MN692 Capstone Project: Implementation of Intrusion Detection System
VerifiedAdded on 2021/06/15
|20
|4252
|34
Capstone Project
AI Summary
This capstone project, MN692, focuses on the development and implementation of a Network Intrusion Detection System (NIDS). The project begins with an introduction to the increasing need for online security due to the rise of internet usage and cyber threats, then delves into the design, implementation, and block diagram of a NIDS using Snort. The project details the software and hardware requirements, including Snort, HoneyD, Virtual Box, Windows 10, and WEKA, along with the weekly activities and roles of team members. It covers both signature-based and anomaly-based detection methods. The implementation section explains the use of Snort for monitoring malicious traffic and HoneyD to capture attacker details. Furthermore, the project includes installation steps, detection methods, and provides details about the architecture of the system. The project uses Snort for intrusion detection, detailing its configuration and testing. The report also includes result analysis, demonstrating the practical application and effectiveness of the developed NIDS.

MN692 Capstone ProjectNetwork Intrusion Detection System
Contents
1. Introduction..............................................................................................................................2
.....................................................................................................................................................6
3.Table of weekly Activities for MN692.....................................................................................6
4. Roles & Responsibilities of each team member......................................................................7
Implementation of snort.................................................................................................................11
Operating with Snort..................................................................................................................12
Testing snort..................................................................................................................................15
Testing snort basic principles....................................................................................................15
Verification of snort intrusion:......................................................................................................15
Result Analysis as well as evaluation............................................................................................16
Experiment one..........................................................................................................................17
Results Analysis.........................................................................................................................17
Experiment2...............................................................................................................................18
Results Analysis.........................................................................................................................19
WEKA...........................................................................................................................................19
Conclusion.....................................................................................................................................20
8.References...................................................................................................................................21
Contents
1. Introduction..............................................................................................................................2
.....................................................................................................................................................6
3.Table of weekly Activities for MN692.....................................................................................6
4. Roles & Responsibilities of each team member......................................................................7
Implementation of snort.................................................................................................................11
Operating with Snort..................................................................................................................12
Testing snort..................................................................................................................................15
Testing snort basic principles....................................................................................................15
Verification of snort intrusion:......................................................................................................15
Result Analysis as well as evaluation............................................................................................16
Experiment one..........................................................................................................................17
Results Analysis.........................................................................................................................17
Experiment2...............................................................................................................................18
Results Analysis.........................................................................................................................19
WEKA...........................................................................................................................................19
Conclusion.....................................................................................................................................20
8.References...................................................................................................................................21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
The use of internet has increased with the advancement in technology such as smart phones
and high-speed internet. With the increase in a number of web users, the demand for online security
has increased as well in order to protect digital frameworks from various security breaches. The online
security breaches and cyber-attacks resulted in compromising security; integrity and authenticity of a
network because it allows cybercriminals to conduct illegal activities such as file modification and
unauthorised access to confidential data [1]. Organisations can use Intrusion Detection System (IDC)
which is a software application that monitors the network for policy violations or malicious practices.
The detection system are divided in two groups 1. Is Host based intrusion detection system and the
other 2. Network based intrusion detection system[2]. In previous few years, the development in
network security and network-based services has become a crucial factor for organisations. In order to
ensure security of networks and identify different cyber-attacks, companies used anomaly-based
network intrusion detection technique. Techniques which are used in anomaly-based network intrusion
detection include knowledge-based, machine learning based, and statistical based.[3] Companies face
challenges while using different security methods, which are based on existing network data characters,
in order to improve their performance. The Network Intrusion Detection System (NIDS) is installed by
corporations at key points of the networkin order to check traffic from and to all hosts that are using a
network [4].This report will focus on the network intrusion detection system, and it will include the
background of the topic, and requirements of the project.
2
The use of internet has increased with the advancement in technology such as smart phones
and high-speed internet. With the increase in a number of web users, the demand for online security
has increased as well in order to protect digital frameworks from various security breaches. The online
security breaches and cyber-attacks resulted in compromising security; integrity and authenticity of a
network because it allows cybercriminals to conduct illegal activities such as file modification and
unauthorised access to confidential data [1]. Organisations can use Intrusion Detection System (IDC)
which is a software application that monitors the network for policy violations or malicious practices.
