COIT20262 Advanced Network Security Assignment 1 Submission Term 2
VerifiedAdded on 2022/09/15
|9
|2573
|41
Homework Assignment
AI Summary
This document presents a comprehensive solution to Assignment 1 for COIT20262, Advanced Network Security, Term 2, 2019. The assignment delves into packet capture and analysis, exploring TCP handshakes, and extracting information from netcat and scp packets. It examines the differences between netcat and scp, including their functionalities and operational speeds. The solution also covers cryptography, detailing the importance of various cryptographic algorithms such as MD5 and ChaCha20, and their applications. It discusses potential security threats such as masquerade attacks, and methods to mitigate them. The assignment further explores ransomware, its infection methods, and the role of cryptography in these attacks. The solution provides insights into the non-payment of ransoms and the strategies that can be adopted to recover from ransomware attacks. The assignment covers key concepts in network security, cryptography, and malware research.
COIT20262 Assignment 1 Submission Term 2, 2019
COIT20262 - Advanced Network Security, Term 2, 2019
Assignment 1 Submission
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: 12078486
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 9
COIT20262 - Advanced Network Security, Term 2, 2019
Assignment 1 Submission
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: 12078486
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 2, 2019
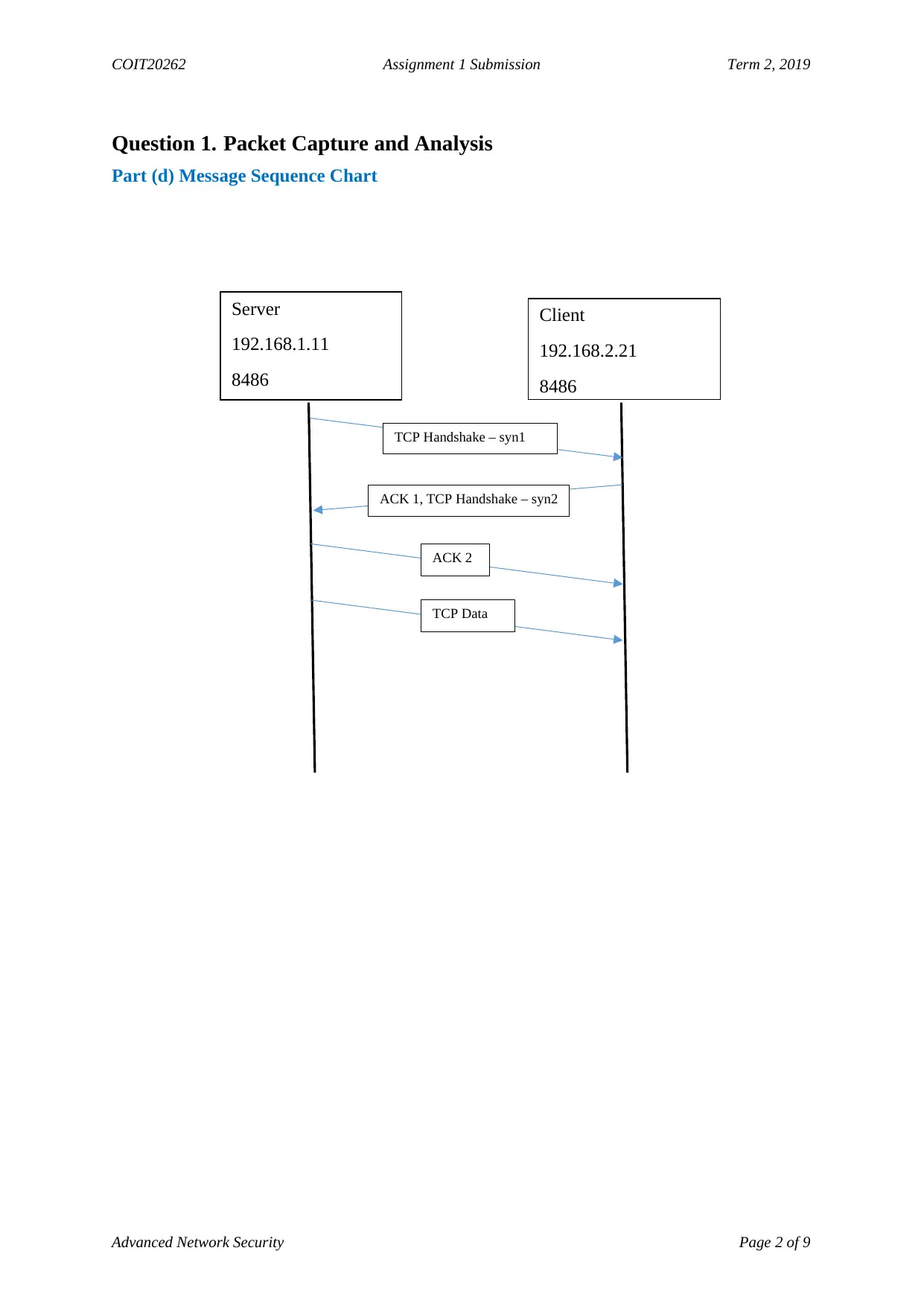
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Advanced Network Security Page 2 of 9
Server
192.168.1.11
8486
Client
192.168.2.21
8486
TCP Handshake – syn1
ACK 1, TCP Handshake – syn2
ACK 2
TCP Data
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Advanced Network Security Page 2 of 9
