Network Performance Management and Troubleshooting Project CSC73002
VerifiedAdded on 2022/11/15
|18
|1932
|191
Project
AI Summary
This assignment focuses on network management, encompassing architecture selection, Zabbix configuration, SNMPv2c setup, and performance baselining. The project requires the student to configure and run a Zabbix appliance, configure SNMP clients, and monitor network devices. The document also includes a section on troubleshooting a network shared folder issue, outlining the steps required to diagnose and resolve the problem. The assignment covers key performance indicators, resource monitoring, and troubleshooting techniques. The student has provided detailed steps for troubleshooting shared folder access, including checking permissions, firewall settings, and network configurations. The document also provides references to relevant sources used in the assignment.

2019
NETWORK MANAGEMENT
NETWORK MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
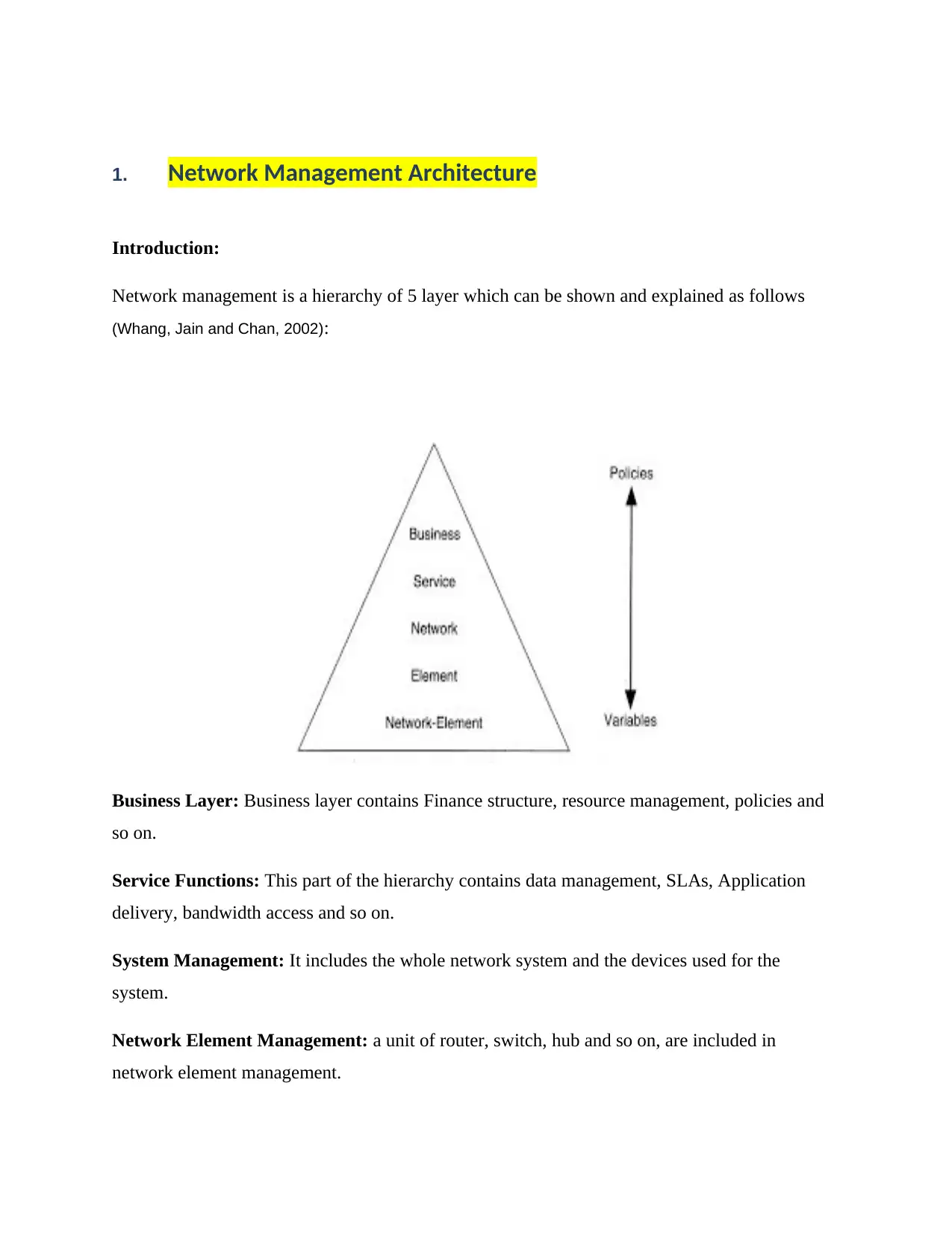
1. Network Management Architecture
Introduction:
Network management is a hierarchy of 5 layer which can be shown and explained as follows
(Whang, Jain and Chan, 2002):
Business Layer: Business layer contains Finance structure, resource management, policies and
so on.
Service Functions: This part of the hierarchy contains data management, SLAs, Application
delivery, bandwidth access and so on.
System Management: It includes the whole network system and the devices used for the
system.
Network Element Management: a unit of router, switch, hub and so on, are included in
network element management.
Introduction:
Network management is a hierarchy of 5 layer which can be shown and explained as follows
(Whang, Jain and Chan, 2002):
Business Layer: Business layer contains Finance structure, resource management, policies and
so on.
Service Functions: This part of the hierarchy contains data management, SLAs, Application
delivery, bandwidth access and so on.
System Management: It includes the whole network system and the devices used for the
system.
Network Element Management: a unit of router, switch, hub and so on, are included in
network element management.
