CP2414 Network Security Assignment 1: Threats, Design, and Mitigation
VerifiedAdded on 2022/12/29
|5
|1141
|66
Homework Assignment
AI Summary
This assignment solution addresses network security threats and designs a secure network for iCreative, an Australian advertising company. Part I analyzes client-side attacks (buffer overflow) and network-based attacks (DoS, drive-by downloads). Recommendations include keeping software up-to-date, installing web filtering and spam filters, and implementing user rights restrictions and anti-spoofing measures. Part II focuses on the Brisbane branch, proposing a secure network diagram with an internal and external router, switches, honeypots (to attract attackers), and firewalls (internal and external) to protect the network. The honeypots are strategically placed to attract attackers and gather information. The firewalls filter incoming and outgoing data, with the internal firewall offering stricter filtering. The solution includes a detailed explanation of the network configuration and justifications for the chosen security technologies.

Assignment 1
Network Security
Part I. Potential Threats
Threats
Complaints 1, 2 and 5 describe the client-side attack. Client applications are the target
vulnerabilities. The running slow and crashing of the computer is caused by the excessive
attacks through the use of the buffer overflow vulnerability. A compromised server is
invaded by a malicious application during their interaction. Data is stored in CPU, RAM,
memory and as a result the size of the buffer is exceeded. This leads to lack of space as
most of the computer resources are filled. Due to this, the computer easily gets crashed
and runs slow and low memory space is available.1
Complaints 3, 4, 6, 7 involve networking-based attacks that target the network. From the
description provided by the employees, it’s evident that there are too many data requests
in the remote server. Denial of service attack prevents the network from offering the
normal services. The attacks occur on the network bandwidth and connection spots. This
attack leads to malfunctioning of the website. Additionally, a drive-by download program
automatically downloads files to the users’ computers without authorization from the
user. This leads to a slow speed of downloading or accessing the network since the
network resources are used up.2
Recommendation
The common preventive measure is to always keep the company software up to date.
Installation of the web filtering software that keeps users from accessing sites infected by
drive-by download attacks.
Users’ rights restrictions can also be implemented in order to restrict the level of damage
in case a user accidentally downloads a malicious software.
1 Martial Carrie and James Wilshire, "Virtual extension of buffer to reduce buffer overflow
during tracing." U.S. Patent 8,612,650, issued December 17, 2013.
2 Rutvij Jhaveri, Sankita Patel and Devesh Jinwala, "DoS attacks in mobile ad hoc networks: A
survey." In 2012 second international conference on advanced computing & communication
technologies, pp. 535-541. IEEE, 2012.
Network Security
Part I. Potential Threats
Threats
Complaints 1, 2 and 5 describe the client-side attack. Client applications are the target
vulnerabilities. The running slow and crashing of the computer is caused by the excessive
attacks through the use of the buffer overflow vulnerability. A compromised server is
invaded by a malicious application during their interaction. Data is stored in CPU, RAM,
memory and as a result the size of the buffer is exceeded. This leads to lack of space as
most of the computer resources are filled. Due to this, the computer easily gets crashed
and runs slow and low memory space is available.1
Complaints 3, 4, 6, 7 involve networking-based attacks that target the network. From the
description provided by the employees, it’s evident that there are too many data requests
in the remote server. Denial of service attack prevents the network from offering the
normal services. The attacks occur on the network bandwidth and connection spots. This
attack leads to malfunctioning of the website. Additionally, a drive-by download program
automatically downloads files to the users’ computers without authorization from the
user. This leads to a slow speed of downloading or accessing the network since the
network resources are used up.2
Recommendation
The common preventive measure is to always keep the company software up to date.
Installation of the web filtering software that keeps users from accessing sites infected by
drive-by download attacks.
Users’ rights restrictions can also be implemented in order to restrict the level of damage
in case a user accidentally downloads a malicious software.
1 Martial Carrie and James Wilshire, "Virtual extension of buffer to reduce buffer overflow
during tracing." U.S. Patent 8,612,650, issued December 17, 2013.
2 Rutvij Jhaveri, Sankita Patel and Devesh Jinwala, "DoS attacks in mobile ad hoc networks: A
survey." In 2012 second international conference on advanced computing & communication
technologies, pp. 535-541. IEEE, 2012.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Installation of a spam filter on the other hand can be use in detection of unwanted and
unverified emails and prevent entry to the user’s inbox.
Denial of service attack can be prevented by use of anti-spoofing. It verifies the accuracy
of the port, packet address and carry out reverse detection.
