Network Intrusion Detection Project: Statistical Function Analysis
VerifiedAdded on 2023/01/20
|17
|4314
|96
Project
AI Summary
This project examines network intrusion detection using statistical functions to enhance system security. It begins with an abstract summarizing the project's goals: detecting and mitigating network intrusions. The introduction highlights the importance of intrusion detection systems (IDS) in identifying unauthorized access and suspicious activities, emphasizing the role of statistical functions in analyzing network traffic. The project provides a background on the prevalence of network hacking and the need for robust security measures, discussing the controls such as firewalls, routers and virus scanners. The motivation behind the project is to develop a secure system, quickly identify intrusions, and act as a deterrent. The project outlines the scope, objectives, and risk management strategies. The project aims to identify system vulnerabilities, implement intrusion detection tools, and train users on security best practices. The project also addresses ethical considerations and potential risks, such as employee negligence, USB drive vulnerabilities, email scams, and software vulnerabilities. The project includes a Gantt chart to illustrate the project timeline and deliverables. This project is a comprehensive analysis of network intrusion detection, providing valuable insights into system security and risk management.

Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
Insert Your Name Here
Insert Your Tutor’s Name Here
Institution Affiliation
Date
NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
Insert Your Name Here
Insert Your Tutor’s Name Here
Institution Affiliation
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
Abstract
System security, is one of the major issues on most network systems. The security issues has to be
monitored on both, the network and the software system being used. System insecurity is one of the
major issues today. The project is meant to perform an intrusion detection on the network using the
statistical function. The intruders of the system tend to have an ill intention once the have access into
the network. They may vandalize a lot of data and system functionalities.
After research, there were a number of risks that were identified and ways to manage the risks
discovered. This shows that the risk identified have solutions.
In conclusion, is it wise to find the flaws in the network, in order to have a secure system. The
statistical function, is the method used in detecting intrusion is a network in this project. By ensuring
we have secure networks, then the systems will function effectively.
Introduction
An intrusion detection system is used to check the network for any suspicious activity or any
unauthorized intrusion into the entire system. People who intrude the system have no good intention in
the activities they do in the system. When an intrusion in the system is detect an alert should be sent to
the people in charge of the system such as the system administrator or the network administrators. The
action that should be taken is first blocking the IP that is being used by the suspicious access. The
hackers tend to use automated systems to get accesses into the system. These tools may fail to be
detected by the firewall leading to having the access into the network (Singh, Goyal & Agarwal, 2014).
The intrusion detection system tend to find what has accessed the network past the firewall. The
performance of the network detection tools is better compared to the firewall. The IDS tends to perform
traffic analysis in any network.
Background
From research, there are many complains that most system networks have been hacked. This shows
that most companies have defaults in their systems. System security is one of the most important things
to consider in the technological area. Without security, a system is prone to vandalism by hackers. A
company could experience data, data distortion, data being stolen and many other issues. Any system
Abstract
System security, is one of the major issues on most network systems. The security issues has to be
monitored on both, the network and the software system being used. System insecurity is one of the
major issues today. The project is meant to perform an intrusion detection on the network using the
statistical function. The intruders of the system tend to have an ill intention once the have access into
the network. They may vandalize a lot of data and system functionalities.
After research, there were a number of risks that were identified and ways to manage the risks
discovered. This shows that the risk identified have solutions.
In conclusion, is it wise to find the flaws in the network, in order to have a secure system. The
statistical function, is the method used in detecting intrusion is a network in this project. By ensuring
we have secure networks, then the systems will function effectively.
Introduction
An intrusion detection system is used to check the network for any suspicious activity or any
unauthorized intrusion into the entire system. People who intrude the system have no good intention in
the activities they do in the system. When an intrusion in the system is detect an alert should be sent to
the people in charge of the system such as the system administrator or the network administrators. The
action that should be taken is first blocking the IP that is being used by the suspicious access. The
hackers tend to use automated systems to get accesses into the system. These tools may fail to be
detected by the firewall leading to having the access into the network (Singh, Goyal & Agarwal, 2014).
The intrusion detection system tend to find what has accessed the network past the firewall. The
performance of the network detection tools is better compared to the firewall. The IDS tends to perform
traffic analysis in any network.