The detection system are divided in two groups 1. Is Host based intrusion detection system and the
other 2. Network based intrusion detection system[2]. In previous few years, the development in
network security and network-based services has become a crucial factor for organisations. In order to
ensure security of networks and identify different cyber-attacks, companies used anomaly-based
network intrusion detection technique. Techniques which are used in anomaly-based network intrusion
detection include knowledge-based, machine learning based, and statistical based.[3] Companies face
challenges while using different security methods, which are based on existing network data characters,
in order to improve their performance. The Network Intrusion Detection System (NIDS) is installed by
corporations at key points of the networkin order to check traffic from and to all hosts that are using a
network [4].This report will focus on the network intrusion detection system, and it will include the
background of the topic, and requirements of the project.
2

2. Design, implementation and block diagram
Network Intrusion Detection System (NIDS) is further protection which examines network
activity to detect attacks or intrusions. NIDS systems can be hardware and software based devices used
to examine an attack. NIDS products are being used to observe connection in detect whether attacks
have been launched. NIDS systems just monitor and generate the alert of an attack, whereas others try
to block the attack.
The network intrusion detection systems can detect several types of the attacks that use the
network. NIDS are excellent for detecting access without authority or some kinds of access in excess of
authority. A NIDS does not require much modification for production hosts or servers. It is benefit
because these servers regularly have close operating system for CPU and installing additional software
updates may exceed the systems capacities. Most NIDSs are quite easy to deploy on a network and can
observe traffic from multiple machines at once.[5]
Figure 1
We are using Snort for the network intrusion detection system. Snort is principally a rule-
oriented detection system to capture the intrusion. It can perform real-time traffic monitoring, analysis
and packet logging on Internet Protocol (IP) networks. Snort reads the rules at the start-up time which
can be predefined or customised and builds internal data structures or chains to apply these rules to
captured data. Snort is accessible with a various.
3
Network Intrusion Detection System (NIDS) is further protection which examines network
activity to detect attacks or intrusions. NIDS systems can be hardware and software based devices used
to examine an attack. NIDS products are being used to observe connection in detect whether attacks
have been launched. NIDS systems just monitor and generate the alert of an attack, whereas others try
to block the attack.
The network intrusion detection systems can detect several types of the attacks that use the
