide the network with
that of the access as well as from all the devices belonging to the four departments taking into
consideration all of the existing LAN configurations that can be very well controlled as well
as managed with the rule related to that of the specified access (Kobo, Abu-Mahfouz and
Hancke, 2017). However, each of the department shall be blocked from the majorly accessing
systems belonging to the other three existing departments utilizing the restrictions to that of
the security that have been implemented internally.
The specific number of workstations as well as the printers that share the existence
between four of the existing departments can be supplied with 48 personal computers along
with that of 1 printer for department 1, 18 of the workstations along with that of the 1 printer

5
NETWORK DESIGN AND INTER VLAN ROUTING
for department 2, 11 workstations as well as 1 printer for department 3 and lastly, 68
workstations with that of 1 printer specifically for department 4 (Liu, 2015).
Solution
Network Design
This figure particularly highlights the basic design of the small network belonging to
the alm.co.uk that can turn out to be. This network diagram clearly represents that this
specific network has been built mainly based upon three of the layer related to that of the
hierarchical model of networking consisting of the involvement of a specific core,
distribution as well as the layers of access that follows the approach of top down. Present at
the top of the main router belonging to that of the company consists of the core layer related
to this specific layer (Park et al., 2017). This specific router is where the variety of the
configurations such as the likes of subnet classification, DHCP, the inter VLAN related
routing for the entire network has been built upon. Followed by this, the network, which is
routed is provided as a supply to the multilayer switch constituting of the specific layer of
distribution. The switch belonging to that of the multilayer has been entrusted upon with the
responsibility for the distribution of the access related to that of the network for the specific
switches of the various existing departments along with that of the LAN configurations
NETWORK DESIGN AND INTER VLAN ROUTING
for department 2, 11 workstations as well as 1 printer for department 3 and lastly, 68
workstations with that of 1 printer specifically for department 4 (Liu, 2015).
Solution
Network Design
This figure particularly highlights the basic design of the small network belonging to
the alm.co.uk that can turn out to be. This network diagram clearly represents that this
specific network has been built mainly based upon three of the layer related to that of the
hierarchical model of networking consisting of the involvement of a specific core,
distribution as well as the layers of access that follows the approach of top down. Present at
the top of the main router belonging to that of the company consists of the core layer related
to this specific layer (Park et al., 2017). This specific router is where the variety of the
configurations such as the likes of subnet classification, DHCP, the inter VLAN related
routing for the entire network has been built upon. Followed by this, the network, which is
routed is provided as a supply to the multilayer switch constituting of the specific layer of
distribution. The switch belonging to that of the multilayer has been entrusted upon with the
responsibility for the distribution of the access related to that of the network for the specific
switches of the various existing departments along with that of the LAN configurations
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK DESIGN AND INTER VLAN ROUTING
consisting of the inclusion of all the servers as well as of the wireless network (Le et al.,
2016). This specific connection belong to the specified switches have been provided with the
respective and particular VLAN’s. the switches belonging to the lower layers carry the
responsibility of connecting the devices existing individually constitutes of the layer of access
hence, completing the three layer of the specific networking model. There is the existence of
six such layers of switches, four among which provides the service to four of the different
departments belonging to that of the al.co.uk on the other hand, the remaining two switches
together form the configuration of the LAN belonging to that of the servers along with that of
the wirelessly working network (Kobo, Abu-Mahfouz and Hancke, 2017). There is the
existence of four installed servers within this specific network. These specifically refer to the
likes of a web server, the mail server, the specific DNS server along with that of the server
responsible for the file sharing. While, this specific network has been segmented based upon
the implementation of the VLAN’s for each of the LAN configuration, the access to as well
as from the various of the existing departments has been managed with the help of the
specific access control consisting of the list of extended commands (Dadheech, Choudhary
and Bhatia, 2018).