Server
192.168.1.11
8486
Client
192.168.2.21
8486
TCP Handshake – syn1
ACK 1, TCP Handshake – syn2
ACK 2
TCP Data
COIT20262 Assignment 1 Submission Term 2, 2019
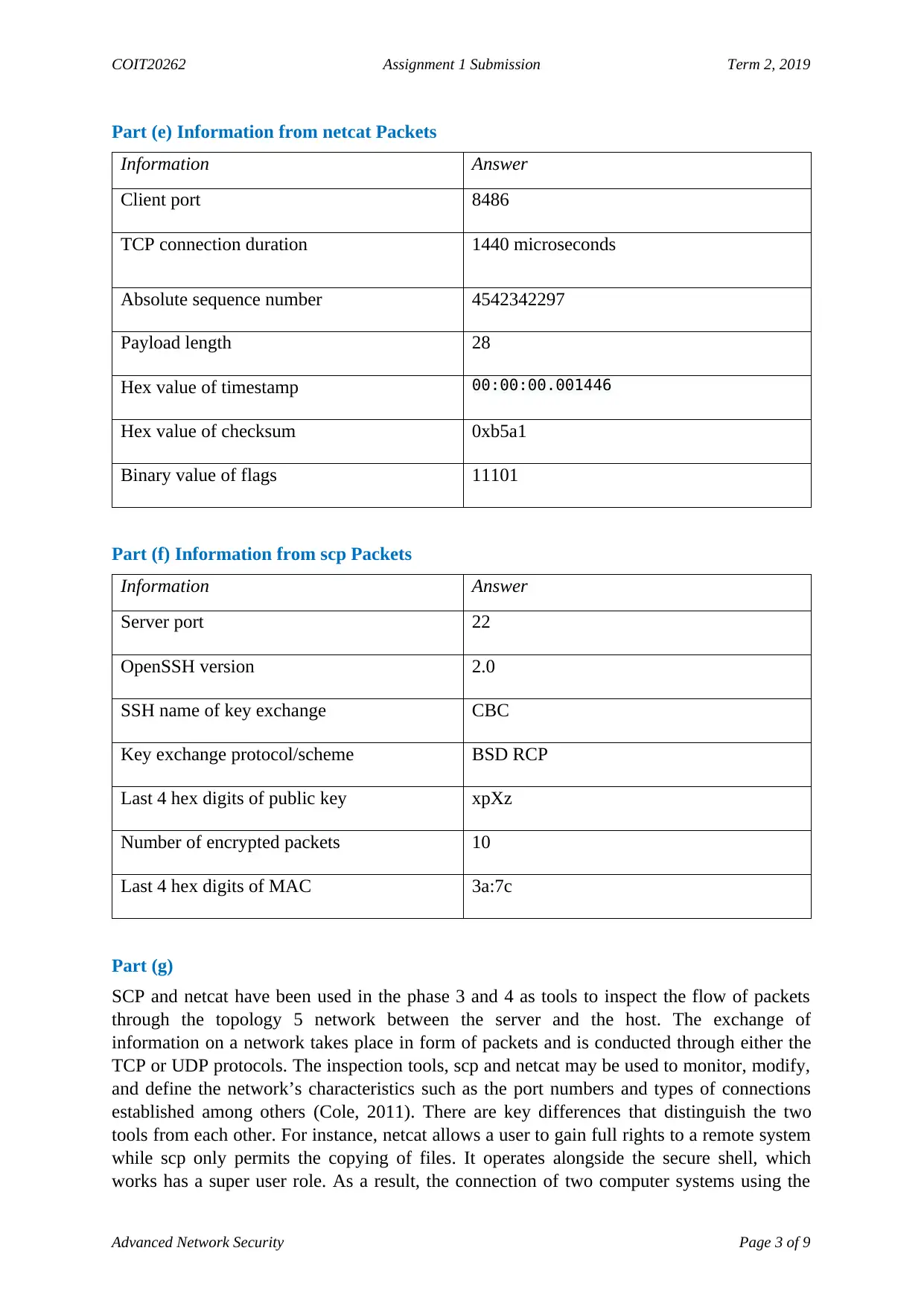
Part (e) Information from netcat Packets
Information Answer
Client port 8486
TCP connection duration 1440 microseconds
Absolute sequence number 4542342297
Payload length 28
Hex value of timestamp 00:00:00.001446
Hex value of checksum 0xb5a1
Binary value of flags 11101
Part (f) Information from scp Packets
Information Answer
Server port 22
OpenSSH version 2.0
SSH name of key exchange CBC
Key exchange protocol/scheme BSD RCP
Last 4 hex digits of public key xpXz
Number of encrypted packets 10
Last 4 hex digits of MAC 3a:7c
Part (g)
SCP and netcat have been used in the phase 3 and 4 as tools to inspect the flow of packets
through the topology 5 network between the server and the host. The exchange of
information on a network takes place in form of packets and is conducted through either the
TCP or UDP protocols. The inspection tools, scp and netcat may be used to monitor, modify,
and define the network’s characteristics such as the port numbers and types of connections
established among others (Cole, 2011). There are key differences that distinguish the two
tools from each other. For instance, netcat allows a user to gain full rights to a remote system
while scp only permits the copying of files. It operates alongside the secure shell, which
works has a super user role. As a result, the connection of two computer systems using the
Advanced Network Security Page 3 of 9
Part (e) Information from netcat Packets
Information Answer
Client port 8486
TCP connection duration 1440 microseconds
Absolute sequence number 4542342297
Payload length 28
Hex value of timestamp 00:00:00.001446