Background
From research, there are many complains that most system networks have been hacked. This shows
that most companies have defaults in their systems. System security is one of the most important things
to consider in the technological area. Without security, a system is prone to vandalism by hackers. A
company could experience data, data distortion, data being stolen and many other issues. Any system

Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
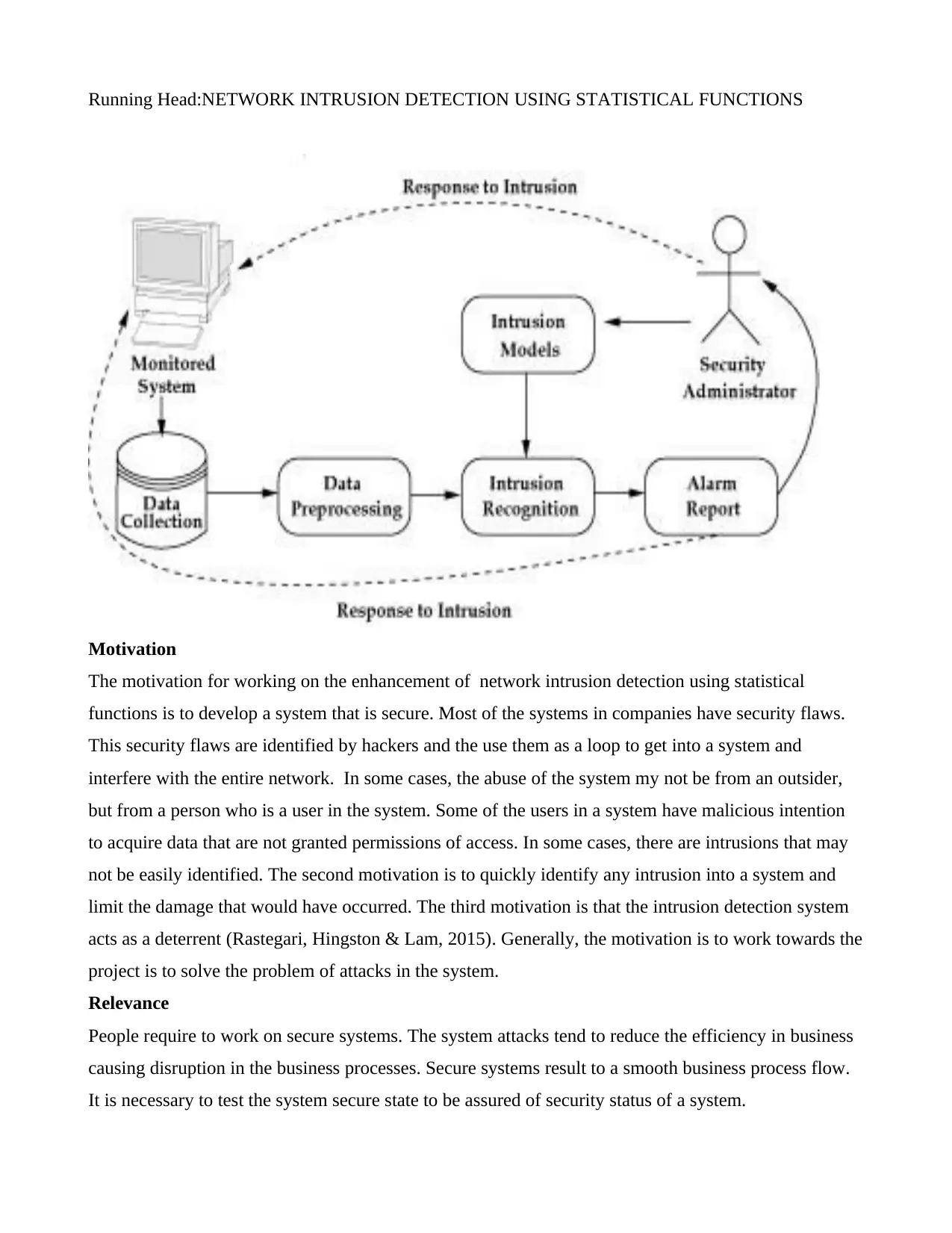
is should be secure and frequent monitoring of the system and the entire network is necessary.
The processes involves some overlapping controls that are used in preventing any intrusion and detect
an intrusion that may have occurred. The detection is places on controls such as the routers, firewalls,
public key infrastructure, virtual private network and virus scanners. In cases where network intrusion
systems have not be implemented, the companies tend to complain of issues such as lack of data,
confidential information stolen, lack of access of some files, users being logged out, their password
changed and many more complaints. A security professional administrator will use the intrusion
detection model and find out if there is an intrusion in the system from the data that has been collected
from the servers and preprocessed. Once an intrusion has been detected an alarm is generated and the
security administrator will respond to the intrusion detected (Thangavel, 2014).
