Network Operating Systems Assignment Report - BTEC HND Computing
VerifiedAdded on 2023/06/10
|32
|6410
|441
Report
AI Summary
This report provides a comprehensive overview of network operating systems (NOS), covering key principles, implementation plans, and management strategies. It begins with an exploration of various operating system types, including batch, time-sharing, distributed, network, and real-time systems, with a detailed comparison of their features and functionalities. The report then delves into business continuity and disaster recovery, outlining advantages of a disaster recovery plan, backup options, and RAID configurations. A significant portion is dedicated to the implementation of a NOS, including installation and configuration of Windows Server 2016, IP addressing, and network security policies. The report also addresses network services configuration, password security policies, network performance, and availability. Finally, it discusses network management, including network monitoring tools and justification for their use in addressing network threats.

Network Operating System 1
Network Operating System
Student Name
Affiliate Institution
Network Operating System
Student Name
Affiliate Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Operating System 2
Table of Contents
1 LO1 Understand network operating systems principles.......................................................................3
1.1 Types of operating systems..........................................................................................................3
1.1.1 Batch Operating System.......................................................................................................3
1.1.2 Time-Sharing Operating Systems........................................................................................3
1.1.3 Distributed Operating Systems............................................................................................4
1.1.4 Network Operating System..................................................................................................4
1.1.5 Real-Time Operating Systems.............................................................................................5
1.1.6 Summary of Types of Network Operating Systems.............................................................5
1.1.7 My Recommended Network Operating System...................................................................8
1.2 Business Continuity and Disaster Recovery................................................................................9
1.2.1 Advantages of the Disaster Recovery Plan..........................................................................9
1.2.2 Types of backup options and devices...................................................................................9
1.2.3 Backup options....................................................................................................................9
1.2.4 Different RAID options in relation to availability..............................................................11
2 LO2: Network operating systems implementations plan...................................................................12
2.1 Plan for the Implementation of NOS..........................................................................................12
2.1.1 Installation.........................................................................................................................12
2.1.2 IP addressing......................................................................................................................13
2.1.3 Network Security Policies..................................................................................................14
2.2 Justification of Evaluation Plan and User Feedback..................................................................15
3 LO3: Network Operating system Implementation.............................................................................15
3.1 Step by step installation and configuration of windows server 2016..........................................15
3.1.1 Configuring Network Services...........................................................................................22
3.2 Configuration and Testing of Password Security Policy............................................................24
3.2.1 Threat and Password Permission Policy.............................................................................24
3.2.2 Network Performance and Availability..............................................................................25
4 LO4: Network Management..............................................................................................................26
4.1 Network Monitoring Tool..........................................................................................................26
4.1.1 Justification........................................................................................................................26
4.2 Network Monitoring against Threats.........................................................................................27
Reference List............................................................................................................................................28
Table of Contents
1 LO1 Understand network operating systems principles.......................................................................3
1.1 Types of operating systems..........................................................................................................3
1.1.1 Batch Operating System.......................................................................................................3
1.1.2 Time-Sharing Operating Systems........................................................................................3
1.1.3 Distributed Operating Systems............................................................................................4
1.1.4 Network Operating System..................................................................................................4
1.1.5 Real-Time Operating Systems.............................................................................................5
1.1.6 Summary of Types of Network Operating Systems.............................................................5
1.1.7 My Recommended Network Operating System...................................................................8
1.2 Business Continuity and Disaster Recovery................................................................................9
1.2.1 Advantages of the Disaster Recovery Plan..........................................................................9
1.2.2 Types of backup options and devices...................................................................................9
1.2.3 Backup options....................................................................................................................9
1.2.4 Different RAID options in relation to availability..............................................................11
2 LO2: Network operating systems implementations plan...................................................................12
2.1 Plan for the Implementation of NOS..........................................................................................12
2.1.1 Installation.........................................................................................................................12
2.1.2 IP addressing......................................................................................................................13
2.1.3 Network Security Policies..................................................................................................14
2.2 Justification of Evaluation Plan and User Feedback..................................................................15
3 LO3: Network Operating system Implementation.............................................................................15
3.1 Step by step installation and configuration of windows server 2016..........................................15
3.1.1 Configuring Network Services...........................................................................................22
3.2 Configuration and Testing of Password Security Policy............................................................24
3.2.1 Threat and Password Permission Policy.............................................................................24
3.2.2 Network Performance and Availability..............................................................................25
4 LO4: Network Management..............................................................................................................26
4.1 Network Monitoring Tool..........................................................................................................26
4.1.1 Justification........................................................................................................................26
4.2 Network Monitoring against Threats.........................................................................................27
Reference List............................................................................................................................................28

Network Operating System 3
1 LO1 Understand network operating systems principles
1.1 Types of operating systems
Being known to be one of the important software in a computer, an operating system is
set to the tasks of managing the memory and processes of a computer including both the
hardware and software part of a computer. You can with the help of an operating system
communicate with a computer without talking to it. A computer, therefore, can be declared to be
useless without an operating system (Technopedia, 2018). Since the error of first computer
generation, an operating system has been there despite all the evolving processes that are known.
There are a number of types of operating systems which I am going to share in this chapter.