Hex value of checksum 0xb5a1
Binary value of flags 11101
Part (f) Information from scp Packets
Information Answer
Server port 22
OpenSSH version 2.0
SSH name of key exchange CBC
Key exchange protocol/scheme BSD RCP
Last 4 hex digits of public key xpXz
Number of encrypted packets 10
Last 4 hex digits of MAC 3a:7c
Part (g)
SCP and netcat have been used in the phase 3 and 4 as tools to inspect the flow of packets
through the topology 5 network between the server and the host. The exchange of
information on a network takes place in form of packets and is conducted through either the
TCP or UDP protocols. The inspection tools, scp and netcat may be used to monitor, modify,
and define the network’s characteristics such as the port numbers and types of connections
established among others (Cole, 2011). There are key differences that distinguish the two
tools from each other. For instance, netcat allows a user to gain full rights to a remote system
while scp only permits the copying of files. It operates alongside the secure shell, which
works has a super user role. As a result, the connection of two computer systems using the
Advanced Network Security Page 3 of 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 2, 2019
scp is enabled using a ssh credentials. Netcat, on the other hand, allows for full control of a
computer by a person operating on a remote location. For instance, if desired, a network
administrator may utilize super user facilities such as the bash terminal to write scripts that
could alter the functionality of the whole computer system, install and uninstall software,
transfer files, and even delete and modify files. The two tools have distinct ways of operation
(Cole, 2011). Due to the level of access that a remote user is granted, the netcat manages a
greater number of packets compared to scp.
