IT Network Design, Server Specifications, and Security Policy for TTF
VerifiedAdded on 2020/05/03
|10
|2476
|148
Report
AI Summary
This report outlines an IT network design proposal for Talon Textile Fasteners (TTF), addressing their outdated network infrastructure. The design includes upgrading client workstations to Windows 7, migrating the server to Windows Server 2008, and replacing the Red Hat Linux file server with a Windows-based solution. The proposed network utilizes dedicated security firewall machines, wireless backhaul links, and the implementation of Internet Information Services. The report specifies server details, including Dell PowerEdge and Cisco UCS C-series rack servers, along with a server build task list and a comprehensive server test plan. A server maintenance plan is also detailed, emphasizing security, connectivity, and updates. Router specifications are provided, along with a security policy and plan, user documentation, and ongoing maintenance support. The directory structure, including sites, organizational units, and groups within the Active Directory, is also described. The report emphasizes security, scalability, and efficient network performance for TTF.
IT NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Network Design.................................................................................................................1
2. Directory Structure...........................................................................................................2
3. Server Specification..........................................................................................................4
4. Server Build Task List Template....................................................................................4
5. Server Test Plan................................................................................................................5
6. Server Maintenance Plan.................................................................................................6
7. Router Specifications........................................................................................................7
8. Security Policy and Plan...................................................................................................7
9. User Documentation.........................................................................................................8
10. Ongoing Maintenance Support....................................................................................8
References.................................................................................................................................9
1
1. Network Design.................................................................................................................1
2. Directory Structure...........................................................................................................2
3. Server Specification..........................................................................................................4
4. Server Build Task List Template....................................................................................4
5. Server Test Plan................................................................................................................5
6. Server Maintenance Plan.................................................................................................6
7. Router Specifications........................................................................................................7
8. Security Policy and Plan...................................................................................................7
9. User Documentation.........................................................................................................8
10. Ongoing Maintenance Support....................................................................................8
References.................................................................................................................................9
1

1. Network Design
The Talon Textile Fasteners organization use the outdated network structure. So, it needs
to upgrade and improves the network structure. The organization team members are first
upgrade the all client workstations from windows XP to windows 7. Because the windows
XP does not provide the effective performance compared to windows 7. It also support the all
hardware in the organization but windows 7 support the organization current hardware and
software applications. So, organization team upgrades the client workstations. After, team
members are upgraders the small business server to windows server 2008. Because the small
business server only supports 25 users and 50 clients. But, windows server 2008 supports the
more than 50 users and 50 clients. It also has the server core to maintain the all configuration
and maintenance. It has improved windows firewall with secure default configuration. After,
Organization team as replacing the red hat Linux file server to windows based file server.
Because it is used to allow window security and it use file and storage services includes
technologies that help user to set up and manage the one or more file servers. These servers
are provide the central locations on user network.
The proposed network structure use dedicated security firewall machine at head office.
Because it easily isolate the main server from the user network and it creates the good sense
to secure the data in the organization. It use the dedicated hardware firewalls to easily deploy
the one or more dedicated servers and it provide the ultimate control over the firewall
configuration. It includes the al traffic monitoring, reporting and logging. In Mr Burr, it use
the internet connectivity has wireless backhaul link. This wireless link provide the secure
network connection and effective performance compared to other wireless links. Then,
implement the internet information services and hosting the company websites in the
perimeter network. This implementation is used to allow orders to come in via the company
website. The organization sales staff are uses the webmail access in remote. The remote
access provides the fast and efficient performance. The organization employees payment are
proceed to online portal by using company website (Digitalocean.com, 2017). Finally,
increase the security for the organization. Mostly organization staffs are using the laptops
outside the office as well as security within our domain. Because all laptops are will be
encrypted with a secret key. The secret key is exchanged using a private and public key
protocol.
