Detailed Project Plan: Network Infrastructure and Security Design
VerifiedAdded on 2023/03/30
|7
|1041
|413
Project
AI Summary
This project plan details the network infrastructure and security measures for an organization. It identifies potential network vulnerabilities such as excessive access and infected USB drives, proposing remedies like limiting user access based on PCI requirement 7 and modifying autorun policies. The plan recommends a Cisco SAFE logical topology, divided into service provider edge, enterprise edge, and enterprise campus, alongside a physical GPON design using optical splitters. It emphasizes the importance of firewalls and manageable switches for device placement. Furthermore, it outlines a network security policy, stressing strong password guidelines and server registration. The revised project plan also addresses cloud technology and virtualization implementation, highlighting key stakeholders, business cases, application deployment strategies, IT governance, risk management, and cloud readiness considerations.

Abstract
Week seven, provided in detailed on cloud computing and virtualization technologies.
One of the benefit which was highlighted is that the tow technologies saves on cost and human
capital. In addition, the paper recommended Amazon cloud providers as the best company which
is able to provide cloud computing services. In addition, the paper gave the reasons as to why an
organization needs to settle on Google as the best company that provides virtualization
technologies. In this week, this paper will focus on network infrastructure and security.
Specifically, the paper will have two sections; part one os a network infrastructure document and
part two is a security plan document.
Section one: Infrastructure document
The possible network infrastructure vulnerabilities
Network security is one of the most challenging item than it was several years ago.
Currently organizations are struggling to fight cyber-security due to the increasing number of
end-points in their network. In addition, there is an ever changing cyber-crime.
One of the most common network vulnerability is excessive access. Most of the organization
users are having an excessive access to more data than what they need. This usually has resulted
to integrity issues. USB thumb drives is another common network vulnerability. This is usually
as a result of the internal users using SUB drives which are infected
Vulnerability category Threat
In-put validation Cross-site scripting
Authentication Brute force type of attacks and replaying of
cookies
Cryptography Poor customization encryption
Week seven, provided in detailed on cloud computing and virtualization technologies.
One of the benefit which was highlighted is that the tow technologies saves on cost and human
capital. In addition, the paper recommended Amazon cloud providers as the best company which
is able to provide cloud computing services. In addition, the paper gave the reasons as to why an
organization needs to settle on Google as the best company that provides virtualization
technologies. In this week, this paper will focus on network infrastructure and security.
Specifically, the paper will have two sections; part one os a network infrastructure document and
part two is a security plan document.
Section one: Infrastructure document
The possible network infrastructure vulnerabilities
Network security is one of the most challenging item than it was several years ago.
Currently organizations are struggling to fight cyber-security due to the increasing number of
end-points in their network. In addition, there is an ever changing cyber-crime.
One of the most common network vulnerability is excessive access. Most of the organization
users are having an excessive access to more data than what they need. This usually has resulted
to integrity issues. USB thumb drives is another common network vulnerability. This is usually
as a result of the internal users using SUB drives which are infected
Vulnerability category Threat
In-put validation Cross-site scripting
Authentication Brute force type of attacks and replaying of
cookies
Cryptography Poor customization encryption
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Remedy to the network vulnerabilities
Excessive data access is reflected in PCI requirement 7, this requires organizations to be
compliant to limit access according to the user needs. In addition, this limits access based on the
need to know. Also excessive access is usually caused by manual network security practices.
USB thumb drives can be prevented by changing the default autorun policies. Other network
vulnerabilities are as shown by the table below
Logical topological layout of the planned layout
The recommended topology in this case is Cisco SAFE logical topological. With this
type of topology an organization is able to achieve technical and business goals. The major
principle of this type of logical design is that it provides the very best practices for implementing
and designing a secure network. Cisco SAFE logical topology uses what is known as modular
approach. In addition, the topology takes what network engineers refer to as defense-in-depth
approach so as to allow flexibility and network troubleshooting. The logical topology will be
divided into three main areas which are; service provider edge, enterprise edge, and enterprise
campus. Service provider edge is used in this case, this functional area is used to represent WAN
and internet connection. The enterprise edge will specifically be used for remote connection. The
enterprise campus is required for independent operations within only one campus.
The logical topology is as shiwn by the figure below
Figure 1: Cisco SAFE logical design
Excessive data access is reflected in PCI requirement 7, this requires organizations to be
compliant to limit access according to the user needs. In addition, this limits access based on the
need to know. Also excessive access is usually caused by manual network security practices.