The functionality also dictates the speeds of the two tools with regards to the transfer. While
the netcat oversees a larger number of packet transfer, it is faster because it operates
independently on the core operating system (Vacca, 2009). On the other hand, scp is a slower
FTP-type transfer tool that operates on top of a the secure shell, and requires that all
communication pass through the SSH layers. As a result, it is slower with regards to the
transfer of files.
Part (h)
The ChaCha20 is an encryption standard that offers an improved interface and utility over the
AES encryption algorithm. It is preferred in modern communication platforms that oversee
the transfer of files between continents, regions, and in short-distance communications on
smaller devices (Clarke, 2012). Examples of everyday tools that utilize this encryption
standard is the Google’s Chrome web browser and Cloudflare, a platform that enables cloud-
based content deliver as a service for entertainment providers. ChaCha20 is fast on computers
with minimal hardware and processing capabilities (Cole, 2011). AES, on the other hand,
requires an investment in the hardware for better speeds. Therefore, encryption and
decryption of content on various devices is better protected by ChaCha20. AES, which is also
highly secure, is utilized majorly on unix systems that run fully-fledged servers.
Advanced Network Security Page 4 of 9
scp is enabled using a ssh credentials. Netcat, on the other hand, allows for full control of a
computer by a person operating on a remote location. For instance, if desired, a network
administrator may utilize super user facilities such as the bash terminal to write scripts that
could alter the functionality of the whole computer system, install and uninstall software,
transfer files, and even delete and modify files. The two tools have distinct ways of operation
(Cole, 2011). Due to the level of access that a remote user is granted, the netcat manages a
greater number of packets compared to scp.
The functionality also dictates the speeds of the two tools with regards to the transfer. While
the netcat oversees a larger number of packet transfer, it is faster because it operates
independently on the core operating system (Vacca, 2009). On the other hand, scp is a slower
FTP-type transfer tool that operates on top of a the secure shell, and requires that all
communication pass through the SSH layers. As a result, it is slower with regards to the
transfer of files.
Part (h)
The ChaCha20 is an encryption standard that offers an improved interface and utility over the
AES encryption algorithm. It is preferred in modern communication platforms that oversee
the transfer of files between continents, regions, and in short-distance communications on
smaller devices (Clarke, 2012). Examples of everyday tools that utilize this encryption
standard is the Google’s Chrome web browser and Cloudflare, a platform that enables cloud-
based content deliver as a service for entertainment providers. ChaCha20 is fast on computers
with minimal hardware and processing capabilities (Cole, 2011). AES, on the other hand,
requires an investment in the hardware for better speeds. Therefore, encryption and
decryption of content on various devices is better protected by ChaCha20. AES, which is also
highly secure, is utilized majorly on unix systems that run fully-fledged servers.
Advanced Network Security Page 4 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 1 Submission Term 2, 2019
Question 1. Cryptography
Part (c)
Cryptography is a practice that has been going on since the ages of the Roman empire where
certain methods of secrecy were involved in the transfer of money. The second world war
oversaw a spiked interest in the development of modern cryptographic algorithms and code-
breaking mechanisms that have been famed through time (Cole, 2011). The interest in the
field has caused the development of many algorithms such as the symmetric, asymmetric, and
the hash algorithms. The use of each of these algorithms is based on the task at hand. Each of
them offers differing features of security features, availability, and integrity. The speed of
encryption is also an issue because it determines the amount of computation power required
to encrypt and decrypt messages, especially if the communication involves lengthy exchange
of information. A single message may involve different cryptographic approaches to securing
different parts, including a sequence of layerd encryption protocols. Such an exercise is
conducted to increase the level of confidentiality and integrity (Cole, 2011). A message can
only be decoded properly if the receiver has the right kinds of files, keys, and initialization
values. Moreover, symmetric and asymmetric keys may also be shared and used in specific
manners and procedures to enhance security of data.
