University Assignment: Computing and Systems Development - NOS Report
VerifiedAdded on 2023/06/10
|18
|5002
|251
Report
AI Summary
This report provides a comprehensive analysis of Network Operating Systems (NOS), covering key principles, implementation strategies, and management techniques. The report begins with an identification and evaluation of different operating system types, including Windows, Mac OS, and Linux, and recommends Windows for its user-friendliness and compatibility. It then delves into business continuity and disaster recovery planning, emphasizing the importance of a disaster plan, reducing downtime, and data backup solutions using RAID configurations. The report continues with a detailed plan for NOS implementation, including server setup, IP addressing schemes, and security measures. It also explores the configuration of network devices, particularly Cisco routers, and the use of IOS. Finally, the report addresses the selection of performance monitoring tools and the evaluation of the NOS to ensure optimal network performance and security. The report also discusses the importance of subnetting and security measures such as disabling unused ports and implementing password policies. The report provides a detailed addressing plan, and the use of backup servers and cloud storage is recommended for data management and redundancy.

Running head: COMPUTING AND SYSTEMS DEVELOPMENT
Network Operating Systems
Name of the Student
Name of the University
Author’s Note
Network Operating Systems
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
COMPUTING AND SYSTEMS DEVELOPMENT
Table of Contents
Lo1: Understanding network Operating System principles.......................................................2
1.1. Identification and evaluation of different types of operating system..............................2
1.2. Business Continuity and disaster recovery.....................................................................3
Lo2: Planning for the Implementation of the network operating system...................................5
2.1. Detailed plan for the implementation of the network operating system.........................5
2.2. Evaluation and justification for the plan.........................................................................9
Lo3: Implementation of the network operating system.............................................................9
3.1. Implementation of the selected NOS..............................................................................9
3.2. Configuration and testing of security policy.................................................................11
Lo4: Management of the network operating system................................................................12
4.1. Selection of the tool and justification for production of performance baseline report. 12
4.2. Evaluation of the network operating system.................................................................13
References................................................................................................................................15
COMPUTING AND SYSTEMS DEVELOPMENT
Table of Contents
Lo1: Understanding network Operating System principles.......................................................2
1.1. Identification and evaluation of different types of operating system..............................2
1.2. Business Continuity and disaster recovery.....................................................................3
Lo2: Planning for the Implementation of the network operating system...................................5
2.1. Detailed plan for the implementation of the network operating system.........................5
2.2. Evaluation and justification for the plan.........................................................................9
Lo3: Implementation of the network operating system.............................................................9
3.1. Implementation of the selected NOS..............................................................................9
3.2. Configuration and testing of security policy.................................................................11
Lo4: Management of the network operating system................................................................12
4.1. Selection of the tool and justification for production of performance baseline report. 12
4.2. Evaluation of the network operating system.................................................................13
References................................................................................................................................15

2
COMPUTING AND SYSTEMS DEVELOPMENT
Lo1: Understanding network Operating System principles
1.1. Identification and evaluation of different types of operating system
There are different operating system that can be installed in the hosts for the
management of the system software and the hardware resources. The newer version of the
Windows are compared for the improvement of the performance of the employees and
creating a controlled environment. The selection of the operating system have an impact on
the memory management, network performance, etc. The windows operating system are user
friendly and it is currently used by 80 to 90 percent users. It provides different functionality
and compatible with most of the service and the application (Peter et al. 2016). The windows
operating system are vulnerable to virus and spyware that can degrade the performance and
requires a lots of memory and processor for running. The Mac OS is used for the Apple
computers and it is developed by the Apple and thus there is less risk of software or hardware
crashing. It cannot be installed on other computers and there are only few programs that can
run on Mac thus it cannot be a choice for its implementation in the current network as a host
operating system (Otani et al. 2017). The third choice is the Linux operating system that is
available at a free of cost and it can be downloaded or modified for using in the proposed
network. The linux comes as a kernel and there are other software that are bundled for
meeting the requirement of the user. It needs a good deal of knowledge for the users to
operate the linux operating system.
Thus it is recommended that the Windows operating system is the best choice for its
deployment because it is easily available and the same configuration of the computer can be
used for installing the Linux. For the development of the network a network design is
prepared by subnetting the network according to the departments of the organization
(Mijumbi et al. 2016). An analysis is made on the available network operating system that
COMPUTING AND SYSTEMS DEVELOPMENT
Lo1: Understanding network Operating System principles
1.1. Identification and evaluation of different types of operating system
There are different operating system that can be installed in the hosts for the
management of the system software and the hardware resources. The newer version of the
Windows are compared for the improvement of the performance of the employees and
creating a controlled environment. The selection of the operating system have an impact on
the memory management, network performance, etc. The windows operating system are user
friendly and it is currently used by 80 to 90 percent users. It provides different functionality
and compatible with most of the service and the application (Peter et al. 2016). The windows
operating system are vulnerable to virus and spyware that can degrade the performance and
requires a lots of memory and processor for running. The Mac OS is used for the Apple
computers and it is developed by the Apple and thus there is less risk of software or hardware
crashing. It cannot be installed on other computers and there are only few programs that can
run on Mac thus it cannot be a choice for its implementation in the current network as a host
operating system (Otani et al. 2017). The third choice is the Linux operating system that is
available at a free of cost and it can be downloaded or modified for using in the proposed
network. The linux comes as a kernel and there are other software that are bundled for
meeting the requirement of the user. It needs a good deal of knowledge for the users to
operate the linux operating system.
