Network Management Assignment: Switching, Routing, and Subnetting
VerifiedAdded on 2020/04/13
|5
|467
|39
Homework Assignment
AI Summary
This document presents a solution to a network management assignment. The assignment covers fundamental networking concepts, including how switches handle frames and update address tables, differentiating between layer 2 and layer 3 operations in the OSI model, and the role of subnet masks. It also explores supported operating systems and provides a subnetting table detailing network names, sizes, allocated sizes, address masks, and assignable IP ranges. The solution references key academic sources to support its claims and provide a comprehensive understanding of the subject matter.

Running head: NETWORK MANAGEMENT
Network Management
[Name of the Student]
[Name of the University]
[Author note]
Network Management
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2NETWORK MANAGEMENT
Table of Contents
Question 1..................................................................................................................................3
Question 2..................................................................................................................................3
Question 3..................................................................................................................................3
Question 4..................................................................................................................................3
Question 5..................................................................................................................................3
References..................................................................................................................................4
Table of Contents
Question 1..................................................................................................................................3
Question 2..................................................................................................................................3
Question 3..................................................................................................................................3
Question 4..................................................................................................................................3
Question 5..................................................................................................................................3
References..................................................................................................................................4
3NETWORK MANAGEMENT
Question 1
When a switch receives a frame, it directly updates the address table with the source
MAC address and the port on which it received the frame. If the destination MAC address is
not on its MAC address table (unknown unicast), it basically floods the frame to all the port,
except the port on which the frame is received (Afanasyev et al., 2014).
Question 2
The traditional switch basically operates at the layer 2 of the OSI model, this is where
the packets are send to a specific switch port based on the MAC address destination. Routing
operating on the layer 3, where packets are basically send to a specific next hop IT address
which is based on the IP address (Davies, 2012).
Question 3
The subnet mask of the local host will always check whether the packet has been send
or not. Whether this is used to discover the source address to use when the sending of the
packing is done or I used to determine if the destination host really exist within the same
subnet as the sender, the subnet mask would be utilized in this way (Afanasyev et al., 2014).
Question 4
The computer operating that would be supported can be any operating system. For
example, windows 7 and window server 2008 (Decusatis, Carranza & DeCusatis, 2012).
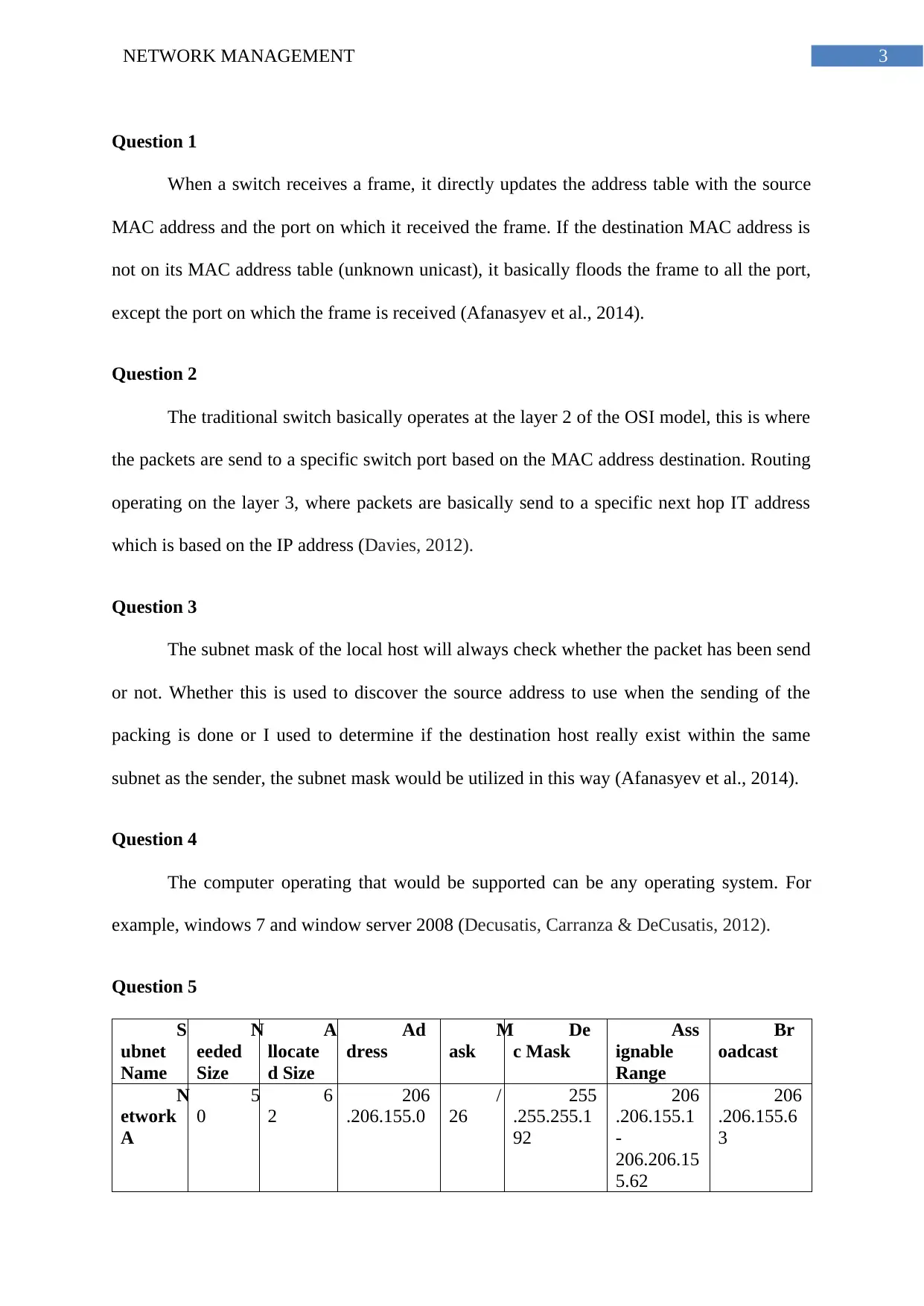
Question 5
S
ubnet
Name
N
eeded
Size
A
llocate
d Size
Ad
dress
M
ask
De
c Mask
Ass
ignable
Range
Br
oadcast
N
etwork
A
5
0
6
2
206
.206.155.0
/
26
255
.255.255.1
92
206
.206.155.1
-
206.206.15
5.62
206
.206.155.6
3
Question 1
When a switch receives a frame, it directly updates the address table with the source
MAC address and the port on which it received the frame. If the destination MAC address is
not on its MAC address table (unknown unicast), it basically floods the frame to all the port,
except the port on which the frame is received (Afanasyev et al., 2014).
Question 2
The traditional switch basically operates at the layer 2 of the OSI model, this is where
the packets are send to a specific switch port based on the MAC address destination. Routing
operating on the layer 3, where packets are basically send to a specific next hop IT address
which is based on the IP address (Davies, 2012).
Question 3
The subnet mask of the local host will always check whether the packet has been send
or not. Whether this is used to discover the source address to use when the sending of the
