University Network Vulnerability and Penetration Testing Report
VerifiedAdded on 2022/10/01
|26
|1373
|25
Report
AI Summary
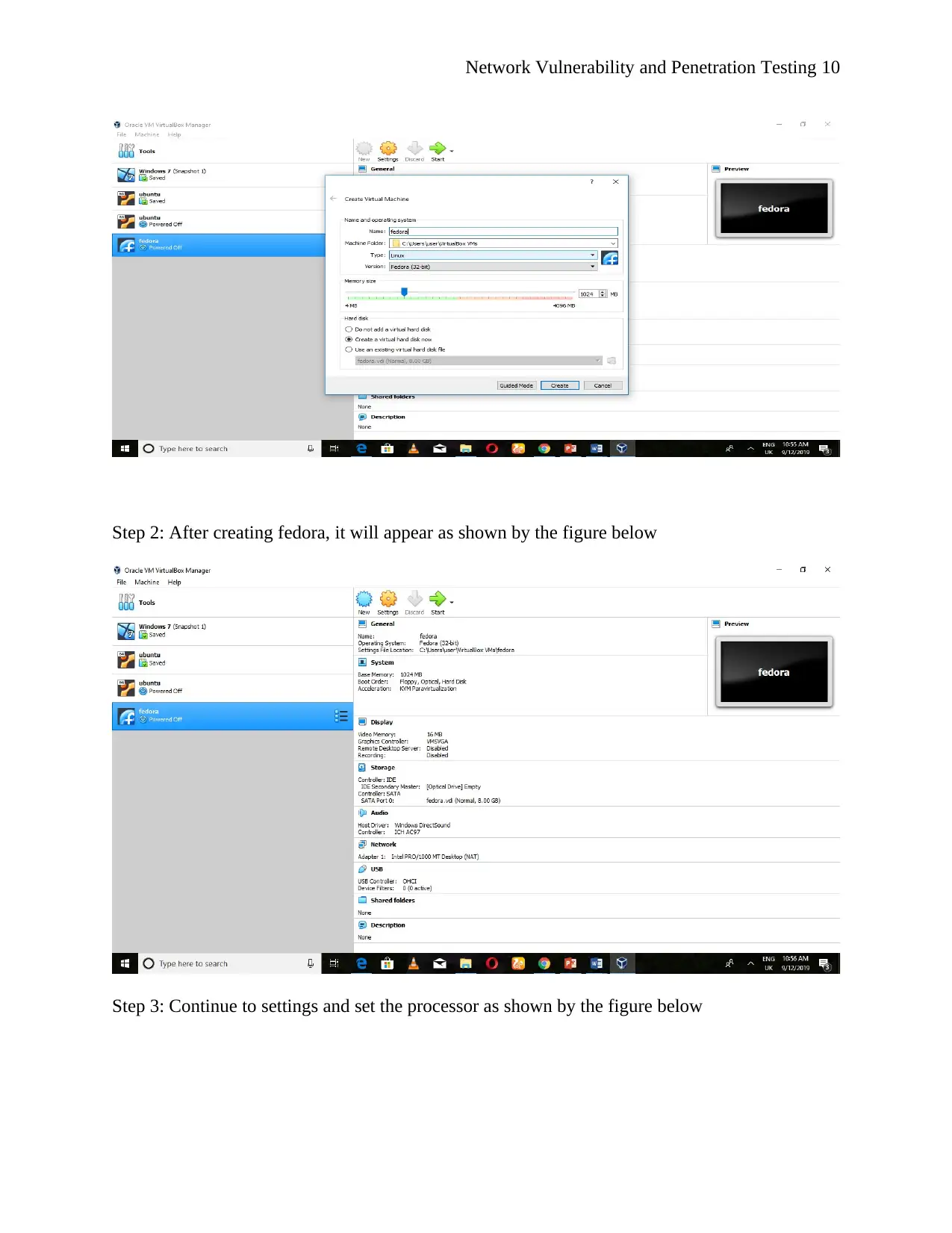
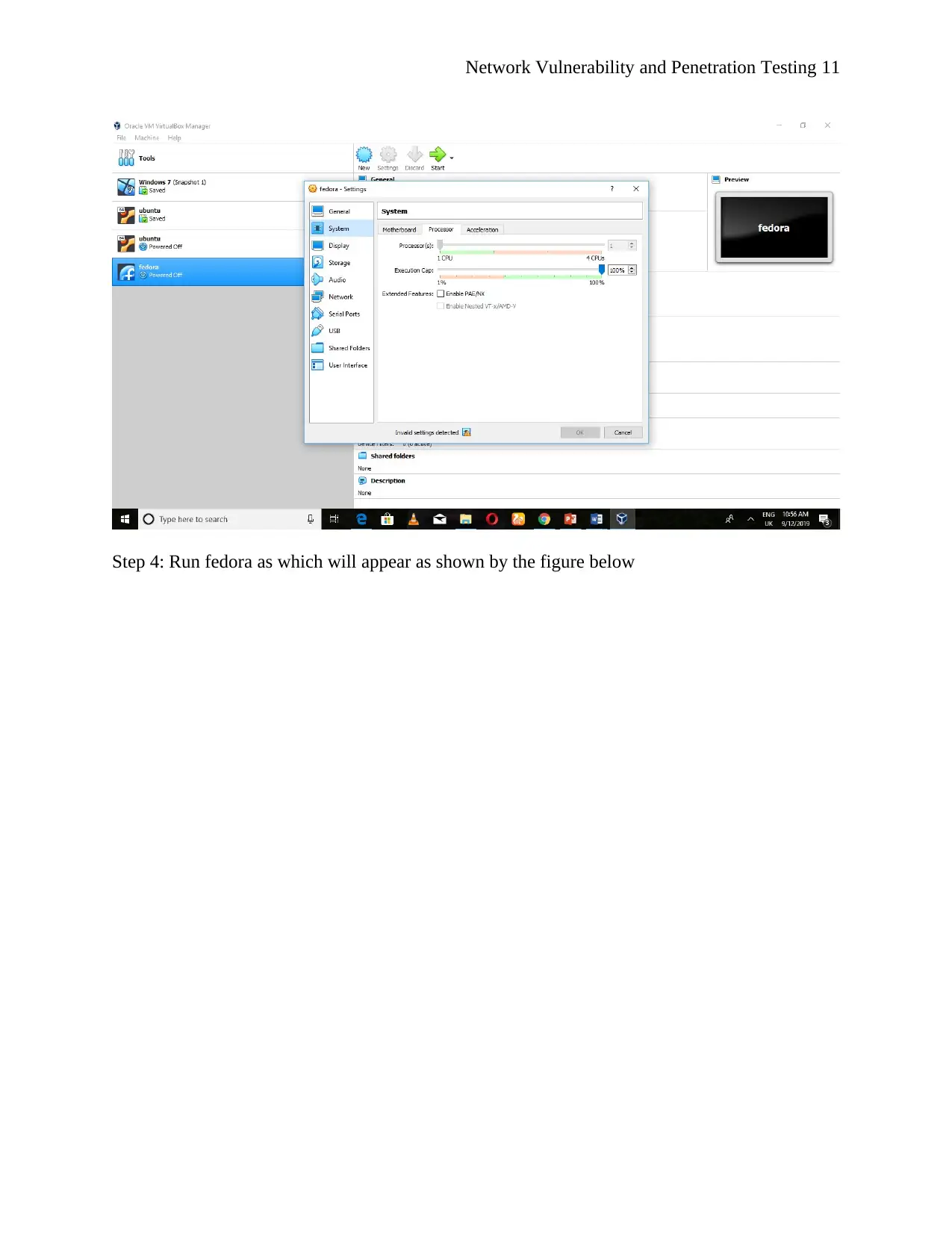
This report details a comprehensive exploration of network vulnerability and penetration testing, fulfilling the requirements of a BIT354 assignment. The report begins by outlining the installation of Windows 7, Ubuntu, and Fedora operating systems within a VirtualBox environment. It then proceeds to describe the creation of a network utilizing these three virtual machines, including the configuration of routers and the establishment of internal network connections to ensure communication between the systems. The core of the report focuses on researching and implementing various network hardening techniques, such as changing default passwords, installing updates and firewalls, and utilizing antivirus software and group policies to enhance system security. Screenshots are included to document the implementation of these techniques. The report concludes with an evaluation of the implemented strategies and provides recommendations for further improving network security, emphasizing the importance of proactive measures to mitigate potential cyber threats.