Thus it is recommended that the Windows operating system is the best choice for its
deployment because it is easily available and the same configuration of the computer can be
used for installing the Linux. For the development of the network a network design is
prepared by subnetting the network according to the departments of the organization
(Mijumbi et al. 2016). An analysis is made on the available network operating system that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
COMPUTING AND SYSTEMS DEVELOPMENT
should be used for the configuration of the servers and improve the security and
manageability of the network. The network operating system is used for the management of
the printing service and sharing of database considering the management of the network
security and the name directory (Luo et al. 2015). The operating system used by the routers
should also be analysed for the selection of the network device and management of the
configuration of the router for reducing the complexity of the network.
Mainly Cisco routers are used that used the internetwork operating system (IOS) as its
NOS. Different technical support is available from CISCO for the management or
troubleshooting problems in the router and the switches used in the network. The use of
similar type of network devices for the whole network can reduce the cost of replacement and
backup devices can be kept for replacement of a faulty device without affecting the downtime
of the network (Perlman, Kaufman and Speciner 2016). The IOS uses the command line
interface for the configuration of the device and there are different cisco simulators that can
be used for the development of the prototype before implementation in the real life for testing
the network. Moreover cisco provides rebuilds and patches for the improvement of the
security of the network operating system used in the cisco device (Shin et al. 2014). The
release are tested rigorously for fixing the bugs and the routers can be upgraded to the latest
version for increasing the security of the network.
1.2. Business Continuity and disaster recovery
It is used by the organization for recovering from any unexpected condition and
resume the current operation of the business. For successful recovery of the business it is
important to create a disaster plan and handle the emergency event according to the plan for
maintaining a continuity in the business. The disaster recovery and the business continuity
plan is used together but they are dissimilar with each other. The business continuity
describes the ability of the business to continue with the critical function and the different
COMPUTING AND SYSTEMS DEVELOPMENT
should be used for the configuration of the servers and improve the security and
manageability of the network. The network operating system is used for the management of
the printing service and sharing of database considering the management of the network
security and the name directory (Luo et al. 2015). The operating system used by the routers
should also be analysed for the selection of the network device and management of the
configuration of the router for reducing the complexity of the network.
Mainly Cisco routers are used that used the internetwork operating system (IOS) as its
NOS. Different technical support is available from CISCO for the management or
troubleshooting problems in the router and the switches used in the network. The use of
similar type of network devices for the whole network can reduce the cost of replacement and
backup devices can be kept for replacement of a faulty device without affecting the downtime
of the network (Perlman, Kaufman and Speciner 2016). The IOS uses the command line
interface for the configuration of the device and there are different cisco simulators that can
be used for the development of the prototype before implementation in the real life for testing
the network. Moreover cisco provides rebuilds and patches for the improvement of the
security of the network operating system used in the cisco device (Shin et al. 2014). The
release are tested rigorously for fixing the bugs and the routers can be upgraded to the latest
version for increasing the security of the network.
1.2. Business Continuity and disaster recovery
It is used by the organization for recovering from any unexpected condition and
resume the current operation of the business. For successful recovery of the business it is
important to create a disaster plan and handle the emergency event according to the plan for
maintaining a continuity in the business. The disaster recovery and the business continuity
plan is used together but they are dissimilar with each other. The business continuity
describes the ability of the business to continue with the critical function and the different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
COMPUTING AND SYSTEMS DEVELOPMENT
business processes when any disaster occurs in the current business (White, Fisch and Pooch
2017). An alternative design of the network should be created for the development of the
disaster recovery plan and it should be audited for the identification of the flaws and
achievement of the goals and objectives of the organization. Different metrics are used for the
measurement of the environment of disaster recovery and the ability of the network to restore
the network to its last working condition (Silberschatz, Galvin and Gagne 2014). The
organization can gain different benefits with the implementation of the disaster recovery plan
and they are given below:
Reducing the network downtime – the medium sized business organization can face a
loss of $82,200 to $256,000 for a downtime of teen hours and the creation of the disaster
management plan can reduce the cost and increase the efficiency.
Quick time of recovery and backing up data – If there is an incident of loss of data
the client can loss the faith and with the implementation of the backup service the redundancy
of the data can be increased and thus no data would be lost.
Containment of cost – A business disaster recovery plan would reduce the risk of loss
of money as the downtime of the network can incur extra cost (Prezioso et al. 2015). The cost
of management of the network can be curtailed with recording the details of the network
equipment’s and creating a recovery zone.
Inventory and management of the network – The list of the device, protocols and the
configuration used for configuring the device should be documented such that the
functionality can be managed. It also helps in troubleshooting the network and identify the
functionality of the network.
Backup servers and cloud storage should be used for the management of the data and
the backup server should be connected using a high speed encrypted link such that the data
COMPUTING AND SYSTEMS DEVELOPMENT
business processes when any disaster occurs in the current business (White, Fisch and Pooch
2017). An alternative design of the network should be created for the development of the
disaster recovery plan and it should be audited for the identification of the flaws and
achievement of the goals and objectives of the organization. Different metrics are used for the
measurement of the environment of disaster recovery and the ability of the network to restore
the network to its last working condition (Silberschatz, Galvin and Gagne 2014). The
organization can gain different benefits with the implementation of the disaster recovery plan
and they are given below:
Reducing the network downtime – the medium sized business organization can face a
loss of $82,200 to $256,000 for a downtime of teen hours and the creation of the disaster
management plan can reduce the cost and increase the efficiency.
