University Network Security Essay: Two-Factor Authentication Analysis
VerifiedAdded on 2022/09/15
|15
|3089
|18
Essay
AI Summary
This essay provides a comprehensive analysis of two-factor authentication (2FA) in network security. It begins with an introduction to 2FA, highlighting its significance in the digital era and addressing the vulnerabilities of single-factor authentication. The essay delves into real-world examples of 2FA implementation by Google, Facebook, Instagram, and WhatsApp, illustrating how these platforms utilize 2FA to enhance user account security. It then explains why 2FA is crucial, discussing its benefits such as enhanced security, increased productivity, and reduced costs. The essay also examines how 2FA mitigates password risks and provides examples of websites that do not use 2FA, along with the potential consequences. Furthermore, it addresses the false sense of security and potential risks associated with 2FA. The conclusion summarizes the key findings and emphasizes the importance of 2FA in modern security practices.

Running head: NETWORK AND SECURITY
NETWORK AND SECURITY
Name of the Student
Name of the University
Author Note:
NETWORK AND SECURITY
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK AND SECURITY
Introduction
At present, Two-factor (2FA) or multi-factor authentication is found to be an additional
security layer for any business. It merely helps in addressing the vulnerabilities of standard
password approach. In the current digital era, there has been huge number of development in the
system sector (Danezis et al. 2016). Single-factor authentication that is password is not
considered to be secure in internet world. There has been growing threats with respect to security
and privacy due to malware. As a result of increase in access to information, there has been
increase in hacking, password cracking and online fraud activities. Two – factor authentication
aims to assure high level protection due to extension of single-factor authentication (Mattos and
Duarte 2016). An overview has been provided with respect to two-factor authentication methods
that are being used for graphical and alphanumeric password. These two aspects are considered
to be password gateway for authentication.
In the coming pages of the essay, a list of example has been provided with respect to
website making use of two-factor authentication. The next part deals with importance of two-
factor authentication. In addition, the essay provides an idea about 2FA can overcome the
password risk. The essay also some example where 2FA is not being used and possible
consequences which leads to social issues.
Discussion
Example of well-known site using 2FA
Google: Google has an easy access to credit card through application google play. In
addition, it has an easy access to messages, documents and YouTube videos. Google look for
two-stage verification where user need to provide password to have an easy access to google
Introduction
At present, Two-factor (2FA) or multi-factor authentication is found to be an additional
security layer for any business. It merely helps in addressing the vulnerabilities of standard
password approach. In the current digital era, there has been huge number of development in the
system sector (Danezis et al. 2016). Single-factor authentication that is password is not
considered to be secure in internet world. There has been growing threats with respect to security
and privacy due to malware. As a result of increase in access to information, there has been
increase in hacking, password cracking and online fraud activities. Two – factor authentication
aims to assure high level protection due to extension of single-factor authentication (Mattos and
Duarte 2016). An overview has been provided with respect to two-factor authentication methods
that are being used for graphical and alphanumeric password. These two aspects are considered
to be password gateway for authentication.
In the coming pages of the essay, a list of example has been provided with respect to
website making use of two-factor authentication. The next part deals with importance of two-
factor authentication. In addition, the essay provides an idea about 2FA can overcome the
password risk. The essay also some example where 2FA is not being used and possible
consequences which leads to social issues.