2
The Talon Textile Fasteners organization use the outdated network structure. So, it needs
to upgrade and improves the network structure. The organization team members are first
upgrade the all client workstations from windows XP to windows 7. Because the windows
XP does not provide the effective performance compared to windows 7. It also support the all
hardware in the organization but windows 7 support the organization current hardware and
software applications. So, organization team upgrades the client workstations. After, team
members are upgraders the small business server to windows server 2008. Because the small
business server only supports 25 users and 50 clients. But, windows server 2008 supports the
more than 50 users and 50 clients. It also has the server core to maintain the all configuration
and maintenance. It has improved windows firewall with secure default configuration. After,
Organization team as replacing the red hat Linux file server to windows based file server.
Because it is used to allow window security and it use file and storage services includes
technologies that help user to set up and manage the one or more file servers. These servers
are provide the central locations on user network.
The proposed network structure use dedicated security firewall machine at head office.
Because it easily isolate the main server from the user network and it creates the good sense
to secure the data in the organization. It use the dedicated hardware firewalls to easily deploy
the one or more dedicated servers and it provide the ultimate control over the firewall
configuration. It includes the al traffic monitoring, reporting and logging. In Mr Burr, it use
the internet connectivity has wireless backhaul link. This wireless link provide the secure
network connection and effective performance compared to other wireless links. Then,
implement the internet information services and hosting the company websites in the
perimeter network. This implementation is used to allow orders to come in via the company
website. The organization sales staff are uses the webmail access in remote. The remote
access provides the fast and efficient performance. The organization employees payment are
proceed to online portal by using company website (Digitalocean.com, 2017). Finally,
increase the security for the organization. Mostly organization staffs are using the laptops
outside the office as well as security within our domain. Because all laptops are will be
encrypted with a secret key. The secret key is exchanged using a private and public key
protocol.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
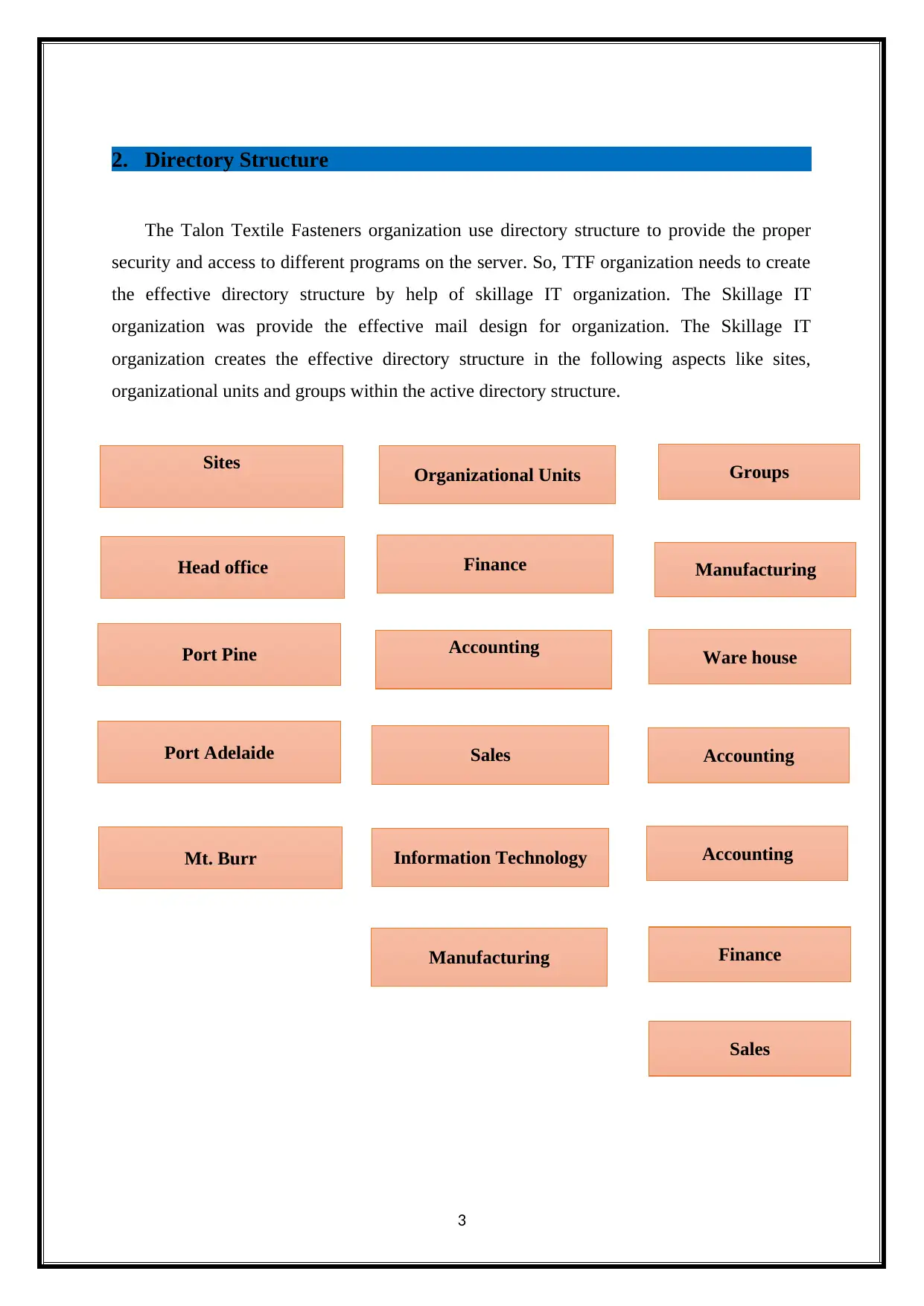
2. Directory Structure
The Talon Textile Fasteners organization use directory structure to provide the proper