Department servers
Referring to each of the VLAN that was assigned with a specific private server with the
inclusion of a static IP due to the various reasons related to that of security along with that of
the network performance, as a reason the data storage of the specific departments will not be
NETWORK DESIGN AND INTER VLAN ROUTING
consisting of the inclusion of all the servers as well as of the wireless network (Le et al.,
2016). This specific connection belong to the specified switches have been provided with the
respective and particular VLAN’s. the switches belonging to the lower layers carry the
responsibility of connecting the devices existing individually constitutes of the layer of access
hence, completing the three layer of the specific networking model. There is the existence of
six such layers of switches, four among which provides the service to four of the different
departments belonging to that of the al.co.uk on the other hand, the remaining two switches
together form the configuration of the LAN belonging to that of the servers along with that of
the wirelessly working network (Kobo, Abu-Mahfouz and Hancke, 2017). There is the
existence of four installed servers within this specific network. These specifically refer to the
likes of a web server, the mail server, the specific DNS server along with that of the server
responsible for the file sharing. While, this specific network has been segmented based upon
the implementation of the VLAN’s for each of the LAN configuration, the access to as well
as from the various of the existing departments has been managed with the help of the
specific access control consisting of the list of extended commands (Dadheech, Choudhary
and Bhatia, 2018).
Department servers
Referring to each of the VLAN that was assigned with a specific private server with the
inclusion of a static IP due to the various reasons related to that of security along with that of
the network performance, as a reason the data storage of the specific departments will not be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
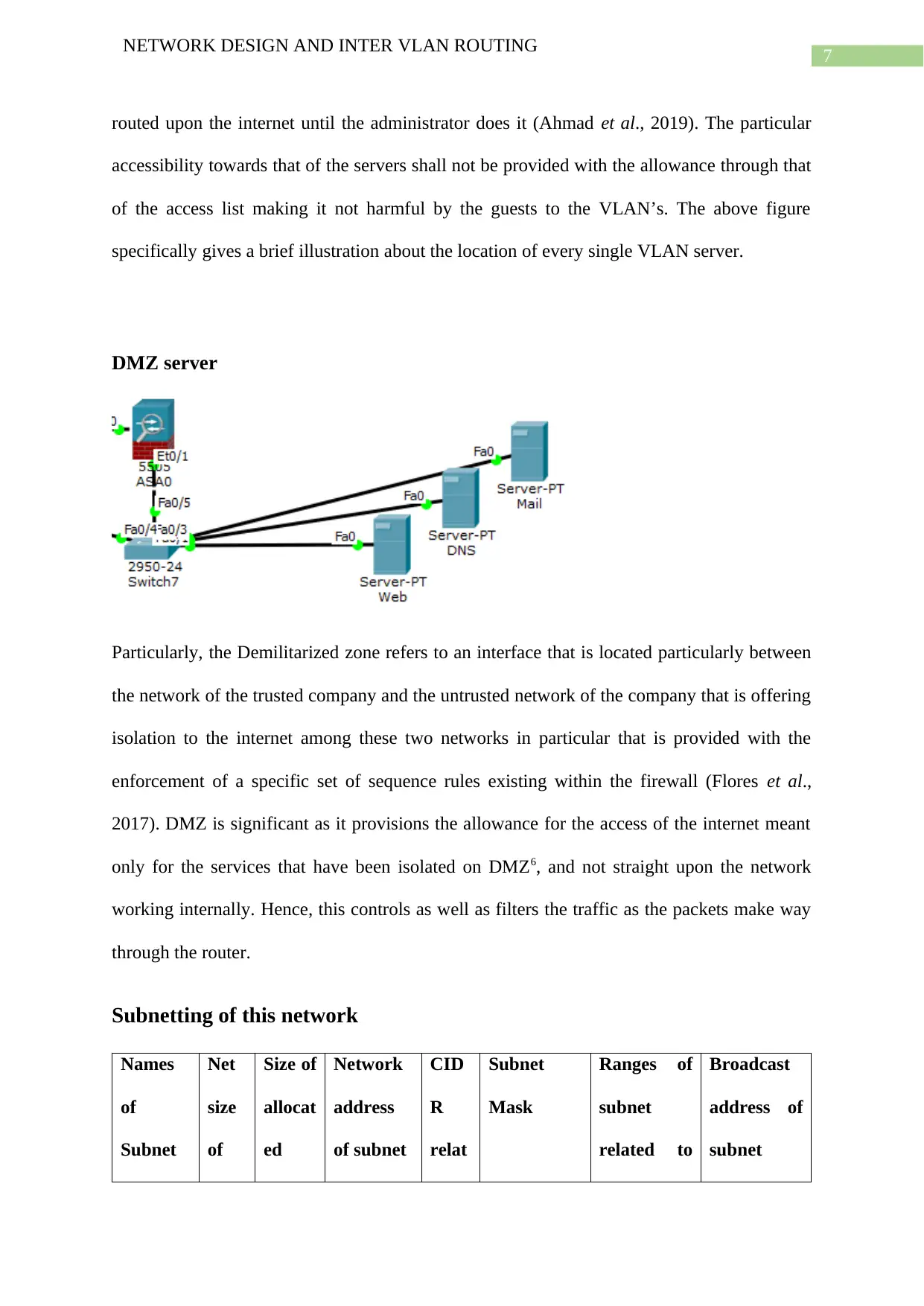
7
NETWORK DESIGN AND INTER VLAN ROUTING
routed upon the internet until the administrator does it (Ahmad et al., 2019). The particular
accessibility towards that of the servers shall not be provided with the allowance through that
of the access list making it not harmful by the guests to the VLAN’s. The above figure
specifically gives a brief illustration about the location of every single VLAN server.
