COIT20261 Network Routing: Subnetting and Network Traffic Analysis
VerifiedAdded on 2023/06/13
|5
|828
|256
Homework Assignment
AI Summary
This assignment solution focuses on network routing and switching, covering classless addressing, subnetting, and network traffic analysis. It includes detailed explanations of IP addressing, subnetting calculations, and the use of tools like Wireshark and Netstat for network monitoring and troubleshooting. The solution provides examples of network address calculations, subnet configurations, and analysis of network packets using UDP and TCP protocols. It also discusses the functionality of command-line tools like Netstat and Tracert for examining network statistics and tracing IP paths, respectively. The assignment aims to demonstrate an understanding of basic routing concepts and their practical application in network management and security.
NETWORK ROUTING AND
SWITCHING
SWITCHING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Question Number
Question 1: (3 marks)
a)
b)
c)
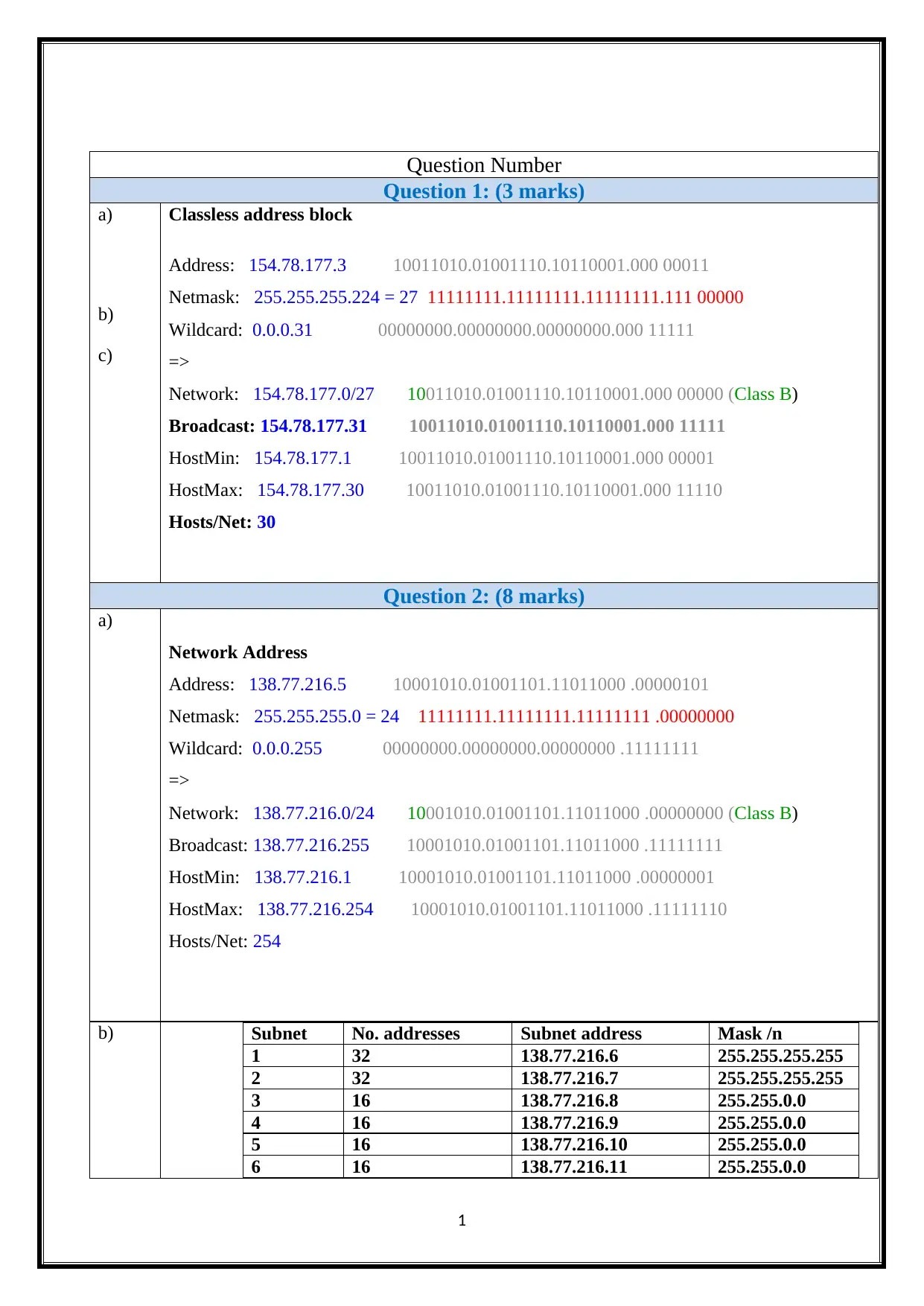
Classless address block
Address: 154.78.177.3 10011010.01001110.10110001.000 00011
Netmask: 255.255.255.224 = 27 11111111.11111111.11111111.111 00000
Wildcard: 0.0.0.31 00000000.00000000.00000000.000 11111
=>
Network: 154.78.177.0/27 10011010.01001110.10110001.000 00000 (Class B)
Broadcast: 154.78.177.31 10011010.01001110.10110001.000 11111
HostMin: 154.78.177.1 10011010.01001110.10110001.000 00001
HostMax: 154.78.177.30 10011010.01001110.10110001.000 11110
Hosts/Net: 30
Question 2: (8 marks)
a)
Network Address
Address: 138.77.216.5 10001010.01001101.11011000 .00000101
Netmask: 255.255.255.0 = 24 11111111.11111111.11111111 .00000000
Wildcard: 0.0.0.255 00000000.00000000.00000000 .11111111
=>
Network: 138.77.216.0/24 10001010.01001101.11011000 .00000000 (Class B)
Broadcast: 138.77.216.255 10001010.01001101.11011000 .11111111
HostMin: 138.77.216.1 10001010.01001101.11011000 .00000001
HostMax: 138.77.216.254 10001010.01001101.11011000 .11111110
Hosts/Net: 254
b) Subnet No. addresses Subnet address Mask /n
1 32 138.77.216.6 255.255.255.255
