Network Routing and Switching Protocols Project: Security Design
VerifiedAdded on 2021/04/17
|7
|926
|55
Project
AI Summary
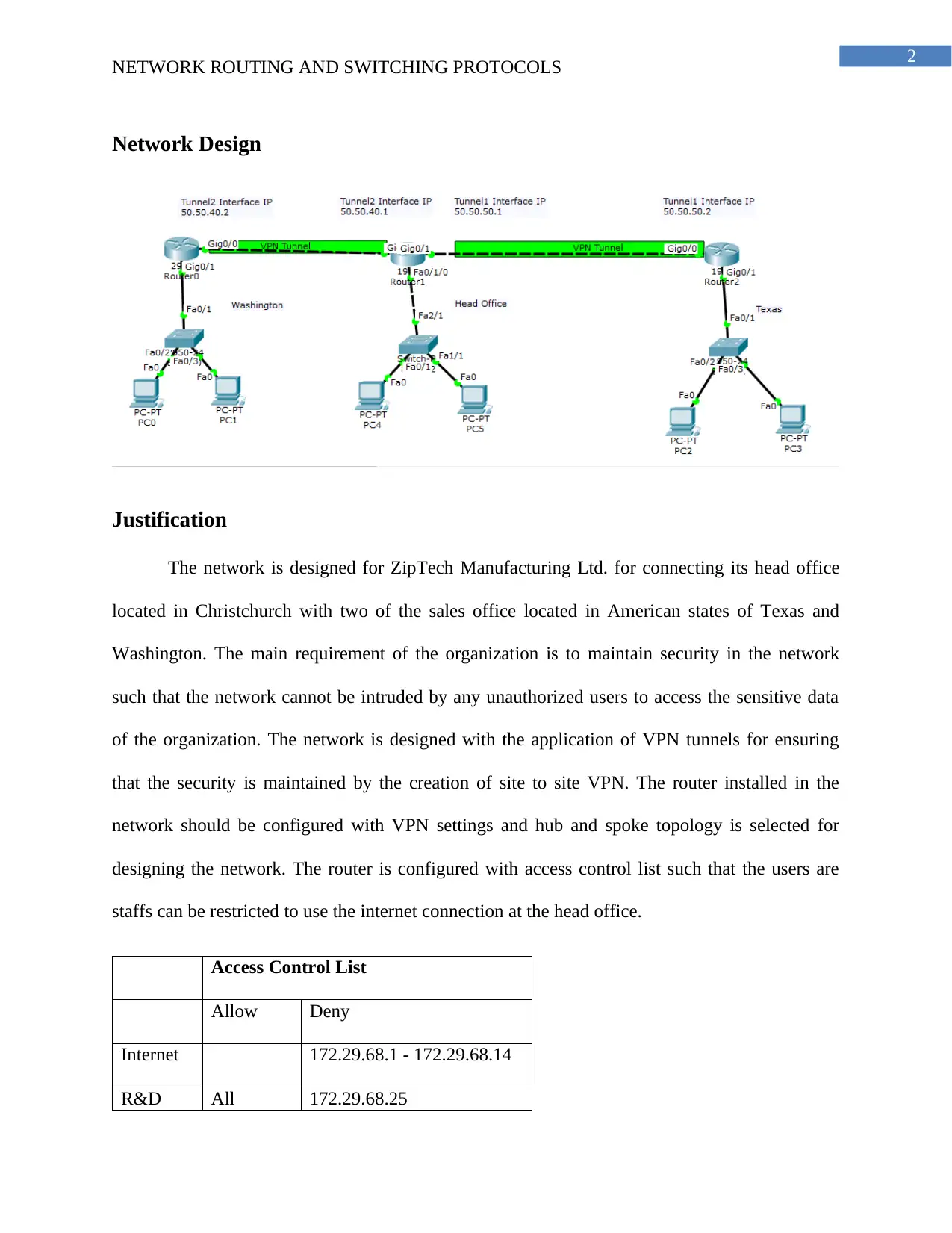
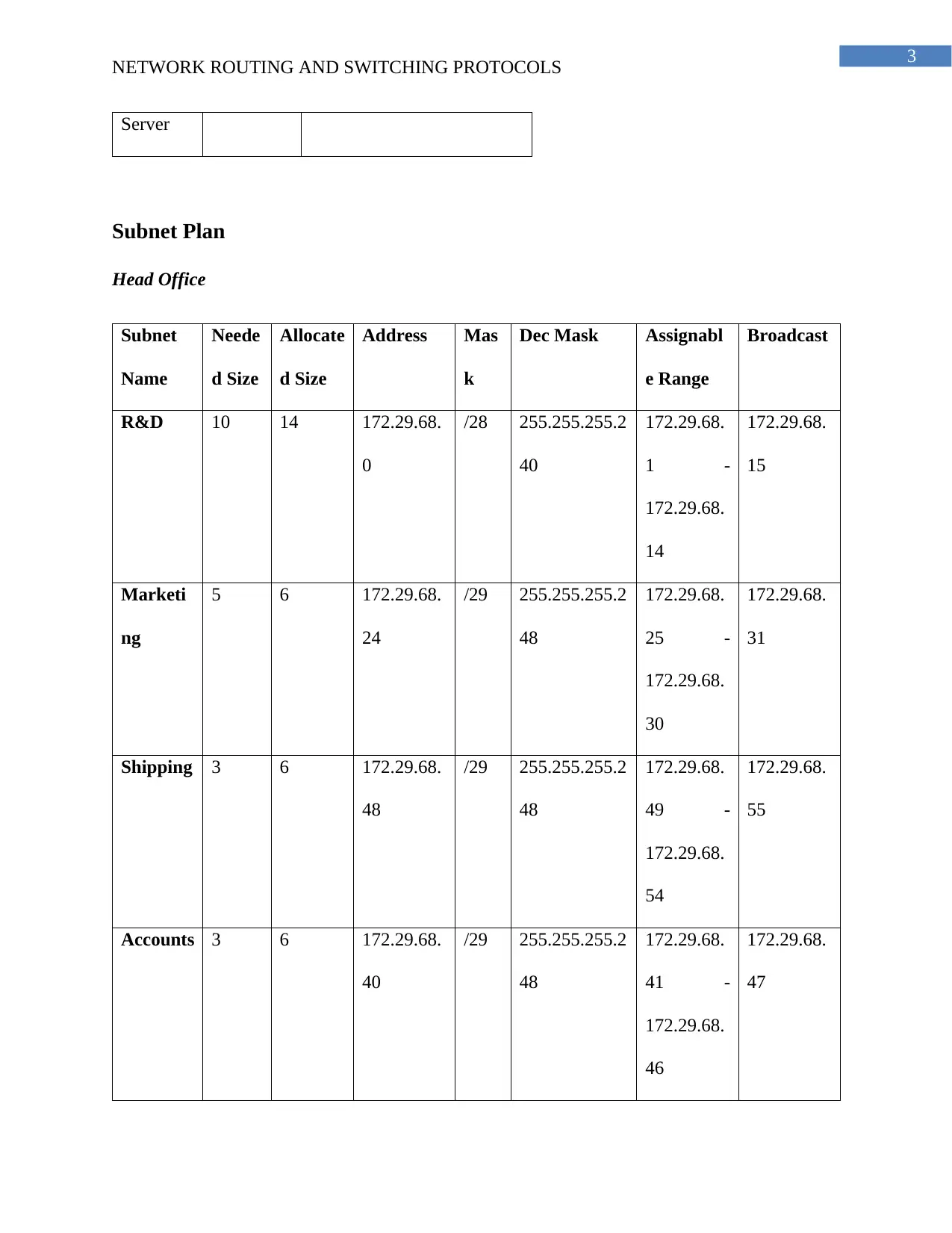
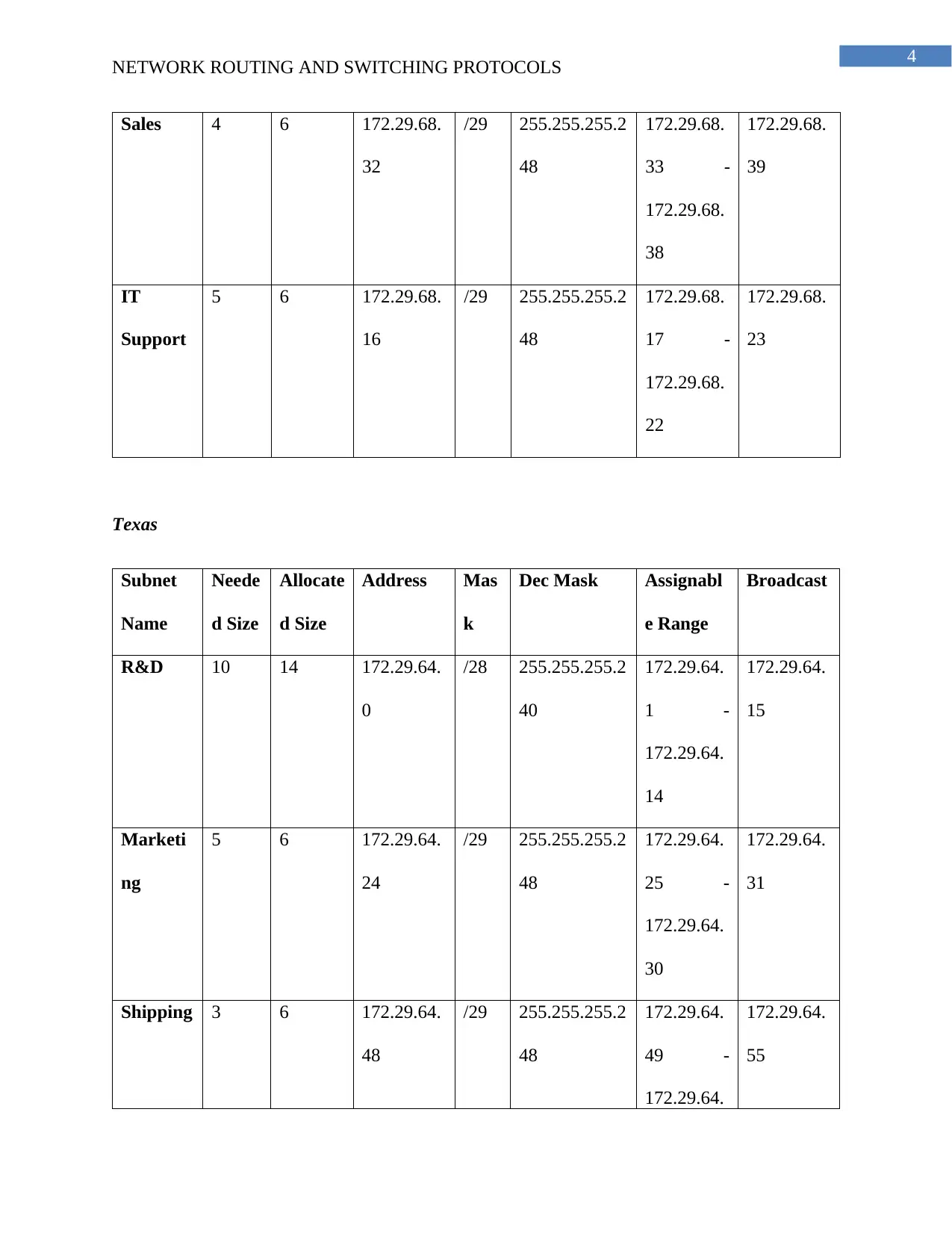