network. NIDS are excellent for detecting access without authority or some kinds of access in excess of
authority. A NIDS does not require much modification for production hosts or servers. It is benefit
because these servers regularly have close operating system for CPU and installing additional software
updates may exceed the systems capacities. Most NIDSs are quite easy to deploy on a network and can
observe traffic from multiple machines at once.[5]
Figure 1
We are using Snort for the network intrusion detection system. Snort is principally a rule-
oriented detection system to capture the intrusion. It can perform real-time traffic monitoring, analysis
and packet logging on Internet Protocol (IP) networks. Snort reads the rules at the start-up time which
can be predefined or customised and builds internal data structures or chains to apply these rules to
captured data. Snort is accessible with a various.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
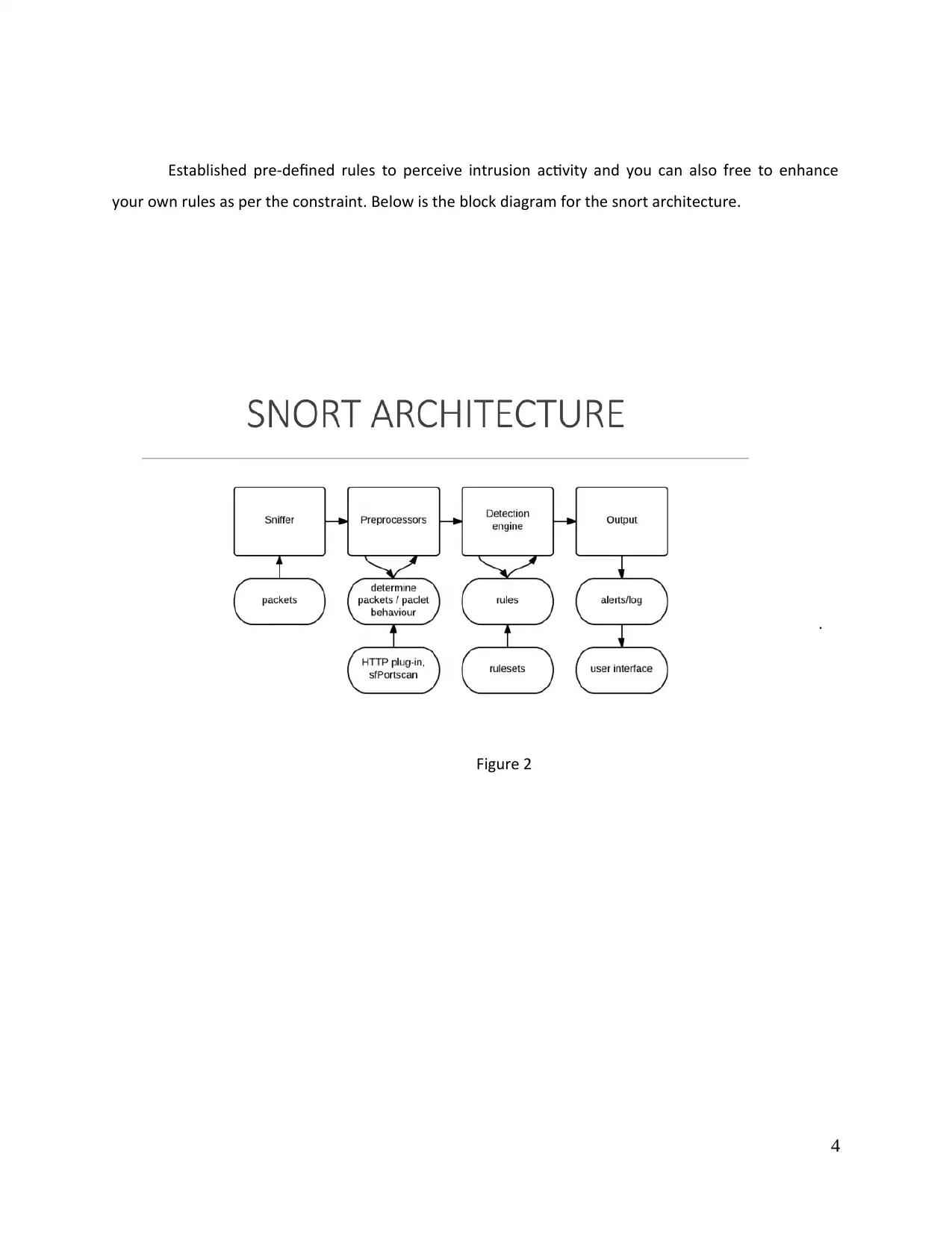
Established pre-defined rules to perceive intrusion activity and you can also free to enhance
your own rules as per the constraint. Below is the block diagram for the snort architecture.
.
Figure 2
4
your own rules as per the constraint. Below is the block diagram for the snort architecture.
.
Figure 2
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Block diagram of Network intrusion detection system
Figure 3
5
Figure 3
5
The above figure is a bock [6] of network intrusion detection system, where it captures the
incoming traffic using wire shark, captured data is sent into the detection mode where it analyses the
files in batch mode and before forwarding it to the system, data is being filtered which leads to
elimination of the network traffic.[7] Once the data id filtered all the known attacks which are signature
based are removed and analysed, after analysing the known attacks it is send to anomaly based
detection technique where it uses association pattern analysis to detect the malicious traffic and notes
its signature so that it can be stored as signature based detection technique.
.
3.Table of weekly Activities for MN692
Week
Number
Activity
Week -1 Will be authenticating all the details and activity to be performed in this
stage of the project from the research done in the previous stage to
complete the project effectively. Doing research on some data
collection method with the help of some basic tools on network traffic,
IP source and destination and packet capture from the network for
network intrusion detection system.
Week-2 To reduce the obscurity and uncontaminated network data for the
research method to be used to get the final outcome, the pre-
processing research method will be used to relate to the data.
Week-3 The concept research method is on use are data mining technique,
which will be used to exploration and understand the application of
decision-tree algorithm.
Week-4 Considerate and illustrative doubts on One-class support vector
machine (1-class SVM).
