Network Design Report: LAN and Network Design for XYZ Company, 2020
VerifiedAdded on 2022/08/18
|7
|1211
|12
Report
AI Summary
This report presents a network design solution for XYZ company, focusing on Local Area Network (LAN) design. It recommends a hybrid topology for connecting different locations, ensuring security and privacy. The report discusses LAN design considerations, including the use of Cisco devices like routers, switches, and access points, along with firewalls and IDS systems. It emphasizes the importance of IP addresses (IPv4) and the need for four subnets to manage the network effectively. The design includes hardware specifications and addresses security concerns through authentication and antivirus measures. The report concludes by suggesting the implementation of a class B private address for network expansion and emphasizes the need for network experts to manage the processes. References to relevant literature are also provided.
Running Head: NETWORK DESIGN 0
Network design
Report
JANUARY 30, 2020
student name
Network design
Report
JANUARY 30, 2020
student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK DESIGN 1
Table of Contents
Introduction:...............................................................................................................................1
Local Area Network (LAN):......................................................................................................1
Network topology:.................................................................................................................1
LAN design:...........................................................................................................................1
IP addresses:...........................................................................................................................2
Conclusion:................................................................................................................................4
References..................................................................................................................................5
Table of Contents
Introduction:...............................................................................................................................1
Local Area Network (LAN):......................................................................................................1
Network topology:.................................................................................................................1
LAN design:...........................................................................................................................1
IP addresses:...........................................................................................................................2
Conclusion:................................................................................................................................4
References..................................................................................................................................5

NETWORK DESIGN 2
Introduction:
XYZ company must use a proper network to manage their different locations and systems. It
is a basic need of a company to manage its computer systems and other IT-assets using all the
things. In addition, Local Area Network (LAN) can be used for securing data and
information. In addition, there are many things to manage in a network. The firm should use
firewalls and IDS systems. Moreover, the company has managed its business from two other
locations. Thus, it is necessary to provide connectivity between all the locations with security
and privacy. This report will provide network design for the firm.
Local Area Network (LAN):
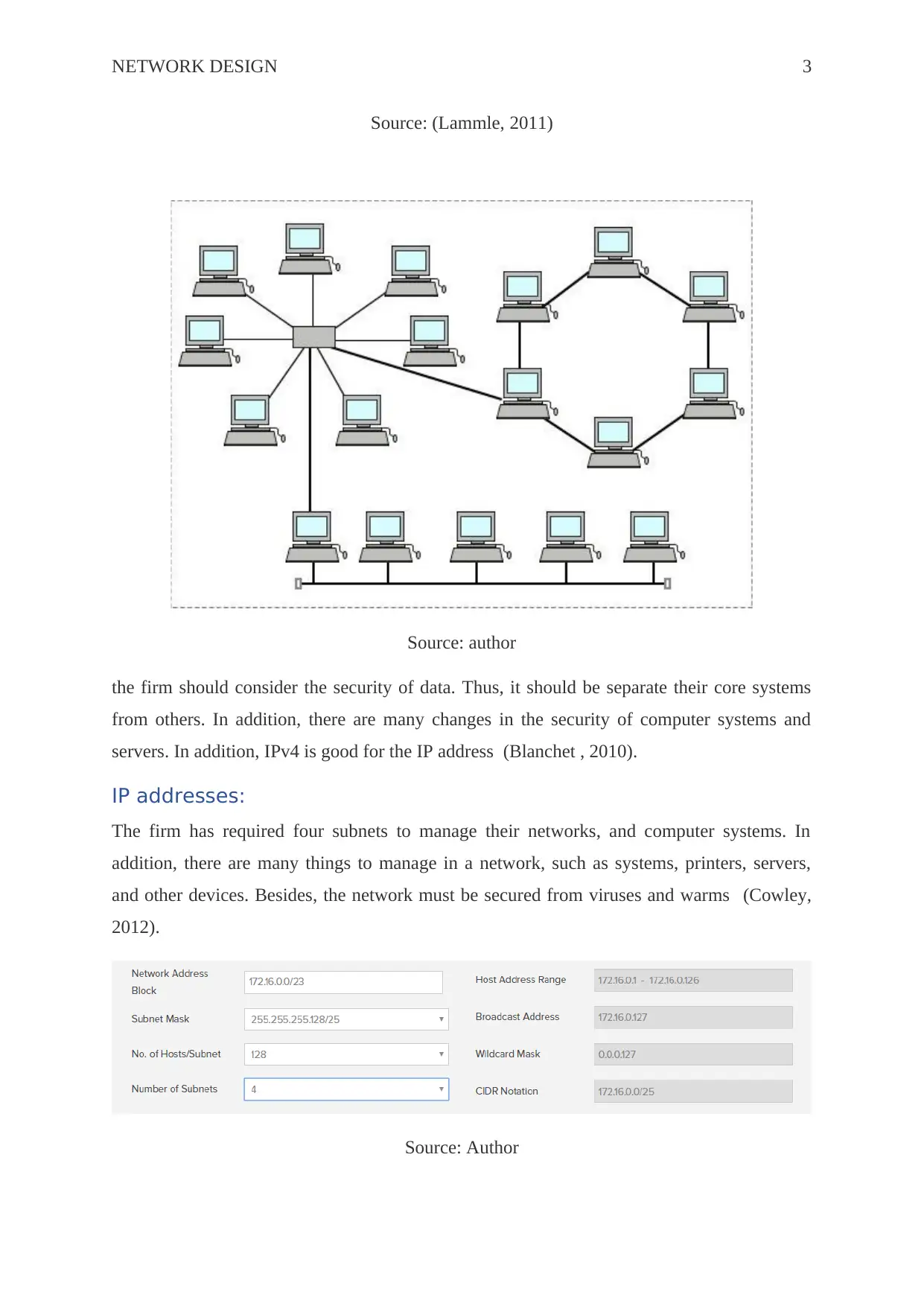