USB thumb drives can be prevented by changing the default autorun policies. Other network
vulnerabilities are as shown by the table below
Logical topological layout of the planned layout
The recommended topology in this case is Cisco SAFE logical topological. With this
type of topology an organization is able to achieve technical and business goals. The major
principle of this type of logical design is that it provides the very best practices for implementing
and designing a secure network. Cisco SAFE logical topology uses what is known as modular
approach. In addition, the topology takes what network engineers refer to as defense-in-depth
approach so as to allow flexibility and network troubleshooting. The logical topology will be
divided into three main areas which are; service provider edge, enterprise edge, and enterprise
campus. Service provider edge is used in this case, this functional area is used to represent WAN
and internet connection. The enterprise edge will specifically be used for remote connection. The
enterprise campus is required for independent operations within only one campus.
The logical topology is as shiwn by the figure below
Figure 1: Cisco SAFE logical design
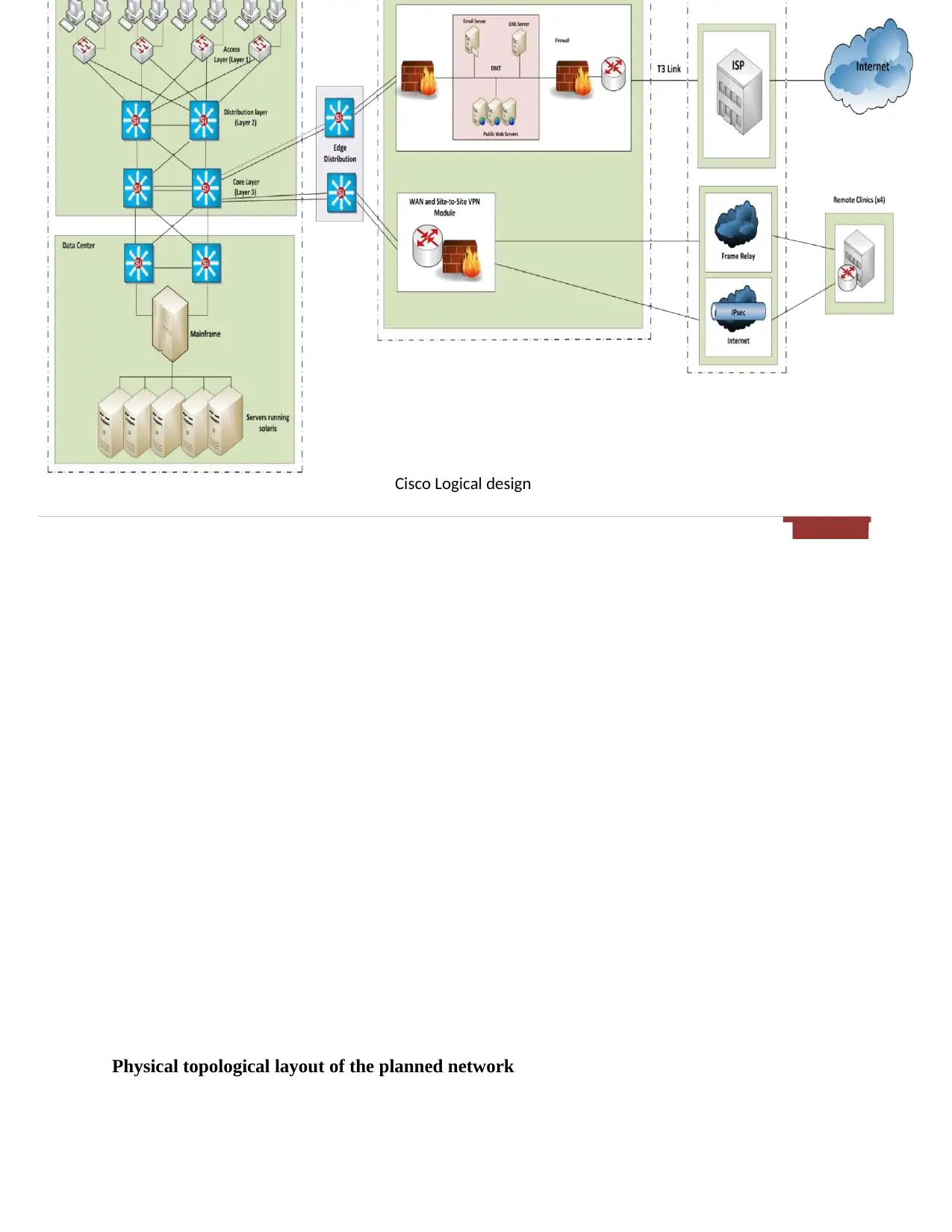
Physical topological layout of the planned network
Cisco Logical design
Cisco Logical design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

A physical design usually demonstrates the direction of physical design implementation.