Part II. Firewall, Honeypot/s, and Other Network Security Technologies Planning and
Design for Brisbane Branch
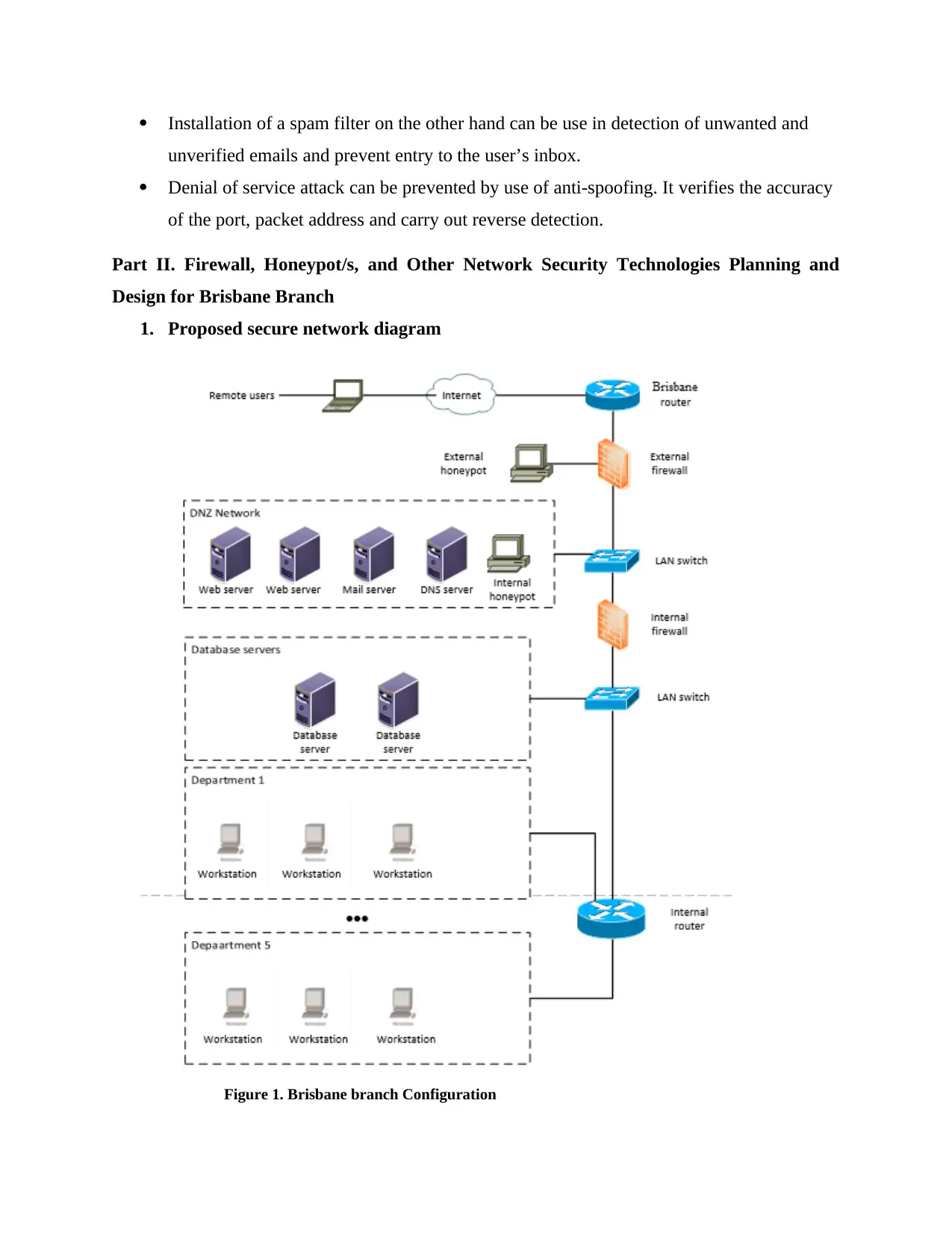
1. Proposed secure network diagram
Figure 1. Brisbane branch Configuration
unverified emails and prevent entry to the user’s inbox.
Denial of service attack can be prevented by use of anti-spoofing. It verifies the accuracy
of the port, packet address and carry out reverse detection.
Part II. Firewall, Honeypot/s, and Other Network Security Technologies Planning and
Design for Brisbane Branch
1. Proposed secure network diagram
Figure 1. Brisbane branch Configuration

2. Configuration diagram explanation and justification
a. Routers
A router generally connects all WANs and LANs in the network. I propose setting up
of two parts of the router; internal router and the external router. From the description
provided, the company is a medium-sized company with about 25 employees in each of
its 5 departments. As a result, the company requires only a few deployments which suits
the two routers. Their design set-up not only improves the network security through
protection of the internal network, it also assures smooth running of the external network
b. Switches
LAN switches are set up between each LAN. They are able to receive, process and
forward data packets through packet switching to the targeted device which is the device
connected on the computer network.
c. Honeypot
This is a system that is used to distract attackers from attacking vital systems. The
system gathers information regarding the activities of the attacker and ensures that the
attacker is kept on the system until the administrator responds to the attack.
The position of the honeypot therefore should be placed in such a way that it connects
with the external firewall in order to attract attackers. Once a successful attack has been
carried out, the administrator will be able to investigate how it was carried out in in order
to stay alert regarding the latest vulnerabilities and attacks against the server.