Part (d)
The MD5, developed by Ronald Rivest, is a hashing algorithm that offers a one-way
encryption mechanism to produce a fixed length digest that authenticates a message. It is
used widely around the world to secure the communication between different networks and
computing platforms in the modern world. It can used as a standalone cryptographic method
or alongside other methods such as the RSA and the AES/DES algorithms (Vacca, 2009).
Despite its renowned usage, it has been proven to have numerous flaws that may take a short
time to decipher or corrupt if a hacker or attacker is skilled enough. The cipher block
produced in MD5 encryption is supposed to be unique for every extra character introduced
into a message and a number of other factors such as the salt and random key inclusion. The
biggest flaw in MD5 is that a hacker may sniff packets, break the code, alter the message, and
re-encrypt to produce a similar digest (Aumasson, 2017). The fact that two different
messages, or altered versions of the same messages produce a single digest indicates a
collision that may open up a system to further loss of integrity. Platforms written to handle
databases of big businesses may be compromised by the breakdown of confidentiality of their
digital certificates, which may validate malicious attacks that cause financial losses. Some of
the possible attacks include SQL injection that have been common in the use of unsecured
dynamic PHP based websites The loss of confidentiality caused by MD5 collisions could lead
to session stealing that results in the installation of ransomware on business or institutional
computing resources, thereby driving economic activities to a halt until a ransom is paid. Its
is capable of replacing AES and RSA algorithms but may be recommended for tasks that do
not involve highly sensitive information.
Part (e)
One of the possible attacks that a hacker may launch on a computing system is the
masquerade attack. It is passive in the sense that a system, if successfully spoofed, may treat
the reception of compromised packets as normal ones, thus allowing them to be accessed by
Advanced Network Security Page 5 of 9
Question 1. Cryptography
Part (c)
Cryptography is a practice that has been going on since the ages of the Roman empire where
certain methods of secrecy were involved in the transfer of money. The second world war
oversaw a spiked interest in the development of modern cryptographic algorithms and code-
breaking mechanisms that have been famed through time (Cole, 2011). The interest in the
field has caused the development of many algorithms such as the symmetric, asymmetric, and
the hash algorithms. The use of each of these algorithms is based on the task at hand. Each of
them offers differing features of security features, availability, and integrity. The speed of
encryption is also an issue because it determines the amount of computation power required
to encrypt and decrypt messages, especially if the communication involves lengthy exchange
of information. A single message may involve different cryptographic approaches to securing
different parts, including a sequence of layerd encryption protocols. Such an exercise is
conducted to increase the level of confidentiality and integrity (Cole, 2011). A message can
only be decoded properly if the receiver has the right kinds of files, keys, and initialization
values. Moreover, symmetric and asymmetric keys may also be shared and used in specific
manners and procedures to enhance security of data.
Part (d)
The MD5, developed by Ronald Rivest, is a hashing algorithm that offers a one-way
encryption mechanism to produce a fixed length digest that authenticates a message. It is
used widely around the world to secure the communication between different networks and
computing platforms in the modern world. It can used as a standalone cryptographic method
or alongside other methods such as the RSA and the AES/DES algorithms (Vacca, 2009).
Despite its renowned usage, it has been proven to have numerous flaws that may take a short
time to decipher or corrupt if a hacker or attacker is skilled enough. The cipher block
produced in MD5 encryption is supposed to be unique for every extra character introduced
into a message and a number of other factors such as the salt and random key inclusion. The
biggest flaw in MD5 is that a hacker may sniff packets, break the code, alter the message, and
re-encrypt to produce a similar digest (Aumasson, 2017). The fact that two different
messages, or altered versions of the same messages produce a single digest indicates a
collision that may open up a system to further loss of integrity. Platforms written to handle
databases of big businesses may be compromised by the breakdown of confidentiality of their
digital certificates, which may validate malicious attacks that cause financial losses. Some of
the possible attacks include SQL injection that have been common in the use of unsecured
dynamic PHP based websites The loss of confidentiality caused by MD5 collisions could lead
to session stealing that results in the installation of ransomware on business or institutional
computing resources, thereby driving economic activities to a halt until a ransom is paid. Its
is capable of replacing AES and RSA algorithms but may be recommended for tasks that do
not involve highly sensitive information.