DMZ server
Particularly, the Demilitarized zone refers to an interface that is located particularly between
the network of the trusted company and the untrusted network of the company that is offering
isolation to the internet among these two networks in particular that is provided with the
enforcement of a specific set of sequence rules existing within the firewall (Flores et al.,
2017). DMZ is significant as it provisions the allowance for the access of the internet meant
only for the services that have been isolated on DMZ6, and not straight upon the network
working internally. Hence, this controls as well as filters the traffic as the packets make way
through the router.
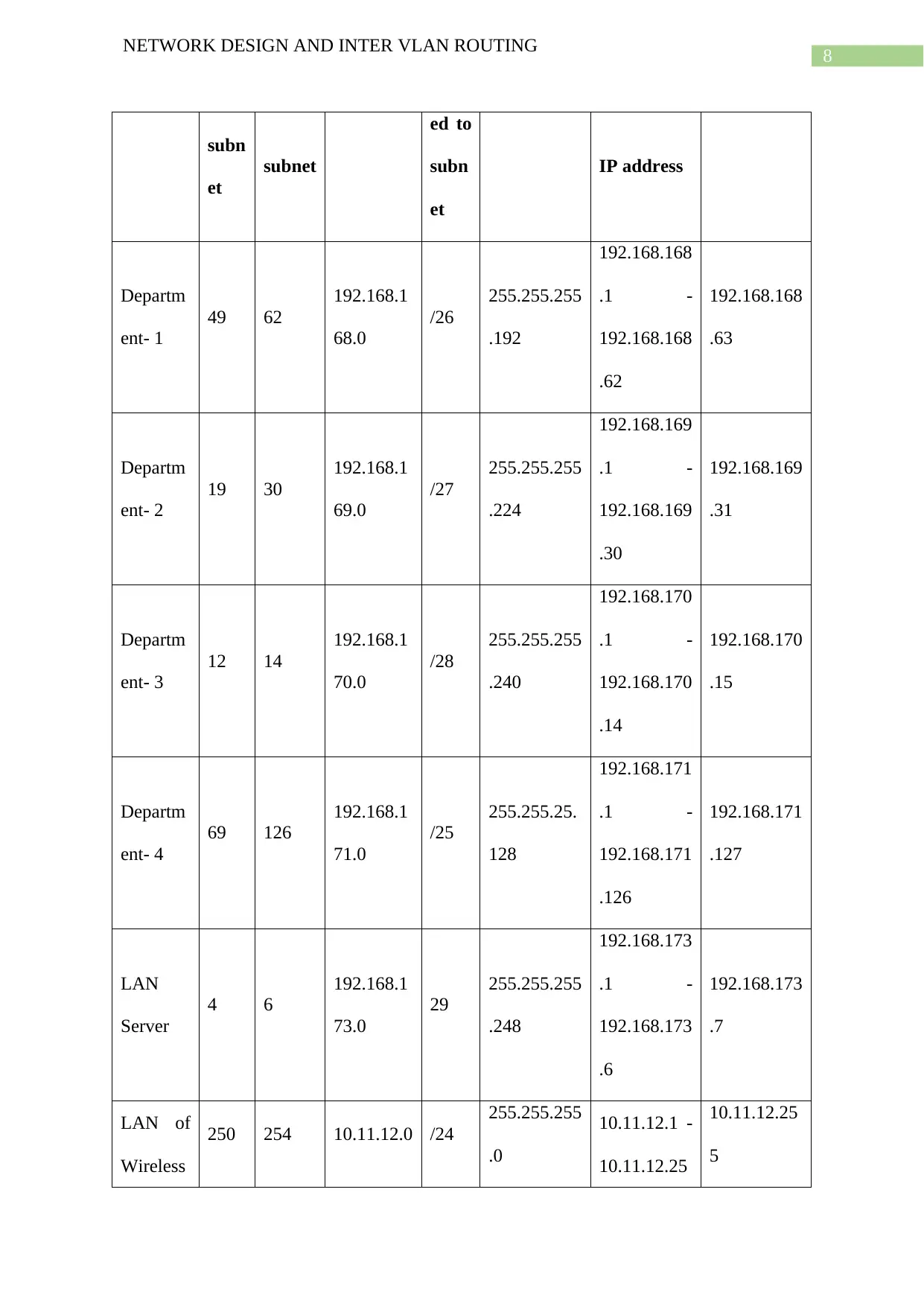
Subnetting of this network
Names
of
Subnet
Net
size
of
Size of
allocat
ed
Network
address
of subnet
CID
R
relat
Subnet
Mask
Ranges of
subnet
related to
Broadcast
address of
subnet
NETWORK DESIGN AND INTER VLAN ROUTING
routed upon the internet until the administrator does it (Ahmad et al., 2019). The particular
accessibility towards that of the servers shall not be provided with the allowance through that
of the access list making it not harmful by the guests to the VLAN’s. The above figure
specifically gives a brief illustration about the location of every single VLAN server.
