Comprehensive Analysis of Network Security Protocols and Models
VerifiedAdded on 2022/10/31
|26
|4499
|411
Homework Assignment
AI Summary
This assignment solution delves into network security, covering the movement of packets within the OSI model, including the roles of each layer and the encapsulation process. It explores wireless MAC protocols, specifically focusing on collision detection and data retransmission techniques. The solution also discusses the inevitability of IPv6 in future technology, highlighting its advantages over IPv4, such as a larger address space and simplified routing. It includes a comparative analysis of IPv4 and IPv6, outlining differences in address length, header structure, and addressing modes. Finally, the assignment examines various IPv6 addressing models, including unicast, multicast, and anycast, explaining their functionalities and applications in network communication.

1
Network security
Student’s Name:
Institution Affiliation:
Network security
Student’s Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Task 2
a) How packet moves in OSI model
As a normal client, the most widely recognized method for associating with a PC would be by
means of an application. In the case of perusing the web, browsing messages, or tuning in to the
most recent scene of The 443 Podcast, run of the mill utilization involves clicking and
composing. All the preparing that a PC does is out of sight and programmed, luckily, as the
specialized subtleties can get slightly muddled. When directing system based exercises, activities
are done by the hidden working framework (OS) and incorporates the need to change a client's
solicitation into a system proper arrangement.
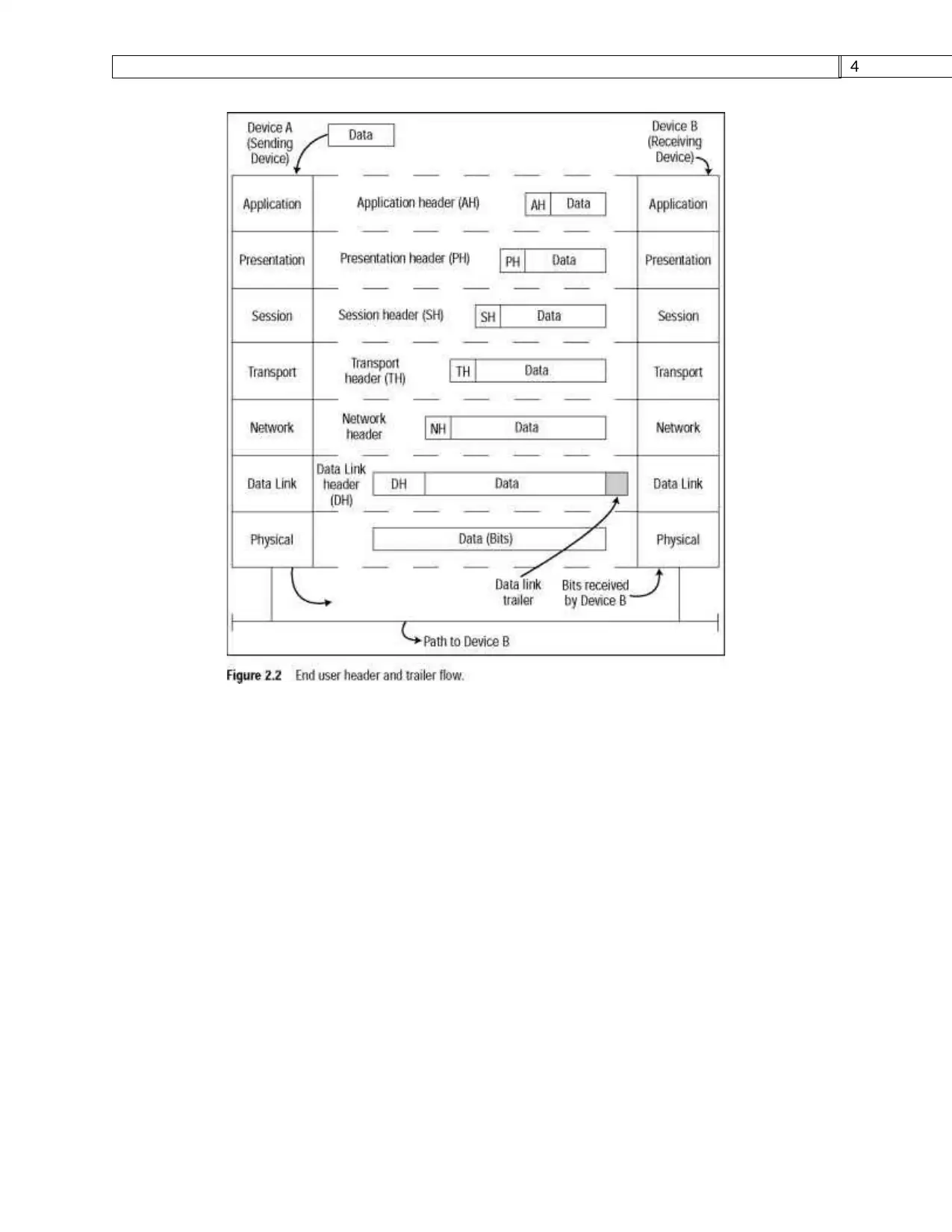
After a solicitation is made, it is changed by the fundamental OS into a payload or information
(allude to Figure 1 Data unit section esteems). Since this payload is made at the Application
(Layer 7 of OSI, Layer 4 of TCP/IP Model), consider it that application's method for organizing
the information by methods for the predefined convention. On the off chance that a client is
utilizing an internet browser, they'll be making HTTP demands, email use would involve
IMAP/POP3/SMTP, and so on. Information on any layer is alluded to as a convention
information unit (PDU). Each consequent layer embodies the past layer's PDU with that layer's
particular headers and is then sent to the following layer(Araújo, Bergman, & Leach, 2017).