1 out of 26

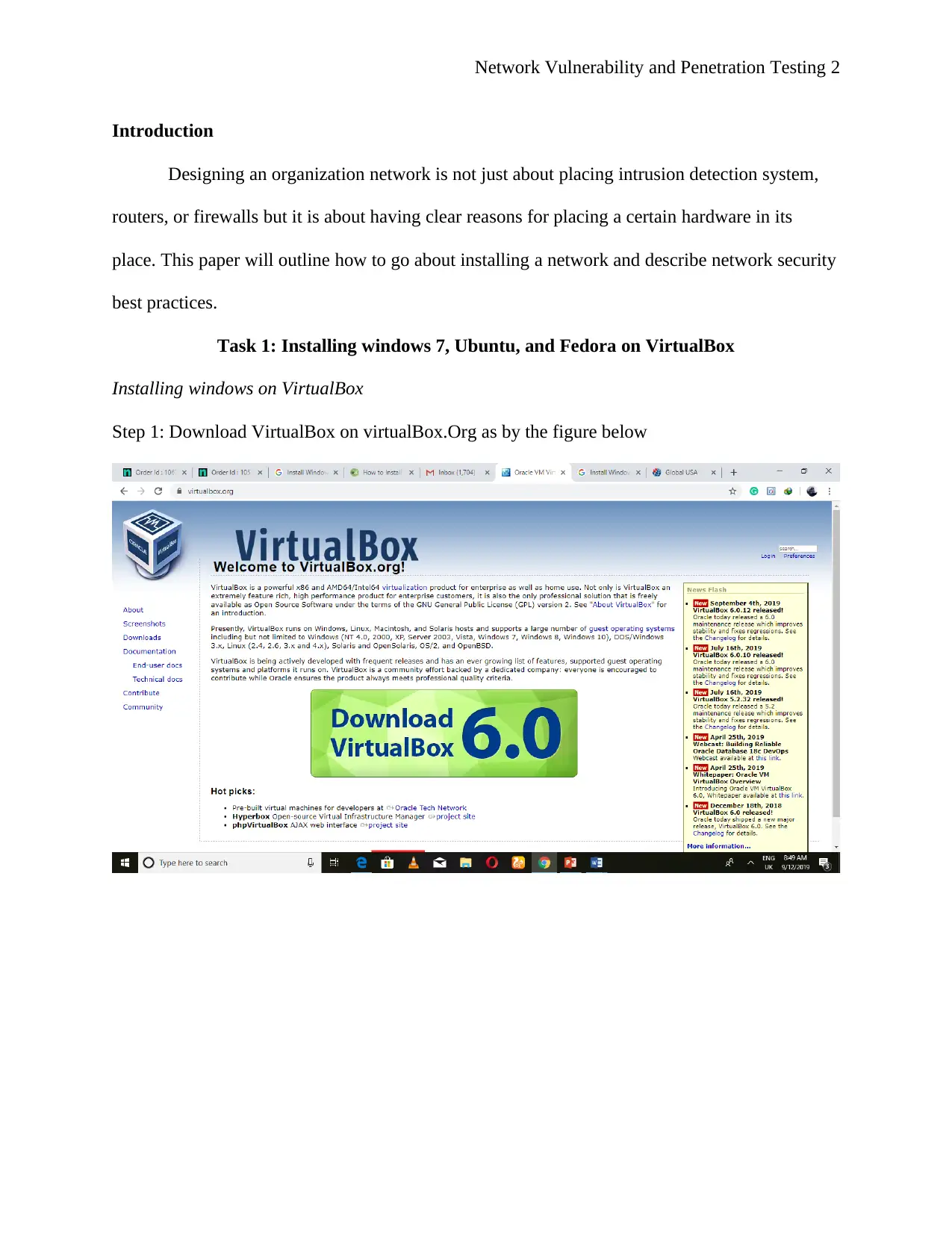