The figure below depicts the mind map diagram for intrusion detection system.
The figure below illustrates the process involved in the intrusion detection system.
is should be secure and frequent monitoring of the system and the entire network is necessary.
The processes involves some overlapping controls that are used in preventing any intrusion and detect
an intrusion that may have occurred. The detection is places on controls such as the routers, firewalls,
public key infrastructure, virtual private network and virus scanners. In cases where network intrusion
systems have not be implemented, the companies tend to complain of issues such as lack of data,
confidential information stolen, lack of access of some files, users being logged out, their password
changed and many more complaints. A security professional administrator will use the intrusion
detection model and find out if there is an intrusion in the system from the data that has been collected
from the servers and preprocessed. Once an intrusion has been detected an alarm is generated and the
security administrator will respond to the intrusion detected (Thangavel, 2014).
The figure below depicts the mind map diagram for intrusion detection system.
The figure below illustrates the process involved in the intrusion detection system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
Motivation
The motivation for working on the enhancement of network intrusion detection using statistical
functions is to develop a system that is secure. Most of the systems in companies have security flaws.
This security flaws are identified by hackers and the use them as a loop to get into a system and
interfere with the entire network. In some cases, the abuse of the system my not be from an outsider,
but from a person who is a user in the system. Some of the users in a system have malicious intention
to acquire data that are not granted permissions of access. In some cases, there are intrusions that may
not be easily identified. The second motivation is to quickly identify any intrusion into a system and
limit the damage that would have occurred. The third motivation is that the intrusion detection system
acts as a deterrent (Rastegari, Hingston & Lam, 2015). Generally, the motivation is to work towards the
project is to solve the problem of attacks in the system.
Relevance
People require to work on secure systems. The system attacks tend to reduce the efficiency in business
causing disruption in the business processes. Secure systems result to a smooth business process flow.
It is necessary to test the system secure state to be assured of security status of a system.
Motivation
The motivation for working on the enhancement of network intrusion detection using statistical
functions is to develop a system that is secure. Most of the systems in companies have security flaws.
This security flaws are identified by hackers and the use them as a loop to get into a system and
interfere with the entire network. In some cases, the abuse of the system my not be from an outsider,
but from a person who is a user in the system. Some of the users in a system have malicious intention
to acquire data that are not granted permissions of access. In some cases, there are intrusions that may
not be easily identified. The second motivation is to quickly identify any intrusion into a system and
limit the damage that would have occurred. The third motivation is that the intrusion detection system