Quick time of recovery and backing up data – If there is an incident of loss of data
the client can loss the faith and with the implementation of the backup service the redundancy
of the data can be increased and thus no data would be lost.
Containment of cost – A business disaster recovery plan would reduce the risk of loss
of money as the downtime of the network can incur extra cost (Prezioso et al. 2015). The cost
of management of the network can be curtailed with recording the details of the network
equipment’s and creating a recovery zone.
Inventory and management of the network – The list of the device, protocols and the
configuration used for configuring the device should be documented such that the
functionality can be managed. It also helps in troubleshooting the network and identify the
functionality of the network.
Backup servers and cloud storage should be used for the management of the data and
the backup server should be connected using a high speed encrypted link such that the data

5
COMPUTING AND SYSTEMS DEVELOPMENT
transmitted through the link is not available to any third part agent. The local servers should
be used for storing the frequently used data for reducing the waiting time of the user ad
increasing the redundancy of the data.
There are different RAID options that are available for the management of the file
server and hosting the website of the organization for the management of the information and
files. Among the different RAID options, RAID 5 is selected for the configuration of the
network attached storage with disk striping and parity (Shin et al. 2014). The striping is used
for reconstruction of the data if the current disk fails. It used parity for reliability and
redundancy for increasing the efficiency of the network. In the RAID configuration more
than drives are working parallel and for the optimization of the situation different levels of
RAID are applied. The RAID 0 is used for stripping, RAID 1 is used for mirroring, RAID 5
is used for parity stripping, RAID 6 is applied for double parity and RAID 10 is applied for
combination of striping and mirroring.
Lo2: Planning for the Implementation of the network operating system
2.1. Detailed plan for the implementation of the network operating system
Installation – the servers created with the minimum hardware requirement that is
essential for supporting different service and operation. The use of commercial server for
base server can be an ideal choice for the organization for providing sufficient support to the
users connected in the organization. The operating system used for the server should be
compatible with the network device and support virtualization of the server. The minimum
memory for the server should be 8 Gb for supporting the virtualization of the server into two
virtual machine and manage the loads on the physical server (Ramaswamy et al. 2016). The
minimum size of the hard disk should be 1TB and 150 Gb free space should be allocated to
the virtual machine. There are different ports available and the ports should be configured for
COMPUTING AND SYSTEMS DEVELOPMENT
transmitted through the link is not available to any third part agent. The local servers should
be used for storing the frequently used data for reducing the waiting time of the user ad
increasing the redundancy of the data.
There are different RAID options that are available for the management of the file
server and hosting the website of the organization for the management of the information and
files. Among the different RAID options, RAID 5 is selected for the configuration of the
network attached storage with disk striping and parity (Shin et al. 2014). The striping is used
for reconstruction of the data if the current disk fails. It used parity for reliability and
redundancy for increasing the efficiency of the network. In the RAID configuration more
than drives are working parallel and for the optimization of the situation different levels of
RAID are applied. The RAID 0 is used for stripping, RAID 1 is used for mirroring, RAID 5
is used for parity stripping, RAID 6 is applied for double parity and RAID 10 is applied for
combination of striping and mirroring.
Lo2: Planning for the Implementation of the network operating system
2.1. Detailed plan for the implementation of the network operating system
Installation – the servers created with the minimum hardware requirement that is
essential for supporting different service and operation. The use of commercial server for
base server can be an ideal choice for the organization for providing sufficient support to the
users connected in the organization. The operating system used for the server should be
compatible with the network device and support virtualization of the server. The minimum
memory for the server should be 8 Gb for supporting the virtualization of the server into two
virtual machine and manage the loads on the physical server (Ramaswamy et al. 2016). The
minimum size of the hard disk should be 1TB and 150 Gb free space should be allocated to
the virtual machine. There are different ports available and the ports should be configured for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
COMPUTING AND SYSTEMS DEVELOPMENT
the management of the incoming and the outgoing traffic from the server. The servers should
be configured with the firewalls policy and proper addressing plan should be used for the
configuration of the interface of the device.
