Comprehensive Analysis of Network Security and Privacy Assignment
VerifiedAdded on 2020/03/28
|14
|1609
|73
Homework Assignment
AI Summary
This assignment solution delves into various aspects of network security, starting with firewall rule configurations and their implementation using iptables. It then explores WiFi security, discussing WPA protocols, transmit power control, and RADIUS authentication. The assignment also covers access control mechanisms, including password protection and storage methods. Furthermore, it examines HTTPS and certificates, explaining their role in secure communication and the potential risks associated with compromised Certificate Authorities (CAs). Finally, the solution investigates internet privacy, comparing and contrasting web proxies, Tor, and VPNs, highlighting their advantages and disadvantages in protecting user anonymity and data security. The document provides a comprehensive overview of these critical network security concepts.
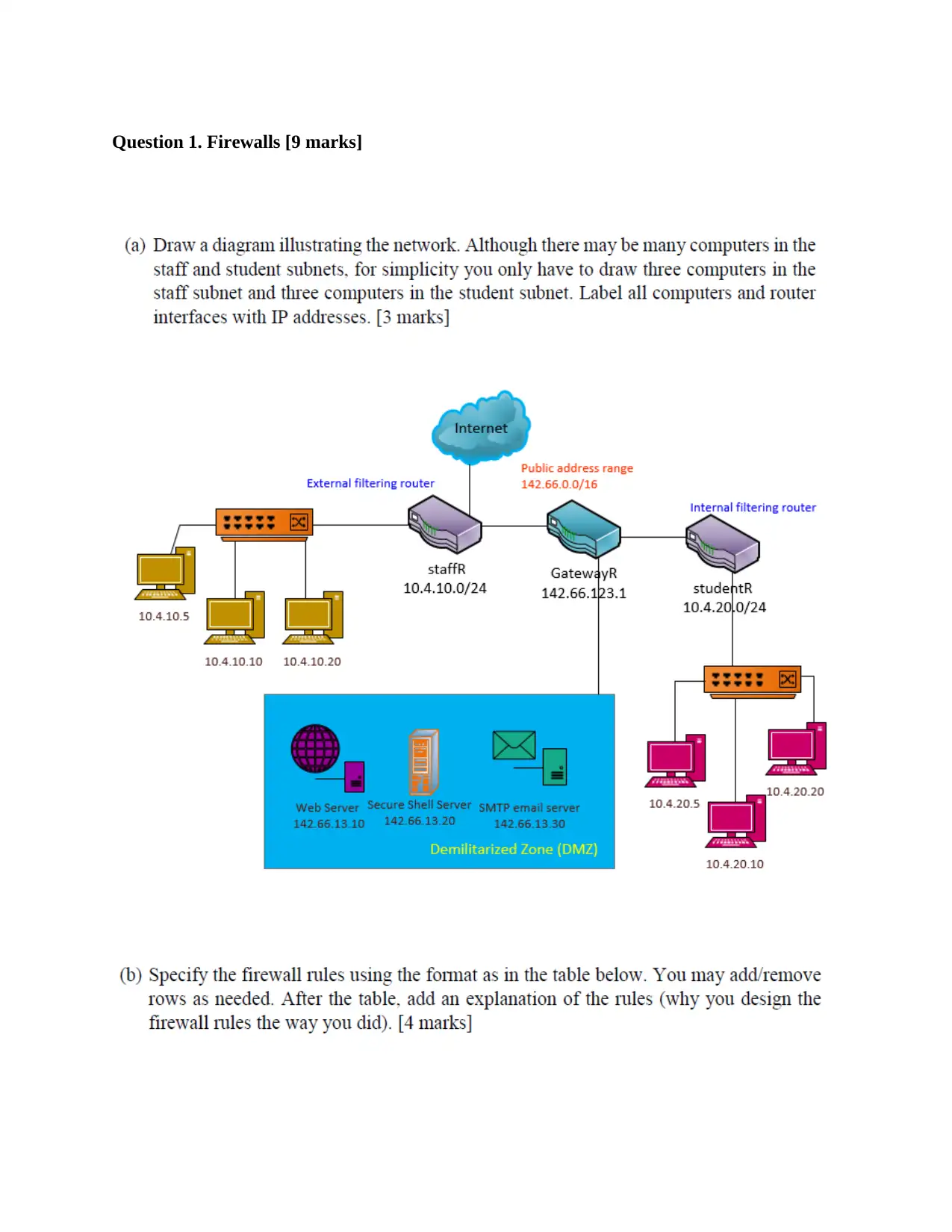
Question 1. Firewalls [9 marks]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
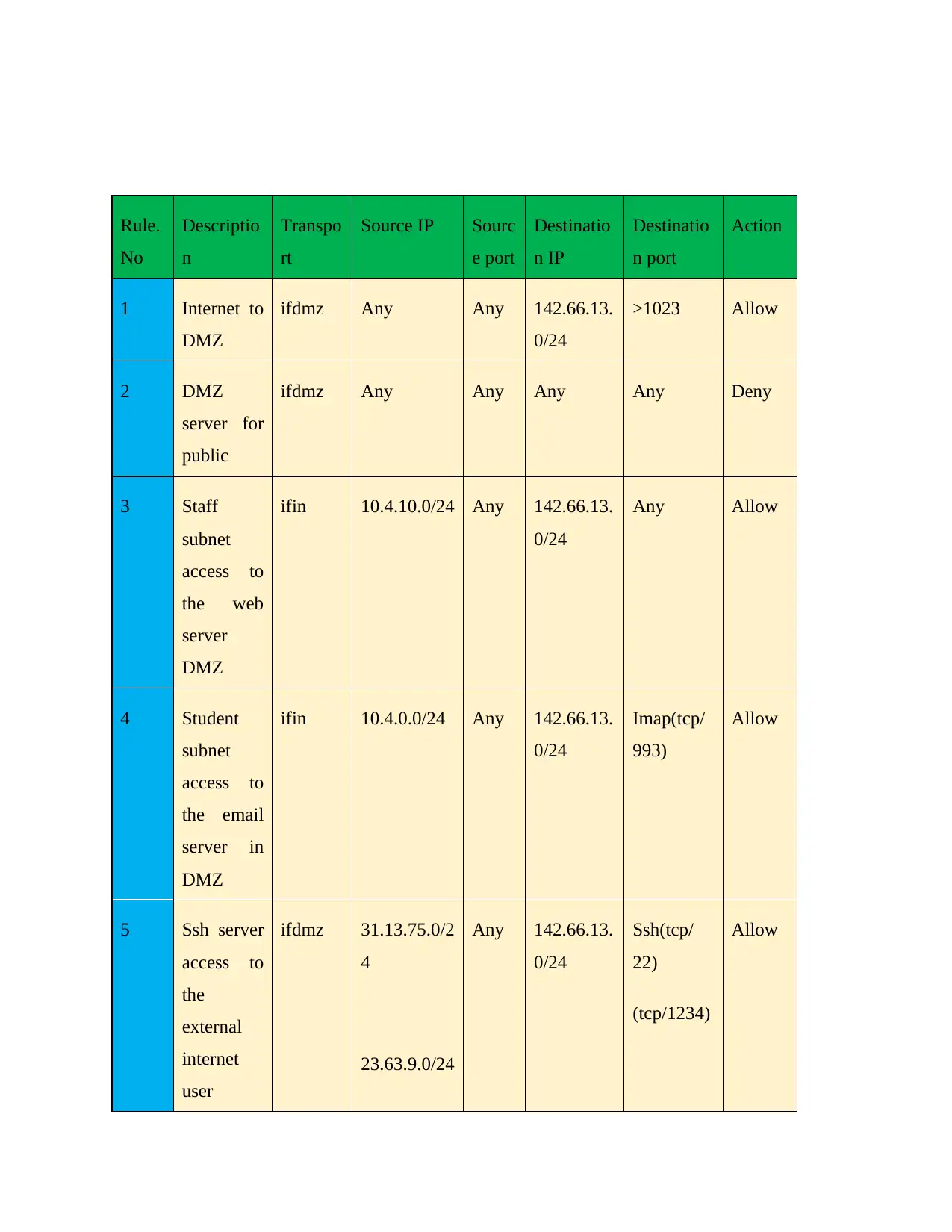
Rule.
No
Descriptio
n
Transpo
rt
Source IP Sourc
e port
Destinatio
n IP
Destinatio
n port
Action
1 Internet to
DMZ
ifdmz Any Any 142.66.13.