Since we start on the Application Layer, there is just that layer's payload information. At the
point when that layer's PDU is sent to the following layer (following the TCP/IP model, it would
Task 2
a) How packet moves in OSI model
As a normal client, the most widely recognized method for associating with a PC would be by
means of an application. In the case of perusing the web, browsing messages, or tuning in to the
most recent scene of The 443 Podcast, run of the mill utilization involves clicking and
composing. All the preparing that a PC does is out of sight and programmed, luckily, as the
specialized subtleties can get slightly muddled. When directing system based exercises, activities
are done by the hidden working framework (OS) and incorporates the need to change a client's
solicitation into a system proper arrangement.
After a solicitation is made, it is changed by the fundamental OS into a payload or information
(allude to Figure 1 Data unit section esteems). Since this payload is made at the Application
(Layer 7 of OSI, Layer 4 of TCP/IP Model), consider it that application's method for organizing
the information by methods for the predefined convention. On the off chance that a client is
utilizing an internet browser, they'll be making HTTP demands, email use would involve
IMAP/POP3/SMTP, and so on. Information on any layer is alluded to as a convention
information unit (PDU). Each consequent layer embodies the past layer's PDU with that layer's
particular headers and is then sent to the following layer(Araújo, Bergman, & Leach, 2017).
Since we start on the Application Layer, there is just that layer's payload information. At the
point when that layer's PDU is sent to the following layer (following the TCP/IP model, it would

3
be Transport Layer however OSI has a couple of middle person layers), the PDU is known as a
portion if TCP is utilized as the Transport convention or datagram if UDP is utilized. When
gotten by the Transport Layer (most regular would be the utilization of TCP to guarantee
legitimate message conveyance), this layer embodies the Application Layer's PDU with the
source and goal ports(Eckert, Balaji, & Freed, 2018).
Descending the line, the Internet Layer would get the Transport Layer's PDU, typify it with the
source and goal IP addresses, at that point send the whole bundle to the suitable beneficiary.
When the beneficiary's system entryway gadget (allowed there is one, maybe a firewall or
switch, and the server isn't legitimately associated with the Internet) gets the parcel, it does what
it does and finds the real nearby have that ought to get the information. Door gadgets keep track
by means of port sending, or Static NAT'ing, explicit administration ports to their separate
administration server system(s). The door gadget, if pertinent, would decide the Media Access
Control (MAC) address of that framework by methods for location goals convention (ARP), at
that point typify the bundle, once more, into a casing that is then gotten by the framework
offering the administration.
be Transport Layer however OSI has a couple of middle person layers), the PDU is known as a
portion if TCP is utilized as the Transport convention or datagram if UDP is utilized. When
gotten by the Transport Layer (most regular would be the utilization of TCP to guarantee
legitimate message conveyance), this layer embodies the Application Layer's PDU with the
source and goal ports(Eckert, Balaji, & Freed, 2018).
Descending the line, the Internet Layer would get the Transport Layer's PDU, typify it with the
source and goal IP addresses, at that point send the whole bundle to the suitable beneficiary.