Week-5 The software required for packet sniffing is snort, which is required to
be installed and configure the rules of snort.
Week-6 Authentication the rules of snort appropriately and cross checking the
6
incoming traffic using wire shark, captured data is sent into the detection mode where it analyses the
files in batch mode and before forwarding it to the system, data is being filtered which leads to
elimination of the network traffic.[7] Once the data id filtered all the known attacks which are signature
based are removed and analysed, after analysing the known attacks it is send to anomaly based
detection technique where it uses association pattern analysis to detect the malicious traffic and notes
its signature so that it can be stored as signature based detection technique.
.
3.Table of weekly Activities for MN692
Week
Number
Activity
Week -1 Will be authenticating all the details and activity to be performed in this
stage of the project from the research done in the previous stage to
complete the project effectively. Doing research on some data
collection method with the help of some basic tools on network traffic,
IP source and destination and packet capture from the network for
network intrusion detection system.
Week-2 To reduce the obscurity and uncontaminated network data for the
research method to be used to get the final outcome, the pre-
processing research method will be used to relate to the data.
Week-3 The concept research method is on use are data mining technique,
which will be used to exploration and understand the application of
decision-tree algorithm.
Week-4 Considerate and illustrative doubts on One-class support vector
machine (1-class SVM).
Week-5 The software required for packet sniffing is snort, which is required to
be installed and configure the rules of snort.
Week-6 Authentication the rules of snort appropriately and cross checking the
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

software required for snort and works perfectly to initiated the project.
Week-7 To build the research method which is the hybrid detection method?
Week-8 To improve the intrusion detection method and also to assess and
random test the system.
Week-9 To do a complete verification of the project in accordance to our
project requirement and accomplishing all the task assigned to
compete and to organize for demonstration of project.
Week-10 Report Writing for the final document.
Week-11 Ongoing report writing and oral presentation document.
Week-12 Finishing the final report and assembly the limitation of the project if
any or submit the final report and prepare for demonstration
.
4. Roles & Responsibilities of each team member
Week # Vinod Allam Solomon waskar Rakesh nunna Abdul Rasheed
Week -1 To comprehend
and validating
the details of the
project and
implementing.
Exploration on
Network data
abstraction.
Extraction of the
rules required for
snort.
To get acquaintance
with ‘Honey D’ and
other network
configuration for
the computer.
Week-2 Complete
understanding of
pre-processing
methods.
Scrutiny on the pre-
processing systems
such as
Normalization,
Discretization and
Feature range.
Congregation and
substantiating
Configure the
snort as per the
rules required for
the project.
Reading from IEEE
journals on SVM
(support vector
machine) model to
create decomposed
subnet.
7
Week-7 To build the research method which is the hybrid detection method?
Week-8 To improve the intrusion detection method and also to assess and
random test the system.
Week-9 To do a complete verification of the project in accordance to our
project requirement and accomplishing all the task assigned to
compete and to organize for demonstration of project.
Week-10 Report Writing for the final document.
Week-11 Ongoing report writing and oral presentation document.
Week-12 Finishing the final report and assembly the limitation of the project if
any or submit the final report and prepare for demonstration
.
4. Roles & Responsibilities of each team member
Week # Vinod Allam Solomon waskar Rakesh nunna Abdul Rasheed
Week -1 To comprehend
and validating
the details of the
project and
implementing.
Exploration on
Network data
abstraction.
Extraction of the
rules required for
snort.
To get acquaintance
with ‘Honey D’ and
other network
configuration for
the computer.
Week-2 Complete
understanding of
pre-processing
methods.
Scrutiny on the pre-
processing systems
such as
Normalization,
Discretization and
Feature range.
Congregation and
substantiating
Configure the
snort as per the
rules required for
the project.
Reading from IEEE
journals on SVM
(support vector
machine) model to
create decomposed
subnet.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Week-3 To get
acquaintance
with decision
tree algorithm
To better understand
the gain based
decision tree
algorithm and
research on gain
calculation for the
implementation.
To build a normal
algorithm for the
requirement of
project.
To contribute the
known from the
svm and explain the
team member for
construct hybrid
detection system
Week-4 To understand all
the
documentation
and research
done and
illustrative the
quires with
supervisor and
team member as
start the project.