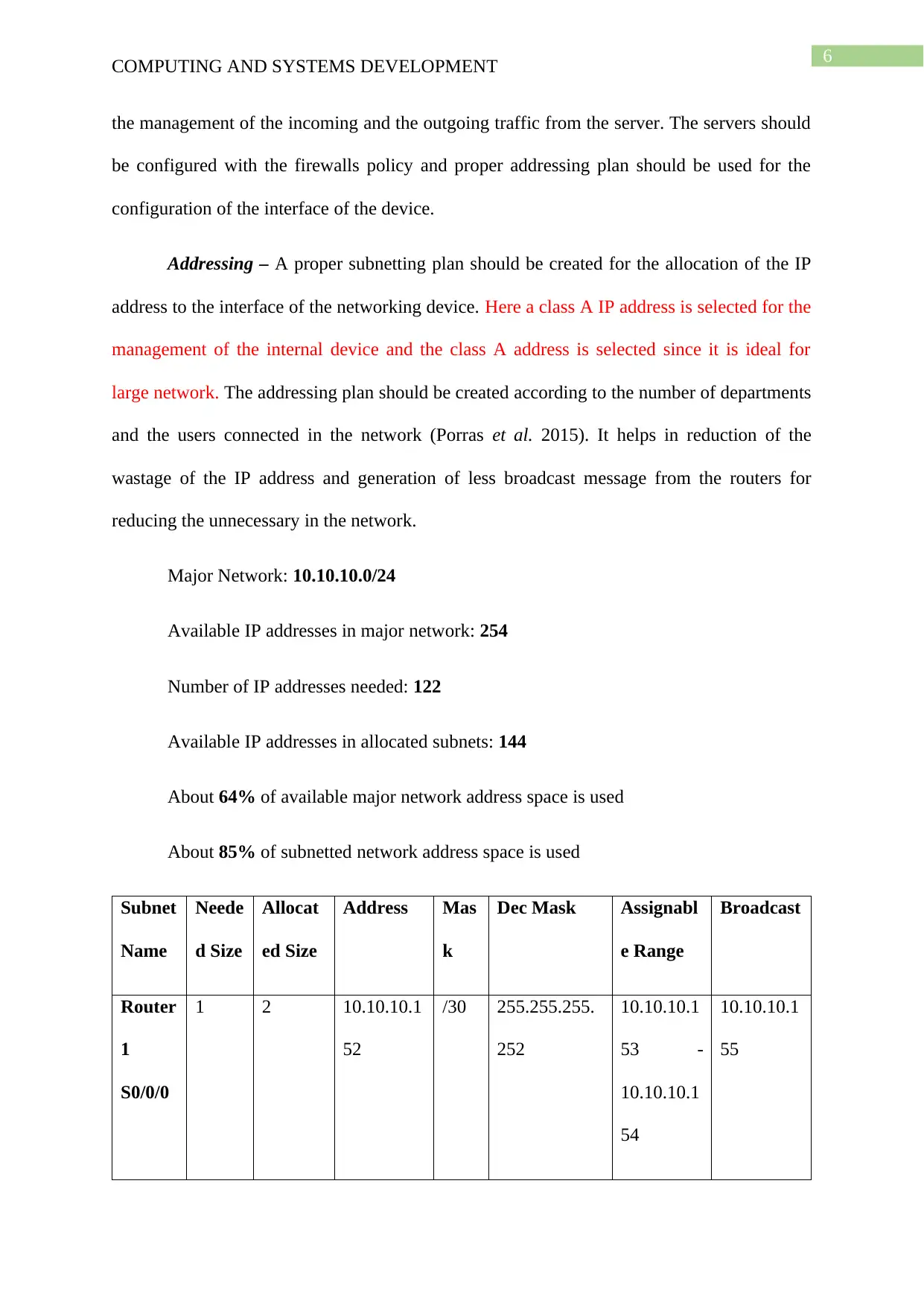
Addressing – A proper subnetting plan should be created for the allocation of the IP
address to the interface of the networking device. Here a class A IP address is selected for the
management of the internal device and the class A address is selected since it is ideal for
large network. The addressing plan should be created according to the number of departments
and the users connected in the network (Porras et al. 2015). It helps in reduction of the
wastage of the IP address and generation of less broadcast message from the routers for
reducing the unnecessary in the network.
Major Network: 10.10.10.0/24
Available IP addresses in major network: 254
Number of IP addresses needed: 122
Available IP addresses in allocated subnets: 144
About 64% of available major network address space is used
About 85% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignabl
e Range
Broadcast
Router
1
S0/0/0
1 2 10.10.10.1
52
/30 255.255.255.
252
10.10.10.1
53 -
10.10.10.1
54
10.10.10.1
55
COMPUTING AND SYSTEMS DEVELOPMENT
the management of the incoming and the outgoing traffic from the server. The servers should
be configured with the firewalls policy and proper addressing plan should be used for the
configuration of the interface of the device.
Addressing – A proper subnetting plan should be created for the allocation of the IP
address to the interface of the networking device. Here a class A IP address is selected for the
management of the internal device and the class A address is selected since it is ideal for
large network. The addressing plan should be created according to the number of departments
and the users connected in the network (Porras et al. 2015). It helps in reduction of the
wastage of the IP address and generation of less broadcast message from the routers for
reducing the unnecessary in the network.
Major Network: 10.10.10.0/24
Available IP addresses in major network: 254
Number of IP addresses needed: 122
Available IP addresses in allocated subnets: 144
About 64% of available major network address space is used
About 85% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignabl
e Range
Broadcast
Router
1
S0/0/0
1 2 10.10.10.1
52
/30 255.255.255.
