Network Implementation Report: Talon Textile Fastener Company Project
VerifiedAdded on 2020/05/28
|18
|3281
|32
Report
AI Summary
This report provides a comprehensive network implementation plan for Talon Textile Fastener Company, covering various aspects of network design, server specifications, router configuration, and security policies. The report details the business requirements analysis, directory structure, and server specifications, including the location and roles of virtual and physical servers. It outlines server build tasks, a server test plan, and a maintenance plan. The report also covers router specifications, cable types, protocols used, and traffic monitoring processes. A significant portion focuses on the security policy plan, including perimeter design, remote access, site-to-site links, defense in depth, security auditing, threat identification, and risk analysis. User documentation for logging on to a PC, setting up a VPN connection, and creating user accounts is also provided. The project signoff and ongoing maintenance support are also included, along with a bibliography.

Running head: NETWORK IMPLEMENTATION
Network Implementation for Talon Textile Fastener Company
Name of the Student
Name of the University
Author’s Note
Network Implementation for Talon Textile Fastener Company
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK IMPLEMENTATION
Table of Contents
a. Network Design and Supporting Documents..................................................................3
b. Directory Structure..........................................................................................................3
i. Sites..............................................................................................................................3
ii. Organizational Units....................................................................................................4
iii. Groups........................................................................................................................4
c. Server Specification.........................................................................................................5
i. Location and Number of Virtual and physical Servers................................................5
ii. Roles of servers...........................................................................................................5
iii. Approval Sign off document......................................................................................5
d. Server build task list........................................................................................................6
e. Server Test Plan...............................................................................................................6
f. Server Maintenance Plan..................................................................................................8
g. Router Specification........................................................................................................9
i. Plan for Implementation...............................................................................................9
ii. Cable types required....................................................................................................9
iii. Protocols used.............................................................................................................9
iv. Traffic monitoring process.......................................................................................10
h. Security policy plan.......................................................................................................10
i. Perimeter Design........................................................................................................10
NETWORK IMPLEMENTATION
Table of Contents
a. Network Design and Supporting Documents..................................................................3
b. Directory Structure..........................................................................................................3
i. Sites..............................................................................................................................3
ii. Organizational Units....................................................................................................4
iii. Groups........................................................................................................................4
c. Server Specification.........................................................................................................5
i. Location and Number of Virtual and physical Servers................................................5
ii. Roles of servers...........................................................................................................5
iii. Approval Sign off document......................................................................................5
d. Server build task list........................................................................................................6
e. Server Test Plan...............................................................................................................6
f. Server Maintenance Plan..................................................................................................8
g. Router Specification........................................................................................................9
i. Plan for Implementation...............................................................................................9
ii. Cable types required....................................................................................................9
iii. Protocols used.............................................................................................................9
iv. Traffic monitoring process.......................................................................................10
h. Security policy plan.......................................................................................................10
i. Perimeter Design........................................................................................................10

2
NETWORK IMPLEMENTATION
ii. Remote Access..........................................................................................................10
iii. Site to site links........................................................................................................10
iv. Defense in depth.......................................................................................................11
v. Security Auditing and Monitoring.............................................................................11
vi. Threat identification.................................................................................................11
vii. Risk Analysis...........................................................................................................11
viii. Response Procedure...............................................................................................12
i. User Documentation.......................................................................................................12
j. Project Signoff................................................................................................................13
k. Ongoing maintenance Support......................................................................................14
Bibliography......................................................................................................................15
NETWORK IMPLEMENTATION
ii. Remote Access..........................................................................................................10
iii. Site to site links........................................................................................................10
iv. Defense in depth.......................................................................................................11
v. Security Auditing and Monitoring.............................................................................11
vi. Threat identification.................................................................................................11
vii. Risk Analysis...........................................................................................................11
viii. Response Procedure...............................................................................................12
i. User Documentation.......................................................................................................12
j. Project Signoff................................................................................................................13
k. Ongoing maintenance Support......................................................................................14
Bibliography......................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK IMPLEMENTATION
a. Network Design and Supporting Documents
The business requirement of the organization is analyzed for the preparation of the
network design for Talon Textile Fastener Company. The network is designed for
accommodation of the future growth of the organization and allowing the staffs to access the
resources on the database server for analysis of the requirement of the material and batch up the
product for shipping. The data types, data sources, number of user and their priority are
identified for the configuration of the active directory of the network.