acts as a deterrent (Rastegari, Hingston & Lam, 2015). Generally, the motivation is to work towards the
project is to solve the problem of attacks in the system.
Relevance
People require to work on secure systems. The system attacks tend to reduce the efficiency in business
causing disruption in the business processes. Secure systems result to a smooth business process flow.
It is necessary to test the system secure state to be assured of security status of a system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
Scope Statement
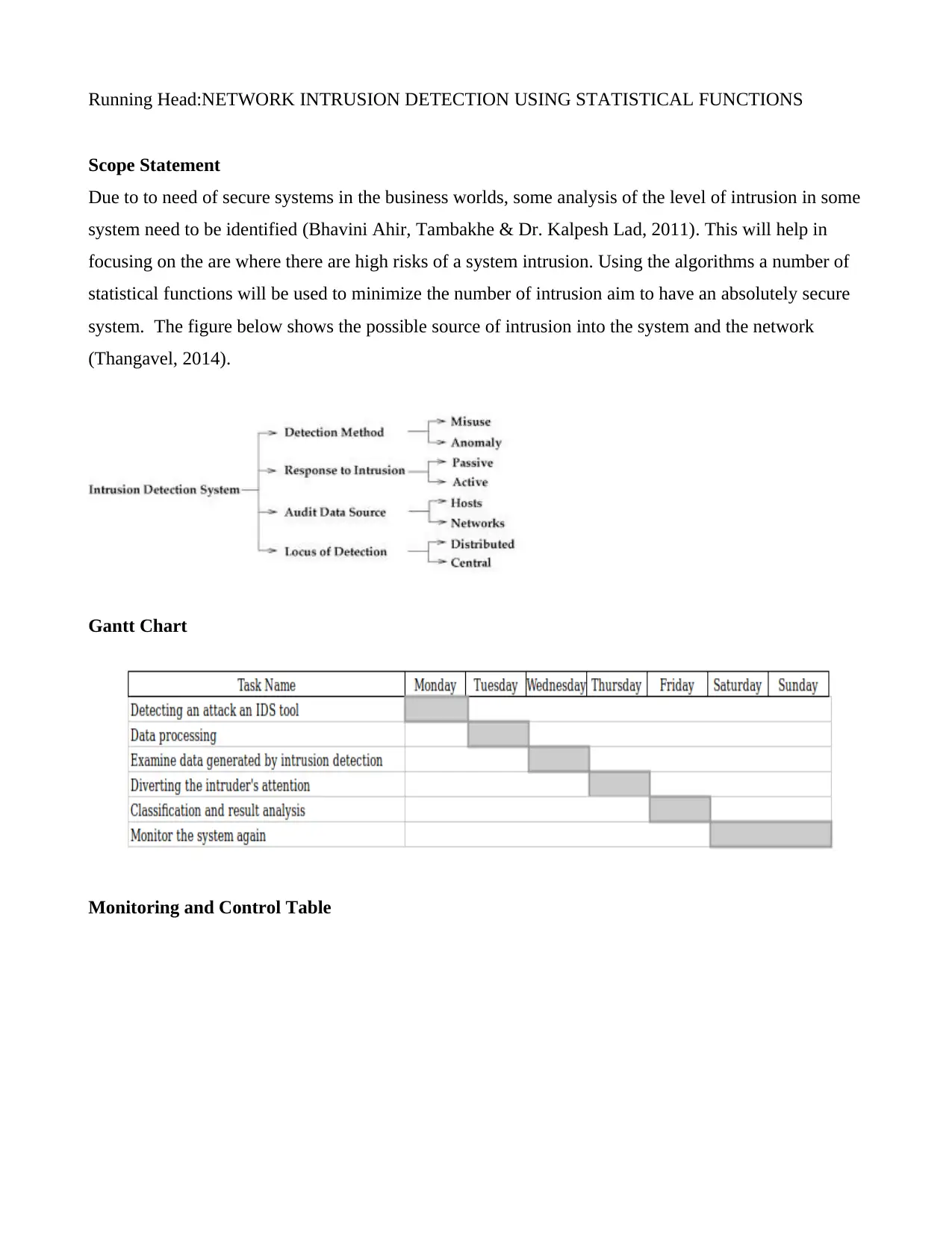
Due to to need of secure systems in the business worlds, some analysis of the level of intrusion in some
system need to be identified (Bhavini Ahir, Tambakhe & Dr. Kalpesh Lad, 2011). This will help in
focusing on the are where there are high risks of a system intrusion. Using the algorithms a number of
statistical functions will be used to minimize the number of intrusion aim to have an absolutely secure
system. The figure below shows the possible source of intrusion into the system and the network
(Thangavel, 2014).
Gantt Chart
Monitoring and Control Table
Scope Statement
Due to to need of secure systems in the business worlds, some analysis of the level of intrusion in some
system need to be identified (Bhavini Ahir, Tambakhe & Dr. Kalpesh Lad, 2011). This will help in
focusing on the are where there are high risks of a system intrusion. Using the algorithms a number of
statistical functions will be used to minimize the number of intrusion aim to have an absolutely secure
system. The figure below shows the possible source of intrusion into the system and the network
(Thangavel, 2014).
Gantt Chart
Monitoring and Control Table

Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
Deliverable
A list of efficient intrusion detection tools.
Documentation on how to use the tools used in intrusion detection.
The report on where there a more risks that need to b e addressed.
Security training of people in order to create awareness on the need of a secure system.
Objectives
1. S:Get to know who is attacking the system.
An intrusion detection tool will be used to identify if there is any intrusion in the system. The reports
generated from the tool to be used will determine how the system has been hacked.
2. M:To ensure the systems and networks is 100% secure.
This will be enhanced by ensuring, the data is well encrypted and there is no flaw in the system as well
as the network.
3. A:Get to understand the full working of the system and the network.
Steps involved in understanding the system include: knowing all the functionalities of the system and
the network connections should be clearly understood. This will include the router, switch and server
connections.
Deliverable
A list of efficient intrusion detection tools.
Documentation on how to use the tools used in intrusion detection.
The report on where there a more risks that need to b e addressed.
Security training of people in order to create awareness on the need of a secure system.
Objectives
1. S:Get to know who is attacking the system.
An intrusion detection tool will be used to identify if there is any intrusion in the system. The reports
generated from the tool to be used will determine how the system has been hacked.
2. M:To ensure the systems and networks is 100% secure.
This will be enhanced by ensuring, the data is well encrypted and there is no flaw in the system as well
as the network.