252
10.10.10.1
53 -
10.10.10.1
54
10.10.10.1
55
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
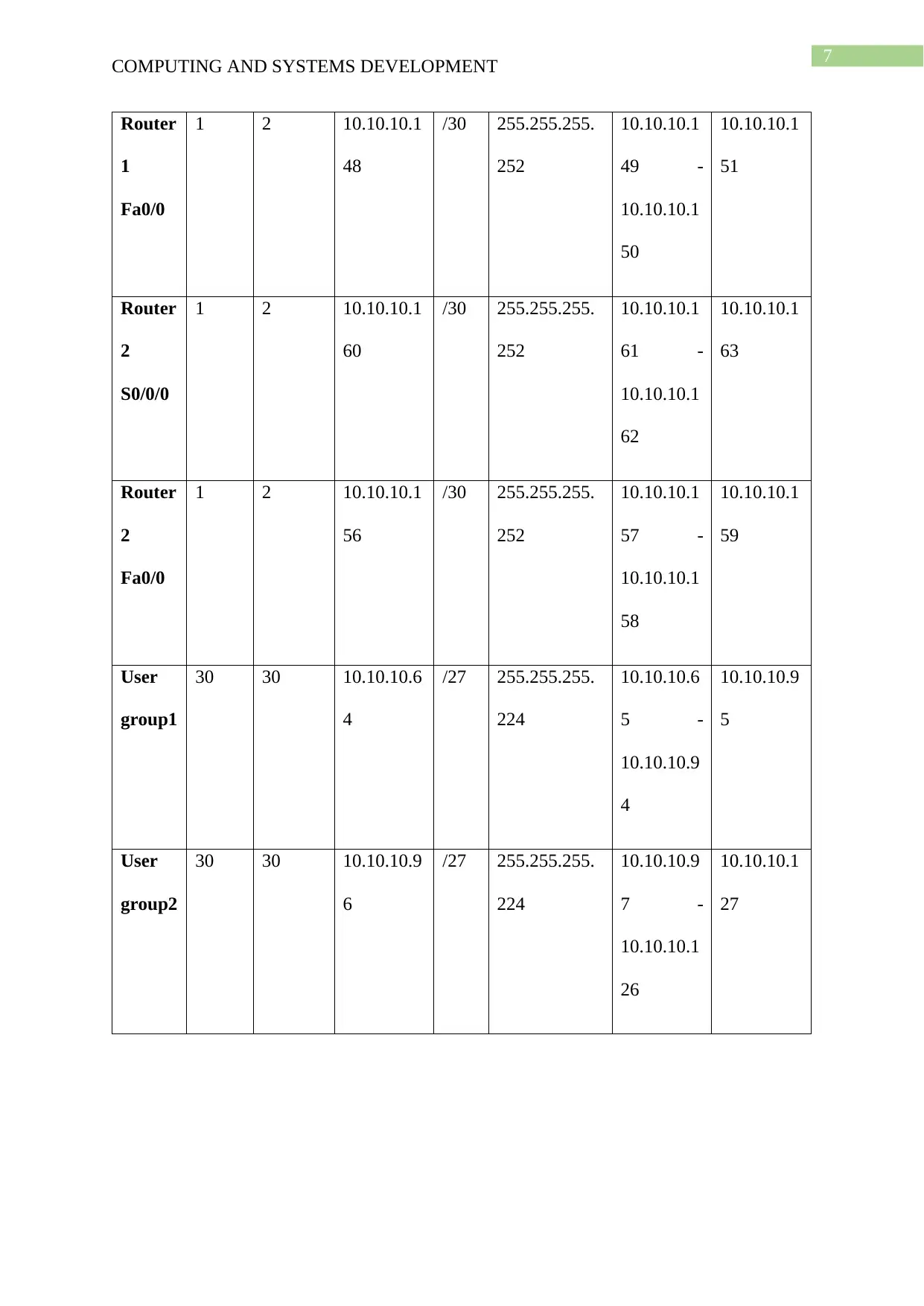
COMPUTING AND SYSTEMS DEVELOPMENT
Router
1
Fa0/0
1 2 10.10.10.1
48
/30 255.255.255.
252
10.10.10.1
49 -
10.10.10.1
50
10.10.10.1
51
Router
2
S0/0/0
1 2 10.10.10.1
60
/30 255.255.255.
252
10.10.10.1
61 -
10.10.10.1
62
10.10.10.1
63
Router
2
Fa0/0
1 2 10.10.10.1
56
/30 255.255.255.
252
10.10.10.1
57 -
10.10.10.1
58
10.10.10.1
59
User
group1
30 30 10.10.10.6
4
/27 255.255.255.
224
10.10.10.6
5 -
10.10.10.9
4
10.10.10.9
5
User
group2
30 30 10.10.10.9
6
/27 255.255.255.
224
10.10.10.9
7 -
10.10.10.1
26
10.10.10.1
27
COMPUTING AND SYSTEMS DEVELOPMENT
Router
1
Fa0/0
1 2 10.10.10.1
48
/30 255.255.255.
252
10.10.10.1
49 -
10.10.10.1
50
10.10.10.1
51
Router
2
S0/0/0
1 2 10.10.10.1
60
/30 255.255.255.
252
10.10.10.1
61 -
10.10.10.1
62
10.10.10.1
63
Router
2
Fa0/0
1 2 10.10.10.1
56
/30 255.255.255.
252
10.10.10.1
57 -
10.10.10.1
58
10.10.10.1
59
User
group1
30 30 10.10.10.6
4
/27 255.255.255.
224
10.10.10.6
5 -
10.10.10.9
4
10.10.10.9
5
User
group2
30 30 10.10.10.9
6
/27 255.255.255.