For this case, this paper will go for GPON type of design. This type of technology is also
reffered to as Passive Optical Networking technology this involves which involves the use of
optical splitters so as to divide one optical connection to serve several points.
Taking the deign requirements of the above logical topology, one can pass one fibre from an
Optical Line Termina point then to every point of connection and then split it off using what is
known as 1:32 splitter then into the 32 various connections. This is as shown by figure two
below
Figure 2: physical GPON connection
For this case, this paper will go for GPON type of design. This type of technology is also
reffered to as Passive Optical Networking technology this involves which involves the use of
optical splitters so as to divide one optical connection to serve several points.
Taking the deign requirements of the above logical topology, one can pass one fibre from an
Optical Line Termina point then to every point of connection and then split it off using what is
known as 1:32 splitter then into the 32 various connections. This is as shown by figure two
below
Figure 2: physical GPON connection
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Possible placement of devices
Having a comprehensive a logical and physical network design facilitates the identity of
propable issues. When a visitor wants to access the network to generate a map of the network
they will better appreaciate the security check-point for the firewalls or a similar device. Firewall
will be automatically be placed on before the organization router. After the router is the
manageable switch where then all the servers will connect from there.
Network security policy
Having a comprehensive a logical and physical network design facilitates the identity of
propable issues. When a visitor wants to access the network to generate a map of the network
they will better appreaciate the security check-point for the firewalls or a similar device. Firewall
will be automatically be placed on before the organization router. After the router is the
manageable switch where then all the servers will connect from there.
Network security policy

A security policy is specifically designated for security controls without specifying the
technologies and also the high-level specifications on unacceptable and acceptable actions so as
to protect the critical assests. A network policy needs to be applied throughout the company.
Password is very essential aspect for computer security. All the system-level passwords like root,
NT admin, the application administration accounts ought to be changed on quarterly basis. All
the production system-level passwords ought to be part of the InforSec administered global
password. All the user-level passwords like the desktops passwords need to be chabged at least
every six months. The guidelines of setting passwords, all the passwords need to have not less
that eight caracters. A Strong password is the one which contains lower and upper case
characters, have not less that eight alphanumeric characters long, password should not be written
down or stored on-line.
All the organizational servers must be registred within the company enterprise management
which ought to be a minium of server contacts and the location, the hardware and operating
system and version and the main functions of the server and applicvations. The general
configuration guidelines needws to be in accordance with the approved InfoSec guidelines. All
the applications and services which are not being used needs to be all be disabled and all the
access services ought to be logged and preotected via access control methods
Section 2: Revised project plan
To implement cloud technology and virtualization, an organization needs to indentify all the
organization goals and the key stakeholders. The important stakeholders here are the project
sponsors.The cloud business case are creating a business case and funding model, adequate
provisioning server capacity, implementing process, policy, and role changes, building
awareness of the available services, and loss of visibility control.
technologies and also the high-level specifications on unacceptable and acceptable actions so as
to protect the critical assests. A network policy needs to be applied throughout the company.
Password is very essential aspect for computer security. All the system-level passwords like root,
NT admin, the application administration accounts ought to be changed on quarterly basis. All
the production system-level passwords ought to be part of the InforSec administered global
password. All the user-level passwords like the desktops passwords need to be chabged at least
every six months. The guidelines of setting passwords, all the passwords need to have not less
that eight caracters. A Strong password is the one which contains lower and upper case
characters, have not less that eight alphanumeric characters long, password should not be written
down or stored on-line.
All the organizational servers must be registred within the company enterprise management
which ought to be a minium of server contacts and the location, the hardware and operating
system and version and the main functions of the server and applicvations. The general
configuration guidelines needws to be in accordance with the approved InfoSec guidelines. All
the applications and services which are not being used needs to be all be disabled and all the
access services ought to be logged and preotected via access control methods
Section 2: Revised project plan
To implement cloud technology and virtualization, an organization needs to indentify all the
organization goals and the key stakeholders. The important stakeholders here are the project
sponsors.The cloud business case are creating a business case and funding model, adequate
provisioning server capacity, implementing process, policy, and role changes, building
awareness of the available services, and loss of visibility control.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The applications which are to be deployed to the cloud and the existing applications are migrated
based on the ROI, difficulty, and suitability. Some of the consideration to made in this case is IT
governance and risk management. Also operation and service management is to be made. The
areas of importance to cloud readiness are model packaging, capacity management, service
portfolio management, business and IT drives, executive sponsorship and service monitoring.
based on the ROI, difficulty, and suitability. Some of the consideration to made in this case is IT
governance and risk management. Also operation and service management is to be made. The
areas of importance to cloud readiness are model packaging, capacity management, service
portfolio management, business and IT drives, executive sponsorship and service monitoring.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