1.1.1 Batch Operating System
In this type, there is no direct interaction between the users of the operating system with
the computer (Pillai, 2017). Users have to involve the services of off-line devices a good
example being punch cards to be able to prepare their jobs and there after they submit them to
the computer operator. There is a need for batching jobs with similar characters together and
running them as a group so as to speed up the processing rates (Anderson, 2018). It is usually
the work of the operator to make sure that the jobs that are left with him by the programmers are
sort into batches with respect to similar requirements. There are some disadvantages that came
with Batch Systems like the absence of user job interaction, slower speed due to delayed
mechanical input-output processes, and poor prioritization.
1.1.2 Time-Sharing Operating Systems
Here, users located at different locations are able to use a particular computer just at the
same time. This is also referred to by many as multitasking or a logical continuation of
multiprogramming. The time of the processor that is shared by many users at the same time is
1 LO1 Understand network operating systems principles
1.1 Types of operating systems
Being known to be one of the important software in a computer, an operating system is
set to the tasks of managing the memory and processes of a computer including both the
hardware and software part of a computer. You can with the help of an operating system
communicate with a computer without talking to it. A computer, therefore, can be declared to be
useless without an operating system (Technopedia, 2018). Since the error of first computer
generation, an operating system has been there despite all the evolving processes that are known.
There are a number of types of operating systems which I am going to share in this chapter.
1.1.1 Batch Operating System
In this type, there is no direct interaction between the users of the operating system with
the computer (Pillai, 2017). Users have to involve the services of off-line devices a good
example being punch cards to be able to prepare their jobs and there after they submit them to
the computer operator. There is a need for batching jobs with similar characters together and
running them as a group so as to speed up the processing rates (Anderson, 2018). It is usually
the work of the operator to make sure that the jobs that are left with him by the programmers are
sort into batches with respect to similar requirements. There are some disadvantages that came
with Batch Systems like the absence of user job interaction, slower speed due to delayed
mechanical input-output processes, and poor prioritization.
1.1.2 Time-Sharing Operating Systems
Here, users located at different locations are able to use a particular computer just at the
same time. This is also referred to by many as multitasking or a logical continuation of
multiprogramming. The time of the processor that is shared by many users at the same time is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Operating System 4
what is simply termed as time-sharing (Chasing, 2018). When differentiating between Time-
Sharing and Batch Systems, in Time-Sharing, the main objective here is to reduce response time
whereas, in Batch Systems, the main objective is to reduce processor time. Time-Sharing
Operating Systems have the advantages like Quick response time, reduced CPU idle time, and
there is no duplication of software. However, it is disadvantaged in terms of reliability, poor data
communication, and the user’s data is not very secure in this type of Operating System
(Networks, 2015).
1.1.3 Distributed Operating Systems
Multiple users and multiple real-time applications are served by multiple central
processors in these types of operating systems. There is the distribution of jobs among the
processors accordingly (chennaicisco. 2013). Various communication lines are used by the
processors like the likes of high-speed buses to communicate to each other. Distributed systems
are also referred to by many people as loosely coupled systems. This types of Operating
Systems have the advantages like a high rate of data exchange through electronic mail, sharing of
resources among users, the robustness of the system since the failure of one site does not affect
the other, minimal delay in processing data, and the host computer is relieved a lot of burdens
(Mullins, 2018).
1.1.4 Network Operating System
This type is set to run on the server allowing the serve r to manage users, data, security,
applications and many more tasks (Cisco, 2013). This type mainly came to enable sharing of
resources among users over the network. There are examples of network operating systems like
Linux, Unix, Mac OS, Microsoft Windows Server 2003 among others. This type has the
advantages of good server managed security protocol, the stability of centralized servers, easy
upgrade process, and the advantage of remote access (ComputerNetworkingNotes. 2018).
what is simply termed as time-sharing (Chasing, 2018). When differentiating between Time-
Sharing and Batch Systems, in Time-Sharing, the main objective here is to reduce response time
whereas, in Batch Systems, the main objective is to reduce processor time. Time-Sharing
Operating Systems have the advantages like Quick response time, reduced CPU idle time, and
there is no duplication of software. However, it is disadvantaged in terms of reliability, poor data
communication, and the user’s data is not very secure in this type of Operating System
(Networks, 2015).
1.1.3 Distributed Operating Systems
Multiple users and multiple real-time applications are served by multiple central
processors in these types of operating systems. There is the distribution of jobs among the
processors accordingly (chennaicisco. 2013). Various communication lines are used by the
processors like the likes of high-speed buses to communicate to each other. Distributed systems
are also referred to by many people as loosely coupled systems. This types of Operating
Systems have the advantages like a high rate of data exchange through electronic mail, sharing of
resources among users, the robustness of the system since the failure of one site does not affect
the other, minimal delay in processing data, and the host computer is relieved a lot of burdens
(Mullins, 2018).
1.1.4 Network Operating System
This type is set to run on the server allowing the serve r to manage users, data, security,
applications and many more tasks (Cisco, 2013). This type mainly came to enable sharing of
resources among users over the network. There are examples of network operating systems like
Linux, Unix, Mac OS, Microsoft Windows Server 2003 among others. This type has the
advantages of good server managed security protocol, the stability of centralized servers, easy
upgrade process, and the advantage of remote access (ComputerNetworkingNotes. 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Operating System 5
Despite all these advantages, these types of Operating Systems have downfalls like high cost,
decentralization, and maintaining and updating is required regularly.