3. A:Get to understand the full working of the system and the network.
Steps involved in understanding the system include: knowing all the functionalities of the system and
the network connections should be clearly understood. This will include the router, switch and server
connections.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
4. R:To train people on the importance of a secure system.
Having training lessons for all the users in the system will be necessary. This is to ensure they
understand the system and the importance of system security.
5. T:To complete the entire task in one week.
The tasks involved include performing a system intrusion detection, analyzing the results,
understanding the system and the network and training the system users.
Risk Management Log
The are a number of risks that could lead to network intrusion .
Risk Description Management
Employee lack of awareness In some situations, the
employees may use weak
password or share passwords
with friends. This forms an easy
access for the unauthorized
users. The people accessing the
system could be having
malicious intention in the
system (Li, Meng, Kwok & IP,
2017).
The employees should be
trained on the importance of
using strong password in the
system. The employees should
not share their passwords with
anyone in the office.
Use of USB drives and supports
devices.
Using the drives to transfer or
save some confidential
information such as the login
credential is not right. One may
forget the USB drive in a port
and the data is then exposed to
unauthorized people. Details
such as private client data is not
secure any longer.
Also malware is written on the
Ensure the confidential data is
not transferred using the flash
disk. Email address are
preferred in sending the
confidential information such as
the login credentials. Using
emails is secure as one is
expected to be authenticated to
view such kind of data.
4. R:To train people on the importance of a secure system.
Having training lessons for all the users in the system will be necessary. This is to ensure they
understand the system and the importance of system security.
5. T:To complete the entire task in one week.
The tasks involved include performing a system intrusion detection, analyzing the results,
understanding the system and the network and training the system users.
Risk Management Log
The are a number of risks that could lead to network intrusion .
Risk Description Management
Employee lack of awareness In some situations, the
employees may use weak
password or share passwords
with friends. This forms an easy
access for the unauthorized
users. The people accessing the
system could be having
malicious intention in the
system (Li, Meng, Kwok & IP,
2017).
The employees should be
trained on the importance of
using strong password in the
system. The employees should
not share their passwords with
anyone in the office.
Use of USB drives and supports
devices.
Using the drives to transfer or
save some confidential
information such as the login
credential is not right. One may
forget the USB drive in a port
and the data is then exposed to
unauthorized people. Details
such as private client data is not
secure any longer.
Also malware is written on the
Ensure the confidential data is
not transferred using the flash
disk. Email address are
preferred in sending the
confidential information such as
the login credentials. Using
emails is secure as one is
expected to be authenticated to
view such kind of data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
flash drives. Once the flash
drive is inserted to the port in
the network, the bugs are
introduced to the machine and
then will affect the entire
network.
Emails Scams and attachment. Hackers and other malicious
people could send an email with
an attachment that has a
malware. One the attachment is
clicked in could execute a
malware in the computer and
eventually the entire network
(Dileep Kumar, Srikanth &
Tejeswini, 2016).
The employees should not click
on any links or attachment if
they are suspicious (Derouet,
2016).
Computer Virus The virus attacks on a global
scale. They corrupt the files or
even detect valuable data on he
servers (Donbavand &
Chernett, 2012).
Companies should ensure they
install antivirus both on the
servers and in the personal
computer in order to clean any
detected virus in the system.
Wi-Fi Eavesdropping Criminals tend to used WiFi
eavesdropping to capture
personal information. The
information could have some
confidential data and company
private data.
People should ensure they are
using encrypted WiFi networks.
Software Vulnerability Some software have
vulnerability that may pose the
network security issues. Some
of these may be the out dated
It is wise for a company to
ensure that the software they
are using is updated. The
software should also have
flash drives. Once the flash
drive is inserted to the port in
the network, the bugs are
introduced to the machine and
then will affect the entire
network.
Emails Scams and attachment. Hackers and other malicious
people could send an email with
an attachment that has a
malware. One the attachment is
clicked in could execute a
malware in the computer and
eventually the entire network
(Dileep Kumar, Srikanth &
Tejeswini, 2016).
The employees should not click
on any links or attachment if
they are suspicious (Derouet,
2016).
Computer Virus The virus attacks on a global
scale. They corrupt the files or
even detect valuable data on he
servers (Donbavand &
Chernett, 2012).
Companies should ensure they
install antivirus both on the
servers and in the personal
computer in order to clean any
detected virus in the system.
Wi-Fi Eavesdropping Criminals tend to used WiFi
eavesdropping to capture
personal information. The
information could have some
confidential data and company
private data.
People should ensure they are
using encrypted WiFi networks.