224
10.10.10.9
7 -
10.10.10.1
26
10.10.10.1
27
8
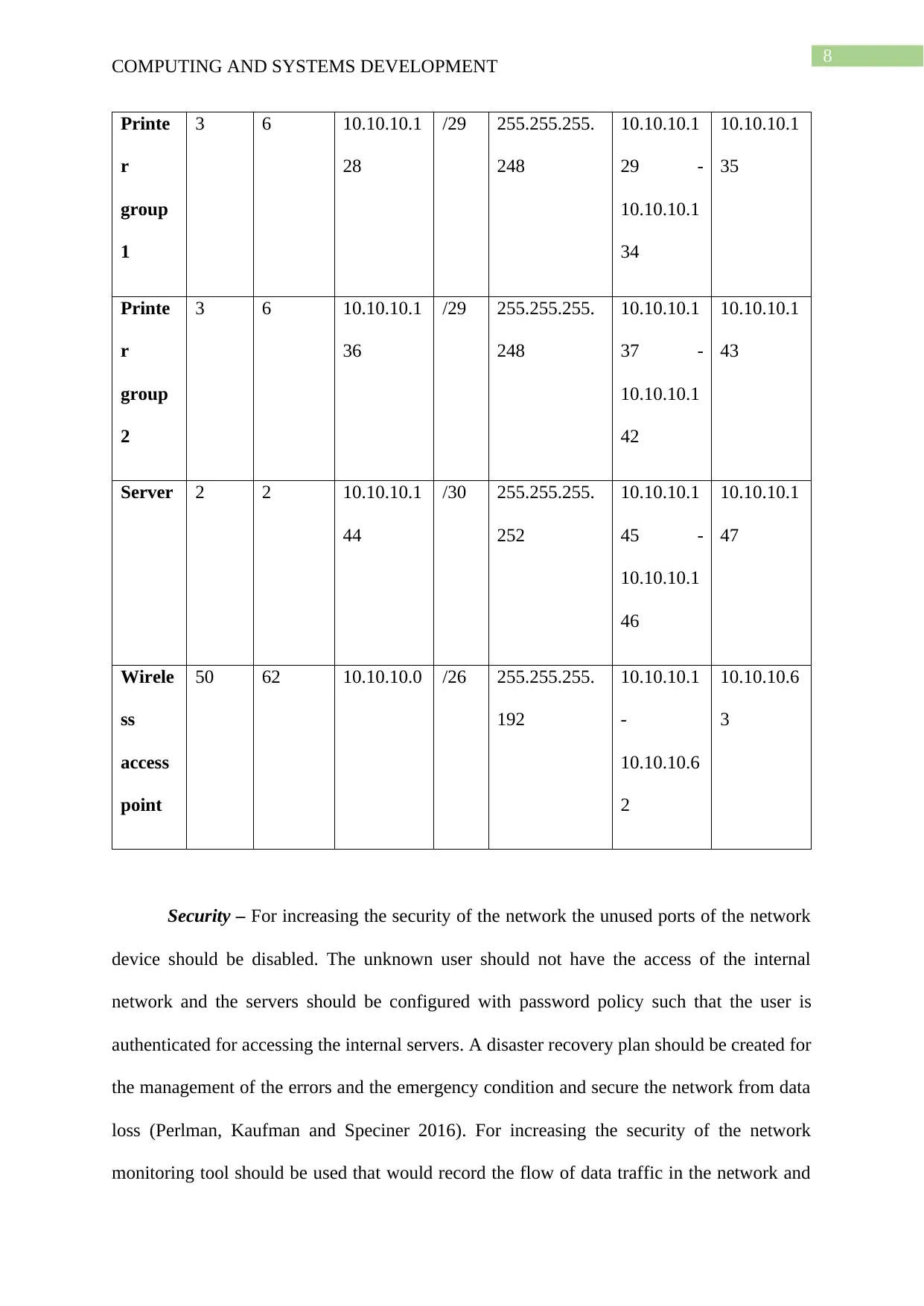
COMPUTING AND SYSTEMS DEVELOPMENT
Printe
r
group
1
3 6 10.10.10.1
28
/29 255.255.255.
248
10.10.10.1
29 -
10.10.10.1
34
10.10.10.1
35
Printe
r
group
2
3 6 10.10.10.1
36
/29 255.255.255.
248
10.10.10.1
37 -
10.10.10.1
42
10.10.10.1
43
Server 2 2 10.10.10.1
44
/30 255.255.255.
252
10.10.10.1
45 -
10.10.10.1
46
10.10.10.1
47
Wirele
ss
access
point
50 62 10.10.10.0 /26 255.255.255.
192
10.10.10.1
-
10.10.10.6
2
10.10.10.6
3
Security – For increasing the security of the network the unused ports of the network
device should be disabled. The unknown user should not have the access of the internal
network and the servers should be configured with password policy such that the user is
authenticated for accessing the internal servers. A disaster recovery plan should be created for
the management of the errors and the emergency condition and secure the network from data
loss (Perlman, Kaufman and Speciner 2016). For increasing the security of the network
monitoring tool should be used that would record the flow of data traffic in the network and
COMPUTING AND SYSTEMS DEVELOPMENT
Printe
r
group
1
3 6 10.10.10.1
28
/29 255.255.255.
248
10.10.10.1
29 -
10.10.10.1
34
10.10.10.1
35
Printe
r
group
2
3 6 10.10.10.1
36
/29 255.255.255.
248
10.10.10.1
37 -
10.10.10.1
42
10.10.10.1
43
Server 2 2 10.10.10.1
44
/30 255.255.255.
252
10.10.10.1
45 -
10.10.10.1
46
10.10.10.1
47
Wirele
ss
access
point
50 62 10.10.10.0 /26 255.255.255.
192
10.10.10.1
-
10.10.10.6
2
10.10.10.6
3
Security – For increasing the security of the network the unused ports of the network
device should be disabled. The unknown user should not have the access of the internal
network and the servers should be configured with password policy such that the user is
authenticated for accessing the internal servers. A disaster recovery plan should be created for
the management of the errors and the emergency condition and secure the network from data
loss (Perlman, Kaufman and Speciner 2016). For increasing the security of the network
monitoring tool should be used that would record the flow of data traffic in the network and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
COMPUTING AND SYSTEMS DEVELOPMENT
can be used as an evidence if any illegal attempt is made for accessing the secure information
of the organization. For increasing the security the routers should be configured with access
control list and applied to the interface of the router (Mijumbi et al. 2016). The inbound and
outbound rules should be created for blocking the unknown users to connect with the internal
server network and maintain the security of the organizational network.