Discussion
Example of well-known site using 2FA
Google: Google has an easy access to credit card through application google play. In
addition, it has an easy access to messages, documents and YouTube videos. Google look for
two-stage verification where user need to provide password to have an easy access to google
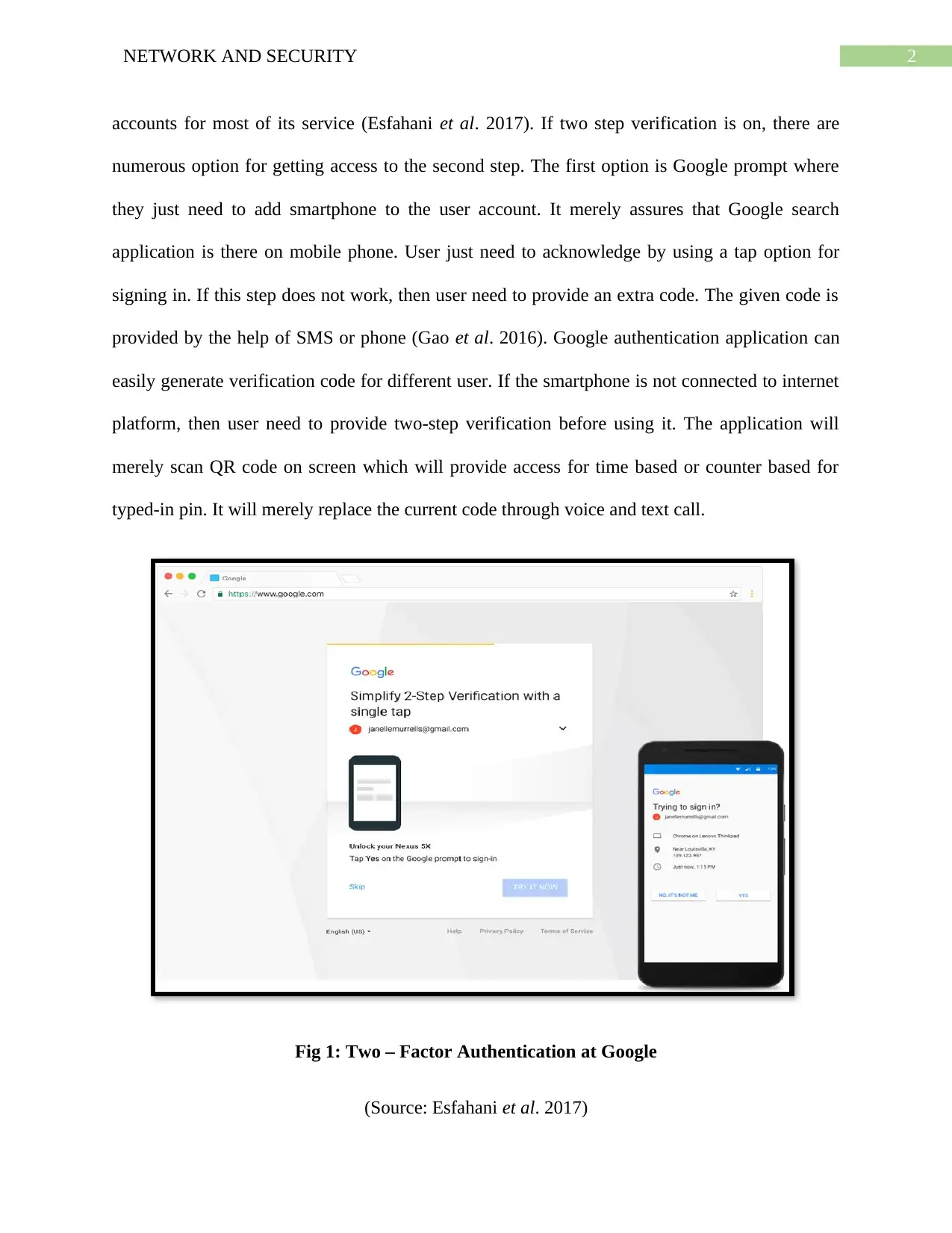
2NETWORK AND SECURITY
accounts for most of its service (Esfahani et al. 2017). If two step verification is on, there are
numerous option for getting access to the second step. The first option is Google prompt where
they just need to add smartphone to the user account. It merely assures that Google search
application is there on mobile phone. User just need to acknowledge by using a tap option for
signing in. If this step does not work, then user need to provide an extra code. The given code is
provided by the help of SMS or phone (Gao et al. 2016). Google authentication application can
easily generate verification code for different user. If the smartphone is not connected to internet
platform, then user need to provide two-step verification before using it. The application will
merely scan QR code on screen which will provide access for time based or counter based for
typed-in pin. It will merely replace the current code through voice and text call.