2 32 138.77.216.7 255.255.255.255
3 16 138.77.216.8 255.255.0.0
4 16 138.77.216.9 255.255.0.0
5 16 138.77.216.10 255.255.0.0
6 16 138.77.216.11 255.255.0.0
1
Question 1: (3 marks)
a)
b)
c)
Classless address block
Address: 154.78.177.3 10011010.01001110.10110001.000 00011
Netmask: 255.255.255.224 = 27 11111111.11111111.11111111.111 00000
Wildcard: 0.0.0.31 00000000.00000000.00000000.000 11111
=>
Network: 154.78.177.0/27 10011010.01001110.10110001.000 00000 (Class B)
Broadcast: 154.78.177.31 10011010.01001110.10110001.000 11111
HostMin: 154.78.177.1 10011010.01001110.10110001.000 00001
HostMax: 154.78.177.30 10011010.01001110.10110001.000 11110
Hosts/Net: 30
Question 2: (8 marks)
a)
Network Address
Address: 138.77.216.5 10001010.01001101.11011000 .00000101
Netmask: 255.255.255.0 = 24 11111111.11111111.11111111 .00000000
Wildcard: 0.0.0.255 00000000.00000000.00000000 .11111111
=>
Network: 138.77.216.0/24 10001010.01001101.11011000 .00000000 (Class B)
Broadcast: 138.77.216.255 10001010.01001101.11011000 .11111111
HostMin: 138.77.216.1 10001010.01001101.11011000 .00000001
HostMax: 138.77.216.254 10001010.01001101.11011000 .11111110
Hosts/Net: 254
b) Subnet No. addresses Subnet address Mask /n
1 32 138.77.216.6 255.255.255.255
2 32 138.77.216.7 255.255.255.255
3 16 138.77.216.8 255.255.0.0
4 16 138.77.216.9 255.255.0.0
5 16 138.77.216.10 255.255.0.0
6 16 138.77.216.11 255.255.0.0
1

c) The company granted a block of address is 1024 and it is allocated form the existing block
because it granted a block of address to provide the host and special addresses for each
subnet. Generally, the company grants the block that used to assign the address to the
network hosts. The network hosts address has the two addresses such as first address is needs
to use as network address and last address is needs to special address.
Question 3: (4 marks)
a)
i)
ii)
iii)
iv)
The wire shark horizontal display is contains the three basic information’s about the
packets such as packet Lists, details and bytes.
In Frame 2, it captures the 85 bytes of the packets by using the user datagram protocol.