There are many types of topologies for a network to connect different internetworking
devices. In addition, hybrid topology can be used for this company. in this topology, all the
system is connected to each other. There are many topologies, such as a tree, mesh, star, and
many others. Hybrid technology is beneficial for the company because of its connectivity and
better facilities. It is a better topology because of provided fast speed and access to each
system in a network.
Network topology:
The hybrid topology will be the best topology for the company. In this topology, there are
different types of topologies are mixed, which are a tree, bus, mesh, and others. In addition,
many devices can be separated for security purposes and privacy of data and security.
Moreover, there are many things to manage in business for security purposes.
LAN design:
In addition, the computer network can be used managing all the things. A network can be
used for connecting all the devices (Tanenbaum, 2014).
Introduction:
XYZ company must use a proper network to manage their different locations and systems. It
is a basic need of a company to manage its computer systems and other IT-assets using all the
things. In addition, Local Area Network (LAN) can be used for securing data and
information. In addition, there are many things to manage in a network. The firm should use
firewalls and IDS systems. Moreover, the company has managed its business from two other
locations. Thus, it is necessary to provide connectivity between all the locations with security
and privacy. This report will provide network design for the firm.
Local Area Network (LAN):
There are many types of topologies for a network to connect different internetworking
devices. In addition, hybrid topology can be used for this company. in this topology, all the
system is connected to each other. There are many topologies, such as a tree, mesh, star, and
many others. Hybrid technology is beneficial for the company because of its connectivity and
better facilities. It is a better topology because of provided fast speed and access to each
system in a network.
Network topology:
The hybrid topology will be the best topology for the company. In this topology, there are
different types of topologies are mixed, which are a tree, bus, mesh, and others. In addition,
many devices can be separated for security purposes and privacy of data and security.
Moreover, there are many things to manage in business for security purposes.
LAN design:
In addition, the computer network can be used managing all the things. A network can be
used for connecting all the devices (Tanenbaum, 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK DESIGN 3
Source: (Lammle, 2011)
Source: author
the firm should consider the security of data. Thus, it should be separate their core systems
from others. In addition, there are many changes in the security of computer systems and
servers. In addition, IPv4 is good for the IP address (Blanchet , 2010).
IP addresses:
The firm has required four subnets to manage their networks, and computer systems. In
addition, there are many things to manage in a network, such as systems, printers, servers,
and other devices. Besides, the network must be secured from viruses and warms (Cowley,
2012).
Source: Author
Source: (Lammle, 2011)
Source: author
the firm should consider the security of data. Thus, it should be separate their core systems
from others. In addition, there are many changes in the security of computer systems and
servers. In addition, IPv4 is good for the IP address (Blanchet , 2010).
IP addresses:
The firm has required four subnets to manage their networks, and computer systems. In
addition, there are many things to manage in a network, such as systems, printers, servers,
and other devices. Besides, the network must be secured from viruses and warms (Cowley,
2012).