This setup however does not cover internal attacks. In order to prevent that, another
honeypot is deployed in the DMZ for the company to be able to counter attack an internal
attack.3
d. Firewall
The firewall setup is divided into network and computer firewall, that is, internal and
external firewall. The external firewall links the network between LAN and WAN while
the internal firewall links the internal network in order to protect it. The internal firewall
detects destination address, protocol and the network layer of the information coming in
3 Ping Wang, Lei Wu, Ryan Cunningham, and Cliff Zou, “Honeypot detection in advanced
botnet attacks." International Journal of Information and Computer Security 4, no. 1 (2010): 30-
51.
a. Routers
A router generally connects all WANs and LANs in the network. I propose setting up
of two parts of the router; internal router and the external router. From the description
provided, the company is a medium-sized company with about 25 employees in each of
its 5 departments. As a result, the company requires only a few deployments which suits
the two routers. Their design set-up not only improves the network security through
protection of the internal network, it also assures smooth running of the external network
b. Switches
LAN switches are set up between each LAN. They are able to receive, process and
forward data packets through packet switching to the targeted device which is the device
connected on the computer network.
c. Honeypot
This is a system that is used to distract attackers from attacking vital systems. The
system gathers information regarding the activities of the attacker and ensures that the
attacker is kept on the system until the administrator responds to the attack.
The position of the honeypot therefore should be placed in such a way that it connects
with the external firewall in order to attract attackers. Once a successful attack has been
carried out, the administrator will be able to investigate how it was carried out in in order
to stay alert regarding the latest vulnerabilities and attacks against the server.
This setup however does not cover internal attacks. In order to prevent that, another
honeypot is deployed in the DMZ for the company to be able to counter attack an internal
attack.3
d. Firewall
The firewall setup is divided into network and computer firewall, that is, internal and
external firewall. The external firewall links the network between LAN and WAN while
the internal firewall links the internal network in order to protect it. The internal firewall
detects destination address, protocol and the network layer of the information coming in
3 Ping Wang, Lei Wu, Ryan Cunningham, and Cliff Zou, “Honeypot detection in advanced
botnet attacks." International Journal of Information and Computer Security 4, no. 1 (2010): 30-
51.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and the form of the application layer in order to filter out external information that does
not conform. When you compare both the external and internal firewall, the internal
firewall brings in stricter function of filtering so that it can protect the company’s
workstations and servers from external attacks. The DMZ is located between the internal
and external firewall since a portion of the data is given access to users which include
FTP servers, web server among others. It also serves as a buffer between secure and
insecure network systems.4
4 Timothy Nelson, Christopher Barratt, Daniel Dougherty, Kathi Fisler, and Shriram
Krishnamurthi, “The Margrave Tool for Firewall Analysis." In LISA, pp. 1-18. 2010.
not conform. When you compare both the external and internal firewall, the internal
firewall brings in stricter function of filtering so that it can protect the company’s
workstations and servers from external attacks. The DMZ is located between the internal
and external firewall since a portion of the data is given access to users which include
FTP servers, web server among others. It also serves as a buffer between secure and
insecure network systems.4
4 Timothy Nelson, Christopher Barratt, Daniel Dougherty, Kathi Fisler, and Shriram
Krishnamurthi, “The Margrave Tool for Firewall Analysis." In LISA, pp. 1-18. 2010.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Bibliography
1. Carrie, Martial, and James C. Wilshire. "Virtual extension of buffer to reduce buffer
overflow during tracing." U.S. Patent 8,612,650, issued December 17, 2013.
2. Jhaveri, Rutvij H., Sankita J. Patel, and Devesh C. Jinwala. "DoS attacks in mobile ad
hoc networks: A survey." In 2012 second international conference on advanced
computing & communication technologies, pp. 535-541. IEEE, 2012.
3. Wang, Ping, Lei Wu, Ryan Cunningham, and Cliff C. Zou. "Honeypot detection in
advanced botnet attacks." International Journal of Information and Computer Security 4,
no. 1 (2010): 30-51.
4. Nelson, Timothy, Christopher Barratt, Daniel J. Dougherty, Kathi Fisler, and Shriram
Krishnamurthi. "The Margrave Tool for Firewall Analysis." In LISA, pp. 1-18. 2010.
1. Carrie, Martial, and James C. Wilshire. "Virtual extension of buffer to reduce buffer
overflow during tracing." U.S. Patent 8,612,650, issued December 17, 2013.
2. Jhaveri, Rutvij H., Sankita J. Patel, and Devesh C. Jinwala. "DoS attacks in mobile ad
hoc networks: A survey." In 2012 second international conference on advanced
computing & communication technologies, pp. 535-541. IEEE, 2012.
3. Wang, Ping, Lei Wu, Ryan Cunningham, and Cliff C. Zou. "Honeypot detection in
advanced botnet attacks." International Journal of Information and Computer Security 4,
no. 1 (2010): 30-51.
4. Nelson, Timothy, Christopher Barratt, Daniel J. Dougherty, Kathi Fisler, and Shriram
Krishnamurthi. "The Margrave Tool for Firewall Analysis." In LISA, pp. 1-18. 2010.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