Fig 1: Two – Factor Authentication at Google
(Source: Esfahani et al. 2017)
accounts for most of its service (Esfahani et al. 2017). If two step verification is on, there are
numerous option for getting access to the second step. The first option is Google prompt where
they just need to add smartphone to the user account. It merely assures that Google search
application is there on mobile phone. User just need to acknowledge by using a tap option for
signing in. If this step does not work, then user need to provide an extra code. The given code is
provided by the help of SMS or phone (Gao et al. 2016). Google authentication application can
easily generate verification code for different user. If the smartphone is not connected to internet
platform, then user need to provide two-step verification before using it. The application will
merely scan QR code on screen which will provide access for time based or counter based for
typed-in pin. It will merely replace the current code through voice and text call.
Fig 1: Two – Factor Authentication at Google
(Source: Esfahani et al. 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK AND SECURITY
Facebook Two-factor authentication: The two-factor authentication of Facebook will
help in preventing any kind of loss control on the account. On system, user can access it going to
the setting option through security and login. In case of two-factor authentication, user needs to
click on right option (Garg et al. 2019). User will receive the second form of authentication
through authentication application and physical security key. If the user selects the authentication
application, then Facebook will provide a QR code on the screen.
Fig 2: Two-Factor Authentication
(Source: Gao et al. 2016)
Instagram: In the year 2016, Facebook bought Instagram and offered two-factor
authentication. For using it, a user just need turn it on that is setting, privacy and security and last