b. Directory Structure
i. Sites
Domain /Sites
NETWORK IMPLEMENTATION
a. Network Design and Supporting Documents
The business requirement of the organization is analyzed for the preparation of the
network design for Talon Textile Fastener Company. The network is designed for
accommodation of the future growth of the organization and allowing the staffs to access the
resources on the database server for analysis of the requirement of the material and batch up the
product for shipping. The data types, data sources, number of user and their priority are
identified for the configuration of the active directory of the network.
b. Directory Structure
i. Sites
Domain /Sites
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK IMPLEMENTATION
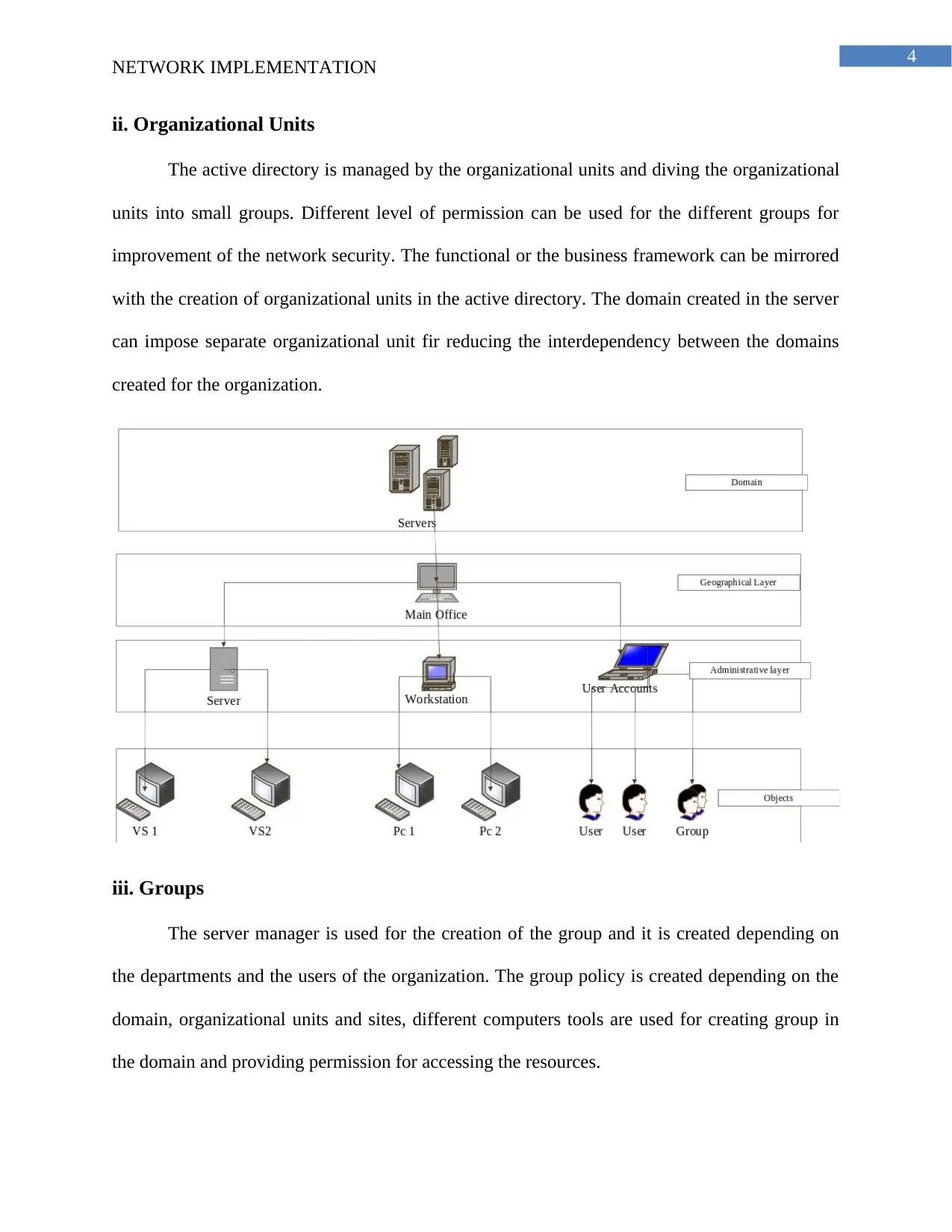
ii. Organizational Units
The active directory is managed by the organizational units and diving the organizational
units into small groups. Different level of permission can be used for the different groups for
improvement of the network security. The functional or the business framework can be mirrored
with the creation of organizational units in the active directory. The domain created in the server
can impose separate organizational unit fir reducing the interdependency between the domains
created for the organization.
iii. Groups
The server manager is used for the creation of the group and it is created depending on
the departments and the users of the organization. The group policy is created depending on the
domain, organizational units and sites, different computers tools are used for creating group in
the domain and providing permission for accessing the resources.