Part (e)
One of the possible attacks that a hacker may launch on a computing system is the
masquerade attack. It is passive in the sense that a system, if successfully spoofed, may treat
the reception of compromised packets as normal ones, thus allowing them to be accessed by
Advanced Network Security Page 5 of 9

COIT20262 Assignment 1 Submission Term 2, 2019
the receiver (Nestler, et al., 2014). It is characterised by the re-sending of delayed packets to a
recipient, for any reason that a hacker may have. Attackers intending to cripple a business or
overload the servers in a bid to force malicious software into the network may launch a DDoS
attack on a server or client system using masquerade attacks that reduce the availability of the
system or network. Masquerade attacks may also be used to test various variants of a
malware to determine open ports on a computer for possible exploitation. It could be
successful in the above described scheme because none of the systems described records the
timestamp as a parameter involved in encryption.
Part (f)
Masquerade attacks succeed in cases where a recipient of an attack is unable to determine
whether the packets being received are valid or invalid. The passing of the validity test of the
first packet due to its legitimacy as per the digital certificate enables the positive verification
of subsequent traffic of a similar description (Rankin, 2017). As described above, such
positively identified traffic may come from a spoofed IP address that dupes the system into
accepting communication and leading to DDoS attacks. The design of firewalls that filter the
contents of a network for the incoming and outgoing traffic could analyse the packets to
determine their nature and check the periodicity to prevent DDoS attacks. Moreover, an
intelligent firewall may escalate cases that may result in potential damage to the network or
the loss of integrity or confidentiality of the data and even determine the source of such
attacks. The utilization of timestamps in the determination of the encryption digests or keys
may be crucial as they can be read to check whether they were generated in a significantly
delayed time or matches the latency of the network. Such a level of analysis is only possible
with artificially intelligent networks.
Part (g)
An encryption algorithm that employs the use of a timestamp in the determination of the
digest or the seed are secure. They could be analysed before the unpacking of the packets to
determine whether the deciphered time header matches the latency of the network
Mismatched latency data results in failed decryption, which effectively protects the system
against communication with hackers (Cole, 2011). Moreover, the analysis may employ the
use of a firewall service alongside an antivirus that trigger the sandboxing of malicious
packets and evaluating for malicious code elements before entering the system. The non-
response and eventual block of compromised sources results in the effective prevention of
masquerade attacks.
Advanced Network Security Page 6 of 9
the receiver (Nestler, et al., 2014). It is characterised by the re-sending of delayed packets to a
recipient, for any reason that a hacker may have. Attackers intending to cripple a business or
overload the servers in a bid to force malicious software into the network may launch a DDoS
attack on a server or client system using masquerade attacks that reduce the availability of the
system or network. Masquerade attacks may also be used to test various variants of a
malware to determine open ports on a computer for possible exploitation. It could be
successful in the above described scheme because none of the systems described records the
timestamp as a parameter involved in encryption.
Part (f)
Masquerade attacks succeed in cases where a recipient of an attack is unable to determine
whether the packets being received are valid or invalid. The passing of the validity test of the
first packet due to its legitimacy as per the digital certificate enables the positive verification
of subsequent traffic of a similar description (Rankin, 2017). As described above, such
positively identified traffic may come from a spoofed IP address that dupes the system into
accepting communication and leading to DDoS attacks. The design of firewalls that filter the
contents of a network for the incoming and outgoing traffic could analyse the packets to
determine their nature and check the periodicity to prevent DDoS attacks. Moreover, an
intelligent firewall may escalate cases that may result in potential damage to the network or
the loss of integrity or confidentiality of the data and even determine the source of such
attacks. The utilization of timestamps in the determination of the encryption digests or keys
may be crucial as they can be read to check whether they were generated in a significantly
delayed time or matches the latency of the network. Such a level of analysis is only possible
with artificially intelligent networks.