When the beneficiary's system entryway gadget (allowed there is one, maybe a firewall or
switch, and the server isn't legitimately associated with the Internet) gets the parcel, it does what
it does and finds the real nearby have that ought to get the information. Door gadgets keep track
by means of port sending, or Static NAT'ing, explicit administration ports to their separate
administration server system(s). The door gadget, if pertinent, would decide the Media Access
Control (MAC) address of that framework by methods for location goals convention (ARP), at
that point typify the bundle, once more, into a casing that is then gotten by the framework
offering the administration.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
b) Protocol for detecting collision and retransmitting of data
A Wireless MAC Protocol
The most prominent techniques for managing parcel crashes at the Medium Access Control
(MAC) layer in appropriated remote systems utilize a mix of bearer detecting and impact
evasion. At the point when the crash shirking methodology flops such plans can't recognize
impacts, and undermined information edges are as yet transmitted completely, in this way
squandering the channel transfer speed and fundamentally diminishing the system throughput.
To address this issue, this paper proposes another remote MAC convention fit for crash
recognition. The essential thought of the proposed convention is the utilization of heartbeats in
an out-of-band control channel for investigating channel condition and medium reservation and
accomplishing both crash evasion and impact location. The presentation of the proposed MAC
convention has been examined utilizing broad investigation and reproductions. Our outcomes
demonstrate that as contrasted and existing MAC conventions, the proposed convention has
noteworthy execution gains as far as hub throughput. Furthermore, the proposed convention is
completely circulated and requires no time synchronization among hubs(Zarbakhshnia,
Soleimani, Goh, and Razavi, 2019). The most well known methodologies for managing parcel
impacts at the medium access control (MAC) layer in appropriated remote systems utilize a
blend of bearer detecting and crash shirking. At the point when the crash shirking technique
comes up short, such plans can't recognize impacts and debased information casings are as yet
transmitted completely, in this way squandering the channel transmission capacity and altogether
b) Protocol for detecting collision and retransmitting of data
A Wireless MAC Protocol
The most prominent techniques for managing parcel crashes at the Medium Access Control
(MAC) layer in appropriated remote systems utilize a mix of bearer detecting and impact
evasion. At the point when the crash shirking methodology flops such plans can't recognize
impacts, and undermined information edges are as yet transmitted completely, in this way
squandering the channel transfer speed and fundamentally diminishing the system throughput.
To address this issue, this paper proposes another remote MAC convention fit for crash
recognition. The essential thought of the proposed convention is the utilization of heartbeats in
an out-of-band control channel for investigating channel condition and medium reservation and
accomplishing both crash evasion and impact location. The presentation of the proposed MAC
convention has been examined utilizing broad investigation and reproductions. Our outcomes
demonstrate that as contrasted and existing MAC conventions, the proposed convention has
noteworthy execution gains as far as hub throughput. Furthermore, the proposed convention is
completely circulated and requires no time synchronization among hubs(Zarbakhshnia,
Soleimani, Goh, and Razavi, 2019). The most well known methodologies for managing parcel
impacts at the medium access control (MAC) layer in appropriated remote systems utilize a
blend of bearer detecting and crash shirking. At the point when the crash shirking technique
comes up short, such plans can't recognize impacts and debased information casings are as yet
transmitted completely, in this way squandering the channel transmission capacity and altogether

6
diminishing the system throughput. To address this issue, this paper proposes another remote
MAC convention fit for impact identification. The fundamental thought of the proposed
convention is the utilization of heartbeats in an out-of-band control channel for investigating
channel condition and medium reservation and accomplishing both crash evasion and impact
discovery. The exhibition of the proposed MAC convention has been examined utilizing broad
investigation and recreations. Our outcomes demonstrate that, as contrasted and existing MAC
conventions, the proposed convention has noteworthy execution gains regarding hub throughput.
Also, the proposed convention is completely appropriated and requires no time synchronization
among hubs(Burt, Akins, Latham, Beck, Salomon, and Ban, 2018).
diminishing the system throughput. To address this issue, this paper proposes another remote
MAC convention fit for impact identification. The fundamental thought of the proposed
convention is the utilization of heartbeats in an out-of-band control channel for investigating
channel condition and medium reservation and accomplishing both crash evasion and impact
discovery. The exhibition of the proposed MAC convention has been examined utilizing broad
investigation and recreations. Our outcomes demonstrate that, as contrasted and existing MAC
conventions, the proposed convention has noteworthy execution gains regarding hub throughput.
Also, the proposed convention is completely appropriated and requires no time synchronization
among hubs(Burt, Akins, Latham, Beck, Salomon, and Ban, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
Utilizing conflict based medium access control (MAC) conventions in submerged sensor systems
(UWSNs) is regularly expensive. This is because of the one of a kind attributes of submerged
acoustic channels, for example, long proliferation delay, constrained data transfer capacity, and
high piece mistake rate. As a result, the conflict based (handshaking and irregular access-based)
MAC conventions don't execute as effectively true to form. The crash free approach is in this
way considered to accomplish superior by dodging the impacts at the MAC layer so as to
improve vitality effectiveness, throughput, and decency. Our broad execution study demonstrates
that GC-MAC performs well by maintaining a strategic distance from impacts to accomplish
better throughput and vitality productivity execution contrasted and those of dispute based
conventions. There is likewise a huge improvement regarding parcel conveyance proportion and
reasonableness among the hubs under various operational conditions(Cervero, Denman, and Jin,
2019).