security and access to different programs on the server. So, TTF organization needs to create
the effective directory structure by help of skillage IT organization. The Skillage IT
organization was provide the effective mail design for organization. The Skillage IT
organization creates the effective directory structure in the following aspects like sites,
organizational units and groups within the active directory structure.
3
Sites Organizational Units Groups
Head office
Port Pine
Port Adelaide
Mt. Burr
Finance
Accounting
Sales
Information Technology
Manufacturing
Manufacturing
Ware house
Accounting
Accounting
Finance
Sales
The Talon Textile Fasteners organization use directory structure to provide the proper
security and access to different programs on the server. So, TTF organization needs to create
the effective directory structure by help of skillage IT organization. The Skillage IT
organization was provide the effective mail design for organization. The Skillage IT
organization creates the effective directory structure in the following aspects like sites,
organizational units and groups within the active directory structure.
3
Sites Organizational Units Groups
Head office
Port Pine
Port Adelaide
Mt. Burr
Finance
Accounting
Sales
Information Technology
Manufacturing
Manufacturing
Ware house
Accounting
Accounting
Finance
Sales
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. Server Specification
The Dell PowerEdge R715 Rack server and Cisco UCS C-series Rack servers are
support the proposed network structure. These two servers has the rack mountable scalable.
These are support the virtualization for a future move. The Cisco UCS C- series rack servers
are used to delivers the unified computing in an industry standard form factor to increase the
agility and reduce the TCO and workload. It identify the workload challenges through an
internal resources, memory, balance of processing, I/O and memory. These two servers are
generally provides the high performance and expandability. Those servers are delivers an
optimal combination of flexibility, combination of performance and efficiency gains. It also
provide the outstanding levels of internal memory and storage expandability. The head office
use the Cisco UCS C-series Rack servers. The Port Pine office also use Cisco USC C- series
Rack servers. The Port Adelaide and Mt. Burr sites are using the Dell PowerEdge R714 rack
servers. So, Skillage It organization requested by the CIO of TTF organization to accept the
chosen server. Because, the TTF organization needs to know the hardware vendors details
and server details. These two servers are have the backup recovery processes. The servers are
provides the high performance compared to other servers. It also provides the scalability and
flexibility for an organization (Xlhost.com, 2017).