0/24
>1023 Allow
2 DMZ
server for
public
ifdmz Any Any Any Any Deny
3 Staff
subnet
access to
the web
server
DMZ
ifin 10.4.10.0/24 Any 142.66.13.
0/24
Any Allow
4 Student
subnet
access to
the email
server in
DMZ
ifin 10.4.0.0/24 Any 142.66.13.
0/24
Imap(tcp/
993)
Allow
5 Ssh server
access to
the
external
internet
user
ifdmz 31.13.75.0/2
4
23.63.9.0/24
Any 142.66.13.
0/24
Ssh(tcp/
22)
(tcp/1234)
Allow
No
Descriptio
n
Transpo
rt
Source IP Sourc
e port
Destinatio
n IP
Destinatio
n port
Action
1 Internet to
DMZ
ifdmz Any Any 142.66.13.
0/24
>1023 Allow
2 DMZ
server for
public
ifdmz Any Any Any Any Deny
3 Staff
subnet
access to
the web
server
DMZ
ifin 10.4.10.0/24 Any 142.66.13.
0/24
Any Allow
4 Student
subnet
access to
the email
server in
DMZ
ifin 10.4.0.0/24 Any 142.66.13.
0/24
Imap(tcp/
993)
Allow
5 Ssh server
access to
the
external
internet
user
ifdmz 31.13.75.0/2
4
23.63.9.0/24
Any 142.66.13.
0/24
Ssh(tcp/
22)
(tcp/1234)
Allow

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In order to communicate with the command line and arrange firewall rules in crispy table,
IP tables are used. Default policies are nothing but the policies that are predefined.INPUT,
OUTPUT, FORWARD are the three default policies present. INPUT default policy is the
destination point to the host system where the OUTPUT default policy is the origin point to the
host system.The transfer or tradeoff between the policies is carried out using packets like
ACCEPT and Drop and also FORWARD default policy that forwards from origin to destination.
Question 2. WiFi Security [8 marks]
WPA
WPA is abbreviated as the Wi-Fi Protected Access. The algorithms used by WPA
appears to be more secured.Temporary Key Integrated Protocol is used by WPA.By utilizing the
protocol, it carries the information packets across network.
Advantages
It has advanced level of security when compared with WEP.
IP tables are used. Default policies are nothing but the policies that are predefined.INPUT,
OUTPUT, FORWARD are the three default policies present. INPUT default policy is the
destination point to the host system where the OUTPUT default policy is the origin point to the
host system.The transfer or tradeoff between the policies is carried out using packets like
ACCEPT and Drop and also FORWARD default policy that forwards from origin to destination.
Question 2. WiFi Security [8 marks]
WPA
WPA is abbreviated as the Wi-Fi Protected Access. The algorithms used by WPA
appears to be more secured.Temporary Key Integrated Protocol is used by WPA.By utilizing the
protocol, it carries the information packets across network.
Advantages
It has advanced level of security when compared with WEP.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It changes the key as data packets using TKIP and hence data appears to be more
protected
Disadvantages
It is incompatible with older operating systems
It has longer transmission rate of data packets
Using antennas, transmit power and AP
The present development creates the strategies to set up the sheltered direct in the
middle of the remote gadget. It incorporates diminishing the gadget transmit control in mix with
keeping the gadget in particular openness to each other. With diminishing the transmit control,
the gadget correspondence not ready to relate to other gadget over the short correspondence run.
Keeping in mind the end goal to create security and encoded correspondence channel, by means
of diminished transmission control, the gadgets trade and make the encryption keys. At the point
of safe channel, the gadget improves their energy transmission back to the typical working
levels. It enables them to continue moreover when dealing with the protected remote
correspondence.
The AP (Access Point) utilizes Omni directional and dipole reception apparatus for
the transmission. By changing the transmit control, the entrance point radio range is altered. The
radio scope of the WI-FI is relying upon the reception apparatus control pick up. To control the
radio range, just a single receiving wire ought to be utilized as a part of the system.