Software Vulnerability Some software have
vulnerability that may pose the
network security issues. Some
of these may be the out dated
It is wise for a company to
ensure that the software they
are using is updated. The
software should also have
Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
software that are not supported
(Rahimi & Zargham, 2013).
secured hosting to minimize the
intrusion.
Unawareness The technology is evolving fast.
This means that the network
risk are becoming sophisticated
too .
Inquire from security experts on
how to approach a certain risk.
Third-Party Technology
solutions.
Most of the third-party
solutions installed on the
network and isn’t patched may
leave a company vulnerable to
attack (Hasselbring, Rohr,
Taeger & Winteler, 2016).
Ensure the third parted
solutions are patched.
Ethics
Ethics refers to doing the right thing. Technology also merges with ethics. Anything done in contrary is
not the right thing. ACM have issued standard of ethic for the entity computing activities. Intrusion in a
system is not ethical. Usually intrusion into a system without authentication is unethical. There are
activities that such are also termed as unethical. They include eavesdropping on emails, data and voice
communications, gaining accesses into a system to change data , accessing protected information is
also unethical.
Hackers can be categorised into two. There are ethical hackers and unethical hackers. The ethical
hackers, tend to get into a system with a good intention. The ethical hackers should always be certified.
Any system administrator or network administrator should follow the ethics. In each company there
are certain ethic guideline that have been set (Cooper, 2016). The administrator has all the permissions
to access all the dat in the servers. This is inclusive of the employee credential, the bank account, the
payroll system, companies private data among other sensitive information. The administrator has the
ability to check every file in the server where the people could have written the most confidential
information such as login details. The administrator should know that going into the personal files
without permission by the owner of the files is unethical. IDS requires ethic codes too. The data in the
software that are not supported
(Rahimi & Zargham, 2013).
secured hosting to minimize the
intrusion.
Unawareness The technology is evolving fast.
This means that the network
risk are becoming sophisticated
too .
Inquire from security experts on
how to approach a certain risk.
Third-Party Technology
solutions.
Most of the third-party
solutions installed on the
network and isn’t patched may
leave a company vulnerable to
attack (Hasselbring, Rohr,
Taeger & Winteler, 2016).
Ensure the third parted
solutions are patched.
Ethics
Ethics refers to doing the right thing. Technology also merges with ethics. Anything done in contrary is
not the right thing. ACM have issued standard of ethic for the entity computing activities. Intrusion in a
system is not ethical. Usually intrusion into a system without authentication is unethical. There are
activities that such are also termed as unethical. They include eavesdropping on emails, data and voice
communications, gaining accesses into a system to change data , accessing protected information is
also unethical.
Hackers can be categorised into two. There are ethical hackers and unethical hackers. The ethical
hackers, tend to get into a system with a good intention. The ethical hackers should always be certified.
Any system administrator or network administrator should follow the ethics. In each company there
are certain ethic guideline that have been set (Cooper, 2016). The administrator has all the permissions
to access all the dat in the servers. This is inclusive of the employee credential, the bank account, the
payroll system, companies private data among other sensitive information. The administrator has the
ability to check every file in the server where the people could have written the most confidential
information such as login details. The administrator should know that going into the personal files
without permission by the owner of the files is unethical. IDS requires ethic codes too. The data in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
system should remain private. The network administrators should depict ethics before looking into the
data. Ethical hackers can try to hack into the system with a positive intention of trying to find if there is
a flow in the system . Once an ethical hacker manages to get into the system without being given the
credential, then he or she identifies the flaw and makes a report about the fault in the system. The
ethical hacker advices a company on how to make the system more secure (Farsole, Kashikar &
Zunzunwala, 2010).
On the other hand the unethical hack refers to the ill motivated people who try to get into a system
without authentication (Fridrich, 2015). The kind of unethical hackers tend to steal data, destroy the
data or use the data for their personal interest. The unethical hackers at time corrupt the file in the
server and ask for a huge amount of money to stop disrupting the files. There is a computer fraud and
abuse act that deals with the hacking cases. There are a number of common tools that are used by the
unethical hackers. This tools include: keylogger, Denial of Service or Distributed Denial of Service and
Water hole attacks. The Keylogger tool is used to log the key strokes of the keyboard into the log files.
The keystrokes are used in capturing the email passwords. These has really affected most banks. The
banking system encourage the use of virtual keyboard to minimize the frauds. Denial of Service is
mostly common in attacked websites (Gupta & Anand, 2017). A lot of requests are sent to the servers.