To see all the
documentation and
research done and
illustrative the quires
with supervisor and
team member as
begin the project
implementation.
Joining all the
exploration done
till now and
illustrative the
questions with all
team member and
supervisor to
begin building of
the project.
Consolidating all the
examination done
till now and
illustrative the
questions with all
the team member
and supervisor to
begin building and
introducing the
project.
Week-5 Install virtual box
and wire-shark.
Installation of snort
subscription software
and win-cap.
To understand
and configure the
rules for snort.
To test if the
configured snort is
running correctly as
per requirement.
Week-6 Enduring the
configuration
steps of software.
Continuing the
configuration steps
of Snort.
To check for more
better
configuration of
snort
To check if the snort
is capturing data as
per requirement.
Week-7 Structure the
decision-tree
algorithm.
Script test situation
to the logic of
decision-tree
algorithm.
Scripting test
circumstances to
one-class SVM.
Construction of the
one-class SVM
detection
algorithm.
8
acquaintance
with decision
tree algorithm
To better understand
the gain based
decision tree
algorithm and
research on gain
calculation for the
implementation.
To build a normal
algorithm for the
requirement of
project.
To contribute the
known from the
svm and explain the
team member for
construct hybrid
detection system
Week-4 To understand all
the
documentation
and research
done and
illustrative the
quires with
supervisor and
team member as
start the project.
To see all the
documentation and
research done and
illustrative the quires
with supervisor and
team member as
begin the project
implementation.
Joining all the
exploration done
till now and
illustrative the
questions with all
team member and
supervisor to
begin building of
the project.
Consolidating all the
examination done
till now and
illustrative the
questions with all
the team member
and supervisor to
begin building and
introducing the
project.
Week-5 Install virtual box
and wire-shark.
Installation of snort
subscription software
and win-cap.
To understand
and configure the
rules for snort.
To test if the
configured snort is
running correctly as
per requirement.
Week-6 Enduring the
configuration
steps of software.
Continuing the
configuration steps
of Snort.
To check for more
better
configuration of
snort
To check if the snort
is capturing data as
per requirement.
Week-7 Structure the
decision-tree
algorithm.
Script test situation
to the logic of
decision-tree
algorithm.
Scripting test
circumstances to
one-class SVM.
Construction of the
one-class SVM
detection
algorithm.
8

Week-8 Continuation
building the
decision-tree
algorithm.
Extension testing the
logic of decision-tree
algorithm.
Additional testing
the logic of one-
class SVM.
Building the one-
class SVM detection
algorithm.
Week-9 Assess and start
acceptance test.
Evaluate and start
acceptance test.
Appraise and start
acceptance test.
Gage and start
acceptance test.
Week-
10
For the final
report divide the
task equally and
to complete
report.
Writing on the fix and
evaluation part of the
report and also fix
issues in project.
To complete the
writing on weekly
report and
problem fixing of
project.
Scrutiny of the
project and its
limitation if any.
Week-
11
Structuring the
final report and
dividing the oral
presentation to
each team
member.
Preparing for
presentation on
evaluation step by
step procedure.
Oral presentation
on decision tree
and one class svm.
Will be writing
troubleshooting
steps.
Week-
12
To collect all the
data and ready
for the
demonstration
on the project
Fixing any trouble
shooting in the
project and
demonstration.
Finding any
project limitation
and fixing it.
Compiling all the
document and oral
presentation and
giving it for final
proof reading.
5. Installation
Network intrusion detection system, virtual box is installed in the computer in order to
simulate the process. Windows is used as the main platform in order to perform. Windows 10 OS is
installed in virtual Box, after installing windows snort is being installed and configured according to
requirements in order to monitor incoming traffic. Honey D is being deployed in the system in order to
9
building the
decision-tree
algorithm.
Extension testing the
logic of decision-tree
algorithm.
Additional testing
the logic of one-
class SVM.
Building the one-
class SVM detection
algorithm.
Week-9 Assess and start
acceptance test.
Evaluate and start
acceptance test.
Appraise and start
acceptance test.
Gage and start
acceptance test.
Week-
10
For the final
report divide the
task equally and
to complete
report.
Writing on the fix and
evaluation part of the
report and also fix
issues in project.