1.1.5 Real-Time Operating Systems
In these types of systems, the time interval for data to be processed and the response to
input is very minimal to an extend that it ends up controlling the environment. The response time
is that period hat is required from the input moment and the output time. Therefore, this is to
mean that in this method, there is less response time when compared to the online type. These
types are used in case of rigid time required in consideration to the flow of data (Docs.ovh.com,
2018). There is a need for a real-time operating system to have the characters of fixed time
constraints to avoid failure. There are as now two types of real-time operating systems namely
Hard and Soft real-time systems. In hard real-time systems, there is a guarantee of on-time
completion of critical tasks and there is no secondary storage meaning the data is just stored in
ROM hence you can conclude that there is no virtual memory. In case of Soft real-time systems,
there are minimal restrictions. Tasks are executed in terms of priority meaning that high priority
tasks are executed until they are over so that the next in line task can come in (Mitchell, 2017).
1.1.6 Summary of Types of Network Operating Systems
Feature Linux Windows Dos comparison
customizatio
n
Its code can be
customized to
the desired
level.
You only have
the capability to
change the color,
background, and
fonts of the
desktop.
The only option
to customize it
is by
downloading its
expansions.
Of all the three,
Linux is the most
customizable due to
its character of
being open source.
Despite Dos being
open source, there
Despite all these advantages, these types of Operating Systems have downfalls like high cost,
decentralization, and maintaining and updating is required regularly.
1.1.5 Real-Time Operating Systems
In these types of systems, the time interval for data to be processed and the response to
input is very minimal to an extend that it ends up controlling the environment. The response time
is that period hat is required from the input moment and the output time. Therefore, this is to
mean that in this method, there is less response time when compared to the online type. These
types are used in case of rigid time required in consideration to the flow of data (Docs.ovh.com,
2018). There is a need for a real-time operating system to have the characters of fixed time
constraints to avoid failure. There are as now two types of real-time operating systems namely
Hard and Soft real-time systems. In hard real-time systems, there is a guarantee of on-time
completion of critical tasks and there is no secondary storage meaning the data is just stored in
ROM hence you can conclude that there is no virtual memory. In case of Soft real-time systems,
there are minimal restrictions. Tasks are executed in terms of priority meaning that high priority
tasks are executed until they are over so that the next in line task can come in (Mitchell, 2017).
1.1.6 Summary of Types of Network Operating Systems
Feature Linux Windows Dos comparison
customizatio
n
Its code can be
customized to
the desired
level.
You only have
the capability to
change the color,
background, and
fonts of the
desktop.
The only option
to customize it
is by
downloading its
expansions.
Of all the three,
Linux is the most
customizable due to
its character of
being open source.
Despite Dos being
open source, there
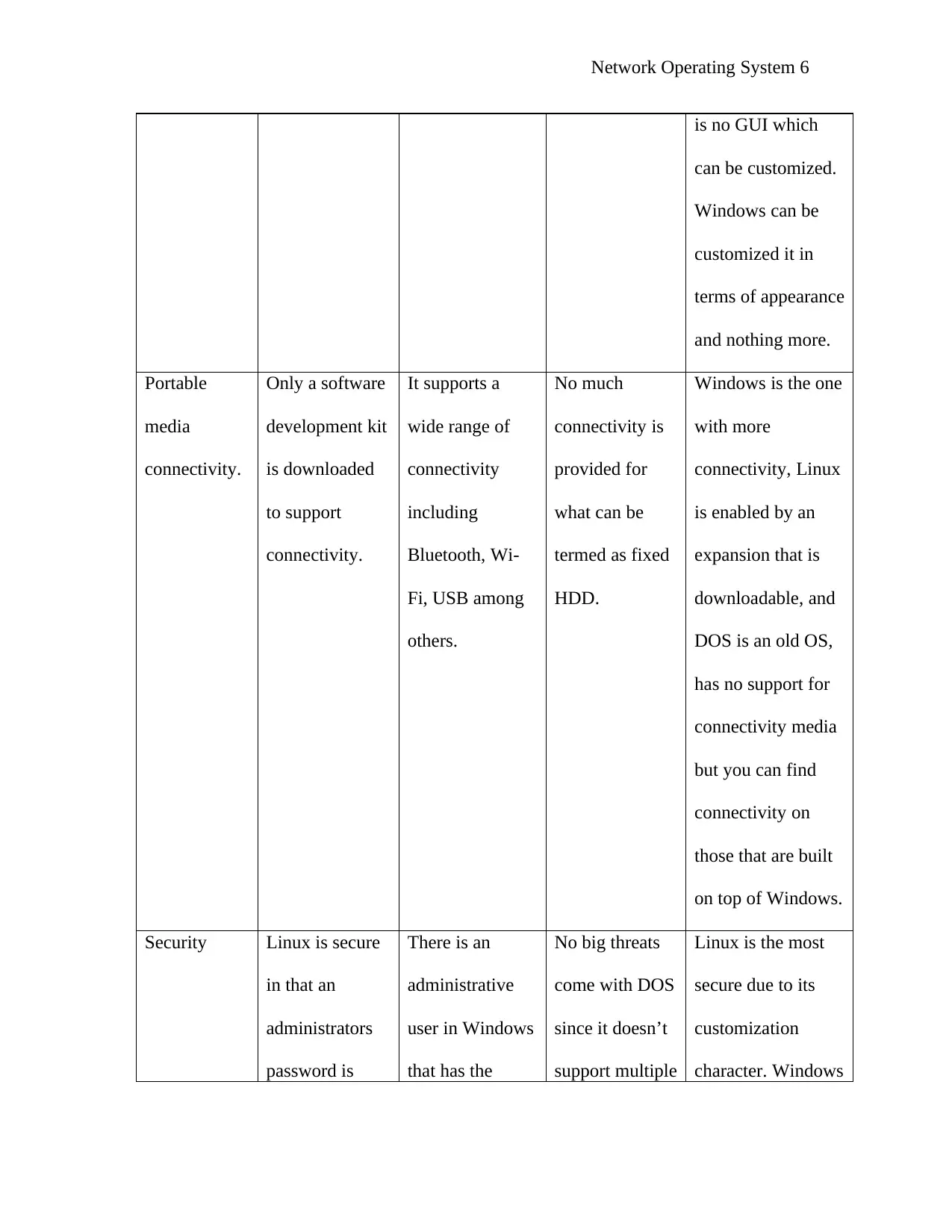
Network Operating System 6
is no GUI which
can be customized.