Task 3
a) Why IPV6 is inevitable in future technology
The most promoted highlight of IPv6 is the bigger location space. In the event that you've
perused anything about IPv6, at that point you likely realize that it expands the location size from
32 bits to 128. This is all that could possibly be needed for each individual at any point destined
to have a private system greater than the present Internet. Regardless of whether all that you
claim (counting things that don't contain any hardware) had its own IPv6 address, at that point
Utilizing conflict based medium access control (MAC) conventions in submerged sensor systems
(UWSNs) is regularly expensive. This is because of the one of a kind attributes of submerged
acoustic channels, for example, long proliferation delay, constrained data transfer capacity, and
high piece mistake rate. As a result, the conflict based (handshaking and irregular access-based)
MAC conventions don't execute as effectively true to form. The crash free approach is in this
way considered to accomplish superior by dodging the impacts at the MAC layer so as to
improve vitality effectiveness, throughput, and decency. Our broad execution study demonstrates
that GC-MAC performs well by maintaining a strategic distance from impacts to accomplish
better throughput and vitality productivity execution contrasted and those of dispute based
conventions. There is likewise a huge improvement regarding parcel conveyance proportion and
reasonableness among the hubs under various operational conditions(Cervero, Denman, and Jin,
2019).
Task 3
a) Why IPV6 is inevitable in future technology
The most promoted highlight of IPv6 is the bigger location space. In the event that you've
perused anything about IPv6, at that point you likely realize that it expands the location size from
32 bits to 128. This is all that could possibly be needed for each individual at any point destined
to have a private system greater than the present Internet. Regardless of whether all that you
claim (counting things that don't contain any hardware) had its own IPv6 address, at that point

9
you would in any case not be utilizing in excess of a little division of the location space(Farrokh,
Azar, Jandaghi, and Ahmadi, 2018).
This is very significant in light of the fact that it can make directing simpler. Switches ordinarily
associate a generally modest number of systems together. The most straightforward case is your
home switch, which interfaces your nearby system to the Internet. For each bundle that it gets, it
must do one of three things: drop it, forward it to the inside system, or forward it to the outer
system(Constantin, and Niţescu, 2018, October).
For a common home system, this is a significant simple choice: If the goal address is in one of
the held private extents, send it inside; generally send it out. Huge business switches need to
settle on substantially more intricate choices. Since the mid '90s, when IPv4 addresses began to
be viewed as a rare asset, they have been apportioned in 8-piece ranges. This implies you may
get three adjoining hinders on totally various systems. With this assignment plot, there are 2^24
potential systems, and a switch should have the option to choose which association along which
a parcel bound for any of them ought to be sent. 2^24 is somewhat less than 17 million. Luckily,
a great deal of these will be easier, so you can join their entrances, yet it's as yet hard to settle on
directing choices(Xu, Batke, Yu, Brandt, & Whitehead, 2018).
With IPv6, there are sufficient tends to since each nation or real system can be allocated an
enormous range. It would then be able to allot subranges inside that to systems that it interfaces
with, etc. This various leveled task (in principle, at any rate) rearranges directing choices.
you would in any case not be utilizing in excess of a little division of the location space(Farrokh,
Azar, Jandaghi, and Ahmadi, 2018).
This is very significant in light of the fact that it can make directing simpler. Switches ordinarily
associate a generally modest number of systems together. The most straightforward case is your
home switch, which interfaces your nearby system to the Internet. For each bundle that it gets, it
must do one of three things: drop it, forward it to the inside system, or forward it to the outer
system(Constantin, and Niţescu, 2018, October).
For a common home system, this is a significant simple choice: If the goal address is in one of
the held private extents, send it inside; generally send it out. Huge business switches need to
settle on substantially more intricate choices. Since the mid '90s, when IPv4 addresses began to
be viewed as a rare asset, they have been apportioned in 8-piece ranges. This implies you may
get three adjoining hinders on totally various systems. With this assignment plot, there are 2^24
potential systems, and a switch should have the option to choose which association along which
a parcel bound for any of them ought to be sent. 2^24 is somewhat less than 17 million. Luckily,
a great deal of these will be easier, so you can join their entrances, yet it's as yet hard to settle on
directing choices(Xu, Batke, Yu, Brandt, & Whitehead, 2018).