two-factor authentication (Farash et al. 2017). User just needs to turn on text message and phone
inclusive of country code. There is second option where user can switch on the authentication
Facebook Two-factor authentication: The two-factor authentication of Facebook will
help in preventing any kind of loss control on the account. On system, user can access it going to
the setting option through security and login. In case of two-factor authentication, user needs to
click on right option (Garg et al. 2019). User will receive the second form of authentication
through authentication application and physical security key. If the user selects the authentication
application, then Facebook will provide a QR code on the screen.
Fig 2: Two-Factor Authentication
(Source: Gao et al. 2016)
Instagram: In the year 2016, Facebook bought Instagram and offered two-factor
authentication. For using it, a user just need turn it on that is setting, privacy and security and last
two-factor authentication (Farash et al. 2017). User just needs to turn on text message and phone
inclusive of country code. There is second option where user can switch on the authentication
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
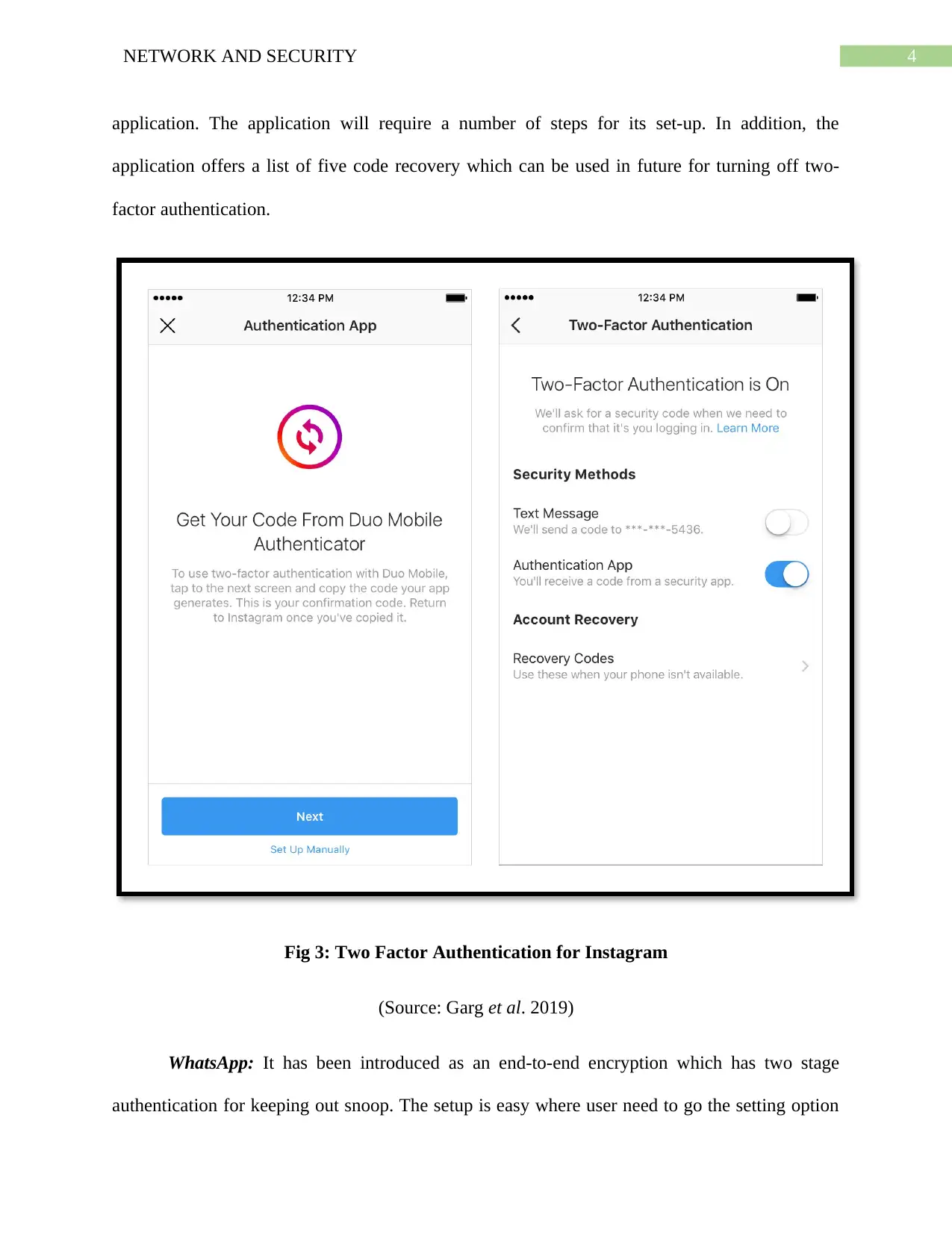
4NETWORK AND SECURITY
application. The application will require a number of steps for its set-up. In addition, the
application offers a list of five code recovery which can be used in future for turning off two-
factor authentication.
Fig 3: Two Factor Authentication for Instagram
(Source: Garg et al. 2019)
WhatsApp: It has been introduced as an end-to-end encryption which has two stage
authentication for keeping out snoop. The setup is easy where user need to go the setting option
application. The application will require a number of steps for its set-up. In addition, the
application offers a list of five code recovery which can be used in future for turning off two-
factor authentication.
Fig 3: Two Factor Authentication for Instagram