Windows can be
customized it in
terms of appearance
and nothing more.
Portable
media
connectivity.
Only a software
development kit
is downloaded
to support
connectivity.
It supports a
wide range of
connectivity
including
Bluetooth, Wi-
Fi, USB among
others.
No much
connectivity is
provided for
what can be
termed as fixed
HDD.
Windows is the one
with more
connectivity, Linux
is enabled by an
expansion that is
downloadable, and
DOS is an old OS,
has no support for
connectivity media
but you can find
connectivity on
those that are built
on top of Windows.
Security Linux is secure
in that an
administrators
password is
There is an
administrative
user in Windows
that has the
No big threats
come with DOS
since it doesn’t
support multiple
Linux is the most
secure due to its
customization
character. Windows
is no GUI which
can be customized.
Windows can be
customized it in
terms of appearance
and nothing more.
Portable
media
connectivity.
Only a software
development kit
is downloaded
to support
connectivity.
It supports a
wide range of
connectivity
including
Bluetooth, Wi-
Fi, USB among
others.
No much
connectivity is
provided for
what can be
termed as fixed
HDD.
Windows is the one
with more
connectivity, Linux
is enabled by an
expansion that is
downloadable, and
DOS is an old OS,
has no support for
connectivity media
but you can find
connectivity on
those that are built
on top of Windows.
Security Linux is secure
in that an
administrators
password is
There is an
administrative
user in Windows
that has the
No big threats
come with DOS
since it doesn’t
support multiple
Linux is the most
secure due to its
customization
character. Windows
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
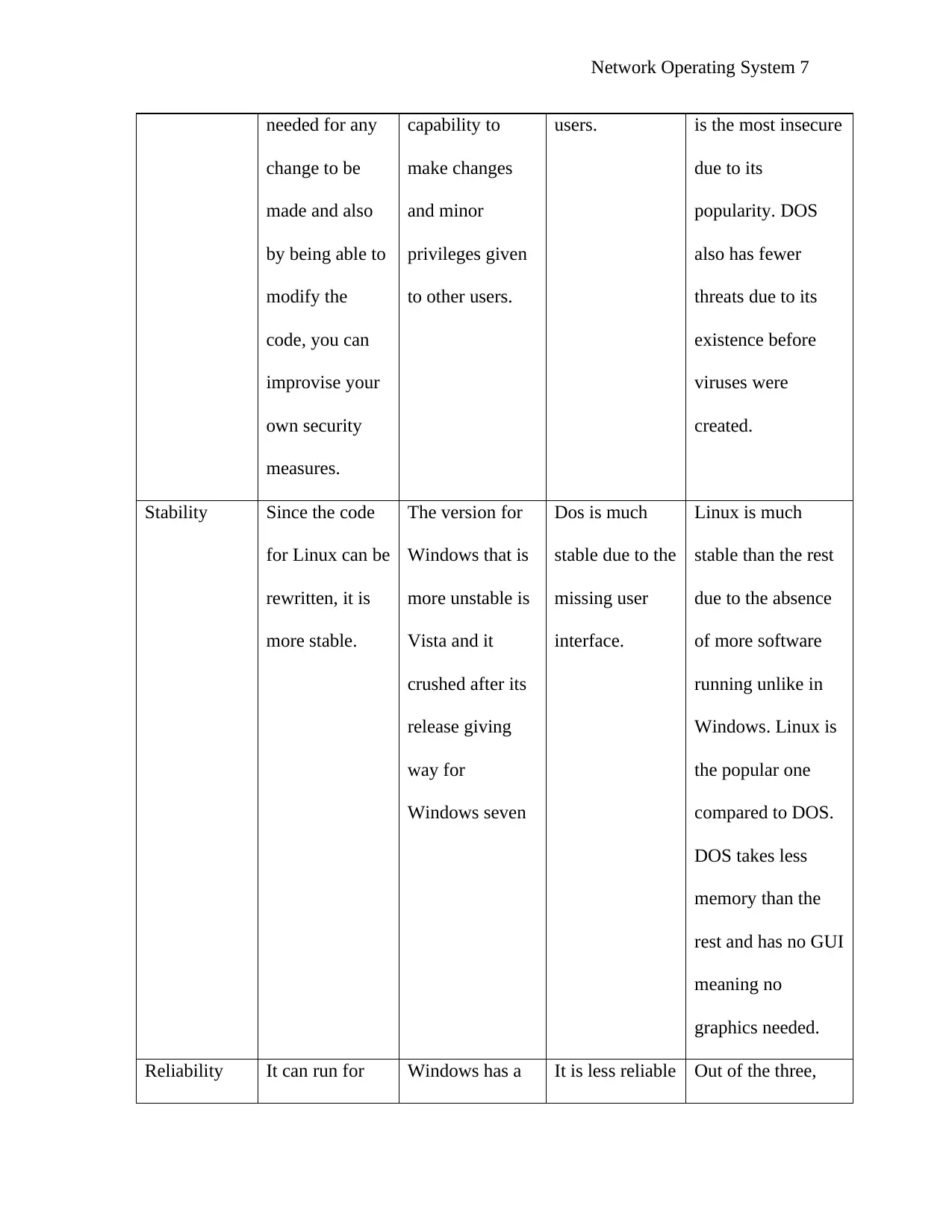
Network Operating System 7
needed for any
change to be
made and also
by being able to
modify the
code, you can
improvise your
own security
measures.