4. Server Build Task List Template
The server Build Task list template is shown below (Digitalocean.com, 2017).
Install Windows Server 2008
Install windows 7
Install and configure the Windows based file server
Install and configure the security firewall machine at head office
Configure the internet connectivity at Mt. Burr
Configure the Wireless links
Install and configure the Internet information services
Configure the remote web mail access
Upgrade the company online portal
4
The Dell PowerEdge R715 Rack server and Cisco UCS C-series Rack servers are
support the proposed network structure. These two servers has the rack mountable scalable.
These are support the virtualization for a future move. The Cisco UCS C- series rack servers
are used to delivers the unified computing in an industry standard form factor to increase the
agility and reduce the TCO and workload. It identify the workload challenges through an
internal resources, memory, balance of processing, I/O and memory. These two servers are
generally provides the high performance and expandability. Those servers are delivers an
optimal combination of flexibility, combination of performance and efficiency gains. It also
provide the outstanding levels of internal memory and storage expandability. The head office
use the Cisco UCS C-series Rack servers. The Port Pine office also use Cisco USC C- series
Rack servers. The Port Adelaide and Mt. Burr sites are using the Dell PowerEdge R714 rack
servers. So, Skillage It organization requested by the CIO of TTF organization to accept the
chosen server. Because, the TTF organization needs to know the hardware vendors details
and server details. These two servers are have the backup recovery processes. The servers are
provides the high performance compared to other servers. It also provides the scalability and
flexibility for an organization (Xlhost.com, 2017).
4. Server Build Task List Template
The server Build Task list template is shown below (Digitalocean.com, 2017).
Install Windows Server 2008
Install windows 7
Install and configure the Windows based file server
Install and configure the security firewall machine at head office
Configure the internet connectivity at Mt. Burr
Configure the Wireless links
Install and configure the Internet information services
Configure the remote web mail access
Upgrade the company online portal
4

Upgrade the Security with encrypted security key.
Configure the Dell Power Edge R715 2 U Rack server
Configure the Cisco UCS C-series Rack servers
Install and configure the perimeter network.
5. Server Test Plan
The server test plan is used to describe the plan for testing the server environment after
moving the server (Hcbridges.net, 2017). The server test plan includes the following
activities.
Test the server connectivity
Test web server are online or offline
Test internal access
Test the external access
Test the DNS server
Also test the DHCP server
Test the Network load balancing
Test the developer’s ability to access the different development, production,
environments and testing.
The server test plan also includes the testing tools such as FTP client browser,
workstation and more. The server test plan provides the testing procedures. It is listed in
below.
First, access the every server via FTP client
Using FTP, upload the files to each server
After, map the shared folders on each server.
Using window explorer to transfer files between server and workstation.
Then, administer the IIS from work station on each server.
Create the virtual sites on each server
Also creates the virtual directories and folders on each server.
Start and stop the IIS
Access the all company websites
Makes the new user accounts
Also makes the new user groups
5
Configure the Dell Power Edge R715 2 U Rack server
Configure the Cisco UCS C-series Rack servers
Install and configure the perimeter network.
5. Server Test Plan
The server test plan is used to describe the plan for testing the server environment after
moving the server (Hcbridges.net, 2017). The server test plan includes the following
activities.
Test the server connectivity
Test web server are online or offline
Test internal access
Test the external access
Test the DNS server
Also test the DHCP server
Test the Network load balancing
Test the developer’s ability to access the different development, production,
environments and testing.
The server test plan also includes the testing tools such as FTP client browser,
workstation and more. The server test plan provides the testing procedures. It is listed in
below.
First, access the every server via FTP client
Using FTP, upload the files to each server
After, map the shared folders on each server.
Using window explorer to transfer files between server and workstation.
Then, administer the IIS from work station on each server.
Create the virtual sites on each server
Also creates the virtual directories and folders on each server.
Start and stop the IIS
Access the all company websites
Makes the new user accounts
Also makes the new user groups
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Add the new users to the existing groups
Finally, manage the user accounts through user manager for domains.