NETWORK IMPLEMENTATION
ii. Organizational Units
The active directory is managed by the organizational units and diving the organizational
units into small groups. Different level of permission can be used for the different groups for
improvement of the network security. The functional or the business framework can be mirrored
with the creation of organizational units in the active directory. The domain created in the server
can impose separate organizational unit fir reducing the interdependency between the domains
created for the organization.
iii. Groups
The server manager is used for the creation of the group and it is created depending on
the departments and the users of the organization. The group policy is created depending on the
domain, organizational units and sites, different computers tools are used for creating group in
the domain and providing permission for accessing the resources.

5
NETWORK IMPLEMENTATION
c. Server Specification
i. Location and Number of Virtual and physical Servers
A database server and a file server is installed in the DMZ zone of the network with high
end configuration such that it can be virtualized for handling more number of user request and
balance the load in the network.
ii. Roles of servers
The server is installed in the network for allowing the users to share file between the
nodes securely and categorize the users according the department. The group policy is created
for assigning permission to the users for securing the files and the resources of the organization
against illegal access.
iii. Approval Sign off document
Prepared by Signature Date
Author’s Name
[Title]
[Organization] _________________________ _________________
Accepted by Signature Date
[Client Acceptor’s Name]
[Title]
[Organization] _________________________ _________________
Approved by Signature Date
NETWORK IMPLEMENTATION
c. Server Specification
i. Location and Number of Virtual and physical Servers
A database server and a file server is installed in the DMZ zone of the network with high
end configuration such that it can be virtualized for handling more number of user request and
balance the load in the network.
ii. Roles of servers
The server is installed in the network for allowing the users to share file between the
nodes securely and categorize the users according the department. The group policy is created
for assigning permission to the users for securing the files and the resources of the organization
against illegal access.
iii. Approval Sign off document
Prepared by Signature Date
Author’s Name
[Title]
[Organization] _________________________ _________________
Accepted by Signature Date
[Client Acceptor’s Name]
[Title]
[Organization] _________________________ _________________
Approved by Signature Date
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK IMPLEMENTATION
[Client Approver’s Name]
[Title]
[Organization] _________________________ _________________
[Project Manager’s Name]
[Title]
[Organization] _________________________ _________________
d. Server build task list
Task 1: Physical server configuration
Task 2: Operating system installation on the server and the nodes
Task 3: Performance tuning and optimizing the OS.
e. Server Test Plan
Scope
The scalability and flexibility is the main scope for the development of the network and
the test plan is created for include the response of the users and configure the servers for
improving the efficiency of the network.
Objectives
Connection testing between the nodes and the server
Online connectivity off the server
Accessing online resources and websites
Testing the external and the internal components for accessibility
NETWORK IMPLEMENTATION
[Client Approver’s Name]
[Title]
[Organization] _________________________ _________________
[Project Manager’s Name]
[Title]
[Organization] _________________________ _________________
d. Server build task list
Task 1: Physical server configuration
Task 2: Operating system installation on the server and the nodes
Task 3: Performance tuning and optimizing the OS.
e. Server Test Plan
Scope
The scalability and flexibility is the main scope for the development of the network and
the test plan is created for include the response of the users and configure the servers for
improving the efficiency of the network.
Objectives
Connection testing between the nodes and the server
Online connectivity off the server
Accessing online resources and websites
Testing the external and the internal components for accessibility
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK IMPLEMENTATION
Analyzing the ability of the system tester for improvement of the response time
and security of the network.
Task and responsibility
Student_Name – test project manager
Fredrik Backman – System tester
General Approach
The accessibility and the functionality of the server installed in the network should be
analyzed before starting the configuration of the server and it should be tested multiple times
before deployment in the network. There are different online and standalone testing tools
available such as FTP client browser, Dreamweaver, Homesites 4.5 and Workstations that can be
applied for the testing of the components of the server.
The test include uploading file via a client using ftp protocol, accessing the websites, etc.
The group policy is checked by accessing the server components from different nodes connected
in the network and virtual sites are used for transferring files between the nodes and the server. A
domain is create on the server for allowing the user to access the resources based on the
permission assigned to them.
System testing and case development strategy
The network for Talon Textile Fastener Company is created after analyzing the
requirement and system is tested for aligning the business requirement with the network and
increase the productivity of the company.