capability to
make changes
and minor
privileges given
to other users.
users. is the most insecure
due to its
popularity. DOS
also has fewer
threats due to its
existence before
viruses were
created.
Stability Since the code
for Linux can be
rewritten, it is
more stable.
The version for
Windows that is
more unstable is
Vista and it
crushed after its
release giving
way for
Windows seven
Dos is much
stable due to the
missing user
interface.
Linux is much
stable than the rest
due to the absence
of more software
running unlike in
Windows. Linux is
the popular one
compared to DOS.
DOS takes less
memory than the
rest and has no GUI
meaning no
graphics needed.
Reliability It can run for Windows has a It is less reliable Out of the three,
needed for any
change to be
made and also
by being able to
modify the
code, you can
improvise your
own security
measures.
capability to
make changes
and minor
privileges given
to other users.
users. is the most insecure
due to its
popularity. DOS
also has fewer
threats due to its
existence before
viruses were
created.
Stability Since the code
for Linux can be
rewritten, it is
more stable.
The version for
Windows that is
more unstable is
Vista and it
crushed after its
release giving
way for
Windows seven
Dos is much
stable due to the
missing user
interface.
Linux is much
stable than the rest
due to the absence
of more software
running unlike in
Windows. Linux is
the popular one
compared to DOS.
DOS takes less
memory than the
rest and has no GUI
meaning no
graphics needed.
Reliability It can run for Windows has a It is less reliable Out of the three,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
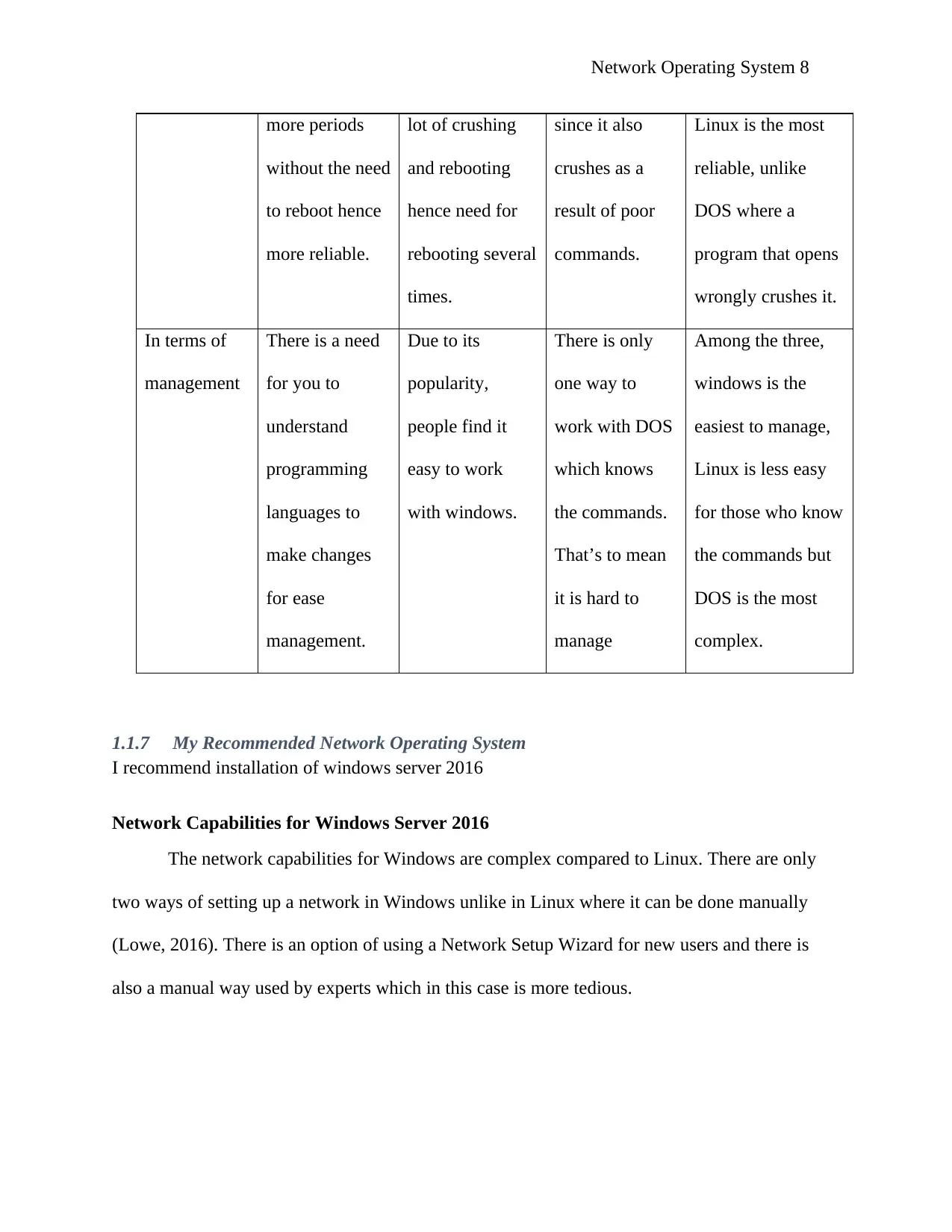
Network Operating System 8
more periods
without the need
to reboot hence
more reliable.