6. Server Maintenance Plan
Server maintenance plan is used to keep the updated information of the server to provide
an effective network for the organization. The server maintenance process increases business
performance. The maintenance of the server reduces the network traffic and monitors the
overall network. Server maintenance plan is used to maintain the server memory, capacity
and RAM. The server maintenance plan is used to reduce the server issues and it prepares
network documentation, to provide the network information for the organization. It boots the
server productivity and overall business productivity. It increases the work efficiency. The
servers are managed by the network management, which has control to maintain the server. It
ensures the server’s availability and security. The server maintenance configures all the
network firewall devices. It maintains routine maintenance actions to provide reliable access.
The server maintenance plan includes the following aspects.
Check the server connectivity
Check internal access and external access
Check and update the DNS and DHCP server configuration
Check the network load balancing
Check the server backup
Check the network trouble shooting
Update the security firewalls
Defragment the network traffic
Update the server security
Delete the existing server configuration
Check the Active directory features.
6
Finally, manage the user accounts through user manager for domains.
6. Server Maintenance Plan
Server maintenance plan is used to keep the updated information of the server to provide
an effective network for the organization. The server maintenance process increases business
performance. The maintenance of the server reduces the network traffic and monitors the
overall network. Server maintenance plan is used to maintain the server memory, capacity
and RAM. The server maintenance plan is used to reduce the server issues and it prepares
network documentation, to provide the network information for the organization. It boots the
server productivity and overall business productivity. It increases the work efficiency. The
servers are managed by the network management, which has control to maintain the server. It
ensures the server’s availability and security. The server maintenance configures all the
network firewall devices. It maintains routine maintenance actions to provide reliable access.
The server maintenance plan includes the following aspects.
Check the server connectivity
Check internal access and external access
Check and update the DNS and DHCP server configuration
Check the network load balancing
Check the server backup
Check the network trouble shooting
Update the security firewalls
Defragment the network traffic
Update the server security
Delete the existing server configuration
Check the Active directory features.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7. Router Specifications
The TTF organization uses Cisco 2800 Series Integrated Services Routers to provide
scalable and reliable performance. The routers give reliable and flexible network access for
an organization, by using the network routing protocols for communicating the overall
network. It specifies data communication attributes like, packer information and structure.
This router provides the flexible network configuration and optimized the secure, wire speed
delivery of voice, video, wireless and data services. It delivers the scalable and fast delivery
of mission critical business applications. This routers delivers the investment protection and
maximum business agility. This routers provide a firewall and connectivity to the wireless
area networks. It also provide the secure network connections.
8. Security Policy and Plan
In TTF organization, the two servers are placed on each location. So, it should be follow
the security policies and plan. The security policy and plan are concerned with hardware and
software security (Docs.oracle.com, 2017). The Skillage IT proposed the below activities to
follow the security plan and policy. The Skillage IT organization first assign the security
policy and plan for Network policy server. The implementation of network policy server is
used to describes the how to configure the NAP polices on NPS. It is implementation of a
RADIUS server and it performs the network connection accounting, authorization and
authentication. It performs the following tasks.
It makes the connection request policies
It makes the network policies
It makes the NAP security policies
The Implementation of NPS is used to provide the security and productivity for an
organization. Basically the external users are must be have the bit lockers to provide the
appropriate policies and configuration requirements depends on the organization business
requirements. It defines the organization current procedures, policies and hardware
environment. It review the existing corporate the security policies. In windows server 2008,
bit lockers can be easily provisioned before the operating system installed
(Technet.microsoft.com, 2017). The branch server between the connection will creates the
secure communication between the two branches. It provides the secure data transmission by
7
The TTF organization uses Cisco 2800 Series Integrated Services Routers to provide
scalable and reliable performance. The routers give reliable and flexible network access for
an organization, by using the network routing protocols for communicating the overall
network. It specifies data communication attributes like, packer information and structure.