(Source: Garg et al. 2019)
WhatsApp: It has been introduced as an end-to-end encryption which has two stage
authentication for keeping out snoop. The setup is easy where user need to go the setting option
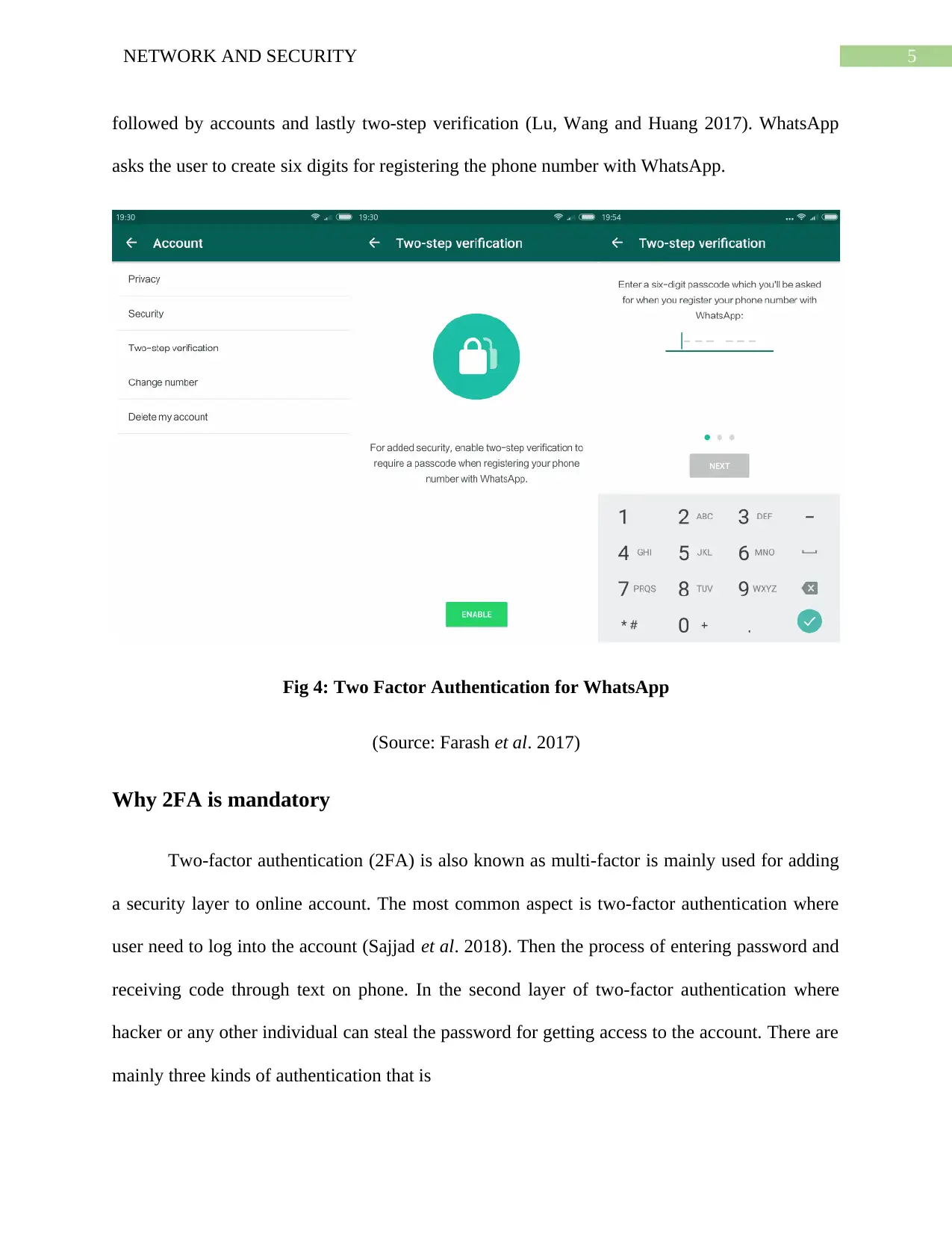
5NETWORK AND SECURITY
followed by accounts and lastly two-step verification (Lu, Wang and Huang 2017). WhatsApp
asks the user to create six digits for registering the phone number with WhatsApp.
Fig 4: Two Factor Authentication for WhatsApp
(Source: Farash et al. 2017)
Why 2FA is mandatory
Two-factor authentication (2FA) is also known as multi-factor is mainly used for adding
a security layer to online account. The most common aspect is two-factor authentication where
user need to log into the account (Sajjad et al. 2018). Then the process of entering password and
receiving code through text on phone. In the second layer of two-factor authentication where
hacker or any other individual can steal the password for getting access to the account. There are
mainly three kinds of authentication that is
followed by accounts and lastly two-step verification (Lu, Wang and Huang 2017). WhatsApp
asks the user to create six digits for registering the phone number with WhatsApp.
Fig 4: Two Factor Authentication for WhatsApp
(Source: Farash et al. 2017)
Why 2FA is mandatory
Two-factor authentication (2FA) is also known as multi-factor is mainly used for adding
a security layer to online account. The most common aspect is two-factor authentication where
user need to log into the account (Sajjad et al. 2018). Then the process of entering password and
receiving code through text on phone. In the second layer of two-factor authentication where
hacker or any other individual can steal the password for getting access to the account. There are
mainly three kinds of authentication that is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK AND SECURITY
Password and Zipcode
Phone or credit card.