NETWORK IMPLEMENTATION
Analyzing the ability of the system tester for improvement of the response time
and security of the network.
Task and responsibility
Student_Name – test project manager
Fredrik Backman – System tester
General Approach
The accessibility and the functionality of the server installed in the network should be
analyzed before starting the configuration of the server and it should be tested multiple times
before deployment in the network. There are different online and standalone testing tools
available such as FTP client browser, Dreamweaver, Homesites 4.5 and Workstations that can be
applied for the testing of the components of the server.
The test include uploading file via a client using ftp protocol, accessing the websites, etc.
The group policy is checked by accessing the server components from different nodes connected
in the network and virtual sites are used for transferring files between the nodes and the server. A
domain is create on the server for allowing the user to access the resources based on the
permission assigned to them.
System testing and case development strategy
The network for Talon Textile Fastener Company is created after analyzing the
requirement and system is tested for aligning the business requirement with the network and
increase the productivity of the company.
8
NETWORK IMPLEMENTATION
f. Server Maintenance Plan
The server maintenance plan is important for maintaining the maintenance task such as
backing up the database, removing the inconsistency in the configuration of the active directory.
The maintenance wizard can be used for automating the maintenance process for the local and
the targeted server for improvement of the multiuser environment. The index are rebuild using
the data and the index pages for the future growth in future. The empty data pages are removed
using the compression of the data files and updating the index statistics.
Backup Every hours
Backup verification After backup is completed
Transaction logs backup Every 30 min
Database integrity testing Everyday
Index table reorganization Everyday
Statistic update Everyday
Database Compression If required
Index rebuilt Done after defragmentation followed by the
index reorganization and statistic update
manually.
Cleanup maintenance Everyday
NETWORK IMPLEMENTATION
f. Server Maintenance Plan
The server maintenance plan is important for maintaining the maintenance task such as
backing up the database, removing the inconsistency in the configuration of the active directory.
The maintenance wizard can be used for automating the maintenance process for the local and
the targeted server for improvement of the multiuser environment. The index are rebuild using
the data and the index pages for the future growth in future. The empty data pages are removed
using the compression of the data files and updating the index statistics.
Backup Every hours
Backup verification After backup is completed
Transaction logs backup Every 30 min
Database integrity testing Everyday
Index table reorganization Everyday
Statistic update Everyday
Database Compression If required
Index rebuilt Done after defragmentation followed by the
index reorganization and statistic update
manually.
Cleanup maintenance Everyday
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK IMPLEMENTATION
g. Router Specification
i. Plan for Implementation
Cisco 2800 series router is installed in the network for communicating with the nodes
connected in the network. The router is selected because it is easy to configure and supports
different features that are required for the management of the network. The router can be
configured for allocation of DHCP address to the different VLANs connected in the network.
The router is also configured with access control list for creation of a DMZ zone and install the
servers in that zone. The access of the servers for all the users are restricted for increasing the
security of the network.
ii. Cable types required
The core network devices are connected using serial cables and fiber optic cable is used
as the backbone of the network as it support a larger bandwidth when compared with the normal
UTP cables. Copper straight through cable is used for connecting the nodes, server with the
switch and copper cross over cable is used for connecting the router with the switch in the
network.
iii. Protocols used
The router is configured with EIGRP protocol for allowing the data packets to
communicate with the nodes connected with the interface of another router installed in the
network. Routing is important enabling the users to communicate with the nodes connected in
another VLAN. Cisco 2811 series router should be used for the management of the network and
the router should be configured with IPSec protocol such that site to site vpn tunnel is created.
NETWORK IMPLEMENTATION
g. Router Specification
i. Plan for Implementation
Cisco 2800 series router is installed in the network for communicating with the nodes
connected in the network. The router is selected because it is easy to configure and supports
different features that are required for the management of the network. The router can be
configured for allocation of DHCP address to the different VLANs connected in the network.