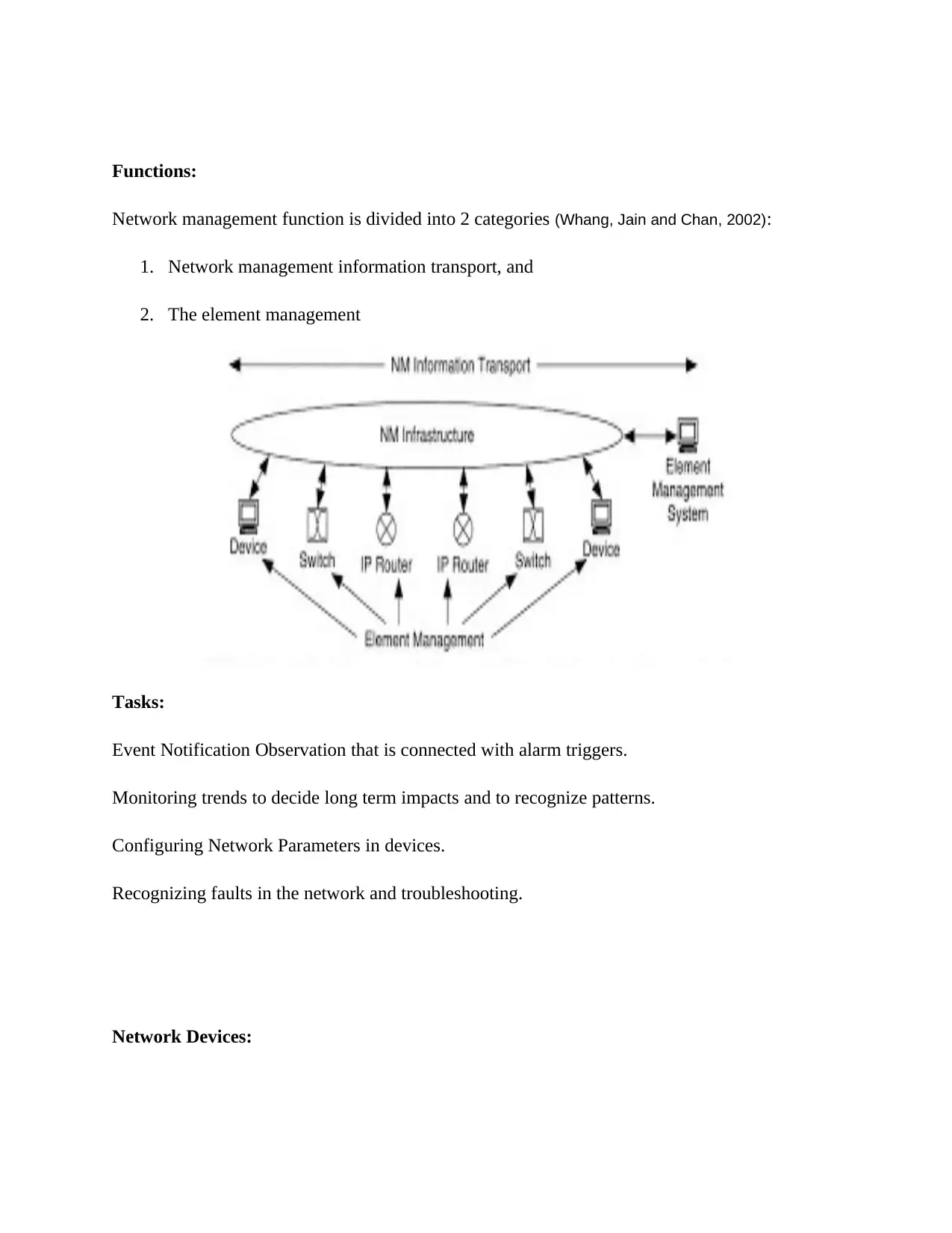
Functions:
Network management function is divided into 2 categories (Whang, Jain and Chan, 2002):
1. Network management information transport, and
2. The element management
Tasks:
Event Notification Observation that is connected with alarm triggers.
Monitoring trends to decide long term impacts and to recognize patterns.
Configuring Network Parameters in devices.
Recognizing faults in the network and troubleshooting.
Network Devices:
Network management function is divided into 2 categories (Whang, Jain and Chan, 2002):
1. Network management information transport, and
2. The element management
Tasks:
Event Notification Observation that is connected with alarm triggers.
Monitoring trends to decide long term impacts and to recognize patterns.
Configuring Network Parameters in devices.
Recognizing faults in the network and troubleshooting.
Network Devices:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
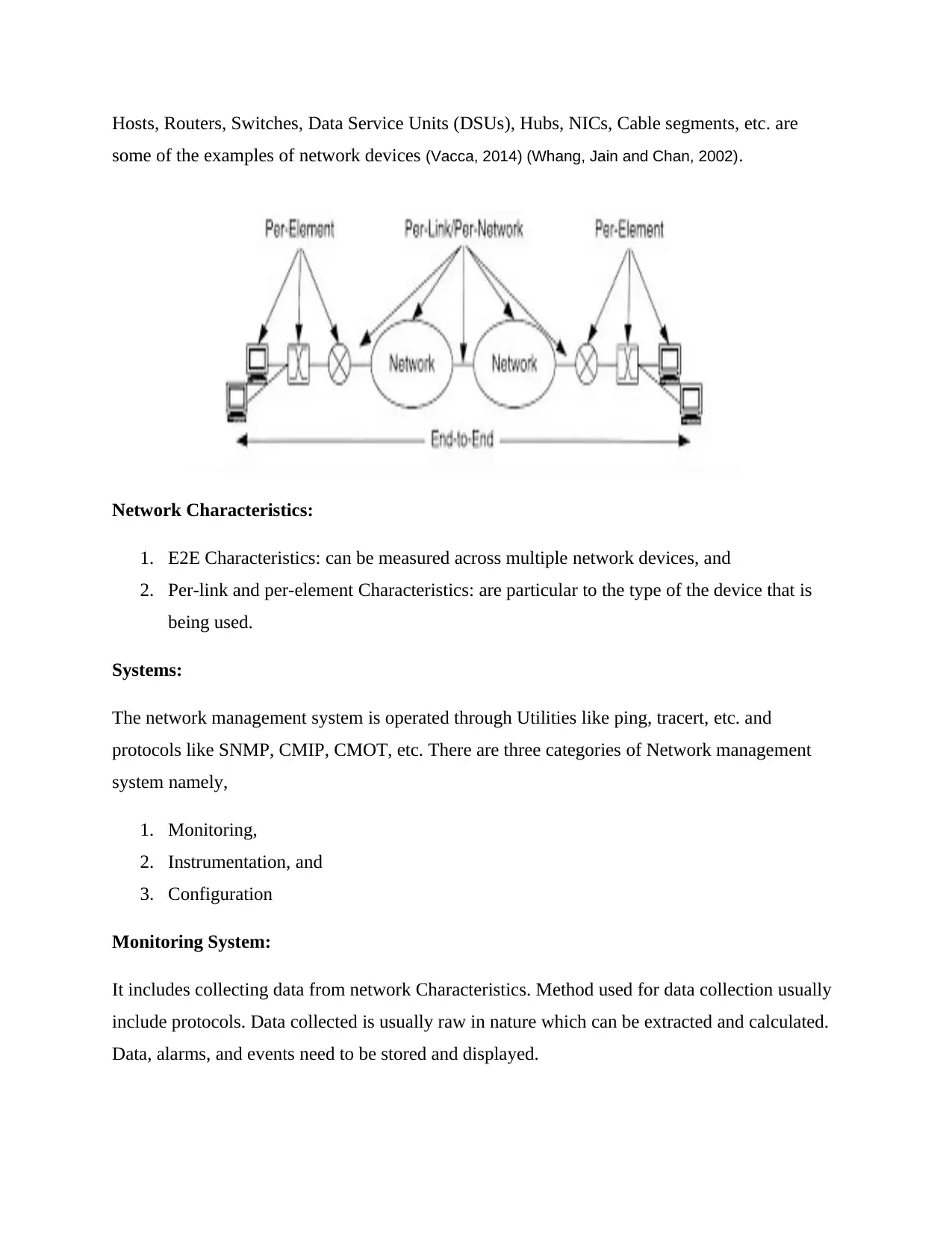
Hosts, Routers, Switches, Data Service Units (DSUs), Hubs, NICs, Cable segments, etc. are
some of the examples of network devices (Vacca, 2014) (Whang, Jain and Chan, 2002).