DMZ server
Particularly, the Demilitarized zone refers to an interface that is located particularly between
the network of the trusted company and the untrusted network of the company that is offering
isolation to the internet among these two networks in particular that is provided with the
enforcement of a specific set of sequence rules existing within the firewall (Flores et al.,
2017). DMZ is significant as it provisions the allowance for the access of the internet meant
only for the services that have been isolated on DMZ6, and not straight upon the network
working internally. Hence, this controls as well as filters the traffic as the packets make way
through the router.
Subnetting of this network
Names
of
Subnet
Net
size
of
Size of
allocat
ed
Network
address
of subnet
CID
R
relat
Subnet
Mask
Ranges of
subnet
related to
Broadcast
address of
subnet
8
NETWORK DESIGN AND INTER VLAN ROUTING
subn
et
subnet
ed to
subn
et
IP address
Departm
ent- 1
49 62
192.168.1
68.0
/26
255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Departm
ent- 2
19 30
192.168.1
69.0
/27
255.255.255
.224
192.168.169
.1 -
192.168.169
.30
192.168.169
.31
Departm
ent- 3
12 14
192.168.1
70.0
/28
255.255.255
.240
192.168.170
.1 -
192.168.170
.14
192.168.170
.15
Departm
ent- 4
69 126
192.168.1
71.0
/25
255.255.25.
128
192.168.171
.1 -
192.168.171
.126
192.168.171
.127
LAN
Server
4 6
192.168.1
73.0
29
255.255.255
.248
192.168.173
.1 -
192.168.173
.6
192.168.173
.7
LAN of
Wireless
250 254 10.11.12.0 /24
255.255.255
.0
10.11.12.1 -
10.11.12.25
10.11.12.25
5
NETWORK DESIGN AND INTER VLAN ROUTING
subn
et
subnet
ed to
subn
et
IP address
Departm
ent- 1
49 62
192.168.1
68.0
/26
255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Departm
ent- 2
19 30
192.168.1
69.0
/27
255.255.255
.224
192.168.169
.1 -
192.168.169
.30
192.168.169
.31
Departm
ent- 3
12 14
192.168.1
70.0
/28
255.255.255
.240
192.168.170
.1 -
192.168.170
.14
192.168.170
.15
Departm
ent- 4
69 126
192.168.1
71.0
/25
255.255.25.