With IPv6, there are sufficient tends to since each nation or real system can be allocated an
enormous range. It would then be able to allot subranges inside that to systems that it interfaces
with, etc. This various leveled task (in principle, at any rate) rearranges directing choices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
One of the significant protests about IPv6 originates from individuals who think NAT is security
and confound "routable" with "available." With IPv4, most home clients (and practically all
versatile clients) use system address interpretation (NAT). Your PC has a private IP address, and
the switch has an open one. Each associated port on your private IP is mapped to a port on the
open IP address. This doesn't give any security. Most NAT executions additionally default to
denying associations beginning outside, while some will advance these to an assigned default
have.
The arrangement of denying remotely starting associations gives security, however that is given
by the firewall part of the switch and isn't natural for NAT. Most non-NAT firewalls will do
likewise(Rahman, 2018).
Because your PC has a remotely routable IPv6 address doesn't imply that it's available. The
firewall gadget that you plug in to your Internet association still characterizes the approach of
who can interface. Given the quantity of hacks used to infiltrate NATs to make things like Voice
over IP work, it's astounding that despite everything anybody thinks it includes security, yet
clearly some do.
b) Header diagram for IPV6 and IPV4
One of the significant protests about IPv6 originates from individuals who think NAT is security
and confound "routable" with "available." With IPv4, most home clients (and practically all
versatile clients) use system address interpretation (NAT). Your PC has a private IP address, and
the switch has an open one. Each associated port on your private IP is mapped to a port on the
open IP address. This doesn't give any security. Most NAT executions additionally default to
denying associations beginning outside, while some will advance these to an assigned default
have.
The arrangement of denying remotely starting associations gives security, however that is given
by the firewall part of the switch and isn't natural for NAT. Most non-NAT firewalls will do
likewise(Rahman, 2018).
Because your PC has a remotely routable IPv6 address doesn't imply that it's available. The
firewall gadget that you plug in to your Internet association still characterizes the approach of
who can interface. Given the quantity of hacks used to infiltrate NATs to make things like Voice
over IP work, it's astounding that despite everything anybody thinks it includes security, yet
clearly some do.
b) Header diagram for IPV6 and IPV4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
c) Comparative analysis between IPV4 and IPV6
IPv4 has 32-piece address length while IPv6 has 128-piece address length.
IPv4 addresses speak to the parallel numbers in decimals. Then again, IPv6 addresses
c) Comparative analysis between IPV4 and IPV6
IPv4 has 32-piece address length while IPv6 has 128-piece address length.
IPv4 addresses speak to the parallel numbers in decimals. Then again, IPv6 addresses

12
express paired numbers in hexadecimal.
IPv6 uses start to finish discontinuity while IPv4 requires a middle of the road switch to
piece any datagram that is excessively huge.
Header length of IPv4 is 20 bytes. Conversely, header length of IPv6 is 40 bytes.
IPv4 utilizes checksum field in the header group for dealing with blunder checking.
Despite what might be expected, IPv6 evacuates the header checksum field.
In IPv4, the base header doesn't contain a field for header length, and 16-piece payload
length field replaces it in the IPv6 header.
The alternative fields in IPv4 are utilized as expansion headers in IPv6.
The Time to live field in IPv4 alludes to as Hop limit in IPv6.
The header length field which is available in IPv4 is disposed of in IPv6 on the grounds
that the length of the header is fixed in this adaptation.
IPv4 uses broadcasting to transmit the parcels to the goal PCs while IPv6 utilizes
multicasting and anycasting.
IPv6 gives verification and encryption, yet IPv4 doesn't give it.
express paired numbers in hexadecimal.
IPv6 uses start to finish discontinuity while IPv4 requires a middle of the road switch to
piece any datagram that is excessively huge.
Header length of IPv4 is 20 bytes. Conversely, header length of IPv6 is 40 bytes.
IPv4 utilizes checksum field in the header group for dealing with blunder checking.
Despite what might be expected, IPv6 evacuates the header checksum field.
In IPv4, the base header doesn't contain a field for header length, and 16-piece payload
length field replaces it in the IPv6 header.
The alternative fields in IPv4 are utilized as expansion headers in IPv6.
The Time to live field in IPv4 alludes to as Hop limit in IPv6.
The header length field which is available in IPv4 is disposed of in IPv6 on the grounds
that the length of the header is fixed in this adaptation.
IPv4 uses broadcasting to transmit the parcels to the goal PCs while IPv6 utilizes
multicasting and anycasting.
IPv6 gives verification and encryption, yet IPv4 doesn't give it.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.