Network Characteristics:
1. E2E Characteristics: can be measured across multiple network devices, and
2. Per-link and per-element Characteristics: are particular to the type of the device that is
being used.
Systems:
The network management system is operated through Utilities like ping, tracert, etc. and
protocols like SNMP, CMIP, CMOT, etc. There are three categories of Network management
system namely,
1. Monitoring,
2. Instrumentation, and
3. Configuration
Monitoring System:
It includes collecting data from network Characteristics. Method used for data collection usually
include protocols. Data collected is usually raw in nature which can be extracted and calculated.
Data, alarms, and events need to be stored and displayed.
some of the examples of network devices (Vacca, 2014) (Whang, Jain and Chan, 2002).
Network Characteristics:
1. E2E Characteristics: can be measured across multiple network devices, and
2. Per-link and per-element Characteristics: are particular to the type of the device that is
being used.
Systems:
The network management system is operated through Utilities like ping, tracert, etc. and
protocols like SNMP, CMIP, CMOT, etc. There are three categories of Network management
system namely,
1. Monitoring,
2. Instrumentation, and
3. Configuration
Monitoring System:
It includes collecting data from network Characteristics. Method used for data collection usually
include protocols. Data collected is usually raw in nature which can be extracted and calculated.
Data, alarms, and events need to be stored and displayed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
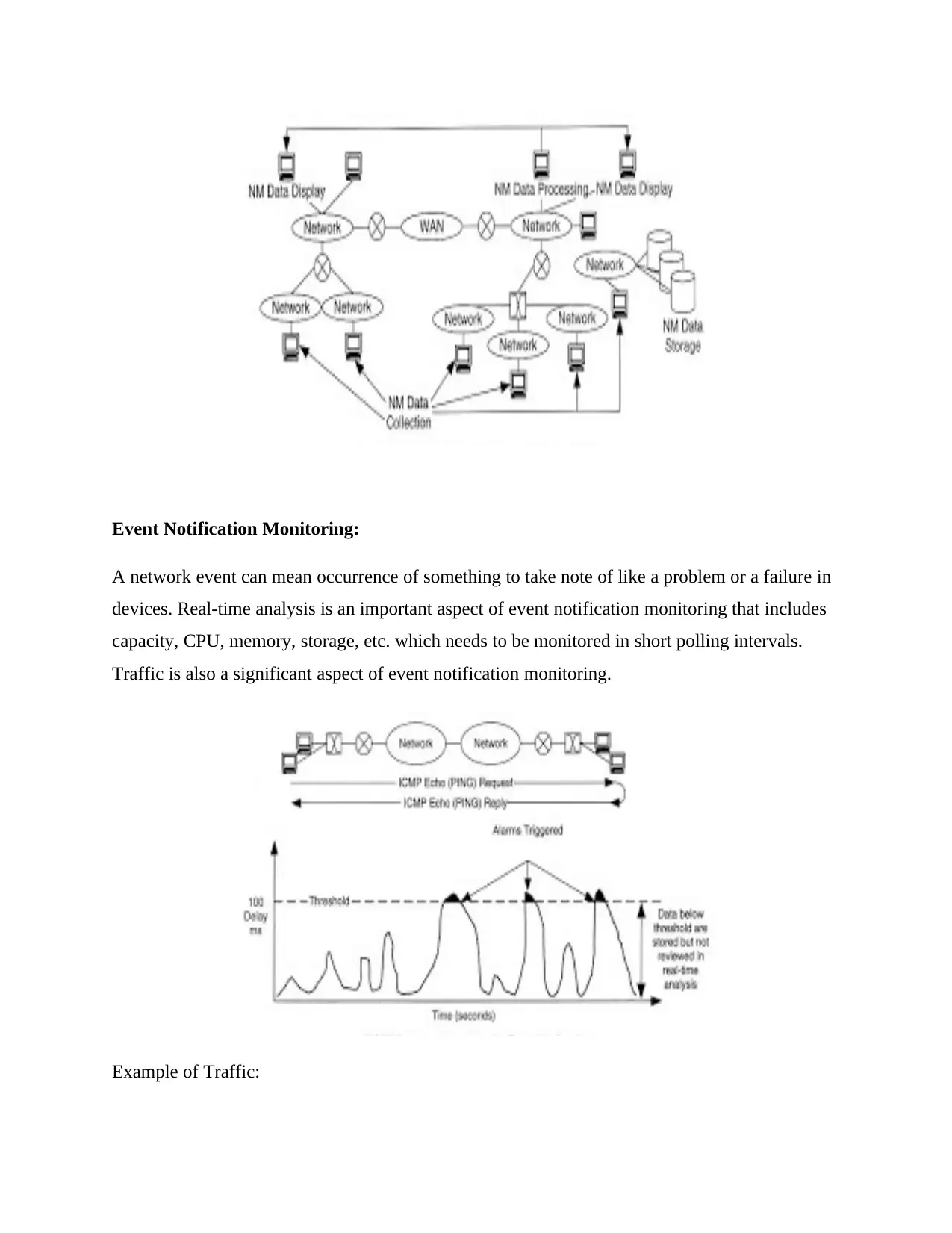
Event Notification Monitoring:
A network event can mean occurrence of something to take note of like a problem or a failure in
devices. Real-time analysis is an important aspect of event notification monitoring that includes
capacity, CPU, memory, storage, etc. which needs to be monitored in short polling intervals.
