Network Analyzer Report: Security Tools, Scenario Analysis
VerifiedAdded on 2021/06/17
|22
|1370
|37
Report
AI Summary
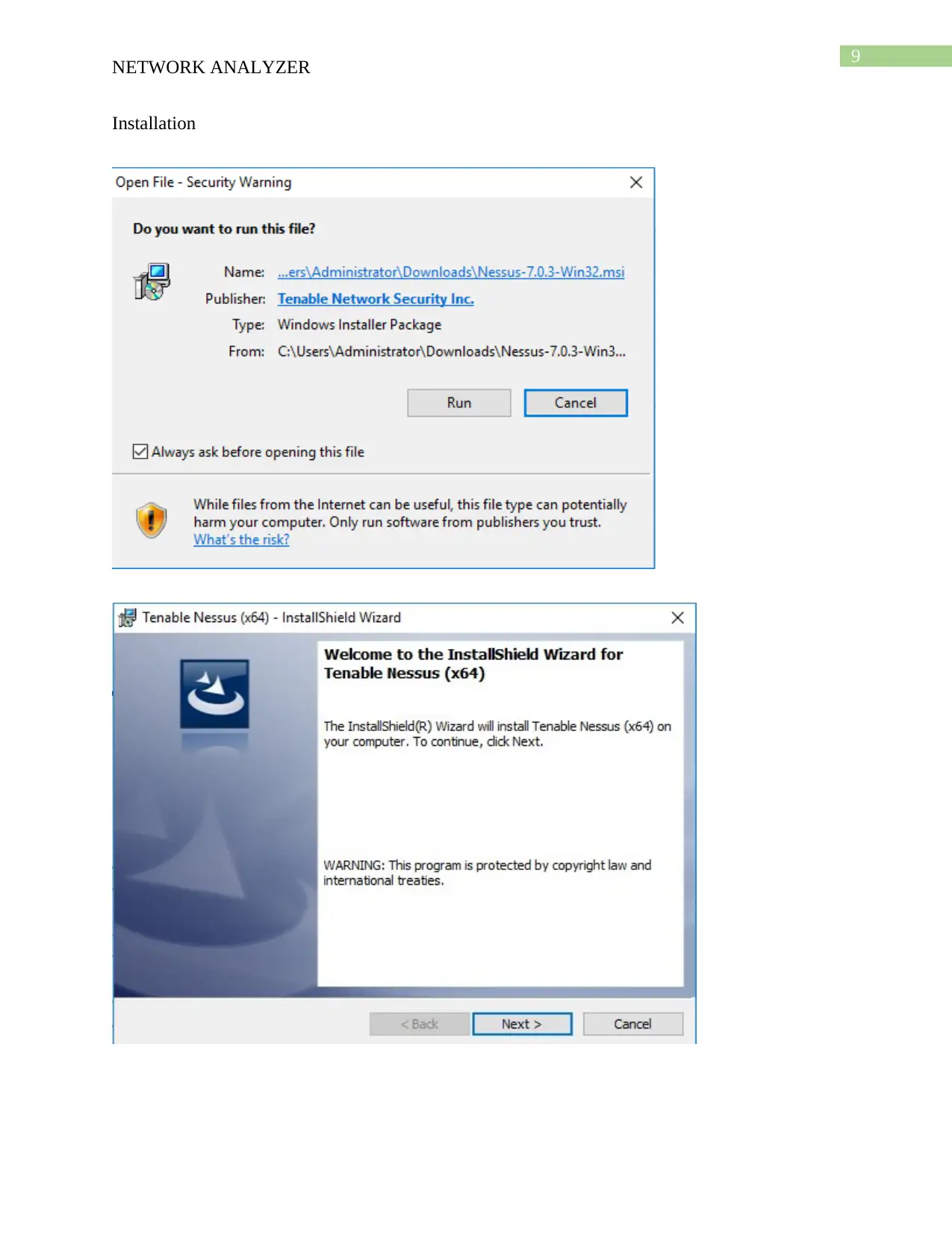
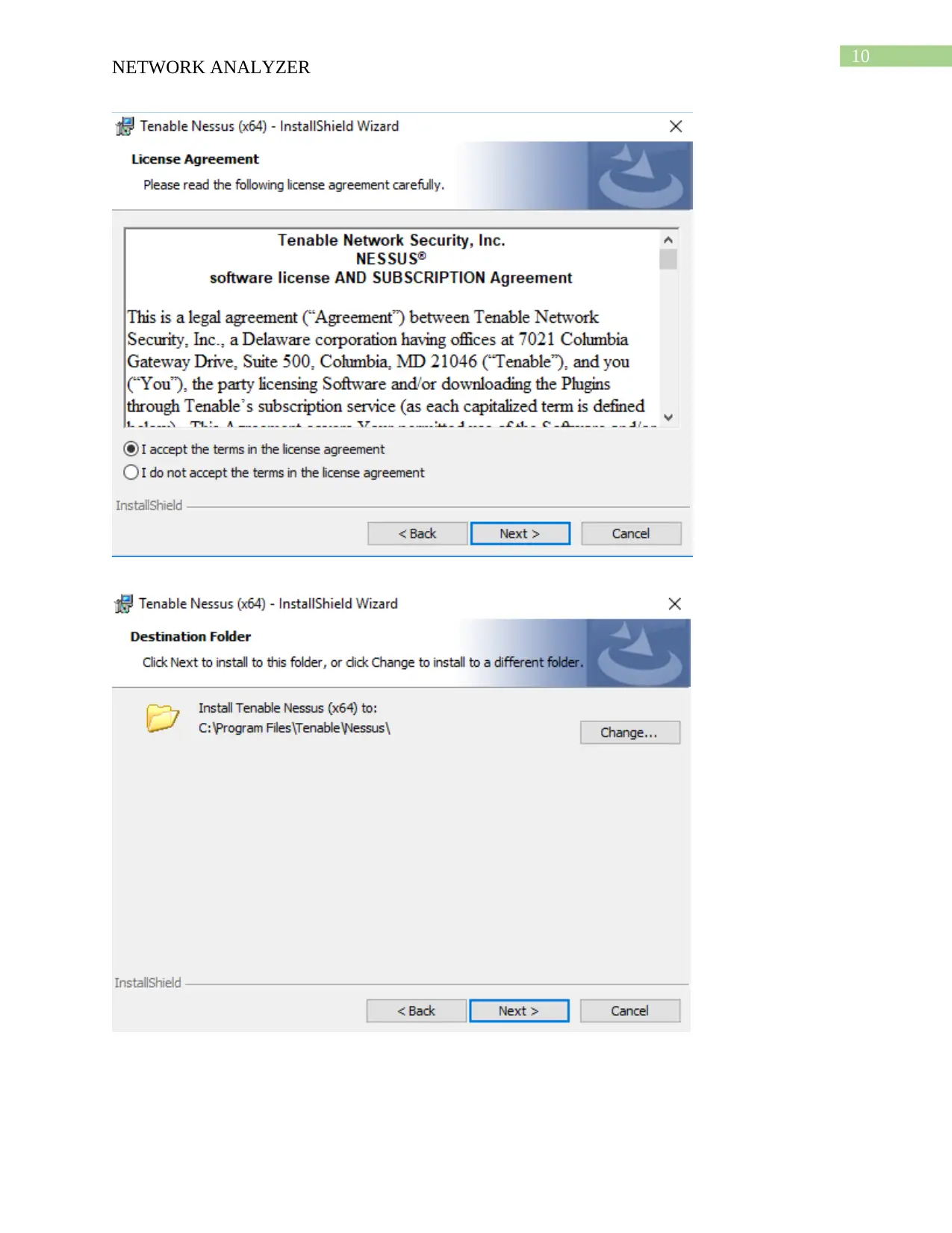
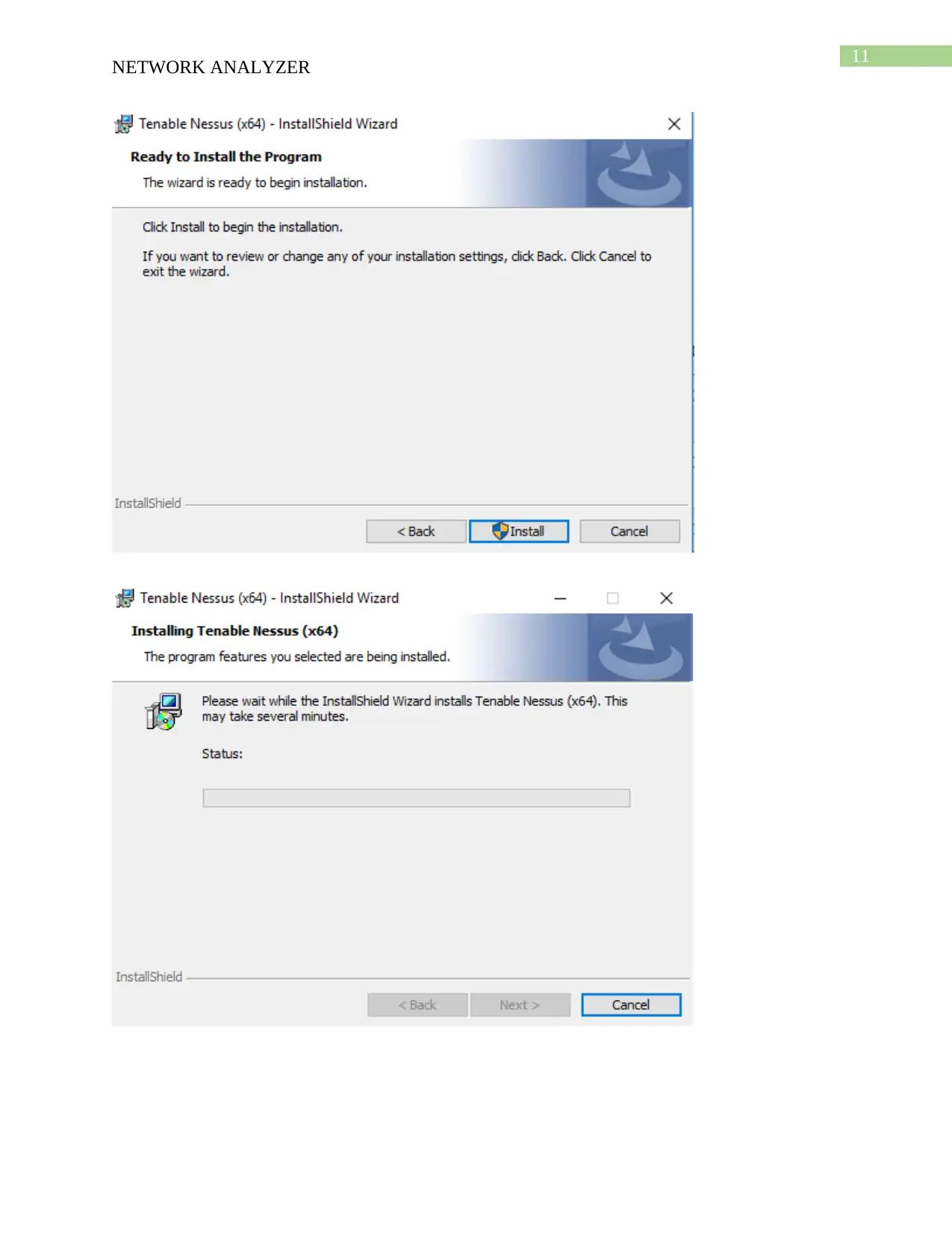
This report provides a comprehensive analysis of network security tools, specifically focusing on Nmap and Nessus. It begins with the download and installation processes of these tools, followed by detailed descriptions of their functionalities. Nmap is presented as a network mapper that aids in network analysis and security assessment, while Nessus is highlighted as a vulnerability detection tool. The report includes a demonstration of how each tool is used, comparing their strengths and weaknesses, such as Nmap's speed and broad scanning capabilities versus Nessus's ease of access and in-depth vulnerability checks. Furthermore, the report analyzes a case study involving an educational institute with a BYOD (Bring Your Own Device) policy, recommending Nessus as a suitable tool to enhance the organization's network security. The report concludes with a bibliography of relevant sources.
1 out of 22








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)