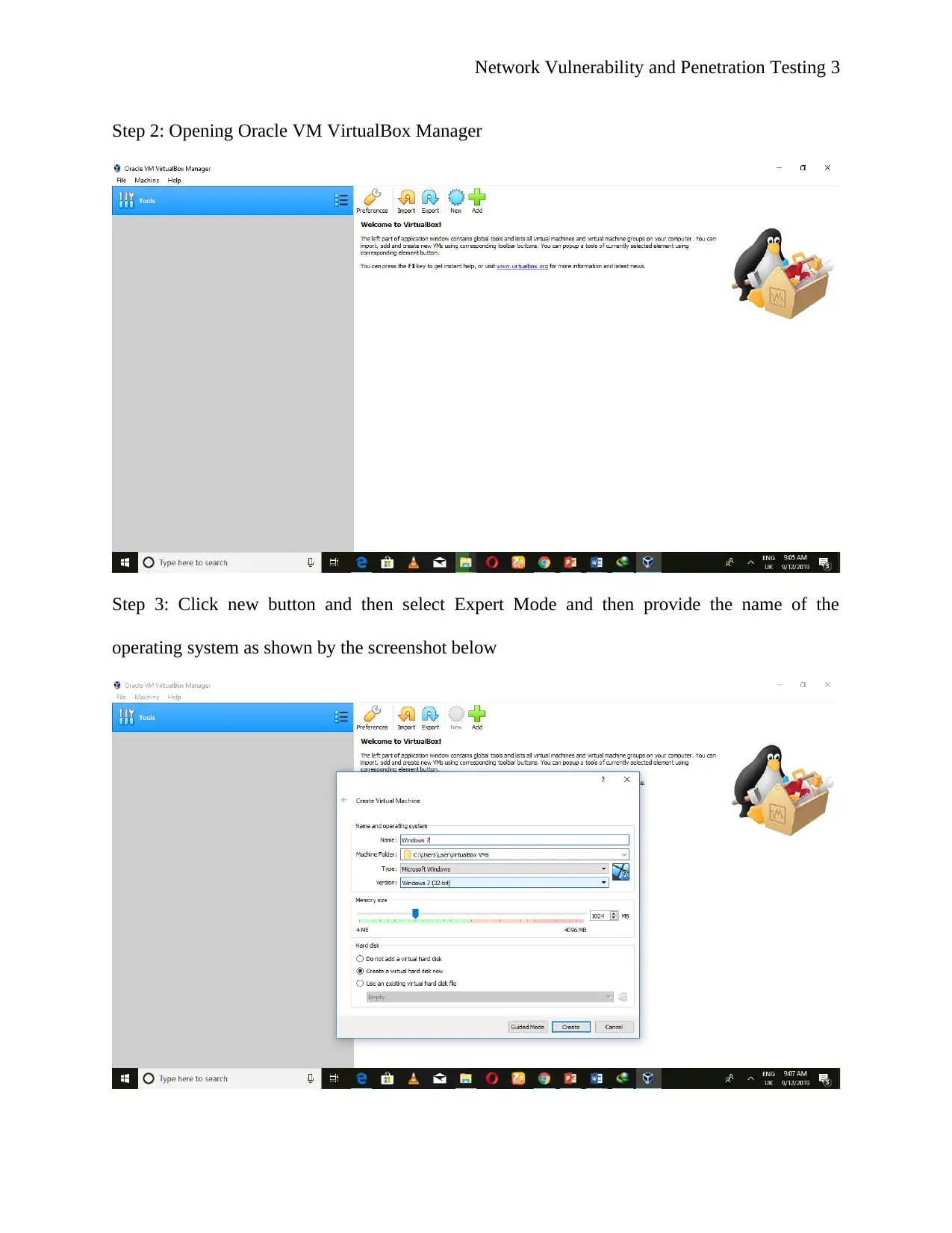

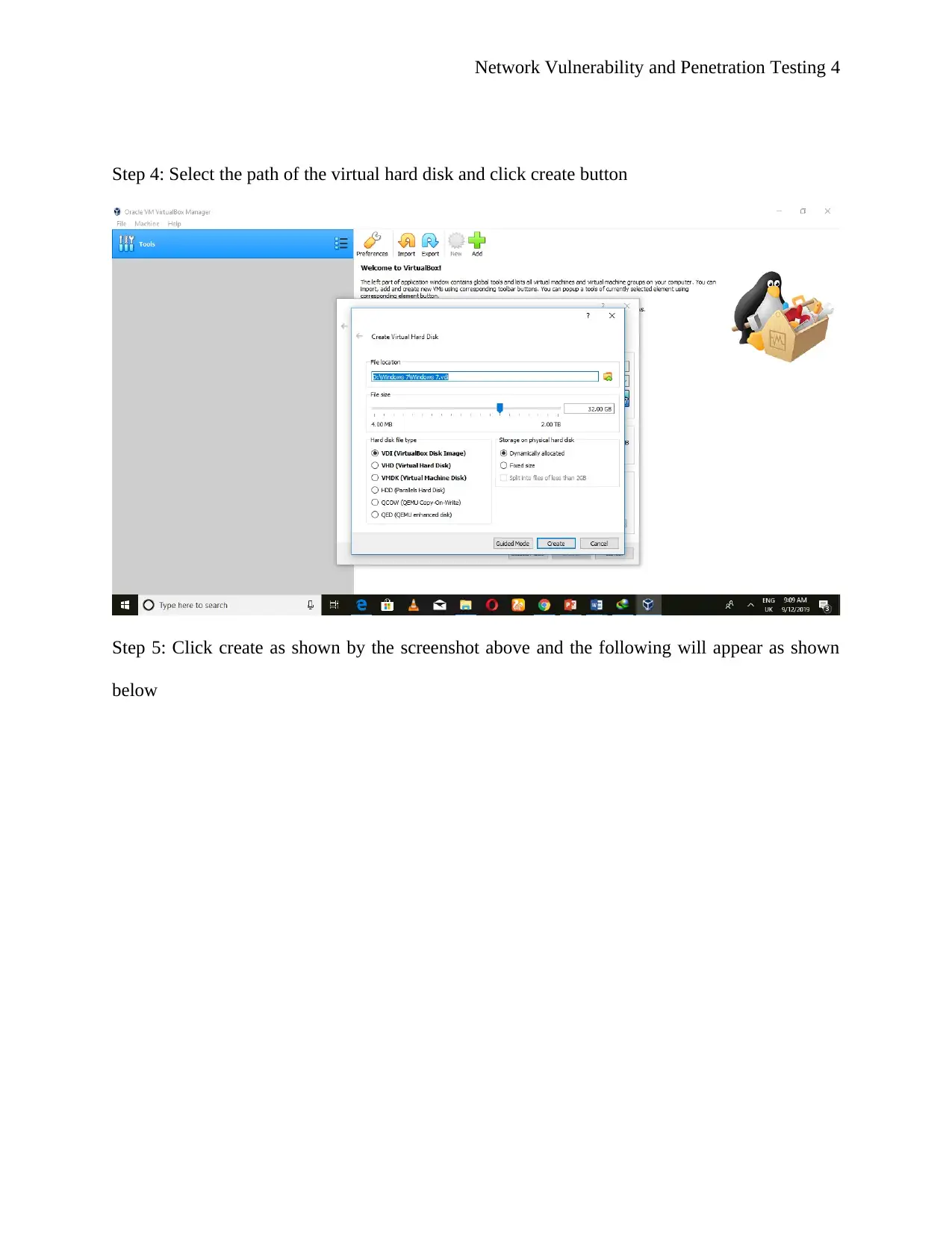