Traffic is also a significant aspect of event notification monitoring.
Example of Traffic:
A network event can mean occurrence of something to take note of like a problem or a failure in
devices. Real-time analysis is an important aspect of event notification monitoring that includes
capacity, CPU, memory, storage, etc. which needs to be monitored in short polling intervals.
Traffic is also a significant aspect of event notification monitoring.
Example of Traffic:
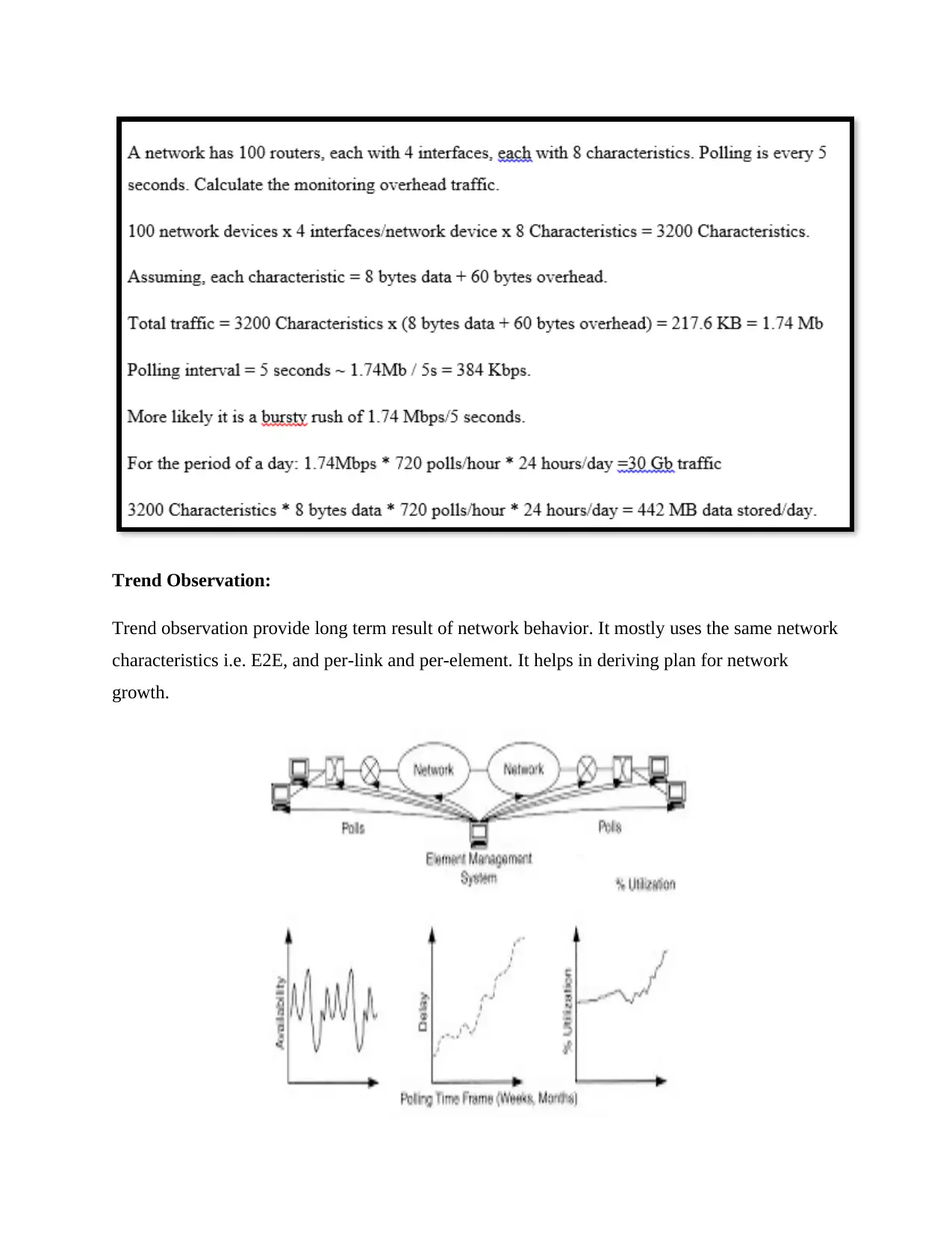
Trend Observation:
Trend observation provide long term result of network behavior. It mostly uses the same network
characteristics i.e. E2E, and per-link and per-element. It helps in deriving plan for network
growth.
Trend observation provide long term result of network behavior. It mostly uses the same network
characteristics i.e. E2E, and per-link and per-element. It helps in deriving plan for network
growth.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
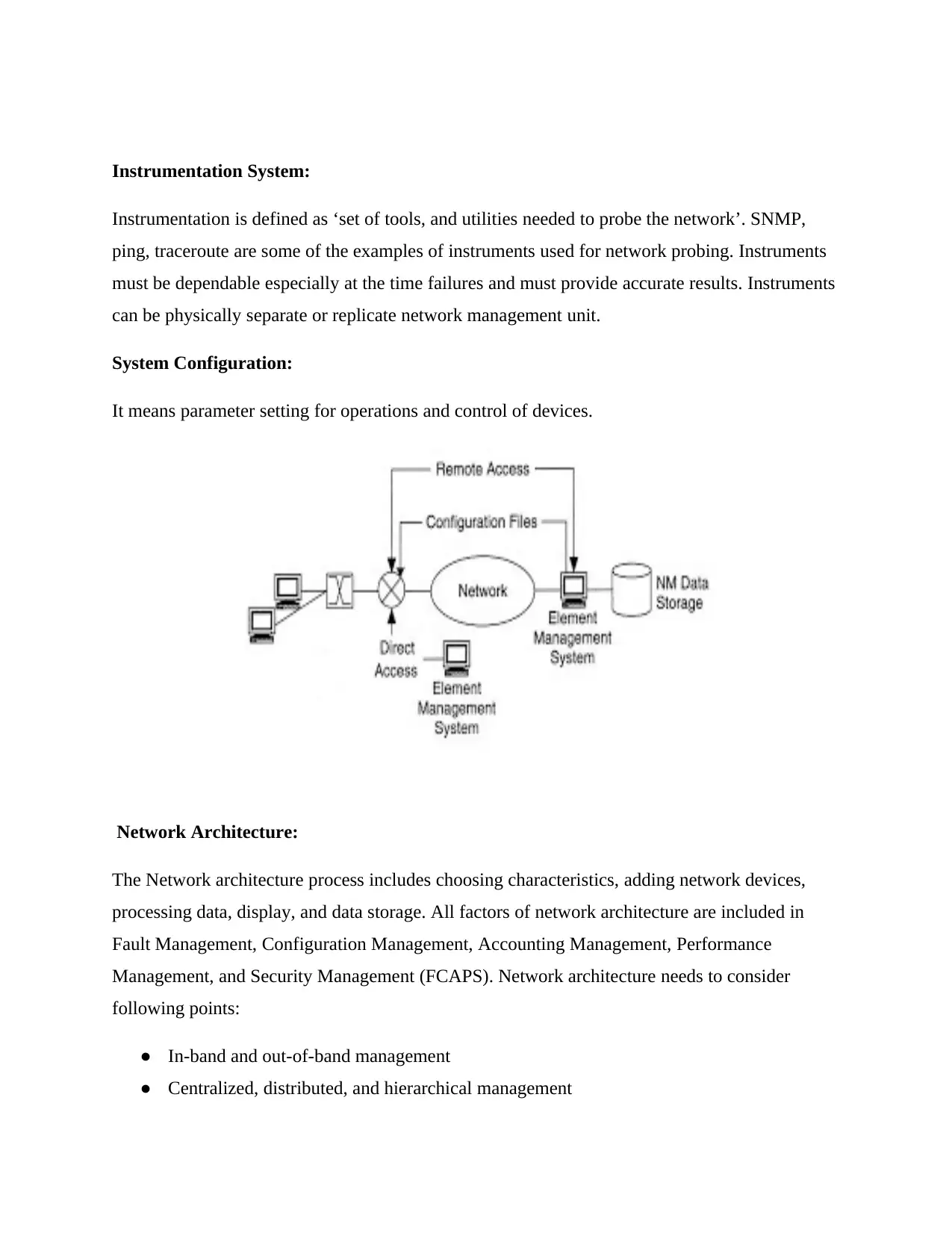
Instrumentation System:
Instrumentation is defined as ‘set of tools, and utilities needed to probe the network’. SNMP,
ping, traceroute are some of the examples of instruments used for network probing. Instruments
must be dependable especially at the time failures and must provide accurate results. Instruments
can be physically separate or replicate network management unit.
System Configuration:
It means parameter setting for operations and control of devices.
Network Architecture:
The Network architecture process includes choosing characteristics, adding network devices,