Source: Author
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK DESIGN 4
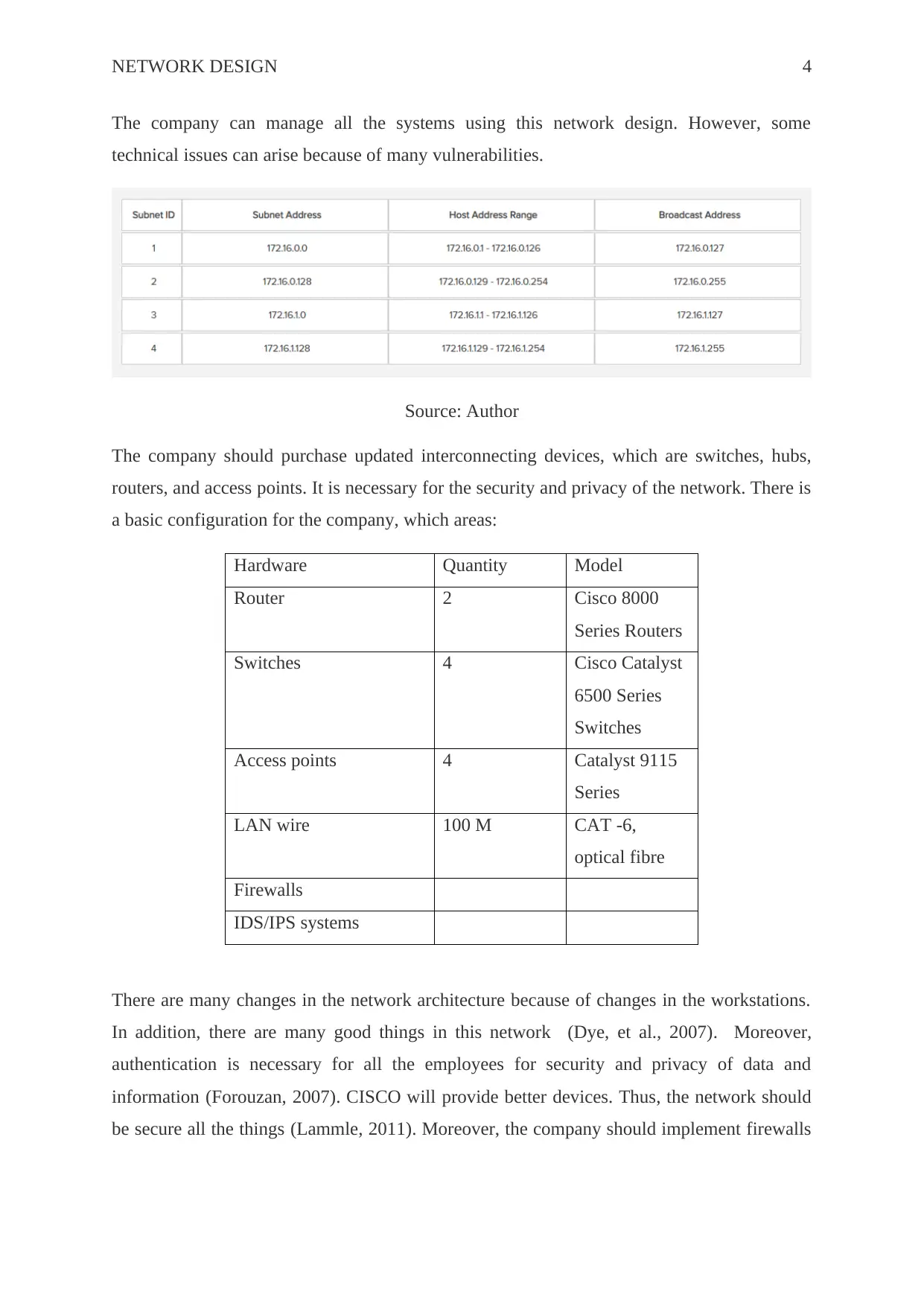
The company can manage all the systems using this network design. However, some
technical issues can arise because of many vulnerabilities.
Source: Author
The company should purchase updated interconnecting devices, which are switches, hubs,
routers, and access points. It is necessary for the security and privacy of the network. There is
a basic configuration for the company, which areas:
Hardware Quantity Model
Router 2 Cisco 8000
Series Routers
Switches 4 Cisco Catalyst
6500 Series
Switches
Access points 4 Catalyst 9115
Series
LAN wire 100 M CAT -6,
optical fibre
Firewalls
IDS/IPS systems
There are many changes in the network architecture because of changes in the workstations.
In addition, there are many good things in this network (Dye, et al., 2007). Moreover,
authentication is necessary for all the employees for security and privacy of data and
information (Forouzan, 2007). CISCO will provide better devices. Thus, the network should
be secure all the things (Lammle, 2011). Moreover, the company should implement firewalls
The company can manage all the systems using this network design. However, some
technical issues can arise because of many vulnerabilities.
Source: Author
The company should purchase updated interconnecting devices, which are switches, hubs,
routers, and access points. It is necessary for the security and privacy of the network. There is
a basic configuration for the company, which areas:
Hardware Quantity Model
Router 2 Cisco 8000
Series Routers
Switches 4 Cisco Catalyst
6500 Series
Switches
Access points 4 Catalyst 9115
Series
LAN wire 100 M CAT -6,
optical fibre
Firewalls
IDS/IPS systems
There are many changes in the network architecture because of changes in the workstations.