To complete the
writing on weekly
report and
problem fixing of
project.
Scrutiny of the
project and its
limitation if any.
Week-
11
Structuring the
final report and
dividing the oral
presentation to
each team
member.
Preparing for
presentation on
evaluation step by
step procedure.
Oral presentation
on decision tree
and one class svm.
Will be writing
troubleshooting
steps.
Week-
12
To collect all the
data and ready
for the
demonstration
on the project
Fixing any trouble
shooting in the
project and
demonstration.
Finding any
project limitation
and fixing it.
Compiling all the
document and oral
presentation and
giving it for final
proof reading.
5. Installation
Network intrusion detection system, virtual box is installed in the computer in order to
simulate the process. Windows is used as the main platform in order to perform. Windows 10 OS is
installed in virtual Box, after installing windows snort is being installed and configured according to
requirements in order to monitor incoming traffic. Honey D is being deployed in the system in order to
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
capture the attacker’s details. All these applications are being installed to neutralise the attacks using
algorithms.
5.1 Implementation
Snort [8] is being deployed to monitor the malicious traffic using signature and anomaly based
detections, it displays required information regarding the incoming and outgoing traffic that is being
captured by the wire shark and analyses the traffic by using algorithms. All this applications are being
deployed inside the OS and incoming traffic is being monitored regularly. HoneyD acts as a trap in order
to capture the incoming requests by the attackers by acting as a main server and noting attacker’s
details.
6. REQUIREMENTS
6.1 Software Requirements
Applications that are being installed
SOFTWARE VERSION
Snort 2.9
HoneyD 1.5
Virtual Box 5.2
Windows 10
Weka 3.8
6.2 Hardware requirements
2 personnel computers
Specifications
8 GB ram
I5 processor
2 GB graphic card
500 GB hard disk
10
algorithms.
5.1 Implementation
Snort [8] is being deployed to monitor the malicious traffic using signature and anomaly based
detections, it displays required information regarding the incoming and outgoing traffic that is being
captured by the wire shark and analyses the traffic by using algorithms. All this applications are being
deployed inside the OS and incoming traffic is being monitored regularly. HoneyD acts as a trap in order
to capture the incoming requests by the attackers by acting as a main server and noting attacker’s
details.
6. REQUIREMENTS
6.1 Software Requirements
Applications that are being installed
SOFTWARE VERSION
Snort 2.9
HoneyD 1.5
Virtual Box 5.2
Windows 10
Weka 3.8
6.2 Hardware requirements
2 personnel computers
Specifications
8 GB ram
I5 processor
2 GB graphic card
500 GB hard disk
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7. Detection methods
IDS is mainly classified into two types (i) signature based (ii) anomaly based detection system
7.1 Signature based:
Signature based detection algorithm [9] notes all the signatures of the malicious activities that has
happened before and stores it signatures in order to detect it. Signature based detection is mainly based
on the attacks that has been happened before
7.2 Anomaly based
Anomaly based detection[9] is mainly based on the behaviour of the traffic, each packet is analysed
thoroughly and divided into parts and in case of any malicious behaviour is found the packet is being
dropped.
Implementation of snort
Linux should be used to implement Snort. The process is made painless and easy by Ubuntu – easier
than to install Snort as well as to configure Windows server. Snort sensors must be seen as apparatuses
(such as UPS or a router) and hence, do not require to coordinate with the server infrastructure.
Actually, one presumably have other system apparatuses running on some versions of Linux. One final
thought is if ones’ intrusion detecting framework is on a similar platform like the rest of the
frameworks, it might progress toward becoming compromised alongside different systems in case of an
effective intrusion.
For minor fittings, a single PC can house the organization applications (ACID and Snort Center and)
screen the network. In bigger organizations, one will presumably need to isolate these capacities. One
PC can play out the administration roles while different PCs acts like sensors. Fig 1 demonstrates a
common course of action of sensors inside a medium measured system. Ubuntu is intended to give a
safe, lightweight condition and, in this way, runs just a negligible arrangement of ordinary Linux services.