packing is done or I used to determine if the destination host really exist within the same
subnet as the sender, the subnet mask would be utilized in this way (Afanasyev et al., 2014).
Question 4
The computer operating that would be supported can be any operating system. For
example, windows 7 and window server 2008 (Decusatis, Carranza & DeCusatis, 2012).
Question 5
S
ubnet
Name
N
eeded
Size
A
llocate
d Size
Ad
dress
M
ask
De
c Mask
Ass
ignable
Range
Br
oadcast
N
etwork
A
5
0
6
2
206
.206.155.0
/
26
255
.255.255.1
92
206
.206.155.1
-
206.206.15
5.62
206
.206.155.6
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4NETWORK MANAGEMENT
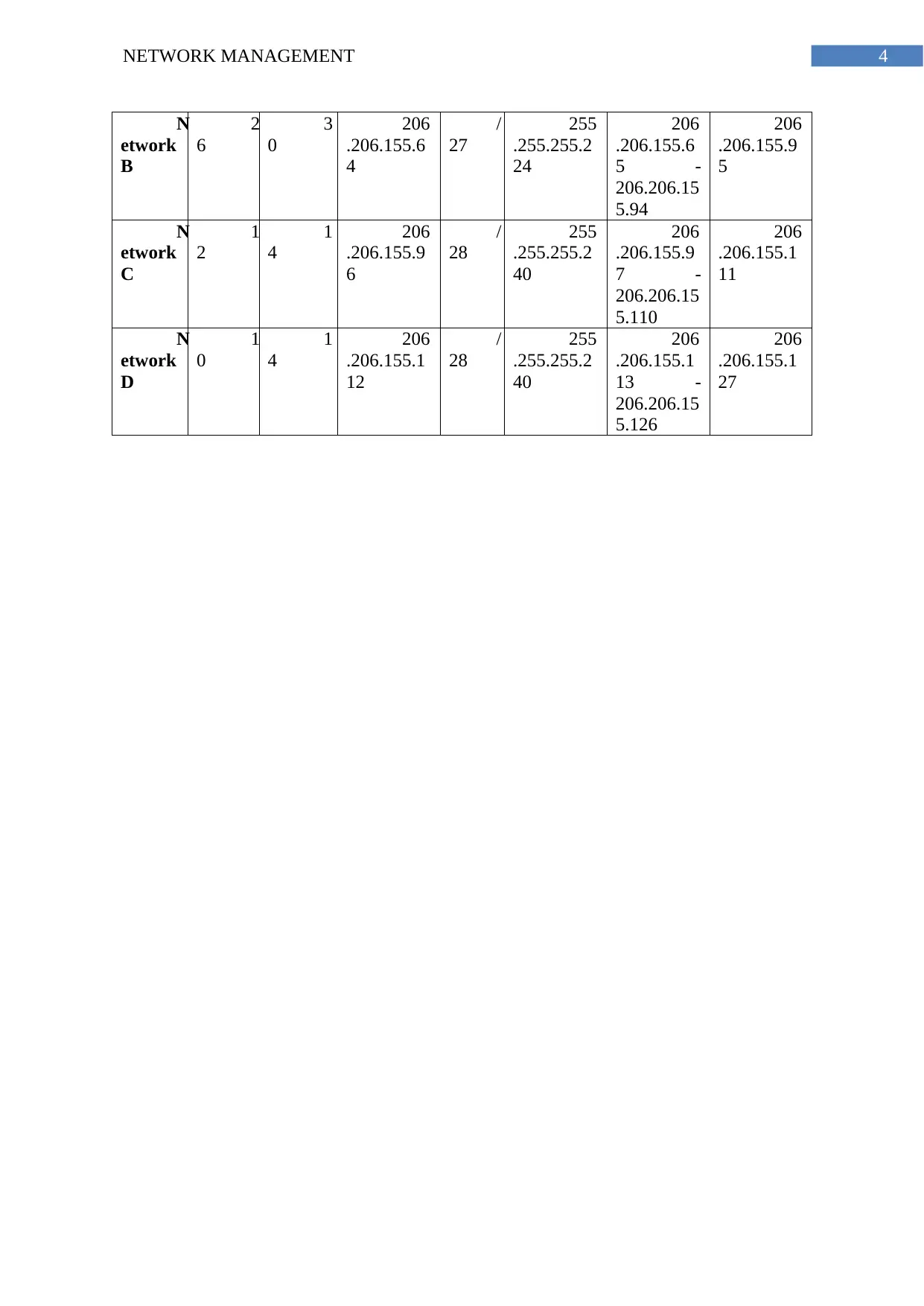
N
etwork
B
2
6
3
0
206
.206.155.6
4
/
27
255
.255.255.2
24
206
.206.155.6
5 -
206.206.15
5.94
206
.206.155.9
5
N
etwork
C
1
2
1
4
206
.206.155.9
6
/
28
255
.255.255.2
40
206
.206.155.9
7 -
206.206.15
5.110
206
.206.155.1
11
N
etwork
D
1
0
1
4
206
.206.155.1
12
/
28
255
.255.255.2
40
206
.206.155.1
13 -
206.206.15
5.126
206
.206.155.1
27
N
etwork
B
2
6
3
0
206
.206.155.6
4
/
27
255
.255.255.2
24
206
.206.155.6
5 -
206.206.15
5.94
206
.206.155.9
5
N
etwork
C
1
2
1
4
206
.206.155.9
6
/
28
255
.255.255.2
40
206
.206.155.9
7 -
206.206.15
5.110
206
.206.155.1
11
N
etwork
D
1
0
1
4
206
.206.155.1
12
/
28
255
.255.255.2
40
206
.206.155.1
13 -
206.206.15
5.126
206
.206.155.1
27
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5NETWORK MANAGEMENT
References
Afanasyev, A., Burke, J., Zhang, L., Claffy, K., Wang, L., Jacobson, V., ... & Zhang, B.
(2014). Named data networking. ACM SIGCOMM Computer Communication
Review, 44(3), 66-73.
Davies, J. (2012). Understanding ipv6. Pearson Education.
Decusatis, C. J. S., Carranza, A., & DeCusatis, C. M. (2012). Communication within clouds:
open standards and proprietary protocols for data center networking. IEEE
Communications Magazine, 50(9).
References
Afanasyev, A., Burke, J., Zhang, L., Claffy, K., Wang, L., Jacobson, V., ... & Zhang, B.
(2014). Named data networking. ACM SIGCOMM Computer Communication
Review, 44(3), 66-73.
Davies, J. (2012). Understanding ipv6. Pearson Education.
Decusatis, C. J. S., Carranza, A., & DeCusatis, C. M. (2012). Communication within clouds:
open standards and proprietary protocols for data center networking. IEEE
Communications Magazine, 50(9).
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
![Network Management Assignment Solution - [Course Code] - [Semester]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fla%2F5bdeac662a0b48479c60f14aac4bb9a2.jpg&w=256&q=75)