128
192.168.171
.1 -
192.168.171
.126
192.168.171
.127
LAN
Server
4 6
192.168.1
73.0
29
255.255.255
.248
192.168.173
.1 -
192.168.173
.6
192.168.173
.7
LAN of
Wireless
250 254 10.11.12.0 /24
255.255.255
.0
10.11.12.1 -
10.11.12.25
10.11.12.25
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK DESIGN AND INTER VLAN ROUTING
network 4
This table particularly provides with the presentation of the different existing subnets that
have been taken into consideration with the calculation for the six different subnets
completely based upon the private network 192.168.X.0/24. In here, the X refers to the
varying portion of this particular network for each of the existing five subnets- belonging to
four of the different departments as well as one related to that of the servers (Aziz et al.,
2017). This is all because of the routes of access that have been configured through the inter
existing VLAN routing as well as each of the segment having their own specific VLAN. Both
of the existing servers along with that of the wireless network it to be provisioned with the
wirelessly working connectivity related to the existing multiple devices belonging to all the
users present within each of the department, an entire subnet has been allocated for this
particular segment. This particular wireless network makes use of the private network
10.11.12.0/24 (Alimi and Mufutau, 2015). Hence, the subnet address related to that of the
network belonging to all the four departments evidently happen to be the 192.168.168.0
specifically for the department 1, 192.168.169.0 belonging to that of the department 2,
192.168.170.0 for Department 3 and lastly, for department 4 it is 192.168.173.0. The wireless
network has 10.11.12.0. the subnet masks related to all of these differently existing subnets
can be placed by 255.255.255.192 specifically for department 1, 255.255.255.224 for that of
department 2, 255.255.255.240 for department 3, 255.255.255.128 belonging to that of
department 4 and lastly, 255.255.255.248 for all the existing servers. On the other hand,
255.255.255.0 has been placed separately for the wirelessly working network. This
specifically refers to that fact that, the IP addressing related procedure has been utilized for
the subnetting of the ALM network, which is the CIDR or commonly referred to as the
Classless Inter Domain Routing. Usage of the CIDR has been based completely upon the
NETWORK DESIGN AND INTER VLAN ROUTING
network 4
This table particularly provides with the presentation of the different existing subnets that
have been taken into consideration with the calculation for the six different subnets
completely based upon the private network 192.168.X.0/24. In here, the X refers to the
varying portion of this particular network for each of the existing five subnets- belonging to
four of the different departments as well as one related to that of the servers (Aziz et al.,
2017). This is all because of the routes of access that have been configured through the inter
existing VLAN routing as well as each of the segment having their own specific VLAN. Both
of the existing servers along with that of the wireless network it to be provisioned with the
wirelessly working connectivity related to the existing multiple devices belonging to all the
users present within each of the department, an entire subnet has been allocated for this
particular segment. This particular wireless network makes use of the private network
10.11.12.0/24 (Alimi and Mufutau, 2015). Hence, the subnet address related to that of the
network belonging to all the four departments evidently happen to be the 192.168.168.0
specifically for the department 1, 192.168.169.0 belonging to that of the department 2,
192.168.170.0 for Department 3 and lastly, for department 4 it is 192.168.173.0. The wireless
network has 10.11.12.0. the subnet masks related to all of these differently existing subnets
can be placed by 255.255.255.192 specifically for department 1, 255.255.255.224 for that of
department 2, 255.255.255.240 for department 3, 255.255.255.128 belonging to that of
department 4 and lastly, 255.255.255.248 for all the existing servers. On the other hand,
255.255.255.0 has been placed separately for the wirelessly working network. This
specifically refers to that fact that, the IP addressing related procedure has been utilized for
the subnetting of the ALM network, which is the CIDR or commonly referred to as the
Classless Inter Domain Routing. Usage of the CIDR has been based completely upon the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK DESIGN AND INTER VLAN ROUTING
addressing that has been proved to be beneficial for the traditional classful related IP
addressing method referring to the change of the various subnet masks resulting to smaller
variations within the space of the address readily available for the subnets (Haq, Ehtesham
and Parveen, 2017). The subnetting based completely upon the CIDR can provide with a
helping hand towards the companies as a method of saving the cost of acquirement as well as
within the implementation of the network.