Biometric like retina or face.
Password is known to be first factor authentication where second-factor authentication
mainly arrives by SMS. User will have a text with numerical code where user need to logging
into the account (Nag, Roy and Dasgupta 2015). 2FA code is only used at a single time where
user will log into the account and new code will be sent to the account. User can also make use
of dedication authentication app to receive codes instead of text. Some of the well-known
authentication applications are DuoMobile, Authy and Google authenticator.
2FA can bring large number of benefits like
Enhancing Security: By having second form of authentication, SMS of 2FA will
decrease the overall probability for attacker gaining access to system, account and sensitive
information of a user (Wang and Wang 2016). If a fraudster has gained access to a password,
then he will second aspect for gaining access to the user account.
Enhances productivity and Flexibility: Most of the organization around the globe are
focusing on mobility which contributes to the overall productivity. By the help of mobile 2FA,
employees can have secure access to some of the corporate documents and back-off office
system from any device (Jiang et al. 2017). The whole thing can take place without any security
risk for network and sensitive information.
Lowering helpdesk and security management cost: Most of the user calls the help
around 1.25 times on monthly basis. Around thirty to forty percent calls are completely related
with respect to password reset. Each of these ticket will require 20 minutes of different
Password and Zipcode
Phone or credit card.
Biometric like retina or face.
Password is known to be first factor authentication where second-factor authentication
mainly arrives by SMS. User will have a text with numerical code where user need to logging
into the account (Nag, Roy and Dasgupta 2015). 2FA code is only used at a single time where
user will log into the account and new code will be sent to the account. User can also make use
of dedication authentication app to receive codes instead of text. Some of the well-known
authentication applications are DuoMobile, Authy and Google authenticator.
2FA can bring large number of benefits like
Enhancing Security: By having second form of authentication, SMS of 2FA will
decrease the overall probability for attacker gaining access to system, account and sensitive
information of a user (Wang and Wang 2016). If a fraudster has gained access to a password,
then he will second aspect for gaining access to the user account.
Enhances productivity and Flexibility: Most of the organization around the globe are
focusing on mobility which contributes to the overall productivity. By the help of mobile 2FA,
employees can have secure access to some of the corporate documents and back-off office
system from any device (Jiang et al. 2017). The whole thing can take place without any security
risk for network and sensitive information.
Lowering helpdesk and security management cost: Most of the user calls the help
around 1.25 times on monthly basis. Around thirty to forty percent calls are completely related
with respect to password reset. Each of these ticket will require 20 minutes of different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK AND SECURITY
technician time (Shah, Choyi and Subramanian 2015). Two-factor authentication is best remedy
for these time-consuming and costly password resets. It merely provides a safe and secure
method for different user so that they can reset their password. The overall business outcomes
are merely inclusive of cost from different calls that results in employee productivity and
satisfaction.
Fig 5: Steps of Two Factor Authentication
(Source: Sajjad et al. 2018)
Mitigating password risk
Two-factor authentication (2FA) is a well-known security process which verifies the user
with two different forms of identification. Most commonly used knowledge is email address and
ownership proof for mobile number (Dasgupta, Roy and Nag 2016). 2FA mainly boast the
overall security by making difficult for any intruder for getting unauthorized access. At present,
2FA is generally employed on online banking website, social media platform and e-commerce
website. It can be defined as the way of hardening the access control for most of the sensitive
technician time (Shah, Choyi and Subramanian 2015). Two-factor authentication is best remedy
for these time-consuming and costly password resets. It merely provides a safe and secure
method for different user so that they can reset their password. The overall business outcomes
are merely inclusive of cost from different calls that results in employee productivity and
satisfaction.