These requests are fake, therefore the server will crash due to the overload. Botnets and zombie are
used to send the many request.When the server is overloaded then the actual users will not access the
server hence denial of service. The other tool is the waterhole attacks. The hackers tend to target the
weak point of a system or the system users. The attackers could create a fake WiFi network. These can
be solved by using an update operating system in the company. Another way used by the unethical
hackers is the fake WAP. The hacker create a WiFi network especially in a public place such as a
coffee shop. Once connected to the fake WAP, the hacker can then access the data on your device
easily. Finally. Eavesdropping in a kind of an attack where the hacker is a third party. The motive
behind such attacks is to closely observe all the activities of the user secretly and gather all the relevant
data that may be useful to the hacker.
Legal
Ethical hacking is legal. Dealing with privacy violation, the legislation does not come out clearly on the
point that are considers private violations. The right to protect the information system and respect
privacy laws should be the same same as government sector and the private sector. Each of the
system should remain private. The network administrators should depict ethics before looking into the
data. Ethical hackers can try to hack into the system with a positive intention of trying to find if there is
a flow in the system . Once an ethical hacker manages to get into the system without being given the
credential, then he or she identifies the flaw and makes a report about the fault in the system. The
ethical hacker advices a company on how to make the system more secure (Farsole, Kashikar &
Zunzunwala, 2010).
On the other hand the unethical hack refers to the ill motivated people who try to get into a system
without authentication (Fridrich, 2015). The kind of unethical hackers tend to steal data, destroy the
data or use the data for their personal interest. The unethical hackers at time corrupt the file in the
server and ask for a huge amount of money to stop disrupting the files. There is a computer fraud and
abuse act that deals with the hacking cases. There are a number of common tools that are used by the
unethical hackers. This tools include: keylogger, Denial of Service or Distributed Denial of Service and
Water hole attacks. The Keylogger tool is used to log the key strokes of the keyboard into the log files.
The keystrokes are used in capturing the email passwords. These has really affected most banks. The
banking system encourage the use of virtual keyboard to minimize the frauds. Denial of Service is
mostly common in attacked websites (Gupta & Anand, 2017). A lot of requests are sent to the servers.
These requests are fake, therefore the server will crash due to the overload. Botnets and zombie are
used to send the many request.When the server is overloaded then the actual users will not access the
server hence denial of service. The other tool is the waterhole attacks. The hackers tend to target the
weak point of a system or the system users. The attackers could create a fake WiFi network. These can
be solved by using an update operating system in the company. Another way used by the unethical
hackers is the fake WAP. The hacker create a WiFi network especially in a public place such as a
coffee shop. Once connected to the fake WAP, the hacker can then access the data on your device
easily. Finally. Eavesdropping in a kind of an attack where the hacker is a third party. The motive
behind such attacks is to closely observe all the activities of the user secretly and gather all the relevant
data that may be useful to the hacker.
Legal
Ethical hacking is legal. Dealing with privacy violation, the legislation does not come out clearly on the
point that are considers private violations. The right to protect the information system and respect
privacy laws should be the same same as government sector and the private sector. Each of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
scenarios have laws that have been set but in most cases they look clearly the same. IDS cannot
differentiate between a malicious activity and a genuine one. The header information is not enough to
distinguish the two. Therefore, IDS needs to look into the packet. Before performing an interception
into a packet, there are specific conditions that has to met before the authorizations is granted to the
person performing the IDS (Thomas, 2012). The law tends to protect the privacy of innocent people.
No one can perform an intercept before a law is passed. In conclusion in performing any forensic
investigation the legal aspect has to be considered first (Farooqui, 2016). The legislation tends to limit
the use of IDS logs as forensic evidence and the legislations need to alter so that they used the risk logs
as proof.
Social,
The social network analaysis is a method used to make analysis of human interacting with felow
human. It is a mathematical framework. The SNA method helps in defining SN-IDS. The social
network embraces the IDS cooperative archetcture. Usually, a group of nodes tends to share the
detected information for global decisions. There are three modules involved in this system . They
include data preprocessing module, social analysis module and the intrusion response.
The lowest is the data preprocessing module. It involves the data collection and data preprocessing.
The data collection component tends to collect all the audit data and then the data is encoded into the
appropriate social formats in the data preprocessing component. In the social analysis model then it is
the generating of the social network from the control metrics and the data mentric. The metrics are
analyzed and the profile statistics are tested. In the intrusion response model there is the global
responses component and the local response component. Both interact with each other. These module
helps in the integration of the local intrusion alerts and the global alerts. The social network analysis is
used to control the data traffic to develop a social network.