processing data, display, and data storage. All factors of network architecture are included in
Fault Management, Configuration Management, Accounting Management, Performance
Management, and Security Management (FCAPS). Network architecture needs to consider
following points:
● In-band and out-of-band management
● Centralized, distributed, and hierarchical management
Instrumentation is defined as ‘set of tools, and utilities needed to probe the network’. SNMP,
ping, traceroute are some of the examples of instruments used for network probing. Instruments
must be dependable especially at the time failures and must provide accurate results. Instruments
can be physically separate or replicate network management unit.
System Configuration:
It means parameter setting for operations and control of devices.
Network Architecture:
The Network architecture process includes choosing characteristics, adding network devices,
processing data, display, and data storage. All factors of network architecture are included in
Fault Management, Configuration Management, Accounting Management, Performance
Management, and Security Management (FCAPS). Network architecture needs to consider
following points:
● In-band and out-of-band management
● Centralized, distributed, and hierarchical management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
● Network traffic management
● Checks and balances
● Network data management
● Selecting MIB
● OSS Integration
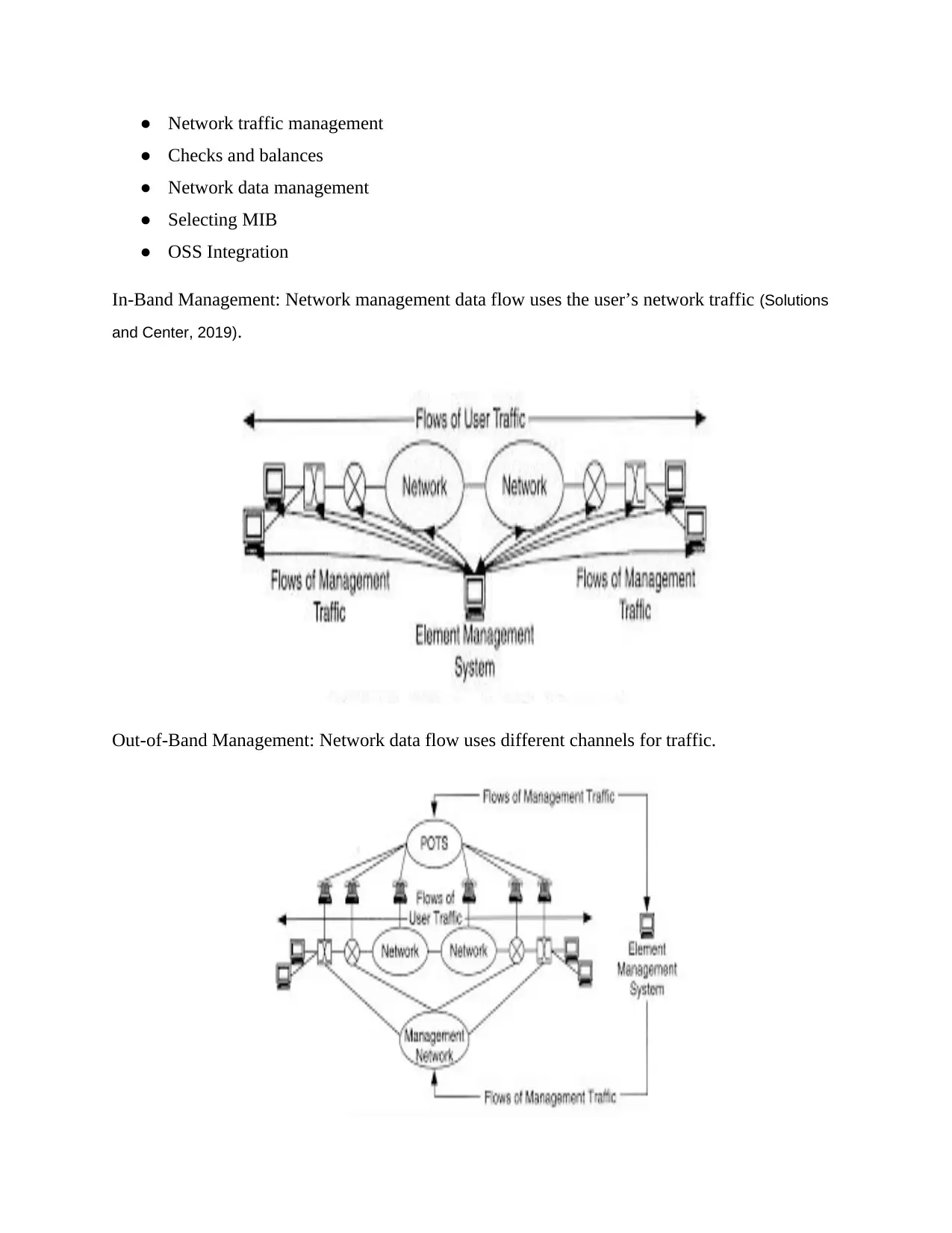
In-Band Management: Network management data flow uses the user’s network traffic (Solutions
and Center, 2019).