RADIUS authentication
RADIUS authentication is nothing but the software that communicates with the
central server and classifies users as authorized users or unauthorizedusers. The profiles are
maintained in a centralized database.UDP port appears to be more helpful in authenticating the
messages. Only one message is sent over the packet at a time. Some of the messages are
Access-Request
Access-Accept
Access-Reject
protected
Disadvantages
It is incompatible with older operating systems
It has longer transmission rate of data packets
Using antennas, transmit power and AP
The present development creates the strategies to set up the sheltered direct in the
middle of the remote gadget. It incorporates diminishing the gadget transmit control in mix with
keeping the gadget in particular openness to each other. With diminishing the transmit control,
the gadget correspondence not ready to relate to other gadget over the short correspondence run.
Keeping in mind the end goal to create security and encoded correspondence channel, by means
of diminished transmission control, the gadgets trade and make the encryption keys. At the point
of safe channel, the gadget improves their energy transmission back to the typical working
levels. It enables them to continue moreover when dealing with the protected remote
correspondence.
The AP (Access Point) utilizes Omni directional and dipole reception apparatus for
the transmission. By changing the transmit control, the entrance point radio range is altered. The
radio scope of the WI-FI is relying upon the reception apparatus control pick up. To control the
radio range, just a single receiving wire ought to be utilized as a part of the system.
RADIUS authentication
RADIUS authentication is nothing but the software that communicates with the
central server and classifies users as authorized users or unauthorizedusers. The profiles are
maintained in a centralized database.UDP port appears to be more helpful in authenticating the
messages. Only one message is sent over the packet at a time. Some of the messages are
Access-Request
Access-Accept
Access-Reject

Access-Challenge
Accounting-Request
Accounting-Response
Advantages
It helps in the best user management
It is very simple to configure
Disadvantages
Unused user accounts will not be removed automatically.
Even after the user account has removed, it will be taken into count to predict the
maximum users.
Manual detection of rogue IPs
The two approaches to detect rouge access point is monitoring IP traffic and RF
waves. Using sniffers, the commercial products use the second one to detect rouge access point
manually scans the RF waves. For example, nets tumbler, air magnet or automatic process via
sensors. Rouge AP is the unofficial AP which is plugged in network wired side. The Aruba OS
produce rouge access point identification functionality which is avail in the fundamental
operating system.For detecting wireless access point, AM should scan air looking for the modern
device and remaining tabs on the device which is existing
Drawbacks
This method consumes more power.
It Suffers network scaling issue.
Accounting-Request
Accounting-Response
Advantages
It helps in the best user management
It is very simple to configure
Disadvantages
Unused user accounts will not be removed automatically.
Even after the user account has removed, it will be taken into count to predict the
maximum users.
Manual detection of rogue IPs
The two approaches to detect rouge access point is monitoring IP traffic and RF
waves. Using sniffers, the commercial products use the second one to detect rouge access point
manually scans the RF waves. For example, nets tumbler, air magnet or automatic process via
sensors. Rouge AP is the unofficial AP which is plugged in network wired side. The Aruba OS
produce rouge access point identification functionality which is avail in the fundamental
operating system.For detecting wireless access point, AM should scan air looking for the modern
device and remaining tabs on the device which is existing
Drawbacks
This method consumes more power.
It Suffers network scaling issue.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Question 3. Access Control [12 marks]
The passwords are protected by encripting text.It is stored in the form of random
text strings at the database or file.The password is always strored in the hash formats.Many ways
are there to protect the password.The password algorithms for secure the password are
alphanumeric characters,password length and minimum a caps lock strings.the /etc/password is
file format for storing the password.The hash value password only stored at the file.To confirm
the password, initially the system converts the entered string password in to hash value and then
verify.
The passwords are protected by encripting text.It is stored in the form of random
text strings at the database or file.The password is always strored in the hash formats.Many ways
are there to protect the password.The password algorithms for secure the password are
alphanumeric characters,password length and minimum a caps lock strings.the /etc/password is
file format for storing the password.The hash value password only stored at the file.To confirm
the password, initially the system converts the entered string password in to hash value and then
verify.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

There are two types of password based on the assign. If one could select not
administratively assigned for the password creation, the system could not find out the two or
more user have same passwords. One is administratively assigned and another one is not
administratively assigned. the tracking process of password is difficult, because the password
hash value is complex.
When the password is created using mix of characters, upper and lower case and length, at
that situation password is complex. The passwords are stored in the hash format at the file or
database
administratively assigned for the password creation, the system could not find out the two or
more user have same passwords. One is administratively assigned and another one is not
administratively assigned. the tracking process of password is difficult, because the password
hash value is complex.