This router provides the flexible network configuration and optimized the secure, wire speed
delivery of voice, video, wireless and data services. It delivers the scalable and fast delivery
of mission critical business applications. This routers delivers the investment protection and
maximum business agility. This routers provide a firewall and connectivity to the wireless
area networks. It also provide the secure network connections.
8. Security Policy and Plan
In TTF organization, the two servers are placed on each location. So, it should be follow
the security policies and plan. The security policy and plan are concerned with hardware and
software security (Docs.oracle.com, 2017). The Skillage IT proposed the below activities to
follow the security plan and policy. The Skillage IT organization first assign the security
policy and plan for Network policy server. The implementation of network policy server is
used to describes the how to configure the NAP polices on NPS. It is implementation of a
RADIUS server and it performs the network connection accounting, authorization and
authentication. It performs the following tasks.
It makes the connection request policies
It makes the network policies
It makes the NAP security policies
The Implementation of NPS is used to provide the security and productivity for an
organization. Basically the external users are must be have the bit lockers to provide the
appropriate policies and configuration requirements depends on the organization business
requirements. It defines the organization current procedures, policies and hardware
environment. It review the existing corporate the security policies. In windows server 2008,
bit lockers can be easily provisioned before the operating system installed
(Technet.microsoft.com, 2017). The branch server between the connection will creates the
secure communication between the two branches. It provides the secure data transmission by
7

follows the security policy and plan. The network should be protected by uitlizing the
defence in depth. The OSI levels provides the secure connections. It also provides the flexible
and scalability of the network. In security policy and plan, the security auditing performs the
major roles for an organizations. The security auditing define the network actions and it
enforces the policy. The security policies include enforcement and auditing. It performs
periodic audits and management to accept the information system security plan. It protects
the organization assets. The security plan must address the asset’s security, to recover the
organization assets by using the recovery strategies. The security policy and plan includes
secured implementation of firewalls, remote protocols, AV filters, packet filtering, firewalls
and spam filters.
9. User Documentation
The Skillage IT organization maintains user documentation. Because, user
documentation basically has network access control for a proposed network infrastructure. It
maintains network’s installing and planning information. The user documentation views the
resolving faults and tracks the network, with the help of the fault management and reporting.
It manages network certificates. Whereas, the server, AVMs, and units are managed with the
help of organization’s maintenance plan. Basically, organization has maintenance plan to
maintain the entire network and its documentation. It adds the devices by managing and
creating the networks. It also maintains the data redundancy. The user documentation has the
two simple page instruction manual to provide the overall network infrastructure. It is very
useful for organization teams and employees.
10. Ongoing Maintenance Support
Ongoing maintenance support is used to provide flexibility to the organization. It
includes more than one activity such as general logistics, organization spirit, organization
work, personnel management, relationship with the larger community, fiscal management
and board maintenance. On-going maintenance and support is used to implement the
organization’s business elements and technology. . It includes training of system
administrators and end users. It set ups user feedback programs, messaging and
communications. The ongoing maintenance support offers the below information for an
8
defence in depth. The OSI levels provides the secure connections. It also provides the flexible
and scalability of the network. In security policy and plan, the security auditing performs the
major roles for an organizations. The security auditing define the network actions and it
enforces the policy. The security policies include enforcement and auditing. It performs
periodic audits and management to accept the information system security plan. It protects
the organization assets. The security plan must address the asset’s security, to recover the
organization assets by using the recovery strategies. The security policy and plan includes
secured implementation of firewalls, remote protocols, AV filters, packet filtering, firewalls
and spam filters.
9. User Documentation
The Skillage IT organization maintains user documentation. Because, user
documentation basically has network access control for a proposed network infrastructure. It
maintains network’s installing and planning information. The user documentation views the
resolving faults and tracks the network, with the help of the fault management and reporting.
It manages network certificates. Whereas, the server, AVMs, and units are managed with the
help of organization’s maintenance plan. Basically, organization has maintenance plan to
maintain the entire network and its documentation. It adds the devices by managing and
creating the networks. It also maintains the data redundancy. The user documentation has the
two simple page instruction manual to provide the overall network infrastructure. It is very
useful for organization teams and employees.