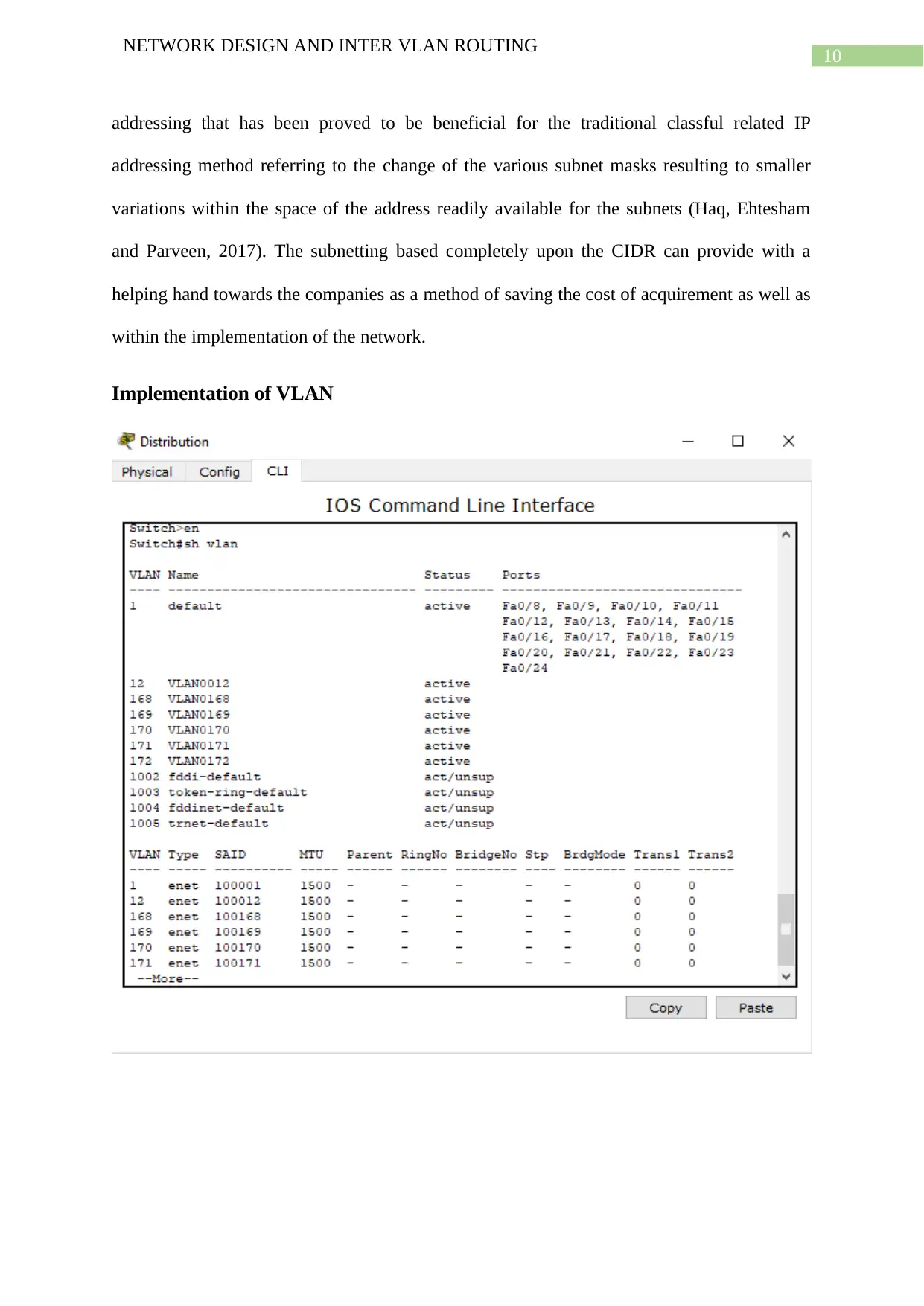
Implementation of VLAN
NETWORK DESIGN AND INTER VLAN ROUTING
addressing that has been proved to be beneficial for the traditional classful related IP
addressing method referring to the change of the various subnet masks resulting to smaller
variations within the space of the address readily available for the subnets (Haq, Ehtesham
and Parveen, 2017). The subnetting based completely upon the CIDR can provide with a
helping hand towards the companies as a method of saving the cost of acquirement as well as
within the implementation of the network.