When the password is created using mix of characters, upper and lower case and length, at
that situation password is complex. The passwords are stored in the hash format at the file or
database

Question 4. HTTPS and Certificates [12 marks]
The client certificate is the certificate of client which is addressed to the server for
certifying the client to utilize the server certificate. For developing link which is between client
and server HTTPS protocol is implemented. It is required that the server possess the digital
server certificate for creating HTTPS.
By using the codes known as response codes, server verification certificate is performed.
1XX, 2XX, 3XX, 4XX, 5XX are few of the response codes. The every code has sub codes which
is responsible to various response.
The client certificate is the certificate of client which is addressed to the server for
certifying the client to utilize the server certificate. For developing link which is between client
and server HTTPS protocol is implemented. It is required that the server possess the digital
server certificate for creating HTTPS.
By using the codes known as response codes, server verification certificate is performed.
1XX, 2XX, 3XX, 4XX, 5XX are few of the response codes. The every code has sub codes which
is responsible to various response.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
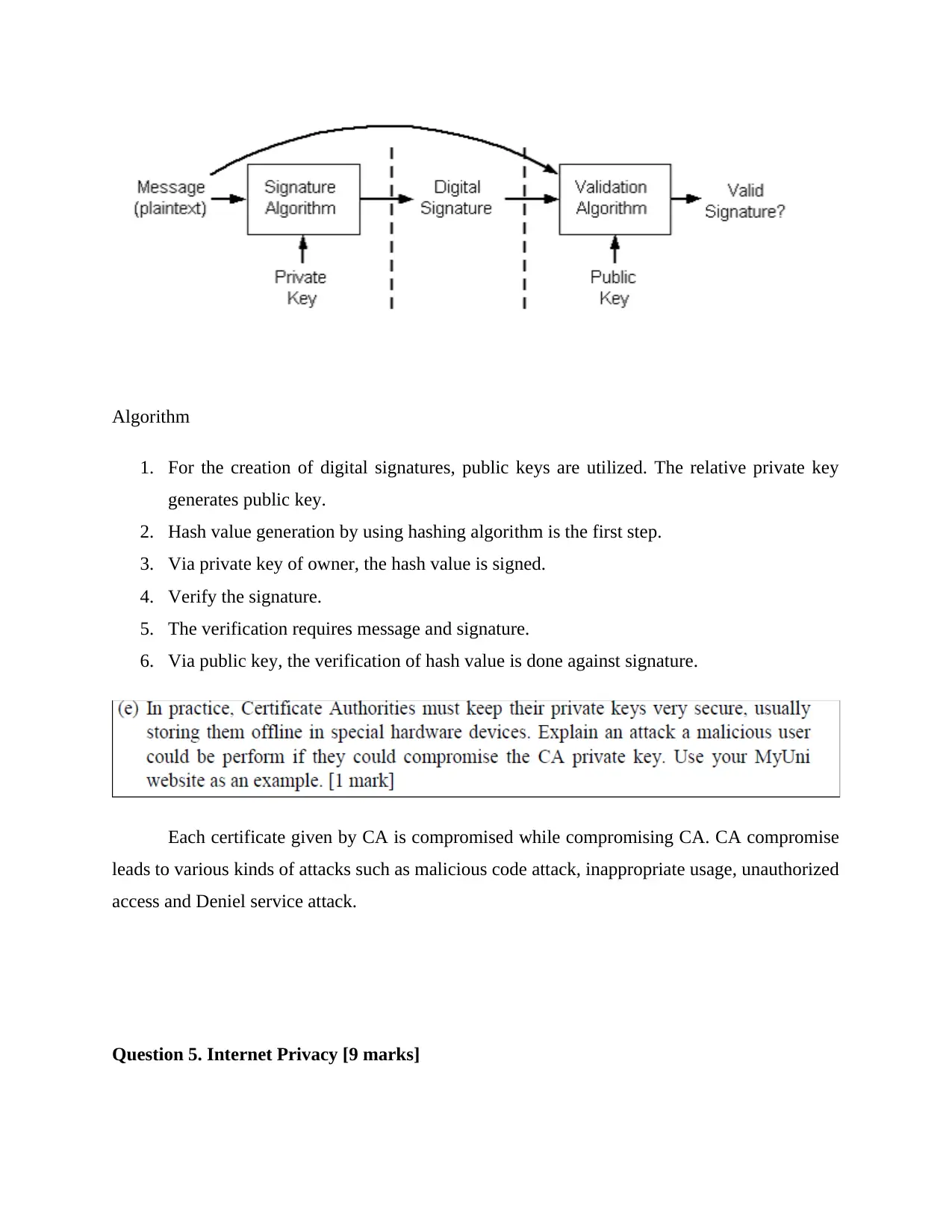
Algorithm
1. For the creation of digital signatures, public keys are utilized. The relative private key
generates public key.