The captured packets is has the hot limit is 128 bits and payload length is 31. It scans the
source port is 59362 and destination port is https 443. The exchange the packets between
source and destination. It is shown below (Kurose and Ross, 2017).
In frame 4, 5 and 6, the packets are exchanges the event by using the UDP and TCP
protocol. These protocols are used to provide the reliable network information in the captured
packets. Here, source port is https that exchanges the packets to destination. It sends the
packets to the destination port that is 59362. These two protocols are exchanges the packets
and message with each other and it uses the SSH protocol to aspects the behind the SSH key
exchanges between the source and destination.
The wire shark is used to monitor the network traffic and provide the network security. It is
very effective tools to reduce the network trouble shooting problems because it easily
determines the network security problems in a user network. It measures the data in a correct
manner to reduce the network problems and gives the effective and secure network.
2
because it granted a block of address to provide the host and special addresses for each
subnet. Generally, the company grants the block that used to assign the address to the
network hosts. The network hosts address has the two addresses such as first address is needs
to use as network address and last address is needs to special address.
Question 3: (4 marks)
a)
i)
ii)
iii)
iv)
The wire shark horizontal display is contains the three basic information’s about the
packets such as packet Lists, details and bytes.
In Frame 2, it captures the 85 bytes of the packets by using the user datagram protocol.
The captured packets is has the hot limit is 128 bits and payload length is 31. It scans the
source port is 59362 and destination port is https 443. The exchange the packets between
source and destination. It is shown below (Kurose and Ross, 2017).
In frame 4, 5 and 6, the packets are exchanges the event by using the UDP and TCP
protocol. These protocols are used to provide the reliable network information in the captured
packets. Here, source port is https that exchanges the packets to destination. It sends the
packets to the destination port that is 59362. These two protocols are exchanges the packets
and message with each other and it uses the SSH protocol to aspects the behind the SSH key
exchanges between the source and destination.
The wire shark is used to monitor the network traffic and provide the network security. It is
very effective tools to reduce the network trouble shooting problems because it easily
determines the network security problems in a user network. It measures the data in a correct
manner to reduce the network problems and gives the effective and secure network.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
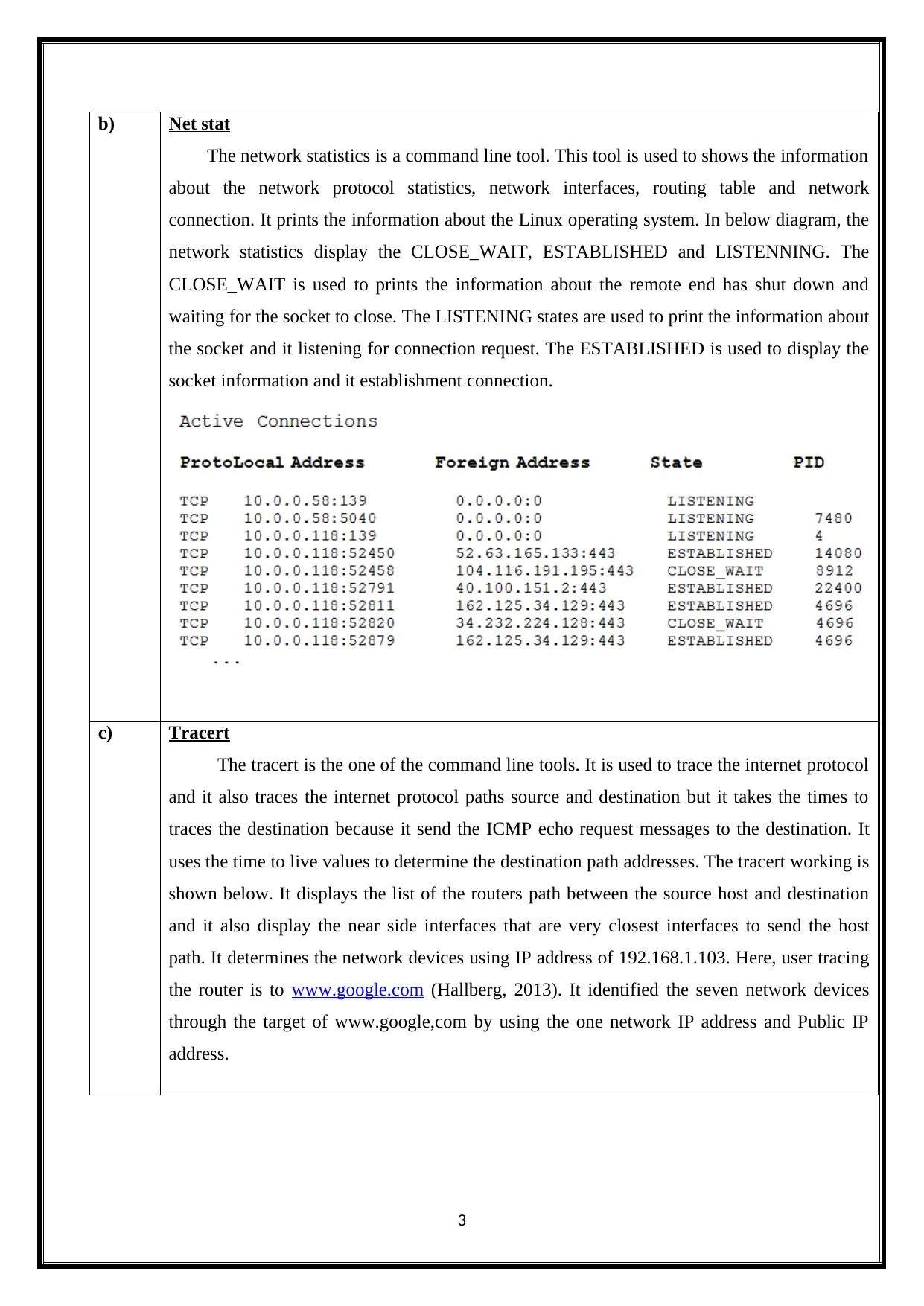
b) Net stat
The network statistics is a command line tool. This tool is used to shows the information
about the network protocol statistics, network interfaces, routing table and network
connection. It prints the information about the Linux operating system. In below diagram, the