Part (g)
An encryption algorithm that employs the use of a timestamp in the determination of the
digest or the seed are secure. They could be analysed before the unpacking of the packets to
determine whether the deciphered time header matches the latency of the network
Mismatched latency data results in failed decryption, which effectively protects the system
against communication with hackers (Cole, 2011). Moreover, the analysis may employ the
use of a firewall service alongside an antivirus that trigger the sandboxing of malicious
packets and evaluating for malicious code elements before entering the system. The non-
response and eventual block of compromised sources results in the effective prevention of
masquerade attacks.
Advanced Network Security Page 6 of 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 2, 2019
Question 2. Malware Research
What is ransomware?
A ransomware is a malicious attack by a hacker that encrypts all information on a computer
system and renders it unusable (Aumasson, 2017). Ransomware attacks are accompanied by
ransom demands that provide the exchange of an offer to restore the service in the case that
the terms are honoured.
Infection Methods
Ransomware attacks may be launched by various hacking methods that include social
engineering, session stealing, or spoofing of the IP addresses to cheat either human operators
or the machines into installing malicious programs. Once the programs are installed, they
begin encrypting the systems (Aumasson, 2017). An example of a way in which a computer
could be infected is through the reception of malicious emails that promise great rewards,
commonly called ‘clickbaits.’ Once a person opens them up, they may trigger background
downloads and installation of software embedded in images through steganography or other
methods. Pen drives may also carry malware from one computer to another (Vacca, 2009). A
successful encryption of files is followed by the message indicating terms of the ransom for
service restoration.
Role of Cryptography
Ransom attacks cannot work without cryptography. AES, DES, and RSA algorithms may be
used in the process of encrypting the systems to deny the authenticated users access. Methods
in which such mechanisms could be conducted include the client-based attacks, client-server
models, or the hybrid model (Vacca, 2009). In a client-based attack, the encryption takes
place on a target computer and the files are stored in a location locally. In the client-server
model, the encryption takes place locally on a target computer but the keys are uploaded to an
attacker’s server. The hybrid system utilizes both mechanisms (Liska & Gallo, 2016). It is
more sophisticated and requires a significant level of technical expertise to execute the hybrid
attack.
Not Pay Ransom
The university can decide to refuse to honour the ransom requests if it maintains a team of
network security engineers with a high level of expertise. They can work to restore the
network without economic sabotage. Another scenario is one in which the systems attacked
are non-crucial and can be cleaned and new software installed. A third scenario of non-
payment is one in which a comprehensive contingency plan has been setup in preparation of
such occurrences and backups can be deployed in a load-balanced manner to proceed with
normal business operations.
Pay Ransom
If the university does not meet the three scenarios mentioned above, then resorting to
honouring the ransom agreement may be a possibly sound decision. Modern hackers prefer
the use of cryptocurrency or shipment of valuable items to desired locations for the exchange
of decryption services.
Advanced Network Security Page 7 of 9
Question 2. Malware Research
What is ransomware?
A ransomware is a malicious attack by a hacker that encrypts all information on a computer
system and renders it unusable (Aumasson, 2017). Ransomware attacks are accompanied by
ransom demands that provide the exchange of an offer to restore the service in the case that
the terms are honoured.
Infection Methods
Ransomware attacks may be launched by various hacking methods that include social
engineering, session stealing, or spoofing of the IP addresses to cheat either human operators
or the machines into installing malicious programs. Once the programs are installed, they
begin encrypting the systems (Aumasson, 2017). An example of a way in which a computer
could be infected is through the reception of malicious emails that promise great rewards,
commonly called ‘clickbaits.’ Once a person opens them up, they may trigger background
downloads and installation of software embedded in images through steganography or other
methods. Pen drives may also carry malware from one computer to another (Vacca, 2009). A
successful encryption of files is followed by the message indicating terms of the ransom for
service restoration.