The router is also configured with access control list for creation of a DMZ zone and install the
servers in that zone. The access of the servers for all the users are restricted for increasing the
security of the network.
ii. Cable types required
The core network devices are connected using serial cables and fiber optic cable is used
as the backbone of the network as it support a larger bandwidth when compared with the normal
UTP cables. Copper straight through cable is used for connecting the nodes, server with the
switch and copper cross over cable is used for connecting the router with the switch in the
network.
iii. Protocols used
The router is configured with EIGRP protocol for allowing the data packets to
communicate with the nodes connected with the interface of another router installed in the
network. Routing is important enabling the users to communicate with the nodes connected in
another VLAN. Cisco 2811 series router should be used for the management of the network and
the router should be configured with IPSec protocol such that site to site vpn tunnel is created.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK IMPLEMENTATION
The GRE protocol can also be used for the encryption of the data packets coming from the VPN
server.
iv. Traffic monitoring process
Intrusion detection system is essential for increasing the security of the network and
analyze the flow of data packets in the network. The health of the server should be monitored for
balancing the loads and reduce the response time for the users accessing the resources residing
the server.
h. Security policy plan
i. Perimeter Design
The security perimeter design should be analyzed for locating the server installed on the
network and it should be used for addressing the requirement and implementation of the security
policy in the organization. The network firewall and the rules used for the configuration of the
firewall should be defined for increasing the security and maintaining confidentiality of the
organizational data. Back channel inter server communication should be used for the
implementation of the onsite server such that the reliability of the network can be increased.
ii. Remote Access
The remote access can be established using the VPN and it can be used for establishment
of secure connection between the remote host and the business private network. The access of
the resources available in the server installed in the network are established using the remote
access VPN. A secure authentication is selected for the establishment of the connection and the
authentication server should be configured separately.
NETWORK IMPLEMENTATION
The GRE protocol can also be used for the encryption of the data packets coming from the VPN
server.
iv. Traffic monitoring process
Intrusion detection system is essential for increasing the security of the network and
analyze the flow of data packets in the network. The health of the server should be monitored for
balancing the loads and reduce the response time for the users accessing the resources residing
the server.
h. Security policy plan
i. Perimeter Design
The security perimeter design should be analyzed for locating the server installed on the
network and it should be used for addressing the requirement and implementation of the security
policy in the organization. The network firewall and the rules used for the configuration of the
firewall should be defined for increasing the security and maintaining confidentiality of the
organizational data. Back channel inter server communication should be used for the
implementation of the onsite server such that the reliability of the network can be increased.
ii. Remote Access
The remote access can be established using the VPN and it can be used for establishment
of secure connection between the remote host and the business private network. The access of
the resources available in the server installed in the network are established using the remote
access VPN. A secure authentication is selected for the establishment of the connection and the
authentication server should be configured separately.

11
NETWORK IMPLEMENTATION
iii. Site to site links
Establishment of a site to site link between the server and the nodes connected in the
network helps in creation of VPN connection. The site link helps a remote user to connect with
the network resources and thus increases the flexibility of the current network infrastructure. It is
also used for the establishment of connection between the two or more local area network.
iv. Defense in depth
The network architecture should be created according to requirement of the organization
and firewall rules should be set according to the business policy and network compatible
protocol should be used for the configuration of the hardware device installed in the network. An
open path should be identified blocking the intruder to access the devices installed in the core
part of the network.
v. Security Auditing and Monitoring
The firewall policy created for the blocking the unknown sources should be audited for
application of the changes in the organization. The security policy should also be reviewed for
implementation of the changes in the requirement of the organization. Network monitoring tool
can also be installed in the server for identification of the flow of the traffic and protect it from
DDoS attacks.
vi. Threat identification
For the identification of the threat in the network a group of friendly user should be
selected for performing a penetration testing and the flaws in the network should be rectified for
increasing the security of the network. Different encryption algorithm and patches should be
applied for securing the ports in the servers.
NETWORK IMPLEMENTATION
iii. Site to site links
Establishment of a site to site link between the server and the nodes connected in the
network helps in creation of VPN connection. The site link helps a remote user to connect with
the network resources and thus increases the flexibility of the current network infrastructure. It is
also used for the establishment of connection between the two or more local area network.
iv. Defense in depth
The network architecture should be created according to requirement of the organization
and firewall rules should be set according to the business policy and network compatible
protocol should be used for the configuration of the hardware device installed in the network. An
open path should be identified blocking the intruder to access the devices installed in the core
part of the network.
v. Security Auditing and Monitoring
The firewall policy created for the blocking the unknown sources should be audited for
application of the changes in the organization. The security policy should also be reviewed for
implementation of the changes in the requirement of the organization. Network monitoring tool
can also be installed in the server for identification of the flow of the traffic and protect it from
DDoS attacks.
vi. Threat identification
For the identification of the threat in the network a group of friendly user should be
selected for performing a penetration testing and the flaws in the network should be rectified for
increasing the security of the network. Different encryption algorithm and patches should be
applied for securing the ports in the servers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