11
IDS is mainly classified into two types (i) signature based (ii) anomaly based detection system
7.1 Signature based:
Signature based detection algorithm [9] notes all the signatures of the malicious activities that has
happened before and stores it signatures in order to detect it. Signature based detection is mainly based
on the attacks that has been happened before
7.2 Anomaly based
Anomaly based detection[9] is mainly based on the behaviour of the traffic, each packet is analysed
thoroughly and divided into parts and in case of any malicious behaviour is found the packet is being
dropped.
Implementation of snort
Linux should be used to implement Snort. The process is made painless and easy by Ubuntu – easier
than to install Snort as well as to configure Windows server. Snort sensors must be seen as apparatuses
(such as UPS or a router) and hence, do not require to coordinate with the server infrastructure.
Actually, one presumably have other system apparatuses running on some versions of Linux. One final
thought is if ones’ intrusion detecting framework is on a similar platform like the rest of the
frameworks, it might progress toward becoming compromised alongside different systems in case of an
effective intrusion.
For minor fittings, a single PC can house the organization applications (ACID and Snort Center and)
screen the network. In bigger organizations, one will presumably need to isolate these capacities. One
PC can play out the administration roles while different PCs acts like sensors. Fig 1 demonstrates a
common course of action of sensors inside a medium measured system. Ubuntu is intended to give a
safe, lightweight condition and, in this way, runs just a negligible arrangement of ordinary Linux services.
11

Operating with Snort
So as to utilize Snort like an Intrusion Detecting System, first snort should be downloaded from its
official site (www.snort.org). Then snort should be designed through the following steps.
• using VirtualBox, install a virtual machine Ubuntu.
• introduce and then design Snort in the Ubuntu machine.
• Open up a terminal by hitting the highest symbol on the left corner to scan for the terminal
application.
• After opening the terminal, type across the board line (in the accompanying summon):"sudo
aptget install flex bison buildessential checkinstall libpcapdev libnet1dev libpcre3dev
libmysqlclient15dev libnetfilterqueuedeviptablesdev"
• Password will be asked for and the login password will be entered to the VM.
• The chosen applications are by then being installed. A prompt might sometime arise requesting
to proceed, type "y"' then proceed.
Building and installation of libdnet from the source code.
1. Type “wget https://libdnet.googlecode.com/files/libdnet1.12.tgz”. Press enter.
2. If you key in “ls”, the file will be downloaded to the home directory. The command: tar xvfvz
libdnet1.12.tgz will be issued. Press Enter.
3. This will unpack every file that was inside the libdnet112.tgz folder and forms a libdnet112
manual. Convert to the libdnet112 directory.
4. Type: ./configure "CFLAGS=fPIC". Press enter. The "fPIC" C flag is important when it is compiled
on 64bit basis.
5. Type “make”. Key in enter.
6. Key in “sudo checkinstall”. The command, checkinstall above will form .deb package. Then will
ask several questions. Agree default values.
12
So as to utilize Snort like an Intrusion Detecting System, first snort should be downloaded from its
official site (www.snort.org). Then snort should be designed through the following steps.
• using VirtualBox, install a virtual machine Ubuntu.
• introduce and then design Snort in the Ubuntu machine.
• Open up a terminal by hitting the highest symbol on the left corner to scan for the terminal
application.
• After opening the terminal, type across the board line (in the accompanying summon):"sudo
aptget install flex bison buildessential checkinstall libpcapdev libnet1dev libpcre3dev
libmysqlclient15dev libnetfilterqueuedeviptablesdev"
• Password will be asked for and the login password will be entered to the VM.
• The chosen applications are by then being installed. A prompt might sometime arise requesting
to proceed, type "y"' then proceed.
Building and installation of libdnet from the source code.
1. Type “wget https://libdnet.googlecode.com/files/libdnet1.12.tgz”. Press enter.
2. If you key in “ls”, the file will be downloaded to the home directory. The command: tar xvfvz
libdnet1.12.tgz will be issued. Press Enter.
3. This will unpack every file that was inside the libdnet112.tgz folder and forms a libdnet112
manual. Convert to the libdnet112 directory.
4. Type: ./configure "CFLAGS=fPIC". Press enter. The "fPIC" C flag is important when it is compiled
on 64bit basis.
5. Type “make”. Key in enter.
6. Key in “sudo checkinstall”. The command, checkinstall above will form .deb package. Then will
ask several questions. Agree default values.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




