Network Security Report for BIT243: Security Techniques and Processes
VerifiedAdded on 2023/01/19
|11
|718
|27
Report
AI Summary
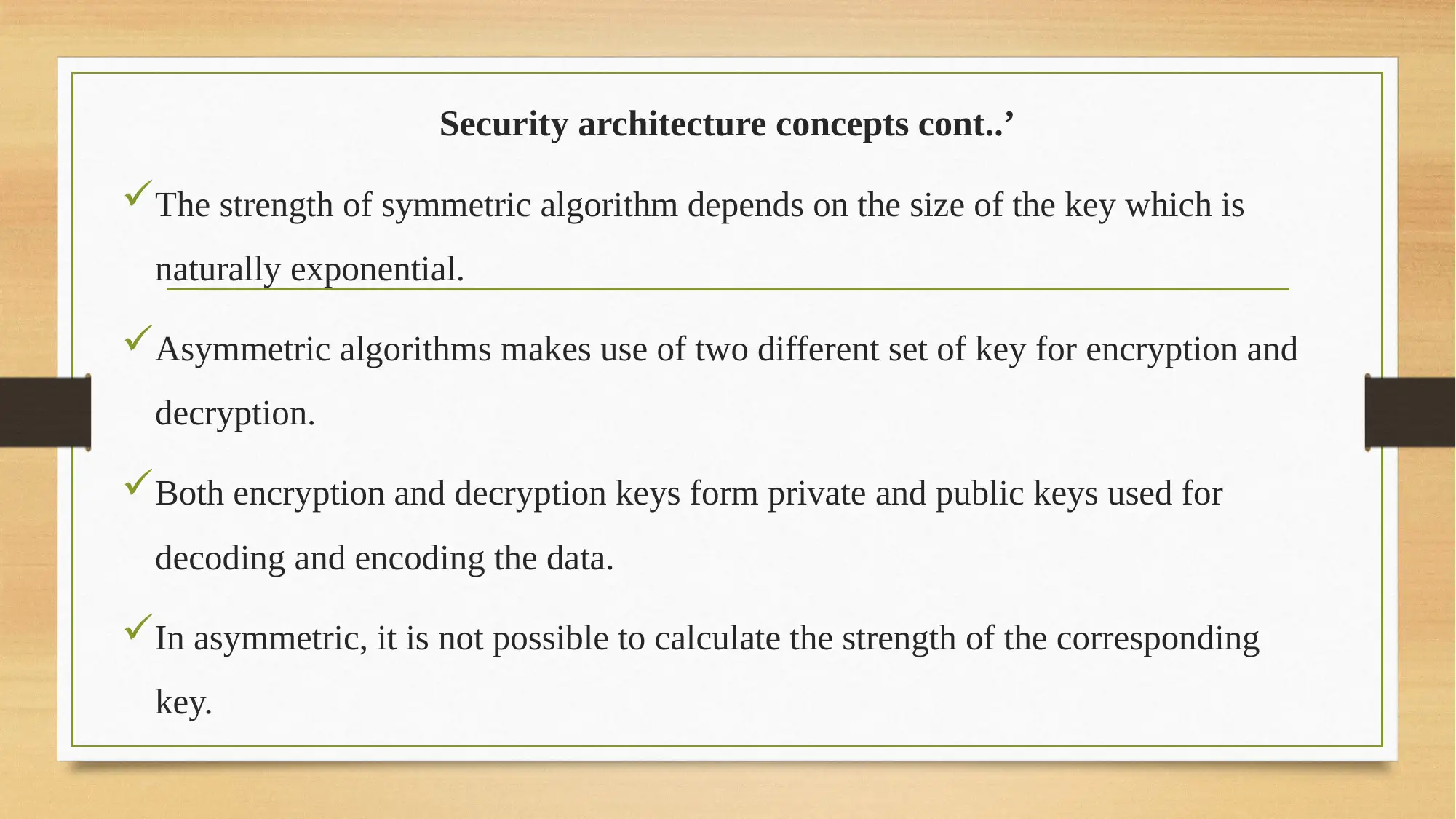
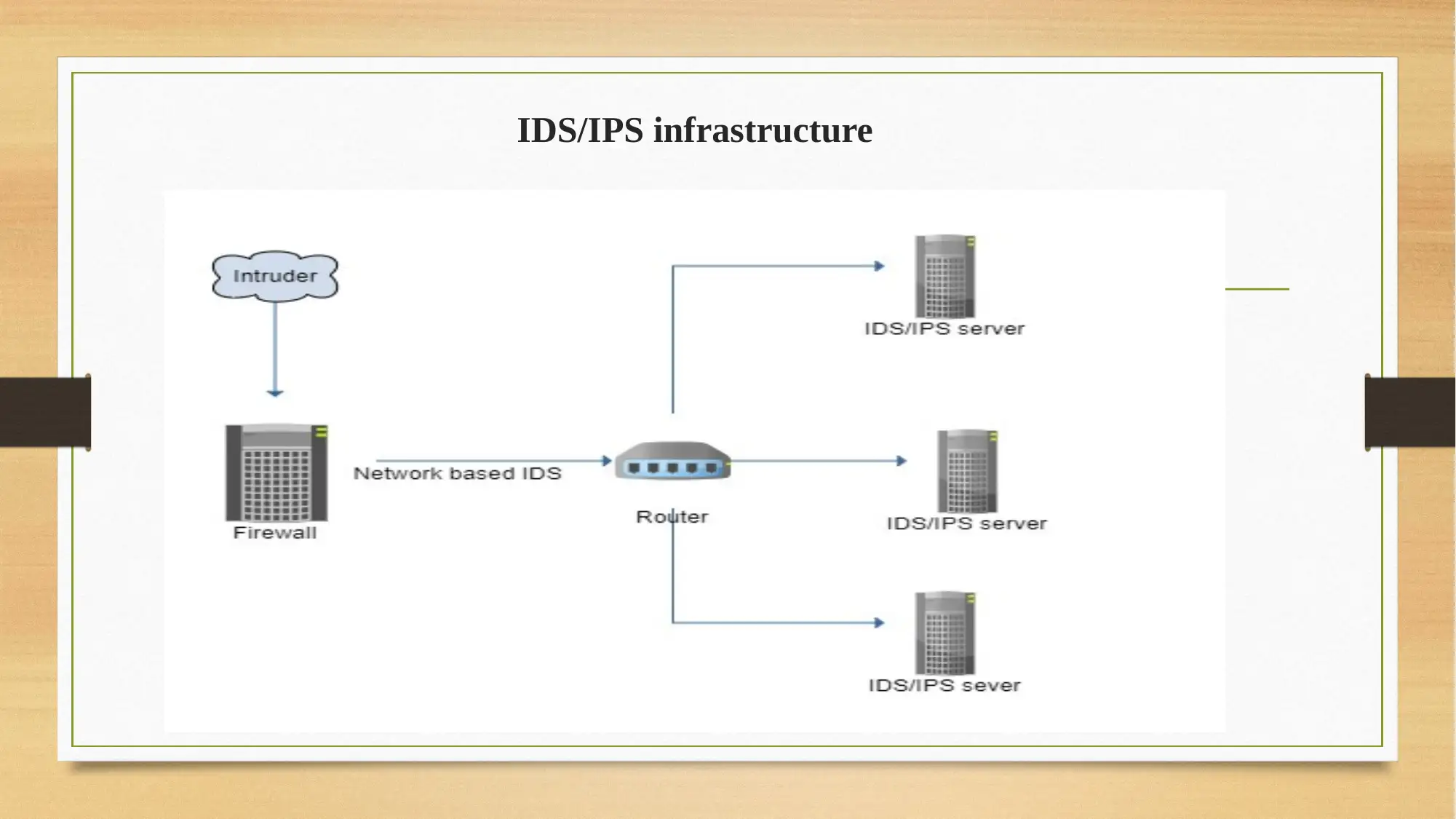
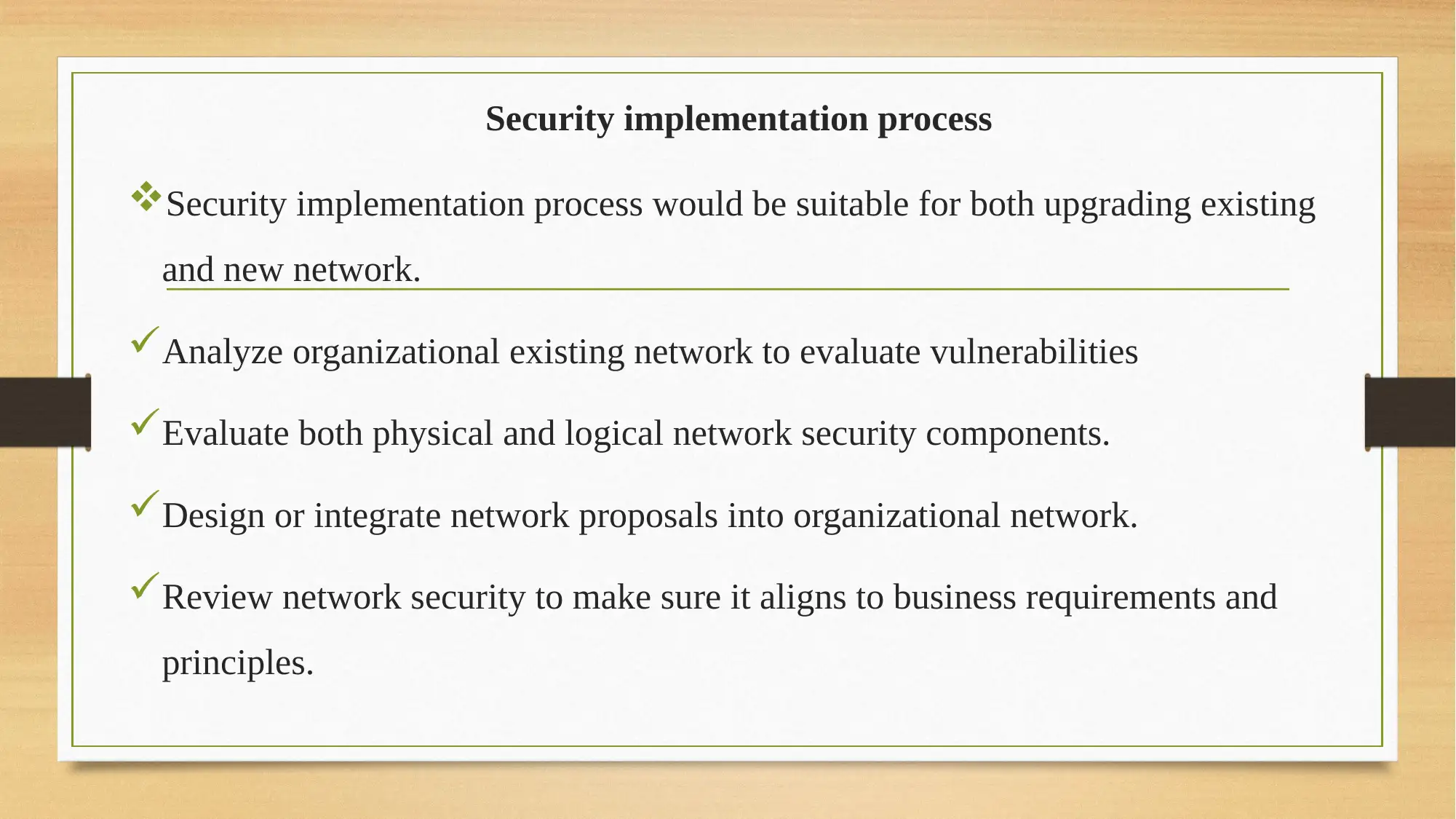
This report provides a comprehensive overview of network security, focusing on security architecture and its components. It delves into the importance of cryptography, including symmetric and asymmetric algorithms, and their role in ensuring data integrity, confidentiality, authentication, and authorization. The report also examines Intrusion Detection and Prevention Systems (IDS and IPS), highlighting their functionalities and the security implementation process. Furthermore, it explores effective security techniques like digital signatures, network authentication, access controls, and identity management. The conclusion emphasizes the ongoing challenges in network security and the significance of implementing these techniques to safeguard organizational data. The report is a solution for the BIT243 Network Security assignment, offering insights into designing and implementing security measures to reduce cyber-attacks and improve system security.
1 out of 11














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)