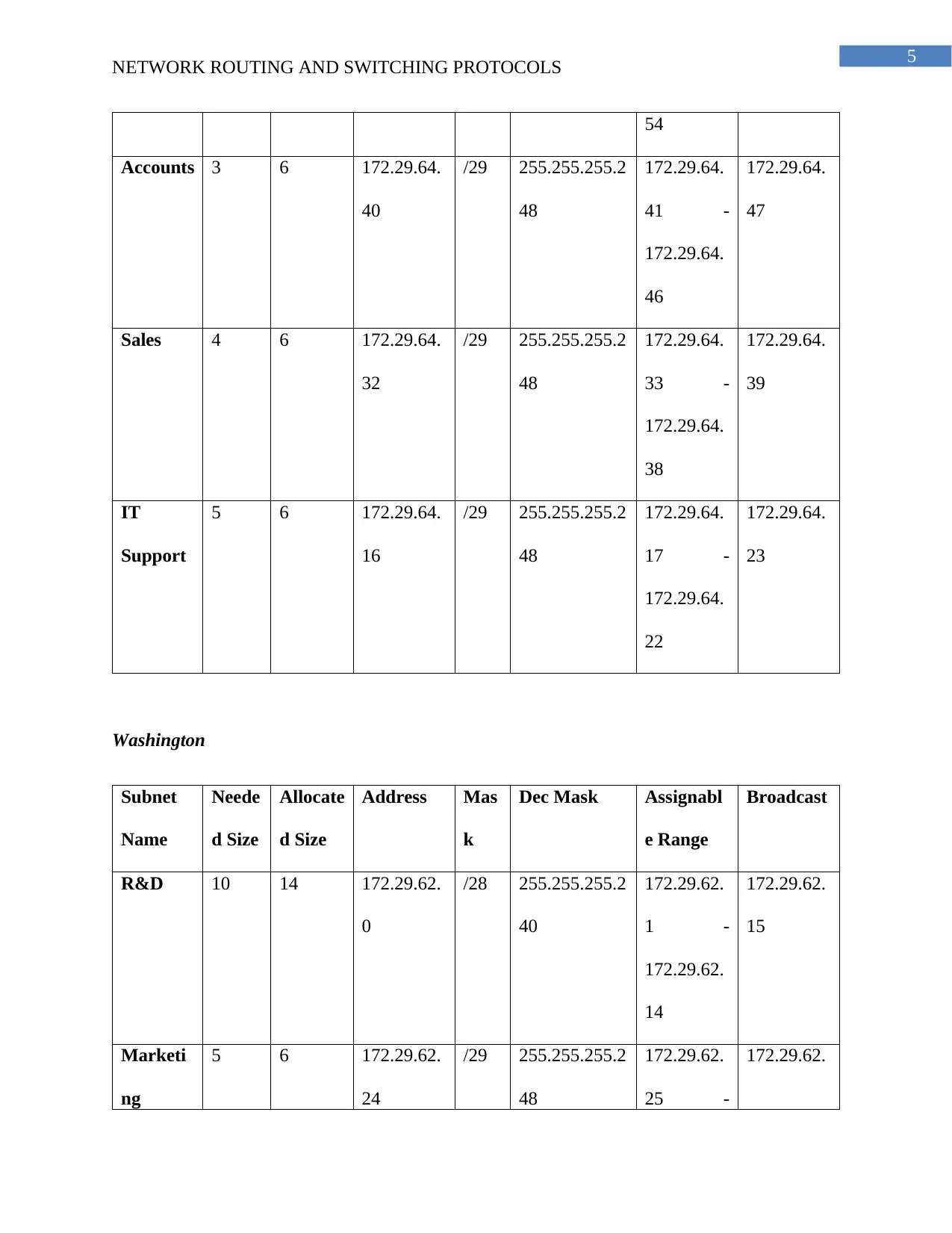
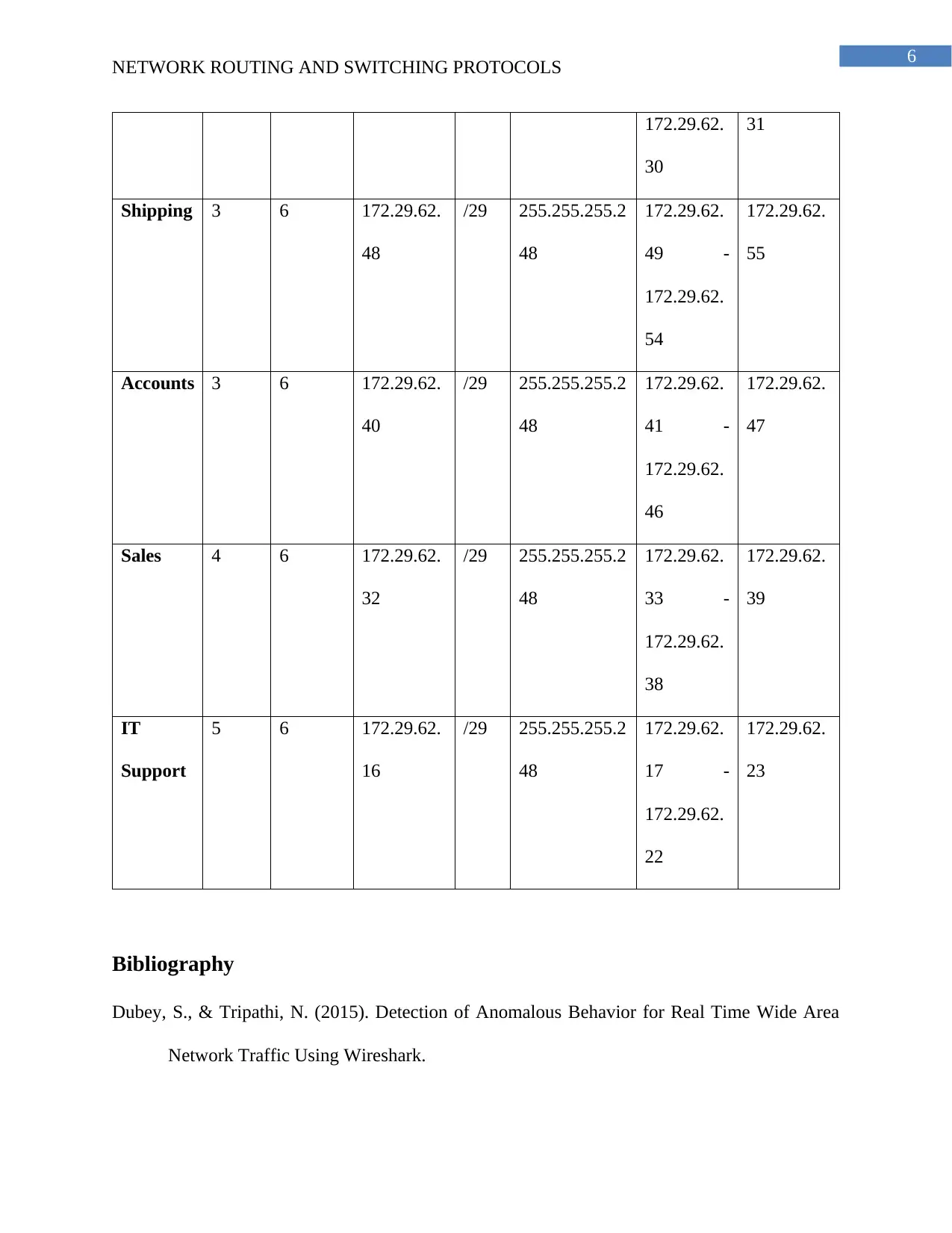
This project focuses on designing a secure network for ZipTech Manufacturing Ltd., connecting its head office in Christchurch with sales offices in Texas and Washington. The design emphasizes security using site-to-site VPN tunnels and a hub-and-spoke topology. The network employs access control lists to restrict internet access and protect sensitive data. The solution includes a detailed subnet plan, allocating IP addresses for various departments in each location. The project also provides a justification for the chosen design, highlighting the importance of VPNs for secure communication and the use of ACLs for managing internet access and overall network security. The subnet plan includes details of the subnet name, size, allocated size, address, mask, assignable range, and broadcast address for each department in each location.
1 out of 7









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)