In addition, there are many good things in this network (Dye, et al., 2007). Moreover,
authentication is necessary for all the employees for security and privacy of data and
information (Forouzan, 2007). CISCO will provide better devices. Thus, the network should
be secure all the things (Lammle, 2011). Moreover, the company should implement firewalls

NETWORK DESIGN 5
and IDS systems. In addition, many devices are connected with wired and wireless systems.
Besides, antiviruses can be used for all the systems (Medhi & Ramasamy, 2017).
Network reference models and protocols can be used for improving security and privacy
(Paquet, 2013). The company should hire network experts to manage and monitor all the
processes (Sunshine, 2013). There is a huge impact of hardware of a company in their speed,
accuracy, productivity, and many more. There are some basic rules and regulations for using
hardware and software for designing a network. In addition, there is some basic concept to
design a network using hardware. Moreover, XYZ can increase the size of their company, a
number of workstations can be increased, as we take class B private network, which is
172.16.0.0. there are many benefits to this type of network. A company can manage all the
resources using this type of network.
Conclusion:
In conclusion, XYZ company should use hybrid topology to separate all the subnets
according to their needs. The company can use its assets for better processing, which is good
for the business of the company. The company should use class B private address, which is
suitable for expending networks as well. Finally, the company should use the proper solution
of its network to manage its business processes. It will improve their profit and productivity
as well.
and IDS systems. In addition, many devices are connected with wired and wireless systems.
Besides, antiviruses can be used for all the systems (Medhi & Ramasamy, 2017).
Network reference models and protocols can be used for improving security and privacy
(Paquet, 2013). The company should hire network experts to manage and monitor all the
processes (Sunshine, 2013). There is a huge impact of hardware of a company in their speed,
accuracy, productivity, and many more. There are some basic rules and regulations for using
hardware and software for designing a network. In addition, there is some basic concept to
design a network using hardware. Moreover, XYZ can increase the size of their company, a
number of workstations can be increased, as we take class B private network, which is
172.16.0.0. there are many benefits to this type of network. A company can manage all the
resources using this type of network.
Conclusion:
In conclusion, XYZ company should use hybrid topology to separate all the subnets
according to their needs. The company can use its assets for better processing, which is good
for the business of the company. The company should use class B private address, which is
suitable for expending networks as well. Finally, the company should use the proper solution
of its network to manage its business processes. It will improve their profit and productivity
as well.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK DESIGN 6
References
Blanchet , M., 2010. IP network node and middleware for establishing connectivity to both
the IPv4 and IPv6 networks.. Washington, Patent No. 7,657,642.
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Dosal, E., 2018. 5 Common Network Security Problems and Solutions. [Online]
Available at: https://www.compuquip.com/blog/5-common-network-security-problems-and-
solutions
[Accessed 29 January 2020].
Dye, M., McDonald, R. & Rufi, A., 2007. Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis: Cisco press..
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata
McGraw-Hill Education.
Lammle, T., 2011. CCNA Cisco Certified Network Associate Deluxe Study Guide. indiana:
John Wiley & Sons.
Medhi, D. & Ramasamy, K., 2017. Network routing: algorithms, protocols, and
architectures. s.l.:Morgan Kaufmann.
Paquet, C., 2013. Network Security Concepts and Policies. [Online]
Available at: http://www.ciscopress.com/articles/article.asp?p=1998559&seqNum=3
[Accessed 2 november 2019].
Sunshine, C. A., 2013. Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S., 2014. Computer networks. Harlow, Essex: Pearson.
References
Blanchet , M., 2010. IP network node and middleware for establishing connectivity to both
the IPv4 and IPv6 networks.. Washington, Patent No. 7,657,642.
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Dosal, E., 2018. 5 Common Network Security Problems and Solutions. [Online]
Available at: https://www.compuquip.com/blog/5-common-network-security-problems-and-
solutions
[Accessed 29 January 2020].
Dye, M., McDonald, R. & Rufi, A., 2007. Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis: Cisco press..
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata
McGraw-Hill Education.
Lammle, T., 2011. CCNA Cisco Certified Network Associate Deluxe Study Guide. indiana:
John Wiley & Sons.
Medhi, D. & Ramasamy, K., 2017. Network routing: algorithms, protocols, and
architectures. s.l.:Morgan Kaufmann.
Paquet, C., 2013. Network Security Concepts and Policies. [Online]
Available at: http://www.ciscopress.com/articles/article.asp?p=1998559&seqNum=3
[Accessed 2 november 2019].
Sunshine, C. A., 2013. Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S., 2014. Computer networks. Harlow, Essex: Pearson.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




