Network Management Assignment: Switch, IPv6, and Subnetting Analysis
VerifiedAdded on 2020/04/15
|5
|778
|77
Homework Assignment
AI Summary
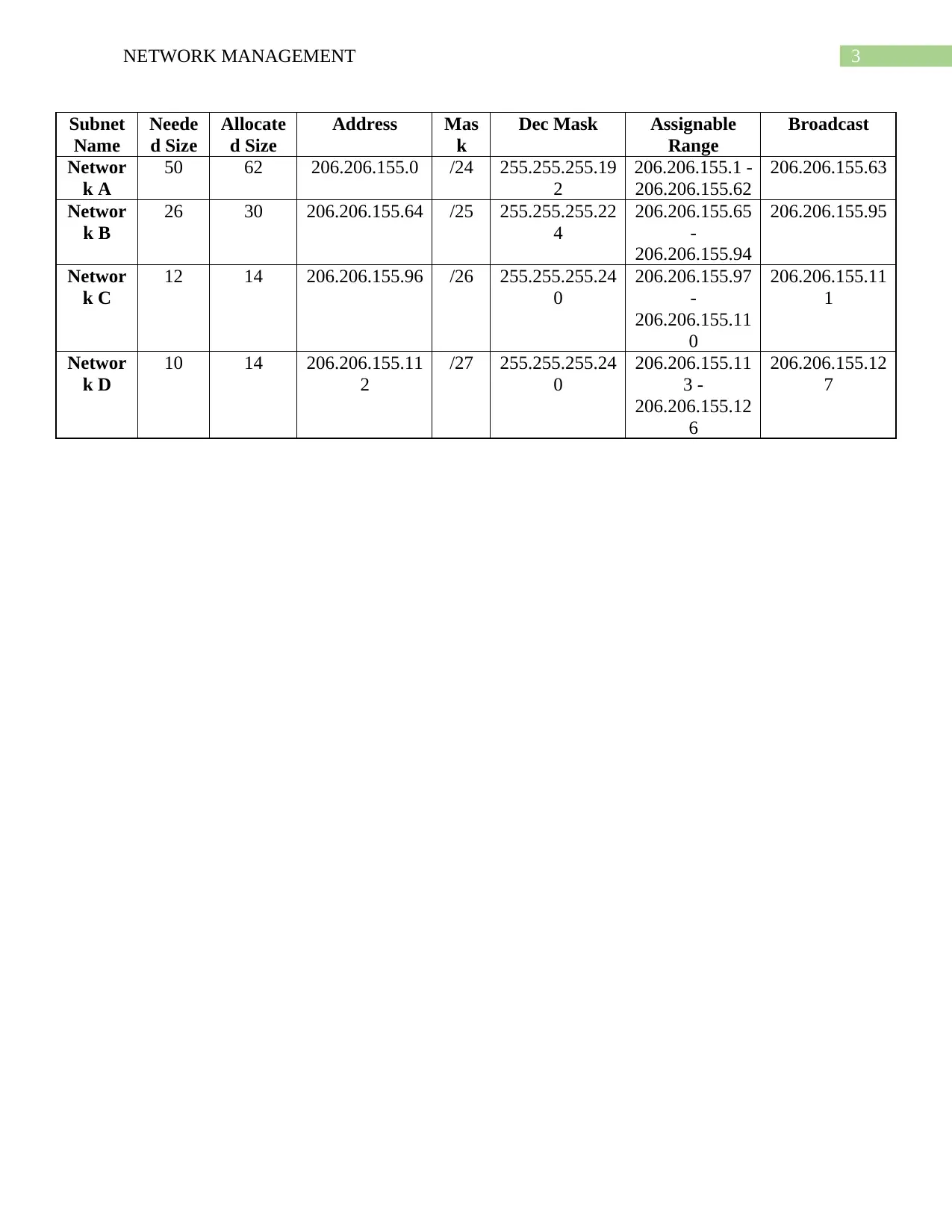
This document presents a comprehensive solution to a network management assignment, addressing key networking concepts. The solution begins by explaining how a switch learns and stores MAC addresses, differentiating between Layer 2 and Layer 3 switches. It then details how a host detects data packet loss, providing a clear understanding of TCP/IP communication. The assignment further explores the transition to IPv6, outlining considerations for network readiness. Finally, it includes a practical exercise in subnetting, where a given CIDR block is divided into subnets to accommodate different network sizes. The solution provides a detailed breakdown of subnet allocation, including address ranges, masks, and broadcast addresses for each subnet, and concludes with a list of relevant references.
1 out of 5





![Network Management Assignment Solution - [Course Code] - [Semester]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fla%2F5bdeac662a0b48479c60f14aac4bb9a2.jpg&w=256&q=75)





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)