Role of Cryptography
Ransom attacks cannot work without cryptography. AES, DES, and RSA algorithms may be
used in the process of encrypting the systems to deny the authenticated users access. Methods
in which such mechanisms could be conducted include the client-based attacks, client-server
models, or the hybrid model (Vacca, 2009). In a client-based attack, the encryption takes
place on a target computer and the files are stored in a location locally. In the client-server
model, the encryption takes place locally on a target computer but the keys are uploaded to an
attacker’s server. The hybrid system utilizes both mechanisms (Liska & Gallo, 2016). It is
more sophisticated and requires a significant level of technical expertise to execute the hybrid
attack.
Not Pay Ransom
The university can decide to refuse to honour the ransom requests if it maintains a team of
network security engineers with a high level of expertise. They can work to restore the
network without economic sabotage. Another scenario is one in which the systems attacked
are non-crucial and can be cleaned and new software installed. A third scenario of non-
payment is one in which a comprehensive contingency plan has been setup in preparation of
such occurrences and backups can be deployed in a load-balanced manner to proceed with
normal business operations.
Pay Ransom
If the university does not meet the three scenarios mentioned above, then resorting to
honouring the ransom agreement may be a possibly sound decision. Modern hackers prefer
the use of cryptocurrency or shipment of valuable items to desired locations for the exchange
of decryption services.
Advanced Network Security Page 7 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 1 Submission Term 2, 2019
Recommendations
In the process of the design of a university network, it is recommended that a university or a
similar entity establish contingency plans of network outages that cause the loss of
availability, confidentiality, or integrity of the systems (Liska & Gallo, 2016). Policy
definitions of ways to operate devices at the premises or the instruction to update software on
every computer frequently could prevent ransomware attacks. The use of intelligent firewall
and antivirus software is also a good preventive mechanism.
Advanced Network Security Page 8 of 9
Recommendations
In the process of the design of a university network, it is recommended that a university or a
similar entity establish contingency plans of network outages that cause the loss of
availability, confidentiality, or integrity of the systems (Liska & Gallo, 2016). Policy
definitions of ways to operate devices at the premises or the instruction to update software on
every computer frequently could prevent ransomware attacks. The use of intelligent firewall
and antivirus software is also a good preventive mechanism.
Advanced Network Security Page 8 of 9

COIT20262 Assignment 1 Submission Term 2, 2019
References
Aumasson, J.-P., 2017. Serious Cryptography: A Practical Introduction to Modern
Encryption. s.l.:No Starch Press.
Clarke, J., 2012. SQL Injection Attacks and Defense. s.l.:Elsevier.
Cole, E., 2011. Network Security Bible. John Wiley & Sons: s.n.
Liska, A. & Gallo, T., 2016. Ransomware: Defending Against Digital Extortion. s.l.:O'Reilly
Media, Inc.
Nestler, V. J., Harrison, K., Hirsch, M. P. & Conklin, W. A., 2014. Principles of Computer
Security Lab Manual, Fourth Edition. s.l.:McGraw Hill Professional.
Rankin, K., 2017. Linux Hardening in Hostile Networks: Server Security from TLS to Tor.
s.l.:Professional, Addison-Wesley.
Vacca, J. R., 2009. Computer and Information Security Handbook. s.l.:Morgan Kaufmann.
Advanced Network Security Page 9 of 9
References
Aumasson, J.-P., 2017. Serious Cryptography: A Practical Introduction to Modern
Encryption. s.l.:No Starch Press.
Clarke, J., 2012. SQL Injection Attacks and Defense. s.l.:Elsevier.
Cole, E., 2011. Network Security Bible. John Wiley & Sons: s.n.
Liska, A. & Gallo, T., 2016. Ransomware: Defending Against Digital Extortion. s.l.:O'Reilly
Media, Inc.
Nestler, V. J., Harrison, K., Hirsch, M. P. & Conklin, W. A., 2014. Principles of Computer
Security Lab Manual, Fourth Edition. s.l.:McGraw Hill Professional.
Rankin, K., 2017. Linux Hardening in Hostile Networks: Server Security from TLS to Tor.
s.l.:Professional, Addison-Wesley.
Vacca, J. R., 2009. Computer and Information Security Handbook. s.l.:Morgan Kaufmann.
Advanced Network Security Page 9 of 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