Out-of-Band Management: Network data flow uses different channels for traffic.
● Checks and balances
● Network data management
● Selecting MIB
● OSS Integration
In-Band Management: Network management data flow uses the user’s network traffic (Solutions
and Center, 2019).
Out-of-Band Management: Network data flow uses different channels for traffic.
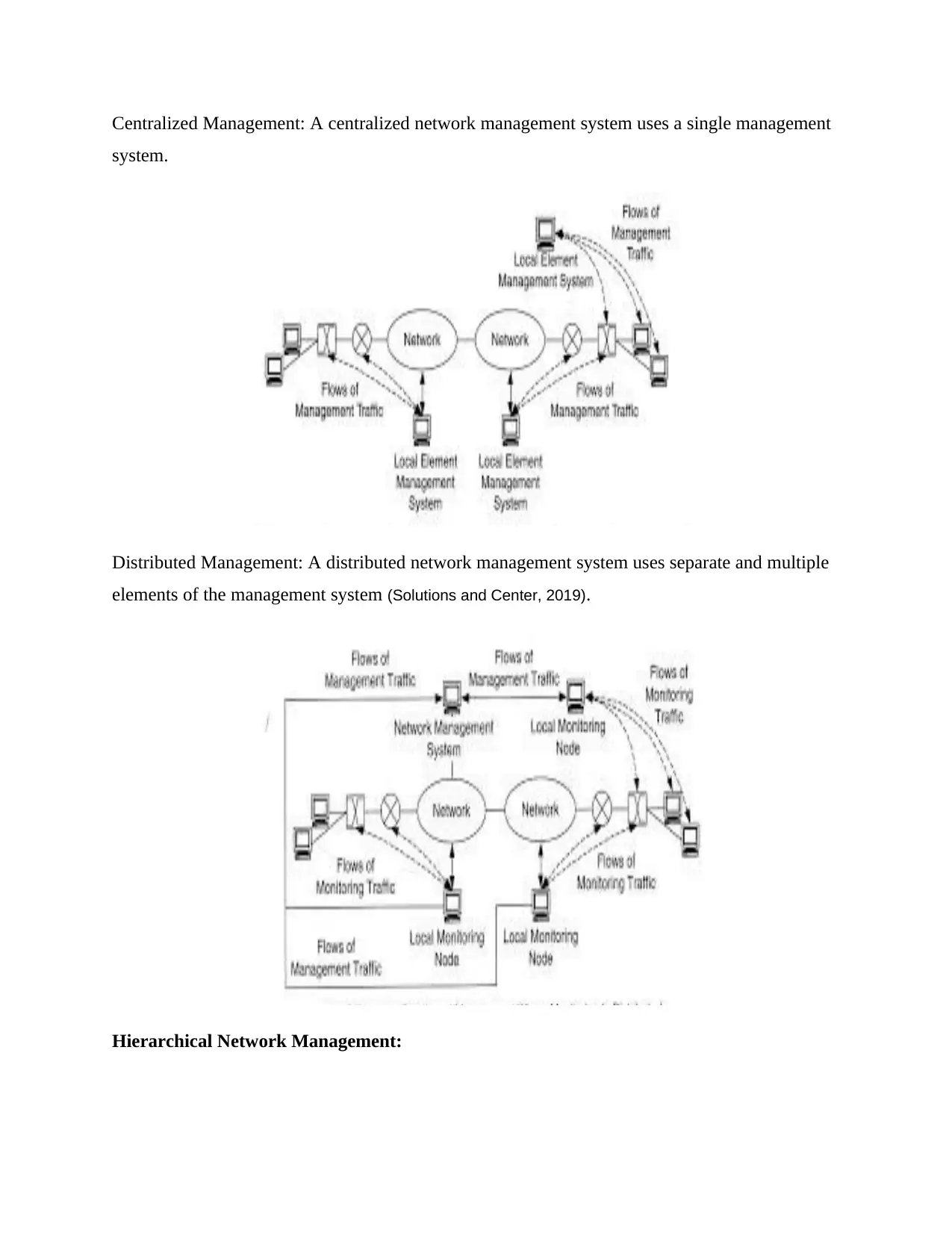
Centralized Management: A centralized network management system uses a single management
system.
Distributed Management: A distributed network management system uses separate and multiple
elements of the management system (Solutions and Center, 2019).
Hierarchical Network Management:
system.
Distributed Management: A distributed network management system uses separate and multiple
elements of the management system (Solutions and Center, 2019).