lot of crushing
and rebooting
hence need for
rebooting several
times.
since it also
crushes as a
result of poor
commands.
Linux is the most
reliable, unlike
DOS where a
program that opens
wrongly crushes it.
In terms of
management
There is a need
for you to
understand
programming
languages to
make changes
for ease
management.
Due to its
popularity,
people find it
easy to work
with windows.
There is only
one way to
work with DOS
which knows
the commands.
That’s to mean
it is hard to
manage
Among the three,
windows is the
easiest to manage,
Linux is less easy
for those who know
the commands but
DOS is the most
complex.
1.1.7 My Recommended Network Operating System
I recommend installation of windows server 2016
Network Capabilities for Windows Server 2016
The network capabilities for Windows are complex compared to Linux. There are only
two ways of setting up a network in Windows unlike in Linux where it can be done manually
(Lowe, 2016). There is an option of using a Network Setup Wizard for new users and there is
also a manual way used by experts which in this case is more tedious.
more periods
without the need
to reboot hence
more reliable.
lot of crushing
and rebooting
hence need for
rebooting several
times.
since it also
crushes as a
result of poor
commands.
Linux is the most
reliable, unlike
DOS where a
program that opens
wrongly crushes it.
In terms of
management
There is a need
for you to
understand
programming
languages to
make changes
for ease
management.
Due to its
popularity,
people find it
easy to work
with windows.
There is only
one way to
work with DOS
which knows
the commands.
That’s to mean
it is hard to
manage
Among the three,
windows is the
easiest to manage,
Linux is less easy
for those who know
the commands but
DOS is the most
complex.
1.1.7 My Recommended Network Operating System
I recommend installation of windows server 2016
Network Capabilities for Windows Server 2016
The network capabilities for Windows are complex compared to Linux. There are only
two ways of setting up a network in Windows unlike in Linux where it can be done manually
(Lowe, 2016). There is an option of using a Network Setup Wizard for new users and there is
also a manual way used by experts which in this case is more tedious.

Network Operating System 9
1.2 Business Continuity and Disaster Recovery
Business continuity is proactive measure put in place by an organization in the process of
making sure that after a disaster, there is a continuation of its functions (Rouse, 2018). There is a
complete planning that is set up putting in mind long-term challenges that may arise for the
organization to succeed. Disaster recovery, on the other hand, is more of reactive in nature
meaning are set options that an organization can take after a disaster so that it can bounce back to
its normality. Disaster recovery focuses on the technological infrastructure whereas Business
continuity bases on the organization as a whole unit (Plett, 2018). The similar thing about them is
that they both put in mind various events that are unplanned like cyberattacks and natural
disasters. They also focus on a goal of getting a business to run in a normal way.
1.2.1 Advantages of the Disaster Recovery Plan
At the end of the exercise, the hardware and data are always protected.
A business is more prepared for any disaster that may come by.
Down-time is reduced and recovery for essential data is easy.
An image of an organization is protected hence it will stand out to be a reliable company.
1.2.2 Types of backup options and devices
Unlike the past where it was hard for you to backup due to the high cost of tape drives,
today there are a number of back up devices and options as you may wish (SearchStorage, 2015).
A good example is CDs, DVDs, and External Hard Drives Online Storage Services among
others.
1.2.3 Backup options
There are generally three options for the backup processes namely, incremental, full, and
differential.
1.2 Business Continuity and Disaster Recovery
Business continuity is proactive measure put in place by an organization in the process of
making sure that after a disaster, there is a continuation of its functions (Rouse, 2018). There is a
complete planning that is set up putting in mind long-term challenges that may arise for the
organization to succeed. Disaster recovery, on the other hand, is more of reactive in nature
meaning are set options that an organization can take after a disaster so that it can bounce back to
its normality. Disaster recovery focuses on the technological infrastructure whereas Business
continuity bases on the organization as a whole unit (Plett, 2018). The similar thing about them is
that they both put in mind various events that are unplanned like cyberattacks and natural
disasters. They also focus on a goal of getting a business to run in a normal way.
1.2.1 Advantages of the Disaster Recovery Plan
At the end of the exercise, the hardware and data are always protected.
A business is more prepared for any disaster that may come by.
Down-time is reduced and recovery for essential data is easy.
An image of an organization is protected hence it will stand out to be a reliable company.
1.2.2 Types of backup options and devices
Unlike the past where it was hard for you to backup due to the high cost of tape drives,
today there are a number of back up devices and options as you may wish (SearchStorage, 2015).
A good example is CDs, DVDs, and External Hard Drives Online Storage Services among
others.