Fig 5: Steps of Two Factor Authentication
(Source: Sajjad et al. 2018)
Mitigating password risk
Two-factor authentication (2FA) is a well-known security process which verifies the user
with two different forms of identification. Most commonly used knowledge is email address and
ownership proof for mobile number (Dasgupta, Roy and Nag 2016). 2FA mainly boast the
overall security by making difficult for any intruder for getting unauthorized access. At present,
2FA is generally employed on online banking website, social media platform and e-commerce
website. It can be defined as the way of hardening the access control for most of the sensitive

8NETWORK AND SECURITY
information of web based application. Two-factor authentication also help the business and
different public institutes to be productive and efficient in nature. It will merely allow the
employee to carry out different task with minimum security concern (Khan et al. 2015). 2FA can
be distinguished into three aspects like knowledge factors, possession factors and inherence
factor. Two-factor authentication play a major role by blocking a number of application
depended attacks. It is merely inclusive of brute force and dictionary attacks that makes use of
automated software for generating huge amount of password combination. By the help of two-
factor authentication, user can help the application to easily tackle attacks from social
engineering like phishing. There has been attempt for user to reveal user sensitive data which is
inclusive of username and password (Colnago et al. 2018). In the case of successful attack, a
perpetrator will have additional form of information by having 2FA.
Examples of not using 2FA
There is list of websites that are not using 2FA like
Adobe creative cloud
Amazon.com
Bluehost.com
Capitalone.com
HostGator.com
Intuit Turbo box
Pinterest
Snapchat
Stack Overflow
information of web based application. Two-factor authentication also help the business and
different public institutes to be productive and efficient in nature. It will merely allow the
employee to carry out different task with minimum security concern (Khan et al. 2015). 2FA can
be distinguished into three aspects like knowledge factors, possession factors and inherence
factor. Two-factor authentication play a major role by blocking a number of application
depended attacks. It is merely inclusive of brute force and dictionary attacks that makes use of
automated software for generating huge amount of password combination. By the help of two-
factor authentication, user can help the application to easily tackle attacks from social
engineering like phishing. There has been attempt for user to reveal user sensitive data which is
inclusive of username and password (Colnago et al. 2018). In the case of successful attack, a
perpetrator will have additional form of information by having 2FA.
Examples of not using 2FA
There is list of websites that are not using 2FA like
Adobe creative cloud
Amazon.com
Bluehost.com
Capitalone.com
HostGator.com
Intuit Turbo box
Snapchat
Stack Overflow
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK AND SECURITY
Consequence of not using 2FA
Technologist around the globe assume the fact that people around the globe are making
use of two-factor authentication as it will increase an extra time for each work.
User can lose access to account: At any point, if the attacker does not have access to
account without second factor, then the user neither have access to it. User cannot recover the
account if he or she does not have authentication application (Danezis et al. 2016). In some
cases, website like GitHub does not allow an individual to easily reset its email for recovery even
if does not second factor.
More opportunities for attackers: If the user changes the mode of signing into the
website, then it will bring new opportunities to user. If the user carries a security key which is
plug into the USB slot of system at home and work. The system is stored in the private space
while the key travels with user (Lu, Wang and Huang 2017). Hacker can steal the security key
when they are in public space like restaurant or even coffee shop by replacing with similar
device. When this similar-looking device is plugged into the system it can get full control of
system by installing a driver. The attacker can get password from password manager of the
system. By using security key and password, attacker can easily log in as per their will.
False Sense of Security: Two-factor authentication aims to provide huge amount of
security and the degree of security which is often very large. If a user has locked out of a
particular service, just because of factor (Mattos and Duarte 2016). Now in this scenario, if the
user can have an access to account without factor, then hacker can easily do the same thing.
Factor can be easily lost: There is no assurance of the fact that the authentication factor
will be made available when it is required. In most of the cases, it just requires only one mistake
Consequence of not using 2FA
Technologist around the globe assume the fact that people around the globe are making
use of two-factor authentication as it will increase an extra time for each work.
User can lose access to account: At any point, if the attacker does not have access to
account without second factor, then the user neither have access to it. User cannot recover the
account if he or she does not have authentication application (Danezis et al. 2016). In some
cases, website like GitHub does not allow an individual to easily reset its email for recovery even
if does not second factor.