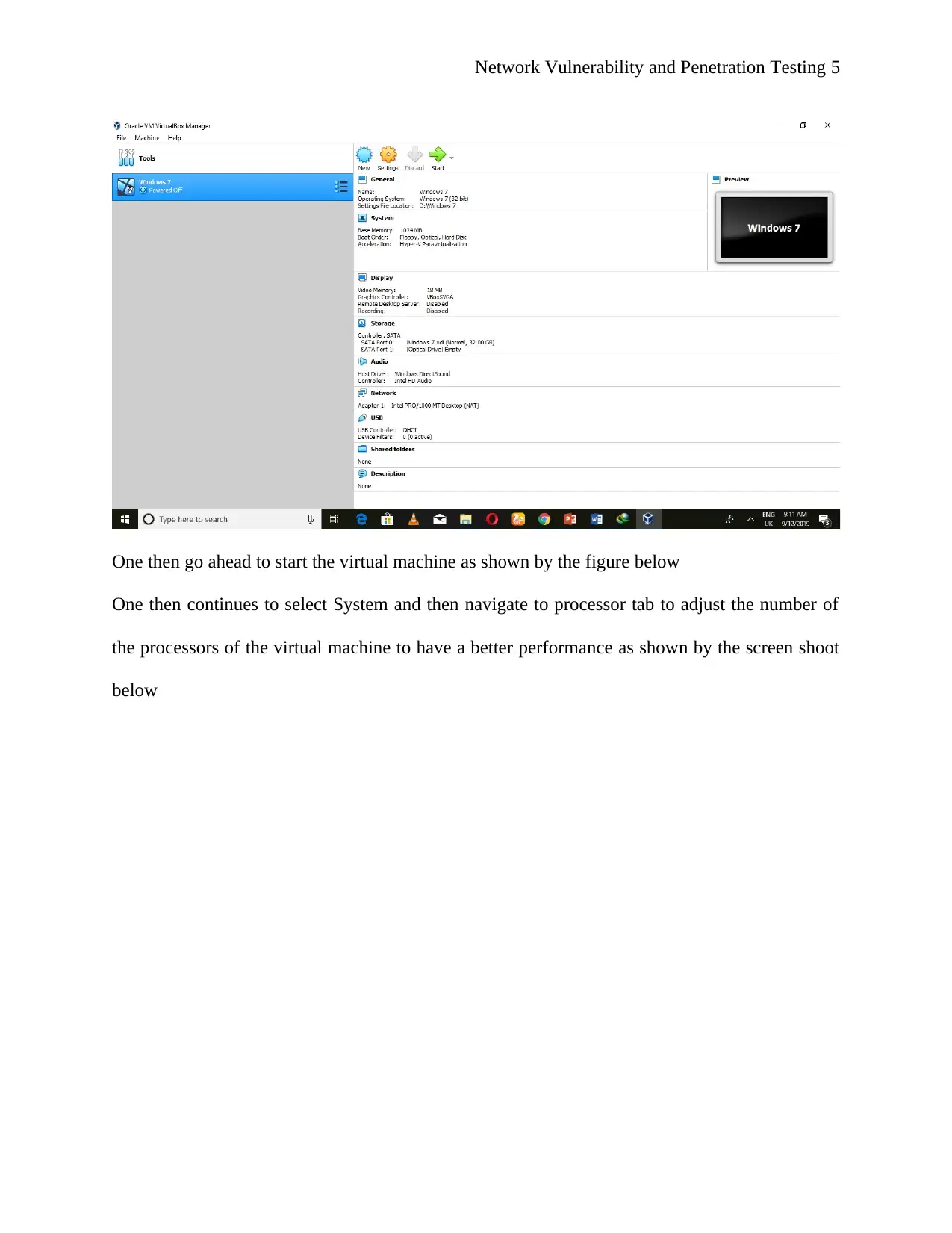







![[object Object]](/_next/static/media/star-bottom.7253800d.svg)