Hierarchical Network Management:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
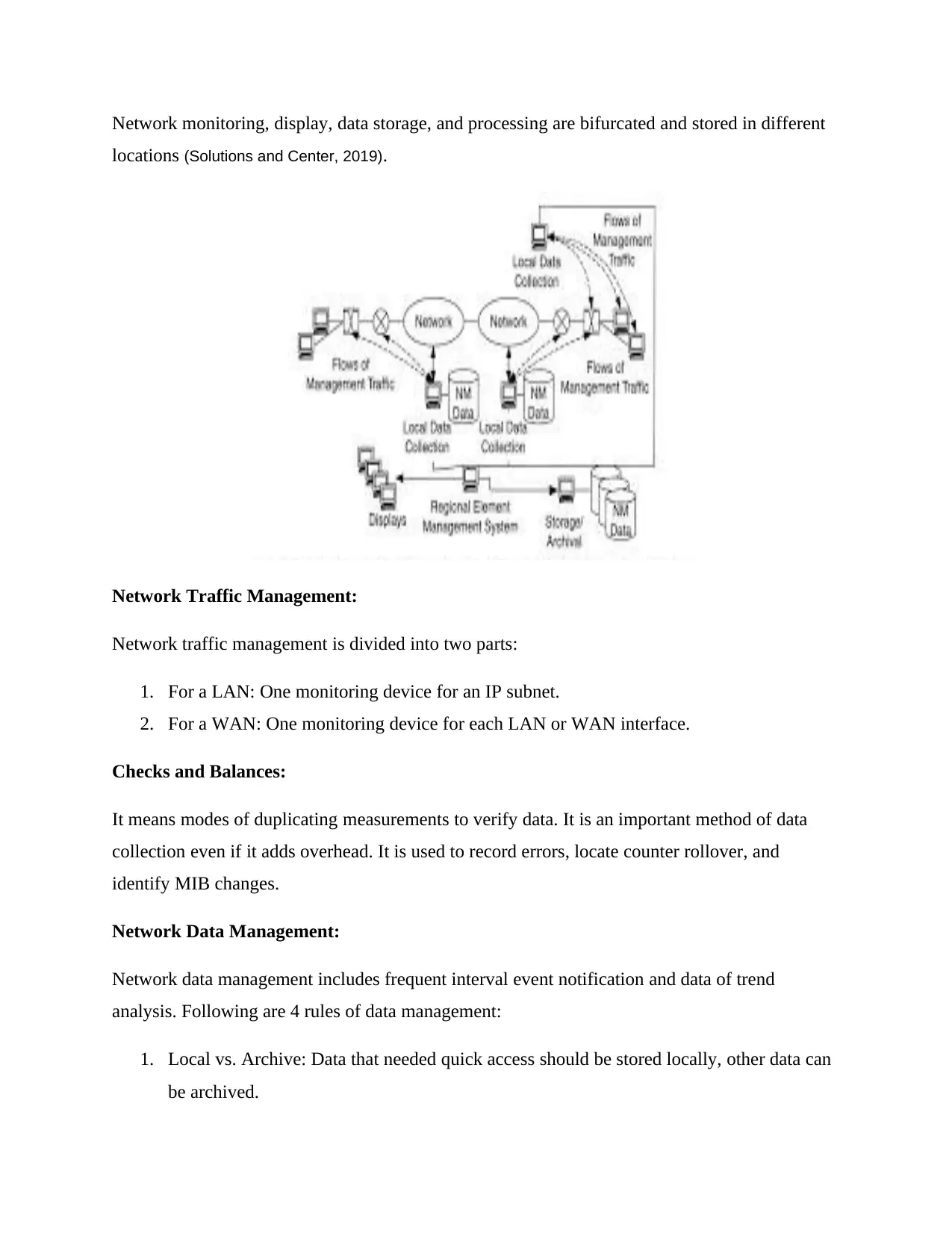
Network monitoring, display, data storage, and processing are bifurcated and stored in different
locations (Solutions and Center, 2019).
Network Traffic Management:
Network traffic management is divided into two parts:
1. For a LAN: One monitoring device for an IP subnet.
2. For a WAN: One monitoring device for each LAN or WAN interface.
Checks and Balances:
It means modes of duplicating measurements to verify data. It is an important method of data
collection even if it adds overhead. It is used to record errors, locate counter rollover, and
identify MIB changes.
Network Data Management:
Network data management includes frequent interval event notification and data of trend
analysis. Following are 4 rules of data management:
1. Local vs. Archive: Data that needed quick access should be stored locally, other data can
be archived.
locations (Solutions and Center, 2019).
Network Traffic Management:
Network traffic management is divided into two parts:
1. For a LAN: One monitoring device for an IP subnet.
2. For a WAN: One monitoring device for each LAN or WAN interface.
Checks and Balances:
It means modes of duplicating measurements to verify data. It is an important method of data
collection even if it adds overhead. It is used to record errors, locate counter rollover, and
identify MIB changes.
Network Data Management:
Network data management includes frequent interval event notification and data of trend
analysis. Following are 4 rules of data management:
1. Local vs. Archive: Data that needed quick access should be stored locally, other data can
be archived.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
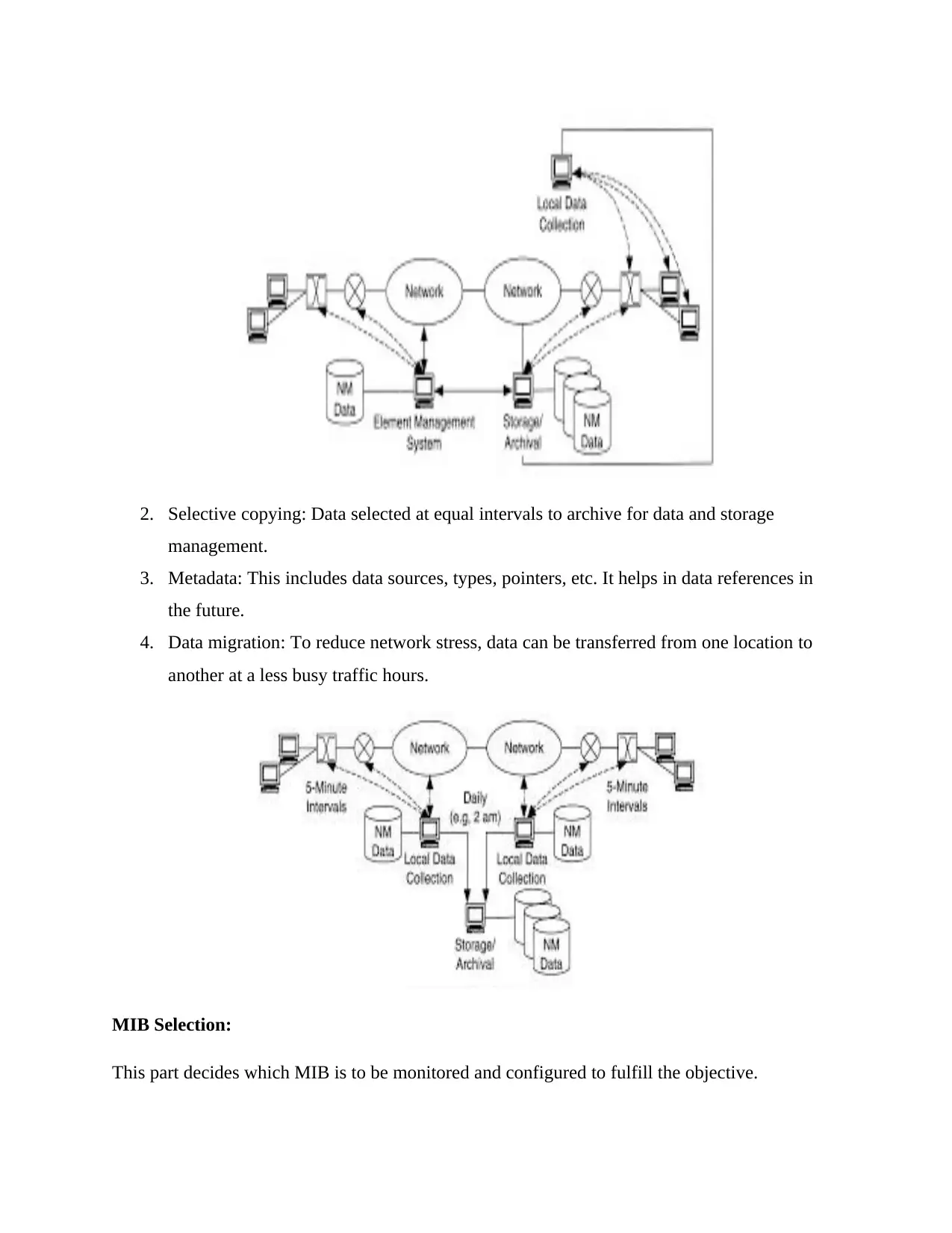
2. Selective copying: Data selected at equal intervals to archive for data and storage
management.