More opportunities for attackers: If the user changes the mode of signing into the
website, then it will bring new opportunities to user. If the user carries a security key which is
plug into the USB slot of system at home and work. The system is stored in the private space
while the key travels with user (Lu, Wang and Huang 2017). Hacker can steal the security key
when they are in public space like restaurant or even coffee shop by replacing with similar
device. When this similar-looking device is plugged into the system it can get full control of
system by installing a driver. The attacker can get password from password manager of the
system. By using security key and password, attacker can easily log in as per their will.
False Sense of Security: Two-factor authentication aims to provide huge amount of
security and the degree of security which is often very large. If a user has locked out of a
particular service, just because of factor (Mattos and Duarte 2016). Now in this scenario, if the
user can have an access to account without factor, then hacker can easily do the same thing.
Factor can be easily lost: There is no assurance of the fact that the authentication factor
will be made available when it is required. In most of the cases, it just requires only one mistake
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK AND SECURITY
to lock a user out of the account (Nag, Roy and Dasgupta 2015). SMS codes are known as the
second most important authentication factor. Depending on USB on second-factor authentication
factor is considered to be bit risky. Even some of the biometric factors like finger and eye can be
lost in an accident.
2FA can be used against user: Two-factor authentication is all about keeping hackers
out of the account (Shah, Choyi and Subramanian 2015). The reverse scenario when the hackers
want to configure two-factor authentication for keeping them out the account.
Fig 6: Two Factor Authentication
(Source: Khan et al. 2015)
Conclusion
to lock a user out of the account (Nag, Roy and Dasgupta 2015). SMS codes are known as the
second most important authentication factor. Depending on USB on second-factor authentication
factor is considered to be bit risky. Even some of the biometric factors like finger and eye can be
lost in an accident.
2FA can be used against user: Two-factor authentication is all about keeping hackers
out of the account (Shah, Choyi and Subramanian 2015). The reverse scenario when the hackers
want to configure two-factor authentication for keeping them out the account.
Fig 6: Two Factor Authentication
(Source: Khan et al. 2015)
Conclusion

11NETWORK AND SECURITY
The above pages help us in concluding the fact that this report is all about two-factor
authentication. Most of the online accounts require second-factor authentication require second
form of identification that can prevent certain number of attacks. Second factor can be easily
used for identifying the authenticator application on mobile phone. The codes changes within 30
seconds. Innovation can easily improve the overall security of online account. It is found to have
well deserved authentication factor. At present, security is considered to be the major concern for
various sectors like banks, military organization and education firms. Most of the government
firms around the globe are making use of certain password and agencies that can comply with the
standard. There are large number of issues when it comes to different security aspects in
changing industries where one the common link is password. With every passing year,
maintaining and keeping up standard is going to be tough. Two factor authentication does not
only improve security but also enhances the resistance to client. Integration of two-factor
authentication is considered to be best security. With the help of two-factor authentication, user
can have assured access to application based on something they and something they have. The
most well-known two-factor authentication is the bank ATM system. Something the user has is
the ATM card while something they know is the ATM pin.
The above pages help us in concluding the fact that this report is all about two-factor
authentication. Most of the online accounts require second-factor authentication require second
form of identification that can prevent certain number of attacks. Second factor can be easily
used for identifying the authenticator application on mobile phone. The codes changes within 30
seconds. Innovation can easily improve the overall security of online account. It is found to have
well deserved authentication factor. At present, security is considered to be the major concern for
various sectors like banks, military organization and education firms. Most of the government
firms around the globe are making use of certain password and agencies that can comply with the
standard. There are large number of issues when it comes to different security aspects in
changing industries where one the common link is password. With every passing year,
maintaining and keeping up standard is going to be tough. Two factor authentication does not
only improve security but also enhances the resistance to client. Integration of two-factor
authentication is considered to be best security. With the help of two-factor authentication, user
can have assured access to application based on something they and something they have. The
most well-known two-factor authentication is the bank ATM system. Something the user has is
the ATM card while something they know is the ATM pin.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