1.2.3 Backup options
There are generally three options for the backup processes namely, incremental, full, and
differential.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Operating System 10
Full Backup
Here, a full copy of all your data set is backed up. There is a lot of time taken for this
process hence most organization don’t go for it. The number of tapes required is also the reason
as to why it is not mostly used.
Incremental Backup
They came as a way to reduce the time taken while doing a full backup. It is known to
only backup the data that changes during the previous backup (Slater, 2015). This type has the
disadvantage of time consuming when trying to restore and in the process, if one tape happens to
be damaged or missing, there cannot be a full restoration.
Differential Backup
This type is similar to incremental in a way that at the start, there is a full backup but as
the process continues, only data that has changed is backed up (Meena, 2017). This type contains
all the data that has changed considering the last backup, unlike incremental backup where it
only contains data that has transformed since the preceding backup. This type also has the
advantage of shorter restore time compared to incremental backup.
Synthetic full backup
This is known to be a variation of the incremental backup where by it takes data step by
step unlike the original incremental where a full backup is taken and a sequence in the
incremental backup (Stanek, 2018). The backup server in this type has the capability to produce
a full backup. The full backup is combined with data that comes from the incremental backup to
produce a full backup. It has an advantage of reduced restore time. There is also decreased time
taken to backup.
Increased-forever backup
Full Backup
Here, a full copy of all your data set is backed up. There is a lot of time taken for this
process hence most organization don’t go for it. The number of tapes required is also the reason
as to why it is not mostly used.
Incremental Backup
They came as a way to reduce the time taken while doing a full backup. It is known to
only backup the data that changes during the previous backup (Slater, 2015). This type has the
disadvantage of time consuming when trying to restore and in the process, if one tape happens to
be damaged or missing, there cannot be a full restoration.
Differential Backup
This type is similar to incremental in a way that at the start, there is a full backup but as
the process continues, only data that has changed is backed up (Meena, 2017). This type contains
all the data that has changed considering the last backup, unlike incremental backup where it
only contains data that has transformed since the preceding backup. This type also has the
advantage of shorter restore time compared to incremental backup.
Synthetic full backup
This is known to be a variation of the incremental backup where by it takes data step by
step unlike the original incremental where a full backup is taken and a sequence in the
incremental backup (Stanek, 2018). The backup server in this type has the capability to produce
a full backup. The full backup is combined with data that comes from the incremental backup to
produce a full backup. It has an advantage of reduced restore time. There is also decreased time
taken to backup.
Increased-forever backup
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Operating System 11
There are disk-to-disk-to-tape systems which are used in this type of backup. A full
backup of data is taken at the start just like the incremental backup. It has an advantage of data
availability due to the automation of restoration process meaning you can easily figure out the
kind of data that you want to restore (Mbaocha, 2012).
The best backup type
An organization has to consider the kind of backup that is the best based on the kind of
data they have and how they value data security (cloud-services, 2017). An organization before
going for a certain type has to ask itself questions like;
What type of backup is compatible with my applications?
Considering the recovery of data, what does my service-level agreement state?
Are the policies with respect to storing of backup tapes offsite favoring the backup type I
want?
1.2.4 Different RAID options in relation to availability
There is no organization that can wish to manage two or more systems that perform a task
that can be handled by one system (Guide, 2011). However, there is need to understand the
organization’s use case for the success to be realized. This is also the same thing with RAID
arrays and archiving. Earlier, there were only two choices for the enterprise archives which were
RAID arrays and tape Silos (Subnetting, 2010). Despite Tape Silos being a cheaper way to
archive a large amount of data, a lot of enterprises are going for the RAID arrays with the target
of re-purposing them in the process of using them. There are currently modern disk-based
archives which have the characters of data durability, rapid retrieval of data and an entry price
that is more affordable. Through hardware and redundancy, the storage system availability can
be achieved but data redundancy can be achieved through durability (Macken, 2016).
There are disk-to-disk-to-tape systems which are used in this type of backup. A full
backup of data is taken at the start just like the incremental backup. It has an advantage of data
availability due to the automation of restoration process meaning you can easily figure out the
kind of data that you want to restore (Mbaocha, 2012).
The best backup type
An organization has to consider the kind of backup that is the best based on the kind of
data they have and how they value data security (cloud-services, 2017). An organization before
going for a certain type has to ask itself questions like;
What type of backup is compatible with my applications?
Considering the recovery of data, what does my service-level agreement state?
Are the policies with respect to storing of backup tapes offsite favoring the backup type I
want?
1.2.4 Different RAID options in relation to availability
There is no organization that can wish to manage two or more systems that perform a task
that can be handled by one system (Guide, 2011). However, there is need to understand the
organization’s use case for the success to be realized. This is also the same thing with RAID
arrays and archiving. Earlier, there were only two choices for the enterprise archives which were
RAID arrays and tape Silos (Subnetting, 2010). Despite Tape Silos being a cheaper way to
archive a large amount of data, a lot of enterprises are going for the RAID arrays with the target
of re-purposing them in the process of using them. There are currently modern disk-based
archives which have the characters of data durability, rapid retrieval of data and an entry price
that is more affordable. Through hardware and redundancy, the storage system availability can
be achieved but data redundancy can be achieved through durability (Macken, 2016).
Network Operating System 12
There are more than two hardware components that are supported by RAID arrays which
include I/O paths, controllers among others which are set to service the drive failures. Six nines
(99.9999) availability are achieved by RAID arrays which can put your data at a great risk if they
fail (www.tutorialspoint.com, 2018). RAID has an advantage in that failure of one drive brings in
high chances of the other backup drive to fail.