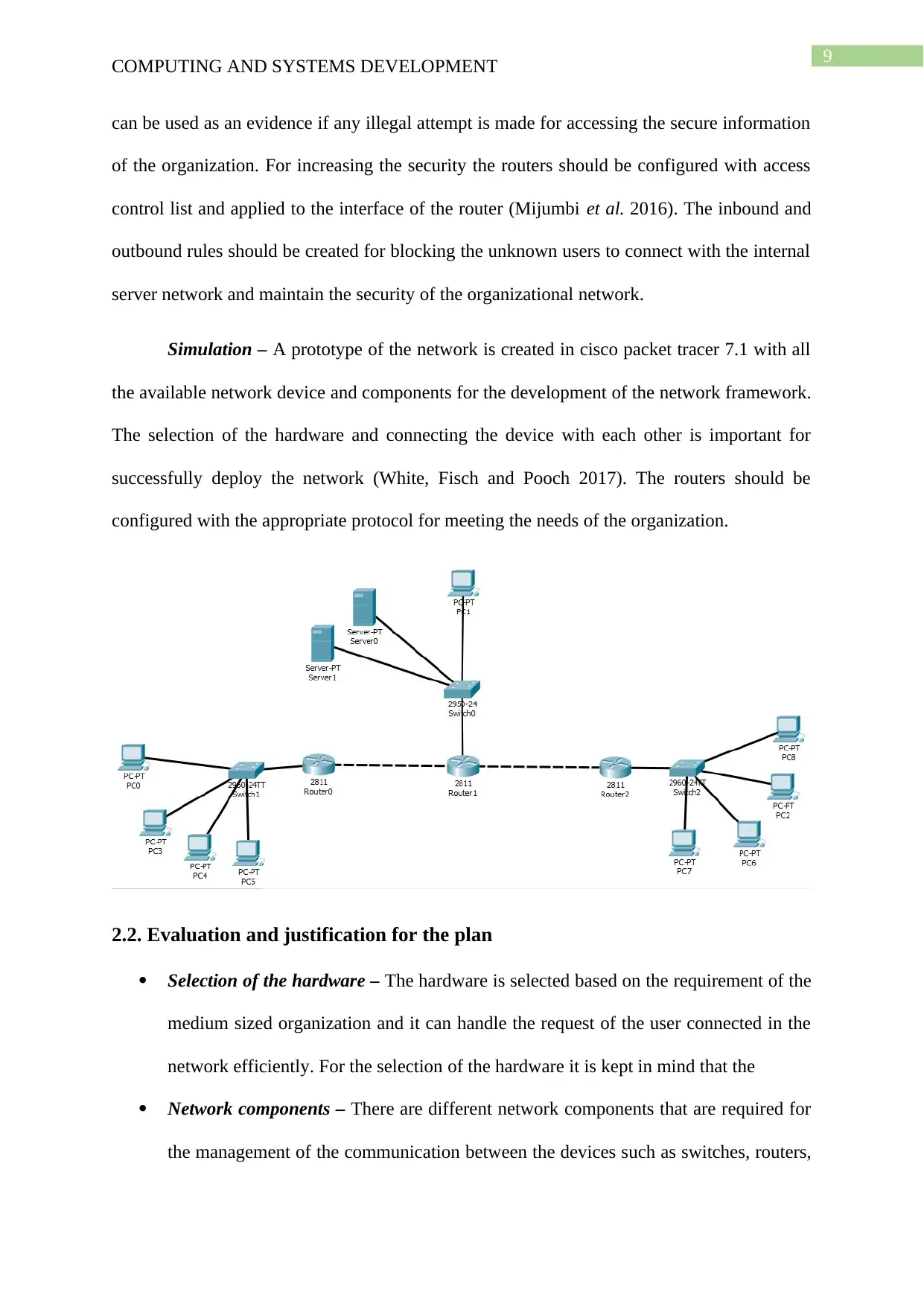
Simulation – A prototype of the network is created in cisco packet tracer 7.1 with all
the available network device and components for the development of the network framework.
The selection of the hardware and connecting the device with each other is important for
successfully deploy the network (White, Fisch and Pooch 2017). The routers should be
configured with the appropriate protocol for meeting the needs of the organization.
2.2. Evaluation and justification for the plan
Selection of the hardware – The hardware is selected based on the requirement of the
medium sized organization and it can handle the request of the user connected in the
network efficiently. For the selection of the hardware it is kept in mind that the
Network components – There are different network components that are required for
the management of the communication between the devices such as switches, routers,
COMPUTING AND SYSTEMS DEVELOPMENT
can be used as an evidence if any illegal attempt is made for accessing the secure information
of the organization. For increasing the security the routers should be configured with access
control list and applied to the interface of the router (Mijumbi et al. 2016). The inbound and
outbound rules should be created for blocking the unknown users to connect with the internal
server network and maintain the security of the organizational network.
Simulation – A prototype of the network is created in cisco packet tracer 7.1 with all
the available network device and components for the development of the network framework.
The selection of the hardware and connecting the device with each other is important for
successfully deploy the network (White, Fisch and Pooch 2017). The routers should be
configured with the appropriate protocol for meeting the needs of the organization.