network statistics display the CLOSE_WAIT, ESTABLISHED and LISTENNING. The
CLOSE_WAIT is used to prints the information about the remote end has shut down and
waiting for the socket to close. The LISTENING states are used to print the information about
the socket and it listening for connection request. The ESTABLISHED is used to display the
socket information and it establishment connection.
c) Tracert
The tracert is the one of the command line tools. It is used to trace the internet protocol
and it also traces the internet protocol paths source and destination but it takes the times to
traces the destination because it send the ICMP echo request messages to the destination. It
uses the time to live values to determine the destination path addresses. The tracert working is
shown below. It displays the list of the routers path between the source host and destination
and it also display the near side interfaces that are very closest interfaces to send the host
path. It determines the network devices using IP address of 192.168.1.103. Here, user tracing
the router is to www.google.com (Hallberg, 2013). It identified the seven network devices
through the target of www.google,com by using the one network IP address and Public IP
address.
3
The network statistics is a command line tool. This tool is used to shows the information
about the network protocol statistics, network interfaces, routing table and network
connection. It prints the information about the Linux operating system. In below diagram, the
network statistics display the CLOSE_WAIT, ESTABLISHED and LISTENNING. The
CLOSE_WAIT is used to prints the information about the remote end has shut down and
waiting for the socket to close. The LISTENING states are used to print the information about
the socket and it listening for connection request. The ESTABLISHED is used to display the
socket information and it establishment connection.
c) Tracert
The tracert is the one of the command line tools. It is used to trace the internet protocol
and it also traces the internet protocol paths source and destination but it takes the times to
traces the destination because it send the ICMP echo request messages to the destination. It
uses the time to live values to determine the destination path addresses. The tracert working is
shown below. It displays the list of the routers path between the source host and destination
and it also display the near side interfaces that are very closest interfaces to send the host
path. It determines the network devices using IP address of 192.168.1.103. Here, user tracing
the router is to www.google.com (Hallberg, 2013). It identified the seven network devices
through the target of www.google,com by using the one network IP address and Public IP
address.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
References
Hallberg, B. (2013). Networking. New York: McGraw-Hill Publishing.
Kurose, J., & Ross, K. (2017). Computer networking. Harlow: Pearson Education.
4
Hallberg, B. (2013). Networking. New York: McGraw-Hill Publishing.
Kurose, J., & Ross, K. (2017). Computer networking. Harlow: Pearson Education.
4
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