3. Metadata: This includes data sources, types, pointers, etc. It helps in data references in
the future.
4. Data migration: To reduce network stress, data can be transferred from one location to
another at a less busy traffic hours.
MIB Selection:
This part decides which MIB is to be monitored and configured to fulfill the objective.
management.
3. Metadata: This includes data sources, types, pointers, etc. It helps in data references in
the future.
4. Data migration: To reduce network stress, data can be transferred from one location to
another at a less busy traffic hours.
MIB Selection:
This part decides which MIB is to be monitored and configured to fulfill the objective.
OSS Integration:
Operation Support System (OSS) also called as a northbound interface is a method to decide
management’s integration with the OSS.
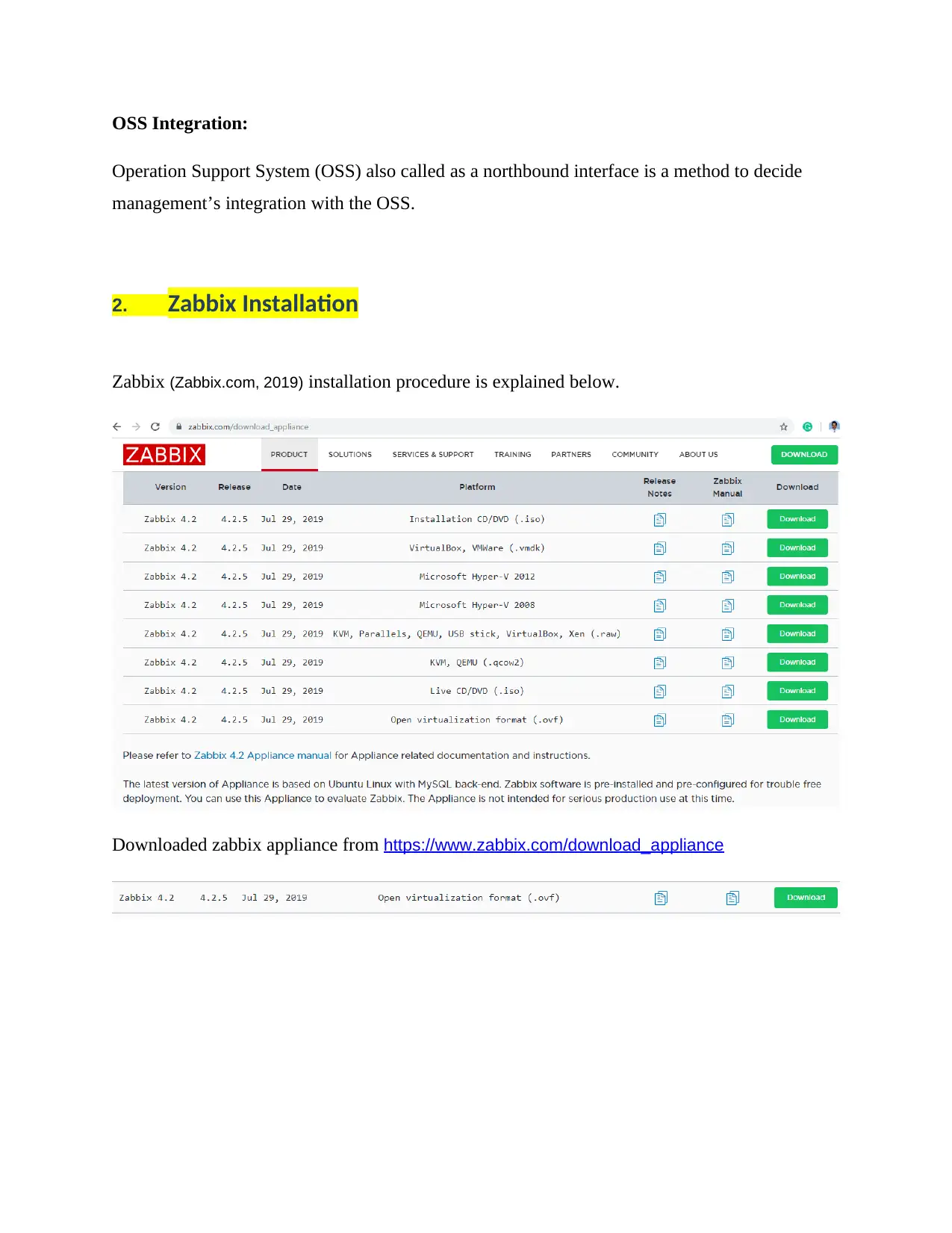
2. Zabbix Installation
Zabbix (Zabbix.com, 2019) installation procedure is explained below.
Downloaded zabbix appliance from https://www.zabbix.com/download_appliance
Operation Support System (OSS) also called as a northbound interface is a method to decide
management’s integration with the OSS.
2. Zabbix Installation
Zabbix (Zabbix.com, 2019) installation procedure is explained below.
Downloaded zabbix appliance from https://www.zabbix.com/download_appliance
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