10. Ongoing Maintenance Support
Ongoing maintenance support is used to provide flexibility to the organization. It
includes more than one activity such as general logistics, organization spirit, organization
work, personnel management, relationship with the larger community, fiscal management
and board maintenance. On-going maintenance and support is used to implement the
organization’s business elements and technology. . It includes training of system
administrators and end users. It set ups user feedback programs, messaging and
communications. The ongoing maintenance support offers the below information for an
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organization such as virus, windows updates, monthly hardware information, on-going
training and internet connections. The Virus information is very useful for an organization.
The ongoing training is useful for organizations team members. The monthly hardware
information is very useful for an organization because it provide the hardware install and
configurations details and updates for the hardware’s. It also provide the windows updates
information for an organization.
References
Digitalocean.com. (2017). 7 Security Measures to Protect Your Servers | DigitalOcean.
[online] Available at: https://www.digitalocean.com/community/tutorials/7-security-
measures-to-protect-your-servers [Accessed 26 Nov. 2017].
Docs.oracle.com. (2017). Why Install the Increased Security Features? (Sun N1 Grid Engine
6.1 Installation Guide). [online] Available at: https://docs.oracle.com/cd/E19957-01/820-
0697/emxzl/index.html [Accessed 26 Nov. 2017].
Hcbridges.net. (2017). Server Test Plan. [online] Available at:
http://www.hcbridges.net/portfolio/documentation/eComm_web_SystemTest.pdf [Accessed
26 Nov. 2017].
Technet.microsoft.com. (2017). File and Storage Services Overview. [online] Available at:
https://technet.microsoft.com/en-us/library/hh831487(v=ws.11).aspx [Accessed 26 Nov.
2017].
Technet.microsoft.com. (2017). Prepare your organization for BitLocker: Planning and
Policies. [online] Available at:
https://technet.microsoft.com/de-de/library/jj592683(v=ws.11).aspx [Accessed 26 Nov.
2017].
Xlhost.com. (2017). Firewall Protection | Dedicated Server Firewall Security. [online]
Available at: http://www.xlhost.com/managed-security/firewall-protection/ [Accessed 26
Nov. 2017].
9
training and internet connections. The Virus information is very useful for an organization.
The ongoing training is useful for organizations team members. The monthly hardware
information is very useful for an organization because it provide the hardware install and
configurations details and updates for the hardware’s. It also provide the windows updates
information for an organization.
References
Digitalocean.com. (2017). 7 Security Measures to Protect Your Servers | DigitalOcean.
[online] Available at: https://www.digitalocean.com/community/tutorials/7-security-
measures-to-protect-your-servers [Accessed 26 Nov. 2017].
Docs.oracle.com. (2017). Why Install the Increased Security Features? (Sun N1 Grid Engine
6.1 Installation Guide). [online] Available at: https://docs.oracle.com/cd/E19957-01/820-
0697/emxzl/index.html [Accessed 26 Nov. 2017].
Hcbridges.net. (2017). Server Test Plan. [online] Available at:
http://www.hcbridges.net/portfolio/documentation/eComm_web_SystemTest.pdf [Accessed
26 Nov. 2017].
Technet.microsoft.com. (2017). File and Storage Services Overview. [online] Available at:
https://technet.microsoft.com/en-us/library/hh831487(v=ws.11).aspx [Accessed 26 Nov.
2017].
Technet.microsoft.com. (2017). Prepare your organization for BitLocker: Planning and
Policies. [online] Available at:
https://technet.microsoft.com/de-de/library/jj592683(v=ws.11).aspx [Accessed 26 Nov.
2017].
Xlhost.com. (2017). Firewall Protection | Dedicated Server Firewall Security. [online]
Available at: http://www.xlhost.com/managed-security/firewall-protection/ [Accessed 26
Nov. 2017].
9
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