Security
There is need for intrusion detection especially in the large companies. The system intrusion detection
can be summed up by a simple principle of the network security, which is deep defense. Defense in
depth is layered approach that is used to check if there is any intrusion into the system (Md, 2014). All
the companies’ aim is to have a secure system. The data and the file should be secure away from any
unauthorized access. Confidential data should also be secure from the hackers (Ekebrink, 2013).
scenarios have laws that have been set but in most cases they look clearly the same. IDS cannot
differentiate between a malicious activity and a genuine one. The header information is not enough to
distinguish the two. Therefore, IDS needs to look into the packet. Before performing an interception
into a packet, there are specific conditions that has to met before the authorizations is granted to the
person performing the IDS (Thomas, 2012). The law tends to protect the privacy of innocent people.
No one can perform an intercept before a law is passed. In conclusion in performing any forensic
investigation the legal aspect has to be considered first (Farooqui, 2016). The legislation tends to limit
the use of IDS logs as forensic evidence and the legislations need to alter so that they used the risk logs
as proof.
Social,
The social network analaysis is a method used to make analysis of human interacting with felow
human. It is a mathematical framework. The SNA method helps in defining SN-IDS. The social
network embraces the IDS cooperative archetcture. Usually, a group of nodes tends to share the
detected information for global decisions. There are three modules involved in this system . They
include data preprocessing module, social analysis module and the intrusion response.
The lowest is the data preprocessing module. It involves the data collection and data preprocessing.
The data collection component tends to collect all the audit data and then the data is encoded into the
appropriate social formats in the data preprocessing component. In the social analysis model then it is
the generating of the social network from the control metrics and the data mentric. The metrics are
analyzed and the profile statistics are tested. In the intrusion response model there is the global
responses component and the local response component. Both interact with each other. These module
helps in the integration of the local intrusion alerts and the global alerts. The social network analysis is
used to control the data traffic to develop a social network.
Security
There is need for intrusion detection especially in the large companies. The system intrusion detection
can be summed up by a simple principle of the network security, which is deep defense. Defense in
depth is layered approach that is used to check if there is any intrusion into the system (Md, 2014). All
the companies’ aim is to have a secure system. The data and the file should be secure away from any
unauthorized access. Confidential data should also be secure from the hackers (Ekebrink, 2013).

Running Head:NETWORK INTRUSION DETECTION USING STATISTICAL FUNCTIONS
Professional
The IDS professional are supposed to provide some services in various companies. The team should
monitor al the operation of various devices such as the routers, firewall, key management servers, files
among other devices. The should also monitor the risk log files in the servers. This will help in
identifying an intrusion into the network faster. The IDS professional should also provide the right
administrator way of tune to understand the entire system. They show have a user friendly interface for
the rest of the staff members in the company. The monitored intrusions should be controlled using a
control table that is set by the profession. When this seem clear the professional should check in all the
log file this include the risk logs, the mail logs and other logs to ensure the system is safe. This will
help the staff member to help I checking for system intrusion. There are various tools that are used in
monitoring the servers such as Nagios and others. Such tools provide a better interface for non-tech to
identify any system intrusion. The IDS professionals should also provide reports when file in the
systems are altered . This can help to track the intrusion damage level.The professional should set up a
mechanism system that will generate an alarm in cases where security has been breached. It is from the
control table that that risks will be managed.
The image below displays the server load depending on the traffic accessing the server depending on
the statistics collected.
Professional
The IDS professional are supposed to provide some services in various companies. The team should
monitor al the operation of various devices such as the routers, firewall, key management servers, files
among other devices. The should also monitor the risk log files in the servers. This will help in
identifying an intrusion into the network faster. The IDS professional should also provide the right
administrator way of tune to understand the entire system. They show have a user friendly interface for
the rest of the staff members in the company. The monitored intrusions should be controlled using a
control table that is set by the profession. When this seem clear the professional should check in all the
log file this include the risk logs, the mail logs and other logs to ensure the system is safe. This will
help the staff member to help I checking for system intrusion. There are various tools that are used in
monitoring the servers such as Nagios and others. Such tools provide a better interface for non-tech to
identify any system intrusion. The IDS professionals should also provide reports when file in the
systems are altered . This can help to track the intrusion damage level.The professional should set up a
mechanism system that will generate an alarm in cases where security has been breached. It is from the
control table that that risks will be managed.
The image below displays the server load depending on the traffic accessing the server depending on
the statistics collected.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