Implementation of VLAN
11
NETWORK DESIGN AND INTER VLAN ROUTING
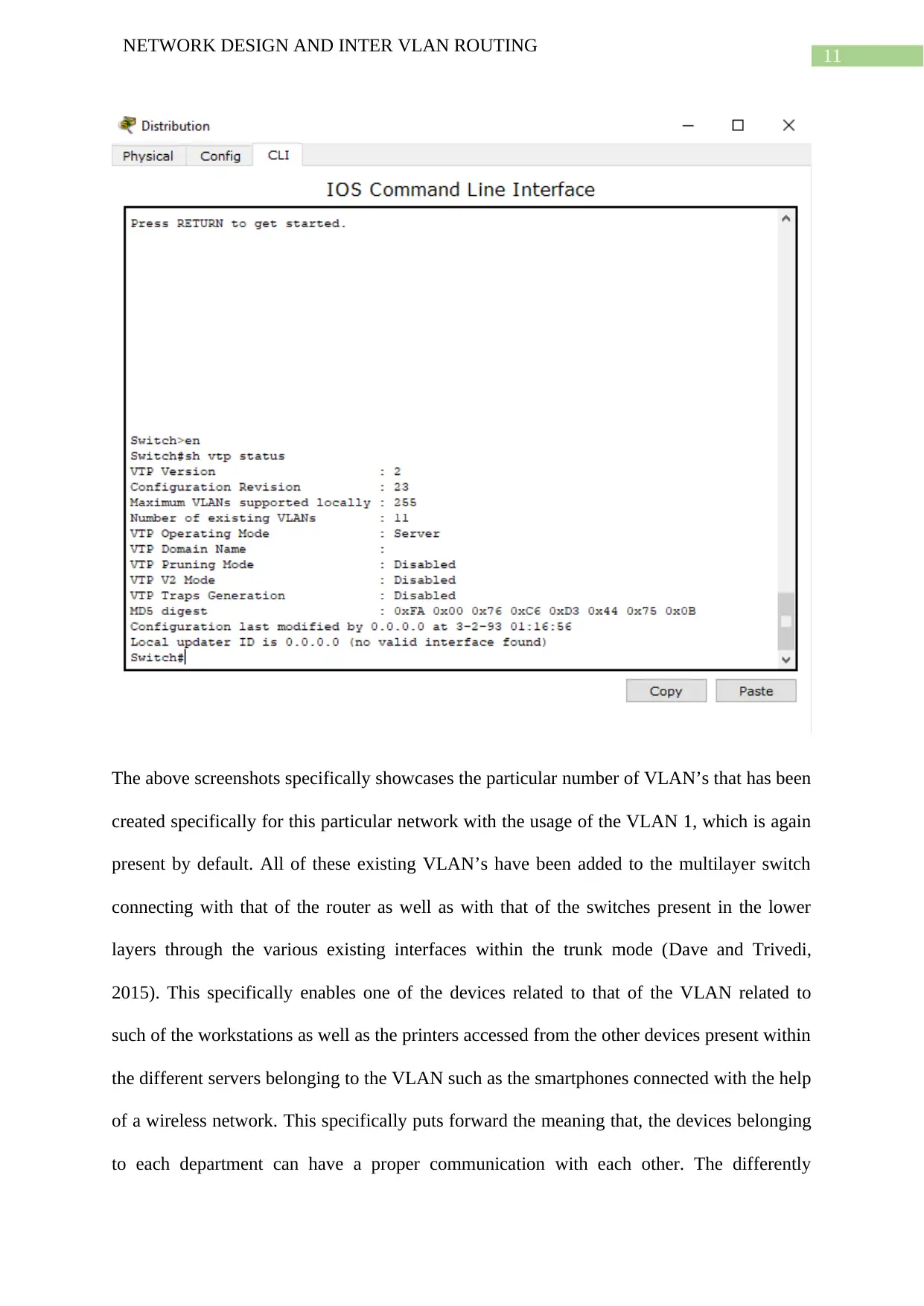
The above screenshots specifically showcases the particular number of VLAN’s that has been
created specifically for this particular network with the usage of the VLAN 1, which is again
present by default. All of these existing VLAN’s have been added to the multilayer switch
connecting with that of the router as well as with that of the switches present in the lower
layers through the various existing interfaces within the trunk mode (Dave and Trivedi,
2015). This specifically enables one of the devices related to that of the VLAN related to
such of the workstations as well as the printers accessed from the other devices present within
the different servers belonging to the VLAN such as the smartphones connected with the help
of a wireless network. This specifically puts forward the meaning that, the devices belonging
to each department can have a proper communication with each other. The differently
NETWORK DESIGN AND INTER VLAN ROUTING
The above screenshots specifically showcases the particular number of VLAN’s that has been
created specifically for this particular network with the usage of the VLAN 1, which is again
present by default. All of these existing VLAN’s have been added to the multilayer switch
connecting with that of the router as well as with that of the switches present in the lower
layers through the various existing interfaces within the trunk mode (Dave and Trivedi,
2015). This specifically enables one of the devices related to that of the VLAN related to
such of the workstations as well as the printers accessed from the other devices present within
the different servers belonging to the VLAN such as the smartphones connected with the help
of a wireless network. This specifically puts forward the meaning that, the devices belonging
to each department can have a proper communication with each other. The differently
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