2. Hash value generation by using hashing algorithm is the first step.
3. Via private key of owner, the hash value is signed.
4. Verify the signature.
5. The verification requires message and signature.
6. Via public key, the verification of hash value is done against signature.
Each certificate given by CA is compromised while compromising CA. CA compromise
leads to various kinds of attacks such as malicious code attack, inappropriate usage, unauthorized
access and Deniel service attack.
Question 5. Internet Privacy [9 marks]
1. For the creation of digital signatures, public keys are utilized. The relative private key
generates public key.
2. Hash value generation by using hashing algorithm is the first step.
3. Via private key of owner, the hash value is signed.
4. Verify the signature.
5. The verification requires message and signature.
6. Via public key, the verification of hash value is done against signature.
Each certificate given by CA is compromised while compromising CA. CA compromise
leads to various kinds of attacks such as malicious code attack, inappropriate usage, unauthorized
access and Deniel service attack.
Question 5. Internet Privacy [9 marks]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Web proxy
The proxy server acts as a mediator which is in-between server and customer pc. To ask
for any website pages, any other assets or any documents, the customer takes the proxy server
guide. Proxy server like a comparing proof shield which is in between the customer machine and
server. Proxy server premier and basic component like a safety defender equipment which is in
between server pc and customer pc.
Some of the advantages of web proxy is following below
1. Additionally, proxy server is used like bypassing blocked sites.
2. By the programmers, customer is encouraged by proxy server to cover their required
information from getting hacked.
The proxy server acts as a mediator which is in-between server and customer pc. To ask
for any website pages, any other assets or any documents, the customer takes the proxy server
guide. Proxy server like a comparing proof shield which is in between the customer machine and
server. Proxy server premier and basic component like a safety defender equipment which is in
between server pc and customer pc.
Some of the advantages of web proxy is following below
1. Additionally, proxy server is used like bypassing blocked sites.
2. By the programmers, customer is encouraged by proxy server to cover their required
information from getting hacked.

Disadvantages of web proxy is as follows
Using scrambled system, the data able to spill which use the methods of SSL and TLS
encoded association.
Attacks
For disguising IP address, assailants use IP satirizing strategy.
2. Tor
It is an administration enables the consumers confidentially to continue the internet. It is
otherwise known as onion router is decentralized framework. It able the client to connect via the
transfer system like opposed to provide sudden association. The pros of this method are that by
ignoring the association to server at arbitrary form the server, IP address avoids the locales.
Disadvantages of Tor
The each transfer hubs has the encoded information. During the encoding process, the
chain code could be trade off the last AP at last hand-off. If it is taken for site, it could not utilize
SSL. It has known downside. The Tor is combined with U.S Naval force for the problem of
administration. It is accessed by numerous administration offices. It reserved one as a criminal
sort. Mostly It monitors the online movement.
Using scrambled system, the data able to spill which use the methods of SSL and TLS
encoded association.
Attacks
For disguising IP address, assailants use IP satirizing strategy.
2. Tor
It is an administration enables the consumers confidentially to continue the internet. It is
otherwise known as onion router is decentralized framework. It able the client to connect via the
transfer system like opposed to provide sudden association. The pros of this method are that by
ignoring the association to server at arbitrary form the server, IP address avoids the locales.
Disadvantages of Tor
The each transfer hubs has the encoded information. During the encoding process, the
chain code could be trade off the last AP at last hand-off. If it is taken for site, it could not utilize
SSL. It has known downside. The Tor is combined with U.S Naval force for the problem of
administration. It is accessed by numerous administration offices. It reserved one as a criminal
sort. Mostly It monitors the online movement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