The Modern Approach
High availability storages that are object based are used nowadays which are estimated to
achieve an approximation of 99.9999999999999% or even more with an effort of ensuring
perfect data preservation (Administrator. 2018). It, therefore, means that no matter the amount of
objects you can store, there is only one that is readable. The way data is laid out on storage and
encoded makes it easy for a durable archive to make its achievements.
2 LO2: Network operating systems implementations plan
2.1 Plan for the Implementation of NOS
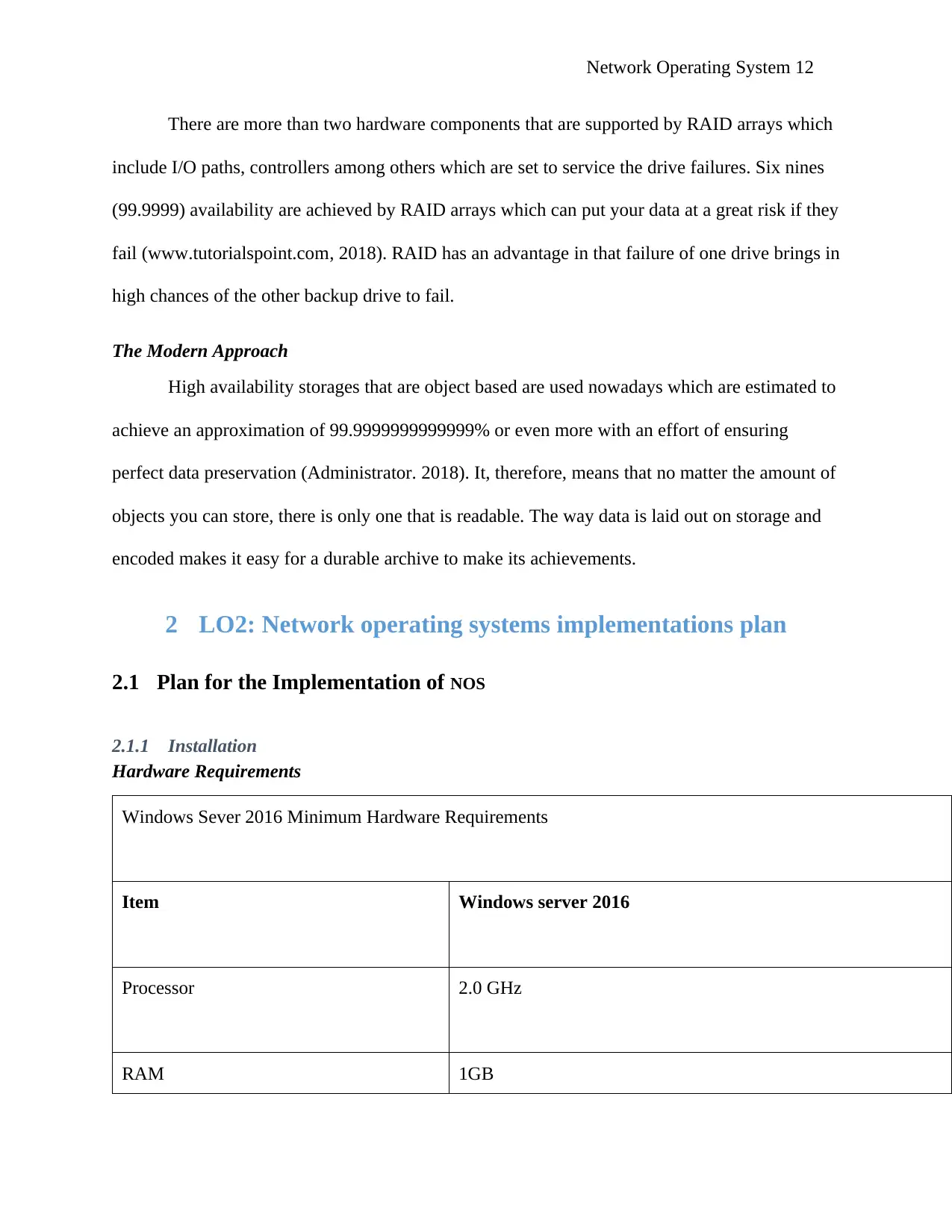
2.1.1 Installation
Hardware Requirements
Windows Sever 2016 Minimum Hardware Requirements
Item Windows server 2016
Processor 2.0 GHz
RAM 1GB
There are more than two hardware components that are supported by RAID arrays which
include I/O paths, controllers among others which are set to service the drive failures. Six nines
(99.9999) availability are achieved by RAID arrays which can put your data at a great risk if they
fail (www.tutorialspoint.com, 2018). RAID has an advantage in that failure of one drive brings in
high chances of the other backup drive to fail.
The Modern Approach
High availability storages that are object based are used nowadays which are estimated to
achieve an approximation of 99.9999999999999% or even more with an effort of ensuring
perfect data preservation (Administrator. 2018). It, therefore, means that no matter the amount of
objects you can store, there is only one that is readable. The way data is laid out on storage and
encoded makes it easy for a durable archive to make its achievements.
2 LO2: Network operating systems implementations plan
2.1 Plan for the Implementation of NOS
2.1.1 Installation
Hardware Requirements
Windows Sever 2016 Minimum Hardware Requirements
Item Windows server 2016
Processor 2.0 GHz
RAM 1GB
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