2.2. Evaluation and justification for the plan
Selection of the hardware – The hardware is selected based on the requirement of the
medium sized organization and it can handle the request of the user connected in the
network efficiently. For the selection of the hardware it is kept in mind that the
Network components – There are different network components that are required for
the management of the communication between the devices such as switches, routers,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
COMPUTING AND SYSTEMS DEVELOPMENT
network interface cards, wireless access points, etc. The information should be shared
with the users using different medium and different resources should be used for the
management of the local and the network operating system.
Lo3: Implementation of the network operating system
3.1. Implementation of the selected NOS
For the implementation of the network operating system a study is made on the
mechanism and the differences across the different systems for sharing of the resources
within the users connected in the network. The execution of the jobs and the data handling
should be managed with the implementation of the network operating system (De Nooy,
Mrvar and Batagelj 2018). The data support should be used for the manipulation of the files
and manage the wide area network directory by limiting the access of the network and
maintaining the security of the network.
Installation – For the installation of the network operating system the network should
be designed with different procedures and processes and the existing hosts should be listed
that should be provided different services. The network operating system should be attached
with the hosts connected in the network and it should be used as a dedicated host (Freeman
2015). For the installation of the network operating system the hardware specification of the
server should be analysed and it should be configured for supporting the needs of the
organization. The servers should have the ability of virtualization for handling the emergency
condition and the active directory of the server should be configured for the users using the
system.
Services – There are different services such as management of the directory which is
important for the management of the different network components and eliminating the
current problems of the organization. The network administrator is responsible for
COMPUTING AND SYSTEMS DEVELOPMENT
network interface cards, wireless access points, etc. The information should be shared
with the users using different medium and different resources should be used for the
management of the local and the network operating system.
Lo3: Implementation of the network operating system
3.1. Implementation of the selected NOS
For the implementation of the network operating system a study is made on the
mechanism and the differences across the different systems for sharing of the resources
within the users connected in the network. The execution of the jobs and the data handling
should be managed with the implementation of the network operating system (De Nooy,
Mrvar and Batagelj 2018). The data support should be used for the manipulation of the files
and manage the wide area network directory by limiting the access of the network and
maintaining the security of the network.
Installation – For the installation of the network operating system the network should
be designed with different procedures and processes and the existing hosts should be listed
that should be provided different services. The network operating system should be attached
with the hosts connected in the network and it should be used as a dedicated host (Freeman
2015). For the installation of the network operating system the hardware specification of the
server should be analysed and it should be configured for supporting the needs of the
organization. The servers should have the ability of virtualization for handling the emergency
condition and the active directory of the server should be configured for the users using the
system.
Services – There are different services such as management of the directory which is
important for the management of the different network components and eliminating the
current problems of the organization. The network administrator is responsible for

11
COMPUTING AND SYSTEMS DEVELOPMENT
maintaining the directory separately for the management of the logins and sharing of files
with the different users connected in the network (Berde et al. 2014). For the network
designed for the medium sized organization Windows servers is used as the network
operating system and active directory is configured for providing different permission to the
users to access the resources of the network. The simplicity of the network can be maintained
with the configuration of the active directory and it can also be used for the management of
the large network.
Naming – For the configuration of the internal domain network the DNS name and
resolution should be configured such that there is no conflict with the initial configuration. A
single namespace should be used for the creation of the DNS zone and it can create a
mismatch with thee security zones. The use of the namespace can reduce the complexity of
the network administrator for the management of the network components. The domain can
different from each other and the naming convention helps in reducing the complexity for the
management of the dynamic environment (Esser et al. 2015). The naming convention should
be selected based on the parsability and minimum character for management of the
informational components. The name should be consistent and used for achievement of the
certain level of logic and deal with the computer name intuitively.
3.2. Configuration and testing of security policy
The security policy is the key factor of the success of the network framework and it
should be created with setting the types of domains and management of the enforcement
process for controlling the allowable transaction in the network. The transaction should
contain the set of rules for the management of the roles and responsibility of the users and
support the changes in the login session. The configuration off the network policy can restrict
the unknown user to connect with the resources of the organization without appropriate
permission.
COMPUTING AND SYSTEMS DEVELOPMENT
maintaining the directory separately for the management of the logins and sharing of files
with the different users connected in the network (Berde et al. 2014). For the network
designed for the medium sized organization Windows servers is used as the network
operating system and active directory is configured for providing different permission to the
users to access the resources of the network. The simplicity of the network can be maintained
with the configuration of the active directory and it can also be used for the management of
the large network.
Naming – For the configuration of the internal domain network the DNS name and
resolution should be configured such that there is no conflict with the initial configuration. A
single namespace should be used for the creation of the DNS zone and it can create a
mismatch with thee security zones. The use of the namespace can reduce the complexity of
the network administrator for the management of the network components. The domain can
different from each other and the naming convention helps in reducing the complexity for the
management of the dynamic environment (Esser et al. 2015). The naming convention should
be selected based on the parsability and minimum character for management of the
informational components. The name should be consistent and used for achievement of the
certain level of logic and deal with the computer name intuitively.
3.2. Configuration and testing of security policy
The security policy is the key factor of the success of the network framework and it
should be created with setting the types of domains and management of the enforcement
process for controlling the allowable transaction in the network. The transaction should
contain the set of rules for the management of the roles and responsibility of the users and
support the changes in the login session. The configuration off the network policy can restrict
the unknown user to connect with the resources of the organization without appropriate
permission.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





